基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.222 |
80
一个普通的web,页面信息能够得到子域名,contact里可以得到8065端口:


那就把已知信息加hosts:
1 | 10.10.10.222 helpdesk.delivery.htb delivery.htb |
8065
一个什么系统,需要登录,可以注册:

随意注册提示需要验证,但自己的邮箱并没有收到,应该是需要某种方式获取它分配的邮箱:
helpdesk
转去helpdesk,就是常规的helpdesk系统:
new ticket
创建一个ticket,得到一个邮箱地址和ticket id:
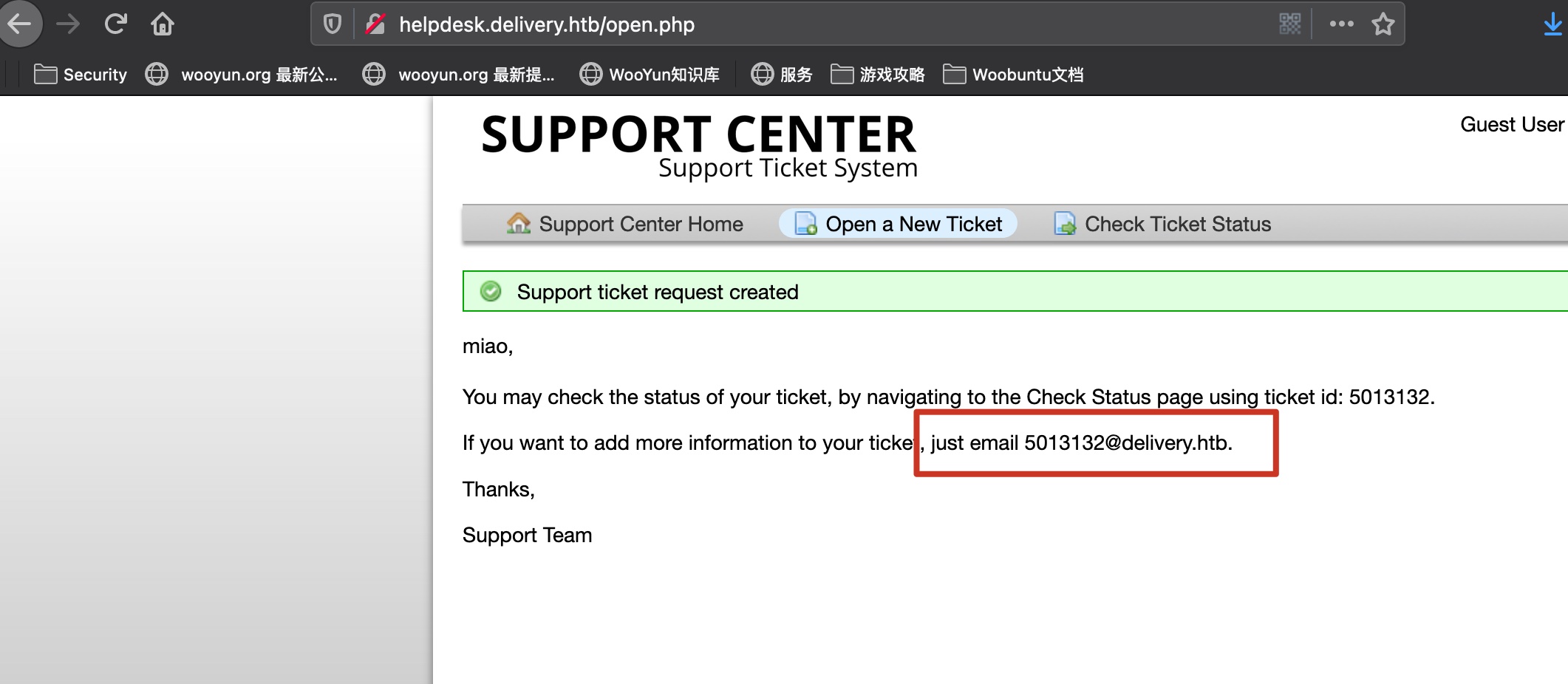
check ticket status
Check status就是进入分配给我们的邮箱的收件箱:
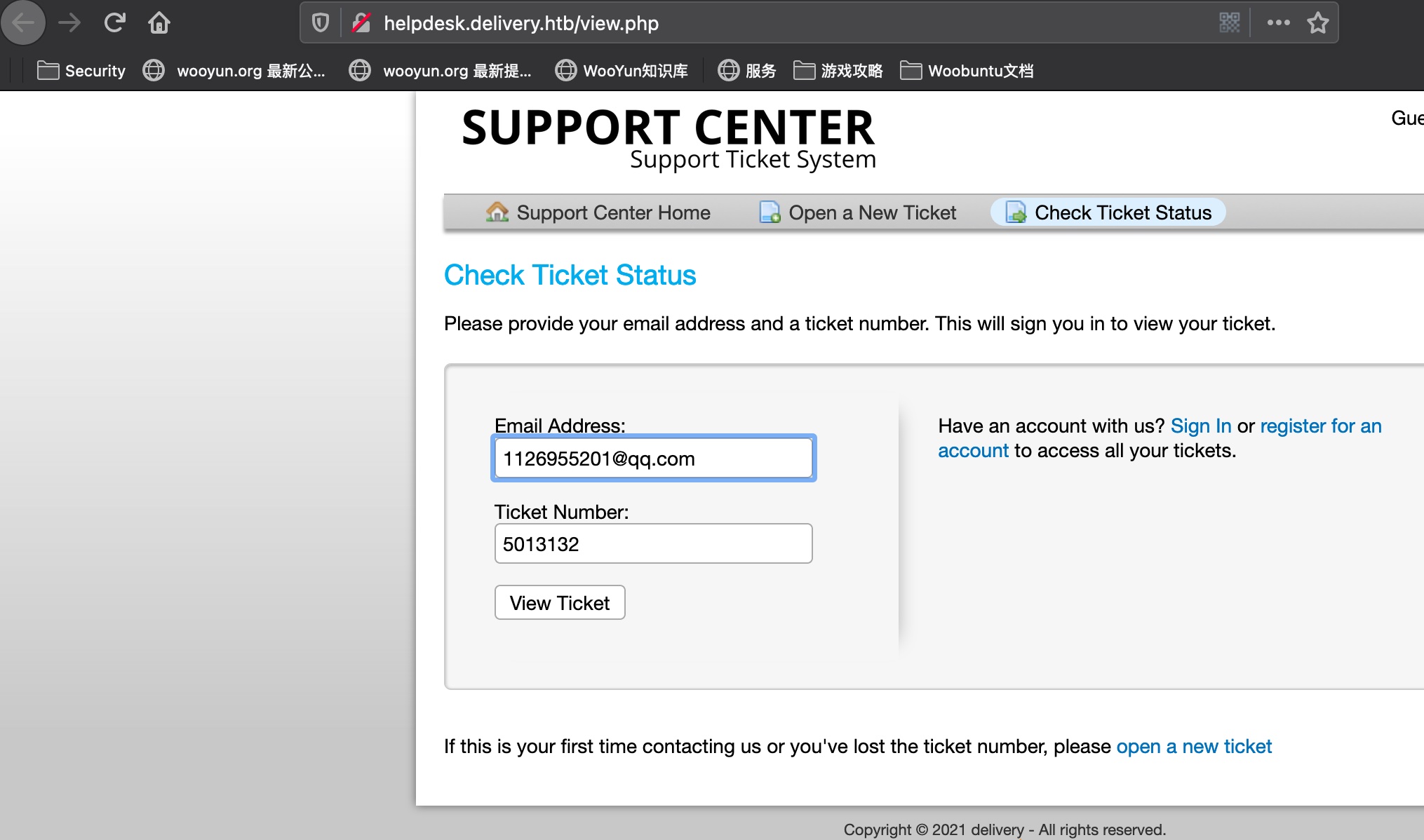
8065 create account
然后去8065使用这个邮箱创建账号:

get verify email
之后去收件箱查看新邮件:

可以看到验证信息:
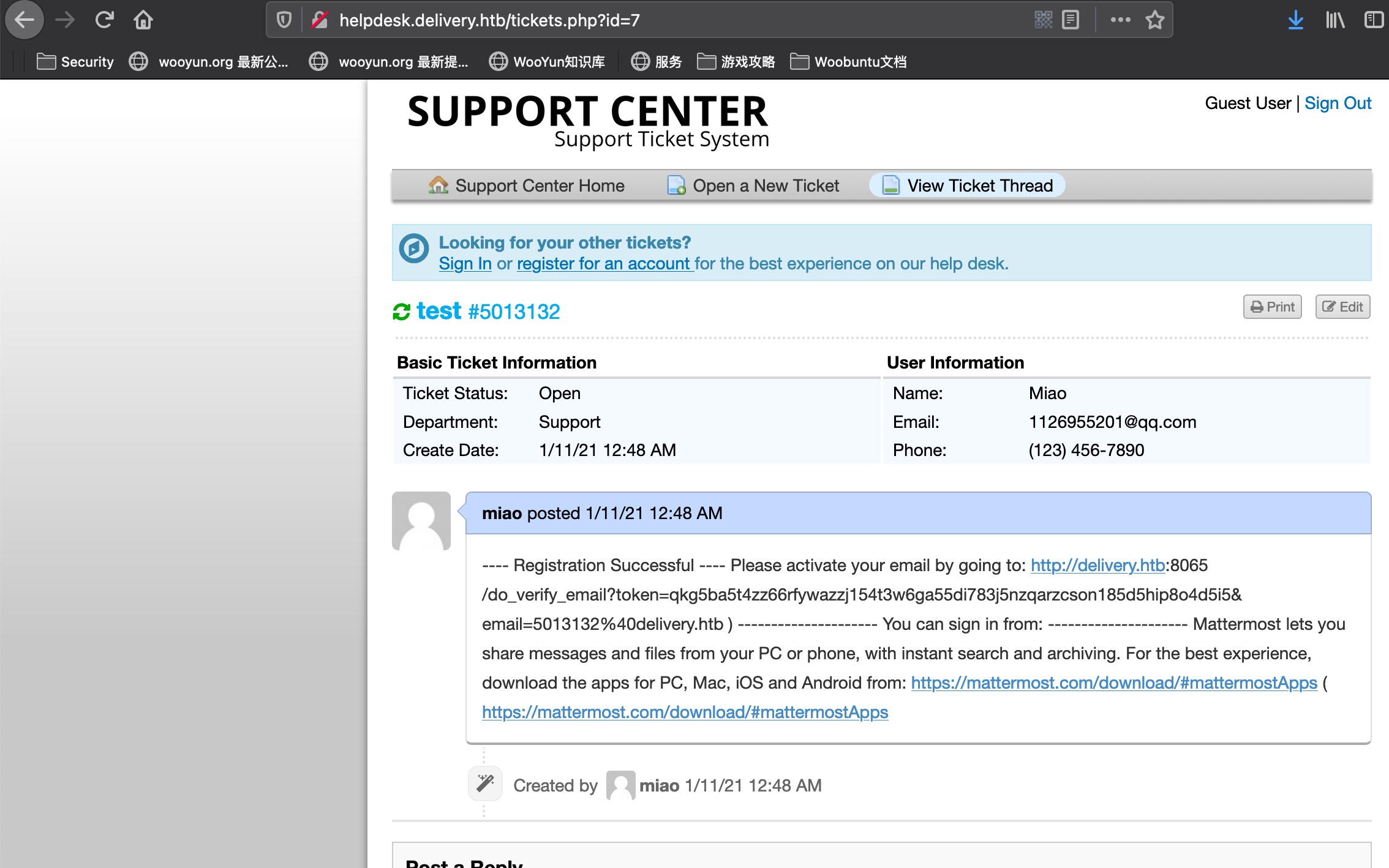
verify email
直接新开一个标签页复制粘贴访问验证链接,验证成功,登录:
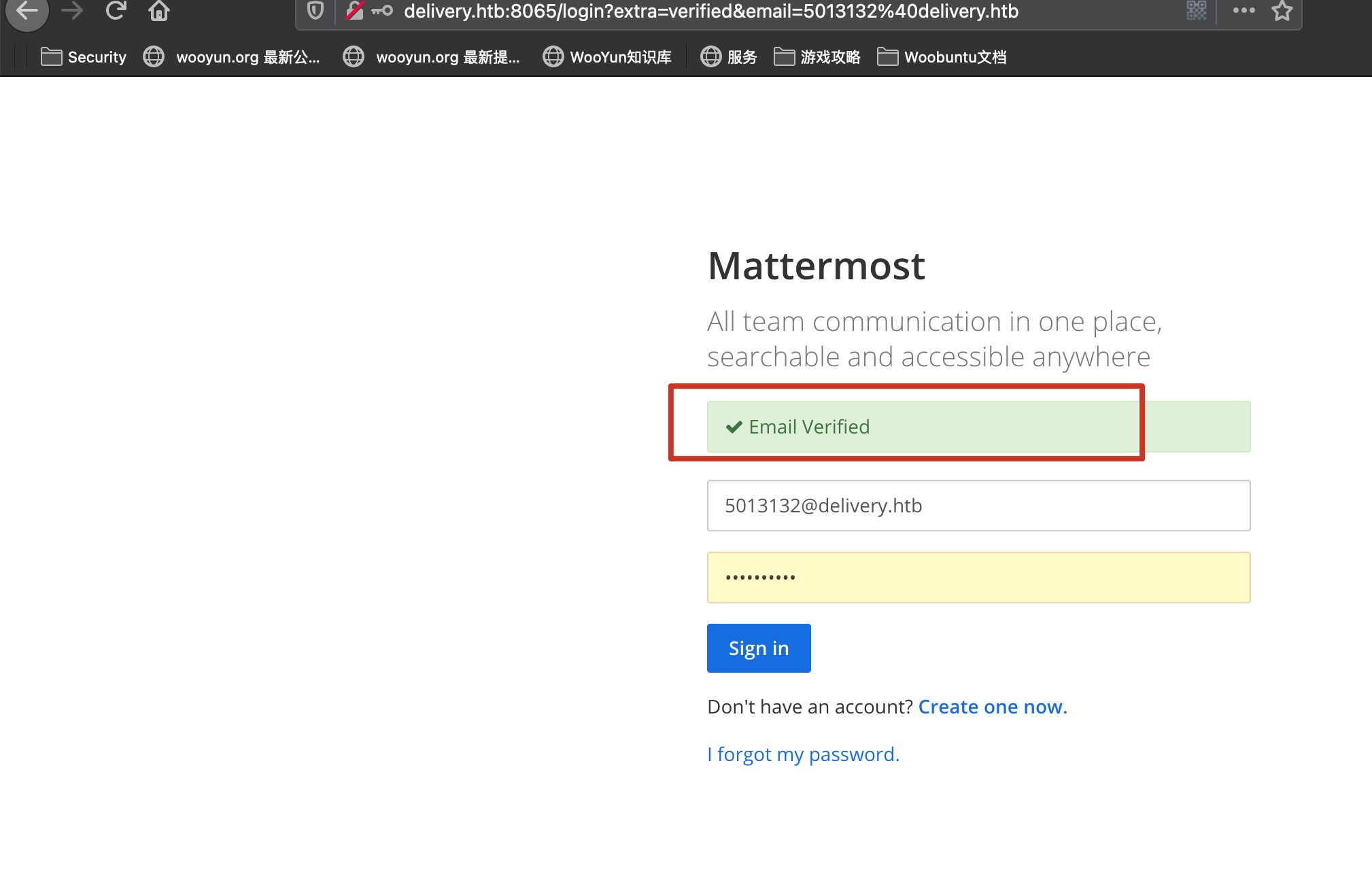

internal
进入internal,跳过教程:
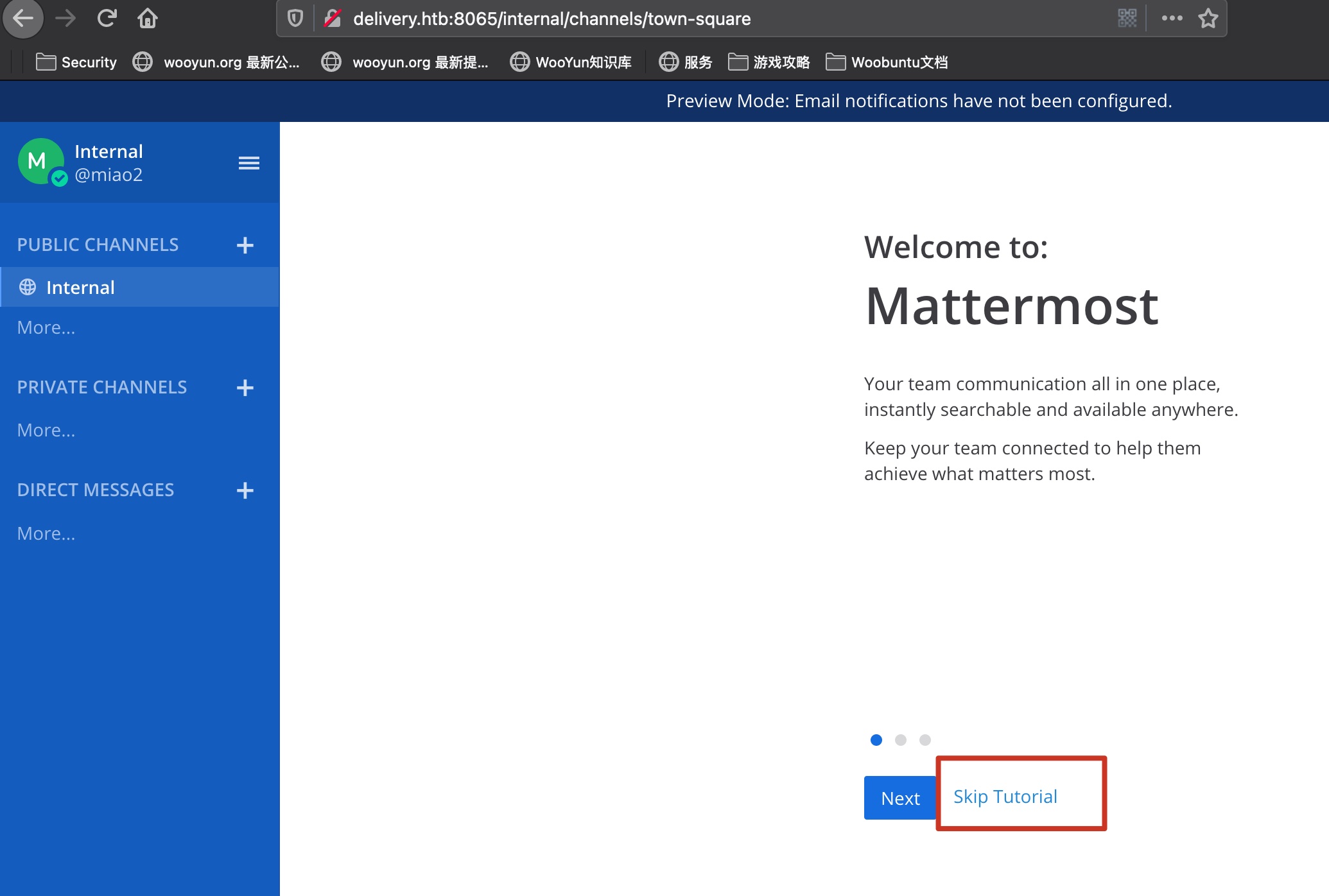
这里其实是后面的提示信息,上面那一行是一组用户名密码:

1 | @developers Please update theme to the OSTicket before we go live. Credentials to the server are maildeliverer:Youve_G0t_Mail! |
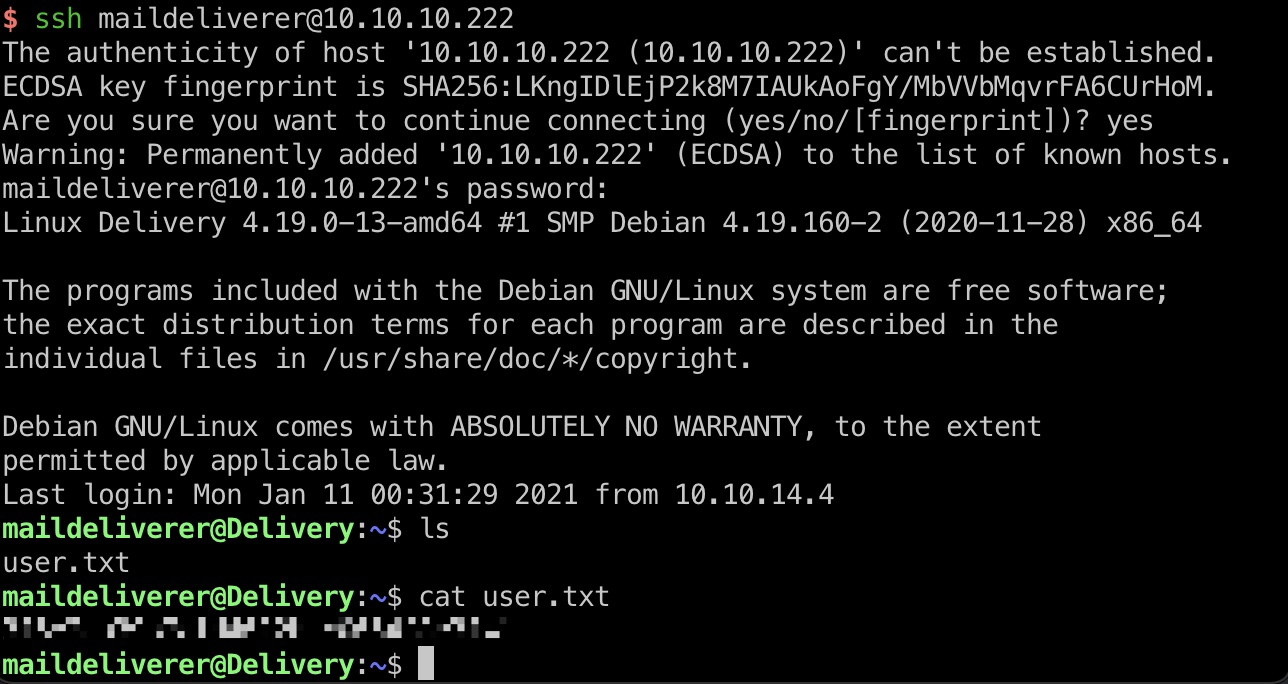
user flag
然后直接ssh连接,得到user.txt:
1 | maildeliverer:Youve_G0t_Mail! |
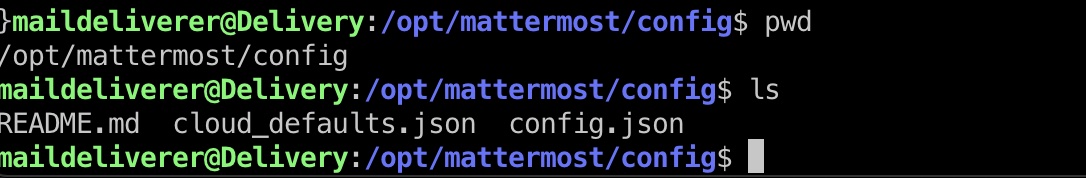
提权信息
/opt/mattermost/config目录里是配置信息,里面有mysql连接信息:
1 | mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s |
mysql
mysql里查看数据,得到root密码hash:
1 | mysql -u mmuser -p'Crack_The_MM_Admin_PW' mattermost |
config.json
1 | ... |
hash crack
这个hash直接常规方式跑不出来的,根据前面的提示信息,PleaseSubscribe! 不在rockyou里,需要根据提示生成新字典:
OneRuleToRuleThemAll
1 | git clone https://github.com/stealthsploit/Optimised-hashcat-Rule.git |
然后使用生成的新字典可以破解出来密码:
1 | sudo john -w=./wordlist.txt hash.txt |
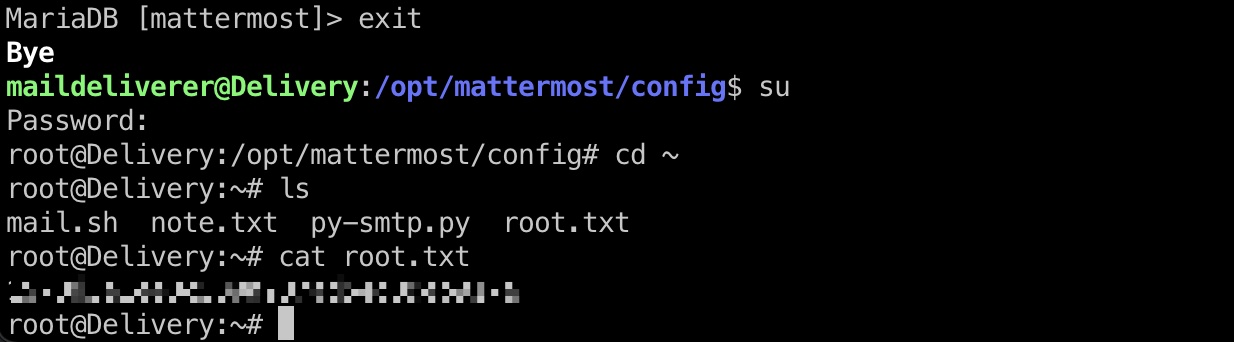
root flag
然后直接使用得到的密码切换到root,读取root.txt:
参考资料
- https://github.com/stealthsploit/Optimised-hashcat-Rule
- Hackthebox Delivery writeup | 0xDedinfosec
https://0xdedinfosec.github.io/posts/htb-delivery/